Powerpoint Templates and Google slides for Secure Work
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Workplace Safety And Security Procedures Powerpoint Presentation Slides
Workplace Safety And Security Procedures Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Workplace Safety And Security Procedures Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fifty nine slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Best Practices For Workplace Security Powerpoint Presentation Slides
Best Practices For Workplace Security Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Best Practices For Workplace Security Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fifty nine slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Cyber Security Working From Home Powerpoint Presentation And Google Slides ICP
Cyber Security Working From Home Powerpoint Presentation And Google Slides ICPElevate your presentation to visual excellence using our adaptable Icon PowerPoint template, accessible in editable PPTx and customizable PNG formats. With this deck, enjoy complete editability to finely tune it for effective message delivery. You will also retain full image ownership, granting you the flexibility to utilize them to your advantage, all within a user-friendly PowerPoint environment.
-
 Tips To Securely Work From Home Training Ppt
Tips To Securely Work From Home Training PptPresenting Tips to Securely Work From Home. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Understanding The Working Of Network Security Training Ppt
Understanding The Working Of Network Security Training PptPresenting Understanding the Working of Network Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Workload Security As A Type Of Network Security Training Ppt
Workload Security As A Type Of Network Security Training PptPresenting Workload Security as a Type of Network Security. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Overview Of Working Of Endpoint Security Training Ppt
Overview Of Working Of Endpoint Security Training PptPresenting Overview of Working of Endpoint Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Seven petal secure authentication cloud communications process workflow
Seven petal secure authentication cloud communications process workflowIntroduce your topic and host expert discussion sessions with this Seven Petal Secure Authentication Cloud Communications Process Workflow. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the seventeen slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Overview Of Working Of Security Tokens Training Ppt
Overview Of Working Of Security Tokens Training PptPresenting Overview of Working of Security Tokens. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Security Guard Security Corporate Strengthen Workplace Inspection Services
Security Guard Security Corporate Strengthen Workplace Inspection ServicesIntroduce your topic and host expert discussion sessions with this Security Guard Security Corporate Strengthen Workplace Inspection Services. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the twelve slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Working Of Zero Trust Network Access Model Zero Trust Security Model
Working Of Zero Trust Network Access Model Zero Trust Security ModelThis slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Deliver an outstanding presentation on the topic using this Working Of Zero Trust Network Access Model Zero Trust Security Model. Dispense information and present a thorough explanation of Demonstrate, Architectures, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Components Of Secure Web Gateway Architecture Network Security Using Secure Web Gateway
Working Components Of Secure Web Gateway Architecture Network Security Using Secure Web GatewayThis slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc. Increase audience engagement and knowledge by dispensing information using Working Components Of Secure Web Gateway Architecture Network Security Using Secure Web Gateway. This template helps you present information on five stages. You can also present information on Application Control, Website Content Inspection, Gateway Architecture using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Working Process Of Firewall In Networking Domain
Firewall Network Security Working Process Of Firewall In Networking DomainThis slide represents how a firewall system works in a network. The purpose of this slide is to showcase the architecture, working, and different technologies used in a firewall mechanism to protect the network from malicious activities. The technologies include real-time monitoring, IP packet filtering, and so on. Deliver an outstanding presentation on the topic using this Firewall Network Security Working Process Of Firewall In Networking Domain Dispense information and present a thorough explanation of Working, Technologies Used, Firewall Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Safety security policy workplace ppt powerpoint presentation gallery display cpb
Safety security policy workplace ppt powerpoint presentation gallery display cpbPresenting our Safety Security Policy Workplace Ppt Powerpoint Presentation Gallery Display Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Safety Security Policy Workplace This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Data security it what is data security and how does it work
Data security it what is data security and how does it workThis slide defines the meaning of data security and how it helps to prevent data through different methods and techniques. Introducing Data Security IT What Is Data Security And How Does IT Work to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Collective Methods, Protect Data, Computer Systems, Networks, Servers And Mobile Devices, using this template. Grab it now to reap its full benefits.
-
 Computer system security what is computer security and how does it work
Computer system security what is computer security and how does it workThis slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Introducing Computer System Security What Is Computer Security And How Does It Work to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Techniques, Collective, Networks, Computer Systems, using this template. Grab it now to reap its full benefits.
