Powerpoint Templates and Google slides for Security Model
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 SD WAN Model Comparison Between Secure Access Service Edge And Sd Wan
SD WAN Model Comparison Between Secure Access Service Edge And Sd WanThis slide compares secure access service edge and software-defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD-WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Present the topic in a bit more detail with this SD WAN Model Comparison Between Secure Access Service Edge And Sd Wan. Use it as a tool for discussion and navigation on Deployment And Architecture, Traffic And Connectivity, Security, Secure Access Service Edge. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Firewall As A Service Fwaas Working And Security Features
SD WAN Model Firewall As A Service Fwaas Working And Security FeaturesThis slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, and IP mapping. Introducing SD WAN Model Firewall As A Service Fwaas Working And Security Features to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Packet Filtering, Internet Protocol Mapping, Network Monitoring, Deep Packet Inspection, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Introduction To Secure Access Service Edge Sase
SD WAN Model Introduction To Secure Access Service Edge SaseThis slide represents the introduction of SASE cloud security technology. The purpose of this slide is to demonstrate the core capabilities, benefits and key components of SASE. The key components include SD-WAN, FWaaS, ZTNA, CASB, SWG, and unified management. Present the topic in a bit more detail with this SD WAN Model Introduction To Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Software Defined Wan, Firewall As A Service, Zero Trust Network Access, Cloud Access Security Broker. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Pillars Of Cloud Access Security Broker Ppt Icon Design Ideas
SD WAN Model Pillars Of Cloud Access Security Broker Ppt Icon Design IdeasThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Increase audience engagement and knowledge by dispensing information using SD WAN Model Pillars Of Cloud Access Security Broker Ppt Icon Design Ideas. This template helps you present information on four stages. You can also present information on Cloud Access Security Broker, Compliance, Visibility, Threat Protection, Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Roadmap To Implement Secure Access Service Edge
SD WAN Model Roadmap To Implement Secure Access Service EdgeThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Introducing SD WAN Model Roadmap To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Regularly, Transition, Troubleshooting And Assistance, Secure Access Service Edge, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Secure Access Service Edge Architecture Characteristics
SD WAN Model Secure Access Service Edge Architecture CharacteristicsThis slide represents the architectural characteristics of a secure access service edge. The purpose of this slide is to showcase the features of SASE architecture that include identity-driven, cloud-native, support for all edges, and global distribution. Introducing SD WAN Model Secure Access Service Edge Architecture Characteristics to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure Access Service Edge, Architecture Characteristics, Cloud Native, Global Distribution, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Secure Access Service Edge Implementation Steps
SD WAN Model Secure Access Service Edge Implementation StepsThis slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD-WAN backbone, incorporating zero-trust solutions, etc. Increase audience engagement and knowledge by dispensing information using SD WAN Model Secure Access Service Edge Implementation Steps. This template helps you present information on five stages. You can also present information on Incorporate Zero Trust Solutions, Test And Troubleshoot, Secure Access Service Edge, Infrastructure Gaps using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Secure Access Service Edge Importance
SD WAN Model Secure Access Service Edge ImportanceThis slide represents the importance of secure access service edge. This slides purpose is to demonstrate why businesses need the SASE model. The main reasons include scaling with business needs, encouraging work from anywhere environment, standing up for cyber threats, and offering a base for IoT adoption. Introducing SD WAN Model Secure Access Service Edge Importance to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Scales With Business, Encourage Work From Anywhere, Network And Security, Compromising Business Security, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Secure Access Service Edge Sase Architecture
