Powerpoint Templates and Google slides for Security Technologies
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Security In 5G Technology Architecture Ppt Powerpoint Presentation Slides Template
Security In 5G Technology Architecture Ppt Powerpoint Presentation Slides TemplateThis slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Increase audience engagement and knowledge by dispensing information using Security In 5G Technology Architecture Ppt Powerpoint Presentation Slides Template. This template helps you present information on four stages. You can also present information on Security Procedures, Mobile Technology, Service Delivery Process using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IoT Edge Computing Security Technology Icon
IoT Edge Computing Security Technology IconPresenting our well structured IoT Edge Computing Security Technology Icon. The topics discussed in this slide are Iot Edge Computing, Security Technology Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 IoT Edge Computing Security Technology Image
IoT Edge Computing Security Technology ImagePresenting our set of slides with IoT Edge Computing Security Technology Image. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Iot Edge Computing, Security Technology Image.
-
 5G Network Technology Architecture Security Architecture In 5G Technology
5G Network Technology Architecture Security Architecture In 5G TechnologyThis slide represents the security architecture in 5G technology, including the system wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Present the topic in a bit more detail with this 5G Network Technology Architecture Security Architecture In 5G Technology. Use it as a tool for discussion and navigation on System Wide Security, Security Functions, Trust Anchoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 5G Network Technology Architecture Security In 5G Technology Architecture
5G Network Technology Architecture Security In 5G Technology ArchitectureThis slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Introducing 5G Network Technology Architecture Security In 5G Technology Architecture to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Mobile Technologys Security, Service Delivery Process, 5G Security Features, using this template. Grab it now to reap its full benefits.
-
 Blockchain Technology For Business Security Icon
Blockchain Technology For Business Security IconIntroducing our Blockchain Technology For Business Security Icon set of slides. The topics discussed in these slides are Blockchain Technology, Business Security Icon. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Hospital Security Trends For Healthcare Technology Advancements
Hospital Security Trends For Healthcare Technology AdvancementsThis slide covers the details related to the hospital security trends. The purpose of this template is to digitally transform healthcare industry. It includes information related to managed access control, hospital management system, technology, etc. Introducing our premium set of slides with name Hospital Security Trends For Healthcare Technology Advancements. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Management System, Management Technology, Healthcare Facilities. So download instantly and tailor it with your information.
-
 Operational Technology Cyber Security In Powerpoint And Google Slides Cpb
Operational Technology Cyber Security In Powerpoint And Google Slides CpbPresenting our Operational Technology Cyber Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Operational Technology Cyber Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Key Smart Home Stats For Enhances Security And Technology Iot Smart Homes Automation IOT SS
Key Smart Home Stats For Enhances Security And Technology Iot Smart Homes Automation IOT SSThis slide provides an overview of the key statistics related to technology growth, security, video assistant and smart speaker. Major stats covered are a majority of the audience feel confutable using security devices, installation of technologies help homeowners save an average of dollar 98, etc Increase audience engagement and knowledge by dispensing information using Key Smart Home Stats For Enhances Security And Technology Iot Smart Homes Automation IOT SS. This template helps you present information on three stages. You can also present information on Technology Growth Stats, Video And Speaker Stats, Security Stats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain Technology Improving Supply Chain Security
Blockchain Technology Improving Supply Chain SecurityThe following slide highlights improving supply chain security using blockchain technology to ensure tamper proof block and transparency. It includes benefits such as error detection, improved security, increased speed and responsiveness and tracing products to root. Presenting our set of slides with Blockchain Technology Improving Supply Chain Security This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Error Detection, Improved Security
-
 Ultimate Guide For Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS
Ultimate Guide For Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SSThe following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Introducing Ultimate Guide For Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Integrity, Authentication using this template. Grab it now to reap its full benefits.
-
 Blockchain And IOT Security Technology For Healthcare Industry
Blockchain And IOT Security Technology For Healthcare IndustryThis slide highlights the importance of blockchain technology in healthcare industry which is used to preserve data and promote workflow authenticity. Key components are supply chain, electronic health records, safety access and staff verification. Presenting our set of slides with Blockchain And IOT Security Technology For Healthcare Industry. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Supply Chain, Electronic Health Records, Safety Access.
