Powerpoint Templates and Google slides for Security Technologies
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Impact Of Emerging Technologies On Information Security
Impact Of Emerging Technologies On Information SecurityThis slide highlights influence of technology on information security. The purpose of this slide is to assist IT teams in assessing and measuring various factors for driving success of security initiatives. It includes elements such as zero trust architecture, IoT security, etc.Introducing our Impact Of Emerging Technologies On Information Security set of slides. The topics discussed in these slides are Artificial Intelligence, Zero Trust Architecture, Iot Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Types Of Web Security Technologies To Prevent Cyber Threats
Types Of Web Security Technologies To Prevent Cyber ThreatsThis slide covers various types of web security technologies. The purpose of this slide is to help businesses in preventing cyber threats to ensure business protection and compliance. It covers technologies such as web application firewalls, vulnerability scanners, password cracking technologies, etc. Presenting our set of slides with Types Of Web Security Technologies To Prevent Cyber Threats This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Web Application Firewalls, Vulnerability Scanners, Password Cracking Technologies
-
 Icon For Ensuring Security By Containerization Technology
Icon For Ensuring Security By Containerization TechnologyPresenting our well structured Icon For Ensuring Security By Containerization Technology. The topics discussed in this slide are Icon, Ensuring Security, Containerization Technology. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Strategies For Implementing AI Powered Global Technology In Cyber Security
Strategies For Implementing AI Powered Global Technology In Cyber SecurityThis slide shows strategic approaches for implementing AI in cyber security. The purpose of this slide is to strengthen organizations defence against potential cyber attacks to maximize effectiveness of global technological solutions. It covers strategies such as resource allocation, training data, internal processes, etc. Presenting our set of slides with Strategies For Implementing AI Powered Global Technology In Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Resource Allocation, Training Data, Internal Processes.
-
 Endpoint Security Emerging Trends And Technologies In Endpoint Security
Endpoint Security Emerging Trends And Technologies In Endpoint SecurityThis slide outlines the technologies and trends in end point security with involvement of technologies such as Artificial Intelligence AI, ML, etc. Increase audience engagement and knowledge by dispensing information using Endpoint Security Emerging Trends And Technologies In Endpoint Security. This template helps you present information on four stages. You can also present information on Emerging Trends, Technologies In Endpoint Security, Artificial Intelligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Big Data Analytics Technologies In Cyber Security
Big Data Analytics Technologies In Cyber SecurityThis slide showcases cyber security technologies in big data analytics. This includes encryptions, user access control and centralizsed key management systems. Presenting our set of slides with name Big Data Analytics Technologies In Cyber Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Big Data Analytics, Centralized Key Management, Technologies In Cyber Security.
-
 Advanced Technologies In Automotive Sector For Cyber Security Management
Advanced Technologies In Automotive Sector For Cyber Security ManagementFollowing slide exhibits embedded advanced software and tools used by automotive manufacturer for securing embedded systems against cyber-attacks. It includes gateways, body electronics, dashboard, connected car, hybrid electric vehicle, powertrain and chassis, etc. Presenting our set of slides with Advanced Technologies In Automotive Sector For Cyber Security Management. This exhibits information on ten stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Advanced Driver Assistance System, Hybrid Electric Vehicle, Connected Car.
-
 Icon For Role Of 5g Technology In Automotive Cyber Security
Icon For Role Of 5g Technology In Automotive Cyber SecurityIntroducing our premium set of slides with Icon For Role Of 5g Technology In Automotive Cyber Security Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon For Role, 5G Technology In Automotive, Cyber Security So download instantly and tailor it with your information.
-
 Tokenization For Improved Data Security Difference Between Tokenization And Masking Technology
Tokenization For Improved Data Security Difference Between Tokenization And Masking TechnologyThis slide represents the comparison between tokenization and masking. The purpose of this slide is to represent a comparative analysis on the basis of various components such as process, purpose, use cases, etc. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Difference Between Tokenization And Masking Technology. Dispense information and present a thorough explanation of Data Preservation, Masking Technology, Maintains Data Format using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Tokenization For Improved Data Security Future Trends Of Tokenization On Business And Technology
Tokenization For Improved Data Security Future Trends Of Tokenization On Business And TechnologyThis slide highlights the anticipated developments in tokenizations impact on the realms of business and technology. The purpose of this slide is to outline the future trends of tokenization. Introducing Tokenization For Improved Data Security Future Trends Of Tokenization On Business And Technology to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Anticipated Developments, Business And Technology, Future Trends Of Tokenization, using this template. Grab it now to reap its full benefits.