-
 Security Business Analyst Work In Powerpoint And Google Slides Cpb
Security Business Analyst Work In Powerpoint And Google Slides CpbPresenting our Security Business Analyst Work In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Business Analyst Work This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security Workplace Policy Guide For Employees
Security Workplace Policy Guide For EmployeesIntroducing Security Workplace Policy Guide For Employees to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Internet, Programs, Secure, using this template. Grab it now to reap its full benefits.
-
 Firewall As A Service Fwaas Working And Architecture Of Firewall Security Technology
Firewall As A Service Fwaas Working And Architecture Of Firewall Security TechnologyThis slide demonstrates the architecture and working of traditional firewalls. The purpose of this slide is to illustrate the firewall architecture and working. The main components include corporate network, operation network and control system network. Present the topic in a bit more detail with this Firewall As A Service Fwaas Working And Architecture Of Firewall Security Technology. Use it as a tool for discussion and navigation on Operator Workstation, Administrator Workstation, Control Systems, Data Acquisition, Internal Databases And Servers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Of Firewall As A Service Security Technology Ppt Ideas Graphic Images
Working Of Firewall As A Service Security Technology Ppt Ideas Graphic ImagesThis slide illustrates the working of Firewall-as-a-service technology. The purpose of this slide is to outline various actions performed by FWaaS such as Intrusion Prevention Systems, DNS security, etc. Main components include accept, drop and block. Deliver an outstanding presentation on the topic using this Working Of Firewall As A Service Security Technology Ppt Ideas Graphic Images. Dispense information and present a thorough explanation of Advanced Unified Threat Management, Active Directory Integration, Compliance Reporting, Single Pane Of Glass using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security Model
F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security ModelThis slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Increase audience engagement and knowledge by dispensing information using F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security Model. This template helps you present information on six stages. You can also present information on Architecture, Workflow, Resources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Microsegmentation Overview And Working In ZTNA Model Zero Trust Security Model
Microsegmentation Overview And Working In ZTNA Model Zero Trust Security ModelThis slide outlines the overview and working of the micro-segmentation concept of cybersecurity. The purpose of this slide is to showcase how micro-segmentation divides the network components into smaller segments, all the way down to workloads. Deliver an outstanding presentation on the topic using this Microsegmentation Overview And Working In ZTNA Model Zero Trust Security Model. Dispense information and present a thorough explanation of Microsegmentation, Overview, Businesses using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Workflows Of STOs And ICOs Funding Options Security Token Offerings BCT SS
Comparative Workflows Of STOs And ICOs Funding Options Security Token Offerings BCT SSThe following slide showcases how security token offerings STOs varies from initial coin offerings ICO to ensure transparency and liquidity. It includes elements such as money, token, investors, security laws, associated risks, etc. Deliver an outstanding presentation on the topic using this Comparative Workflows Of STOs And ICOs Funding Options Security Token Offerings BCT SS. Dispense information and present a thorough explanation of Platform Built On Blockchain, Comparative Workflows, Funding Options using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Security Workday Database Architecture In Powerpoint And Google Slides Cpb
Data Security Workday Database Architecture In Powerpoint And Google Slides CpbPresenting Data Security Workday Database Architecture In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase Four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Data Security Workday, Database Architecture. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Secure Web Gateway Architecture And Working Network Security Using Secure Web Gateway
Secure Web Gateway Architecture And Working Network Security Using Secure Web GatewayThis slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. Present the topic in a bit more detail with this Secure Web Gateway Architecture And Working Network Security Using Secure Web Gateway. Use it as a tool for discussion and navigation on Architecture, Approaches, Enterprises. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Web Gateway For Remote And On Site Workers Network Security Using Secure Web Gateway
Secure Web Gateway For Remote And On Site Workers Network Security Using Secure Web GatewayThis slide represents the on-premise and cloud based SWG technology solution for organizations. The purpose of this slide is to provide visualization of Secure Web Gateway structure enabling encrypted web surfing for both on-site and remote employees. Present the topic in a bit more detail with this Secure Web Gateway For Remote And On Site Workers Network Security Using Secure Web Gateway. Use it as a tool for discussion and navigation on Authenticate, Information, Sources. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Search Engine Marketing Strategy To Enhance How An Ad Auction Works To Secure Top Spots MKT SS V
Search Engine Marketing Strategy To Enhance How An Ad Auction Works To Secure Top Spots MKT SS VThis slide showcases the working of an Ad auction. It includes steps such as google Das algorithm, bid, ad quality, ad rank and competitor analysis. It includes elements such as keywords to bid on and budget specification. Introducing Search Engine Marketing Strategy To Enhance How An Ad Auction Works To Secure Top Spots MKT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Algorithm, Violation Are Ignored, Extensions, using this template. Grab it now to reap its full benefits.
