Powerpoint Templates and Google slides for Security Management
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Project Risk Management Life Cycle
Cyber Security Project Risk Management Life CycleThis slide represents the lifecycle of project risk management. The process include Identification, Analyse, Prioritize and monitoring. Presenting our set of slides with Cyber Security Project Risk Management Life Cycle. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Monitoring, Identification, Prioritize.
-
 Vulnerability Management Cyber Security In Powerpoint And Google Slides Cpb
Vulnerability Management Cyber Security In Powerpoint And Google Slides CpbPresenting Vulnerability Management Cyber Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Vulnerability Management Cyber Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 How Achieve ISO 27001 Certification Current Security Management Capabilities Overview
How Achieve ISO 27001 Certification Current Security Management Capabilities OverviewFollowing slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an outstanding presentation on the topic using this How Achieve ISO 27001 Certification Current Security Management Capabilities Overview. Dispense information and present a thorough explanation of Detect, Protect, Recovery, Capabilities, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 ISO 27001 Information Security Management Standard Ppt File Ideas
ISO 27001 Information Security Management Standard Ppt File IdeasIntroducing ISO 27001 Information Security Management Standard Ppt File Ideas to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Contextual Requirements, Leadership Requirements, Planning Requirements, Support Requirements, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Risk Management Approach With Risk Priority And Control
Cyber Security Risk Management Approach With Risk Priority And ControlThe following slide highlights the cyber security risk management approach with risk priority and control it illustrates risk priority, mitigation, controls, automation, governance and risk culture, which helps organisation to train workforce for cyber awareness and define company policy for cyber security. Presenting our set of slides with name Cyber Security Risk Management Approach With Risk Priority And Control. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Governance, Risk Priority, Mitigation.
-
 Cyber Security Solution For Infrastructure Management
Cyber Security Solution For Infrastructure ManagementThe following slide highlights the cyber security solution for infrastructure management illustrating vulnerability, prevention, detection and respond to provide multiple solution based on requirement. Presenting our set of slides with name Cyber Security Solution For Infrastructure Management. This exhibits information on eleven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Vulnerability, Prevention, Detection, Respond.
-
 Process Of Cyber Security Asset Management
Process Of Cyber Security Asset ManagementThe following slide highlights the process of cyber security asset management depicting four steps which include asset inventory, synchronization, security gaps and response to save assets and mitigate the risk in minimum time. Introducing our premium set of slides with name Process Of Cyber Security Asset Management. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Asset Inventory, Synchronization, Response, Security Gaps. So download instantly and tailor it with your information.
-
 Three Layers Of Cyber Security Management Process
Three Layers Of Cyber Security Management ProcessThe following slide highlights the three layers of cyber security management process which are dependent on people, process and technology, it helps company to manage cyber risks such as phishing attacks, data loss and exposed vulnerabilities. Presenting our set of slides with name Three Layers Of Cyber Security Management Process. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on People, Process, Technology.
-
 Executive Leadership And Management Team Wireless Home Security Systems Company Profile
Executive Leadership And Management Team Wireless Home Security Systems Company ProfileThis slide highlights the security company leadership and management team which includes president and CEO, executive vice president of finance, EVP home security, chief administration officer. Increase audience engagement and knowledge by dispensing information using Executive Leadership And Management Team Wireless Home Security Systems Company Profile. This template helps you present information on five stages. You can also present information on Executive Leadership, Management Team using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Obtaining ISO 27001 Certificate Current Security Management Capabilities Overview
Obtaining ISO 27001 Certificate Current Security Management Capabilities OverviewFollowing slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Present the topic in a bit more detail with this Obtaining ISO 27001 Certificate Current Security Management Capabilities Overview. Use it as a tool for discussion and navigation on Core Functions, Key Enablers, Required Standard Rating. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Obtaining ISO 27001 Certificate ISO 27001 Information Security Management Standard
Obtaining ISO 27001 Certificate ISO 27001 Information Security Management StandardIntroducing Obtaining ISO 27001 Certificate ISO 27001 Information Security Management Standard to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Contextual Requirements, Leadership Requirements, Planning Requirements, using this template. Grab it now to reap its full benefits.
