Powerpoint Templates and Google slides for Security Checklist
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Team Skills Improvement Checklist
Cyber Security Team Skills Improvement ChecklistThis slide explores a checklist for enhancing cybersecurity team skills ensuring robust training and skill development to build defenses against evolving cyber threats. Introducing our Cyber Security Team Skills Improvement Checklist set of slides. The topics discussed in these slides are Training Workshops, Skill Assessments, Hands On Exercises, Incident Response Drills. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 IOT Security Platform Consideration Checklist
IOT Security Platform Consideration ChecklistThis slide showcases checklist for considering factors while selecting IoT security platform. Key features of platform covered are compliance certificate, access control protection, data securing, etc. Introducing our IOT Security Platform Consideration Checklist set of slides. The topics discussed in these slides are Features, Network Devices, Ensures Communication Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Checklist To Optimize Security Of Wireless Lan Network
Checklist To Optimize Security Of Wireless Lan NetworkThis slide represents checklist that helps network and security teams of companies enhance wireless LAN protection efficiently. It includes various points such as preferring 802.1x authentication, conducting wireless scan, etc. Introducing our Checklist To Optimize Security Of Wireless Lan Network set of slides. The topics discussed in these slides are Checklist, Status, CommentsThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Checklist To Secure Commercial Building Premises
Checklist To Secure Commercial Building PremisesThis slide showcases the checklist safeguarding commercial building premises which helps an organization to protect companys assets,property and occupants from malicious threats. It include details such as organize risk assessment,analyze security vulnerabilities,etc. Presenting our well structured Checklist To Secure Commercial Building Premises. The topics discussed in this slide are Organize Risks Assessment,Analyze Security Vulnerabilities,Set Security Perimeter. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Checklist To Conduct Web Security In Organization
Checklist To Conduct Web Security In OrganizationThis slide showcases actions performed while conducting web security in an organization which include actions, person responsible, status, etc. Present the topic in a bit more detail with this Checklist To Conduct Web Security In Organization. Use it as a tool for discussion and navigation on Authentication And Authorization, Session Management, Connectivity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Incident Response Plan Checklist For Organizations
Security Incident Response Plan Checklist For OrganizationsThis slide showcases the security incident response plan checklist. The purpose of this slide is to help the business ensure all the tasks are completed in order to prevent security incident. It includes elements such as incident identification, containment and mitigation, etc. Introducing our Security Incident Response Plan Checklist For Organizations set of slides. The topics discussed in these slides are Time, Activity, Person Responsible. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Essential Checklist For Security Configuration Management
Essential Checklist For Security Configuration ManagementThis slide depicts the important components required for security configuration management. This slide suggest disabling unnecessary accounts, changing passwords, authentication, best practices, etc. Presenting our well structured Essential Checklist For Security Configuration Management. The topics discussed in this slide are Disable Unnecessary Accounts, Change Default Passwords, Remove Unnecessary Software. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Checklist To Ensure Mobile Application Security Mobile Device Security Cybersecurity SS
Checklist To Ensure Mobile Application Security Mobile Device Security Cybersecurity SSThis slide showcases checklist that can help to improve mobile application security. It can help to safeguard data in organization and protect confidential information. Present the topic in a bit more detail with this Checklist To Ensure Mobile Application Security Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Update Devices In Organization, Conduct Security Training For Users This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Network Security Audit Checklist
IT Network Security Audit ChecklistThis slide exhibits systematic assessment of security postures of organizations IT infrastructure to protect against various threats. It includdes aspects such as access control, network security measures, incident response, etc. Introducing our IT Network Security Audit Checklist set of slides. The topics discussed in these slides are Tasks, Aspects, Applicable. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Supply Chain Security Checklist To Prevent Cyber Attacks
Supply Chain Security Checklist To Prevent Cyber AttacksThis slide represents checklist that helps companies to enhance their supply chain security and prevent suppliers from potential cyberattacks effectively. It includes various parameters such as documenting supply chain security plan, conducting suppliers meeting, etc. Presenting our well structured Supply Chain Security Checklist To Prevent Cyber Attacks. The topics discussed in this slide are Supply Chain Security Plan, Network, Evaluation Processes. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Value Investing Checklist To Manage Securities
Value Investing Checklist To Manage SecuritiesThis slide showcases stock marketers value investment checklist. It includes steps to look out such as fundamental analysis, analyse financial reports, ratio analysis and final evaluation. Presenting our well structured Value Investing Checklist To Manage Securities The topics discussed in this slide are Investment Option, Real Estate AssetsThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Ensuring Checklist For Mobile Security Deployment Contd Android Device Security Management
Ensuring Checklist For Mobile Security Deployment Contd Android Device Security ManagementThis slide provides information regarding mobile device security deployment checklist in terms of ensuring secure connections to corporate networks, prevent network based intrusion, centralized policies control and corporate directories. Introducing Ensuring Checklist For Mobile Security Deployment Contd Android Device Security Management to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Parameters, Ensuring Checklist, Mobile Security Deployment, using this template. Grab it now to reap its full benefits.
