Powerpoint Templates and Google slides for Security Checklist
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Checklist For Organizations Training Ppt
Cyber Security Checklist For Organizations Training PptPresenting Cyber Security Checklist for Organizations. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Tick icon circle security mark sign checklist project
Tick icon circle security mark sign checklist projectIntroduce your topic and host expert discussion sessions with this Tick Icon Circle Security Mark Sign Checklist Project. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the twelve slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Firewall Network Security Checklist For Firewall Rules Configuration
Firewall Network Security Checklist For Firewall Rules ConfigurationThis slide outlines the best practices for firewall regulation configurations. The purpose of this slide is to showcase the different measures that businesses should keep in mind while performing firewall rules configuration, including planning firewall deployment, setting firewall rules, setting explicitly drop regulations, etc. Present the topic in a bit more detail with this Firewall Network Security Checklist For Firewall Rules Configuration Use it as a tool for discussion and navigation on Plan Firewall Deployment, Keep Audit Logs This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Post Incident Review Checklist Business Recovery Plan To Overcome Cyber Security Threat
Cyber Post Incident Review Checklist Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about the incident assessment checklist. It includes key assessment areas such as incident documentation, communication, incident response team activation, containment of threats, etc. Present the topic in a bit more detail with this Cyber Post Incident Review Checklist Business Recovery Plan To Overcome Cyber Security Threat. Use it as a tool for discussion and navigation on Communication, Response Team, Contain Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web hosting security checklist ppt powerpoint presentation pictures demonstration cpb
Web hosting security checklist ppt powerpoint presentation pictures demonstration cpbPresenting Web Hosting Security Checklist Ppt Powerpoint Presentation Pictures Demonstration Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Web Hosting Security Checklist. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
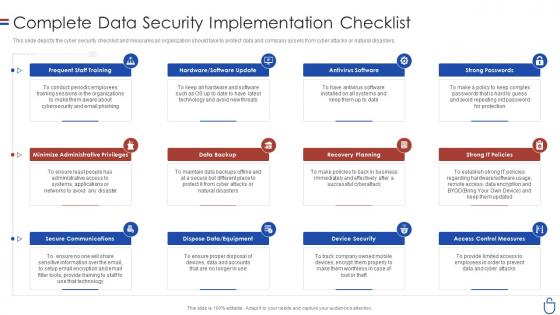 Data security it complete data security implementation checklist
Data security it complete data security implementation checklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Introducing Data Security IT Complete Data Security Implementation Checklist to increase your presentation threshold. Encompassed with twelve stages, this template is a great option to educate and entice your audience. Dispence information on Frequent Staff Training, Antivirus Software, Strong Passwords, Minimize Administrative Privileges, Data Backup, Recovery Planning, Strong IT Policies, Secure Communications, Device Security, using this template. Grab it now to reap its full benefits.
-
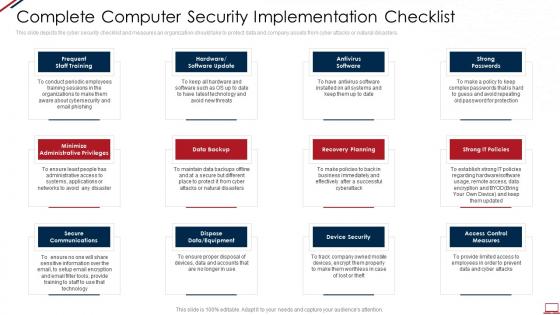 Computer system security complete computer security implementation checklist
Computer system security complete computer security implementation checklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Increase audience engagement and knowledge by dispensing information using Computer System Security Complete Computer Security Implementation Checklist. This template helps you present information on twelve stages. You can also present information on Data Backup, Secure Communications, Recovery Planning, Strong Passwords, Device Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Audit Smart Contracts With Review Checklist Security Token Offerings BCT SS
Audit Smart Contracts With Review Checklist Security Token Offerings BCT SSThe following slide depicts smart contract review checklist to ensure security and trustworthiness. It includes elements such as pre requisites, core checks, automation, manual testing, resiliency, auditing, etc. Deliver an outstanding presentation on the topic using this Audit Smart Contracts With Review Checklist Security Token Offerings BCT SS. Dispense information and present a thorough explanation of Review Agreement, Blockchain Operations, Performance Summary using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Develop Checklist To Review KYC And AML Policy Security Token Offerings BCT SS
Develop Checklist To Review KYC And AML Policy Security Token Offerings BCT SSThe following slide depicts KYC and AML policy checklist to prevent money laundering and ensure customer due diligence. It includes elements such as collect users personal data, verifying details, specifying duration for checking, defining actions for unverified clients, checking taxation laws, etc. Deliver an outstanding presentation on the topic using this Develop Checklist To Review KYC And AML Policy Security Token Offerings BCT SS. Dispense information and present a thorough explanation of Develop Checklist, Determine Whether, Verify User Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Review Legal Considerations With Due Diligence Checklist Security Token Offerings BCT SS
