Powerpoint Templates and Google slides for Secure Work
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
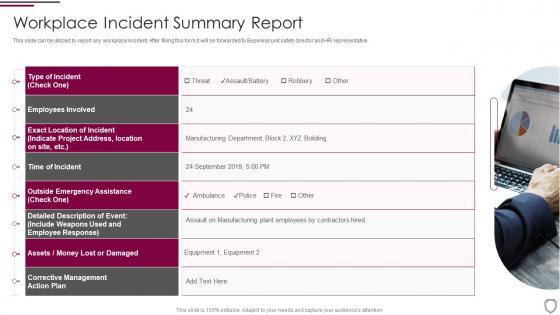 Workplace incident summary report corporate security management
Workplace incident summary report corporate security managementThis slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. Increase audience engagement and knowledge by dispensing information using Workplace Incident Summary Report Corporate Security Management. This template helps you present information on one stages. You can also present information on Workplace Incident Summary Report using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Workplace security policy procedures ppt powerpoint presentation outline images cpb
Workplace security policy procedures ppt powerpoint presentation outline images cpbPresenting our Workplace Security Policy Procedures Ppt Powerpoint Presentation Outline Images Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Workplace Security Policy Procedures This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Improve it security with vulnerability management how siem works
Improve it security with vulnerability management how siem worksIncrease audience engagement and knowledge by dispensing information using Improve It Security With Vulnerability Management How Siem Works. This template helps you present information on four stages. You can also present information on Databases, Applications, Security Device using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Real time analysis of security alerts how siem works
Real time analysis of security alerts how siem worksDeliver an outstanding presentation on the topic using this Real Time Analysis Of Security Alerts How Siem Works. Dispense information and present a thorough explanation of Correlation, Behavior Analytics, Taxonomy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security What Is Information Security And How Does It Work
Information Security What Is Information Security And How Does It WorkThis slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Increase audience engagement and knowledge by dispensing information using Information Security What Is Information Security And How Does It Work. This template helps you present information on five stages. You can also present information on Techniques, Procedures, Approach using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Program Categorization Worksheet For Assets Owned Organization
Information Security Program Categorization Worksheet For Assets Owned OrganizationThis slide illustrates asset categorization worksheet covering information about security system such as system name, its version, system location and other general information. Present the topic in a bit more detail with this Information Security Program Categorization Worksheet For Assets Owned Organization. Use it as a tool for discussion and navigation on Categorization, Worksheet, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Risk Assessment Worksheet Risk Management Framework For
Information Security Risk Assessment Worksheet Risk Management Framework ForMentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm. Present the topic in a bit more detail with this Information Security Risk Assessment Worksheet Risk Management Framework For. Use it as a tool for discussion and navigation on Threat Encountered, Vulnerability, Asset And Consequences, Risk To Firm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Risk Assessment Worksheet Cybersecurity Risk Management Framework
Information Security Risk Assessment Worksheet Cybersecurity Risk Management FrameworkMentioned slide illustrates information security risk assessment worksheet. It include information about threat encountered, its vulnerability, asset and consequences and risk to the firm. Present the topic in a bit more detail with this Information Security Risk Assessment Worksheet Cybersecurity Risk Management Framework. Use it as a tool for discussion and navigation on Threat Encountered, Vulnerability, Asset And Consequences, Risk To Firm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan handle financial crisis at workplace
Building organizational security strategy plan handle financial crisis at workplaceThis slide covers information regarding how firm can handle financial crisis by safeguarding financial stability in terms of abundant cash requirements, overhead analysis, currency hedging, etc. Introducing Building Organizational Security Strategy Plan Handle Financial Crisis At Workplace to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Information, Safeguarding, Financial, using this template. Grab it now to reap its full benefits.