-
 Social Security Taxable Benefits Worksheet In Powerpoint And Google Slides Cpb
Social Security Taxable Benefits Worksheet In Powerpoint And Google Slides CpbPresenting Social Security Taxable Benefits Worksheet In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase Three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Social Security Taxable, Benefits Worksheet. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cloud Access Security Broker CASB V2 Forward Proxy Deployment Overview And Working
Cloud Access Security Broker CASB V2 Forward Proxy Deployment Overview And WorkingThis slide describes the overview of the forward proxy deployment mode of the CASB model, including its working. The purpose of this slide is to showcase the working of proxy-based CASB deployment and the main components include user or clients, forward proxy, internet and origin server. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Forward Proxy Deployment Overview And Working. Use it as a tool for discussion and navigation on Deployment Overview And Working, Web Servers They Visit, Forward Proxy Method Is A Configuration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics Example
Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics ExampleThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Working Process Ppt Ideas Graphics Example. This template helps you present information on three stages. You can also present information on Cloud Access Security, Broker Working Process, Classification And Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Security Website Not Working In Powerpoint And Google Slides Cpb
Social Security Website Not Working In Powerpoint And Google Slides CpbPresenting Social Security Website Not Working In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Social Security Website Not Working. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Architecture And Working Of SD Wide Area Network Cloud Security Model
Architecture And Working Of SD Wide Area Network Cloud Security ModelThis slide represents the architecture and working of a software defined wide area network. The purpose of this slide is to demonstrate the different types of SD WAN architectures, such as on premise, cloud enabled and cloud enabled with backbone. It also caters to the basic operation of SD WAN. Increase audience engagement and knowledge by dispensing information using Architecture And Working Of SD Wide Area Network Cloud Security Model. This template helps you present information on three stages. You can also present information on Working, Architecture, Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Working Process Cloud Security Model
Cloud Access Security Broker Working Process Cloud Security ModelThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process Cloud Security Model. This template helps you present information on three stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall As A Service FWaaS Working And Security Features Cloud Security Model
Firewall As A Service FWaaS Working And Security Features Cloud Security ModelThis slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, and IP mapping. Introducing Firewall As A Service FWaaS Working And Security Features Cloud Security Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Packet, Internet, Network, using this template. Grab it now to reap its full benefits.
-
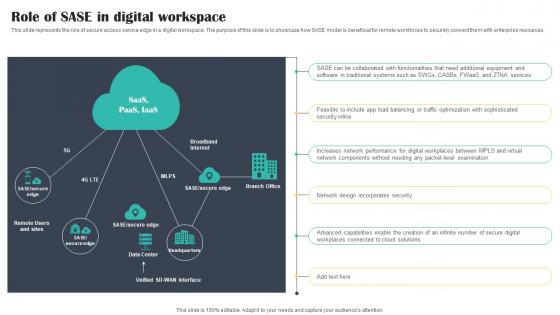 Role Of SASE In Digital Workspace Cloud Security Model
Role Of SASE In Digital Workspace Cloud Security ModelThis slide represents the role of secure access service edge in a digital workspace. The purpose of this slide is to showcase how SASE model is beneficial for remote workforces to securely connect them with enterprise resources. Introducing Role Of SASE In Digital Workspace Cloud Security Model to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Software, Optimization, Examination, using this template. Grab it now to reap its full benefits.
