Powerpoint Templates and Google slides for Security Model
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Reasons To Adopt Zero Trust Network Access Model Zero Trust Security Model
Reasons To Adopt Zero Trust Network Access Model Zero Trust Security ModelThis slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Introducing Reasons To Adopt Zero Trust Network Access Model Zero Trust Security Model to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Businesses, Resources, Organizations, using this template. Grab it now to reap its full benefits.
-
 Role Of ZTNA To Improve Business Operations And Security Zero Trust Security Model
Role Of ZTNA To Improve Business Operations And Security Zero Trust Security ModelThis slide talks about the ways in which ZTNA improves the business operations and security. The purpose of this slide is to showcase the various domains that zero trust network access improves, including increased user experience, remote workforce protection, improve data protection, and network visibility. Deliver an outstanding presentation on the topic using this Role Of ZTNA To Improve Business Operations And Security Zero Trust Security Model. Dispense information and present a thorough explanation of Enhanced User Experience, Remote Workforce Protection, Improve Data Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Security Model
Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Security ModelThis slide illustrates the overview of the self-hosted deployment approach of ZTNA architecture. The purpose of this slide is to highlight the self-hosted deployment architecture of ZTNA and includes the pros and cons of the self-hosted deployment approach. Present the topic in a bit more detail with this Self Hosted Deployment Approach Of ZTNA Architecture Zero Trust Security Model. Use it as a tool for discussion and navigation on Architecture, Deployment, Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Service Initiated Zero Trust Network Topology Model Zero Trust Security Model
Service Initiated Zero Trust Network Topology Model Zero Trust Security ModelThis slide provides an overview of service initiated zero-trust network topology model. The purpose of this slide is to showcase its architecture, benefits, and disadvantages. The architectural components include a user device, controller, broker proxy, and connector. Deliver an outstanding presentation on the topic using this Service Initiated Zero Trust Network Topology Model Zero Trust Security Model. Dispense information and present a thorough explanation of Environment, Enterprise, Access Connection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Solutions To Overcome ZTNA Implementation Challenges Zero Trust Security Model
Solutions To Overcome ZTNA Implementation Challenges Zero Trust Security ModelThis slide talks about the various solutions to overcome the ZTNA deployment challenges. The purpose of this slide is to showcase the remedies to overcome ZTNA obstacles. The leading solutions include running zero-trust trials, starting small, scaling slowly, and keeping people and zero trust in mind. Present the topic in a bit more detail with this Solutions To Overcome ZTNA Implementation Challenges Zero Trust Security Model. Use it as a tool for discussion and navigation on Implementation, Solutions, Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Step 1 Form A Dedicated Zero Trust Team Zero Trust Security Model
Step 1 Form A Dedicated Zero Trust Team Zero Trust Security ModelThis slide represents the first step of ZTNA implementation, which is forming a dedicated zero-trust team. The purpose of this slide is to highlight the objective behind building a dedicated team and representing the domains and names of team members. Deliver an outstanding presentation on the topic using this Step 1 Form A Dedicated Zero Trust Team Zero Trust Security Model. Dispense information and present a thorough explanation of Responsible, Planning, Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Security Model
Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Security ModelThis slide outlines the second step of zero trust network access implementation, which is choosing the on-ramp option. The purpose of this slide is to showcase the various on-ramp options and technologies used in each option. The three on-ramp options include user and device identity, app and data, and the network. Present the topic in a bit more detail with this Step 2 Choose Zero Trust Implementation On Ramp Zero Trust Security Model. Use it as a tool for discussion and navigation on User And Device Identity, Applications And Data, Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Step 3 Assess The Environment Zero Trust Security Model
Step 3 Assess The Environment Zero Trust Security ModelThis slide outlines the third step of ZTNA deployment, which is assessing the environment. The purpose of this slide is to highlight the questions that should be answered to evaluate the ecosystem and the questions include knowing the security controls, knowledge gaps and so on. Deliver an outstanding presentation on the topic using this Step 3 Assess The Environment Zero Trust Security Model. Dispense information and present a thorough explanation of Knowledge, Categorizations, Structures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Zero Trust Security Model
Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Zero Trust Security ModelThis slide outlines the sixth and seventh steps for ZTNA implementation, which are defining operational changes and implementing, rinsing and repeating the process. The purpose of this slide is to showcase the following steps in zero trust model deployment. Deliver an outstanding presentation on the topic using this Step 6 And 7 Define Operational Changes And Implement Rinse Repeat Zero Trust Security Model. Dispense information and present a thorough explanation of Operational, Implement, Performance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Steps To Implement Zero Trust Network Access Model Zero Trust Security Model
Steps To Implement Zero Trust Network Access Model Zero Trust Security ModelThis slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Present the topic in a bit more detail with this Steps To Implement Zero Trust Network Access Model Zero Trust Security Model. Use it as a tool for discussion and navigation on Architecture, Protection, Monitor The Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technologies Used In Zero Trust Network Access Zero Trust Security Model
Technologies Used In Zero Trust Network Access Zero Trust Security ModelThis slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer. Deliver an outstanding presentation on the topic using this Technologies Used In Zero Trust Network Access Zero Trust Security Model. Dispense information and present a thorough explanation of Technologies, Techniques, Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Timeline To Implement Zero Trust Network Access Model Zero Trust Security Model
Timeline To Implement Zero Trust Network Access Model Zero Trust Security ModelThis slide showcases the timeline for implementing the ZTNA security model. This slide highlights the various steps organizations will take while deploying the ZTNA system, forming a dedicated team, choosing zero-trust implementation on-ramp, assessing the environment and so on. Introducing Timeline To Implement Zero Trust Network Access Model Zero Trust Security Model to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Timeline, Implementation, Applications, using this template. Grab it now to reap its full benefits.
-
 Top Zero Trust Network Access Software Solutions Zero Trust Security Model
Top Zero Trust Network Access Software Solutions Zero Trust Security ModelThis slide illustrates the top software solution for zero-trust network access. The purpose of this slide is to showcase the prominent tools for ZTNA implementation, including Okta identity-driven security, ping identity, Google BeyondCorp, Twingate, Permiter 81 and so on. Present the topic in a bit more detail with this Top Zero Trust Network Access Software Solutions Zero Trust Security Model. Use it as a tool for discussion and navigation on Software, Solutions, Implementation . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Traditional Perimeter Based Network Security Overview And Limitations Zero Trust Security Model
Traditional Perimeter Based Network Security Overview And Limitations Zero Trust Security ModelThis slide represents the overview of traditional perimeter-based network security. The purpose of this slide is to showcase the various challenges of conventional perimeter-based security and how ZTNA can overcome those challenges. Deliver an outstanding presentation on the topic using this Traditional Perimeter Based Network Security Overview And Limitations Zero Trust Security Model. Dispense information and present a thorough explanation of Traditional, Overview, Limitations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Traditional Security Models Vs Zero Trust Network Access Zero Trust Security Model
Traditional Security Models Vs Zero Trust Network Access Zero Trust Security ModelThis slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Present the topic in a bit more detail with this Traditional Security Models Vs Zero Trust Network Access Zero Trust Security Model. Use it as a tool for discussion and navigation on Dependence, Foundation, Attack Surface. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Training Program For Zero Trust Network Access Model Zero Trust Security Model
Training Program For Zero Trust Network Access Model Zero Trust Security ModelThis slide outlines the training program for implementing the zero-trust network access model in the organization. The purpose of this slide is to highlight the training agenda, objectives, system requirements, mode of training and cost of the training. Deliver an outstanding presentation on the topic using this Training Program For Zero Trust Network Access Model Zero Trust Security Model. Dispense information and present a thorough explanation of Micro Segmentation, Solutions, Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Of Zero Trust Network Access ZTNA Models Zero Trust Security Model
Types Of Zero Trust Network Access ZTNA Models Zero Trust Security ModelThis Slide Describes The Various Types Of Zero-Trust Network Access Models. The Purpose Of This Slide Is To Demonstrate The Various ZTNA Models And Core Elements Of ZTNA Implementation. The Model Types Include User Protection, Workload Protection, And Device Protection. Present The Topic In A Bit More Detail With This Types Of Zero Trust Network Access ZTNA Models Zero Trust Security Model. Use It As A Tool For Discussion And Navigation On Knowledge Conviction, Disruptive Technologies, Cultural Mindset Change. This Template Is Free To Edit As Deemed Fit For Your Organization. Therefore Download It Now.