-
 Budget for effective threat management workplace cyber security risk management
Budget for effective threat management workplace cyber security risk managementFirm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Present the topic in a bit more detail with this Budget For Effective Threat Management Workplace Cyber Security Risk Management. Use it as a tool for discussion and navigation on Incident Management, Risk Management, Client Onboarding Process, Document Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security risk management roles and responsibilities ensure work environment
Cyber security risk management roles and responsibilities ensure work environmentThis slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Roles And Responsibilities Ensure Work Enviro. This template helps you present information on four stages. You can also present information on Employee Responsibilities, Unit Supervisor, Manager Responsibilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber security risk management statistics associated to workplace threats
Cyber security risk management statistics associated to workplace threatsThis slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Introducing Cyber Security Risk Management Statistics Associated To Workplace Threats to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Attacks Costs, Organizations Face, Data Records, Business, Financial, using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management various types of workplace violence and threats
Cyber security risk management various types of workplace violence and threatsThis slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. Introducing Cyber Security Risk Management Various Types Of Workplace Violence And Threats to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Threats Or Threatening Behavior, Physical Assault, Property Damage, using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management workplace employee assistance program
Cyber security risk management workplace employee assistance programThe employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Risk Management Workplace Employee Assistance Program. This template helps you present information on three stages. You can also present information on Clinical Services, Work And Life Services, Employer Services, Online Resources, Offline Resources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Workplace incident summary report cyber security risk management
Workplace incident summary report cyber security risk managementThis slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. Deliver an outstanding presentation on the topic using this Workplace Incident Summary Report Cyber Security Risk Management. Dispense information and present a thorough explanation of Type Incident, Employees Involved, Time Incident, Assets Money Lost, Damaged using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Risk Assessment Worksheet
Information Security And Iso 27001 Risk Assessment WorksheetFollowing slide displays information security risk assessment worksheet. It covers details about risk encountered, its description, vulnerability asset and consequences and risk to the firm. Present the topic in a bit more detail with this Information Security And Iso 27001 Risk Assessment Worksheet. Use it as a tool for discussion and navigation on Risk Assessment Worksheet. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secured Working Capital Loans Ppt Powerpoint Presentation Ideas Master Slide Cpb
Secured Working Capital Loans Ppt Powerpoint Presentation Ideas Master Slide CpbPresenting our Secured Working Capital Loans Ppt Powerpoint Presentation Ideas Master Slide Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Secured Working Capital Loans This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Network Security What Is Network Security And How Does It Work
Network Security What Is Network Security And How Does It WorkThis slide defines the meaning of network security and how it helps to prevent data through different methods and techniques. Increase audience engagement and knowledge by dispensing information using Network Security What Is Network Security And How Does It Work. This template helps you present information on five stages. You can also present information on Approach, Methods, Techniques, Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security What Is Information Technology Security And How Does It Work
Information Technology Security What Is Information Technology Security And How Does It WorkThis slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Introducing Information Technology Security What Is Information Technology Security And How Does It Work to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Information, Technology, Security, using this template. Grab it now to reap its full benefits.
-
 Advantages And Working Of Secure Sdlc Software Development Life Cycle It
Advantages And Working Of Secure Sdlc Software Development Life Cycle ItThis slide represents the advantages and working of secure software development life cycle, including its various phases, such as concept, planning, design and development, testing, release, sustain, and disposal. Present the topic in a bit more detail with this Advantages And Working Of Secure Sdlc Software Development Life Cycle It. Use it as a tool for discussion and navigation on Organizations, Commercial, Development. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Siem For Security Analysis How Siem Works
Siem For Security Analysis How Siem WorksDeliver an outstanding presentation on the topic using this Siem For Security Analysis How Siem Works. Dispense information and present a thorough explanation of Network Device, Investigation, Correlation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing Asset Security Categorization Vulnerability Administration At Workplace
Addressing Asset Security Categorization Vulnerability Administration At WorkplaceThis slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Present the topic in a bit more detail with this Addressing Asset Security Categorization Vulnerability Administration At Workplace. Use it as a tool for discussion and navigation on Location, Availability, Categorization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Vulnerability Administration At Workplace Selecting Secured Threat Management Software
Vulnerability Administration At Workplace Selecting Secured Threat Management SoftwareThis slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Present the topic in a bit more detail with this Vulnerability Administration At Workplace Selecting Secured Threat Management Software. Use it as a tool for discussion and navigation on Management, Software, Workflows. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing physical security at workplace building organizational security strategy plan
