Powerpoint Templates and Google slides for Secure Work
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Tokenization Working Process For Data Security Implementing Effective Tokenization
Tokenization Working Process For Data Security Implementing Effective TokenizationThis slide represents the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Deliver an outstanding presentation on the topic using this Tokenization Working Process For Data Security Implementing Effective Tokenization. Dispense information and present a thorough explanation of Tokenization Working Process, Data Security, Mobile Payment Application, Generating Tokens using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Platforms Working For Smart Contracts Security Ppt Summary Template
Platforms Working For Smart Contracts Security Ppt Summary TemplateThe purpose of this slide is to explain the platforms working to provide smart contracts security, these platforms include Open Zeppelin, Why3, Oyente, etc. Introducing Platforms Working For Smart Contracts Security Ppt Summary Template to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Operating Decentralized Applications, Deductive Program Verification, Smart Contracts Security, using this template. Grab it now to reap its full benefits.
-
 Strategic Roadmap To Implement DevSecOps Pipeline Security Working Of DevSecOps Model
Strategic Roadmap To Implement DevSecOps Pipeline Security Working Of DevSecOps ModelThis slide discusses the pipeline security of DevSecOps. The purpose of this slide is to explain pipeline security and its importance in DevSecOps, which includes maximizing security personnel efficiency, automating non-intellectual tasks, improving the tracking of task statuses, and so on. Deliver an outstanding presentation on the topic using this Strategic Roadmap To Implement DevSecOps Pipeline Security Working Of DevSecOps Model. Dispense information and present a thorough explanation of Boost Workflow Efficiency, Performance Metrics, Pipeline Security Working using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Email Authentication And Security Working Process
Email Authentication And Security Working ProcessThis slide highlights the email authentication and security working process which includes sender establishes authentication rules, and sender configuration. Presenting our set of slides with Email Authentication And Security Working Process. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Email Infrastructure, Authentication Rules, Authentication Results.
-
 Email Security Gateway Workflow Process
Email Security Gateway Workflow ProcessThis slide outlines the workflow process of email gateway which involves incoming emails, validate sender, validate content, advanced threat detection, etc. Presenting our well structured Email Security Gateway Workflow Process. The topics discussed in this slide are Email Gateway, Protection Against, Validate Sender. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Application Security Implementation Plan Working Process Of Effective Logging Implementation
Application Security Implementation Plan Working Process Of Effective Logging ImplementationThis slide outlines the steps for deploying effective logging which include assess requirements, select logging tool, defining logging standards, etc. Introducing Application Security Implementation Plan Working Process Of Effective Logging Implementation to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Ensure Security, Centralize Log Management, Define Logging Standards, Select Logging Tools, using this template. Grab it now to reap its full benefits.
-
 How Does IP Security Work Effectively
How Does IP Security Work EffectivelyThis slide showcases ways in which IP security works. The main purpose of this template is to showcase the formation of security in data. This includes host recognition, negotiation, IPsec Circuit, etc. Introducing our premium set of slides with name How Does IP Security Work Effectively. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Host Recognition, Negotiation, Security Work Effectively. So download instantly and tailor it with your information.
-
 Tokenization For Improved Data Security Tokenization Working Process For Data Security
Tokenization For Improved Data Security Tokenization Working Process For Data SecurityThis slide represents the workflow of tokenization. The purpose of this slide is to highlight the process of tokenization which includes downloading a mobile payment application, generating tokens, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Tokenization Working Process For Data Security. Dispense information and present a thorough explanation of Tokenization Working Process, Data Security, Mobile Payment Application, Generating Tokens using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Working Of Security Tokenization In Financial Assets
Tokenization For Improved Data Security Working Of Security Tokenization In Financial AssetsThis slide highlights the phases of security tokenization. The purpose of this slide is to showcase the working of security tokenization along with its phases which include creation, dividend distribution, etc. Introducing Tokenization For Improved Data Security Working Of Security Tokenization In Financial Assets to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Working Of Security Tokenization, Financial Assets, Dividend Distribution, Security Token Classification, using this template. Grab it now to reap its full benefits.
