Powerpoint Templates and Google slides for Security Technologies
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Information Technology Security Powerpoint Presentation Slides
Information Technology Security Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts,this Information Technology Security Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought provoking. All the eighty one slides are editable and modifiable,so feel free to adjust them to your business setting. The font,color,and other components also come in an editable format making this PPT design the best choice for your next presentation. So,download now.
-
 Enterprise Risk Management And Information Technology Security Complete Deck
Enterprise Risk Management And Information Technology Security Complete DeckDeliver an informational PPT on various topics by using this Enterprise Risk Management And Information Technology Security Complete Deck. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with fifty two slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
-
 Security Automation In Information Technology Powerpoint Presentation Slides
Security Automation In Information Technology Powerpoint Presentation SlidesThis complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fourty two slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the color, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
-
 Smart Farming Technology Pitch Deck For Food Security Ppt Template
Smart Farming Technology Pitch Deck For Food Security Ppt TemplateThe right tools and strategies are crucial for success in the business world. And introducing your business to your stakeholders requires a Powerful Pitch Deck. Introduce your investor to our potential Smart Farming Technology Pitch Deck For Food Security Ppt Template Pitch Deck PPT Template. Dive into your company story with comprehensive slides covering essential information and key statistics. Customized charts and graphs to offer strategic insights into revenue models and key metrics, giving your pitch a competitive edge in front of your investors. Highlight your brands unique selling points with our 100 percent editable slides. Our Pitch Deck is perfect for introducing new products or refining existing ones. Also, you can edit the elements font color of the slide to make it fit for your use. Compatible with various Microsoft versions and Google Slides it can be downloaded in JPG, JPEG, PNG, and PDF format making this Pitch Standout.
-
 Risk Management Maturity Model Information Security Data Technology Culture
Risk Management Maturity Model Information Security Data Technology CultureDeliver a credible and compelling presentation by deploying this Risk Management Maturity Model Information Security Data Technology Culture. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twenty eight slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Risk Management Maturity Model Information Security Data Technology Culture PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Security Technology Stack Powerpoint Ppt Template Bundles
Security Technology Stack Powerpoint Ppt Template BundlesIf you require a professional template with great design, then this Security Technology Stack Powerpoint Ppt Template Bundles is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using Fourteen slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Security Technology Powerpoint Ppt Template Bundles
Security Technology Powerpoint Ppt Template BundlesIf you require a professional template with great design, then this Security Technology Powerpoint Ppt Template Bundles is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using seventeen slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Information Technology Security Powerpoint PPT Template Bundles
Information Technology Security Powerpoint PPT Template BundlesIntroduce your topic and host expert discussion sessions with this Information Technology Security Powerpoint PPT Template Bundles. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the twelve slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Blockchain Technology For Educational Institutes Security Systems Training Ppt
Blockchain Technology For Educational Institutes Security Systems Training PptPresenting Multiple ways by which Blockchain Technology can help Improve Educational Institutes Security Systems. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Benefits Of Blockchain Technology For Data Security Training Ppt
Benefits Of Blockchain Technology For Data Security Training PptPresenting Benefits of Blockchain Technology for Data Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Download this professionally designed business presentation, add your content, and present it with confidence.
-
 Security And Privacy Benefit Of Blockchain Technology Training Ppt
Security And Privacy Benefit Of Blockchain Technology Training PptPresenting Security and Privacy Benefit of Blockchain Technology. This slide is well crafted and designed by our PowerPoint specialists. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. You can add or delete the content as per your need.
-
 Router Icon Computer Technology Strength Security Arrow Network
Router Icon Computer Technology Strength Security Arrow NetworkIt has PPT slides covering wide range of topics showcasing all the core areas of your business needs. This complete deck focuses on Router Icon Computer Technology Strength Security Arrow Network and consists of professionally designed templates with suitable graphics and appropriate content. This deck has total of twelve slides. Our designers have created customizable templates for your convenience. You can make the required changes in the templates like colour, text and font size. Other than this, content can be added or deleted from the slide as per the requirement. Get access to this professionally designed complete deck PPT presentation by clicking the download button below.
-
 Technology Security Process Framework Assessment Management Awareness
Technology Security Process Framework Assessment Management AwarenessThis complete deck can be used to present to your team. It has PPT slides on various topics highlighting all the core areas of your business needs. This complete deck focuses on Technology Security Process Framework Assessment Management Awareness and has professionally designed templates with suitable visuals and appropriate content. This deck consists of total of twelve slides. All the slides are completely customizable for your convenience. You can change the colour, text and font size of these templates. You can add or delete the content if needed. Get access to this professionally designed complete presentation by clicking the download button below.
