Powerpoint Templates and Google slides for Security Management
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Risk Associated With Identity And Access Management Process Securing Systems With Identity
Risk Associated With Identity And Access Management Process Securing Systems With IdentityThis slide outlines the potential hazards linked to the Identity and Access Management process. The purpose of this slide is to discuss the risks these include incorrectly defined roles and attributes, infrequent audits, and complex implementations. Introducing Risk Associated With Identity And Access Management Process Securing Systems With Identity to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Roles And Attributes, Infrequent Audits, Complex Implementations using this template. Grab it now to reap its full benefits.
-
 Roadmap For Identity And Access Management Implementation Securing Systems With Identity
Roadmap For Identity And Access Management Implementation Securing Systems With IdentityThis slide highlights the project roadmap to implement the Identity and Access Management process. The purpose of this slide is to showcase the different phases of the IAM implementation plan, such as implementing emerging IAM technologies, BYOI adoption, etc. Increase audience engagement and knowledge by dispensing information using Roadmap For Identity And Access Management Implementation Securing Systems With Identity This template helps you present information on Four stages. You can also present information on Iam Technologies, Byoi Adoption, Testing And Security Assurance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Role Of Identity And Access Management In Data Security Securing Systems With Identity
Role Of Identity And Access Management In Data Security Securing Systems With IdentityThis slide discusses the Identity and Access Management importance in data security. The purpose of this slide is to highlight the importance, including protecting business data, addressing new challenges, beyond perimeter security, combatting compromised credentials, and so on. Deliver an outstanding presentation on the topic using this Role Of Identity And Access Management In Data Security Securing Systems With Identity Dispense information and present a thorough explanation of Protecting Business Data, Combatting Compromised Credentials using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Securing Systems With Identity And Access Management Table Of Content
Securing Systems With Identity And Access Management Table Of ContentIntroducing Securing Systems With Identity And Access Management Table Of Content to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Introduction And Functions, Biometric Authentication using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Identity And Access Management In Enterprises Securing Systems With Identity
Steps To Implement Identity And Access Management In Enterprises Securing Systems With IdentityThis slide discusses the Identity and Access Management implementing process in enterprises. The purpose of this slide is to highlight the implementation process, including usage assessment, environment understanding, key IAM considerations, and so on. Introducing Steps To Implement Identity And Access Management In Enterprises Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Usage Assessment, Environment Understanding using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Identity And Access Management Securing Systems With Identity
Steps To Implement Identity And Access Management Securing Systems With IdentityThis slide discusses the Identity and Access Management implementing program. The purpose of this slide is to highlight the implementation process of IAM, including scope identification, evaluating the right IAM approach, finding the best solution, and so on. Increase audience engagement and knowledge by dispensing information using Steps To Implement Identity And Access Management Securing Systems With Identity This template helps you present information on Six stages. You can also present information on Scope Identification, Define A Strategy, Assess Cost Factors using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Streamlining Identity Management Process Within IAM Securing Systems With Identity
Streamlining Identity Management Process Within IAM Securing Systems With IdentityThis slide discusses the identity management of the Identity and Access Management process. The purpose of this slide is to explain identity management that relies on a combination of process, organizational structure, and enabling technologies. Introducing Streamlining Identity Management Process Within IAM Securing Systems With Identity to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Organization Structure, Processes, Technology using this template. Grab it now to reap its full benefits.
-
 Table Of Content For Securing Systems With Identity And Access Management
Table Of Content For Securing Systems With Identity And Access ManagementIncrease audience engagement and knowledge by dispensing information using Table Of Content For Securing Systems With Identity And Access Management This template helps you present information on One stages. You can also present information on Iam Overview, Training And Budget using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline To Implement Identity And Access Management Plan Securing Systems With Identity
Timeline To Implement Identity And Access Management Plan Securing Systems With IdentityThis slide shows the timeline for implementing the Identity and Access Management plan. The key steps include defining the project objective, identifying key stakeholders, determining compliance, integrating IAM with the existing system, etc. Introducing Timeline To Implement Identity And Access Management Plan Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Applications And Data, Public Cloud Platforms using this template. Grab it now to reap its full benefits.
-
 Understanding Of Identity And Access Management Securing Systems With Identity
Understanding Of Identity And Access Management Securing Systems With IdentityThis slide discusses the concepts of the Identity and Access Management process. The purpose of this slide is to explain the key components of IAM, including authentication, authorization, user management, and central user repository. Introducing Understanding Of Identity And Access Management Securing Systems With Identity to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Access Management, Identity Mgmt using this template. Grab it now to reap its full benefits.