Addressing physical security at workplace building organizational security strategy planThis slide provides information about physical security at workplace in terms of workplace surveillance, employee monitoring, and factors to consider while implementing physical security such as industry guidelines, authority codes. Increase audience engagement and knowledge by dispensing information using Addressing Physical Security At Workplace Building Organizational Security Strategy Plan. This template helps you present information on two stages. You can also present information on Physical, Workplace, Surveillance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Building organizational security strategy addressing workforce assistance program
Building organizational security strategy addressing workforce assistance programThe workforce assistance program will help firms in enhancing their well being at workplace and enable them to handle critical or emergence situations. This program will render services like clinical services, work and life services and employer services, etc. Increase audience engagement and knowledge by dispensing information using Building Organizational Security Strategy Addressing Workforce Assistance Program. This template helps you present information on five stages. You can also present information on Services, Resources, Assistance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Building organizational security strategy plan addressing role of chief security officer at workplace
Building organizational security strategy plan addressing role of chief security officer at workplaceThis slide provides information regarding role of chief security officer at workplace and determine their key priorities in terms of day to day operations, security, compliance, innovation, etc. Deliver an outstanding presentation on the topic using this Building Organizational Security Strategy Plan Addressing Role Of Chief Security Officer At Workplace. Dispense information and present a thorough explanation of Management, Workplace, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Building organizational security strategy plan contingency plan for threat handling at workplace
Building organizational security strategy plan contingency plan for threat handling at workplaceThis slide portrays information contingency plan for handling threats at workplace with the help of technical equipment that assist contingency solution and considerations. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Contingency Plan For Threat Handling At Workplace. Use it as a tool for discussion and navigation on Workplace, Information, Equipment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan determine security policy framework at workplace
Building organizational security strategy plan determine security policy framework at workplaceThis slide provides information about security policy framework at workplace in terms of management, operational procedures, information, personnel, training, crisis management, etc. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Determine Security Policy Framework At Workplace. Use it as a tool for discussion and navigation on Framework, Workplace, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan effective security management at workplace
Building organizational security strategy plan effective security management at workplaceThis slide portrays information regarding how firm is successful in handling security issues or events and is able in reducing the occurrence of events. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Effective Security Management At Workplace. Use it as a tool for discussion and navigation on Management, Workplace, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan how firm handle various insider threats at workplace
Building organizational security strategy plan how firm handle various insider threats at workplaceThis slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. Introducing Building Organizational Security Strategy Plan How Firm Handle Various Insider Threats At Workplace to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Workplace, Information, Coordination, using this template. Grab it now to reap its full benefits.
-
 Building organizational security strategy plan workplace crisis incident summary report
Building organizational security strategy plan workplace crisis incident summary reportThis slide can be utilized to report any workplace violence. After filling this form it will be forwarded to Business unit safety director and HR representative. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Workplace Crisis Incident Summary Report. Use it as a tool for discussion and navigation on Business, Representative, Workplace. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan workplace physical security audit checklist
Building organizational security strategy plan workplace physical security audit checklistThis slide provides information about physical security audit checklist at workplace in terms of general, roofing, HVAC, plumbing, lighting, etc. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Workplace Physical Security Audit Checklist. Use it as a tool for discussion and navigation on Workplace, Physical, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introducing security at workplace to ensure assets safety building organizational security strategy plan
Introducing security at workplace to ensure assets safety building organizational security strategy planThis slide provides information about introducing security at workplace in order to ensure assets safety and details regarding security mission statement and objectives. Introducing Introducing Security At Workplace To Ensure Assets Safety Building Organizational Security Strategy Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information, Organizational, Strategy, using this template. Grab it now to reap its full benefits.
-
 Enhancing overall project security it budget for effective project management at workplace
Enhancing overall project security it budget for effective project management at workplaceFirm has prepared a budget for managing projects effectively by optimizing various functional areas across workplace. It also provides information about the software used and the duration required for implementation. Present the topic in a bit more detail with this Enhancing Overall Project Security It Budget For Effective Project Management At Workplace. Use it as a tool for discussion and navigation on Management, Workplace, Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enhancing overall project security it roles and responsibilities to ensure work environment
Enhancing overall project security it roles and responsibilities to ensure work environmentThis slide provides information regarding roles and responsibilities assigned to ensure minimum violence work environment. Introducing Enhancing Overall Project Security It Roles And Responsibilities To Ensure Work Environment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Environment, Responsibilities, Resources, using this template. Grab it now to reap its full benefits.