-
 Cyber Security Policy Critical Components Of Information Technology Policy
Cyber Security Policy Critical Components Of Information Technology PolicyThis slide depicts the critical components of information technology policy, and it includes integrity, confidentiality, and availability, including how these components work. Deliver an outstanding presentation on the topic using this Cyber Security Policy Critical Components Of Information Technology Policy. Dispense information and present a thorough explanation of Information, Technology, Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Policy Information Technology Policy Implementation Budget For Fy2022
Cyber Security Policy Information Technology Policy Implementation Budget For Fy2022This slide represents the companys IT policy implementation budget for FY2022. It covers the details of the software application and security services that need to be purchased and updated. Present the topic in a bit more detail with this Cyber Security Policy Information Technology Policy Implementation Budget For Fy2022. Use it as a tool for discussion and navigation on Information, Technology, Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Policy Introduction To Information Technology Policy
Cyber Security Policy Introduction To Information Technology PolicyThis slide represents the introduction to information technology policy, and it also describes the components of IT policy, such as investments, business applications, architecture, and infrastructure. Increase audience engagement and knowledge by dispensing information using Cyber Security Policy Introduction To Information Technology Policy. This template helps you present information on seven stages. You can also present information on Introduction, Information, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
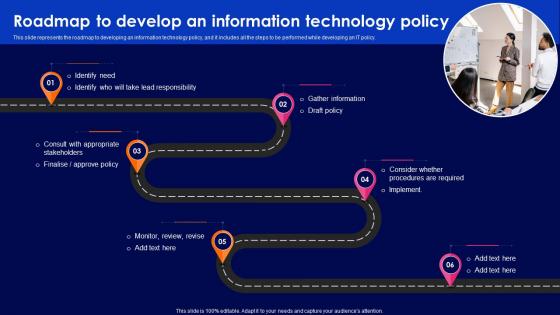 Cyber Security Policy Roadmap To Develop An Information Technology Policy
Cyber Security Policy Roadmap To Develop An Information Technology PolicyThis slide represents the roadmap to developing an information technology policy, and it includes all the steps to be performed while developing an IT policy. Introducing Cyber Security Policy Roadmap To Develop An Information Technology Policy to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Roadmap, Information, Technology, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Policy Timeline To Develop An Information Technology Policy
Cyber Security Policy Timeline To Develop An Information Technology PolicyThis slide represents the timeline to develop an information technology policy and it includes all the steps to be performed while developing an IT policy. Introducing Cyber Security Policy Timeline To Develop An Information Technology Policy to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Information, Technology, using this template. Grab it now to reap its full benefits.
-
 Latest Technologies Cyber Security Technology Market Overview Ppt Slides Summary
Latest Technologies Cyber Security Technology Market Overview Ppt Slides SummaryThis slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Deliver an outstanding presentation on the topic using this Latest Technologies Cyber Security Technology Market Overview Ppt Slides Summary. Dispense information and present a thorough explanation of Technology, Security, Market using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Latest Technologies Need For Cyber Security Technology Ppt Slides Inspiration
Latest Technologies Need For Cyber Security Technology Ppt Slides InspirationThis slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Increase audience engagement and knowledge by dispensing information using Latest Technologies Need For Cyber Security Technology Ppt Slides Inspiration. This template helps you present information on three stages. You can also present information on Internet, Security, Cyber using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
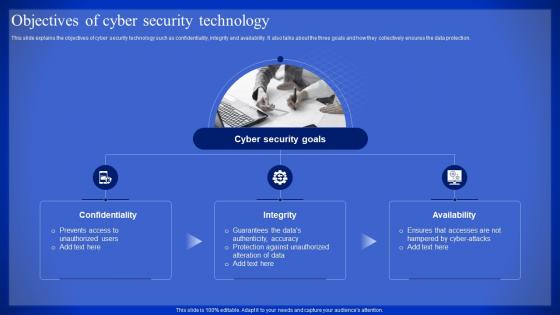 Latest Technologies Objectives Of Cyber Security Technology Ppt Slides Infographics
Latest Technologies Objectives Of Cyber Security Technology Ppt Slides InfographicsThis slide explains the objectives of cyber security technology such as confidentiality, integrity and availability. It also talks about the three goals and how they collectively ensures the data protection. Introducing Latest Technologies Objectives Of Cyber Security Technology Ppt Slides Infographics to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Integrity, Availability, using this template. Grab it now to reap its full benefits.
-
 Communication Technologies In Security Plan For Large Events
Communication Technologies In Security Plan For Large EventsThis slide presents major communication technologies which can be used by security teams to manage and report incidents in large events. The technologies covered are automated alerts, geofencing capabilities, cloud based system, etc.Introducing our premium set of slides with Communication Technologies In Security Plan For Large Events. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Geofencing Capabilities, Automated Alerts, Multi Channel Delivery. So download instantly and tailor it with your information.