-
 Working Functions Of Zero Trust Network Access Architecture Zero Trust Security Model
Working Functions Of Zero Trust Network Access Architecture Zero Trust Security ModelThis slide gives an overview of the working features of zero trust network access architecture. The purpose of this slide is to highlight the various functions that ZTNA architecture performs, including identification, protection, detection and response to threats. Introducing Working Functions Of Zero Trust Network Access Architecture Zero Trust Security Model to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Architecture, Abnormalities, Processing, using this template. Grab it now to reap its full benefits.
-
 Zero Trust Exchange Overview And Benefits Zero Trust Security Model
Zero Trust Exchange Overview And Benefits Zero Trust Security ModelThis slide provides an overview of zero trust exchange and its benefits. The purpose of this slide is to highlight the key advantages of zero trust exchange to businesses including enhancing user experience, reducing internet attacks and later threat movement, lowering costs and complexity, and so on. Present the topic in a bit more detail with this Zero Trust Exchange Overview And Benefits Zero Trust Security Model. Use it as a tool for discussion and navigation on Overview, Businesses, Experience. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Zero Trust Network Access Vs Zero Trust Architecture Zero Trust Security Model
Zero Trust Network Access Vs Zero Trust Architecture Zero Trust Security ModelThis slide represents the comparison between zero-trust network access and zero-trust architecture. The purpose of this slide is to highlight the key differences between ZTNA and ZTA based on definition, focus, objective, technologies, and implementation. Deliver an outstanding presentation on the topic using this Zero Trust Network Access Vs Zero Trust Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Implementation, Technologies using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Define Security Token Project Business Model Security Token Offerings BCT SS
Define Security Token Project Business Model Security Token Offerings BCT SSThe following slide depicts sample security token project business model to enhance liquidity and accessibility for fund raising. It includes elements such as overview tokenization, revenue streams, fund utilization, etc. Present the topic in a bit more detail with this Define Security Token Project Business Model Security Token Offerings BCT SS. Use it as a tool for discussion and navigation on Project, Overview, Tokenization Model, Revenue Streams. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Operating Maturity Model Levels
Security Operating Maturity Model LevelsThe slide contains security operating maturity levels that assist in providing overall consistency, reliability, and resilience to IT systems at the hands of management, design, etc. The slide has improved visibility, quick identification of threats,and decreased response time. Presenting our set of slides with Security Operating Maturity Model Levels. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Decreased Response, Improvement In Visibility, Quick Identification.
-
 Key Access Security Control Models Delivering ICT Services For Enhanced Business Strategy SS V
Key Access Security Control Models Delivering ICT Services For Enhanced Business Strategy SS VThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role-based access control and attributes based access control, Deliver an outstanding presentation on the topic using this Key Access Security Control Models Delivering ICT Services For Enhanced Business Strategy SS V. Dispense information and present a thorough explanation of Access Control Method, Description using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Model To Effective Delivering ICT Services For Enhanced Business Strategy SS V
Network Security Model To Effective Delivering ICT Services For Enhanced Business Strategy SS VThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Introducing Network Security Model To Effective Delivering ICT Services For Enhanced Business Strategy SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Threats, Security Breaches, Virtual Private, using this template. Grab it now to reap its full benefits.