-
 Ensuring Checklist For Mobile Security Deployment Management And Monitoring
Ensuring Checklist For Mobile Security Deployment Management And MonitoringThis slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Introducing Ensuring Checklist For Mobile Security Deployment Management And Monitoring to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Ensuring Checklist, Mobile Security Deployment, using this template. Grab it now to reap its full benefits.
-
 Ensuring Checklist For Mobile Security Deployment Enterprise Mobile Security For On Device
Ensuring Checklist For Mobile Security Deployment Enterprise Mobile Security For On DeviceThis slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Deliver an outstanding presentation on the topic using this Ensuring Checklist For Mobile Security Deployment Enterprise Mobile Security For On Device. Dispense information and present a thorough explanation of Enforcing Effective, Automatic Configuration, Effective Handling using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ensuring Checklist For Mobile Security Deployment Unified Endpoint Security
Ensuring Checklist For Mobile Security Deployment Unified Endpoint SecurityThis slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Introducing Ensuring Checklist For Mobile Security Deployment Unified Endpoint Security to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Password Protection, Automatic Configuration, Patches Management, using this template. Grab it now to reap its full benefits.
-
 Managing Mobile Device Solutions For Workforce Ensuring Checklist For Mobile Security Deployment
Managing Mobile Device Solutions For Workforce Ensuring Checklist For Mobile Security DeploymentThis slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Present the topic in a bit more detail with this Managing Mobile Device Solutions For Workforce Ensuring Checklist For Mobile Security Deployment. Use it as a tool for discussion and navigation on Device Security, Protection Against, Malicious Codes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managing Mobile Devices For Optimizing Ensuring Checklist For Mobile Security Deployment
Managing Mobile Devices For Optimizing Ensuring Checklist For Mobile Security DeploymentThis slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Present the topic in a bit more detail with this Managing Mobile Devices For Optimizing Ensuring Checklist For Mobile Security Deployment. Use it as a tool for discussion and navigation on Parameters, Protection, Malicious Codes, Mobile Security Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Complete electronic information security implementation checklist
Complete electronic information security implementation checklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Increase audience engagement and knowledge by dispensing information using Complete Electronic Information Security Implementation Checklist. This template helps you present information on nine stages. You can also present information on Frequent Staff Training, Antivirus Software, Strong Passwords, Recovery Planning, Strong IT Policies, Device Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Employer secure documents checklist ppt powerpoint presentation infographics clipart cpb
Employer secure documents checklist ppt powerpoint presentation infographics clipart cpbPresenting Employer Secure Documents Checklist Ppt Powerpoint Presentation Infographics Clipart Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Employer Secure Documents Checklist. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 System disposal checklist effective information security risk management process
System disposal checklist effective information security risk management processMentioned slide shows system disposal checklist. It covers information such as system requirement, its compliance and remarks.Deliver an outstanding presentation on the topic using this System Disposal Checklist Effective Information Security Risk Management Process. Dispense information and present a thorough explanation of Stored Information Is Removed, Hardcopy Information, Requirement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 System management checklist effective information security risk management process
System management checklist effective information security risk management processFollowing slide displays system management checklist. It includes system management activities and frequency of performing them.Present the topic in a bit more detail with this System Management Checklist Effective Information Security Risk Management Process. Use it as a tool for discussion and navigation on System Monitoring, Security Patches, Virus Scanning . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information security risk management checklist
Information security risk management checklistMentioned slide shows checklist which can be used for information security risk management. The checklist covers multiple points such as security audit, establishing physical security, limit user permission, run regular software update etc. Introducing our Information Security Risk Management Checklist set of slides. The topics discussed in these slides are Security, Risk, Protected. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Key activities checklist associated to managing critical threat vulnerabilities and security threats
Key activities checklist associated to managing critical threat vulnerabilities and security threatsThis slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Introducing Key Activities Checklist Associated To Managing Critical Threat Vulnerabilities And Security Threats to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Plan And Collect, Review And Analyze, Develop Strategic Framework, using this template. Grab it now to reap its full benefits.
