Powerpoint Templates and Google slides for Secure Work
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 SASE Network Security Role Of SASE In Digital Workspace
SASE Network Security Role Of SASE In Digital WorkspaceThis slide represents the role of secure access service edge in a digital workspace. The purpose of this slide is to showcase how SASE model is beneficial for remote workforces to securely connect them with enterprise resources. Increase audience engagement and knowledge by dispensing information using SASE Network Security Role Of SASE In Digital Workspace. This template helps you present information on six stages. You can also present information on Systems, Security, Components using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE Network Security Secure Web Gateways SWG Setup And Working
SASE Network Security Secure Web Gateways SWG Setup And WorkingThis slide depicts the methods to setup the secure web gateways and their working. The purpose of this slide is to demonstrate the various ways in which organizations can install the SWGs. It also caters to the working and functions performed by SWGs to protect data and safe browsing on the internet. Increase audience engagement and knowledge by dispensing information using SASE Network Security Secure Web Gateways SWG Setup And Working. This template helps you present information on eight stages. You can also present information on Regulations, Incoming, Effective using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SASE Network Security Working Of Zero Trust Network Access
SASE Network Security Working Of Zero Trust Network AccessThis slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Increase audience engagement and knowledge by dispensing information using SASE Network Security Working Of Zero Trust Network Access. This template helps you present information on five stages. You can also present information on Access, Connection, Resources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Working Of Secure Access Service Edge SASE Network Security
Working Of Secure Access Service Edge SASE Network SecurityThis slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. Deliver an outstanding presentation on the topic using this Working Of Secure Access Service Edge SASE Network Security. Dispense information and present a thorough explanation of Security, Network, Challenges using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Management System Workflow
Information Security Management System WorkflowThis slide represents the workflow that helps businesses to implement effective information security management system in organization. This workflow includes major phases , tasks and users responsible for each activity. Introducing our premium set of slides with Information Security Management System Workflow. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Develop ISMS, Document Policy Freme Work, Designate Internal Auditor. So download instantly and tailor it with your information.
-
 Blockchain Cyberattack Identification Workflow Model Hands On Blockchain Security Risk BCT SS V
Blockchain Cyberattack Identification Workflow Model Hands On Blockchain Security Risk BCT SS VThe following slide depicts blockchain attack identification workflow. It includes elements such as recording blockchain fingerprints, determining data breaches, aiming to deliver data to manufacturer, stealing and corrupting data, etc. Present the topic in a bit more detail with this Blockchain Cyberattack Identification Workflow Model Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Blockchain Fingerprints, Data Ownership, Data And Corrupt. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How Does Phishing Attack Works On Blockchain Network Hands On Blockchain Security Risk BCT SS V
How Does Phishing Attack Works On Blockchain Network Hands On Blockchain Security Risk BCT SS VThe following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Present the topic in a bit more detail with this How Does Phishing Attack Works On Blockchain Network Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Attacker, Phishing Email, Internet Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview And Workflow Of Blockchain Cybersecurity Technology Hands On Blockchain Security Risk BCT SS V
Overview And Workflow Of Blockchain Cybersecurity Technology Hands On Blockchain Security Risk BCT SS VThe following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc. Increase audience engagement and knowledge by dispensing information using Overview And Workflow Of Blockchain Cybersecurity Technology Hands On Blockchain Security Risk BCT SS V. This template helps you present information on seven stages. You can also present information on Transaction Requested, Created Transaction, Existing Blockchain using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS V
Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS VThe following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer-to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. Introducing Overview And Workflow Process Of Eclipse Attack Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Enabled Attack, Achieve Control, Incoming And Outgoing, using this template. Grab it now to reap its full benefits.