-
 Endpoint Cyber Security Automated Workflow
Endpoint Cyber Security Automated WorkflowThis slide lays out framework for automated workflow for endpoint cyber security process. The purpose of this slide is to secure organization network and assets against cyber threats. It covers processes such as collecting data, selecting security tools and deploying tools. Introducing our premium set of slides with Endpoint Cyber Security Automated Workflow Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Collect Data, Select Security Tools, Deploy Tools So download instantly and tailor it with your information.
-
 Cyber Security Lateral Movement Work Infrastructure
Cyber Security Lateral Movement Work InfrastructureThe slide underscores critical aspects like attackers, initial compromise, lateral movement, and ransomware, providing insights into cybersecurity infrastructure vulnerabilities. It aids in understanding and fortifying defenses against lateral movement within the digital landscape. Introducing our Cyber Security Lateral Movement Work Infrastructure set of slides. The topics discussed in these slides are Infrastructure, Lateral Movement, Ransomware Deployment. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Hids Cyber Security Architecture And Working
Hids Cyber Security Architecture And WorkingThis slide represents HIDS cyber security architecture and working which operates in encrypted network environment and prevents network based attacks. It includes ley components such as touter, firewall, IDS, etc Presenting our well structured Hids Cyber Security Architecture And Working. The topics discussed in this slide are Architecture, Administrator, Computers. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Securing Food Safety In Online Working Of Online Food Delivery Application
Securing Food Safety In Online Working Of Online Food Delivery ApplicationThis slide covers how online food delivery application works involves steps such as customer sign in, payment options, real time notifications, route optimization and timely delivery. Introducing Securing Food Safety In Online Working Of Online Food Delivery Application to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Customer Track Order Preparation, Server Contact, using this template. Grab it now to reap its full benefits.
-
 Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SS
Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding training program to ensure information security at workplace by considering focus areas such as data security and encryption, network security, incident response, etc.Deliver an outstanding presentation on the topic using this Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SS. Dispense information and present a thorough explanation of Duration, Delivery Method, Assessment, Cost, Modules using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IAM Authentication And Authorization Workflow Process Securing Systems With Identity
IAM Authentication And Authorization Workflow Process Securing Systems With IdentityThis slide showcases the workflow of IAM authentication and authorization. The purpose of this slide is to explain the process, starting with user authentication and authorization, that often uses a single sign-on solution that incorporates multi-factor authentication and assigns access rights to resources. Increase audience engagement and knowledge by dispensing information using IAM Authentication And Authorization Workflow Process Securing Systems With Identity This template helps you present information on Two stages. You can also present information on Authentication, Authorization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Identity And Access Management Process In Workplace Securing Systems With Identity
Identity And Access Management Process In Workplace Securing Systems With IdentityThis slide discusses the Identity and Access Management process in the workplace. The purpose of this slide is to highlight the various usages of IAM in the workplace these include increasing the number of applications, managing identity data, and complex access scenarios. Increase audience engagement and knowledge by dispensing information using Identity And Access Management Process In Workplace Securing Systems With Identity This template helps you present information on Three stages. You can also present information on Increasing Number Of Applications, Managing Identity Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Identity And Access Management Working Functions Securing Systems With Identity
Identity And Access Management Working Functions Securing Systems With IdentityThis slide discusses the working process of Identity and Access Management . The purpose of this slide is to explain the workflow of the IAM this includes identity management that validates login attempts and access management that manages the entitys access. Introducing Identity And Access Management Working Functions Securing Systems With Identity to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Identity Management, Access Management using this template. Grab it now to reap its full benefits.