-
 Tokenization For Improved Data Security Regulations Of Security Tokens In Blockchain Technology
Tokenization For Improved Data Security Regulations Of Security Tokens In Blockchain TechnologyThis slide discusses the regulations of security tokens for data security. The purpose of this slide is to showcase various security token regulations which include D, A plus, S regulations, etc. Introducing Tokenization For Improved Data Security Regulations Of Security Tokens In Blockchain Technology to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Regulations Of Security Tokens, Blockchain Technology, Data Security, using this template. Grab it now to reap its full benefits.
-
 Evolution Of Technological SIEM Cyber Security
Evolution Of Technological SIEM Cyber SecurityThis slide showcases the evolution of technology SIEM cyber security. Its aim is to set rule and awareness for threat data management. This slide includes machine learning, risk management, rules, event, etc. Presenting our set of slides with name Evolution Of Technological SIEM Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Early 2000s, Mid 2000s, Late 2000s.
-
 Common Security Types In Blockchain Technology
Common Security Types In Blockchain TechnologyPresenting our set of slides with Common Security Types In Blockchain Technology. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Public Blockchain, Hybrid Blockchain, Restricted Access.
-
 Cyber Security Attacks In Blockchain Technology
Cyber Security Attacks In Blockchain TechnologyPresenting our set of slides with Cyber Security Attacks In Blockchain Technology. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Interception, Floods Networks, False Identities.
-
 Icon For Blockchain Technology In Cyber Security
Icon For Blockchain Technology In Cyber SecurityPresenting our well structured Icon For Blockchain Technology In Cyber Security. The topics discussed in this slide are Icon, Blockchain Technology, Cyber Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Structural Design Of Blockchain Technology On Security Threats
Structural Design Of Blockchain Technology On Security ThreatsIntroducing our Structural Design Of Blockchain Technology On Security Threats set of slides. The topics discussed in these slides are Application Layer, Contract Layer, Incentive Layer. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ai Technology Implementation Icon For Robust OT Cyber Security
Ai Technology Implementation Icon For Robust OT Cyber SecurityPresenting our set of slides with Ai Technology Implementation Icon For Robust OT Cyber Security This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on AI Technology Implementation Icon, Robust OT Cyber Security
-
 Identity And Access Management Technologies And Tools Securing Systems With Identity
Identity And Access Management Technologies And Tools Securing Systems With IdentityThis slide discusses the tools and technologies used in the Identity and Access Management process. The purpose of this slide is to highlight the various tools, which are security assertion markup language, open ID connect, and a system for cross-domain identity management. Present the topic in a bit more detail with this Identity And Access Management Technologies And Tools Securing Systems With Identity Use it as a tool for discussion and navigation on Saml, Oidc, Scim This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technology Integration For Security Operations Center
Technology Integration For Security Operations CenterThe below slide provides a technological integration architecture for security operation center that helps to understand the various technology used for threat identification and mitigation. The various technologies are cloud, network sensors, etc. Introducing our premium set of slides with name Technology Integration For Security Operations Center. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Analysis, SIEM, Intrusion Activity. So download instantly and tailor it with your information.
-
 Technology Trends And Impact Of Security Operations Center
Technology Trends And Impact Of Security Operations CenterThe following slide represents the technological trends of security operations center along with their impact on security. The various trends are rise in adoption of cloud deployment, increased use of AI and ML, etc. Presenting our set of slides with name Technology Trends And Impact Of Security Operations Center. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Impact, MDR Security Assessment.
-
 Tool And Technologies For Security Operations Center
Tool And Technologies For Security Operations CenterThe following slide showcases the various tools that are used in functioning of security operations center for effective monitoring and prevention of threats. The different tools are log collection and management, endpoint detection, etc. Introducing our premium set of slides with name Tool And Technologies For Security Operations Center. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Log Collection And Management, Endpoint Detection And Response. So download instantly and tailor it with your information.