-
 Endpoint security controls checklist ppt powerpoint presentation infographic template cpb
Endpoint security controls checklist ppt powerpoint presentation infographic template cpbPresenting our Endpoint Security Controls Checklist Ppt Powerpoint Presentation Infographic Template Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Endpoint Security Controls Checklist This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security And Safety Checklist For Hotel Industry
Security And Safety Checklist For Hotel IndustryThis slide covers checklist for ensuring safety of visitors at hotels. The checklist includes security screening of bags, professional security team and screening of people at entrance. Introducing our Security And Safety Checklist For Hotel Industry set of slides. The topics discussed in these slides are Security And Safety Checklist For Hotel Industry. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security checklist project analysis templates bundle ppt slides
Security checklist project analysis templates bundle ppt slidesIncrease audience engagement and knowledge by dispensing information using Security Checklist Project Analysis Templates Bundle Ppt Slides. This template helps you present information on one stages. You can also present information on Project It Project, Human Threats, General Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Complete Information Security Implementation Checklist
Information Security Complete Information Security Implementation ChecklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Present the topic in a bit more detail with this Information Security Complete Information Security Implementation Checklist. Use it as a tool for discussion and navigation on Information, Security, Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Cybersecurity Checklist Effectively Managing Asset Security
Information Security Program Cybersecurity Checklist Effectively Managing Asset SecurityFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Present the topic in a bit more detail with this Information Security Program Cybersecurity Checklist Effectively Managing Asset Security. Use it as a tool for discussion and navigation on Checklist For Effectively Managing Asset Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Framework For Information Security System Disposal Checklist
Risk Management Framework For Information Security System Disposal ChecklistMentioned slide shows system disposal checklist. It covers information such as system requirement, its compliance and remarks. Deliver an outstanding presentation on the topic using this Risk Management Framework For Information Security System Disposal Checklist. Dispense information and present a thorough explanation of Stored Information, Requirement, All Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Framework For Information Security System Management Checklist
Risk Management Framework For Information Security System Management ChecklistFollowing slide displays system management checklist. It includes system management activities and frequency of performing them. Present the topic in a bit more detail with this Risk Management Framework For Information Security System Management Checklist. Use it as a tool for discussion and navigation on System Monitoring, Data Backup, Security Patches, Virus Scanning. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist For Effectively Managing Asset Security Risk Based Methodology To Cyber
Checklist For Effectively Managing Asset Security Risk Based Methodology To CyberFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them.Increase audience engagement and knowledge by dispensing information using Checklist For Effectively Managing Asset Security Risk Based Methodology To Cyber This template helps you present information on one stage. You can also present information on System Monitoring, Data Backup, Security Patches using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Checklist For Effectively Managing Asset Security Introducing A Risk Based Approach
Checklist For Effectively Managing Asset Security Introducing A Risk Based ApproachFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them.Introducing Checklist For Effectively Managing Asset Security Introducing A Risk Based Approach to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on System Monitoring, Virus Scanning, System Monitoring using this template. Grab it now to reap its full benefits.
-
 Security termination checklist ppt powerpoint presentation infographic cpb
Security termination checklist ppt powerpoint presentation infographic cpbPresenting Security Termination Checklist Ppt Powerpoint Presentation Infographic Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Termination Checklist. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber security risk management key activities checklist associated to insider threat
Cyber security risk management key activities checklist associated to insider threatThis slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Deliver an outstanding presentation on the topic using this Cyber Security Risk Management Key Activities Checklist Associated To Insider Threat. Dispense information and present a thorough explanation of Plan And Collet, Review And Analyze, Develop Strategic Framework, Track Present Inventory using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Checklist Mandatory Documents Required Iso 27001 Certification
Information Security And Iso 27001 Checklist Mandatory Documents Required Iso 27001 CertificationFollowing slide displays checklist of mandatory documents required to get ISO 27001 certification along with the status. Present the topic in a bit more detail with this Information Security And Iso 27001 Checklist Mandatory Documents Required Iso 27001 Certification. Use it as a tool for discussion and navigation on Mandatory, Documents, Required. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 It Asset Disposal Checklist
Information Security And Iso 27001 It Asset Disposal ChecklistThis slide displays IT asset disposal checklist. It includes information such as system requirement, its compliance and remarks. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 It Asset Disposal Checklist. Dispense information and present a thorough explanation of It Asset Disposal Checklist using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Complete Network Security Implementation Checklist
Network Security Complete Network Security Implementation ChecklistThis slide depicts the network security checklist and measures an organization should take to protect data and company assets from network attacks or natural disasters. Introducing Network Security Complete Network Security Implementation Checklist to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Complete Network Security Implementation Checklist, using this template. Grab it now to reap its full benefits.