SD WAN Model Secure Access Service Edge Sase ArchitectureThis slide represents the SASE architecture overview and its goals. The purpose of this slide is to demonstrate the secure access service edge architecture and its goals. The building blocks of SASE architecture include SWG, CASB, ZTNA, FWaaS, SD-WAN, Thin Edge, and so on. Deliver an outstanding presentation on the topic using this SD WAN Model Secure Access Service Edge Sase Architecture. Dispense information and present a thorough explanation of Secure Access Service Edge, Architecture And Its Goals, Geographic Distribution using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Secure Access Service Edge Training Program
SD WAN Model Secure Access Service Edge Training ProgramThis slide represents the training program for the secure access service edge model. The purpose of this slide is to demonstrate the teams eligible for training, the modules to be covered during the training, the schedule and venue of the training. Present the topic in a bit more detail with this SD WAN Model Secure Access Service Edge Training Program. Use it as a tool for discussion and navigation on Training Program, Secure Access Service Edge, Teams Eligible For Training, Modules To Be Covered. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Secure Access Service Edge Use Cases
SD WAN Model Secure Access Service Edge Use CasesThis slide represents the use cases of secure access service edge within an organization. The purpose of this slide is to demonstrate the various use cases of the SASE model, including rapid response to network demand, support for IoT and edge computing, VPN replacement, performance assurance and so on. Increase audience engagement and knowledge by dispensing information using SD WAN Model Secure Access Service Edge Use Cases. This template helps you present information on six stages. You can also present information on Performance Assurance, Support For Multiple Operating Systems, Controlled Move To Cloud Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Secure Web Gateway Swg Functional Components
SD WAN Model Secure Web Gateway Swg Functional ComponentsThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Deliver an outstanding presentation on the topic using this SD WAN Model Secure Web Gateway Swg Functional Components. Dispense information and present a thorough explanation of Data Loss Prevention, Policy Enforcement, Secure Web Gateway, Functional Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Secure Web Gateway Swg Importance For Businesses
SD WAN Model Secure Web Gateway Swg Importance For BusinessesThis slide outlines the importance of secure web gateways to businesses. The purpose of this slide is to demonstrate the need for SWGs for companies to protect their critical data and applications from malicious activities and actors. Introducing SD WAN Model Secure Web Gateway Swg Importance For Businesses to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Secure Web Gateway, Critical Data And Applications, Outdated Technologies, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Secure Web Gateway Swg Introduction And Features
SD WAN Model Secure Web Gateway Swg Introduction And FeaturesThis slide describes the overview and features of the secure gateway. The purpose of this slide is to demonstrate the SWG and its benefits to businesses. The features include URL filtering, application control, data loss prevention, antivirus, and HTTPS inspection. Increase audience engagement and knowledge by dispensing information using SD WAN Model Secure Web Gateway Swg Introduction And Features. This template helps you present information on two stages. You can also present information on Application Control, Data Loss Prevention, Antivirus, Secure Web Gateway using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Secure Web Gateways Swg Setup And Working
SD WAN Model Secure Web Gateways Swg Setup And WorkingThis slide depicts the methods to setup the secure web gateways and their working. The purpose of this slide is to demonstrate the various ways in which organizations can install the SWGs. It also caters to the working and functions performed by SWGs to protect data and safe browsing on the internet. Introducing SD WAN Model Secure Web Gateways Swg Setup And Working to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Cost Effective Alternative, Secure Web Gateways, Setup And Working, Preventing Restricted Data Sources, using this template. Grab it now to reap its full benefits.