Review Legal Considerations With Due Diligence Checklist Security Token Offerings BCT SSThe following slide depicts due diligence checklist to cross-check legal concerns before security token offerings STO project launch. It includes elements such as anti-money laundering compliance, intellectual property safety, data protection, smart contracts inspection, etc. Present the topic in a bit more detail with this Review Legal Considerations With Due Diligence Checklist Security Token Offerings BCT SS. Use it as a tool for discussion and navigation on Regulation Assessment, Data Protection, Smart Contract Inspection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Security With Checklist Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security With Checklist Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis Data Security Action Plan Checklist Icon is a vibrant and colourful PowerPoint icon that is perfect for illustrating data security action plans. It is a great visual aid to help explain the importance of data security and the steps needed to ensure it.
-
 Data Security With Checklist Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security With Checklist Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Data Security Action Plan Checklist is perfect for presentations on data security and planning. It features a checklist to ensure all security measures are taken and provides a visual representation of the importance of data security.
-
 Folder Security With Checklist Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Folder Security With Checklist Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis Data Security Action Plan Checklist Icon is a vibrant and colourful PowerPoint icon that is perfect for illustrating data security action plans. It is a great visual aid to help explain the importance of data security and the steps needed to ensure it.
-
 Folder Security With Checklist Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Folder Security With Checklist Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Data Security Action Plan Checklist is perfect for presentations on data security and planning. It features a checklist to ensure all security measures are taken and provides a visual representation of the importance of data security.
-
 Checklist To Implement Secure Web Gateway Network Security Using Secure Web Gateway
Checklist To Implement Secure Web Gateway Network Security Using Secure Web GatewayThis slide represents the checklist to implement Secure Web Gateway for application security. The key components included are determine use case, select best solution, plan deployment, configure solution, test and improve, roll out and monitor. Deliver an outstanding presentation on the topic using this Checklist To Implement Secure Web Gateway Network Security Using Secure Web Gateway. Dispense information and present a thorough explanation of Configure Solution, Plan Deployment, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Storage Area Network San Checklist To Secure Storage Area Network Layers
Storage Area Network San Checklist To Secure Storage Area Network LayersThis Slide Represents The Checklist To Protect The SAN Architecture Layers. The Purpose Of This Slide Is To Showcase The Various Steps And Actions That Organizations Should Keep In Mind While Deploying Or Working With A SAN Environment. The Measures Include Changing Passwords, Setting Firewalls, Taking Inventory, Etc. Present The Topic In A Bit More Detail With This Storage Area Network San Checklist To Secure Storage Area Network Layers. Use It As A Tool For Discussion And Navigation On Organizations, Environment, Measures. This Template Is Free To Edit As Deemed Fit For Your Organization. Therefore Download It Now.
-
 Security Awareness Communication Plan Checklist
Security Awareness Communication Plan ChecklistThe slide showcases checklist that assist to evaluate if the tasks have been completed on the assigned date. It contains points such as security awareness plan, communication plan, agenda, etc. along with assigned to and additional comments. Introducing our Security Awareness Communication Plan Checklist set of slides. The topics discussed in these slides are Parameters, Additional, Communication. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS V
Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS VThis slide covers checklist for assessing vendor before integrating technology strategy in operations to enhance security. It involves key points such as IT risk assessment, threat and security experts and expertise in developing new technologies. Deliver an outstanding presentation on the topic using this Checklist For Vendor Assessment In Operational Technology Security Guide For Integrating Technology Strategy SS V. Dispense information and present a thorough explanation of Cloud Environments, Risk Arising, Digital Transformation Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Incident Response Checklist For Security Manager Job
Incident Response Checklist For Security Manager JobThis slide shows checklists for incident response security manager job which helps to identify errors in advance and track the performance of manager It further includes components such as create a policy, list of responsibilities and roles etc. Presenting our set of slides with Incident Response Checklist For Security Manager Job. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Components, Status, Manager.