-
 Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS V
Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS VThe following slide illustrates brief introduction of distributed denial of service DDOS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. Increase audience engagement and knowledge by dispensing information using Overview And Working Process Of Ddos Attack Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Website Hostage, Close The Attack, Inability To Resolve using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of Blockchain 51 Percent Attack With Workflow Hands On Blockchain Security Risk BCT SS V
Overview Of Blockchain 51 Percent Attack With Workflow Hands On Blockchain Security Risk BCT SS VThe following slide showcases brief introduction of 51percentage attack to analyze hashing power of cryptocurrency users. It includes elements such at mining faster rate, malicious user, along with its workflow, etc. Introducing Overview Of Blockchain 51 Percent Attack With Workflow Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain Network, Public Network, using this template. Grab it now to reap its full benefits.
-
 Bring Your Own Device Policy Overview Of Network Security Policy For Workers
Bring Your Own Device Policy Overview Of Network Security Policy For WorkersThis slide describes the network security policy, which ensures systems have the proper hardware, software, and auditing processes. It logs details of activities such as failed log-in attempts, information starts up or shutdown, etc. Introducing Bring Your Own Device Policy Overview Of Network Security Policy For Workers to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Policy, Software And Auditing Processes, Data On Firm Systems, using this template. Grab it now to reap its full benefits.
-
 Secure Your Digital Assets About Structures And Working Of Cryptocurrency Wallets
Secure Your Digital Assets About Structures And Working Of Cryptocurrency WalletsThis slide showcases the structure and workings of crypto wallets in market. This slide outlines the workings of crypto transactions as they are transmitted to a network, and the computer confirms the validity and legitimacy. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets About Structures And Working Of Cryptocurrency Wallets. This template helps you present information on six stages. You can also present information on Crypto Wallets, Crypto Transactions, Transmitted To A Network, Validity And Legitimacy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Your Digital Assets Evolution Of Cryptocurrency Wallets And How They Work
Secure Your Digital Assets Evolution Of Cryptocurrency Wallets And How They WorkThis slide represents the evolution of crypto wallets and how they work in the market. This slide highlights the evolution of crypto wallets from 2009 to 2030. It also includes the various enhancements made in the crypto wallets and projects as well. Increase audience engagement and knowledge by dispensing information using Secure Your Digital Assets Evolution Of Cryptocurrency Wallets And How They Work. This template helps you present information on seven stages. You can also present information on Evolution Of Cryptocurrency Wallets, Crypto Wallets, Market For Cryptocurrency Wallets using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Your Digital Assets Overview And Working Of Two Factor Authentication
Secure Your Digital Assets Overview And Working Of Two Factor AuthenticationThis slide represents an overview and working of 2-factor authentication 2FA. The purpose of this slide is to outline a 2FA overview, how it works, and why we need 2FA. 2FA is a two-step verification for protection and security, it is user-friendly, etc. Deliver an outstanding presentation on the topic using this Secure Your Digital Assets Overview And Working Of Two Factor Authentication. Dispense information and present a thorough explanation of Phishing, Social Engineering, Password Brute Force Attacks, Prevents Attackers, Stolen Credentials using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Working Process Next Generation CASB
Cloud Access Security Broker Working Process Next Generation CASBThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Cloud Access Security Broker Working Process Next Generation CASB to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Working Process, Discovery, Classification, Remediation using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Packet Filtering Firewalls Working And Packet Approval Criteria
Firewall Network Security Packet Filtering Firewalls Working And Packet Approval CriteriaThis slide outlines the working process of packet-filtering firewall type and packet approval criteria. The purpose of this slide is to showcase how packet-filtering firewall works and what parameters it uses to approve or deny a packet to secure the network. Deliver an outstanding presentation on the topic using this Firewall Network Security Packet Filtering Firewalls Working And Packet Approval Criteria Dispense information and present a thorough explanation of Provider, Services, Features And Suitable using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Stateless Firewall Filter Overview And Workflow
