Powerpoint Templates and Google slides for Security Technologies
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Edge Computing Technology Key Edge AI Security Strategies AI SS
Edge Computing Technology Key Edge AI Security Strategies AI SSThis slide showcases 5 major edge AI security strategies so that developers can build and deploy their models in secured way. It provides details about secured perimeter, secured applications, early detection, automated patch, etc. Introducing Edge Computing Technology Key Edge AI Security Strategies AI SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Creating A Secure Perimeter, Securing Applications, Early Detection, Creating Automated Patch, using this template. Grab it now to reap its full benefits.
-
 Edge Computing Technology Security Considerations For Edge Computing Software AI SS
Edge Computing Technology Security Considerations For Edge Computing Software AI SSThis slide showcases major security considerations for edge computing software solutions. It provides details about Securing data transmissions, Access control and authentication, Encryption for data protection, etc. Present the topic in a bit more detail with this Edge Computing Technology Security Considerations For Edge Computing Software AI SS. Use it as a tool for discussion and navigation on Securing Data Transmissions, Access Control And Authentication, Encryption For Data Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Biometric Technology For Enhancing Mobile Banking Security E Wallets As Emerging Payment Method Fin SS V
Biometric Technology For Enhancing Mobile Banking Security E Wallets As Emerging Payment Method Fin SS VThis slide shows information which can be used by organizations to get insights about biometric technology growth in mobile banking. It includes details about process and types of biometric data. Present the topic in a bit more detail with this Biometric Technology For Enhancing Mobile Banking Security E Wallets As Emerging Payment Method Fin SS V. Use it as a tool for discussion and navigation on Biometric, Technology, Iris Recognition. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Emerging Technologies Cyber Security Technology Market Overview
Emerging Technologies Cyber Security Technology Market OverviewThis slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Deliver an outstanding presentation on the topic using this Emerging Technologies Cyber Security Technology Market Overview. Dispense information and present a thorough explanation of Overview Of Cyber Security, False Sense Of Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Emerging Technologies Need For Cyber Security Technology
Emerging Technologies Need For Cyber Security TechnologyThis slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Deliver an outstanding presentation on the topic using this Emerging Technologies Need For Cyber Security Technology. Dispense information and present a thorough explanation of Protection, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Emerging Technologies Objectives Of Cyber Security Technology
Emerging Technologies Objectives Of Cyber Security TechnologyThis slide explains the objectives of cyber security technology such as confidentiality, integrity and availability. It also talks about the three goals and how they collectively ensures the data protection. Introducing Emerging Technologies Objectives Of Cyber Security Technology to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Integrity, using this template. Grab it now to reap its full benefits.
-
 Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use
Encryption Implementation Strategies Data Protection Technologies To Secure Information In UseThis slide compares different data in use protection methods, and their working and associated cost. These methods are IDM Identity and Access Management, RBAC Role Based Access and conditional access, IRM Information Rights Management, etc. Present the topic in a bit more detail with this Encryption Implementation Strategies Data Protection Technologies To Secure Information In Use. Use it as a tool for discussion and navigation on Identity Management Tools, Digital Rights Protection, Data Protection Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Implementation Strategies Encryption Technologies To Secure Data At Rest
Encryption Implementation Strategies Encryption Technologies To Secure Data At RestThis slide compares different data protection methods, highlighting their advantages and limitations. These methods are full disk encryption, file-level encryption, database encryption, information rights management IRM, data leak prevention DLP,etc. Deliver an outstanding presentation on the topic using this Encryption Implementation Strategies Encryption Technologies To Secure Data At Rest. Dispense information and present a thorough explanation of Information Rights Management, Data Leak Prevention, Full Disk Encryption, Cloud Access Security Brokers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Encryption Implementation Strategies Secure Socket Layer SSL Security Technology