-
 Working Process Of Security Operations Center
Working Process Of Security Operations CenterThe below slide highlights the various steps involved in the working of security operations center that helps to safeguard sensitive data from cyber attacks. The major steps are asset discovery, behavioral monitoring, etc. Presenting our set of slides with name Working Process Of Security Operations Center. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Compliance Management, Incident Response, Alert Ranking.
-
 NIDS Workflow To Establish Organizational Cyber Security
NIDS Workflow To Establish Organizational Cyber SecurityThis slide represents process to develop business cyber security utilizing NIDS. It aims to maintain proactive stance against potential cyber threats and ensure security posture. Introducing our premium set of slides with NIDS Workflow To Establish Organizational Cyber Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Incident Response And Mitigation, Alert Creation And Notification, Traffic Analysis And Capture. So download instantly and tailor it with your information.
-
 Working Process Of Phishing Attacks In Devices Mobile Security
Working Process Of Phishing Attacks In Devices Mobile SecurityThis slide depicts about the working of phishing attacks in mobile devices which include attacker, victim, phishing website and legitimate website. Deliver an outstanding presentation on the topic using this Working Process Of Phishing Attacks In Devices Mobile Security Dispense information and present a thorough explanation of Sends Email To Victim, Legitimate Website using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Construction Risk Management Software For Security Of Workers Revolutionizing Construction With Robots
Construction Risk Management Software For Security Of Workers Revolutionizing Construction With RobotsThis slide showcases various softwares to easily conduct inspections and proactively identify risks. It includes of tools such as Raken, Zepth, etc.Present the topic in a bit more detail with this Construction Risk Management Software For Security Of Workers Revolutionizing Construction With Robots. Use it as a tool for discussion and navigation on Key Features, Pros, Cons, Free Trial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organizational Workplace Security Maintenance Checklist
Organizational Workplace Security Maintenance ChecklistThe below slide provides a checklist of activities for development of enhanced workplace security. The different activities involved are identification of risks, policy development, conducting training sessions, etc. Presenting our set of slides with Organizational Workplace Security Maintenance Checklist. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Development Emergency Response Plan, Conduct Employee, Security Awareness Training Sessions.
-
 Web Security Solution Working Process Of Web Application Firewall WAF
Web Security Solution Working Process Of Web Application Firewall WAFThie slide represents the process of WAF in web security with its various components such as origin server, web application firewalls, etc. Present the topic in a bit more detail with this Web Security Solution Working Process Of Web Application Firewall WAF. Use it as a tool for discussion and navigation on Working Process, Web Application Firewall Waf. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Authorization Working Process For Application Security
Authorization Working Process For Application SecurityThis slide discusses the workflow of authorization for application security which includes authorized user, resource owner, etc. Introducing our Authorization Working Process For Application Security set of slides. The topics discussed in these slides are Resource Owner, Authorized UserThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Create Secure Workplace For Employee Well Being And Safety Practicing Inclusive Leadership DTE SS
Create Secure Workplace For Employee Well Being And Safety Practicing Inclusive Leadership DTE SSThis slide covers major strategies for establishing a secure workplace, such as diverse safety committee involvement, address unconscious bias, and flexible work arrangements. Introducing Create Secure Workplace For Employee Well Being And Safety Practicing Inclusive Leadership DTE SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Deloitte, Google, Facebook using this template. Grab it now to reap its full benefits.