-
 Security Operating Model In Powerpoint And Google Slides Cpb
Security Operating Model In Powerpoint And Google Slides CpbPresenting our Security Operating Model In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Operating Model This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Implementation Of Information Data Encryption Model For Effective Information Security Strategy SS V
Implementation Of Information Data Encryption Model For Effective Information Security Strategy SS VThis slide represents data encryption model for effective information security. It includes data encoding, data decoding, backup repository etc. Present the topic in a bit more detail with this Implementation Of Information Data Encryption Model For Effective Information Security Strategy SS V. Use it as a tool for discussion and navigation on Backup Repository, Encrypted Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Information Key Access Security Control Models Strategy SS V
Implementation Of Information Key Access Security Control Models Strategy SS VThis slide represents key access security control models for organizations. It includes discretionary access control, mandatory access control, role based access control and attributes based access control, Present the topic in a bit more detail with this Implementation Of Information Key Access Security Control Models Strategy SS V. Use it as a tool for discussion and navigation on Discretionary Access, Mandatory Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementation Of Information Network Security Model To Effective Communication Strategy SS V
Implementation Of Information Network Security Model To Effective Communication Strategy SS VThis slide represents the network security model for effective communication in the organization. It covers information regarding security threats, firewalls, virtual private networks, etc. Present the topic in a bit more detail with this Implementation Of Information Network Security Model To Effective Communication Strategy SS V. Use it as a tool for discussion and navigation on Message Transformation, Information Channel. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Grid Computing Architecture Introduction To Grid Computing Security Model
Grid Computing Architecture Introduction To Grid Computing Security ModelThis slide represents the introduction to the grid computing security model, including the security components such as authentication and delegation. The security model consists of intrusion detection, anti-virus management, policy management, user management, key management, and so on. Deliver an outstanding presentation on the topic using this Grid Computing Architecture Introduction To Grid Computing Security Model. Dispense information and present a thorough explanation of Grid Computing Security Model, Security Components, Authentication And Delegation, Intrusion Detection, Anti Virus Management, Policy Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 API Scanning CASB Deployment Model
Cloud Access Security Broker CASB V2 API Scanning CASB Deployment ModelThis slide outlines the overview of the API scanning model of CASB deployment. The purpose of this slide is to showcase its features and introduce APIs and how this deployment works. It also represents the architecture of the API scanning model and its components include mobile and corporate devices and APIs. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 API Scanning CASB Deployment Model. Use it as a tool for discussion and navigation on Corporate Devices, Facilitate Communication, Real Time Protection, Non Intrusive Security Technique. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB V2 Future Use Of Emerging Technologies In CASB Model
Cloud Access Security Broker CASB V2 Future Use Of Emerging Technologies In CASB ModelThis slide gives an overview of the technologies that can be used in the Cloud Access Security Broker model in the future. The purpose of this slide is to showcase the various emerging technologies that can help CASB to grow in the future. The technologies include AI, ML, CSPM, data privacy and protection, etc. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Future Use Of Emerging Technologies In CASB Model. Dispense information and present a thorough explanation of Cloud Security Posture Management, Data Privacy And Protection, Zero Trust Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Overview Of CASB Deployment Models
Cloud Access Security Broker CASB V2 Overview Of CASB Deployment ModelsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Overview Of CASB Deployment Models. This template helps you present information on four stages. You can also present information on Cloud Access Security Broker, Unmanaged Gadgets, Inline Deployment, Scalable And Strong Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Proxy Based CASB Deployment Model