Encryption Implementation Strategies Secure Socket Layer SSL Security TechnologyThe purpose of this slide is to explain the role of HTTPS and the secure sockets layer SSL protocol for secure connections. This slide also discusses the incorporation of symmetric and asymmetric encryption during the SSL handshake process. Present the topic in a bit more detail with this Encryption Implementation Strategies Secure Socket Layer SSL Security Technology. Use it as a tool for discussion and navigation on Secure Socket Layer, Security Technology, Symmetric And Asymmetric Encryption, Protocol For Secure Connections. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encryption Technologies To Secure Data In Transit Encryption Implementation Strategies
Encryption Technologies To Secure Data In Transit Encryption Implementation StrategiesThis slide compares different data in transit protection methods, including their working and associated cost. These methods are email encryption, Managed File Transfer MFT, Data Leak Prevention DLP, Cloud Access Security Brokers CASB, etc. Deliver an outstanding presentation on the topic using this Encryption Technologies To Secure Data In Transit Encryption Implementation Strategies. Dispense information and present a thorough explanation of Managed File Transfer, Cloud Access Security Brokers, Email Encryption, Encryption Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Green Cloud Computing V2 Improving Security By Green Computing Technology
Green Cloud Computing V2 Improving Security By Green Computing TechnologyThis slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Present the topic in a bit more detail with this Green Cloud Computing V2 Improving Security By Green Computing Technology. Use it as a tool for discussion and navigation on Green Computing, Data Security, Security Concerns And Solution, Computers And Networks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Trending Technologies Cyber Security Technology Market Overview
Trending Technologies Cyber Security Technology Market OverviewThis slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Deliver an outstanding presentation on the topic using this Trending Technologies Cyber Security Technology Market Overview. Dispense information and present a thorough explanation of Pros, Cons using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Trending Technologies Need For Cyber Security Technology
Trending Technologies Need For Cyber Security TechnologyThis slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Increase audience engagement and knowledge by dispensing information using Trending Technologies Need For Cyber Security Technology. This template helps you present information on three stages. You can also present information on Cyber Security Solutions, Malicious Criminals, Data And Privacy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
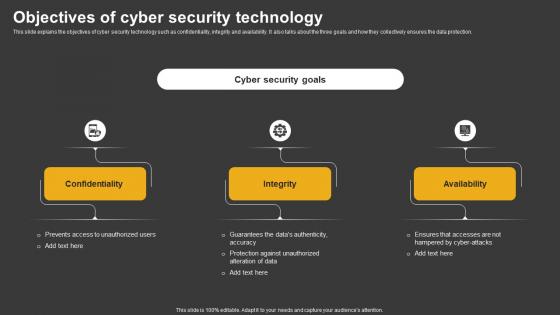 Trending Technologies Objectives Of Cyber Security Technology
Trending Technologies Objectives Of Cyber Security TechnologyThis slide explains the objectives of cyber security technology such as confidentiality, integrity and availability. It also talks about the three goals and how they collectively ensures the data protection. Introducing Trending Technologies Objectives Of Cyber Security Technology to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Integrity, Availability, using this template. Grab it now to reap its full benefits.
-
 Secured Automated Lending Technology In Powerpoint And Google Slides Cpb
Secured Automated Lending Technology In Powerpoint And Google Slides CpbPresenting Secured Automated Lending Technology In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secured Automated Lending Technology. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Biometric Technology For Enhancing Online Security Ultimate Guide To Commercial Fin SS
Biometric Technology For Enhancing Online Security Ultimate Guide To Commercial Fin SSThis slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data. Present the topic in a bit more detail with this Biometric Technology For Enhancing Online Security Ultimate Guide To Commercial Fin SS. Use it as a tool for discussion and navigation on Biometric Authentication Process, Make Biometrics More Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain Technology For Securing IoT Data How IoT Technology Is Transforming IoT SS
Blockchain Technology For Securing IoT Data How IoT Technology Is Transforming IoT SSThe following slide showcases solutions to overcome Internet of Things IoT security challenges faced by mining companies. Information covered in this slide is related to secure data sharing, improved compliance and safety, secure transactions and payments.Introducing Blockchain Technology For Securing IoT Data How IoT Technology Is Transforming IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure Data Sharing, Blockchain Technology, Enables Execution, using this template. Grab it now to reap its full benefits.