Firewall Network Security Stateless Firewall Filter Overview And WorkflowThis slide gives an introduction to stateless firewall filters and the process of filtering network traffic. The purpose of this slide is to showcase the workflow of a stateless firewall filter, including its benefits and limitations. Deliver an outstanding presentation on the topic using this Firewall Network Security Stateless Firewall Filter Overview And Workflow Dispense information and present a thorough explanation of Firewall Network Security Stateless Firewall Filter Overview And Workflow using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security Working Functions Of Cloud Firewall System
Firewall Network Security Working Functions Of Cloud Firewall SystemThis slide talks about the different working functions that help cloud-based firewall systems to protect the user network and devices from malicious activities. The purpose of this slide is to showcase the various tasks of cloud firewalls, including packet filtering, stateful inspection, and proxy service. Introducing Firewall Network Security Working Functions Of Cloud Firewall System to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Stateful Inspection, Proxy Service, Packet Filtering using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Working Lifecycle Of Web Application Firewall
Firewall Network Security Working Lifecycle Of Web Application FirewallThis slide depicts the various steps that the WAF mechanism takes to prevent the applications from harmful traffic. The purpose of this slide is to showcase the working lifecycle of WAF, including session block, IP address block, request block, user block, generating admin alerts, and creating history logs. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Working Lifecycle Of Web Application Firewall This template helps you present information on Seven stages. You can also present information on Log Out The User, Block The User, Generate Admin Alerts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Firewall Network Security Working Of Next Generation Firewall Systems
Firewall Network Security Working Of Next Generation Firewall SystemsThis slide gives architectures of traditional firewalls and Next Generation Firewall systems, including their working. The purpose of this slide is to showcase how Next Generation Firewall works in comparison with conventional firewall systems. Introducing Firewall Network Security Working Of Next Generation Firewall Systems to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Malicious Traffic, Reaches A Network, Security Posture using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Working Procedure Of Software Firewall In Network
Firewall Network Security Working Procedure Of Software Firewall In NetworkThis slide illustrates the working of a software firewall, including its architecture. The purpose of this slide is to showcase the working steps of a software firewall and its architecture. The architecture components include managed firewall as a service, a virtual firewall, and a containerized firewall. Present the topic in a bit more detail with this Firewall Network Security Working Procedure Of Software Firewall In Network Use it as a tool for discussion and navigation on Virtual Machine, Container, Private Cloud This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Working Process Of Proxy Firewall System
Firewall Network Security Working Process Of Proxy Firewall SystemThis slide represents a proxy firewall systems working process and user query flow. The purpose of this slide is to showcase how a proxy firewall works to safeguard network data from unethical activities. The components include a proxy server, proxy client, internet, and real server. Present the topic in a bit more detail with this Firewall Network Security Working Process Of Proxy Firewall System Use it as a tool for discussion and navigation on Working, Technologies Used, Firewall Architecture This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Working Process Of Stateful Inspection Firewalls
Firewall Network Security Working Process Of Stateful Inspection FirewallsThis slide describes how stateful inspection firewalls work. The purpose of this slide is to showcase the working process of a stateful inspection firewall, and the components include active sessions, authorized users, security policy, state recording, and a secure internal network. Present the topic in a bit more detail with this Firewall Network Security Working Process Of Stateful Inspection Firewalls Use it as a tool for discussion and navigation on Filtering Framework, Inspection Process, Valid Response This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Firewall As A Service FWaas Working And Security Features
Firewall Network Security Firewall As A Service FWaas Working And Security FeaturesThis slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, andIP mapping. Present the topic in a bit more detail with this Firewall Network Security Firewall As A Service FWaas Working And Security Features Use it as a tool for discussion and navigation on Firewall Correctly, Audit Software And Logs This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security How Circuit Level Gateway Firewalls Work
