Powerpoint Templates and Google slides for Security Checklist
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cloud Security Checklist Backup And Data Recovery Cloud Computing Security
Cloud Security Checklist Backup And Data Recovery Cloud Computing SecurityThis slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Backup And Data Recovery Cloud Computing Security. This template helps you present information on three stages. You can also present information on Cyber Attacks, Physical Location, Backup And Recovery Plans using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Data Encryption Cloud Computing Security
Cloud Security Checklist Data Encryption Cloud Computing SecurityThis slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. Introducing Cloud Security Checklist Data Encryption Cloud Computing Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Public Keys, Private Keys, Data Servers, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Logging And Monitoring Cloud Computing Security
Cloud Security Checklist Logging And Monitoring Cloud Computing SecurityThis slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Logging And Monitoring Cloud Computing Security. This template helps you present information on five stages. You can also present information on Future Evaluation, Organization, Policy Change Activities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Networking Cloud Computing Security
Cloud Security Checklist Networking Cloud Computing SecurityThis slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks. Introducing Cloud Security Checklist Networking Cloud Computing Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Critical Data, Cloud Security Checklist, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Policies And Procedures Cloud Computing Security
Cloud Security Checklist Policies And Procedures Cloud Computing SecurityThis slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Policies And Procedures Cloud Computing Security. This template helps you present information on five stages. You can also present information on Organization, Cloud Security, Security Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Security Patches And Updates Cloud Computing Security
Cloud Security Checklist Security Patches And Updates Cloud Computing SecurityThis slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly. Introducing Cloud Security Checklist Security Patches And Updates Cloud Computing Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Organization, Advanced Security Tools, Security Measures, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Vulnerability Analysis Checklist
Cyber Security Vulnerability Analysis ChecklistThis slide contains the checklist of multiple human threats human error, dishonesty, social engineering attacks and general threats with their impact and probability to occur in the business. Introducing our premium set of slides with Cyber Security Vulnerability Analysis Checklist. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Human Threats, General Threats, Unsecure Devices. So download instantly and tailor it with your information.
-
 Checklist For Information Security Risk Assessment And Management Plan For Information Security
Checklist For Information Security Risk Assessment And Management Plan For Information SecurityThis slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status Deliver an outstanding presentation on the topic using this Checklist For Information Security Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Information, Management, Consequences using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Implement Cloud Security In Business Cloud Data Protection
Checklist To Implement Cloud Security In Business Cloud Data ProtectionThis slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Introducing Checklist To Implement Cloud Security In Business Cloud Data Protection to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispense information on Logging And Monitoring, Networking, Data Encryption, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Access Control Cloud Data Protection
Cloud Security Checklist Access Control Cloud Data ProtectionThis slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Introducing Cloud Security Checklist Access Control Cloud Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Cloud Services, Information, Data Servers, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Backup And Data Recovery Cloud Data Protection
Cloud Security Checklist Backup And Data Recovery Cloud Data ProtectionThis slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them. Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Backup And Data Recovery Cloud Data Protection. This template helps you present information on five stages. You can also present information on Data Servers, Location, Effective Data Plan using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Security Checklist Data Encryption Cloud Data Protection
Cloud Security Checklist Data Encryption Cloud Data ProtectionThis slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys. Introducing Cloud Security Checklist Data Encryption Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Data Servers, Network, Cloud, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Logging And Monitoring Cloud Data Protection
Cloud Security Checklist Logging And Monitoring Cloud Data ProtectionThis slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis. Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Logging And Monitoring Cloud Data Protection. This template helps you present information on five stages. You can also present information on Organization, Network, Security using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Security Checklist Networking Cloud Data Protection
Cloud Security Checklist Networking Cloud Data ProtectionThis slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks. Introducing Cloud Security Checklist Networking Cloud Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Ensure Security, Network, Critical Data, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Policies And Procedures Cloud Data Protection
Cloud Security Checklist Policies And Procedures Cloud Data ProtectionThis slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization. Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Policies And Procedures Cloud Data Protection. This template helps you present information on five stages. You can also present information on Organization, On Boarding Employees, Cloud Security using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Cloud Security Checklist Security Patches And Updates Cloud Data Protection
Cloud Security Checklist Security Patches And Updates Cloud Data ProtectionThis slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly. Introducing Cloud Security Checklist Security Patches And Updates Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Technologies, Organization, Servers, using this template. Grab it now to reap its full benefits.