-
 Consequences Of Security Challenge On Mining How IoT Technology Is Transforming IoT SS
Consequences Of Security Challenge On Mining How IoT Technology Is Transforming IoT SSThe following slide showcases impact of Internet of Things IoT security challenges on mining companies. The slide covers information about unsafe working conditions, lost data, higher downtime, data leak, cost associated with security incident, loss of productivity, etc.Increase audience engagement and knowledge by dispensing information using Consequences Of Security Challenge On Mining How IoT Technology Is Transforming IoT SS. This template helps you present information on five stages. You can also present information on Compromised Smart, Working Conditions, Higher Downtime using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Computer Technology Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Secure Computer Technology Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a visual representation of secure computer. It is a modern, vibrant and eye catching icon that will help to create an impactful presentation. It is a great way to emphasize the importance of data security and safety.
-
 Secure Computer Technology Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Secure Computer Technology Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone PowerPoint Icon is perfect for presentations on secure computer systems. It features a black and white design depicting a computer with a padlock, symbolizing the safety of your data. Use this icon to emphasize the importance of secure computing.
-
 IoT Cyber Security Technologies For Data Improving IoT Device Cybersecurity IoT SS
IoT Cyber Security Technologies For Data Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase various types of Internet of Things IoT security technologies which can assist companies in safeguarding customer data. Blockchain, IoT security analytics, Zero Trust Architecture, and Edge Computing are the most trending technologies which are outlined in slide. Increase audience engagement and knowledge by dispensing information using IoT Cyber Security Technologies For Data Improving IoT Device Cybersecurity IoT SS. This template helps you present information on four stages. You can also present information on Devices, Architecture, Computing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Financial Technology Services AI Image PowerPoint Presentation PPT ECS
Secure Financial Technology Services AI Image PowerPoint Presentation PPT ECSIntroducing a Visual PPT on Secure Financial Technology Services. Our Presentation Specialists have taken great care in designing each slide in this PowerPoint. Feel free to tailor the content. The PPT Template fits well with any screen size, and its also compatible with Google Slides. Download the PPT, and present it confidently.
-
 Improving Security By Green Computing Technology Green IT
Improving Security By Green Computing Technology Green ITThis slide outlines how green computing can improve security. The purpose of this slide is to showcase the pillars of data security, security concerns and solution, and different antivirus software that can help users to protect their computers and networks. Deliver an outstanding presentation on the topic using this Improving Security By Green Computing Technology Green IT. Dispense information and present a thorough explanation of Technology, Computing, Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 5G Security Technologies To Overcome Threats
5G Security Technologies To Overcome ThreatsThis slide shows 5G network technologies to overcome threats in network. It further includes dos attacks, hijacking attacks, user identity theft, scanning attacks, timings attacks and boundary attacks. Introducing our 5G Security Technologies To Overcome Threats set of slides. The topics discussed in these slides are Hijacking Attacks, Dos Attacks. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Technology Market Overview Modern Technologies
Cyber Security Technology Market Overview Modern TechnologiesThis slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028.Present the topic in a bit more detail with this Cyber Security Technology Market Overview Modern Technologies. Use it as a tool for discussion and navigation on Business Continuity,Cybersecurity Measures,Manufacturing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Need For Cyber Security Technology Modern Technologies
Need For Cyber Security Technology Modern TechnologiesThis slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed.Deliver an outstanding presentation on the topic using this Need For Cyber Security Technology Modern Technologies. Dispense information and present a thorough explanation of Confidentiality,Integrity,Availability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
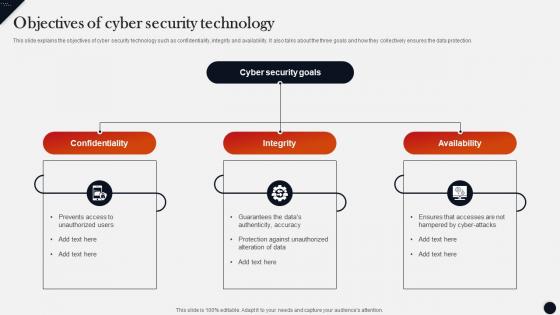 Objectives Of Cyber Security Technology Modern Technologies
Objectives Of Cyber Security Technology Modern TechnologiesThis slide explains the objectives of cyber security technology such as confidentiality,integrity and availability. It also talks about the three goals and how they collectively ensures the data protection.Introducing Objectives Of Cyber Security Technology Modern Technologies to increase your presentation threshold. Encompassed with three stages,this template is a great option to educate and entice your audience. Dispence information on Entertainment Gaming,Hardware Components,Sensors Such,using this template. Grab it now to reap its full benefits.