Firewall Network Security How Circuit Level Gateway Firewalls WorkThis slide describes the working process of circuit-level gateways through the workflow. The purpose of this slide is to showcase how circuit-level gateway firewalls work with the help of a workflow diagram and explaining step by step procedures. Present the topic in a bit more detail with this Firewall Network Security How Circuit Level Gateway Firewalls Work Use it as a tool for discussion and navigation on Data Traffic, Web Application, Web Server This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security How Does A Hardware Firewall Works
Firewall Network Security How Does A Hardware Firewall WorksThis slide provides an overview of the working of hardware firewalls. The purpose of this slide is to showcase the various steps a hardware firewall takes to protect a network and devices from malicious activities. The components of a network containing hardware firewall include LAN, hardware firewall, and internet. Deliver an outstanding presentation on the topic using this Firewall Network Security How Does A Hardware Firewall Works Dispense information and present a thorough explanation of Security From Insider Attacks, Intrusion Detection, Service Exposure And Port Scanning using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Network Security How Does Web Application Firewall Works
Firewall Network Security How Does Web Application Firewall WorksThis slide depicts the working process of the Web Application Firewall and how it analysis the web traffic and detects harmful traffic. The purpose of this slide is to showcase the working of WAF and how it prevents malicious traffic from reaching web application servers. Present the topic in a bit more detail with this Firewall Network Security How Does Web Application Firewall Works Use it as a tool for discussion and navigation on Importance, Functions This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Cloud Access Security Broker Working Process
SD WAN Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing SD WAN Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Classification And Remediation, Control And Transparency Across Data, Risks In The Cloud, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Firewall As A Service Fwaas Working And Security Features
SD WAN Model Firewall As A Service Fwaas Working And Security FeaturesThis slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, and IP mapping. Introducing SD WAN Model Firewall As A Service Fwaas Working And Security Features to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Packet Filtering, Internet Protocol Mapping, Network Monitoring, Deep Packet Inspection, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Secure Web Gateways Swg Setup And Working
SD WAN Model Secure Web Gateways Swg Setup And WorkingThis slide depicts the methods to setup the secure web gateways and their working. The purpose of this slide is to demonstrate the various ways in which organizations can install the SWGs. It also caters to the working and functions performed by SWGs to protect data and safe browsing on the internet. Introducing SD WAN Model Secure Web Gateways Swg Setup And Working to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Cost Effective Alternative, Secure Web Gateways, Setup And Working, Preventing Restricted Data Sources, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Working Of Secure Access Service Edge
SD WAN Model Working Of Secure Access Service EdgeThis slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. Present the topic in a bit more detail with this SD WAN Model Working Of Secure Access Service Edge. Use it as a tool for discussion and navigation on Precise Amount Of Performance, Dependability, Security, Cost For Each Network Connection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
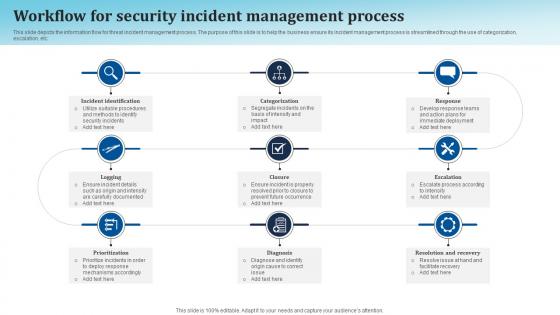 Workflow For Security Incident Management Process
Workflow For Security Incident Management ProcessThis slide depicts the information flow for threat incident management process. The purpose of this slide is to help the business ensure its incident management process is streamlined through the use of categorization, escalation, etc. Presenting our set of slides with Workflow For Security Incident Management Process. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identification, Categorization, Escalation.
-
 About Devsecops Model Workflow Process Devsecops Best Practices For Secure
About Devsecops Model Workflow Process Devsecops Best Practices For SecureThis slide gives an overview of the working procedure of DevSecOps. The purpose of this slide is to discuss the various steps involved in the DevSecOps working process, these include committing, analyzing, setting up the environment, testing, deploying, monitoring, and repeating. Introducing About Devsecops Model Workflow Process Devsecops Best Practices For Secure to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Devsecops Working Process, Analyzing, Testing, Deploying, Monitoring, using this template. Grab it now to reap its full benefits.