-
 Uniting Identity And Access Management Processes Securing Systems With Identity
Uniting Identity And Access Management Processes Securing Systems With IdentityThis slide discusses the Identity and Access Management uniting process. The purpose of this slide is to explain the Identity and Access Management unit, which involves users, access management, resources, identity management, and ID sources. Increase audience engagement and knowledge by dispensing information using Uniting Identity And Access Management Processes Securing Systems With Identity This template helps you present information on Four stages. You can also present information on Key Takeaways, Iam Market Size using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Use Cases Of Identity And Access Management Securing Systems With Identity
Use Cases Of Identity And Access Management Securing Systems With IdentityThis slide highlights the Identity and Access Management process use cases. The purpose of this slide is to discuss the cases these include IAM for zero trust at better.com and IAM for streamlined onboarding at hearst. Introducing Use Cases Of Identity And Access Management Securing Systems With Identity to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Loss Prevention, Compromising Security using this template. Grab it now to reap its full benefits.
-
 Patch Management In Mobile Device Security Mobile Security
Patch Management In Mobile Device Security Mobile SecurityThis slide gives an overview of patch management in mobile security which is defined as subset of systems management tasks intended to address bugs. Introducing Patch Management In Mobile Device Security Mobile Security to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Increased Employee Satisfaction, Simplified Device Management using this template. Grab it now to reap its full benefits.
-
 Primary Benefits Of Patch Management In Mobile Security Mobile Security
Primary Benefits Of Patch Management In Mobile Security Mobile SecurityThis slide highlights the primary benefits of patch management in mobile security which include addresses vulnerabilities promptly, mitigates exploitation risk, etc. Increase audience engagement and knowledge by dispensing information using Primary Benefits Of Patch Management In Mobile Security Mobile Security This template helps you present information on Five stages. You can also present information on Plan And Assess, Update Security Policies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Salient Features Of Patch Management In Security Mobile Security
Salient Features Of Patch Management In Security Mobile SecurityThis slide discusses the key features of patch management in security which includes administrative controls for patch approvals and automated patching. Increase audience engagement and knowledge by dispensing information using Salient Features Of Patch Management In Security Mobile Security This template helps you present information on Five stages. You can also present information on Software Versions, Assets And Patches using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Patch Management Process Lifecycle Mobile Security
Security Patch Management Process Lifecycle Mobile SecurityThis slide represents the patch management process lifecycle which include steps like standardize software versions, categorize assets and patches, etc. Introducing Security Patch Management Process Lifecycle Mobile Security to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Information Gathering, Exploitation using this template. Grab it now to reap its full benefits.
-
 Software Update And Patch Management Best Practices Mobile Security
Software Update And Patch Management Best Practices Mobile SecurityThis slide gives an overview of best practices followed in software update and patch management which includes create asset inventory, patch management, etc. Introducing Software Update And Patch Management Best Practices Mobile Security to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Security Threats, Jailbreaking And Rooting using this template. Grab it now to reap its full benefits.
-
 Identify Risks For Insurance Organizations Security Optimizing Risk Management Practices Risk SS
Identify Risks For Insurance Organizations Security Optimizing Risk Management Practices Risk SSThis slide defines the process of conducting a comprehensive risk assessment to identify potential threats to the insurance organizations security, utilizing automated platforms for efficient risk identification. Present the topic in a bit more detail with this Identify Risks For Insurance Organizations Security Optimizing Risk Management Practices Risk SS. Use it as a tool for discussion and navigation on Underwriting Errors, Failure To Meet Regulatory Requirements, Poor Customer Service, Internal Operational Risks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Business Survey Highlighting Challenges In Managing Implementing E Commerce Security Measures
Business Survey Highlighting Challenges In Managing Implementing E Commerce Security MeasuresThis slide highlights common challenges that businesses face while managing ecommerce frauds. It include problems such as identifying fraud attacks, gap un fraud tool functionalities, lack of internal resources etc. Introducing Business Survey Highlighting Challenges In Managing Implementing E Commerce Security Measures to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Identifying Fraud Attacks, Updating Fraud Risk Model, Sufficient Internal Resources, using this template. Grab it now to reap its full benefits.