-
 Open Ran Technology Role Of Security In Open Ran Standards Ppt Professional Design Templates
Open Ran Technology Role Of Security In Open Ran Standards Ppt Professional Design TemplatesThis slide represents the role of security in open RAN, which is built on the zero trust model. It means not to trust anybody and all the authorized and unauthorized devices, personnel, or networks have to go through some security checks. Present the topic in a bit more detail with this Open Ran Technology Role Of Security In Open Ran Standards Ppt Professional Design Templates. Use it as a tool for discussion and navigation on Infrastructure Components, Technological, Scrutinized. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Is Blockchain Technology Secure Cryptographic Ledger IT
Is Blockchain Technology Secure Cryptographic Ledger ITThis slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain.Present the topic in a bit more detail with this Is Blockchain Technology Secure Cryptographic Ledger IT. Use it as a tool for discussion and navigation on Generated Math Algorithms, Weaknesses Blockchain, Networks Nevertheless. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Play 11 Administering Security Privacy Through Digital Services Playbook For Technological Advancement
Play 11 Administering Security Privacy Through Digital Services Playbook For Technological AdvancementThis slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc. Deliver an outstanding presentation on the topic using this Play 11 Administering Security Privacy Through Digital Services Playbook For Technological Advancement. Dispense information and present a thorough explanation of Procedures, Service, Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F861 Security Architecture In 5g Technology Of 5g Technology Ppt Professional Design Templates
F861 Security Architecture In 5g Technology Of 5g Technology Ppt Professional Design TemplatesThis slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Deliver an outstanding presentation on the topic using this F861 Security Architecture In 5g Technology Of 5g Technology Ppt Professional Design Templates. Dispense information and present a thorough explanation of Architecture, Technology, Virtualization Infrastructure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security In 5g Technology Architecture Functions Of 5g Technology Ppt Show Designs Download
Security In 5g Technology Architecture Functions Of 5g Technology Ppt Show Designs DownloadThis slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Increase audience engagement and knowledge by dispensing information using Security In 5g Technology Architecture Functions Of 5g Technology Ppt Show Designs Download. This template helps you present information on five stages. You can also present information on Technology, Architecture, Process using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Blockchain Technology For Efficient Security Initiatives Protecting Recruitment Process
Blockchain Technology For Efficient Security Initiatives Protecting Recruitment ProcessThis slide showcases security initiatives which can help recruiters protect their sensitive information. It provides details about record keeping, secured storage, verification, decentralized info, etc. Increase audience engagement and knowledge by dispensing information using Blockchain Technology For Efficient Security Initiatives Protecting Recruitment Process. This template helps you present information on four stages. You can also present information on Candidate Information, Decentralized Job Listing, Candidate Qualifications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets Security
Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc. Deliver an outstanding presentation on the topic using this Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Potential, Technologies, Communication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SecOps Tools And Technologies Used In Security Operations Center Ppt Summary
SecOps Tools And Technologies Used In Security Operations Center Ppt SummaryThis slide highlights the crucial tools and technologies used in the SecOps environment. The purpose of this slide is to showcase the various tools and techniques a SOC requires. The main tools include log collection and management, vulnerability management, security information, and event management, etc. Deliver an outstanding presentation on the topic using this SecOps Tools And Technologies Used In Security Operations Center Ppt Summary. Dispense information and present a thorough explanation of Features, Technologies, Description using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Biometric Technology For Enhancing Mobile Banking For Convenient And Secure Online Payments Fin SS
Biometric Technology For Enhancing Mobile Banking For Convenient And Secure Online Payments Fin SSThis slide shows information which can be used by organizations to get insights about biometric technology growth in mobile banking. It includes details about process and types of biometric data. Deliver an outstanding presentation on the topic using this Biometric Technology For Enhancing Mobile Banking For Convenient And Secure Online Payments Fin SS. Dispense information and present a thorough explanation of Technology, Organizations, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Analysis Of Technologies Mobile Banking For Convenient And Secure Online Payments Fin SS