Cloud Access Security Broker CASB V2 Proxy Based CASB Deployment ModelThis slide outlines the overview of proxy-based CASB deployment. The purpose of this slide is to highlight the proxy-based implementation of the CASB model and it also includes the fundamental modes of proxy deployment, including forward proxy and reverse proxy. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Proxy Based CASB Deployment Model. Dispense information and present a thorough explanation of Proxy Based Implementation, Proxy Deployment, Proxy And Reverse Proxy, Operation Of Several using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Requirements For Appropriate Cloud Security Model
Cloud Access Security Broker CASB V2 Requirements For Appropriate Cloud Security ModelThis slide outlines the different prerequisites organizations should consider when choosing a cloud security model and provider. The purpose of this slide is to showcase the various requirements a cloud security provider should possess, including visibility and threat detection, continuous compliance, data encryption and so on. Introducing Cloud Access Security Broker CASB V2 Requirements For Appropriate Cloud Security Model to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Visibility And Threat Detection, Continuous Compliance, Data Encryption, Strong Authentication, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker CASB V2 Reverse Proxy CASB Deployment Model
Cloud Access Security Broker CASB V2 Reverse Proxy CASB Deployment ModelThis slide outlines the overview of the reverse proxy cloud access security model broker. The purpose of this slide is to showcase overview of working and various types of reverse proxy CASB. The main types include regular reverse proxies and load balancers. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker CASB V2 Reverse Proxy CASB Deployment Model. This template helps you present information on five stages. You can also present information on Reverse Proxy, Cloud Access Security Model Broker, Web Server Anonymity, Websites With High Traffic using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Compliance Conceptual Model Framework
Security Compliance Conceptual Model FrameworkThis slide shows compliance conceptual model framework of security to provide senior management with a structured framework. It further includes details such as compliance drivers, laws, regulations etc. Introducing our Security Compliance Conceptual Model Framework set of slides. The topics discussed in these slides are Contracts, Standards. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Secops V2 RACI Matrix For Soc As A Service Security Model
Secops V2 RACI Matrix For Soc As A Service Security ModelThis slide outlines the RACI matrix for the SOC-as-a-Service security model. The purpose of this slide is to highlight the various roles and responsibilities in a SOC as a Service environment. The main roles include SOC manager, security analyst, security architecture, compliance auditor, and SOC coordinator. Present the topic in a bit more detail with this Secops V2 RACI Matrix For Soc As A Service Security Model. Use it as a tool for discussion and navigation on Classified And Prioritizes Alerts, Evaluate Network Security, Service Security Model, Compliance Auditor. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secops V2 Roles And Responsibilities Of Soc As A Service Security Model
Secops V2 Roles And Responsibilities Of Soc As A Service Security ModelThis slide illustrates the roles and responsibilities of the SOC-as-a-Service security model. The purpose of this slide is to highlight the various roles and responsibilities in a SOC as a Service environment. The main roles include SOC manager, security analyst, security architecture, compliance auditor, and SOC coordinator. Increase audience engagement and knowledge by dispensing information using Secops V2 Roles And Responsibilities Of Soc As A Service Security Model. This template helps you present information on seven stages. You can also present information on Roles And Responsibilities, Security Analyst, Security Architecture, Compliance Auditor using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
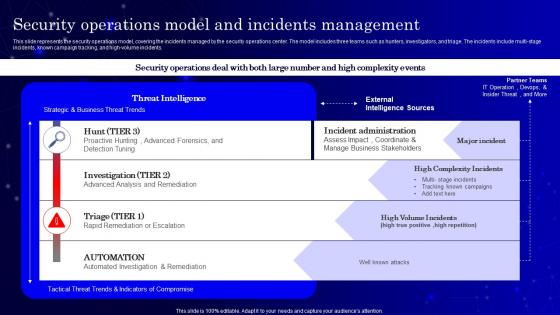 Secops V2 Security Operations Model And Incidents Management
Secops V2 Security Operations Model And Incidents ManagementThis slide represents the security operations model, covering the incidents managed by the security operations center. The model includes three teams such as hunters, investigators, and triage. The incidents include multi-stage incidents, known campaign tracking, and high-volume incidents. Present the topic in a bit more detail with this Secops V2 Security Operations Model And Incidents Management. Use it as a tool for discussion and navigation on Security Operations Model, Incidents Management, Known Campaign Tracking, Rapid Remediation Or Escalation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda For Cloud Security Model Ppt Information
Agenda For Cloud Security Model Ppt InformationIntroducing Agenda For Cloud Security Model Ppt Information to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Provides, Components, Process, using this template. Grab it now to reap its full benefits.