-
 Shield Security Protection Coronavirus Financial Technology Insurance
Shield Security Protection Coronavirus Financial Technology InsuranceDeliver a lucid presentation by utilizing this Shield Security Protection Coronavirus Financial Technology Insurance. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Shield, Security, Protection, Coronavirus, Financial. All the twelve slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
 Blockchain icon symbol circle computers encryption security technology
Blockchain icon symbol circle computers encryption security technologyEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Blockchain Icon Symbol Circle Computers Encryption Security Technology is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
 Threat Technology Security Displaying Cybersecurity Companies
Threat Technology Security Displaying Cybersecurity CompaniesIntroduce your topic and host expert discussion sessions with this Threat Technology Security Displaying Cybersecurity Companies. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the twelve slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Blockchain in banking technology security payment transactions financial settlement
Blockchain in banking technology security payment transactions financial settlementEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Blockchain In Banking Technology Security Payment Transactions Financial Settlement is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
 Industrial security management evaluation technology structure
Industrial security management evaluation technology structureThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Industrial Security Management Evaluation Technology Structure and has templates with professional background images and relevant content. This deck consists of total of eleven slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the colour, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
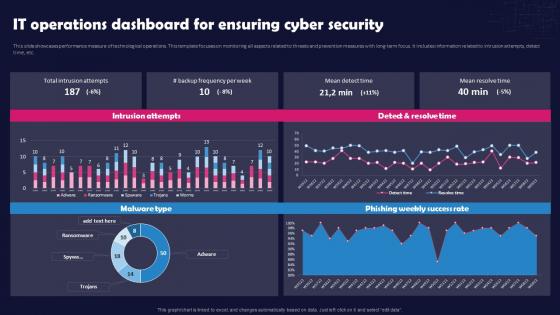 Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber Security
Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber SecurityThis slide showcases performance measure of technological operations. This template focuses on monitoring all aspects related to threats and prevention measures with long-term focus. It includes information related to intrusion attempts, detect time, etc. Present the topic in a bit more detail with this Unlocking The Impact Of Technology It Operations Dashboard For Ensuring Cyber Security. Use it as a tool for discussion and navigation on IT Operations Dashboard, Ensuring Cyber Security, Threats And Prevention, Technological Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Confidential Driven By Cloud And Security Initiatives Confidential Computing System Technology
Confidential Driven By Cloud And Security Initiatives Confidential Computing System TechnologyThis slide talks about the confidential computing market driven by cloud and security initiatives. The purpose of this slide is to showcase the confidential computing total addressable market growth drivers, such as awareness about confidential computing, increased demand for security and so on. Deliver an outstanding presentation on the topic using this Confidential Driven By Cloud And Security Initiatives Confidential Computing System Technology. Dispense information and present a thorough explanation of Confidential, Enterprise, Awareness using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Challenges Faced By Mining Industry How IoT Technology Is Transforming IoT SS
Security Challenges Faced By Mining Industry How IoT Technology Is Transforming IoT SSThe following slide showcases multiple Internet of Things IoT security issues faced by mining companies. The challenges mentioned in slide are IoT devices risk, lack of security update, insider threats, physical security, and distributed attack surfaces. Present the topic in a bit more detail with this Security Challenges Faced By Mining Industry How IoT Technology Is Transforming IoT SS. Use it as a tool for discussion and navigation on Iot Devices Vulnerabilities, Lack Security Update, Physical Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Various Types Of Honeypot Technologies In Blockchain Hands On Blockchain Security Risk BCT SS V
Various Types Of Honeypot Technologies In Blockchain Hands On Blockchain Security Risk BCT SS VThe following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Honeypot Technologies In Blockchain Hands On Blockchain Security Risk BCT SS V. This template helps you present information on two stages. You can also present information on Client Honeyspot, Malware Honeypots using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
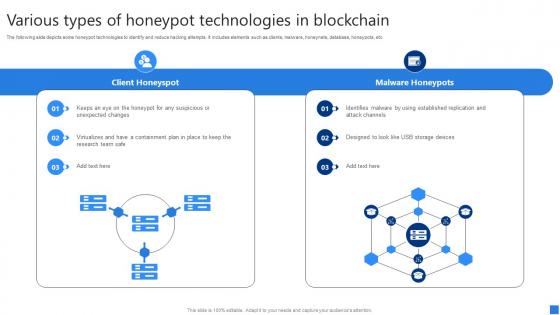 Various Types Of Honeypot Technologies Securing Blockchain Transactions A Beginners Guide BCT SS V
Various Types Of Honeypot Technologies Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc. Deliver an outstanding presentation on the topic using this Various Types Of Honeypot Technologies Securing Blockchain Transactions A Beginners Guide BCT SS V. Dispense information and present a thorough explanation of Client Honeyspot, Malware Honeypots, Honeypot Suspicious using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Expenditure Summary Dashboard Creating Cyber Security Awareness