-
 Data Encryption Working Model For Security
Data Encryption Working Model For SecurityThe purpose of this slide is to elucidate how data encryption working model for security offers insight into safeguarding sensitive data through encryption mechanisms. It helps thwart unauthorized access or breaches. Introducing our Data Encryption Working Model For Security set of slides. The topics discussed in these slides are Sender, Plaintext, Ciphertext. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Tracking Mobile Device Activities At Workplace Android Device Security Management
Tracking Mobile Device Activities At Workplace Android Device Security ManagementThis slide covers information regarding the tracking mobile device activities at workplace with details about device security, ownership, last seen status. Present the topic in a bit more detail with this Tracking Mobile Device Activities At Workplace Android Device Security Management. Use it as a tool for discussion and navigation on Compromised, Last Seen Overview, Ownership. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Tracking Mobile Device Activities At Workplace Enterprise Mobile Security For On Device
Tracking Mobile Device Activities At Workplace Enterprise Mobile Security For On DeviceThis slide covers information regarding the tracking mobile device activities at workplace with details about device security, ownership, last seen status. Deliver an outstanding presentation on the topic using this Tracking Mobile Device Activities At Workplace Enterprise Mobile Security For On Device. Dispense information and present a thorough explanation of Compromised, Undefined, Encrypted using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tracking Mobile Device Activities At Workplace Unified Endpoint Security
Tracking Mobile Device Activities At Workplace Unified Endpoint SecurityThis slide covers information regarding the tracking mobile device activities at workplace with details about device security, ownership, last seen status. Present the topic in a bit more detail with this Tracking Mobile Device Activities At Workplace Unified Endpoint Security. Use it as a tool for discussion and navigation on Compromised, Ownership, Passcode. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Statistics associated to workplace threats corporate security management
Statistics associated to workplace threats corporate security managementThis slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Present the topic in a bit more detail with this Statistics Associated To Workplace Threats Corporate Security Management. Use it as a tool for discussion and navigation on Cyber Attacks Costs, Organizations, Data Records. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Dashboard Highlighting Resolved Events And Workload Enabling Automation In Cyber Security
Security Automation Dashboard Highlighting Resolved Events And Workload Enabling Automation In Cyber SecurityThis slide highlights the security automation dashboard which includes resolved events, mean dwell time, time and dollar saved, workload, events by status and top actions. Deliver an outstanding presentation on the topic using this Security Automation Dashboard Highlighting Resolved Events And Workload Enabling Automation In Cyber Security. Dispense information and present a thorough explanation of Dashboard, Security Automation, Workload using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Architecture And Security Review Model For Workload Placement For On And Off Premises
Cloud Architecture And Security Review Model For Workload Placement For On And Off PremisesThis slide covers the workload placement such as Workloads shown on the left are marked as off premises which are more suitable for a public cloud where as those on the right are for on premises appropriate for a private cloud and those in the middle are for a hybrid cloud. Deliver an outstanding presentation on the topic using this Cloud Architecture And Security Review Model For Workload Placement For On And Off Premises. Dispense information and present a thorough explanation of Model For Workload, Placement, On And Off Premises using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing Mobile Device Solutions For Workforce Ensuring Checklist For Mobile Security Deployment
Managing Mobile Device Solutions For Workforce Ensuring Checklist For Mobile Security DeploymentThis slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Present the topic in a bit more detail with this Managing Mobile Device Solutions For Workforce Ensuring Checklist For Mobile Security Deployment. Use it as a tool for discussion and navigation on Device Security, Protection Against, Malicious Codes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Workplace Safety Dashboard Highlighting Injury Severity Best Practices For Workplace Security
Workplace Safety Dashboard Highlighting Injury Severity Best Practices For Workplace SecurityThis slide highlights the dashboard which showcase the critical incidents, incident cost, injury consequence, type of incident and severity level of the injury.Deliver an outstanding presentation on the topic using this Workplace Safety Dashboard Highlighting Injury Severity Best Practices For Workplace Security. Dispense information and present a thorough explanation of Workplace Safety, Dashboard Highlighting, Injury Severity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Workplace Safety Dashboard To Monitor Incidents Best Practices For Workplace Security
Workplace Safety Dashboard To Monitor Incidents Best Practices For Workplace SecurityThis slide highlights the workplace safety dashboard which showcase incidents per employee, worksite incident total, incidents by total and top injuries by body part.Present the topic in a bit more detail with this Workplace Safety Dashboard To Monitor Incidents Best Practices For Workplace Security. Use it as a tool for discussion and navigation on Incidents Reported, Incidents Employee, Total Incident. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Occupation Of Fatal And Injured Employees Best Practices For Workplace Security
Occupation Of Fatal And Injured Employees Best Practices For Workplace SecurityThis slide highlights the occupation of fatal and injured employees on the organization which showcase machine operator, care worker, maintenance worker, plant operatives and emergency service worker.Deliver an outstanding presentation on the topic using this Occupation Of Fatal And Injured Employees Best Practices For Workplace Security. Dispense information and present a thorough explanation of Implementing Safety, Secure Organization, Instant Assistance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 What is electronic information security and how does it work
What is electronic information security and how does it workThis slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Introducing What Is Electronic Information Security And How Does IT Work to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Caused Natural Disasters, Collective Methods, Techniques And Procedures, Protect Data, using this template. Grab it now to reap its full benefits.