-
 Secure Web Gateways SWG Setup And Working Cloud Security Model
Secure Web Gateways SWG Setup And Working Cloud Security ModelThis slide depicts the methods to setup the secure web gateways and their working. The purpose of this slide is to demonstrate the various ways in which organizations can install the SWGs. It also caters to the working and functions performed by SWGs to protect data and safe browsing on the internet. Increase audience engagement and knowledge by dispensing information using Secure Web Gateways SWG Setup And Working Cloud Security Model. This template helps you present information on eight stages. You can also present information on Implemented, Classifications, Programs using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Working Of Secure Access Service Edge Cloud Security Model
Working Of Secure Access Service Edge Cloud Security ModelThis slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. Present the topic in a bit more detail with this Working Of Secure Access Service Edge Cloud Security Model. Use it as a tool for discussion and navigation on Network, Security, Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Of Zero Trust Network Access Cloud Security Model
Working Of Zero Trust Network Access Cloud Security ModelThis slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Deliver an outstanding presentation on the topic using this Working Of Zero Trust Network Access Cloud Security Model. Dispense information and present a thorough explanation of Working, Network, Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Workplace Skills For Security Analysts
Cybersecurity Workplace Skills For Security AnalystsThe following slide highlights technical expertise and proficiency levels to demonstrate cybersecurity workplace skills for security analytics. It helps organizations evaluate and develop cybersecurity workforce effectively. Presenting our set of slides with Cybersecurity Workplace Skills For Security Analysts. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cybersecurity, Skills, Security.
-
 Sase Security Architecture And Working Of Sd Wide Area Network
Sase Security Architecture And Working Of Sd Wide Area NetworkThis slide represents the architecture and working of a software-defined wide area network. The purpose of this slide is to demonstrate the different types of SD-WAN architectures, such as on-premise, cloud-enabled and cloud-enabled with backbone. It also caters to the basic operation of SD-WAN. Present the topic in a bit more detail with this Sase Security Architecture And Working Of Sd Wide Area Network. Use it as a tool for discussion and navigation on Architecture, Enterprises, Connections. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Cloud Access Security Broker Working Process
Sase Security Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, an remediation. Deliver an outstanding presentation on the topic using this Sase Security Cloud Access Security Broker Working Process. Dispense information and present a thorough explanation of Remediation, Classification, Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Firewall Fwaas Working And Security Features Ppt Show Graphics Example
Sase Security Firewall Fwaas Working And Security Features Ppt Show Graphics ExampleThis slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, and IP mapping. Present the topic in a bit more detail with this Sase Security Firewall Fwaas Working And Security Features Ppt Show Graphics Example. Use it as a tool for discussion and navigation on Service, Demonstrate, Describes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Role Of Sase In Digital Workspace
Sase Security Role Of Sase In Digital WorkspaceThis slide represents the role of secure access service edge in a digital workspace. The purpose of this slide is to showcase how SASE model is beneficial for remote workforces to securely connect them with enterprise resources. Present the topic in a bit more detail with this Sase Security Role Of Sase In Digital Workspace. Use it as a tool for discussion and navigation on Examination, Performance, Collaborated. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Secure Web Gateways Swg Setup And Working
Sase Security Secure Web Gateways Swg Setup And WorkingThis slide depicts the methods to setup the secure web gateways and their working. The purpose of this slide is to demonstrate the various ways in which organizations can install the SWGs. It also caters to the working and functions performed by SWGs to protect data and safe browsing on the internet. Increase audience engagement and knowledge by dispensing information using Sase Security Secure Web Gateways Swg Setup And Working. This template helps you present information on eight stages. You can also present information on Implemented, Classifications, Businesses using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Security Working Of Secure Access Service Edge
Sase Security Working Of Secure Access Service EdgeThis slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. Present the topic in a bit more detail with this Sase Security Working Of Secure Access Service Edge. Use it as a tool for discussion and navigation on Performance, Scalability, Omnipresent. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Working Of Zero Trust Network Access
Sase Security Working Of Zero Trust Network AccessThis slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Deliver an outstanding presentation on the topic using this Sase Security Working Of Zero Trust Network Access. Dispense information and present a thorough explanation of Resources, Situations, Multiprotocol using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Architecture And Working Of Sd Wide Area Network Secure Access Service Edge Sase