-
 Crisis Management Team Security And Manpower Services Company Profile
Crisis Management Team Security And Manpower Services Company ProfileThis slide highlights the security company crisis management team which includes general manager, guard supervisor, mobile response team manpower and equipment. Introducing Crisis Management Team Security And Manpower Services Company Profile to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Mobile Response Team, Crisis Management Team, using this template. Grab it now to reap its full benefits.
-
 Executive Leadership And Management Team Security And Manpower Services Company Profile
Executive Leadership And Management Team Security And Manpower Services Company ProfileThis slide highlights the security guard company management team which includes company s chairman and MD, head of security operations, training, strategic growth and site. Increase audience engagement and knowledge by dispensing information using Executive Leadership And Management Team Security And Manpower Services Company Profile. This template helps you present information on five stages. You can also present information on Holds Business Economist Degree, Studied Aviation From Stanford University, Started His Career With Boeing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Event Management In Powerpoint And Google Slides Cpb
Security Event Management In Powerpoint And Google Slides CpbPresenting our Security Event Management In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Security Event Management This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Iot Security Lock For Safe Fleet Management Implementing Iot Architecture In Shipping Business
Iot Security Lock For Safe Fleet Management Implementing Iot Architecture In Shipping BusinessThe following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Deliver an outstanding presentation on the topic using this Iot Security Lock For Safe Fleet Management Implementing Iot Architecture In Shipping Business. Dispense information and present a thorough explanation of Management, Potential Impact, Key Applications using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
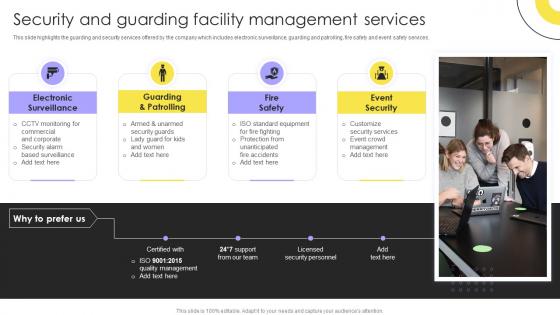 Security And Guarding Facility Management Services Integrated Facility Management Services And Solutions
Security And Guarding Facility Management Services Integrated Facility Management Services And SolutionsThis slide highlights the guarding and security services offered by the company which includes electronic surveillance, guarding and patrolling, fire safety and event safety services. Increase audience engagement and knowledge by dispensing information using Security And Guarding Facility Management Services Integrated Facility Management Services And Solutions. This template helps you present information on four stages. You can also present information on Management Services, Electronic, Surveillance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices To Manage Cyber Security Of Organization
Best Practices To Manage Cyber Security Of OrganizationThis slide shows various practices which can be used to by organizations to manage information technology security. These practices are monitor, risk plan, security protocols and use technology. Introducing our premium set of slides with Best Practices To Manage Cyber Security Of Organization. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Success Rate, Security Protocols, Use Technology. So download instantly and tailor it with your information.
-
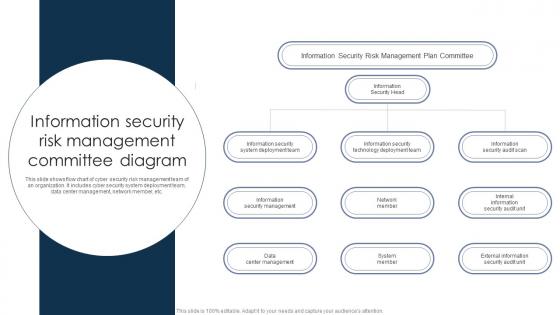 Information Security Risk Management Committee Diagram
Information Security Risk Management Committee DiagramThis slide shows flow chart of cyber security risk management team of an organization. It includes cyber security system deployment team, data center management, network member, etc. Presenting our set of slides with Information Security Risk Management Committee Diagram. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Information Security Head, Network Member, System Member.