-
 Comprehensive Guide To Understand Checklist To Ensure Security Of Bitcoin Wallets Fin SS
Comprehensive Guide To Understand Checklist To Ensure Security Of Bitcoin Wallets Fin SSThis slide shows checklist which can be used to adopt various security measure while using Bitcoin wallets. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Increase audience engagement and knowledge by dispensing information using Comprehensive Guide To Understand Checklist To Ensure Security Of Bitcoin Wallets Fin SS. This template helps you present information on one stages. You can also present information on Biometric Authentication, Monitor Regular Transactions History, Change Passwords Frequently using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Access Security Broker CASB V2 Checklist To Adopt A Cloud Access Security Broker
Cloud Access Security Broker CASB V2 Checklist To Adopt A Cloud Access Security BrokerThis slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Present the topic in a bit more detail with this Cloud Access Security Broker CASB V2 Checklist To Adopt A Cloud Access Security Broker. Use it as a tool for discussion and navigation on Cloud Access Security Broker, Cloud Requirements, Conduct Regular Audits. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Healthcare And Medical Security Compliance Checklist Icon
Healthcare And Medical Security Compliance Checklist IconIntroducing our premium set of slides with Healthcare And Medical Security Compliance Checklist Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Healthcare Medical Security, Compliance Checklist. So download instantly and tailor it with your information.
-
 Security Compliance Evaluation Checklist To Reduce Frauds
Security Compliance Evaluation Checklist To Reduce FraudsThis slide shows evaluation checklist for security compliance to identify areas of frauds and techniques to mitigate them. It further includes components such as does the system include a built in way of separating roles by qualified internal auditors etc. Presenting our set of slides with Security Compliance Evaluation Checklist To Reduce Frauds. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Components, Partially.
-
 ERP Product Security Management Criteria Checklist
ERP Product Security Management Criteria ChecklistThis slide showcases the ERP management criteria checklist. Its aim is to check for the selection criteria features. This slide includes quality, investment, business process reengineering, etc. Presenting our well structured ERP Product Security Management Criteria Checklist. The topics discussed in this slide are Drivers, Criteria, Checklist. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Checklist To Secure Organizations From Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Checklist To Secure Organizations From PhishingThis slide outlines the steps to be taken to protect the organization and its employees from phishing attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Checklist To Secure Organizations From Phishing. Use it as a tool for discussion and navigation on Phishing Attacks, Real Time Monitoring, Spam Filters, Multi Factor Authentication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Ensure Secure Mobile Banking E Wallets As Emerging Payment Method Fin SS V
Checklist To Ensure Secure Mobile Banking E Wallets As Emerging Payment Method Fin SS VThis slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Present the topic in a bit more detail with this Checklist To Ensure Secure Mobile Banking E Wallets As Emerging Payment Method Fin SS V. Use it as a tool for discussion and navigation on Measure, Transactions, Passwords Frequently. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Implement Secure Access Service Edge Cloud Security Model
Checklist To Implement Secure Access Service Edge Cloud Security ModelPresent the topic in a bit more detail with this Checklist To Implement Secure Access Service Edge Cloud Security Model. Use it as a tool for discussion and navigation on Service, Access, Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Checklist To Implement Secure Access Service Edge
Sase Security Checklist To Implement Secure Access Service EdgePresent the topic in a bit more detail with this Sase Security Checklist To Implement Secure Access Service Edge. Use it as a tool for discussion and navigation on Service, Implement, Secure Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Implement Secure Access Service Edge Secure Access Service Edge Sase