-
 Enhancing overall project security it workplace employee assistance program
Enhancing overall project security it workplace employee assistance programThe employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Introducing Enhancing Overall Project Security It Workplace Employee Assistance Program to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Organizational, Management, Consultations, using this template. Grab it now to reap its full benefits.
-
 Workplace security policies ppt powerpoint presentation background images cpb
Workplace security policies ppt powerpoint presentation background images cpbPresenting Workplace Security Policies Ppt Powerpoint Presentation Background Images Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Workplace Security Policies. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Q70 Risk Management Framework For Information Security Incident Management Workflow Process
Q70 Risk Management Framework For Information Security Incident Management Workflow ProcessFollowing slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Present the topic in a bit more detail with this Q70 Risk Management Framework For Information Security Incident Management Workflow Process. Use it as a tool for discussion and navigation on Incident Occurs, Team Takes Action, Auto Alerting, Fail Over Report, Organize Team, Incident Resolution. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business Security Management Four Stage Workflow
Business Security Management Four Stage WorkflowThe purpose of this slide is to outline the risk management procedures in a business organization and to provide desired solutions. This includes four steps- monitor, identify, evaluate and treat Presenting our set of slides with name Business Security Management Four Stage Workflow. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Business, Management, Evaluate.
-
 Android Device Security Management Determine Various Mobile Devices Existing At Workplace
Android Device Security Management Determine Various Mobile Devices Existing At WorkplaceThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Present the topic in a bit more detail with this Android Device Security Management Determine Various Mobile Devices Existing At Workplace. Use it as a tool for discussion and navigation on Activate Devices, Technology, Consumerization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Incident Response Playbook Best Work From Home Data Security Practices
Incident Response Playbook Best Work From Home Data Security PracticesPurpose of this slide is to provide information about the best data security practices that can be followed by employees who are working from home. Practices covered are configure WIFI encryption, avoid external devices, system update etc. Increase audience engagement and knowledge by dispensing information using Incident Response Playbook Best Work From Home Data Security Practices. This template helps you present information on six stages. You can also present information on System Update, Avoid Using External Device, Communication using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Incident Response Playbook Checklist For Work From Home Data Security
Incident Response Playbook Checklist For Work From Home Data SecurityIncrease audience engagement and knowledge by dispensing information using Incident Response Playbook Checklist For Work From Home Data Security. This template helps you present information on one stages. You can also present information on Training, Policies, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
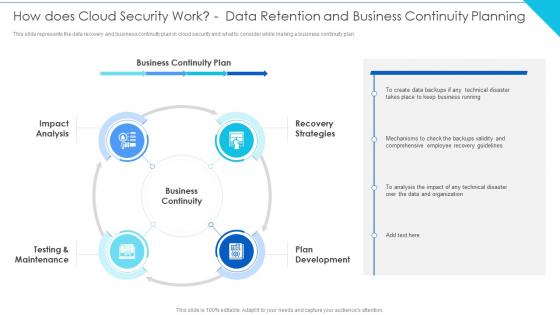 Cloud Information Security How Does Cloud Security Work Data Planning
Cloud Information Security How Does Cloud Security Work Data PlanningThis slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan.Increase audience engagement and knowledge by dispensing information using Cloud Information Security How Does Cloud Security Work Data Planning This template helps you present information on five stages. You can also present information on Implement Information, Authentication Process, Data Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does Cloud Security Work Cloud Information Security
How Does Cloud Security Work Cloud Information SecurityThis slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud.Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Cloud Information Security This template helps you present information on five stages. You can also present information on Information Security, Wireless Security, Endpoint Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does Cloud Security Work Data Security Cloud Information Security
How Does Cloud Security Work Data Security Cloud Information SecurityThis slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security.Introducing How Does Cloud Security Work Data Security Cloud Information Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Accessibility, Knowledge, Organized Documented using this template. Grab it now to reap its full benefits.