-
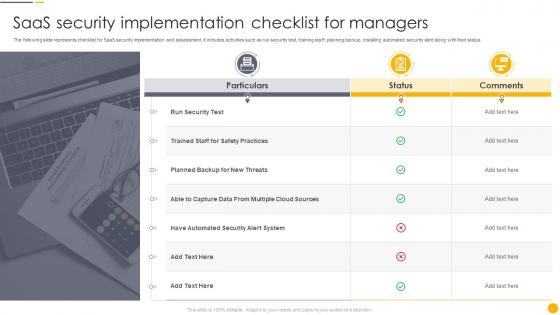 Saas Security Implementation Checklist For Managers
Saas Security Implementation Checklist For ManagersThe following slide represents checklist for SaaS security implementation and assessment. It includes activities such as run security test, training staff, planning backup, installing automated security alert along with their status. Presenting our well structured Saas Security Implementation Checklist For Managers. The topics discussed in this slide are Implementation, Automated, Represents. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Saas Security Maturity Assessment Checklist
Saas Security Maturity Assessment ChecklistThe following slide represents the SaaS security analysis to prevent data breaches and safeguards from cyber attacks. It constitutes of three security levels basic, intermediate and advanced based on that certain points are allocated and overall maturity is assessed. Introducing our Saas Security Maturity Assessment Checklist set of slides. The topics discussed in these slides are Analysis, Assessment, Intermediate. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Multipoint Checklist To Improve Information Technology Security
Multipoint Checklist To Improve Information Technology SecurityThis slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Presenting our well structured Multipoint Checklist To Improve Information Technology Security. The topics discussed in this slide are Control Administrative, Antivirus And Anti Malware, Email Phishing Training. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Threat Assessment Checklist With Solution
Cyber Security Threat Assessment Checklist With SolutionThe following slide highlights the cyber security threat assessment checklist with solution to assist management in decision making, id depicts threat, vulnerability, asset, consequences, risks and solution to control the risk. Introducing our Cyber Security Threat Assessment Checklist With Solution set of slides. The topics discussed in these slides are System Threat, Data Threat, Cloud Security Threat. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Third Party Cyber Security Implementation Checklist
Third Party Cyber Security Implementation ChecklistIntroducing our premium set of slides with name Third Party Cyber Security Implementation Checklist. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Third Party Cyber Security, Implementation Checklist. So download instantly and tailor it with your information.
-
 Checklist For Monthly Site Visit Security Report
Checklist For Monthly Site Visit Security ReportThis slide shows checklist which can be used to prepare monthly site visit security report. It includes points such as security officers wear inform, security officers have license, site have security cameras or not, etc. Introducing our Checklist For Monthly Site Visit Security Report set of slides. The topics discussed in these slides are Security Officers, Working Properly, Full Uniform. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Checklist To Improve Information Technology Security
Checklist To Improve Information Technology SecurityThis slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Presenting our set of slides with Checklist To Improve Information Technology Security. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Change Passwords Frequently, Email Phishing Training, Regular Firewall Holes Checking.
-
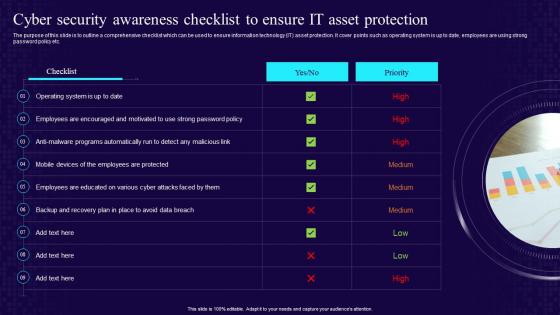 Developing Cyber Security Awareness Cyber Security Awareness Checklist To Ensure It Asset Protection
Developing Cyber Security Awareness Cyber Security Awareness Checklist To Ensure It Asset ProtectionThe purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Introducing Developing Cyber Security Awareness Cyber Security Awareness Checklist To Ensure It Asset Protection to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Security, Awareness Checklist, IT Asset Protection, using this template. Grab it now to reap its full benefits.