Checklist To Implement Secure Access Service Edge Secure Access Service Edge SaseDeliver an outstanding presentation on the topic using this Checklist To Implement Secure Access Service Edge Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Service, Responsible Person, Implement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Storage Security Based Checklist
Cloud Storage Security Based ChecklistThis slide outlines the cloud storage security checklist template that helps in right application to manage inventory. It includes important functions and features. Introducing our Cloud Storage Security Based Checklist set of slides. The topics discussed in these slides are Secure Sensitive Information, Physical Security Measures. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Review Cyber Security Status With Due Diligence Checklist Improving Cyber Security Risks Management
Review Cyber Security Status With Due Diligence Checklist Improving Cyber Security Risks ManagementThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Improving Cyber Security Risks Management. Use it as a tool for discussion and navigation on Disaster Recovery, Password And Encryption, Parameters. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE Network Security Checklist To Implement Secure Access Service Edge
SASE Network Security Checklist To Implement Secure Access Service EdgePresent the topic in a bit more detail with this SASE Network Security Checklist To Implement Secure Access Service Edge. Use it as a tool for discussion and navigation on Responsible, Service, Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Adopt Security Auditing Checklist To Verify Processes Hands On Blockchain Security Risk BCT SS V
Adopt Security Auditing Checklist To Verify Processes Hands On Blockchain Security Risk BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Adopt Security Auditing Checklist To Verify Processes Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Parameters, Description, Comments. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Functional Testing Checklist To Review Key Components Hands On Blockchain Security Risk BCT SS V
Functional Testing Checklist To Review Key Components Hands On Blockchain Security Risk BCT SS VThe following slide showcases checklist for functional testing to ensure blockchain security. It includes elements such as size of blockchain, addition of blocks, data transmission, API, integration, performance and security testing, etc. Present the topic in a bit more detail with this Functional Testing Checklist To Review Key Components Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Parameters, Description, Status. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist For Cyber Security Audit In Companies
Checklist For Cyber Security Audit In CompaniesThis slide covers online protection audits and provides details about parameters that give valuable insights to organizations before implementing cyber audits. It includes elements such as management, employees, etc. Introducing our Checklist For Cyber Security Audit In Companies set of slides. The topics discussed in these slides are Management, Company Security Policies Organizations, Security Policies Enforced. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Network Security Management Tasks Checklist Icon
Network Security Management Tasks Checklist IconIntroducing our premium set of slides with Network Security Management Tasks Checklist Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Security Management, Tasks Checklist Icon. So download instantly and tailor it with your information.
-
 NEO Banks For Digital Funds Checklist To Ensure Secure Mobile Banking Fin SS V
NEO Banks For Digital Funds Checklist To Ensure Secure Mobile Banking Fin SS VThis slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Present the topic in a bit more detail with this NEO Banks For Digital Funds Checklist To Ensure Secure Mobile Banking Fin SS V. Use it as a tool for discussion and navigation on Ensure Secure Mobile Banking, Change Passwords Frequently, Monitor Transactions, Public Networks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Blockchain And Cybersecurity Adopt Security Auditing Checklist To Verify Processes BCT SS V
Blockchain And Cybersecurity Adopt Security Auditing Checklist To Verify Processes BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Blockchain And Cybersecurity Adopt Security Auditing Checklist To Verify Processes BCT SS V Use it as a tool for discussion and navigation on Parameters, Description, Verify Processes This template is free to edit as deemed fit for your organization. Therefore download it now.