-
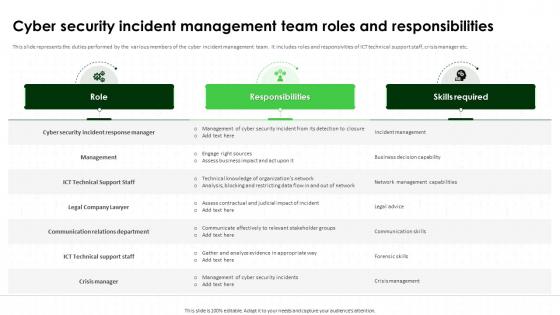 Cyber Security Incident Management Team Roles IT Security Awareness Training Cybersecurity SS
Cyber Security Incident Management Team Roles IT Security Awareness Training Cybersecurity SSThis slide represents the duties performed by the various members of the cyber incident management team. It includes roles and responsivities of ICT technical support staff, crisis manager etc. Deliver an outstanding presentation on the topic using this Cyber Security Incident Management Team Roles IT Security Awareness Training Cybersecurity SS. Dispense information and present a thorough explanation of Cyber Security Incident Response, Management, Roles And Responsibilities, Network Management Capabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
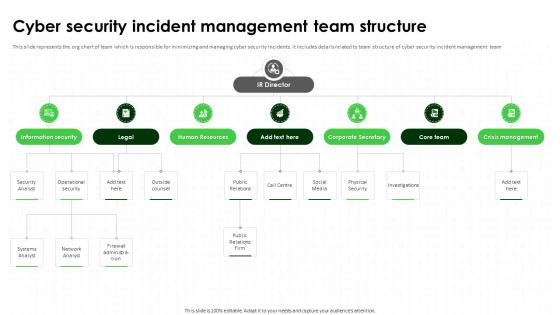 Cyber Security Incident Management Team Structure IT Security Awareness Training Cybersecurity SS
Cyber Security Incident Management Team Structure IT Security Awareness Training Cybersecurity SSThis slide represents the org chart of team which is responsible for minimizing and managing cyber security incidents. It includes details related to team structure of cyber security incident management team. Increase audience engagement and knowledge by dispensing information using Cyber Security Incident Management Team Structure IT Security Awareness Training Cybersecurity SS. This template helps you present information on four stages. You can also present information on Cyber Security Incident, Management Team Structure, Managing Cyber Security Incidents using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Robust Password Management Training For End Users IT Security Awareness Training Cybersecurity SS
Robust Password Management Training For End Users IT Security Awareness Training Cybersecurity SSThis slide represents training plan for robust management of verifying identity of user accessing a digital system. It includes details related to training modules such as beyond passwords etc. Present the topic in a bit more detail with this Robust Password Management Training For End Users IT Security Awareness Training Cybersecurity SS. Use it as a tool for discussion and navigation on Beyond Passwords, Multi Factor Authentication, Password Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Establishing Endpoint Privilege Management Building Next Generation Endpoint Security Cybersecurity SS
Establishing Endpoint Privilege Management Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases endpoint privilege management for maximum security. It includes details about admin rights, application privileges, just in time access, etcIntroducing Establishing Endpoint Privilege Management Building Next Generation Endpoint Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Current Scenario, Remedial Solutions, Potential Impact, using this template. Grab it now to reap its full benefits.
-
 Establishing Privilege Access Management Building Next Generation Endpoint Security Cybersecurity SS
Establishing Privilege Access Management Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases how to establish privilege access management process. It provides details about prepare, protect, operate, monitor, etc.Present the topic in a bit more detail with this Establishing Privilege Access Management Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Prepare, Protect, Operate, Monitor. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Construction Risk Management Software For Security Of Workers Revolutionizing Construction With Robots
Construction Risk Management Software For Security Of Workers Revolutionizing Construction With RobotsThis slide showcases various softwares to easily conduct inspections and proactively identify risks. It includes of tools such as Raken, Zepth, etc.Present the topic in a bit more detail with this Construction Risk Management Software For Security Of Workers Revolutionizing Construction With Robots. Use it as a tool for discussion and navigation on Key Features, Pros, Cons, Free Trial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Multi Layered Managed Organization Security Services
Multi Layered Managed Organization Security ServicesThe following slide provides the various types of managed security services provided by company for different risk categories. The various security requirements are endpoint. Application, cloud, etc. Presenting our set of slides with Multi Layered Managed Organization Security Services. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Endpoint Security, Application Security, Cloud Security.