-
 NIDS Technologies To Detect Cyber Security Breach
NIDS Technologies To Detect Cyber Security BreachThis slide represents NIDS equipment used to identify cyber security vulnerabilities. It aims to detect, identify, and respond to security breaches and threats within network to mitigate risks. Introducing our premium set of slides with NIDS Technologies To Detect Cyber Security Breach. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Protocols, Applications, Operating Systems. So download instantly and tailor it with your information.
-
 NFC Technology Risks Associated With Mobile Security Mobile Security
NFC Technology Risks Associated With Mobile Security Mobile SecurityThis slide discusses the NFC technology risks associated with mobile security which includes data tampering, data interception, smartphone malware, etc. Increase audience engagement and knowledge by dispensing information using NFC Technology Risks Associated With Mobile Security Mobile Security This template helps you present information on Five stages. You can also present information on Installing Patches, Add Features, Systems Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Methods To Ensure Data Security And Privacy In Biochip Technology Shaping The Future TC SS
Methods To Ensure Data Security And Privacy In Biochip Technology Shaping The Future TC SSIncrease audience engagement and knowledge by dispensing information using Methods To Ensure Data Security And Privacy In Biochip Technology Shaping The Future TC SS. This template helps you present information on three stages. You can also present information on Security Protocols, Authorized Access, Responsible Data Use using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices For Secure Embedded Systems Mastering Embedded Systems Technology
Best Practices For Secure Embedded Systems Mastering Embedded Systems TechnologyThis slide showcases the best methods for developing secure embedded systems. The purpose of this slide is to showcase the best practices for building secure embedded systems, and these are securing boot, securing enclaves with Trusted Execution Environments TEE, implementing FOTA, etc. Present the topic in a bit more detail with this Best Practices For Secure Embedded Systems Mastering Embedded Systems Technology. Use it as a tool for discussion and navigation on Operating Systems In Market, Consumer Electronics, Industrial, Agriculture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Challenges In Maintaining Security Of Embedded Systems Mastering Embedded Systems Technology
Challenges In Maintaining Security Of Embedded Systems Mastering Embedded Systems TechnologyThis slide showcases the various security challenges and mitigation methods for embedded systems. The purpose of this slide is to represent the challenges in maintaining the security of embedded systems, such as irregular security updates, attack replication, dependability, and so on. Deliver an outstanding presentation on the topic using this Challenges In Maintaining Security Of Embedded Systems Mastering Embedded Systems Technology. Dispense information and present a thorough explanation of Irregular Security Updates, Dependability, Industrial Protocols, Remote Deployment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Develop Secure Embedded Systems Mastering Embedded Systems Technology
Checklist To Develop Secure Embedded Systems Mastering Embedded Systems TechnologyThis slide outlines the checklist for building secure embedded systems. The purpose of this slide is to showcase the various tasks that need to be performed to develop secure embedded systems, required actions, responsible person, and status. Present the topic in a bit more detail with this Checklist To Develop Secure Embedded Systems Mastering Embedded Systems Technology. Use it as a tool for discussion and navigation on Operating System Selection, Processor And Peripherals, Prototype Development, System Architecture Design. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Technology Strategies For Fintech Cyber Security
Best Technology Strategies For Fintech Cyber SecurityThis slide showcases the best technologies to choose for fintech security management. Its aim is to prioritise the resources and execute the best strategy. This slide includes governance, risk, crisis, service, threat, access, privacy, etc. Presenting our set of slides with name Best Technology Strategies For Fintech Cyber Security. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Governance Strategy, Emerging Trends, Risk Compliance, Crisis Management .