-
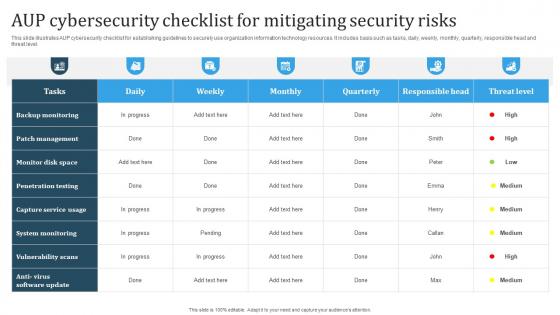 AUP Cybersecurity Checklist For Mitigating Security Risks
AUP Cybersecurity Checklist For Mitigating Security RisksThis slide illustrates AUP cybersecurity checklist for establishing guidelines to securely use organization information technology resources. It includes basis such as tasks, daily, weekly, monthly, quarterly, responsible head and threat level. Introducing our AUP Cybersecurity Checklist For Mitigating Security Risks set of slides. The topics discussed in these slides are Backup Monitoring, Patch Management, System Monitoring This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Checklist To Implement Data Breach Security Response Plan
Checklist To Implement Data Breach Security Response PlanThis slide depicts the checklist to execute response plans during data security breaches. The purpose of this checklist is to help the business ensure all suitable actions are implemented in order to prevent data leaks. It includes elements such as activity status, person responsible, etc. Presenting our well structured Checklist To Implement Data Breach Security Response Plan. The topics discussed in this slide are Isolate Affected Systems, Notify Appropriate Stakeholders, Identify The Nature. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS V
Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS V Dispense information and present a thorough explanation of Consensus Mechanism, Smart Contract Security, Data Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process
Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management ProcessThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Parameters, Tasks, Status, Reviews. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ransomware In Digital Age Ransomware Prevention Checklist For Security Teams
Ransomware In Digital Age Ransomware Prevention Checklist For Security TeamsThis slide represents the current status of ransomware prevention measures in an organization. The purpose of this slide is to showcase the status of different security measures such as data backups, antivirus software upgradation, network segmentation, etc. Present the topic in a bit more detail with this Ransomware In Digital Age Ransomware Prevention Checklist For Security Teams. Use it as a tool for discussion and navigation on Email Protection, Vulnerability Scanning And Patching, Backup Testing And Data Restoration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Adopt A Cloud Access Security Broker Next Generation CASB
Checklist To Adopt A Cloud Access Security Broker Next Generation CASBThis slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Deliver an outstanding presentation on the topic using this Checklist To Adopt A Cloud Access Security Broker Next Generation CASB Dispense information and present a thorough explanation of Vendor Landscape, Conduct A Trial, Functionalities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Everything About Mobile Banking Checklist To Ensure Secure Mobile Banking Fin SS V
Everything About Mobile Banking Checklist To Ensure Secure Mobile Banking Fin SS VThis slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Present the topic in a bit more detail with this Everything About Mobile Banking Checklist To Ensure Secure Mobile Banking Fin SS V. Use it as a tool for discussion and navigation on Ensure Secure Mobile Banking, Change Passwords Frequently, Monitor Transactions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Checklist To Implement Secure Access Service Edge
SD WAN Model Checklist To Implement Secure Access Service EdgePresent the topic in a bit more detail with this SD WAN Model Checklist To Implement Secure Access Service Edge. Use it as a tool for discussion and navigation on Test And Troubleshoot, Incorporate Zero Trust Solutions, Goals And Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Attacks Prevention Checklist To Secure Organizations From Social Engineering
Social Engineering Attacks Prevention Checklist To Secure Organizations From Social EngineeringThis slide outlines the steps to be taken to protect the organization and its employees from social engineering attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan. Present the topic in a bit more detail with this Social Engineering Attacks Prevention Checklist To Secure Organizations From Social Engineering. Use it as a tool for discussion and navigation on Provide Staff Training, Multi Factor Authentication, Develop An Incident Response Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Ensure Secure Mobile Smartphone Banking For Transferring Funds Digitally Fin SS V
Checklist To Ensure Secure Mobile Smartphone Banking For Transferring Funds Digitally Fin SS VThis slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Deliver an outstanding presentation on the topic using this Checklist To Ensure Secure Mobile Smartphone Banking For Transferring Funds Digitally Fin SS V. Dispense information and present a thorough explanation of Change Passwords Frequently, Monitor Regular Transactions History, Set Account Alerts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Banking Solutions For Improving Customer Checklist To Ensure Secure Mobile Banking Fin SS V
Banking Solutions For Improving Customer Checklist To Ensure Secure Mobile Banking Fin SS VThis slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Deliver an outstanding presentation on the topic using this Banking Solutions For Improving Customer Checklist To Ensure Secure Mobile Banking Fin SS V. Dispense information and present a thorough explanation of Mobile Banking, Change Passwords Frequently, Monitor Transactions, Avoid Using Public Networks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Saas Compliance Checklist For Organizational Security