Information Technology Expenditure Summary Dashboard Creating Cyber Security AwarenessThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Deliver an outstanding presentation on the topic using this Information Technology Expenditure Summary Dashboard Creating Cyber Security Awareness Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Security Failure By Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats
Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Deliver an outstanding presentation on the topic using this Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Cyber Security Budget Spent, It Costs And Revenue, Issue Status Summary using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Allocation Of Funds Smart Farming Technology Pitch Deck For Food Security
Allocation Of Funds Smart Farming Technology Pitch Deck For Food SecurityFollowing slide showcases company funds usage for various agriculture and farming development. It includes funds allocated for technology, marketing, food security etc. Present the topic in a bit more detail with this Allocation Of Funds Smart Farming Technology Pitch Deck For Food Security Use it as a tool for discussion and navigation on Funds Allocation, Crop Productivity, Overcome Operational This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Shareholding Pattern Smart Farming Technology Pitch Deck For Food Security
Shareholding Pattern Smart Farming Technology Pitch Deck For Food SecurityFollowing slide showcases shareholding pattern of company. It include details about company shareholders name, designation and percentage of shares holdings. Present the topic in a bit more detail with this Shareholding Pattern Smart Farming Technology Pitch Deck For Food Security Use it as a tool for discussion and navigation on Shareholding Pattern, Banking Company This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technological Use Cases Of Fintech Cyber Security
Technological Use Cases Of Fintech Cyber SecurityThis slide graphically represent the best technologies of fintech cyber security industry. Its aim is to manage the best available method for securing the industry. This slide includes cloud, data analytics, cyber security, mobile banking, AI, payments, etc. Introducing our Technological Use Cases Of Fintech Cyber Security set of slides. The topics discussed in these slides are . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Email Security Best Practices Benefits Of Using Email Security Technologies
Email Security Best Practices Benefits Of Using Email Security TechnologiesThis slide outlines the advantages of email security. These include control device access, identify suspicious user behaviour, improve spam and phishing protection, maintain communication confidentiality, protection against zero-day threats, real-time threat protection, etc. Present the topic in a bit more detail with this Email Security Best Practices Benefits Of Using Email Security Technologies. Use it as a tool for discussion and navigation on Control Device Access, Identify Suspicious User Behaviour, Real-Time Threat Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
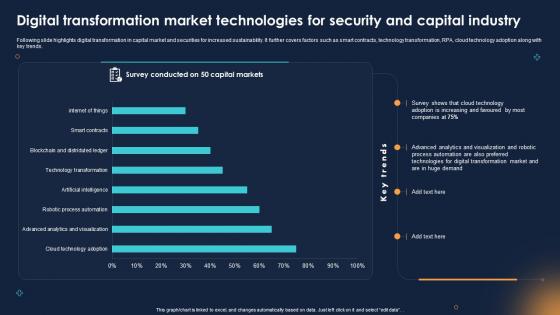 Digital Transformation Market Technologies For Security And Capital Industry
Digital Transformation Market Technologies For Security And Capital IndustryFollowing slide highlights digital transformation in capital market and securities for increased sustainability. It further covers factors such as smart contracts, technology transformation, RPA, cloud technology adoption along with key trends. Presenting our well structured Digital Transformation Market Technologies For Security And Capital Industry. The topics discussed in this slide are Digital Transformation Market Technologies, Security And Capital Industry, Visualization And Robotic Process. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Information Technology Security Assessment Dashboard
Information Technology Security Assessment DashboardThis slide represents dashboard for information technology security assessment which includes elements such as intrusion attempts, mean resolve time, mean detect time, etc. Introducing our Information Technology Security Assessment Dashboard set of slides. The topics discussed in these slides are Intrusion Attempts, IT Security Rating, Phishing Test Success Rate. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Automation Ideas Mechanization Cyber Security Infrastructure Implement Technology Material
Automation Ideas Mechanization Cyber Security Infrastructure Implement Technology MaterialEnhance your audiences knowledge with this well researched complete deck. Showcase all the important features of the deck with perfect visuals. This deck comprises of total of ten slides with each slide explained in detail. Each template comprises of professional diagrams and layouts. Our professional PowerPoint experts have also included icons, graphs and charts for your convenience. All you have to do is DOWNLOAD the deck. Make changes as per the requirement. Yes, these PPT slides are completely customizable. Edit the colour, text and font size. Add or delete the content from the slide. And leave your audience awestruck with the professionally designed Automation Ideas Mechanization Cyber Security Infrastructure Implement Technology Material complete deck.