-
 Fast Evolving Fintech Cyber Security Technologies
Fast Evolving Fintech Cyber Security TechnologiesThis slide showcases the fast evolving fintech cyber security technologies. Its aim is to ward off different threats to protect fintech. This slide includes cyber crime, employees, application, financial compliance, organisational strategy and vendors. Presenting our well structured Fast Evolving Fintech Cyber Security Technologies. The topics discussed in this slide are Financial Compliance, Organisational Strategy, Vendor Information. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Email Security Best Practices Recent Trends In Email Security Technologies
Email Security Best Practices Recent Trends In Email Security TechnologiesThis slide discusses the latest trends in the field of email security advancements. The key components of this slide are machine learning and artificial intelligence, cloud-based email security, zero-trust security and advanced threat protection. Introducing Email Security Best Practices Recent Trends In Email Security Technologies to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Machine Learning And Artificial Intelligence, Cloud-Based Email Security, Zero-Trust Security, Advanced Threat Protection, using this template. Grab it now to reap its full benefits.
-
 Organizational Information Technology Security Budget Analysis
Organizational Information Technology Security Budget AnalysisThis slide provides the budget analysis for development of organizational security by installation of new services. The various cost estimation parameters are new license required, subscription cost, purchase status, etc. Introducing our Organizational Information Technology Security Budget Analysis set of slides. The topics discussed in these slides are Revenue, Security Goal, IT Security Budget. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Organizational Physical Security Technology Infographic
Organizational Physical Security Technology InfographicThe following slide provides the infographic for use of various technologies and gadgets for optimizing the physical security of a premise. The various methods are fire alarms, control sensors, security cameras, etc. Introducing our premium set of slides with Organizational Physical Security Technology Infographic. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Cameras, Smart Doors, Motion Sensor. So download instantly and tailor it with your information.
-
 Organizational Physical Security Technology Trends
Organizational Physical Security Technology TrendsThis slide provides the latest technological trends and developments of physical security in organizations that help to understand the working of devices with technology. The major trends include artificial intelligence, machine learning, etc. Presenting our set of slides with Organizational Physical Security Technology Trends. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on AI And ML, Iot, Cloud Solutions.
-
 IOT Technology Data Security Icon
IOT Technology Data Security IconPresenting our set of slides with name IOT Technology Data Security Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on IoT Technology, Data Security.
-
 IOT Technology Security Layer Architecture
IOT Technology Security Layer ArchitectureThis slide showcases IoT security architecture along with three layers. It includes IoT application and support layer, local area network, core network, access network and perception node. Introducing our IOT Technology Security Layer Architecture set of slides. The topics discussed in these slides are Secure Service, System Security, Secure Connection, Network Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Protection Technologies Used For Web Security Solution
Protection Technologies Used For Web Security SolutionThis slide showcases the tools and technologies utilized, their description, and the cost, for web security in cyber security. Present the topic in a bit more detail with this Protection Technologies Used For Web Security Solution. Use it as a tool for discussion and navigation on Web Application Firewalls, Password-Cracking Tools, Security Or Vulnerability Scanners. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Technology Collaboration Icon
Cloud Security Technology Collaboration IconIntroducing our premium set of slides with Cloud Security Technology Collaboration Icon. Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud Security Technology Partnership Icon. So download instantly and tailor it with your information.
-
 Cyber Security Information Technology List
Cyber Security Information Technology ListThis slide showcases list of cyber security data technology. The purpose of this template is to help businesses in maintaining confidentiality of information systems for building trust of customers in digital age. It includes elements such as firewalls, antivirus, etc. Presenting our set of slides with name Cyber Security Information Technology List. This exhibits information on Eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Firewalls, Intrusion Detection And Prevention Systems, Antivirus, Access Control Systems.
-
 Technology List For Ensuring Security In Telecommunication Sector
Technology List For Ensuring Security In Telecommunication SectorThis slide highlights types of telecommunications security technologies. The purpose of this slide is to aid businesses in safeguarding communications and data transmissions from unauthorized access. It includes elements such as aspect, measure, benefits, applications, etc. Presenting our set of slides with name Technology List For Ensuring Security In Telecommunication Sector. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Aspect, Measure, Benefits, Applications.
-
 Information Technology Network Security Icon
Information Technology Network Security IconIntroducing our premium set of slides with name Information Technology Network Security Icon. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Technology, Network Security. So download instantly and tailor it with your information.