Saas Compliance Checklist For Organizational SecurityThis slide presents organizational security checklist to manage governance and compliance requirements for SaaS businesses. It aims to provide assistance during the SaaS compliance journey for securing cloud-based applications. It covers elements such as determining compliance requirements, evaluating risks, assessing compliance level, formulating strategy, implementing controls, etc. Introducing our Saas Compliance Checklist For Organizational Security set of slides. The topics discussed in these slides are Data Handling Processes, Security Risks, Resource Requirements. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Adopt Security Auditing Checklist To Verify Processes Guide For Blockchain BCT SS V
Adopt Security Auditing Checklist To Verify Processes Guide For Blockchain BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Adopt Security Auditing Checklist To Verify Processes Guide For Blockchain BCT SS V Use it as a tool for discussion and navigation on Network Security, Node Security, Consensus Mechanism This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devsecops Best Practices For Secure Checklist To Implement Devsecops In Organization
Devsecops Best Practices For Secure Checklist To Implement Devsecops In OrganizationThis slide represents the checklist to implement the DevSecOps in an organization. The purpose of this slide is to provide key functional requirements for implementing and deploying the DevSecOps system in an enterprise environment. Present the topic in a bit more detail with this Devsecops Best Practices For Secure Checklist To Implement Devsecops In Organization. Use it as a tool for discussion and navigation on Security Training And Awareness, Collaboration And Communication, Security Automation, Vulnerability Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Checklist To Implement Secure Access Service Edge
Sase Model Checklist To Implement Secure Access Service EdgeDeliver an outstanding presentation on the topic using this Sase Model Checklist To Implement Secure Access Service Edge. Dispense information and present a thorough explanation of Steps, Responsible Person, Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Adopt Security Auditing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS V
Adopt Security Auditing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Present the topic in a bit more detail with this Adopt Security Auditing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS V. Use it as a tool for discussion and navigation on Parameters, Comments, Comply Safe Communication Protocols. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Functional Testing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS V
Functional Testing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide showcases checklist for functional testing to ensure blockchain security. It includes elements such as size of blockchain, addition of blocks, data transmission, API, integration, performance and security testing, etc. Introducing Functional Testing Checklist Securing Blockchain Transactions A Beginners Guide BCT SS V to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Size Of Blockchain, Addition Blocks, Data Transmission, using this template. Grab it now to reap its full benefits.
-
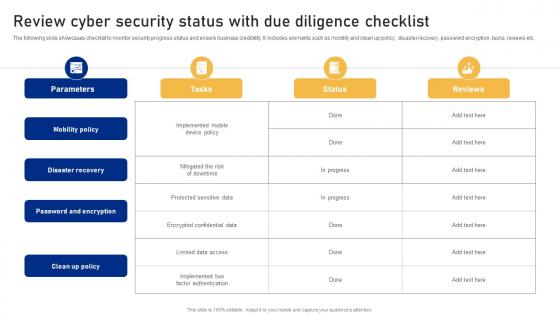 Review Cyber Security Status With Due Diligence Checklist Cyber Risk Assessment
Review Cyber Security Status With Due Diligence Checklist Cyber Risk AssessmentThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Cyber Risk Assessment Use it as a tool for discussion and navigation on Mobility Policy, Disaster Recovery, Password And Encryption This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Review Cyber Security Status With Due Diligence Checklist Creating Cyber Security Awareness
Review Cyber Security Status With Due Diligence Checklist Creating Cyber Security AwarenessThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Risk Probability, Risk Severity This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Ensure Secure Mobile Banking Digital Wallets For Making Hassle Fin SS V
Checklist To Ensure Secure Mobile Banking Digital Wallets For Making Hassle Fin SS VThis slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Present the topic in a bit more detail with this Checklist To Ensure Secure Mobile Banking Digital Wallets For Making Hassle Fin SS V. Use it as a tool for discussion and navigation on Secure, Banking, Mobile. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Devops Automation Checklist For Cloud Security
Devops Automation Checklist For Cloud SecurityThis slide showcases devOps automation checklist that helps to reduce manual errors and security operation automation. It includes elements such as cloud automation, access management, cloud resources, devOps pipeline, security testing and rapid detection. Introducing our Devops Automation Checklist For Cloud Securityset of slides. The topics discussed in these slides are Management Practices, Cloud Resources, Cloud Environment. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Checklist For Cryptography In Cyber Security
Checklist For Cryptography In Cyber SecurityThis slide covers a checklist for cryptography and provides details about the work of company to prioritize risk for systems. It includes elements such as patch management, system monitoring, etc. Introducing our Checklist For Cryptography In Cyber Security set of slides. The topics discussed in these slides are System Monitoring, Backup Monitoring, Vulnerability Scans . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.