-
 Devsecops Best Practices For Secure About Devsecops Introduction And Working Process
Devsecops Best Practices For Secure About Devsecops Introduction And Working ProcessThis slide gives an overview of DevSecOps and its process. The purpose of this slide is to explain DevSecOps, including its process steps, which are release, deploy, operate, monitor, plan, code, build, and test. Present the topic in a bit more detail with this Devsecops Best Practices For Secure About Devsecops Introduction And Working Process. Use it as a tool for discussion and navigation on Development, Security, Operations, Smooth Integration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure About Workflow Process Of Devops Model
Devsecops Best Practices For Secure About Workflow Process Of Devops ModelThis slide discusses the working procedure of the DevOps model. The purpose of this slide is to showcase the working steps of the DevOps model for software building, these components include coding, branch, repo, CI or CD, production, registry, building, etc. Present the topic in a bit more detail with this Devsecops Best Practices For Secure About Workflow Process Of Devops Model. Use it as a tool for discussion and navigation on Software Building, Coding, Production, Registry, Security Considerations Occur Late. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure Overview Of Working Process Of Devsecops Model
Devsecops Best Practices For Secure Overview Of Working Process Of Devsecops ModelThis slide discusses the workflow procedure of DevSecOps model. The purpose of this slide is to showcase the working steps of DevSecOps model for software building and enhancing security at each level these include coding, branch, repo, CI or CD, production, etc. Present the topic in a bit more detail with this Devsecops Best Practices For Secure Overview Of Working Process Of Devsecops Model. Use it as a tool for discussion and navigation on Workflow Procedure Of Devsecops, Software Building, Enhancing Security, Production. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Cloud Access Security Broker Working Process
Sase Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Sase Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Discovery, Classification, Remediation, using this template. Grab it now to reap its full benefits.
-
 Sase Model Firewall As A Service Fwaas Working And Security Features
Sase Model Firewall As A Service Fwaas Working And Security FeaturesThis slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, and IP mapping. Deliver an outstanding presentation on the topic using this Sase Model Firewall As A Service Fwaas Working And Security Features. Dispense information and present a thorough explanation of Cloud Database, Email Cloud using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Secure Web Gateways SWG Setup And Working
Sase Model Secure Web Gateways SWG Setup And WorkingThis slide depicts the methods to setup the secure web gateways and their working. The purpose of this slide is to demonstrate the various ways in which organizations can install the SWGs. It also caters to the working and functions performed by SWGs to protect data and safe browsing on the internet. Introducing Sase Model Secure Web Gateways SWG Setup And Working to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Hardware Device, Access Regulations, Implementing Policies, using this template. Grab it now to reap its full benefits.
-
 Sase Model Working Of Secure Access Service Edge
Sase Model Working Of Secure Access Service EdgeThis slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. Present the topic in a bit more detail with this Sase Model Working Of Secure Access Service Edge. Use it as a tool for discussion and navigation on Traditional Network Security Model, Network Security Model. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How Does Phishing Attack Works Securing Blockchain Transactions A Beginners Guide BCT SS V
How Does Phishing Attack Works Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Increase audience engagement and knowledge by dispensing information using How Does Phishing Attack Works Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on six stages. You can also present information on Attackers Dispense Email, Steals Data, Obtains Information From System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview And Workflow Process Securing Blockchain Transactions A Beginners Guide BCT SS V
Overview And Workflow Process Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide showcases the brief introduction of eclipse attack to have understanding of malicious node among peer to peer network P2P. It includes elements such as how does and eclipse attack works, reconnecting with malicious node, exposure to information, etc. Present the topic in a bit more detail with this Overview And Workflow Process Securing Blockchain Transactions A Beginners Guide BCT SS V. Use it as a tool for discussion and navigation on Target Node, Attacker Nodes, Participating Nodes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview And Workflow Securing Blockchain Transactions A Beginners Guide BCT SS V
Overview And Workflow Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc. Introducing Overview And Workflow Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Transaction Requested, Node Validates Transaction, Transaction Completed, using this template. Grab it now to reap its full benefits.