-
 Organizational Employee Security Management Icon
Organizational Employee Security Management IconIntroducing our Organizational Employee Security Management Icon set of slides. The topics discussed in these slides are Organizational, Employee Security Management, Icon. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Wireless Lan Security Policy Management System Framework
Wireless Lan Security Policy Management System FrameworkThis slide represents framework that assists organizations that relies on wireless network to enhance LAN security compliance and incident response. It includes various components such as global policy server, WLAN policy zone, access point, etc. Presenting our well structured Wireless Lan Security Policy Management System Framework The topics discussed in this slide are Local Role Server, Mobile Hast, Mobile Host, Global Policy ServerThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Crisis Management Icon For Digital Security
Cyber Crisis Management Icon For Digital SecurityIntroducing our premium set of slides with name Cyber Crisis Management Icon For Digital Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Crisis Management, Digital Security. So download instantly and tailor it with your information.
-
 Cyber Security Crisis Management Team
Cyber Security Crisis Management TeamThe purpose of this slide is to underscore how the cybersecurity crisis management team functions by delivering a coordinated and rapid response to cyber threats, thereby minimizing impact and safeguarding organizational assets. Introducing our premium set of slides with name Cyber Security Crisis Management Team. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like External Counsel, Stakeholders, Central Team, Inquiry Team. So download instantly and tailor it with your information.
-
 Cyber Security Crisis Management Timeline
Cyber Security Crisis Management TimelineThe purpose of this slide is to highlight how a cybersecurity crisis management timeline aids in orchestrating swift and sequential responses, mitigating cyber threats effectively, and minimizing potential damages to the organization. Presenting our set of slides with name Cyber Security Crisis Management Timeline. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identification, Communication, Recover Learn.
-
 Icon For Managing Big Data Governance And Security With AWS
Icon For Managing Big Data Governance And Security With AWSPresenting our set of slides with Icon For Managing Big Data Governance And Security With AWS. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon, Managing Big Data, Governance And Security, AWS.
-
 Cloud Data Management Virtualization Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Data Management Virtualization Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon represents the importance of data security in cloud virtualization. With a vibrant design, it visually conveys the significance of protecting sensitive information in a virtual environment. Use it to enhance your presentations on cloud computing and data protection.
-
 Cloud Data Management Virtualization Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cloud Data Management Virtualization Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is the perfect addition to your presentation on Cloud virtualization data security. With a sleek design and clear imagery, it effectively represents the topic of data security in the cloud. Use it to enhance your slides and make a lasting impression on your audience.
-
 Patch Management Process For IOT Device Security
Patch Management Process For IOT Device SecurityThe purpose of this slide is to ensure cybersecurity through compliance management and regular audits of network device patch management. It covers steps such as defining goals, conducting vulnerability scanning, managing patch compliance, etc. Presenting our set of slides with name Patch Management Process For IOT Device Security. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Evaluate Device Inventory, Embrace Automation, Test Patches.
-
 Security Patch Management Process Icon
Security Patch Management Process IconIntroducing our premium set of slides with name Security Patch Management Process Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security, Patch Management, Process. So download instantly and tailor it with your information.
-
 Software Security Patch Management Process
Software Security Patch Management ProcessThe purpose of this slide is to optimize software security through efficient patch management. It covers steps such as information retrieval, vulnerability scanning and patch testing. Presenting our set of slides with name Software Security Patch Management Process. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Information Retrieval, Vulnerability Scanning, Patch Testing.
-
 Business Security Configuration Management Icon
Business Security Configuration Management IconPresenting our well structured Business Security Configuration Management Icon. The topics discussed in this slide are Business Security Configuration Management Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Advantages In Configuration Management
Cyber Security Advantages In Configuration ManagementThis slide formulates the benefits of cyber security in configuration management. Its use is to control the data better and increase visibility. Introducing our premium set of slides with name Cyber Security Advantages In Configuration Management. Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Better Control Of Data, Better Understanding Of Environment, Produce Efficiency, Visibility. So download instantly and tailor it with your information.