-
 Organizational Information Security Management Icon
Organizational Information Security Management IconPresenting our set of slides with Organizational Information Security Management Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Organizational Information, Security Management Icon.
-
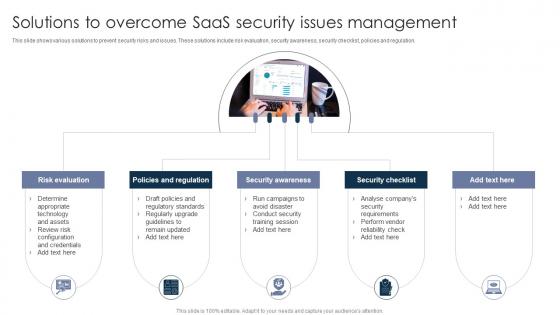 Solutions To Overcome SaaS Security Issues Management
Solutions To Overcome SaaS Security Issues ManagementThis slide shows various solutions to prevent security risks and issues. These solutions include risk evaluation, security awareness, security checklist, policies and regulation. Presenting our set of slides with Solutions To Overcome SaaS Security Issues Management. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Risk Evaluation, Policies And Regulation, Security Awareness, Security Checklist.
-
 Managing Supply Chain Risk Security In Powerpoint And Google Slides Cpb
Managing Supply Chain Risk Security In Powerpoint And Google Slides CpbPresenting our Managing Supply Chain Risk Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases seven stages. It is useful to share insightful information on Managing Supply Chain Risk Security. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security And Guarding Facility Management Services Facilities Management And Maintenance Company
Security And Guarding Facility Management Services Facilities Management And Maintenance CompanyThis slide highlights the guarding and security services offered by the company which includes electronic surveillance, guarding and patrolling, fire safety and event safety services. Introducing Security And Guarding Facility Management Services Facilities Management And Maintenance Company to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Electronic Surveillance, Guarding And Patrolling, Fire Safety, using this template. Grab it now to reap its full benefits.
-
 Problem Management Process For Enhancing Cyber Security
Problem Management Process For Enhancing Cyber SecurityThis slide signifies increasing cyber security and IT through problem management process. It includes stages like detection, define, investigate, identify resolutions, implement and follow up Introducing our premium set of slides with Problem Management Process For Enhancing Cyber Security. Elucidate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Problem Detection, Define, Investigate, Identify Resolutions, Implement. So download instantly and tailor it with your information.
-
 IT Risk Management Strategies Detection And Prevention Of Management Security Controls
IT Risk Management Strategies Detection And Prevention Of Management Security ControlsThe following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Introducing IT Risk Management Strategies Detection And Prevention Of Management Security Controls to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Preventive Management, Security Controls, Detection Management, using this template. Grab it now to reap its full benefits.