Comparative Analysis Of Technologies Mobile Banking For Convenient And Secure Online Payments Fin SSThis slide shows comparison which can be used to understand the key differences between techs used by e-wallets. It includes various basis of difference such as technology, compatibility, security, speed, range, etc. Present the topic in a bit more detail with this Comparative Analysis Of Technologies Mobile Banking For Convenient And Secure Online Payments Fin SS. Use it as a tool for discussion and navigation on Comparative, Analysis, Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1399 Flow Chart Showing Nfc Technology Mobile Banking For Convenient And Secure Online Payments Fin SS
F1399 Flow Chart Showing Nfc Technology Mobile Banking For Convenient And Secure Online Payments Fin SSThis slide shows details which can be used to understand how near field communication technology works in mobile payments. It includes various components such as mobile phone, payment app, bank, card issuer, card reader, etc. Deliver an outstanding presentation on the topic using this F1399 Flow Chart Showing Nfc Technology Mobile Banking For Convenient And Secure Online Payments Fin SS. Dispense information and present a thorough explanation of Technology, Verification, Transaction using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Flow Chart Showing Qr Code Technology Mobile Banking For Convenient And Secure Online Payments Fin SS
Flow Chart Showing Qr Code Technology Mobile Banking For Convenient And Secure Online Payments Fin SSThis slide shows diagram which can be used to understand the flow of payments when done through QR Quick Response code. It includes steps such as QR code creation, payer scans code, transaction request, request result, etc. Deliver an outstanding presentation on the topic using this Flow Chart Showing Qr Code Technology Mobile Banking For Convenient And Secure Online Payments Fin SS. Dispense information and present a thorough explanation of Technology, Transaction Request, Participating Vendor using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Near Field Communication Nfc Technology Mobile Banking Convenient And Secure Online Payments Fin SS
Near Field Communication Nfc Technology Mobile Banking Convenient And Secure Online Payments Fin SSThis slide shows information regarding NFC technology which is used for payments via mobile banking apps or e-wallets. It also includes advantages and disadvantages of near field communication technology. Present the topic in a bit more detail with this Near Field Communication Nfc Technology Mobile Banking Convenient And Secure Online Payments Fin SS. Use it as a tool for discussion and navigation on Communication, Technology, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Qr Quick Response Code Technology Mobile Banking For Convenient And Secure Online Payments Fin SS
Qr Quick Response Code Technology Mobile Banking For Convenient And Secure Online Payments Fin SSThis slide shows information regarding quick response technology which is commonly used for instant payments via mobile banking apps or e-wallets. It also includes advantages and disadvantages of QR codes. Deliver an outstanding presentation on the topic using this Qr Quick Response Code Technology Mobile Banking For Convenient And Secure Online Payments Fin SS. Dispense information and present a thorough explanation of Technology, Information, Disadvantages using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Three Layer Technological Framework Mobile Banking For Convenient And Secure Online Payments Fin SS
Three Layer Technological Framework Mobile Banking For Convenient And Secure Online Payments Fin SSThis slide shows details about technological model used by neobanks for running banking operations smoothly. It includes three layers which are hosting infrastructure, open source core platform architecture and front end apps for users. Present the topic in a bit more detail with this Three Layer Technological Framework Mobile Banking For Convenient And Secure Online Payments Fin SS. Use it as a tool for discussion and navigation on Technological, Framework, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
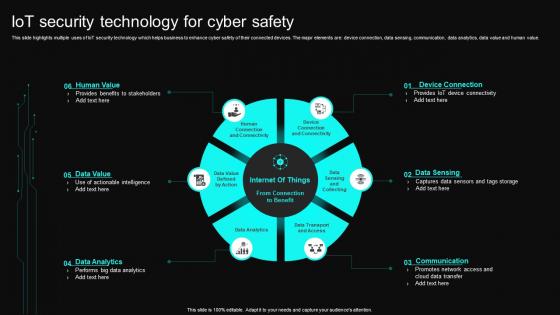 IOT Security Technology For Cyber Safety
IOT Security Technology For Cyber SafetyThis slide highlights multiple uses of IoT security technology which helps business to enhance cyber safety of their connected devices. The major elements are device connection, data sensing, communication, data analytics, data value and human value. Presenting our set of slides with IOT Security Technology For Cyber Safety. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Device Connection, Data Sensing, Communication, Data Analytics.
-
 Blockchain Technology Cyber Security Cases
Blockchain Technology Cyber Security CasesThis slide outlines cyber security use cases of block chain technology aimed at adopting secure, vigilant, resilient solution for building secure infrastructure. It covers secure private messaging, IoT security, secure DNS and DDoS, provenance of software and infrastructure verification. Presenting our set of slides with Blockchain Technology Cyber Security Cases. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure Private Messaging, Infrastructure Verification, Iot Security.