-
 Checklist For Information Security Risk Management Ppt Microsoft
Checklist For Information Security Risk Management Ppt MicrosoftThis slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Deliver an outstanding presentation on the topic using this Checklist For Information Security Risk Management Ppt Microsoft. Dispense information and present a thorough explanation of Checklist, Information Security, Risk Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist For Data Security Incident Management
Checklist For Data Security Incident ManagementIntroducing our Checklist For Data Security Incident Management set of slides. The topics discussed in these slides are Additional Data Losses, Response Team, Risk Assessment. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Checklist To Ensure Asset Protection From Internal Threats Security Incident Response Playbook
Checklist To Ensure Asset Protection From Internal Threats Security Incident Response PlaybookFollowing slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Deliver an outstanding presentation on the topic using this Checklist To Ensure Asset Protection From Internal Threats Security Incident Response Playbook. Dispense information and present a thorough explanation of Protection, Measures, Ensure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Incident Response Playbook Checklist For Work From Home Data Security
Security Incident Response Playbook Checklist For Work From Home Data SecurityDeliver an outstanding presentation on the topic using this Security Incident Response Playbook Checklist For Work From Home Data Security. Dispense information and present a thorough explanation of Remote, Workstations, Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Online Banking Security Measures Checklist For Fraud Prevention
Online Banking Security Measures Checklist For Fraud PreventionThis slide presents a checklist for increasing security, preventing loss from fraud activities and identifying theft in digital banking. It also shows status, impact and priority of activities. Introducing our Online Banking Security Measures Checklist For Fraud Prevention set of slides. The topics discussed in these slides are Online Banking, Security Measures Checklist, Fraud Prevention. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Architecture And Security Review Checklist For Effective Multi Cloud Automation And Management
Cloud Architecture And Security Review Checklist For Effective Multi Cloud Automation And ManagementThis slide covers the checklist for designing and implementation of the given elements of the multi cloud orchestration and automation efforts. Increase audience engagement and knowledge by dispensing information using Cloud Architecture And Security Review Checklist For Effective Multi Cloud Automation And Management. This template helps you present information on one stages. You can also present information on Orchestration Tool, Roles And Implementing Policies, Compatible Cloud Infrastructure, Environments Automatically using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Awareness Checklist To Ensure IT Asset Protection Conducting Security Awareness
Cyber Security Awareness Checklist To Ensure IT Asset Protection Conducting Security AwarenessThe purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Present the topic in a bit more detail with this Cyber Security Awareness Checklist To Ensure IT Asset Protection Conducting Security Awareness. Use it as a tool for discussion and navigation on Checklist, Operating System, Employees Encouraged. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Mobile Device Maintenance Checklist Enterprise Mobile Security For On Device
Determine Mobile Device Maintenance Checklist Enterprise Mobile Security For On DeviceThis slide provides information regarding mobile device maintenance checklist that is prepared, and essential activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver an outstanding presentation on the topic using this Determine Mobile Device Maintenance Checklist Enterprise Mobile Security For On Device. Dispense information and present a thorough explanation of Backup Monitoring, Preventive Maintenance, Virus Scanning using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Multistep Security Automation System Checklist
Multistep Security Automation System ChecklistThe following slide highlights a comprehensive checklist for security automation. The checklist covers key points such as deciding the budget, selecting the right tools, deciding the tasks for automation etc. Presenting our set of slides with name Multistep Security Automation System Checklist. This exhibits information on one stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Multistep, Security Automation System, Checklist.
-
 Cyber Security Incident Response Plan Checklist
Cyber Security Incident Response Plan ChecklistThis slide covers cyber security incident response plan checklist. It involves pre requisites such as identify fundamentals, terms and contracts, identify phases, team communication plan and incident response forms. Presenting our well structured Cyber Security Incident Response Plan Checklist. The topics discussed in this slide are Cyber Security, Incident Response, Plan Checklist. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Awareness Checklist To Ensure Implementing Security Awareness Training
Cyber Security Awareness Checklist To Ensure Implementing Security Awareness TrainingThe purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Deliver an outstanding presentation on the topic using this Cyber Security Awareness Checklist To Ensure Implementing Security Awareness Training. Dispense information and present a thorough explanation of Cyber Security, Awareness Checklist, Asset Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Mobile Device Maintenance Checklist Unified Endpoint Security
Determine Mobile Device Maintenance Checklist Unified Endpoint SecurityThis slide provides information regarding mobile device maintenance checklist that is prepared, and essential activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Introducing Determine Mobile Device Maintenance Checklist Unified Endpoint Security to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Preventive Maintenance, Virus Scanning, Executive Reporting, using this template. Grab it now to reap its full benefits.