-
 Effective Security Configuration Management Tools
Effective Security Configuration Management ToolsThis slide includes various tools for managing security configuration in the organisation. Its objective is to use the best available tool which is feature rich. This slide showcases tool such as solar winds, auvik, Microsoft intune, etc. Presenting our well structured Effective Security Configuration Management Tools. The topics discussed in this slide are Software, Endpoint Central Manage Engine, Network Configuration Manager. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Essential Checklist For Security Configuration Management
Essential Checklist For Security Configuration ManagementThis slide depicts the important components required for security configuration management. This slide suggest disabling unnecessary accounts, changing passwords, authentication, best practices, etc. Presenting our well structured Essential Checklist For Security Configuration Management. The topics discussed in this slide are Disable Unnecessary Accounts, Change Default Passwords, Remove Unnecessary Software. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
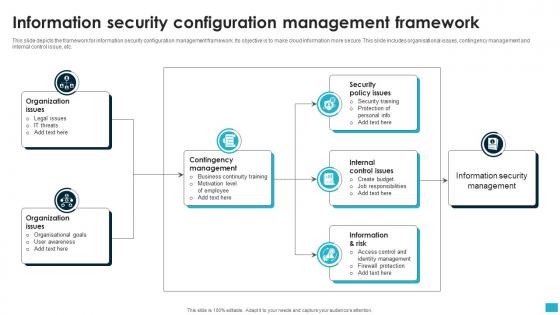 Information Security Configuration Management Framework
Information Security Configuration Management FrameworkThis slide depicts the framework for information security configuration management framework. Its objective is to make cloud information more secure. This slide includes organisational issues, contingency management and internal control issue, etc. Introducing our premium set of slides with name Information Security Configuration Management Framework. Ellicudate the Seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Organization Issues, Contingency Management, Internal Control Issues. So download instantly and tailor it with your information.
-
 Information Security Configuration Management Phases
Information Security Configuration Management PhasesThis slide depicts a set of activities for securing configuration management in phases. Its objective is to support information system and avoid organisational risk. This slide includes planning, implementing configuration, configuration changes, monitoring, etc. Introducing our premium set of slides with name Information Security Configuration Management Phases. Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Planning, Controlling Configuration Changes, Monitoring. So download instantly and tailor it with your information.
-
 Monitor Security Configuration Management System
Monitor Security Configuration Management SystemThis slide depicts the security configuration management flow. Its aim is to manage the configuration system efficiently. This slide includes publisher, automatic checks, configuration guide, rule implementation, administrator monitoring, etc. Presenting our well structured Monitor Security Configuration Management System. The topics discussed in this slide are Administrator, System Testing, Legend, Implement Rules. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Configuration Management Flowchart
Security Configuration Management FlowchartThis slide depicts the flowchart for security configuration management. Its objective is to analyse the changes and report the new requirements. This slide includes taking up new changes, verifying, generating new ECR, etc. Introducing our premium set of slides with name Security Configuration Management Flowchart. Ellicudate the One stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Configuration Management, Cm Database. So download instantly and tailor it with your information.
-
 Security Configuration Management Impact Analysis
Security Configuration Management Impact AnalysisThis slide showcases the security configuration management impact analysis. Its objective is to identify vulnerability and change the configuration to reduce risk. This slide includes understanding change, assess risk, evaluate control, deploy countermeasures, etc. Introducing our premium set of slides with name Security Configuration Management Impact Analysis. Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Assess Risk, Identify Vulnerability, Evaluate Impact On Controls. So download instantly and tailor it with your information.
-
 Security Configuration Management Solutions In Cyber Network
Security Configuration Management Solutions In Cyber NetworkThis slide depicts the management solution for security configuration in cyber network. Its objective is to find the weak points of the company and fix them fast to safeguard them from attacks. This slide includes vulnerability assessment, remediation phase, etc. Introducing our premium set of slides with name Security Configuration Management Solutions In Cyber Network. Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Vulnerability, Automated Remediation, Configuration Assessment. So download instantly and tailor it with your information.
-
 Security Configuration Management User Roles
Security Configuration Management User RolesThis slide showcases the roles assigned to users for security configuration management. Its aim is to record the activities of the configuration management users. This slide includes auditor, administrator, configuration, tools, etc. Presenting our well structured Security Configuration Management User Roles. The topics discussed in this slide are Configuration Administrator, Configuration Auditor, Configuration Manager. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Protection And Configuration Management Icon
Security Protection And Configuration Management IconIntroducing our premium set of slides with name Security Protection And Configuration Management Icon. Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Protection And Configuration Management Icon. So download instantly and tailor it with your information.
-
 Steps For Security Configuration Management Process
Steps For Security Configuration Management ProcessThis slide depicts the process for security configuration management. Its objective is to harden the system to perform and control the tasks. This slide includes security requirement, identify, control, establish process, etc. Introducing our premium set of slides with name Steps For Security Configuration Management Process. Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify, Control, Develop And Adapt, Establish Process. So download instantly and tailor it with your information.