-
 Technological Trends Used For Enhancing Information Security Management
Technological Trends Used For Enhancing Information Security ManagementThis slide represents various technologies that help organizations enhance information security management and reduce data loss incidents. It includes strategies such as user behavior analytics, cloud access security brokers, etc. Presenting our well structured Technological Trends Used For Enhancing Information Security Management. The topics discussed in this slide are Security Testing Devops, User Behavior Analytics, Cloud Access Security Brokers. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
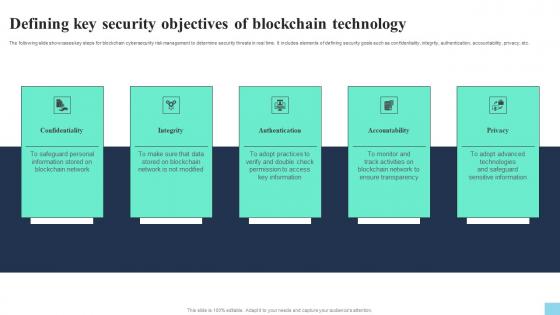 Defining Key Security Objectives Of Blockchain Technology Hands On Blockchain Security Risk BCT SS V
Defining Key Security Objectives Of Blockchain Technology Hands On Blockchain Security Risk BCT SS VThe following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Increase audience engagement and knowledge by dispensing information using Defining Key Security Objectives Of Blockchain Technology Hands On Blockchain Security Risk BCT SS V. This template helps you present information on five stages. You can also present information on Confidentiality, Integrity, Authentication using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Hackers Attack Blockchain Technology Hands On Blockchain Security Risk BCT SS V
How Hackers Attack Blockchain Technology Hands On Blockchain Security Risk BCT SS VThe following slide showcases how hackers attacks blockchain technology to protect key information and mange threats. It includes elements such as false transactions, private keys, hampering network nodes, fake cryptocurrencies, personal information, etc. Introducing How Hackers Attack Blockchain Technology Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Modify Data, Swindles Private, System Accessibility, using this template. Grab it now to reap its full benefits.
-
 Importance Of Cybersecurity In Blockchain Technology Hands On Blockchain Security Risk BCT SS V
Importance Of Cybersecurity In Blockchain Technology Hands On Blockchain Security Risk BCT SS VThe following slide highlights how blockchain cybersecurity is important to boost security and prevent cyberattacks. It includes elements such as decentralized architecture, immutable records, public key cryptography, smart contracts, etc. Introducing Importance Of Cybersecurity In Blockchain Technology Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Decentralized Architecture, Public Key Cryptography, Smart Contracts, using this template. Grab it now to reap its full benefits.