-
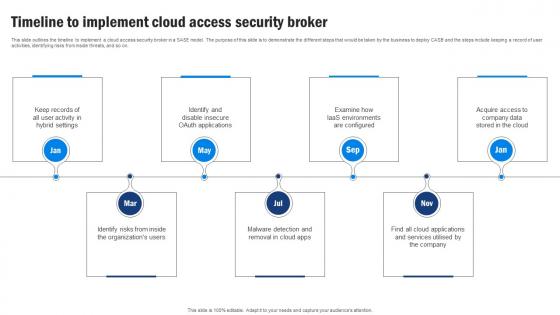 SD WAN Model Timeline To Implement Cloud Access Security Broker
SD WAN Model Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using SD WAN Model Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Cloud Access Security Broker, Environments Are Configured, Identify Risks, Malware Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
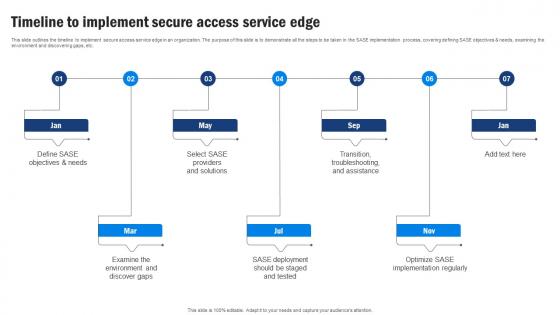 SD WAN Model Timeline To Implement Secure Access Service Edge
SD WAN Model Timeline To Implement Secure Access Service EdgeThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing SD WAN Model Timeline To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Secure Access Service Edge, Examining The Environment, Discovering Gaps, Timeline, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Traditional Networking Security Problems And Sase Solutions
SD WAN Model Traditional Networking Security Problems And Sase SolutionsThis slide describes the traditional networking security problems and how SASE model can overcome those problems. The main problems include, remote access to on-premises resources, access to cloud resources, network access controls etc. Deliver an outstanding presentation on the topic using this SD WAN Model Traditional Networking Security Problems And Sase Solutions. Dispense information and present a thorough explanation of Traditional Networking Security Problems, On Premises Resources, Access To Cloud Resources, Network Access Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Working Of Secure Access Service Edge
SD WAN Model Working Of Secure Access Service EdgeThis slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. Present the topic in a bit more detail with this SD WAN Model Working Of Secure Access Service Edge. Use it as a tool for discussion and navigation on Precise Amount Of Performance, Dependability, Security, Cost For Each Network Connection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 About Devsecops Model Workflow Process Devsecops Best Practices For Secure
About Devsecops Model Workflow Process Devsecops Best Practices For SecureThis slide gives an overview of the working procedure of DevSecOps. The purpose of this slide is to discuss the various steps involved in the DevSecOps working process, these include committing, analyzing, setting up the environment, testing, deploying, monitoring, and repeating. Introducing About Devsecops Model Workflow Process Devsecops Best Practices For Secure to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Devsecops Working Process, Analyzing, Testing, Deploying, Monitoring, using this template. Grab it now to reap its full benefits.
-
 Devsecops Best Practices For Secure About Pipeline Security Of Devsecops Model
Devsecops Best Practices For Secure About Pipeline Security Of Devsecops ModelThis slide discusses the pipeline security of DevSecOps. The purpose of this slide is to explain pipeline security and its importance in DevSecOps, which includes maximizing security personnel efficiency, automating non-intellectual tasks, improving the tracking of task statuses, and so on. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure About Pipeline Security Of Devsecops Model. Dispense information and present a thorough explanation of Pipeline Security Devsecops, Pipeline Security, Security Personnel Efficiency, Non Intellectual Tasks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Devsecops Best Practices For Secure About Workflow Process Of Devops Model
Devsecops Best Practices For Secure About Workflow Process Of Devops ModelThis slide discusses the working procedure of the DevOps model. The purpose of this slide is to showcase the working steps of the DevOps model for software building, these components include coding, branch, repo, CI or CD, production, registry, building, etc. Present the topic in a bit more detail with this Devsecops Best Practices For Secure About Workflow Process Of Devops Model. Use it as a tool for discussion and navigation on Software Building, Coding, Production, Registry, Security Considerations Occur Late. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure Benefits Of Devsecops Model In Organization
Devsecops Best Practices For Secure Benefits Of Devsecops Model In OrganizationThis slide explains the importance of the DevSecOps model in an organization. The purpose of this slide is to highlight the Benefits these are faster delivery, improved security posture, reduced cost, enhanced value of DevSecOps, improved security integration and peace, etc. Present the topic in a bit more detail with this Devsecops Best Practices For Secure Benefits Of Devsecops Model In Organization. Use it as a tool for discussion and navigation on Responsibility Ensures Security, Identifying Vulnerabilities, Reduced Costs. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure Comparison Between Devops And Devsecops Models