-
 How Does Cloud Security Work Governance Cloud Information Security
How Does Cloud Security Work Governance Cloud Information SecurityThis slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored.Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Governance Cloud Information Security This template helps you present information on four stages. You can also present information on Authentication, Access Management, Verification Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does Cloud Security Work Identity And IAM Cloud Information Security
How Does Cloud Security Work Identity And IAM Cloud Information SecurityThis slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository.Present the topic in a bit more detail with this How Does Cloud Security Work Identity And IAM Cloud Information Security Use it as a tool for discussion and navigation on Requirements, Transparency, Governance This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How Does Cloud Security Work Legal Compliance Cloud Information Security
How Does Cloud Security Work Legal Compliance Cloud Information SecurityThis slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud.Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Legal Compliance Cloud Information Security This template helps you present information on eight stages. You can also present information on Firewalls Ensure, Organization Security, Permitting Limited using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security How Does Cloud Security Work Data Retention And Business
Cloud Computing Security How Does Cloud Security Work Data Retention And BusinessThis slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security How Does Cloud Security Work Data Retention And Business. This template helps you present information on four stages. You can also present information on Impact Analysis, Recovery Strategies, Testing And Maintenance, Plan Development using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security How Does Cloud Security Work Data Security
Cloud Computing Security How Does Cloud Security Work Data SecurityThis slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. Introducing Cloud Computing Security How Does Cloud Security Work Data Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Application Security, Physical Security, Internet Security, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Cloud Computing Security How Does Cloud Security Work Governance
Cloud Computing Security How Does Cloud Security Work GovernanceThis slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored.This slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security How Does Cloud Security Work Governance. This template helps you present information on five stages. You can also present information on Data Governance, Security, Technology, Ownership using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security How Does Cloud Security Work Identity And Access Management
Cloud Computing Security How Does Cloud Security Work Identity And Access ManagementThis slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Introducing Cloud Computing Security How Does Cloud Security Work Identity And Access Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Authorization, Access Management, Central User Repository, using this template. Grab it now to reap its full benefits.
-
 Cloud Computing Security How Does Cloud Security Work Legal Compliance
Cloud Computing Security How Does Cloud Security Work Legal ComplianceThis slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security How Does Cloud Security Work Legal Compliance. This template helps you present information on eight stages. You can also present information on Transparency, Regulations, Governance, Compliance, Policies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Computing Security How Does Cloud Security Work Ppt Introduction
Cloud Computing Security How Does Cloud Security Work Ppt IntroductionThis slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. Introducing Cloud Computing Security How Does Cloud Security Work Ppt Introduction to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Data Security, Access Management, Cloud Security, Business Continuity Planning, using this template. Grab it now to reap its full benefits.
-
 Advantages And Working Of Secure SDLC Software Development Process
Advantages And Working Of Secure SDLC Software Development ProcessThis slide represents the advantages and working of secure software development life cycle, including its various phases, such as concept, planning, design and development, testing, release, sustain, and disposal. Introducing Advantages And Working Of Secure SDLC Software Development Process to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Security Planning, Existing Development, Design And Development, using this template. Grab it now to reap its full benefits.
-
 How Does Cloud Security Work Cloud Data Protection
How Does Cloud Security Work Cloud Data ProtectionThis slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud. Introducing How Does Cloud Security Work Cloud Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Data Security, Access Management, Business Continuity Planning, Cloud Security, using this template. Grab it now to reap its full benefits.
-
 How Does Cloud Security Work Data Retention And Business Cloud Data Protection
How Does Cloud Security Work Data Retention And Business Cloud Data ProtectionThis slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan. Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Data Retention And Business Cloud Data Protection. This template helps you present information on four stages. You can also present information on Impact Analysis, Business Continuity, Plan Development, Recovery Strategies using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 How Does Cloud Security Work Data Security Cloud Data Protection
How Does Cloud Security Work Data Security Cloud Data ProtectionThis slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security. Introducing How Does Cloud Security Work Data Security Cloud Data Protection to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispense information on Wireless Security, Internet Security, Application Security, Network Security, Information Security, using this template. Grab it now to reap its full benefits.
-
 How Does Cloud Security Work Governance Cloud Data Protection
How Does Cloud Security Work Governance Cloud Data ProtectionThis slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored. Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Governance Cloud Data Protection. This template helps you present information on five stages. You can also present information on Knowledge, Quality, Security, Accessibility, Data Governance using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 How Does Cloud Security Work Identity And Access Management Cloud Data Protection
How Does Cloud Security Work Identity And Access Management Cloud Data ProtectionThis slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Introducing How Does Cloud Security Work Identity And Access Management Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Access Management, Authentication, Authorization, Central User Repository, using this template. Grab it now to reap its full benefits.