-
 IT Risk Management Strategies Financial Burden To Company From It Security Breaches
IT Risk Management Strategies Financial Burden To Company From It Security BreachesThis slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Present the topic in a bit more detail with this IT Risk Management Strategies Financial Burden To Company From It Security Breaches. Use it as a tool for discussion and navigation on Professional Services, Lost Business Opportunities, Total Damage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Risk Management Strategies IT Security Residual Risk Matrix With Response Actions
IT Risk Management Strategies IT Security Residual Risk Matrix With Response ActionsThis slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver an outstanding presentation on the topic using this IT Risk Management Strategies IT Security Residual Risk Matrix With Response Actions. Dispense information and present a thorough explanation of Control Topic, Evaluation Question, Response Action, Threat using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation Plan
IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation PlanThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Increase audience engagement and knowledge by dispensing information using IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation Plan. This template helps you present information on one stages. You can also present information on Threat, Risk, Risk Priority, Risk Reduction Timeline using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IT Risk Management Strategies Security Criteria And Control Measures For IT System Vulnerabilities
IT Risk Management Strategies Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing IT Risk Management Strategies Security Criteria And Control Measures For It System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
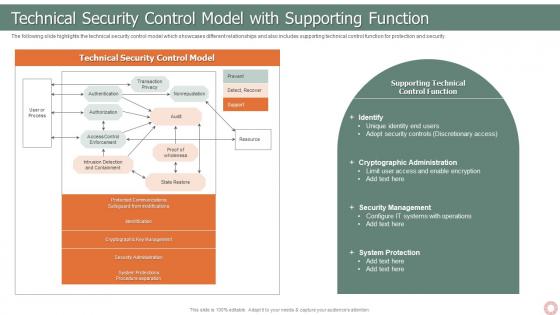 IT Risk Management Strategies Technical Security Control Model With Supporting Function
IT Risk Management Strategies Technical Security Control Model With Supporting FunctionThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Introducing IT Risk Management Strategies Technical Security Control Model With Supporting Function to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Technical Security, Control Model, Transaction Privacy, State Restore, using this template. Grab it now to reap its full benefits.
-
 Agenda Enterprise Risk Management And Information Technology Security
Agenda Enterprise Risk Management And Information Technology SecurityIntroducing Agenda Enterprise Risk Management And Information Technology Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Organization, IT Networks, IT Risk Management, using this template. Grab it now to reap its full benefits.
-
 Enterprise Risk Management And Information Technology Security Table Of Contents
Enterprise Risk Management And Information Technology Security Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Enterprise Risk Management And Information Technology Security Table Of Contents. This template helps you present information on one stages. You can also present information on Security Criteria, Control Measures, IT System Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise Risk Management Detection And Prevention Of Management Security Controls
Enterprise Risk Management Detection And Prevention Of Management Security ControlsThe following slide highlights the management security controls which includes preventive management security controls showcasing IT security polices and guidelines with detection management security controls. Increase audience engagement and knowledge by dispensing information using Enterprise Risk Management Detection And Prevention Of Management Security Controls. This template helps you present information on two stages. You can also present information on Preventive Management, Security Controls, Detection Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise Risk Management Financial Burden To Company From IT Security Breaches
Enterprise Risk Management Financial Burden To Company From IT Security BreachesThis slide highlights the financial burden of information technology security breaches which includes professional services, lost business opportunities, down time from multiple offices with losses. Deliver an outstanding presentation on the topic using this Enterprise Risk Management Financial Burden To Company From IT Security Breaches. Dispense information and present a thorough explanation of Professional Services, Lost Business Opportunities, Total Damage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Risk Management IT Security Residual Risk Matrix With Response Actions
Enterprise Risk Management IT Security Residual Risk Matrix With Response ActionsThis slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Present the topic in a bit more detail with this Enterprise Risk Management IT Security Residual Risk Matrix With Response Actions. Use it as a tool for discussion and navigation on Control Topic, Evaluation Question, Response Action, Threat. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation Plan
Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation PlanThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation Plan. Use it as a tool for discussion and navigation on Threat, Risk, Risk Priority, Risk Reduction Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Risk Management Security Criteria And Control Measures For IT System Vulnerabilities
Enterprise Risk Management Security Criteria And Control Measures For IT System VulnerabilitiesThis slide highlights the security criteria for information technology system vulnerabilities with security area which includes management security, operational security and technical security. Introducing Enterprise Risk Management Security Criteria And Control Measures For IT System Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Management Security, Operational Security, Technical Security, using this template. Grab it now to reap its full benefits.