-
 Cyber threat management workplace addressing asset security categorization
Cyber threat management workplace addressing asset security categorizationThis slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an outstanding presentation on the topic using this Cyber Threat Management Workplace Addressing Asset Security Categorization. Dispense information and present a thorough explanation of Position, Ownership, Location, Security Categorization, Confidentiality using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber threat management workplace selecting secured threat management
Cyber threat management workplace selecting secured threat managementThis slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an outstanding presentation on the topic using this Cyber Threat Management Workplace Selecting Secured Threat Management. Dispense information and present a thorough explanation of Centralized Platform, Security Incident Forms, Access Rights, API Integration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security information and event management how siem works
Security information and event management how siem worksDeliver an outstanding presentation on the topic using this Security Information And Event Management How SIEM Works. Dispense information and present a thorough explanation of Operating Systems, Network Device, Security Device using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing advanced analytics system at workplace contingency plan for threat handling security
Implementing advanced analytics system at workplace contingency plan for threat handling securityThis slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Deliver an outstanding presentation on the topic using this Implementing Advanced Analytics System At Workplace Contingency Plan For Threat Handling Security. Dispense information and present a thorough explanation of Contingency Plan For Threat Handling In Security Centre using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing advanced analytics system at workplace determine role of security centre in firm
Implementing advanced analytics system at workplace determine role of security centre in firmThis slide covers information regarding the role of security center in in order to protect sensitive data and how firm behave before, after and towards security centre implementation. Present the topic in a bit more detail with this Implementing Advanced Analytics System At Workplace Determine Role Of Security Centre In Firm. Use it as a tool for discussion and navigation on Determine Role Of Security Centre In Firm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing advanced analytics system at workplace enabling data security risk management action plan
Implementing advanced analytics system at workplace enabling data security risk management action planThe data security risk management action plan will help in keeping the track of potential risks that are existing and what are their level, what are the resources required to handle them. Deliver an outstanding presentation on the topic using this Implementing Advanced Analytics System At Workplace Enabling Data Security Risk Management Action Plan. Dispense information and present a thorough explanation of Management, Resources, Enabling using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
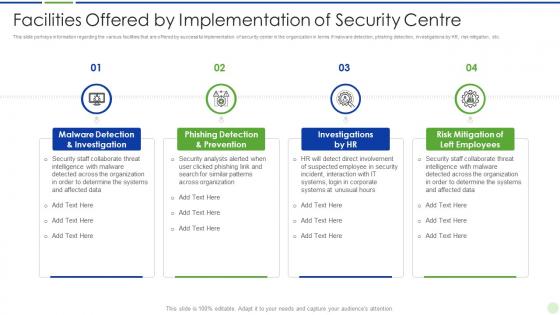 Implementing advanced analytics system at workplace facilities offered by implementation of security
Implementing advanced analytics system at workplace facilities offered by implementation of securityThis slide portrays information regarding the various facilities that are offered by successful implementation of security center in the organization in terms if malware detection, phishing detection, investigations by HR, risk mitigation, etc. Deliver an outstanding presentation on the topic using this Implementing Advanced Analytics System At Workplace Facilities Offered By Implementation Of Security. Dispense information and present a thorough explanation of Implementation, Prevention, Investigation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implementing advanced analytics system at workplace overview established security centre
Implementing advanced analytics system at workplace overview established security centreThis slide provides information regarding the overview of security center associated with firms business units, management, steering committee, external and internal system. Present the topic in a bit more detail with this Implementing Advanced Analytics System At Workplace Overview Established Security Centre. Use it as a tool for discussion and navigation on Business, Management, Steering. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing advanced analytics system at workplace timeframe for incident management in security centre