-
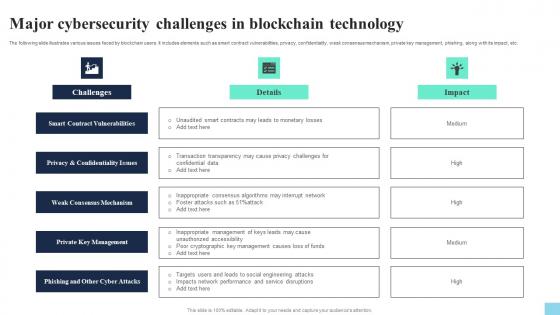 Major Cybersecurity Challenges In Blockchain Technology Hands On Blockchain Security Risk BCT SS V
Major Cybersecurity Challenges In Blockchain Technology Hands On Blockchain Security Risk BCT SS VThe following slide illustrates various issues faced by blockchain users. It includes elements such as smart contract vulnerabilities, privacy, confidentiality, weak consensus mechanism, private key management, phishing, along with its impact, etc. Introducing Major Cybersecurity Challenges In Blockchain Technology Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Smart Contract Vulnerabilities, Weak Consensus Mechanism, Private Key Management, using this template. Grab it now to reap its full benefits.
-
 Overview And Workflow Of Blockchain Cybersecurity Technology Hands On Blockchain Security Risk BCT SS V
Overview And Workflow Of Blockchain Cybersecurity Technology Hands On Blockchain Security Risk BCT SS VThe following slide showcases brief introduction of blockchain security to minimize frauds and attacks. It includes elements such as risk management strategies, assurance offerings, workflow of blockchain, validating transactions, etc. Increase audience engagement and knowledge by dispensing information using Overview And Workflow Of Blockchain Cybersecurity Technology Hands On Blockchain Security Risk BCT SS V. This template helps you present information on seven stages. You can also present information on Transaction Requested, Created Transaction, Existing Blockchain using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of Phishing Attack In Blockchain Technology Hands On Blockchain Security Risk BCT SS V
Overview Of Phishing Attack In Blockchain Technology Hands On Blockchain Security Risk BCT SS VThe following slide illustrates brief introduction of phishing attacks impacting Blockchain to minimize theft of user data. It includes elements such as sharing personal information, sending fake links through emails, stealing private keys, gaining access to account details, data breach, etc. Increase audience engagement and knowledge by dispensing information using Overview Of Phishing Attack In Blockchain Technology Hands On Blockchain Security Risk BCT SS V. This template helps you present information on five stages. You can also present information on Fake Links, Investment Opportunities, Towards Fake Website using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Network Security Audit Technology Icon
Cyber Network Security Audit Technology IconPresenting our set of slides with Cyber Network Security Audit Technology Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Network Security, Audit Technology Icon.
-
 NEO Banks For Digital Funds Biometric Technology For Enhancing Mobile Banking Security Fin SS V
NEO Banks For Digital Funds Biometric Technology For Enhancing Mobile Banking Security Fin SS VThis slide shows information which can be used by organizations to get insights about biometric technology growth in mobile banking. It includes details about process and types of biometric data. Introducing NEO Banks For Digital Funds Biometric Technology For Enhancing Mobile Banking Security Fin SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Biometric Technology, Mobile Banking Security, Biometric Data, Facial Recognition, using this template. Grab it now to reap its full benefits.