-
 Checklist For Selecting Operational Technology Security Vendor
Checklist For Selecting Operational Technology Security VendorFollowing slide shows a comprehensive operational technology OT checklist which can be used by an organization for selecting the security vendor. organization can select the best security vendor for improving OT security system after considering points such as vendor understanding regard to OT and IT risk assessment etc. Deliver an outstanding presentation on the topic using this Checklist For Selecting Operational Technology Security Vendor. Dispense information and present a thorough explanation of Checklist, Vendor Understand OT, IT Risk Assessment, Digital Transformation Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
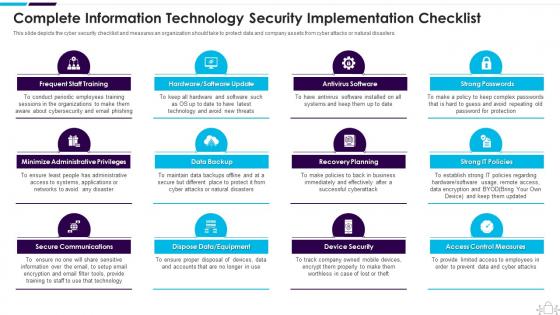 Information Technology Security Complete Information Security Implementation Checklist
Information Technology Security Complete Information Security Implementation ChecklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Introducing Information Technology Security Complete Information Security Implementation Checklist to increase your presentation threshold. Encompassed with twelve stages, this template is a great option to educate and entice your audience. Dispence information on Frequent Staff Training, Administrative Privileges, Data Backup, using this template. Grab it now to reap its full benefits.
-
 Ai Transformation Playbook Stage Five Security Breach Readiness Checklist
Ai Transformation Playbook Stage Five Security Breach Readiness ChecklistPurpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions.Present the topic in a bit more detail with this Ai Transformation Playbook Stage Five Security Breach Readiness Checklist Use it as a tool for discussion and navigation on Proper Risk Management, Each Organizational, Governance Procedures This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan workplace physical security audit checklist
Building organizational security strategy plan workplace physical security audit checklistThis slide provides information about physical security audit checklist at workplace in terms of general, roofing, HVAC, plumbing, lighting, etc. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Workplace Physical Security Audit Checklist. Use it as a tool for discussion and navigation on Workplace, Physical, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
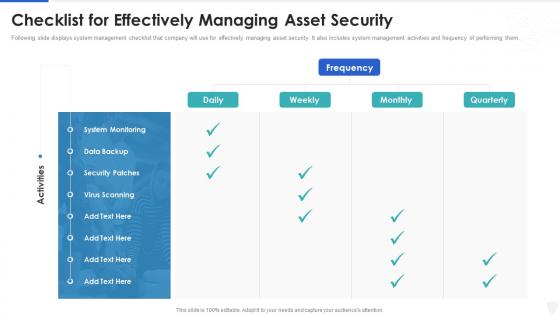 Cybersecurity and digital business risk management checklist for effectively managing asset security
Cybersecurity and digital business risk management checklist for effectively managing asset securityFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Present the topic in a bit more detail with this Cybersecurity And Digital Business Risk Management Checklist For Effectively Managing Asset Security. Use it as a tool for discussion and navigation on System Monitoring, Data Backup, Security Patches . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Effective Mobile Device Management Ensuring Checklist For Mobile Security Deployment
Effective Mobile Device Management Ensuring Checklist For Mobile Security DeploymentThis slide provides information regarding mobile device security deployment checklist in terms of device security, protection against malicious codes. Present the topic in a bit more detail with this Effective Mobile Device Management Ensuring Checklist For Mobile Security Deployment. Use it as a tool for discussion and navigation on Ensuring Checklist For Mobile Security Deployment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 AIOps Playbook Stage Five Security Breach Readiness Checklist Ppt Topics
AIOps Playbook Stage Five Security Breach Readiness Checklist Ppt TopicsPurpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions. Introducing AIOps Playbook Stage Five Security Breach Readiness Checklist Ppt Topics to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Stage Five Security Breach Readiness Checklist, using this template. Grab it now to reap its full benefits.