-
 Guide to serverless technologies security related challenges in serverless technology
Guide to serverless technologies security related challenges in serverless technologyThe purpose of the following slide is to show the various challenges that may present to the organization, these issues can be authentication issues, no-proper monitoring, and third-party dependency.Increase audience engagement and knowledge by dispensing information using Guide To Serverless Technologies Security Related Challenges In Serverless Technology. This template helps you present information on four stages. You can also present information on Serverless Technology, Improper Monitoring And Controlling, Detecting Any Malware using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Play 11 Administering Security And Privacy Technological Advancement Playbook
Play 11 Administering Security And Privacy Technological Advancement PlaybookThis slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc.Deliver an outstanding presentation on the topic using this Play 11 Administering Security And Privacy Technological Advancement Playbook. Dispense information and present a thorough explanation of Develop Automated, Metrics Tracking, Customer Satisfaction using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Zero Trust Security Model Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch
Zero Trust Security Model Step 4 And 5 Available Technology Review And Zero Trust Initiatives LaunchThis slide represents the fourth and fifth steps of ZTNA deployment, which is reviewing available technology and launching primary zero trust projects. The purpose of this slide is to showcase the next steps in zero trust model implementation. Present the topic in a bit more detail with this Zero Trust Security Model Step 4 And 5 Available Technology Review And Zero Trust Initiatives Launch. Use it as a tool for discussion and navigation on Technology, Equipment, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Play 11 Administering Security And Privacy Through Reusable Modern Technology Stack Playbook
Play 11 Administering Security And Privacy Through Reusable Modern Technology Stack PlaybookThis slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc. Present the topic in a bit more detail with this Play 11 Administering Security And Privacy Through Reusable Modern Technology Stack Playbook. Use it as a tool for discussion and navigation on Security, Privacy, Procedures. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall As A Service Fwaas Working And Architecture Of Firewall Security Technology
Firewall As A Service Fwaas Working And Architecture Of Firewall Security TechnologyThis slide demonstrates the architecture and working of traditional firewalls. The purpose of this slide is to illustrate the firewall architecture and working. The main components include corporate network, operation network and control system network. Present the topic in a bit more detail with this Firewall As A Service Fwaas Working And Architecture Of Firewall Security Technology. Use it as a tool for discussion and navigation on Operator Workstation, Administrator Workstation, Control Systems, Data Acquisition, Internal Databases And Servers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Working Of Firewall As A Service Security Technology Ppt Ideas Graphic Images
Working Of Firewall As A Service Security Technology Ppt Ideas Graphic ImagesThis slide illustrates the working of Firewall-as-a-service technology. The purpose of this slide is to outline various actions performed by FWaaS such as Intrusion Prevention Systems, DNS security, etc. Main components include accept, drop and block. Deliver an outstanding presentation on the topic using this Working Of Firewall As A Service Security Technology Ppt Ideas Graphic Images. Dispense information and present a thorough explanation of Advanced Unified Threat Management, Active Directory Integration, Compliance Reporting, Single Pane Of Glass using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enhanced Security Application With Blockchain Technology Icon
Enhanced Security Application With Blockchain Technology IconIntroducing our Enhanced Security Application With Blockchain Technology Icon set of slides. The topics discussed in these slides are Enhanced Security Application, Blockchain Technology Icon. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
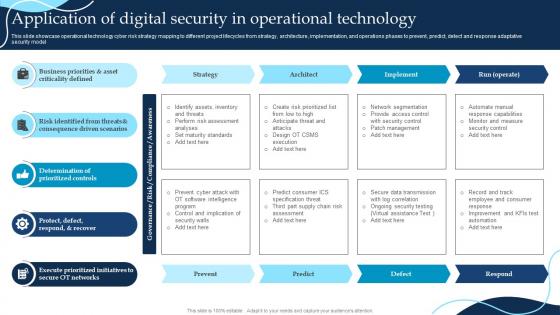 Application Of Digital Security In Operational Technology
Application Of Digital Security In Operational TechnologyThis slide showcase operational technology cyber risk strategy mapping to different project lifecycles from strategy, architecture, implementation, and operations phases to prevent, predict, detect and response adaptative security model Presenting our well structured Application Of Digital Security In Operational Technology. The topics discussed in this slide are Digital, Priorities, Scenarios. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Technologies Used In Zero Trust Network Access Zero Trust Security Model
Technologies Used In Zero Trust Network Access Zero Trust Security ModelThis slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer. Deliver an outstanding presentation on the topic using this Technologies Used In Zero Trust Network Access Zero Trust Security Model. Dispense information and present a thorough explanation of Technologies, Techniques, Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Security Encryption Technology Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Encryption Technology Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis high quality coloured PowerPoint icon depicts Data Encryption Technology, with a bright and vibrant design. Perfect for presentations, brochures, and other digital projects. Easily add to your project to illustrate the importance of data security.