-
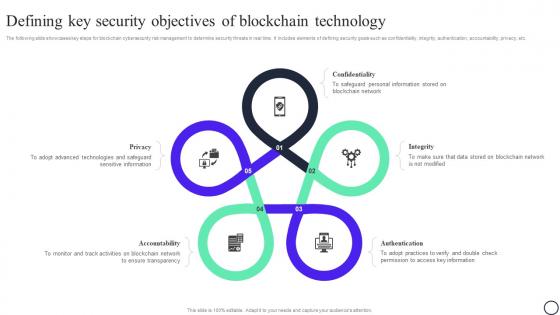 Blockchain And Cybersecurity Defining Key Security Objectives Of Blockchain Technology BCT SS V
Blockchain And Cybersecurity Defining Key Security Objectives Of Blockchain Technology BCT SS VThe following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Increase audience engagement and knowledge by dispensing information using Blockchain And Cybersecurity Defining Key Security Objectives Of Blockchain Technology BCT SS V This template helps you present information on Five stages. You can also present information on Privacy, Confidentiality, Integrity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Application Of Crime Prevention Technology In Security Force
Application Of Crime Prevention Technology In Security ForceThis slide showcases the various use cases in crime prevention in police force. Its purpose is to understand the SOFT and HARD technology uses. This slide includes crime prevention, police, cctv camera, threat assessment, bio- metric, crime mapping, etc. Introducing our Application Of Crime Prevention Technology In Security Force set of slides. The topics discussed in these slides are Crime Prevention, Technology, Security Force This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
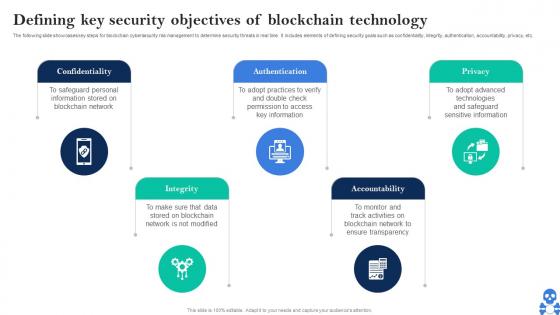 Cyber Threats In Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS V
Cyber Threats In Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS VThe following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Introducing Cyber Threats In Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Integrity, Authentication using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Technologies Used In Firewall Network Protection
Firewall Network Security Technologies Used In Firewall Network ProtectionThis slide gives an overview of the technologies used in firewall mechanisms. The purpose of this slide is to showcase the different technologies and techniques used in firewalls to protect a network, such as real-time monitoring, proxy servers, virtual private network, network address translation, and so on. Introducing Firewall Network Security Technologies Used In Firewall Network Protection to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Packet Filters, Proxy Servers, Virtual Private Network using this template. Grab it now to reap its full benefits.
-
 Current Trending Technologies Cyber Security Technology Market Overview
Current Trending Technologies Cyber Security Technology Market OverviewThis slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Deliver an outstanding presentation on the topic using this Current Trending Technologies Cyber Security Technology Market Overview. Dispense information and present a thorough explanation of Cyber Security Technology, Market Growth, Compound Annual Growth Rate, Business Continuity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Current Trending Technologies Need For Cyber Security Technology
Current Trending Technologies Need For Cyber Security TechnologyThis slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Increase audience engagement and knowledge by dispensing information using Current Trending Technologies Need For Cyber Security Technology. This template helps you present information on three stages. You can also present information on Cyber Security Technology, Prevention Of Cybercrime, Protection Of Sensitive Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Current Trending Technologies Objectives Of Cyber Security Technology
Current Trending Technologies Objectives Of Cyber Security TechnologyThis slide explains the objectives of cyber security technology such as confidentiality, integrity and availability. It also talks about the three goals and how they collectively ensures the data protection. Introducing Current Trending Technologies Objectives Of Cyber Security Technology to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Cyber Security Technology, Data Protection, Integrity And Availability, using this template. Grab it now to reap its full benefits.
-
 New Technologies Cyber Security Technology Market Overview
New Technologies Cyber Security Technology Market OverviewThis slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Present the topic in a bit more detail with this New Technologies Cyber Security Technology Market Overview. Use it as a tool for discussion and navigation on Technology, Overview, Cyber Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 New Technologies Need For Cyber Security Technology
New Technologies Need For Cyber Security TechnologyThis slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Deliver an outstanding presentation on the topic using this New Technologies Need For Cyber Security Technology. Dispense information and present a thorough explanation of Technology, Information, Protecting using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
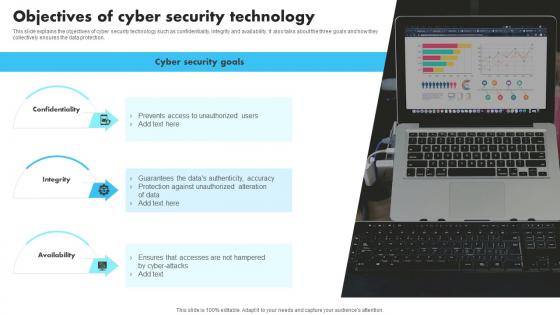 New Technologies Objectives Of Cyber Security Technology
New Technologies Objectives Of Cyber Security TechnologyThis slide explains the objectives of cyber security technology such as confidentiality, integrity and availability. It also talks about the three goals and how they collectively ensures the data protection. Introducing New Technologies Objectives Of Cyber Security Technology to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Technology, Availability, using this template. Grab it now to reap its full benefits.