-
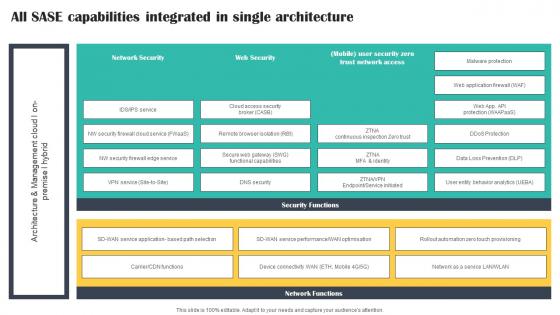 All SASE Capabilities Integrated In Single Architecture Cloud Security Model
All SASE Capabilities Integrated In Single Architecture Cloud Security ModelPresent the topic in a bit more detail with this All SASE Capabilities Integrated In Single Architecture Cloud Security Model. Use it as a tool for discussion and navigation on Capabilities, Integrated, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Approaches To Implement Zero Trust Network Access Cloud Security Model
Approaches To Implement Zero Trust Network Access Cloud Security ModelThis slide depicts the two primary approaches to implementing zero trust network access for organizations. The purpose of this slide is to showcase the endpoint initiated and service initiated approach of zero-trust network access. It also includes how users access business services and applications in both approaches. Deliver an outstanding presentation on the topic using this Approaches To Implement Zero Trust Network Access Cloud Security Model. Dispense information and present a thorough explanation of Network, Access, Implement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Architecture And Working Of SD Wide Area Network Cloud Security Model
Architecture And Working Of SD Wide Area Network Cloud Security ModelThis slide represents the architecture and working of a software defined wide area network. The purpose of this slide is to demonstrate the different types of SD WAN architectures, such as on premise, cloud enabled and cloud enabled with backbone. It also caters to the basic operation of SD WAN. Increase audience engagement and knowledge by dispensing information using Architecture And Working Of SD Wide Area Network Cloud Security Model. This template helps you present information on three stages. You can also present information on Working, Architecture, Network using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Benefits Of Secure Access Service Edge SASE Cloud Security Model
Benefits Of Secure Access Service Edge SASE Cloud Security ModelThis slide outlines the key benefits of secure access service edge. The purpose of this slide is to showcase the advantages of the SASE model, such as flexibility, cost savings, reduced complexity, increased performance, threat and data protection and increased network performance. Present the topic in a bit more detail with this Benefits Of Secure Access Service Edge SASE Cloud Security Model. Use it as a tool for discussion and navigation on Secure, Benefits, Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Benefits Of Software Defined Wide Area Network Cloud Security Model
Benefits Of Software Defined Wide Area Network Cloud Security ModelThis slide outlines the various advantages of the software defined wide area network to businesses. The purpose of this slide is to demonstrate the multiple benefits of SD WAN, including improved security, better application experience, simplified management and optimized cloud connectivity. Increase audience engagement and knowledge by dispensing information using Benefits Of Software Defined Wide Area Network Cloud Security Model. This template helps you present information on four stages. You can also present information on Improved, Experience, Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Benefits Of Zero Trust Network Access ZTNA Cloud Security Model
Benefits Of Zero Trust Network Access ZTNA Cloud Security ModelThis slide represents the benefits of zero trust network access, a component of SASE technology. The purpose of this slide is to demonstrate the multiple benefits of ZTNA to businesses and users. It also caters to the security benefits such as increased control and visibility, invisible infrastructure, and simple app segmentation. Deliver an outstanding presentation on the topic using this Benefits Of Zero Trust Network Access ZTNA Cloud Security Model. Dispense information and present a thorough explanation of Benefits, Description, Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Evaluate SASE Solutions Cloud Security Model
Best Practices To Evaluate SASE Solutions Cloud Security ModelThis slide represents the best practices to evaluate secure access service edge solutions. The purpose of this slide is to demonstrate the various considerations businesses should keep in mind while choosing and implementing a SASE solution. Present the topic in a bit more detail with this Best Practices To Evaluate SASE Solutions Cloud Security Model. Use it as a tool for discussion and navigation on Practices, Evaluate, Solutions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices To Implement Cloud Access Security Broker Cloud Security Model
Best Practices To Implement Cloud Access Security Broker Cloud Security ModelThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker Cloud Security Model. Dispense information and present a thorough explanation of Implement, Practices, Visibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Budget To Implement Secure Access Service Edge Cloud Security Model
Budget To Implement Secure Access Service Edge Cloud Security ModelThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD WAN, SWG, ZTNA, CASB, and FWaaS. Present the topic in a bit more detail with this Budget To Implement Secure Access Service Edge Cloud Security Model. Use it as a tool for discussion and navigation on Implement, Network, Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business Benefits Of Firewall As A Service Cloud Security Model