Devsecops Best Practices For Secure Comparison Between Devops And Devsecops ModelsThis slide showcases the comparison between DevOps and DevSecOps models. The purpose of this slide is to highlight the key differences in terms of definition, objective, benefits, attack surface, tool and methods, collaboration and continuous improvement. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure Comparison Between Devops And Devsecops Models. Dispense information and present a thorough explanation of Benefits, Attack Surface, Tool And Methods, Collaboration And Continuous Improvement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Devsecops Best Practices For Secure Core Principles Followed In Devsecops Model
Devsecops Best Practices For Secure Core Principles Followed In Devsecops ModelThis slide discusses the core principle used in the DevSecOps model. The purpose of this slide is to explain the principles of DevSecOps in detail, these include automation, continuous monitoring, and collaboration across functions. Increase audience engagement and knowledge by dispensing information using Devsecops Best Practices For Secure Core Principles Followed In Devsecops Model. This template helps you present information on three stages. You can also present information on Continuous Monitoring, Collaboration Across Functions, Configuration Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Devsecops Best Practices For Secure Four Levels Of Devsecops Maturity Model
Devsecops Best Practices For Secure Four Levels Of Devsecops Maturity ModelThis slide discusses the level of the DevSecOps maturity model. The purpose of this slide is to highlight the various levels, these include pre-DevOps with no automation, early DevOps or DevSecOps lightweight automation, DevOps to DevSecOps transition advance automation, etc. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure Four Levels Of Devsecops Maturity Model. Dispense information and present a thorough explanation of Lightweight Automation, Devops To Devsecops Transition, Application And Infrastructure Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Devsecops Best Practices For Secure Importance Of Devsecops Model In Organizations
Devsecops Best Practices For Secure Importance Of Devsecops Model In OrganizationsThis slide highlights the benefits of DevSecOps in an organization. The purpose of this slide is to explain the importance of DevSecOps model, these are improved security, increased efficiency, proactive threat management, regulatory compliance and so on. Present the topic in a bit more detail with this Devsecops Best Practices For Secure Importance Of Devsecops Model In Organizations. Use it as a tool for discussion and navigation on Building Secure Software, Mandating Integrated Security, Integration Enhances System, Application Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure IT Ops Responsibilities In Devsecops Model
Devsecops Best Practices For Secure IT Ops Responsibilities In Devsecops ModelThis slide highlights the IT operation responsibility in DevSecOps. The purpose of this slide is to discuss the IT responsibilities these are implementing infrastructure as code to create consistent and traceable resources and so on. Deliver an outstanding presentation on the topic using this Devsecops Best Practices For Secure IT Ops Responsibilities In Devsecops Model. Dispense information and present a thorough explanation of Consistent And Traceable Resources, Configuration Management Tools, Incorporate Security Measures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Devsecops Best Practices For Secure Overview Of Devsecops Model Cultural Aspects
Devsecops Best Practices For Secure Overview Of Devsecops Model Cultural AspectsThis slide gives an overview of the associated DevSecOps culture. The purpose of this slide is to discuss the cultural aspects of DevSecOps, these are communication aspect, technology aspect, people aspect, and processes aspect with their importance. Introducing Devsecops Best Practices For Secure Overview Of Devsecops Model Cultural Aspects to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Associated Devsecops Culture, Communication Aspect, Technology Aspect, using this template. Grab it now to reap its full benefits.