-
 Overview And Working Process Securing Blockchain Transactions A Beginners Guide BCT SS V
Overview And Working Process Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates brief introduction of distributed denial of service DDoS attack to prevent user from leveraging key information. It includes elements such as hampering website with excessive internet traffic, minimizing website downtime, etc. Increase audience engagement and knowledge by dispensing information using Overview And Working Process Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on four stages. You can also present information on Attacker Controls Website Hostage, Demands Hefty Amount, Companies Are Imposed using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Internet Protocol Security Architecture And Working Encryption For Data Privacy In Digital Age It
Internet Protocol Security Architecture And Working Encryption For Data Privacy In Digital Age ItThis slide demonstrates the working of Internet Protocol Security. The main components of IPsec architecture are ESP protocol, AH protocol, encryption algorithm, authentication algorithm, key management, etc. Present the topic in a bit more detail with this Internet Protocol Security Architecture And Working Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Protocol Security, Architecture, Encryption Algorithm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Of Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age It
Working Of Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age ItThis slide illustrates the flow of several components in the working of Hypertext Transfer Protocol Secure HTTPS. The purpose of this slide is to showcase how data is encrypted in transit and transferred to the user using public and private keys. Present the topic in a bit more detail with this Working Of Hypertext Transfer Protocol Secure Encryption For Data Privacy In Digital Age It. Use it as a tool for discussion and navigation on Asymmetric Encryption, Symmetric Encryption, Transmission. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Protection Workplace Skills For Security Analysts
Cyber Protection Workplace Skills For Security AnalystsThe following slide highlights technical expertise and proficiency levels to demonstrate cybersecurity workplace skills for security analytics. It helps organizations evaluate and develop cybersecurity workforce effectively Presenting our well structured Cyber Protection Workplace Skills For Security Analysts. The topics discussed in this slide are Beginner, Intermediate, Advance. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Integrating ChatGPT With Other Systems Security How ChatGPT Actually Work ChatGPT SS V
Integrating ChatGPT With Other Systems Security How ChatGPT Actually Work ChatGPT SS VThis slide provides information regarding the integration of ChatGPT with other systems for managing security and compliance in terms of fraud detection, handling cybersecurity, risk assessment and compliance monitoring. Increase audience engagement and knowledge by dispensing information using Integrating ChatGPT With Other Systems Security How ChatGPT Actually Work ChatGPT SS V. This template helps you present information on four stages. You can also present information on Fraud Detection, Compliance Tracking, Risk Analysis using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Working And Architecture Of Firewall Security Technology Firewall Virtualization
Working And Architecture Of Firewall Security Technology Firewall VirtualizationThis slide demonstrates the architecture and working of traditional firewalls. The purpose of this slide is to illustrate the firewall architecture and working. The main components include corporate network, operation network and control system network. Deliver an outstanding presentation on the topic using this Working And Architecture Of Firewall Security Technology Firewall Virtualization. Dispense information and present a thorough explanation of Firewall Architecture, Corporate Network, Control System Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Of Firewall As A Service Security Technology Firewall Virtualization
Working Of Firewall As A Service Security Technology Firewall VirtualizationThis slide illustrates the working of Firewall-as-a-service technology. The purpose of this slide is to outline various actions performed by FWaaS such as Intrusion Prevention Systems, DNS security, etc. Main components include accept, drop and block. Increase audience engagement and knowledge by dispensing information using Working Of Firewall As A Service Security Technology Firewall Virtualization. This template helps you present information on five stages. You can also present information on Public Internet, Corporate Network, Companys Architecture using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Internet Gateway Security IT Secure Web Gateway Architecture And Working
Internet Gateway Security IT Secure Web Gateway Architecture And WorkingThis slide demonstrates the working process of Secure Web Gateway by providing a visualization of its various components. The purpose of this slide is to explain how SWG works. Key points included are offices, private data centres, interface, etc. Introducing Internet Gateway Security IT Secure Web Gateway Architecture And Working to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Policy Enforcement, Malware Detection, Web Proxy, Public Internet, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Working Components Of Secure Web Gateway
Internet Gateway Security IT Working Components Of Secure Web GatewayThis slide represents the key elements involved in the working of Secure Web Gateway. The purpose of this slide is to explain the different components of SWG. These include traffic inspection, URL filtering, application control, website content inspection, etc. Introducing Internet Gateway Security IT Working Components Of Secure Web Gateway to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Traffic Inspection, URL Filtering, Application Control, Website Content Inspection, Secure Socket Layer SSL Inspection, using this template. Grab it now to reap its full benefits.