-
 Strategic Information Technology Security Plan
Strategic Information Technology Security PlanThis slide represents strategic plan for information technology security which includes security types such as network security, internet security, endpoint security, etc. Introducing our premium set of slides with name Strategic Information Technology Security Plan. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Purpose, Person Responsible, Actions Required, Status. So download instantly and tailor it with your information.
-
 Threat landscape operational security behavioral analytics technologies
Threat landscape operational security behavioral analytics technologiesIf you require a professional template with great design, then this Threat Landscape Operational Security Behavioral Analytics Technologies is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using nine slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Secure future technology leadership presentation powerpoint
Secure future technology leadership presentation powerpointPowerPoint slides are wholly compatible with Google slides. Presentation designs are available in standard and widescreen view. Access to PPT templates with different nodes and stages. Quickly downloadable presentation design. Adaptable template slides as can be converted into JPEG and PDF format. Useful for technology managers and executives. The stages in this process are expand distribution, secure future technology leadership, optimize productivity infrastructure, executive initiatives.
-
 Cyber security technology skills gap priorities
Cyber security technology skills gap prioritiesThis slide illustrates the top IT security concerns for business managers. It includes data loss prevention, firewalls, access management, cloud security, risk management, legal compliance and predictive analysis. Introducing our Cyber Security Technology Skills Gap Priorities set of slides. The topics discussed in these slides are Cyber Security Technology Skills Gap Priorities. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber threat security industry overview with technology adoption rate
Cyber threat security industry overview with technology adoption rateThis slide highlights the cyber threat security industry overview which illustrates the total malware reported and technology invested. Presenting our well structured Cyber Threat Security Industry Overview With Technology Adoption Rate. The topics discussed in this slide are Technology Investment. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Technology assessment scorecard with device security ppt slides deck
Technology assessment scorecard with device security ppt slides deckThis graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Deliver an outstanding presentation on the topic using this Technology Assessment Scorecard With Device Security Ppt Slides Deck. Dispense information and present a thorough explanation of Compromised, Not Encrypted, Mention Security Feature, Last Seen Overview, Ownership using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Technology assessment scorecard with security incidents ppt slides graphics
Technology assessment scorecard with security incidents ppt slides graphicsThis graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data. Present the topic in a bit more detail with this Technology Assessment Scorecard With Security Incidents Ppt Slides Graphics. Use it as a tool for discussion and navigation on Criminal Activity, Investigation, Denial Service, Data Breach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
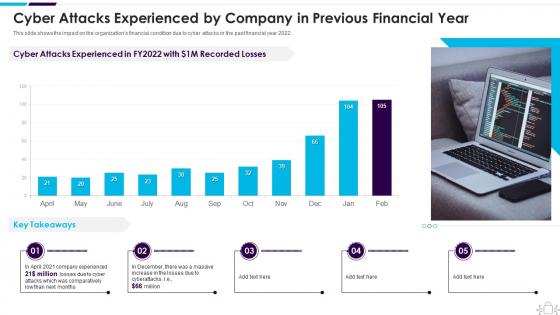 Cyber Attacks Experienced By Company In Previous Information Technology Security
Cyber Attacks Experienced By Company In Previous Information Technology SecurityThis slide shows the impact on the organizations financial condition due to cyber attacks in the past financial year 2022. Present the topic in a bit more detail with this Cyber Attacks Experienced By Company In Previous Information Technology Security. Use it as a tool for discussion and navigation on Experienced, Previous, Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Compliance Dashboard Snapshot For Information Technology Security
Information Technology Security Compliance Dashboard Snapshot For Information Technology SecurityThis slide depicts the cyber security compliance report on how data and hardware are monitored in different categories such as standard, regulation, and asset type control. Present the topic in a bit more detail with this Information Technology Security Compliance Dashboard Snapshot For Information Technology Security. Use it as a tool for discussion and navigation on Dashboard, Information, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Dashboard Snapshot Threat Tracking Information Technology Security
Information Technology Security Dashboard Snapshot Threat Tracking Information Technology SecurityThis slide depicts the dashboard for threat tracking in cyber security by covering monthly threat status, current risk status, threat-based on the role, threats by owners, risk by threats, and threat report. Present the topic in a bit more detail with this Information Technology Security Dashboard Threat Tracking Information Technology Security. Use it as a tool for discussion and navigation on Dashboard, Information, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Detail Impact Information Technology Reduce Organization