-
 Devsecops Best Practices For Secure Overview Of Working Process Of Devsecops Model
Devsecops Best Practices For Secure Overview Of Working Process Of Devsecops ModelThis slide discusses the workflow procedure of DevSecOps model. The purpose of this slide is to showcase the working steps of DevSecOps model for software building and enhancing security at each level these include coding, branch, repo, CI or CD, production, etc. Present the topic in a bit more detail with this Devsecops Best Practices For Secure Overview Of Working Process Of Devsecops Model. Use it as a tool for discussion and navigation on Workflow Procedure Of Devsecops, Software Building, Enhancing Security, Production. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure Success Criteria For Devsecops Model Process
Devsecops Best Practices For Secure Success Criteria For Devsecops Model ProcessThis slide highlights the success criteria followed for the DevSecOps process. The purpose of this slide is to discuss the various standards, including open collaboration to shared objectives, security at source, reinforcement and elevations through automation, and so on. Introducing Devsecops Best Practices For Secure Success Criteria For Devsecops Model Process to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Proactive Monitoring And Recursive, Reinforce And Elevate Through Automation, Security At Source, using this template. Grab it now to reap its full benefits.
-
 Sase Model Benefits Of Secure Access Service Edge Sase
Sase Model Benefits Of Secure Access Service Edge SaseThis slide outlines the key benefits of secure access service edge. The purpose of this slide is to showcase the advantages of the SASE model, such as flexibility, cost savings, reduced complexity, increased performance, threat and data protection and increased network performance. Deliver an outstanding presentation on the topic using this Sase Model Benefits Of Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Benefits, Description, Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Best Practices To Implement Cloud Access Security Broker
Sase Model Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Present the topic in a bit more detail with this Sase Model Best Practices To Implement Cloud Access Security Broker. Use it as a tool for discussion and navigation on Best Practices, Description, Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Budget To Implement Secure Access Service Edge
Sase Model Budget To Implement Secure Access Service EdgeThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD-WAN, SWG, ZTNA, CASB, and FWaaS. Deliver an outstanding presentation on the topic using this Sase Model Budget To Implement Secure Access Service Edge. Dispense information and present a thorough explanation of Components, Estimated Cost, Actual Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Challenges With Traditional Network Security Approaches
Sase Model Challenges With Traditional Network Security ApproachesThis slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Present the topic in a bit more detail with this Sase Model Challenges With Traditional Network Security Approaches. Use it as a tool for discussion and navigation on Disjointed Management, Workload, Slower Cloud Adoption. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Checklist To Implement Secure Access Service Edge
Sase Model Checklist To Implement Secure Access Service EdgeDeliver an outstanding presentation on the topic using this Sase Model Checklist To Implement Secure Access Service Edge. Dispense information and present a thorough explanation of Steps, Responsible Person, Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Cloud Access Security Broker Casb Overview
Sase Model Cloud Access Security Broker Casb OverviewThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Increase audience engagement and knowledge by dispensing information using Sase Model Cloud Access Security Broker Casb Overview. This template helps you present information on five stages. You can also present information on Risk Visibility, Threat Prevention, Granular Cloud using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Cloud Access Security Broker Implementation Models
Sase Model Cloud Access Security Broker Implementation ModelsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing Sase Model Cloud Access Security Broker Implementation Models to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Scanning, Forward Proxy, Reverse Proxy, using this template. Grab it now to reap its full benefits.
-
 Sase Model Cloud Access Security Broker Use Cases
Sase Model Cloud Access Security Broker Use CasesThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Present the topic in a bit more detail with this Sase Model Cloud Access Security Broker Use Cases. Use it as a tool for discussion and navigation on Protection Against Threats, Govern Usage, Secure Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Cloud Access Security Broker Working Process
Sase Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Sase Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Discovery, Classification, Remediation, using this template. Grab it now to reap its full benefits.