-
 EDR Work Flowchart For Managing Security Incidents
EDR Work Flowchart For Managing Security IncidentsThis slide highlights EDR working flowchart and includes endpoints, database, restoration, IT analysts, and attackers. Introducing our EDR Work Flowchart For Managing Security Incidents set of slides. The topics discussed in these slides are Realtime Endpoint Behavior, Restoration, Behavioral Data, Managing Security Incidents. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Access Security Broker Working Process CASB Cloud Security
Cloud Access Security Broker Working Process CASB Cloud SecurityThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process CASB Cloud Security. This template helps you present information on three stages. You can also present information on Cloud Access Security, Broker Working Process, Classification And Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Forward Proxy Deployment Overview And Working CASB Cloud Security
Forward Proxy Deployment Overview And Working CASB Cloud SecurityThis slide describes the overview of the forward proxy deployment mode of the CASB model, including its working. The purpose of this slide is to showcase the working of proxy-based CASB deployment and the main components include user or clients, forward proxy, internet and origin server. Increase audience engagement and knowledge by dispensing information using Forward Proxy Deployment Overview And Working CASB Cloud Security. This template helps you present information on eight stages. You can also present information on Forward Proxy Deployment, Internet And Origin Server, According To The Internet Server using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparative Workflows Of Stos Beginners Guide To Successfully Launch Security Token BCT SS V
Comparative Workflows Of Stos Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide showcases how security token offerings STOs varies from initial coin offerings ICO to ensure transparency and liquidity. It includes elements such as money, token, investors, security laws, associated risks, etc. Introducing Comparative Workflows Of Stos Beginners Guide To Successfully Launch Security Token BCT SS V to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Securities Laws, Low Risks, High Risks, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Management Workflow
Cyber Security Incident Management WorkflowThis slide highlights workflow for handlingdigital safety incident. The purpose of this template is to assist businesses in mitigating threats for safeguarding sensitive data and maintain integrity of digital systems. It includes elements such as prepare, detect, analyze, etc. Presenting our set of slides with Cyber Security Incident Management Workflow. This exhibits information on Seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Prepare, Detect, Analyze, Contain
-
 Crisis Evaluation For Workplace Safety And Security
Crisis Evaluation For Workplace Safety And SecurityThe purpose of this slide is to emphasize how crisis evaluation for workplace safety and security ensures a systematic assessment, facilitating the implementation of measures to enhance workplace safety, security, and effective response during emergencies. Introducing our premium set of slides with Crisis Evaluation For Workplace Safety And Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Physical Security, Emergency Response Planning, Workplace Violence Prevention. So download instantly and tailor it with your information.
-
 Security Digital Hub Transformation In Workplace
Security Digital Hub Transformation In WorkplaceThis slide showcases the digital hub transformation workplace. Its aim is to integrate the workplace with digital platforms with easy user experience. This slide includes document, intranet, voice, video, enterprise, productivity apps, etc. Presenting our well structured Security Digital Hub Transformation In Workplace. The topics discussed in this slide are Document, Intranet, Social Network Enterprise. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.