-
 Stage Five Security Breach Readiness Checklist Artificial Intelligence Playbook For Business
Stage Five Security Breach Readiness Checklist Artificial Intelligence Playbook For BusinessPurpose of this slide is to illustrate readiness checklist that will assist businesses in countering any security breach in advance. Readiness level will be evaluated based on different questions. Introducing Stage Five Security Breach Readiness Checklist Artificial Intelligence Playbook For Business to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Organizational Procedure, IT Operations, Operational Team, using this template. Grab it now to reap its full benefits.
-
 Determine Mobile Device Maintenance Checklist Android Device Security Management
Determine Mobile Device Maintenance Checklist Android Device Security ManagementThis slide provides information regarding mobile device maintenance checklist that is prepared, and essential activities mentioned will be performed on daily, weekly, monthly or quarterly basis. Deliver an outstanding presentation on the topic using this Determine Mobile Device Maintenance Checklist Android Device Security Management. Dispense information and present a thorough explanation of Activities, Preventive Maintenance, Planning Meeting using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Incident Response Playbook Checklist For Work From Home Data Security
Incident Response Playbook Checklist For Work From Home Data SecurityIncrease audience engagement and knowledge by dispensing information using Incident Response Playbook Checklist For Work From Home Data Security. This template helps you present information on one stages. You can also present information on Training, Policies, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Checklist To Implement Cloud Security In Business Cloud Information Security
Checklist To Implement Cloud Security In Business Cloud Information SecurityThis slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc.Introducing Checklist To Implement Cloud Security In Business Cloud Information Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Impact Analysis, Recovery Strategies, Plan Development using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Access Control Cloud Information Security
Cloud Security Checklist Access Control Cloud Information SecurityThis slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management.Introducing Cloud Security Checklist Access Control Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Service Provider, Physical Access, Natural Disasters using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Backup And Data Recovery Cloud Information Security
Cloud Security Checklist Backup And Data Recovery Cloud Information SecurityThis slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them.Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Backup And Data Recovery Cloud Information Security This template helps you present information on five stages. You can also present information on Sensitive Information, Encode Sensitive, Encrypted Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Data Encryption Cloud Information Security
Cloud Security Checklist Data Encryption Cloud Information SecurityThis slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys.Introducing Cloud Security Checklist Data Encryption Cloud Information Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Future Evaluation, Device Is Detected, Change Activities using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Logging And Monitoring Cloud Information Security
Cloud Security Checklist Logging And Monitoring Cloud Information SecurityThis slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis.Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Logging And Monitoring Cloud Information Security This template helps you present information on five stages. You can also present information on Data Supposed, Malware Mechanisms, Security Precautions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Networking Cloud Information Security
Cloud Security Checklist Networking Cloud Information SecurityThis slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks.Introducing Cloud Security Checklist Networking Cloud Information Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implement Policies, Security Solutions, Boarding Employees using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Policies And Procedures Cloud Information Security
Cloud Security Checklist Policies And Procedures Cloud Information SecurityThis slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization.Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Policies And Procedures Cloud Information Security This template helps you present information on four stages. You can also present information on Measures Organization, Technologies Security, Latest Advanced using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Security Patches And Updates Cloud Information Security
Cloud Security Checklist Security Patches And Updates Cloud Information SecurityThis slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly.Introducing Cloud Security Checklist Security Patches And Updates Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Revenue Losses, Compliance Violations, Malware Attacks using this template. Grab it now to reap its full benefits.
-
 Cyber Security Awareness Checklist Building A Security Awareness Program
Cyber Security Awareness Checklist Building A Security Awareness ProgramThe purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Introducing Cyber Security Awareness Checklist Building A Security Awareness Program to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Operating System, Programs Automatically, Asset Protection, using this template. Grab it now to reap its full benefits.
-
 Security Policy Checklist Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Security Policy Checklist Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Security policy checklist colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Security Policy Checklist Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Security Policy Checklist Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Security policy checklist monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Cloud Computing Security Checklist To Implement Cloud Security In Business
Cloud Computing Security Checklist To Implement Cloud Security In BusinessThis slide shows the checklist to implement cloud security in business, including policies and procedures, access control, networking, backup data, security patches, etc. Introducing Cloud Computing Security Checklist To Implement Cloud Security In Business to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Logging And Monitoring, Data Encryption, Backup And Data Recovery, Policies And Procedures, Networking, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Access Control Cloud Computing Security
Cloud Security Checklist Access Control Cloud Computing SecurityThis slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Introducing Cloud Security Checklist Access Control Cloud Computing Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Multi Factor Authorization, Cloud Services, Networks, using this template. Grab it now to reap its full benefits.