-
 Blockchain Technology Impact On Data Security
Blockchain Technology Impact On Data SecurityThis slide highlights impact on blockchain on data security aimed at reducing costs, increasing transparency, enhancing security and efficiency. It covers encryption and validation, decentralized data security with difficulties in hacking. Introducing our premium set of slides with Blockchain Technology Impact On Data Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Encryption And Validation, Decentralized Data Security, Difficulties In Hacking. So download instantly and tailor it with your information.
-
 Data Transfer Security Using Blockchain Technology Icon
Data Transfer Security Using Blockchain Technology IconIntroducing our premium set of slides with Data Transfer Security Using Blockchain Technology Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Transfer, Security Using, Blockchain Technology, Icon. So download instantly and tailor it with your information.
-
 Ecommerce Payment Security Using Blockchain Technology Icon
Ecommerce Payment Security Using Blockchain Technology IconPresenting our set of slides with Ecommerce Payment Security Using Blockchain Technology Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Ecommerce Payment, Security Using, Blockchain Technology, Icon.
-
 Network Security Methods Using Blockchain Technology
Network Security Methods Using Blockchain TechnologyThis slide outlines network secure methods using blockchain medium by using strong authentication and cryptography key vaulting mechanisms. It covers strong identification and authentication, secure core technologies and communication. Introducing our premium set of slides with Network Security Methods Using Blockchain Technology. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Strong Identities Authentication, Securing Core Technologies, Secure Communications. So download instantly and tailor it with your information.
-
 Security Issues Information Technology In Powerpoint And Google Slides Cpb
Security Issues Information Technology In Powerpoint And Google Slides CpbPresenting our Security Issues Information Technology In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Security Issues Information Technology. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Use Of Blockchain Technology In Cyber Security Blockchain Applications In Different Sectors
Use Of Blockchain Technology In Cyber Security Blockchain Applications In Different SectorsThis slide outlines the applications of blockchain technology in protecting against cyber security attacks. The purpose of this slide is to showcase the benefits, deployment factors, and top adopters for blockchain technology. It also includes the key feature that prevents fraud. Deliver an outstanding presentation on the topic using this Use Of Blockchain Technology In Cyber Security Blockchain Applications In Different Sectors. Dispense information and present a thorough explanation of Blockchain Features, Blockchain Platforms, Data Tampering using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB Future Use Of Emerging Technologies In CASB Model
Cloud Access Security Broker CASB Future Use Of Emerging Technologies In CASB ModelThis slide gives an overview of the technologies that can be used in the cloud access security broker model in the future. The purpose of this slide is to showcase the various emerging technologies that can help CASB to grow in the future. The technologies include AI, ML, CSPM, data privacy and protection, etc. Present the topic in a bit more detail with this Cloud Access Security Broker CASB Future Use Of Emerging Technologies In CASB Model. Use it as a tool for discussion and navigation on Technologies, Description, Zero Trust Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing It Technology Vendor Assessment Strategic Plan To Secure It Infrastructure Strategy SS V
Managing It Technology Vendor Assessment Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding assessment of IT technology vendors in order to select potential vendors by assessing them on different parameters such as incident management, testing, quality, etc. Present the topic in a bit more detail with this Managing It Technology Vendor Assessment Strategic Plan To Secure It Infrastructure Strategy SS V. Use it as a tool for discussion and navigation on Assessment, Technology, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prerequisites For Technology Leaders To Ensure Strategic Plan To Secure It Infrastructure Strategy SS V
Prerequisites For Technology Leaders To Ensure Strategic Plan To Secure It Infrastructure Strategy SS VThis slide provides information regarding IT professionals prerequisites to enable firm and IT success. The technology leaders include CIO, IT head, strategy team by highlighting their collaborative initiatives. Deliver an outstanding presentation on the topic using this Prerequisites For Technology Leaders To Ensure Strategic Plan To Secure It Infrastructure Strategy SS V. Dispense information and present a thorough explanation of Technology, Organizational, Success using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IoT Technologies For Logistics Securing Operations Of Logistics Through Integrated IoT
IoT Technologies For Logistics Securing Operations Of Logistics Through Integrated IoTThis slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. Deliver an outstanding presentation on the topic using this IoT Technologies For Logistics Securing Operations Of Logistics Through Integrated IoT. Dispense information and present a thorough explanation of Securing Operations Of Logistics, Threat Intelligence, Asset Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Bitcoin Vs Blockchain Technology Implementing Blockchain Security Solutions