-
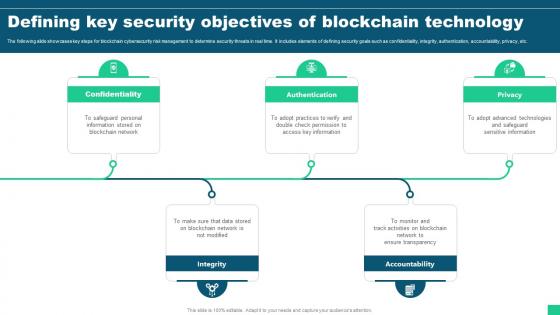 Defining Key Security Objectives Of Blockchain Technology Guide For Blockchain BCT SS V
Defining Key Security Objectives Of Blockchain Technology Guide For Blockchain BCT SS VThe following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Introducing Defining Key Security Objectives Of Blockchain Technology Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Authentication, Integrity, Accountability using this template. Grab it now to reap its full benefits.
-
 Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age It
Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age ItThe purpose of this slide is to explain the role of HTTPS in encrypting web communication and use of the Secure Sockets Layer SSL protocol for secure connections. This slide also discusses the incorporation of symmetric and asymmetric encryption during the SSL handshake. Deliver an outstanding presentation on the topic using this Secure Socket Layer Ssl Security Technology Encryption For Data Privacy In Digital Age It. Dispense information and present a thorough explanation of Technology, Asymmetric, Symmetric using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Drone Technology Icon For Security Surveillance
Drone Technology Icon For Security SurveillancePresenting our well structured Drone Technology Icon For Security Surveillance. The topics discussed in this slide are Drone Technology Icon, Security Surveillance. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Ai And Machine Learning Technology IoT Security And Privacy Safeguarding IoT SS
Ai And Machine Learning Technology IoT Security And Privacy Safeguarding IoT SSThis slide showcases the application of artificial intelligence and machine learning technology in enhancing IoT security. It includes applications such as threat detection, access control, vulnerability detection, and predictive maintenance. Deliver an outstanding presentation on the topic using this Ai And Machine Learning Technology IoT Security And Privacy Safeguarding IoT SS. Dispense information and present a thorough explanation of Threat Detection, Access Control, Vulnerability Detection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Case Study 1 Enhancing Operational Technology IoT Security And Privacy Safeguarding IoT SS
Case Study 1 Enhancing Operational Technology IoT Security And Privacy Safeguarding IoT SSThis slide includes a case study of the company providing operational digital safety solutions integrating Cisco technology to enhance visibility at scale. It includes elements such as objectives of company , solutions implemented, and results. Introducing Case Study 1 Enhancing Operational Technology IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Operational Technology, Identify Service Engine, Security Posture, using this template. Grab it now to reap its full benefits.