-
 Data Security Encryption Technology Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Encryption Technology Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is a great visual representation of Data Encryption Technology. It is a simple and modern design that easily conveys the concept of secure data transmission. It is perfect for presentations on data security and encryption technology.
-
 Future Of Secure Web Gateway Technology Network Security Using Secure Web Gateway
Future Of Secure Web Gateway Technology Network Security Using Secure Web GatewayThis slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. Increase audience engagement and knowledge by dispensing information using Future Of Secure Web Gateway Technology Network Security Using Secure Web Gateway. This template helps you present information on five stages. You can also present information on Predicted, Investment, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Introduction To Secure Web Gateway Technology Network Security Using Secure Web Gateway
Introduction To Secure Web Gateway Technology Network Security Using Secure Web GatewayThis slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Deliver an outstanding presentation on the topic using this Introduction To Secure Web Gateway Technology Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Introduction, Technology, Overview using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risk Assessment And Technology Deployment Plan To Improve Organizations
Cyber Security Risk Assessment And Technology Deployment Plan To Improve OrganizationsThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Technology Deployment Plan To Improve Organizations. Dispense information and present a thorough explanation of Consequences, Vulnerability, Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various Cyber Security Incidents Detected By Technology Deployment Plan To Improve Organizations
Various Cyber Security Incidents Detected By Technology Deployment Plan To Improve OrganizationsThis slide represents the detection of certain attacks which affected the systems and networks of the organization by the IT department of the organization. It includes detection of cyber security incidents such as insider threat, phishing attack, malware attack etc. Introducing Various Cyber Security Incidents Detected By Technology Deployment Plan To Improve Organizations to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Phishing, Malware, Application, using this template. Grab it now to reap its full benefits.
-
 Emerging Security Technologies In Powerpoint And Google Slides Cpb
Emerging Security Technologies In Powerpoint And Google Slides CpbPresenting our Emerging Security Technologies In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases Five stages. It is useful to share insightful information on Emerging Security Technologies This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Technology Cyber Security In Powerpoint And Google Slides Cpb
Technology Cyber Security In Powerpoint And Google Slides CpbPresenting our Technology Cyber Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Technology Cyber Security. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
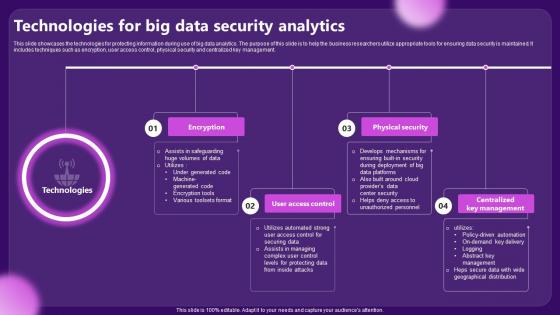 Technologies For Big Data Security Analytics
Technologies For Big Data Security AnalyticsThis slide showcases the technologies for protecting information during use of big data analytics. The purpose of this slide is to help the business researchers utilize appropriate tools for ensuring data security is maintained. It includes techniques such as encryption, user access control, physical security and centralized key management. Introducing our premium set of slides with Technologies For Big Data Security Analytics. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Encryption, Physical Security. So download instantly and tailor it with your information.