-
 Sase Model Comparison Between Secure Access Service Edge And Sd Wan
Sase Model Comparison Between Secure Access Service Edge And Sd WanThis slide compares secure access service edge and software-defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD-WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Deliver an outstanding presentation on the topic using this Sase Model Comparison Between Secure Access Service Edge And Sd Wan. Dispense information and present a thorough explanation of Factors, Sd Wan, Sase using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Firewall As A Service Fwaas Working And Security Features
Sase Model Firewall As A Service Fwaas Working And Security FeaturesThis slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, and IP mapping. Deliver an outstanding presentation on the topic using this Sase Model Firewall As A Service Fwaas Working And Security Features. Dispense information and present a thorough explanation of Cloud Database, Email Cloud using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Introduction To Secure Access Service Edge Sase
Sase Model Introduction To Secure Access Service Edge SaseThis slide represents the introduction of SASE cloud security technology. The purpose of this slide is to demonstrate the core capabilities, benefits and key components of SASE. The key components include SD-WAN, FWaaS, ZTNA, CASB, SWG, and unified management. Present the topic in a bit more detail with this Sase Model Introduction To Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Key Components, Benefits. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Pillars Of Cloud Access Security Broker
Sase Model Pillars Of Cloud Access Security BrokerThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Increase audience engagement and knowledge by dispensing information using Sase Model Pillars Of Cloud Access Security Broker. This template helps you present information on four stages. You can also present information on Compliance, Visibility, Threat Prevention using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Roadmap To Implement Secure Access Service Edge
Sase Model Roadmap To Implement Secure Access Service EdgeThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Introducing Sase Model Roadmap To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Examine The Environment, Providers And Solutions, Implementation Regularly, using this template. Grab it now to reap its full benefits.
-
 Sase Model Secure Access Service Edge Architecture Characteristics
Sase Model Secure Access Service Edge Architecture CharacteristicsThis slide represents the architectural characteristics of a secure access service edge. The purpose of this slide is to showcase the features of SASE architecture that include identity-driven, cloud-native, support for all edges, and global distribution. Introducing Sase Model Secure Access Service Edge Architecture Characteristics to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identity Driven, Support For All Edges, Globally Distributed, using this template. Grab it now to reap its full benefits.
-
 Sase Model Secure Access Service Edge Implementation Steps
Sase Model Secure Access Service Edge Implementation StepsThis slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD-WAN backbone, incorporating zero-trust solutions, etc. Increase audience engagement and knowledge by dispensing information using Sase Model Secure Access Service Edge Implementation Steps. This template helps you present information on five stages. You can also present information on Goals And Requirements, Incorporate Zero Trust Solutions, Test And Troubleshoot using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Secure Access Service Edge Importance
Sase Model Secure Access Service Edge ImportanceThis slide represents the importance of secure access service edge. This slides purpose is to demonstrate why businesses need the SASE model. The main reasons include scaling with business needs, encouraging work from anywhere environment, standing up for cyber threats, and offering a base for IoT adoption. Introducing Sase Model Secure Access Service Edge Importance to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Scales With Business, Cyberthreat Evolution, Provides Base Iot Adoption, using this template. Grab it now to reap its full benefits.
-
 Sase Model Secure Access Service Edge Sase Architecture
Sase Model Secure Access Service Edge Sase ArchitectureThis slide represents the SASE architecture overview and its goals. The purpose of this slide is to demonstrate the secure access service edge architecture and its goals. The building blocks of SASE Architecture include SWG, CASB, ZTNA, FWaaS, SD-WAN, Thin Edge, and so on. Deliver an outstanding presentation on the topic using this Sase Model Secure Access Service Edge Sase Architecture. Dispense information and present a thorough explanation of Secure Access Service, Edge Sase Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Secure Access Service Edge Training Program
Sase Model Secure Access Service Edge Training ProgramThis slide represents the training program for the secure access service edge model. The purpose of this slide is to demonstrate the teams eligible for training, the modules to be covered during the training, the schedule and venue of the training. Present the topic in a bit more detail with this Sase Model Secure Access Service Edge Training Program. Use it as a tool for discussion and navigation on . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Secure Access Service Edge Use Cases
Sase Model Secure Access Service Edge Use CasesThis slide represents the use cases of secure access service edge within an organization. The purpose of this slide is to demonstrate the various use cases of the SASE model, including rapid response to network demand, support for IoT and edge computing, VPN replacement, performance assurance and so on. Introducing Sase Model Secure Access Service Edge Use Cases to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Rapid Response, Edge Computing, Performance Assurance, using this template. Grab it now to reap its full benefits.