Architecture And Working Of Sd Wide Area Network Secure Access Service Edge SaseThis slide represents the architecture and working of a software-defined wide area network. The purpose of this slide is to demonstrate the different types of SD-WAN architectures, such as on-premise, cloud-enabled and cloud-enabled with backbone. It also caters to the basic operation of SD-WAN. Present the topic in a bit more detail with this Architecture And Working Of Sd Wide Area Network Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Architecture, Enterprises, Connections. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Working Process Secure Access Service Edge Sase
Cloud Access Security Broker Working Process Secure Access Service Edge SaseThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process Secure Access Service Edge Sase. This template helps you present information on three stages. You can also present information on Information, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall As A Service Fwaas Working And Security Features Secure Access Service Edge Sase
Firewall As A Service Fwaas Working And Security Features Secure Access Service Edge SaseThis slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, and IP mapping. Present the topic in a bit more detail with this Firewall As A Service Fwaas Working And Security Features Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Information, Demonstrate, Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Role Of Sase In Digital Workspace Secure Access Service Edge Sase
Role Of Sase In Digital Workspace Secure Access Service Edge SaseThis slide represents the role of secure access service edge in a digital workspace. The purpose of this slide is to showcase how SASE model is beneficial for remote workforces to securely connect them with enterprise resources. Deliver an outstanding presentation on the topic using this Role Of Sase In Digital Workspace Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Performance, Examination, Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Web Gateways Swg Setup And Working Secure Access Service Edge Sase
Secure Web Gateways Swg Setup And Working Secure Access Service Edge SaseThis slide depicts the methods to setup the secure web gateways and their working. The purpose of this slide is to demonstrate the various ways in which organizations can install the SWGs. It also caters to the working and functions performed by SWGs to protect data and safe browsing on the internet. Increase audience engagement and knowledge by dispensing information using Secure Web Gateways Swg Setup And Working Secure Access Service Edge Sase. This template helps you present information on eight stages. You can also present information on Information, Businesses, Determination using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Working Of Secure Access Service Edge Secure Access Service Edge Sase
Working Of Secure Access Service Edge Secure Access Service Edge SaseThis slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. Present the topic in a bit more detail with this Working Of Secure Access Service Edge Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Service, Performance, Dependability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Of Zero Trust Network Access Secure Access Service Edge Sase
Working Of Zero Trust Network Access Secure Access Service Edge SaseThis slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Deliver an outstanding presentation on the topic using this Working Of Zero Trust Network Access Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Verification, Authorization, Applications using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secured Credit Card Work In Powerpoint And Google Slides Cpb
Secured Credit Card Work In Powerpoint And Google Slides CpbPresenting our Secured Credit Card Work In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Secured Credit Card Work. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Secured Credit Cards Work In Powerpoint And Google Slides Cpb
Secured Credit Cards Work In Powerpoint And Google Slides CpbPresenting our Secured Credit Cards Work In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Secured Credit Cards Work This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber Security Analyst Work In Powerpoint And Google Slides Cpb
Cyber Security Analyst Work In Powerpoint And Google Slides CpbPresenting our Cyber Security Analyst Work In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Cyber Security Analyst Work This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Securities Business Work In Powerpoint And Google Slides Cpb
Securities Business Work In Powerpoint And Google Slides CpbPresenting our Securities Business Work In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Securities Business Work This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Firewall As A Service FWaaS Working And Security Features SASE Network Security
Firewall As A Service FWaaS Working And Security Features SASE Network SecurityThis slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, and IP mapping. Present the topic in a bit more detail with this Firewall As A Service FWaaS Working And Security Features SASE Network Security. Use it as a tool for discussion and navigation on Web, Source, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE Network Security Architecture And Working Of SD Wide Area Network
SASE Network Security Architecture And Working Of SD Wide Area NetworkThis slide represents the architecture and working of a software defined wide area network. The purpose of this slide is to demonstrate the different types of SD WAN architectures, such as on premise, cloud enabled and cloud enabled with backbone. It also caters to the basic operation of SD WAN. Present the topic in a bit more detail with this SASE Network Security Architecture And Working Of SD Wide Area Network. Use it as a tool for discussion and navigation on Architecture, Operation, Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE Network Security Cloud Access Security Broker Working Process
SASE Network Security Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using SASE Network Security Cloud Access Security Broker Working Process. This template helps you present information on three stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.