-
 Communication Plan For Cyber Security Technology Initiatives
Communication Plan For Cyber Security Technology InitiativesThis slide shows communication plan for tackling with different types of cyber attacks that can affect organization security in several ways. It include cyber attacks, initiates and owner, etc. Introducing our premium set of slides with Communication Plan For Cyber Security Technology Initiatives. Ellicudate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Ransom Ware, Denial Of Services, Malicious Insider. So download instantly and tailor it with your information.
-
 Information Technology Network Security Computing Illustration
Information Technology Network Security Computing IllustrationThis colourful PowerPoint icon is perfect for presentations on Information Technology topics. It features a laptop with a blue and green screen, a yellow and red processor, and a purple and orange hard drive. It is a great visual aid to help you explain complex IT concepts.
-
 Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS V
Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS VThis slide covers checklist for assessing vendor before integrating technology strategy in operations to enhance security. It involves key points such as IT risk assessment, threat and security experts and expertise in developing new technologies. Deliver an outstanding presentation on the topic using this Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS V. Dispense information and present a thorough explanation of Cloud Environments, Risk Arising, Digital Transformation Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Operational Technology Security Controls To Enhance Safety Guide For Integrating Technology Strategy SS V
Operational Technology Security Controls To Enhance Safety Guide For Integrating Technology Strategy SS VThis slide covers operational technology security controls to improve IT safety. It involves five kinds of security controls such as update asset inventory, training, ,manage portable media and secure configuration. Introducing Operational Technology Security Controls To Enhance Safety Guide For Integrating Technology Strategy SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Update Asset Inventory, Portable Media, Backup And Restore, using this template. Grab it now to reap its full benefits.
-
 Advanced Technologies Cyber Security Technology Market Overview
Advanced Technologies Cyber Security Technology Market OverviewThis slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Increase audience engagement and knowledge by dispensing information using Advanced Technologies Cyber Security Technology Market Overview. This template helps you present information on Two stages. You can also present information on Pros, Cons using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Advanced Technologies Need For Cyber Security Technology
Advanced Technologies Need For Cyber Security TechnologyThis slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Deliver an outstanding presentation on the topic using this Advanced Technologies Need For Cyber Security Technology. Dispense information and present a thorough explanation of Need For Cyber Security, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Advanced Technologies Objectives Of Cyber Security Technology
Advanced Technologies Objectives Of Cyber Security TechnologyThis slide explains the objectives of cyber security technology such as confidentiality, integrity and availability. It also talks about the three goals and how they collectively ensures the data protection. Increase audience engagement and knowledge by dispensing information using Advanced Technologies Objectives Of Cyber Security Technology. This template helps you present information on Three stages. You can also present information on Confidentiality, Integrity, Availability using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Future Use Of Emerging Technologies In CASB Model
Cloud Access Security Broker CASB V2 Future Use Of Emerging Technologies In CASB ModelThis slide gives an overview of the technologies that can be used in the Cloud Access Security Broker model in the future. The purpose of this slide is to showcase the various emerging technologies that can help CASB to grow in the future. The technologies include AI, ML, CSPM, data privacy and protection, etc. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Future Use Of Emerging Technologies In CASB Model. Dispense information and present a thorough explanation of Cloud Security Posture Management, Data Privacy And Protection, Zero Trust Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Lorawan Lorawan Technology Security Session Keys Ppt Show Inspiration
Lorawan Lorawan Technology Security Session Keys Ppt Show InspirationThis slide explains LoRaWAN security session keys which are used to ensure secure communication between LoRaWAN devices and network servers. Purpose of this slide is to define two types of session keys the application session key AppSKey and the network session key NwkSKey. Deliver an outstanding presentation on the topic using this Lorawan Lorawan Technology Security Session Keys Ppt Show Inspiration. Dispense information and present a thorough explanation of Overview, Technology, Transmission using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secops V2 Tools And Technologies Used In Security Operations Center
Secops V2 Tools And Technologies Used In Security Operations CenterThis slide highlights the crucial tools and technologies used in the SecOps environment. The purpose of this slide is to showcase the various tools and techniques a SOC requires. The main tools include log collection and management, vulnerability management, security information, and event management, etc. Deliver an outstanding presentation on the topic using this Secops V2 Tools And Technologies Used In Security Operations Center. Dispense information and present a thorough explanation of Vulnerability Management, Log Collection And Management Tool, Security Information And Event Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