Bitcoin Vs Blockchain Technology Implementing Blockchain Security SolutionsThis slide defines the difference between bitcoin and blockchain technology based on goal, trade, scope, strategy and status.Increase audience engagement and knowledge by dispensing information using Bitcoin Vs Blockchain Technology Implementing Blockchain Security Solutions. This template helps you present information on five stages. You can also present information on Efficiently Government Restrictions, Numerical Sequence, Property Currency using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Green Cloud Computing Improving Security By Green Computing Technology
Green Cloud Computing Improving Security By Green Computing TechnologyThis slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Present the topic in a bit more detail with this Green Cloud Computing Improving Security By Green Computing Technology. Use it as a tool for discussion and navigation on Security, Computing, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
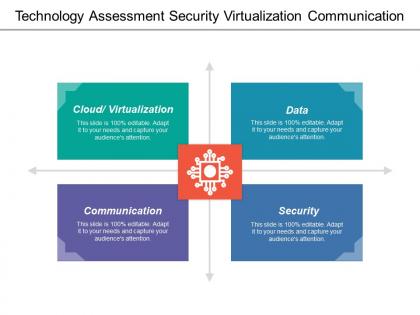 Technology assessment security virtualization communication
Technology assessment security virtualization communicationPresenting this set of slides with name - Technology Assessment Security Virtualization Communication. This is a four stage process. The stages in this process are Technology Assessment, Technology Forecasting, Technology Evaluation.
-
 Major internet security technologies internet protocol stack stateful inspection
Major internet security technologies internet protocol stack stateful inspectionPresenting this set of slides with name - Major Internet Security Technologies Internet Protocol Stack Stateful Inspection. This is an editable four graphic that deals with topics like Major Internet Security Technologies, Internet Protocol Stack, Stateful Inspection to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security technology roadmap risk framework protect framework
Security technology roadmap risk framework protect frameworkPresenting this set of slides with name - Security Technology Roadmap Risk Framework Protect Framework. This is an editable three stages graphic that deals with topics like Security Technology Roadmap, Risk Framework, Protect Framework to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Technology platform showing deployment and security model
Technology platform showing deployment and security modelPresenting technology platform showing deployment and security model. This is a technology platform showing deployment and security model. This is a nine stage process. The stages in this process are technology platform, software development, software architecture.
-
 Technology stack web applications services mobile security
Technology stack web applications services mobile securityPresenting this Technology Stack Web Applications Services Mobile Security presentation. The template is 100% customizable in PowerPoint and other similar software. Modify the font style, font color, and other attributes. The PPT is also compatible with Google Slides. Transform this template into various images or document formats such as JPEG or PDF. High-quality graphics ensure that quality is not affected even when size is enlarged.
-
 Introduction new technology product security policy implementation phase cpb
Introduction new technology product security policy implementation phase cpbPresenting this set of slides with name - Introduction New Technology Product Security Policy Implementation Phase Cpb. This is an editable three graphic that deals with topics like Introduction New Technology, Product Security Policy, Implementation Phase to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Technology security service quality load reduction swim lane
Technology security service quality load reduction swim lanePresenting technology security service quality load reduction swim lane PowerPoint slide. This layout is Compatible with Google Slides. Easy to put in company logo, trademark or name; accommodate words to support the key points. Images do no blur out even when they are projected on large screen.PPT template can be utilized by sales and marketing teams and business managers. Instantly downloadable slide and supports formats like JPEG and PDF. Adjust colors, text and fonts as per your business requirements.
-
 Half yearly technology security service quality operations timeline
Half yearly technology security service quality operations timelinePresenting this set of slides with name - Half Yearly Technology Security Service Quality Operations Timeline. This is a two stage process. The stages in this process are Technology Timeline, Technology Roadmap, It Timeline.
-
 Quarterly technology security service quality operations timeline
Quarterly technology security service quality operations timelinePresenting this set of slides with name - Quarterly Technology Security Service Quality Operations Timeline. This is a four stage process. The stages in this process are Technology Timeline, Technology Roadmap, It Timeline.
-
 Six months technology security service quality operations timeline
Six months technology security service quality operations timelinePresenting this set of slides with name - Six Months Technology Security Service Quality Operations Timeline. This is a six stage process. The stages in this process are Technology Timeline, Technology Roadmap, It Timeline.