-
 Information System Security And Risk Administration Plan Checklist For Information Security Risk
Information System Security And Risk Administration Plan Checklist For Information Security RiskThis slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Deliver an outstanding presentation on the topic using this Information System Security And Risk Administration Plan Checklist For Information Security Risk. Dispense information and present a thorough explanation of Process To Tackle Risks, Identify Vulnerabilities, Formulating Risk Management Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Incident Handling Checklist Ppt Powerpoint Presentation Model Introduction
Cyber Security Incident Handling Checklist Ppt Powerpoint Presentation Model IntroductionThis slide represents the checklist to ensure activities to effectively handle and manage cyber security incidents. It includes details related to detection and analysis, containment, eradication and recovery and post incident activity. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Handling Checklist Ppt Powerpoint Presentation Model Introduction. This template helps you present information on one stage. You can also present information on Detection And Analysis, Containment, Eradication And Recovery using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Checklist After An Incident Ppt Guidelines
Cyber Security Incident Management Checklist After An Incident Ppt GuidelinesThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management after the occurrence of the incident. Introducing Cyber Security Incident Management Checklist After An Incident Ppt Guidelines to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Cyber Security, Incident Management, Quantify Financial, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Incident Management Checklist Before An Incident Ppt Slides
Cyber Security Incident Management Checklist Before An Incident Ppt SlidesThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management before the occurrence of the incident. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Checklist Before An Incident Ppt Slides. This template helps you present information on one stage. You can also present information on Cyber Security, Incident Management, Technologies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Incident Management Checklist During An Incident Ppt Clipart
Cyber Security Incident Management Checklist During An Incident Ppt ClipartThis slide represents the checklist to effectively ensure activities aiming towards minimizing the impact of cyber security incidents on organizations. It includes checklist of cyber security incident management during the occurrence of the incident. Introducing Cyber Security Incident Management Checklist During An Incident Ppt Clipart to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Cyber Security, Incident Management, Executive Management, using this template. Grab it now to reap its full benefits.
-
 Enterprise Security Operation Center Audit Checklist
Enterprise Security Operation Center Audit ChecklistThis slide covers enterprise security operation center audit checklist. It involves vulnerability scan, employee cyber training, security provisions, asset management policy and network segmentation procedures. Introducing our Enterprise Security Operation Center Audit Checklist set of slides. The topics discussed in these slides are Employee Cyber Training Guide, Vulnerability Scan And Analysis, Incident Response Policy. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Checklist For Information Security Risk Management Cybersecurity Risk Analysis And Management Plan
Checklist For Information Security Risk Management Cybersecurity Risk Analysis And Management PlanThis slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status Introducing Checklist For Information Security Risk Management Cybersecurity Risk Analysis And Management Plan to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Management, Information, Different Vulnerabilities, using this template. Grab it now to reap its full benefits.
-
 Security System Evaluation Checklist To Enhance Effectiveness
Security System Evaluation Checklist To Enhance EffectivenessThis slide covers security system evaluation checklist to enhance effectiveness. It involves aspects such as vulnerability analysis, database hardening procedures, configuration management, access controls and network segmentation procedures. Introducing our Security System Evaluation Checklist To Enhance Effectiveness set of slides. The topics discussed in these slides are Security System Evaluation, Checklist, Enhance Effectiveness. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security For Remote Workplace Strategy Checklist
Cyber Security For Remote Workplace Strategy ChecklistThis slide represents cyber security for remote workplace checklist illustrating approval of remote platforms, employee training, deployment of firewall etc. Introducing our Cyber Security For Remote Workplace Strategy Checklist set of slides. The topics discussed in these slides are Cyber Security, Remote Workplace, Strategy Checklist. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Checklist For Information Security Risk Management Formulating Cybersecurity Plan
Checklist For Information Security Risk Management Formulating Cybersecurity PlanThis slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Present the topic in a bit more detail with this Checklist For Information Security Risk Management Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Identifying Potential, Different Vulnerabilities, Risk Management Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Erp Assessment Checklist To Improve It Security
Erp Assessment Checklist To Improve It SecurityThis slide signifies the enterprise resource planning evaluation to increase IT security. It covers information about automated testing tool, check system functionality and quality assurance etc. Presenting our well structured Erp Assessment Checklist To Improve It Security. The topics discussed in this slide are Business, Framework, Systems. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Checklist For Work From Home Data Security Cybersecurity Incident And Vulnerability
Checklist For Work From Home Data Security Cybersecurity Incident And VulnerabilityDeliver an outstanding presentation on the topic using this Checklist For Work From Home Data Security Cybersecurity Incident And Vulnerability. Dispense information and present a thorough explanation of Data Security, Reporting Process, Employees using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Awareness Checklist To Ensure It Asset Preventing Data Breaches Through Cyber Security
Cyber Security Awareness Checklist To Ensure It Asset Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Introducing Cyber Security Awareness Checklist To Ensure It Asset Preventing Data Breaches Through Cyber Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Employees, Data Breach, Operating System, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Checklist To Mitigate Threats Of Attack
Cyber Security Checklist To Mitigate Threats Of AttackThe given slide provides the key activities to be done to alleviate the effects of cyber threats. It includes managing social media profiles, backing up the data, crosschecking privacy and security settings etc. Introducing our premium set of slides with Cyber Security Checklist To Mitigate Threats Of Attack. Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security Checklist, Mitigate Threats Attack. So download instantly and tailor it with your information.