-
 Sase Model Secure Web Gateway SWG Functional Components
Sase Model Secure Web Gateway SWG Functional ComponentsThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Present the topic in a bit more detail with this Sase Model Secure Web Gateway SWG Functional Components. Use it as a tool for discussion and navigation on Components, Working, Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Secure Web Gateway SWG Importance For Businesses
Sase Model Secure Web Gateway SWG Importance For BusinessesThis slide outlines the importance of secure web gateways to businesses. The purpose of this slide is to demonstrate the need for SWGs for companies to protect their critical data and applications from malicious activities and actors. Introducing Sase Model Secure Web Gateway SWG Importance For Businesses to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Remote Workforces, Headquarters Apps, Exposed To Danger, using this template. Grab it now to reap its full benefits.
-
 Sase Model Secure Web Gateway SWG Introduction And Features
Sase Model Secure Web Gateway SWG Introduction And FeaturesThis slide describes the overview and features of the secure gateway. The purpose of this slide is to demonstrate the SWG and its benefits to businesses. The features include URL filtering, application control, data loss prevention, antivirus, and HTTPS inspection. Present the topic in a bit more detail with this Sase Model Secure Web Gateway SWG Introduction And Features. Use it as a tool for discussion and navigation on According To Acceptable, Secure Internet Access, Unlawful Transmission. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Secure Web Gateways SWG Setup And Working
Sase Model Secure Web Gateways SWG Setup And WorkingThis slide depicts the methods to setup the secure web gateways and their working. The purpose of this slide is to demonstrate the various ways in which organizations can install the SWGs. It also caters to the working and functions performed by SWGs to protect data and safe browsing on the internet. Introducing Sase Model Secure Web Gateways SWG Setup And Working to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Hardware Device, Access Regulations, Implementing Policies, using this template. Grab it now to reap its full benefits.
-
 Sase Model Timeline To Implement Cloud Access Security Broker
Sase Model Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Sase Model Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Hybrid Settings, Environments Are Configured, Cloud App using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Timeline To Implement Secure Access Service Edge
Sase Model Timeline To Implement Secure Access Service EdgeThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing Sase Model Timeline To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Jan, Mar, May, Jul, using this template. Grab it now to reap its full benefits.
-
 Sase Model Traditional Networking Security Problems And Sase Solutions
Sase Model Traditional Networking Security Problems And Sase SolutionsThis slide describes the traditional networking security problems and how SASE model can overcome those problems. The main problems include, remote access to on-premises resources, access to cloud resources, network access controls etc. Present the topic in a bit more detail with this Sase Model Traditional Networking Security Problems And Sase Solutions. Use it as a tool for discussion and navigation on Traditional Networking Models. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Working Of Secure Access Service Edge
Sase Model Working Of Secure Access Service EdgeThis slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. Present the topic in a bit more detail with this Sase Model Working Of Secure Access Service Edge. Use it as a tool for discussion and navigation on Traditional Network Security Model, Network Security Model. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business Model Investor Capital Pitch Deck For Secure Digital Payment Platform
Business Model Investor Capital Pitch Deck For Secure Digital Payment PlatformThe following slide showcases business model of payment infrastructure company. It includes mix of product and feed based along with components such as payment processing, developer oriented platform, value added services, etc. Introducing Business Model Investor Capital Pitch Deck For Secure Digital Payment Platform to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Payment Processing, Software Platforms, Value, Oriented Platform, using this template. Grab it now to reap its full benefits.