Business Benefits Of Firewall As A Service Cloud Security ModelThis slide illustrates the advantages of firewall as a service to businesses. The purpose of this slide is to demonstrate the business benefits of FWaaS, such as easy maintenance, simple infrastructure, better visibility, easy configuration, scalability and protection of remote workers. Deliver an outstanding presentation on the topic using this Business Benefits Of Firewall As A Service Cloud Security Model. Dispense information and present a thorough explanation of Maintain, Visibility, Configuration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Challenges And Solutions For SASE Implementation Cloud Security Model
Challenges And Solutions For SASE Implementation Cloud Security ModelThis slide represents the challenges and solutions for implementing a secure access service edge in an organization. The purpose of this slide is to showcase the different challenges that a business can face while deploying the SASE model into a business. The key challenges include networking and security team misalignment, change management, etc. Present the topic in a bit more detail with this Challenges And Solutions For SASE Implementation Cloud Security Model. Use it as a tool for discussion and navigation on Solutions, Implementation, Challenges. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Challenges With Traditional Network Security Approaches Cloud Security Model
Challenges With Traditional Network Security Approaches Cloud Security ModelThis slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Deliver an outstanding presentation on the topic using this Challenges With Traditional Network Security Approaches Cloud Security Model. Dispense information and present a thorough explanation of Approaches, Security, Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Implement Secure Access Service Edge Cloud Security Model
Checklist To Implement Secure Access Service Edge Cloud Security ModelPresent the topic in a bit more detail with this Checklist To Implement Secure Access Service Edge Cloud Security Model. Use it as a tool for discussion and navigation on Service, Access, Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker CASB Overview Cloud Security Model
Cloud Access Security Broker CASB Overview Cloud Security ModelThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Introducing Cloud Access Security Broker CASB Overview Cloud Security Model to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Visibility, Prevention, Management, using this template. Grab it now to reap its full benefits.
-
 Cloud Access Security Broker Implementation Models Cloud Security Model
Cloud Access Security Broker Implementation Models Cloud Security ModelThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out of band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Implementation Models Cloud Security Model. This template helps you present information on three stages. You can also present information on Scanning, Forward, Reverse using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker Use Cases Cloud Security Model
Cloud Access Security Broker Use Cases Cloud Security ModelThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Use Cases Cloud Security Model. Dispense information and present a thorough explanation of Protection, Govern, Secure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Working Process Cloud Security Model
Cloud Access Security Broker Working Process Cloud Security ModelThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Increase audience engagement and knowledge by dispensing information using Cloud Access Security Broker Working Process Cloud Security Model. This template helps you present information on three stages. You can also present information on Discovery, Classification, Remediation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Model Table Of Contents Ppt Demonstration
Cloud Security Model Table Of Contents Ppt DemonstrationIntroducing Cloud Security Model Table Of Contents Ppt Demonstration to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Secure, Architecture, Network, using this template. Grab it now to reap its full benefits.
-
 Comparative Analysis For Corporate Network Efficacy Cloud Security Model
Comparative Analysis For Corporate Network Efficacy Cloud Security ModelThis slide depicts the comparison between SASE and other approaches for corporate network efficacy. The purpose of this slide is to demonstrate the various network security approaches and their comparison based on latency, management, app prioritization, and unified provisioning. Increase audience engagement and knowledge by dispensing information using Comparative Analysis For Corporate Network Efficacy Cloud Security Model. This template helps you present information on five stages. You can also present information on Security, Backhauls, Web using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Comparison Between Secure Access Service Edge And SD WAN Cloud Security Model
Comparison Between Secure Access Service Edge And SD WAN Cloud Security ModelThis slide compares secure access service edge and software defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Present the topic in a bit more detail with this Comparison Between Secure Access Service Edge And SD WAN Cloud Security Model. Use it as a tool for discussion and navigation on Deployment, Architecture, Security. This template is free to edit as deemed fit for your organization. Therefore download it now.