-
 Checklist For Work From Home Data Security Upgrading Cybersecurity With Incident Response Playbook
Checklist For Work From Home Data Security Upgrading Cybersecurity With Incident Response PlaybookDeliver an outstanding presentation on the topic using this Checklist For Work From Home Data Security Upgrading Cybersecurity With Incident Response Playbook. Dispense information and present a thorough explanation of Process, Technology, Standards using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Security Strategic Checklist For It Business
Cloud Security Strategic Checklist For It BusinessThis slide shows checklist which can be used by organizations to develop cloud security plan. It includes points such as change passwords every week, make multi factor authentication mandatory, enable anti phishing protections, etc. Presenting our well structured Cloud Security Strategic Checklist For It Business. The topics discussed in this slide are Cloud Security, Strategic Checklist, Business. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Workplace Safety And Security Inspection Checklist
Workplace Safety And Security Inspection ChecklistThis slide shows comprehensive checklist which can be used to measure safety and security in organization. It includes points such as whether CCTVs are working or employees wear id card or not etc. Presenting our well structured Workplace Safety And Security Inspection Checklist. The topics discussed in this slide are Employee Wear Id Badges, Employee Safety Training, Cyber Systems. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Software Checklist To Respond Cyber Security Incidents
Software Checklist To Respond Cyber Security IncidentsThis slide provides checklist of operating systems used in responding to cyber threat incidents. The purpose of this checklist is to use most appropriate software to respond and to reduce risk. It includes incidents such as information leakage, password change, data stealing etc.Presenting our well structured Software Checklist To Respond Cyber Security Incidents. The topics discussed in this slide are Confidential Information, Misleading Advertising, Hacker Changed. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Checklist For API Security Testing Practices
Checklist For API Security Testing PracticesThis slide illustrates list of best practices for API security testing to ensure it is thorough. It includes budget resources and time, define the test types to run, etc. Introducing our Checklist For API Security Testing Practices set of slides. The topics discussed in these slides are Establish Overall, Budget Resources, Security Testing. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Secured Transactions Checklist In Powerpoint And Google Slides Cpb
Secured Transactions Checklist In Powerpoint And Google Slides CpbPresenting our Secured Transactions Checklist In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Secured Transactions Checklist This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Ultimate Guide For Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS
Ultimate Guide For Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SSThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Ultimate Guide For Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS Use it as a tool for discussion and navigation on Network Security, Node Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IaaS Security Protocol Customer Checklist
IaaS Security Protocol Customer ChecklistThis side highlights IaaS security protocol customer checklist. It includes various tasks such as understand provider security model, encryption data at rest, consistent patching, inventory and assess management. Presenting our well structured IaaS Security Protocol Customer Checklist. The topics discussed in this slide are Tasks. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Policy Checklist For Creating Bring Your Own Device Policy
Cyber Security Policy Checklist For Creating Bring Your Own Device PolicyThis slide represents the checklist for creating a BYOD policy, including the key considerations such as the list of allowed devices and apps, payment agreement, and so on. Deliver an outstanding presentation on the topic using this Cyber Security Policy Checklist For Creating Bring Your Own Device Policy. Dispense information and present a thorough explanation of Considerations, Agreement, Represents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Policy Checklist For Writing An Effective It Policy
Cyber Security Policy Checklist For Writing An Effective It PolicyThis slide describes the checklist for an effective information technology policy, and it includes all the best practices that should be considered while writing an IT policy. Present the topic in a bit more detail with this Cyber Security Policy Checklist For Writing An Effective It Policy. Use it as a tool for discussion and navigation on Assessment, Essential, Weaknesses. This template is free to edit as deemed fit for your organization. Therefore download it now.