-
 Emerging Technologies Enhancing IoT Security And IoT Security And Privacy Safeguarding IoT SS
Emerging Technologies Enhancing IoT Security And IoT Security And Privacy Safeguarding IoT SSThis slide includes key technologies integrated with IoT ecosystem that helps to tackle cyberattacks and resolve any other issues. It includes technologies such as blockchain technology, artificial intelligence and machine learning and quantum computing.Present the topic in a bit more detail with this Emerging Technologies Enhancing IoT Security And IoT Security And Privacy Safeguarding IoT SS. Use it as a tool for discussion and navigation on Transactions Securely, Identity Management, Predictive Maintenance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Implications For Face Recognition Technology
Security Implications For Face Recognition TechnologyThe slide aims to explain the advanced architecture of a face recognition system, optimizing accuracy and performance for robust facial identification. Presenting our set of slides with Security Implications For Face Recognition Technology. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Authentication Security, Spoofing Protection, Encryption.
-
 Working And Architecture Of Firewall Security Technology Firewall Virtualization
Working And Architecture Of Firewall Security Technology Firewall VirtualizationThis slide demonstrates the architecture and working of traditional firewalls. The purpose of this slide is to illustrate the firewall architecture and working. The main components include corporate network, operation network and control system network. Deliver an outstanding presentation on the topic using this Working And Architecture Of Firewall Security Technology Firewall Virtualization. Dispense information and present a thorough explanation of Firewall Architecture, Corporate Network, Control System Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Of Firewall As A Service Security Technology Firewall Virtualization
Working Of Firewall As A Service Security Technology Firewall VirtualizationThis slide illustrates the working of Firewall-as-a-service technology. The purpose of this slide is to outline various actions performed by FWaaS such as Intrusion Prevention Systems, DNS security, etc. Main components include accept, drop and block. Increase audience engagement and knowledge by dispensing information using Working Of Firewall As A Service Security Technology Firewall Virtualization. This template helps you present information on five stages. You can also present information on Public Internet, Corporate Network, Companys Architecture using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Internet Gateway Security IT Future Of Secure Web Gateway Technology
Internet Gateway Security IT Future Of Secure Web Gateway TechnologyThis slide talks about the future of Secure Web Gateway security technology. The purpose of this slide is to explain how SWG can lead the cyber security market in future as more businesses are migrating to the cloud. Introducing Internet Gateway Security IT Future Of Secure Web Gateway Technology to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Sales Are Predicted, SWG Market Anticipated, Security Solution, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Introduction To Secure Web Gateway Technology
Internet Gateway Security IT Introduction To Secure Web Gateway TechnologyThis slide talks about the network security solution called Secure Web Gateway. The purpose of this slide is to outline the various benefits of SWG. This slide also represents different working components of SWG such as traffic inspection, malware protection, etc. Introducing Internet Gateway Security IT Introduction To Secure Web Gateway Technology to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Traffic Inspection, Application Control, Website Content Inspection, Data Loss Prevention, using this template. Grab it now to reap its full benefits.
-
 Everything About Commercial Banking Biometric Technology For Enhancing Online Security Fin SS V
Everything About Commercial Banking Biometric Technology For Enhancing Online Security Fin SS VThis slide shows information which can be used by organizations to get insights about use of biometric technology growth in commercial banking. It includes details about process and types of biometric data. Increase audience engagement and knowledge by dispensing information using Everything About Commercial Banking Biometric Technology For Enhancing Online Security Fin SS V. This template helps you present information on one stages. You can also present information on Biometric Technology, Enhancing Online Security, Commercial Banking, Data Is Encrypted using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Technologies Used In Web Security Solutions
Technologies Used In Web Security SolutionsThis slide highlights the different technologies utilized in web security approach which includes firewall, Content Security Policy CSP, etc. Presenting our set of slides with name Technologies Used In Web Security Solutions. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Regulates Traffic, Intrusion Detection System, Content Security Policy.
-
 Emerging Technologies Associated With Wireless Internet Security
Emerging Technologies Associated With Wireless Internet SecurityThe following slide outlines emerging technologies, potential future threats, and security implications and opportunities, offering insights into evolving trends in wireless internet security for organizational planning and preparedness. Presenting our set of slides with Emerging Technologies Associated With Wireless Internet Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Technologies, Associated, Considerations.