Implementing advanced analytics system at workplace timeframe for incident management in security centreThis slide provides information regarding entire duration of incident handling process which occur in various phases. Present the topic in a bit more detail with this Implementing Advanced Analytics System At Workplace Timeframe For Incident Management In Security Centre. Use it as a tool for discussion and navigation on Timeframe, Management, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
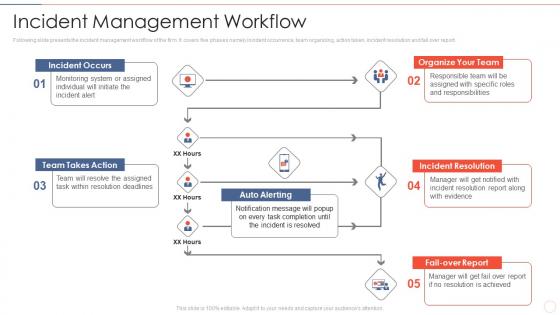 Incident management workflow effective information security risk management process
Incident management workflow effective information security risk management processFollowing slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report.Introducing Incident Management Workflow Effective Information Security Risk Management Process to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Organize Your Team, Incident Resolution, Team Takes Action, using this template. Grab it now to reap its full benefits.
-
 Introducing process workflow effective information security risk management process
Introducing process workflow effective information security risk management processFollowing slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results Deliver an outstanding presentation on the topic using this Introducing Process Workflow Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Threat Categorization, System Characterization, Assigned Remediation Measures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 System categorization worksheet effective information security risk management process
System categorization worksheet effective information security risk management processThis slide illustrates system categorization worksheet. It includes information about security system such as system name, its version, system location and other general information.Present the topic in a bit more detail with this System Categorization Worksheet Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on System Accessibility, Accessible Within Organization Boundary, Valuable Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
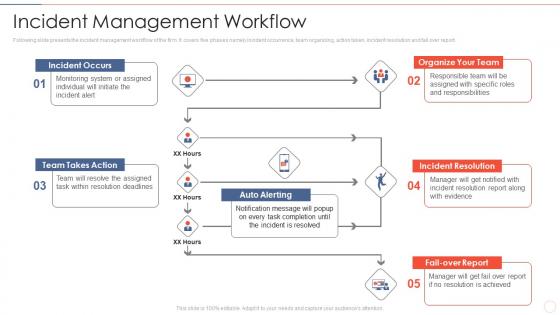 Effective information security incident management workflow
Effective information security incident management workflowFollowing slide presents the incident management workflow of the firm. It covers five phases namely incident occurrence, team organizing, action taken, incident resolution and fail over report. Present the topic in a bit more detail with this Effective Information Security Incident Management Workflow. Use it as a tool for discussion and navigation on Incident Occurs, Team Takes Action, Organize Team, Auto Alerting, Incident Resolution, Fail Over Report. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective information security information security decision framework prism workflow
Effective information security information security decision framework prism workflowDeliver an outstanding presentation on the topic using this Effective Information Security Information Security Decision Framework Prism Workflow. Dispense information and present a thorough explanation of Key Risk Areas Vectors, Risk Factors, Prioritization Weighting using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Effective information security information security risk assessment worksheet
Effective information security information security risk assessment worksheetThis slide illustrates information security risk assessment worksheet. Risk covered are monetary loss, reputation loss and loss of customer confidence. Present the topic in a bit more detail with this Effective Information Security Information Security Risk Assessment Worksheet. Use it as a tool for discussion and navigation on Facilities And Equipment, Software Application, At Personnel Level, Risk. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Statistics associated to workplace managing critical threat vulnerabilities and security threats