-
 Steps In Security Configuration Management System
Steps In Security Configuration Management SystemThis slide depicts the security configuration management steps. Its aim Is to discover assets, solve problem, initiate baseline and make changes in it. This slide includes discovery of asset, baseline device, solve problem and make changes. Introducing our premium set of slides with name Steps In Security Configuration Management System. Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Discover Asset, Initiate Baseline, Make Changes, Solve Problem. So download instantly and tailor it with your information.
-
 Techniques Of Including Security Configuration Management
Techniques Of Including Security Configuration ManagementThis slide depicts the techniques to handle security configuration management in an enterprise. Its aim is to reduce security vulnerabilities. This slide includes monitoring, endpoint, configuration, avoid jams, etc. Introducing our premium set of slides with name Techniques Of Including Security Configuration Management. Ellicudate the Seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Configure Remote Endpoints, Monitor Results, Operating System Endpoint. So download instantly and tailor it with your information.
-
 Endpoint Protection Security Patch Management Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Endpoint Protection Security Patch Management Colored Icon In Powerpoint Pptx Png And Editable Eps FormatUpgrade your endpoint cyber security with our vibrant PowerPoint icon for software patching. This eye-catching icon visually represents the importance of regularly updating your software to protect against cyber threats. Use it to enhance your presentations on endpoint security and educate your audience on the importance of staying protected.
-
 Endpoint Protection Security Patch Management Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Endpoint Protection Security Patch Management Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is designed to represent the process of software patching for ensuring endpoint cyber security. It is perfect for use in presentations, reports, and other materials related to software security and protection. The icon features a simple yet impactful design that will enhance the visual appeal of your content.
-
 Management Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Management Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon represents Mitigate EDR incidents, a cutting-edge cybersecurity technology. It is designed to help businesses prevent and respond to advanced cyber threats and attacks. With its intuitive interface and powerful features, this technology is a must-have for any organization looking to enhance their cybersecurity measures.
-
 Management Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Management Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatIntroducing the Monotone PowerPoint icon, designed specifically for Mitigate EDR incidents in cybersecurity technology. This sleek and modern icon represents the powerful capabilities of Mitigate EDR in detecting and responding to potential threats. With its minimalist design, it is the perfect addition to any cybersecurity presentation.
-
 Security Management Jobs In Powerpoint And Google Slides Cpp
Security Management Jobs In Powerpoint And Google Slides CppPresenting Security Management Jobs In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Management Jobs. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
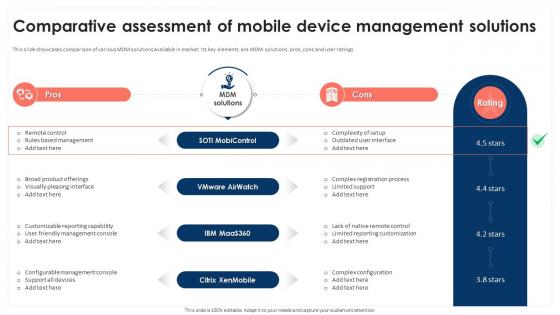 Comparative Assessment Of Mobile Device Management Solutions Mobile Device Security Cybersecurity SS
Comparative Assessment Of Mobile Device Management Solutions Mobile Device Security Cybersecurity SSThis slide showcases comparison of various MDM solutions available in market. Its key elements are MDM solutions, pros, cons and user ratings Increase audience engagement and knowledge by dispensing information using Comparative Assessment Of Mobile Device Management Solutions Mobile Device Security Cybersecurity SS This template helps you present information on Two stages. You can also present information on SOTI Mobicontrol, Vmware Airwatch, Citrix Xenmobile using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Factors To Consider Before Purchasing Mobile Device Management Mobile Device Security Cybersecurity SS
Factors To Consider Before Purchasing Mobile Device Management Mobile Device Security Cybersecurity SSThis slide showcases factors to be considered before buying MDM solutions. Its key elements are supported operating systems, budget and feature requirements Introducing Factors To Consider Before Purchasing Mobile Device Management Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Biometrics, Mobile VPN, Encryption using this template. Grab it now to reap its full benefits.
-
 Kpis To Track Mobile Security Management Plan Mobile Device Security Cybersecurity SS
Kpis To Track Mobile Security Management Plan Mobile Device Security Cybersecurity SSThis slide showcases metrics that can help to track the effectiveness of mobile security management plan. Various KPIs are mobile threat detection rate, incident response time etc. Deliver an outstanding presentation on the topic using this Kpis To Track Mobile Security Management Plan Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Phase, Key Tasks, Estimated Duration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