Information Technology Security Detail Impact Information Technology Reduce OrganizationThis slide represents the current status of the cyber attacks in an organization after implementing the cyber security model. Present the topic in a bit more detail with this Information Technology Security Detail Impact Information Technology Reduce Organization. Use it as a tool for discussion and navigation on Information, Technology, Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Highest Number Of Malware Attacks In Departments
Information Technology Security Highest Number Of Malware Attacks In DepartmentsThis slide shows the status of malware attacks on different departments such as IT, development, accounts, and HR in the organization for the FY2022 year. Present the topic in a bit more detail with this Information Technology Security Highest Number Of Malware Attacks In Departments. Use it as a tool for discussion and navigation on Department, Experienced, Malware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Impact Organization After Implementing Strategy Training
Information Technology Security Impact Organization After Implementing Strategy TrainingThis slide depicts the impact of cyber security training on an organization. It also shows how trained employees can reduce cyber attacks in the organization. Present the topic in a bit more detail with this Information Technology Security Impact Organization After Implementing Strategy Training. Use it as a tool for discussion and navigation on Organization, Implementing, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Prepare And Deploy Strong It Policies
Information Technology Security Prepare And Deploy Strong It PoliciesThis slide represents the value of having strong IT policies within an organization regarding software, hardware, passwords, and data transfer. Deliver an outstanding presentation on the topic using this Information Technology Security Prepare And Deploy Strong It Policies. Dispense information and present a thorough explanation of Prepare And Deploy Strong IT Policies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Problems Faced By The Organization
Information Technology Security Problems Faced By The OrganizationThis slide shows the organizations current situation through the total losses in millions experienced because of different cyberattacks. Present the topic in a bit more detail with this Information Technology Security Problems Faced By The Organization. Use it as a tool for discussion and navigation on Problems Faced By The Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Requirement Of Information Technology Security In Different Sectors
Information Technology Security Requirement Of Information Technology Security In Different SectorsThis slide depicts the requirement of cyber security in different sectors and the percentage of attacks experienced in the medical, govt, military, and corporate sectors in the past 12 months. Deliver an outstanding presentation on the topic using this Information Technology Security Requirement Of Information Technology Security In Different Sectors. Dispense information and present a thorough explanation of Requirement, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Update And Installation Of Antivirus Software
Information Technology Security Update And Installation Of Antivirus SoftwareThis slide depicts the benefits of using antivirus software in the organization, different antivirus software available in the market, and their usage by a graph. Deliver an outstanding presentation on the topic using this Information Technology Security Update And Installation Of Antivirus Software. Dispense information and present a thorough explanation of Update And Installation Of Antivirus Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Dashboard With Incident And Threat Management
Information Technology Security Dashboard With Incident And Threat ManagementThis slide shows the dashboard of cyber security with incidents and threat management. It includes overall progress, risk identified , number of critical incidents, initiative , incident and threat management etc. Introducing our Information Technology Security Dashboard With Incident And Threat Management set of slides. The topics discussed in these slides are Threat Management, Incident Management, Critical Risks Identified. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Quarterly Comparison Of Information Technology Security Threats
Quarterly Comparison Of Information Technology Security ThreatsThis slide shows the four types of security threats occurred during four quarters. It includes phishing, malware, IoT and password attacks. Introducing our Quarterly Comparison Of Information Technology Security Threats set of slides. The topics discussed in these slides are Quarterly Comparison, Information Technology, Security Threats. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 F652 Security Automation In Information Technology Security Automation Dashboard Highlighting Phishing
F652 Security Automation In Information Technology Security Automation Dashboard Highlighting PhishingThis slide highlights the dashboard for security automation which includes total automations performed, hours saved, cost savings, records created, automation ratio, incidents by group and incident timeline. Present the topic in a bit more detail with this F652 Security Automation In Information Technology Security Automation Dashboard Highlighting Phishing. Use it as a tool for discussion and navigation on Automation, Dashboard, Phishing Alerts. This template is free to edit as deemed fit for your organization. Therefore download it now.