Statistics associated to workplace managing critical threat vulnerabilities and security threatsThis slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Increase audience engagement and knowledge by dispensing information using Statistics Associated To Workplace Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on five stages. You can also present information on Cyber Attacks Cost, Organizations Face, Data Records using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various types of workplace violence managing critical threat vulnerabilities and security threats
Various types of workplace violence managing critical threat vulnerabilities and security threatsThis slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Workplace Violence Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on six stages. You can also present information on Threatening Behavior Stalking, Physical Assault, Harassment And Intimidation, Property Damage using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Workplace employee assistance managing critical threat vulnerabilities and security threats
Workplace employee assistance managing critical threat vulnerabilities and security threatsThe employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Introducing Workplace Employee Assistance Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Clinical Services, Online Resources, Offline Resources, Employer Services, using this template. Grab it now to reap its full benefits.
-
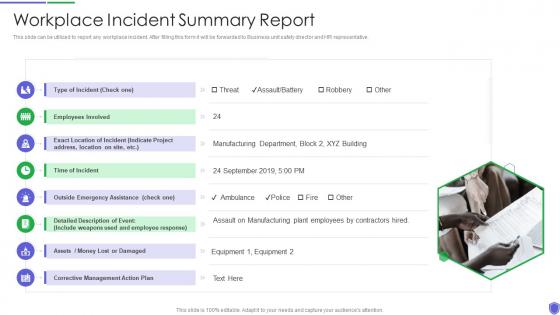 Workplace incident summary managing critical threat vulnerabilities and security threats
Workplace incident summary managing critical threat vulnerabilities and security threatsThis slide can be utilized to report any workplace incident. After filling this form it will be forwarded to Business unit safety director and HR representative. Increase audience engagement and knowledge by dispensing information using Workplace Incident Summary Managing Critical Threat Vulnerabilities And Security Threats. This template helps you present information on one stages. You can also present information on Employees, Corrective Management, Time Of Incident using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Budget for effective threat management at workplace corporate security management
Budget for effective threat management at workplace corporate security managementFirm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Present the topic in a bit more detail with this Budget For Effective Threat Management At Workplace Corporate Security Management. Use it as a tool for discussion and navigation on Incident Management, Risk Management, Client Onboarding Process, Information Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Roles and responsibilities to ensure work environment with corporate security management
Roles and responsibilities to ensure work environment with corporate security managementThis slide provides details regarding roles and responsibilities assigned to ensure minimum violence work environment. Increase audience engagement and knowledge by dispensing information using Roles And Responsibilities To Ensure Work Environment With Corporate Security Management. This template helps you present information on four stages. You can also present information on Employee Responsibilities, Manager Responsibilities, Unit Responsibilities, Human Resources Responsibilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various types of workplace violence and threats corporate security management
Various types of workplace violence and threats corporate security managementThis slide provides details regarding various types of workplace violence threats created by people in terms of stalking, physical assault, harassment or intimidation, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Workplace Violence And Threats Corporate Security Management. This template helps you present information on six stages. You can also present information on Threatening Behavior, Physical Assault, Property Damage, Harassment And Intimidation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Workplace employee assistance program corporate security management
Workplace employee assistance program corporate security managementThe employee assistance program will help firm in enhancing their well being at workplace and enable them to handle critical situations. This program will render services like clinical services, work and life services and employer services, etc. Introducing Workplace Employee Assistance Program Corporate Security Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Clinical Services, Work And Life Services, Employer Services, using this template. Grab it now to reap its full benefits.