-
 Enterprise Risk Management Technical Security Control Model With Supporting Function
Enterprise Risk Management Technical Security Control Model With Supporting FunctionThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Introducing Enterprise Risk Management Technical Security Control Model With Supporting Function to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identify, Cryptographic Administration, Security Management, System Protection, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Enterprise Risk Management And Information Technology Security
Icons Slide For Enterprise Risk Management And Information Technology SecurityIntroducing our well researched set of slides titled Icons Slide For Enterprise Risk Management And Information Technology Security. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table Of Contents For Enterprise Risk Management And Information Technology Security
Table Of Contents For Enterprise Risk Management And Information Technology SecurityIntroducing Table Of Contents For Enterprise Risk Management And Information Technology Security to increase your presentation threshold. Encompassed with eleven stages, this template is a great option to educate and entice your audience. Dispence information on IT Risks, Threat Evaluation, IT Risk Management, Cost Estimation, using this template. Grab it now to reap its full benefits.
-
 IT Security Residual Risk Matrix With Risk Management Guide For Information Technology Systems
IT Security Residual Risk Matrix With Risk Management Guide For Information Technology SystemsThis slide highlights the information technology security residual risk matrix which includes asset, control topic, evaluation questions, response action and threat. Deliver an outstanding presentation on the topic using this IT Security Residual Risk Matrix With Risk Management Guide For Information Technology Systems. Dispense information and present a thorough explanation of Database Access, Evaluation Question, Response Action using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems
Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology SystemsThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Threat Risk, Risk Mitigation Plan, Risk Owner. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technical Security Control Model With Isk Management Guide For Information Technology Systems
Technical Security Control Model With Isk Management Guide For Information Technology SystemsThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver an outstanding presentation on the topic using this Technical Security Control Model With Isk Management Guide For Information Technology Systems. Dispense information and present a thorough explanation of Technical Security, Control Model, Supporting Technical, Control Function using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Project Management Timeline With Security And Technology
Project Management Timeline With Security And TechnologyThis slide shows the monthly project management timeline for website development which includes two teams such as UX and Backend team whose main tasks are system designing, getting approval from client, creating wireframes of pages, defining website policies, etc. Presenting our well structured Project Management Timeline With Security And Technology. The topics discussed in this slide are Security, Technology, People. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Risk Management Icon In Information Technology
Cyber Security Risk Management Icon In Information TechnologyPresent the topic in a bit more detail with this Cyber Security Risk Management Icon In Information Technology. Use it as a tool for discussion and navigation on Cyber Security, Risk Management, Icon In Information Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security And Risk Management With Capabilities
Information Technology Security And Risk Management With CapabilitiesThis slide focuses on the information technology security and risk management which covers capabilities such as enterprise security strategy, compliance, vulnerability management, security architecture, data leakage protection, identify management, etc. Deliver an outstanding presentation on the topic using this Information Technology Security And Risk Management With Capabilities. Dispense information and present a thorough explanation of Security Policy Compliance, Compliance, Enterprise Security Strategy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Model For Information Technology Security Risk Management
Model For Information Technology Security Risk ManagementThis slide shows the model that depicts IT security risk management which focuses on identification, protection, detection, response and recovery planning with security asset management, governance, data security, detection processes, risk analysis and planning, etc. Introducing Model For Information Technology Security Risk Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Identifying, Protecting, Detecting, using this template. Grab it now to reap its full benefits.
-
 Risk Management Matrix For Information Technology Security
Risk Management Matrix For Information Technology SecurityThis slide shows the risk management matrix for information technology security which covers the business workflow and technical systems with IT risks and threats such as software security, business controls, control risk modelling, penetration testing, attack modelling, etc. Present the topic in a bit more detail with this Risk Management Matrix For Information Technology Security. Use it as a tool for discussion and navigation on Corporate Workflow, Risks, Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Methodology In Information Technology Security
Risk Management Methodology In Information Technology SecurityThis slide focuses on the risk management methodology in information technology security which includes three different phases such as assessment, mitigation and continual evaluation assessment that are helpful in effective management of security risks and hazards. Deliver an outstanding presentation on the topic using this Risk Management Methodology In Information Technology Security. Dispense information and present a thorough explanation of Assessment, Mitigation, Continual Evaluation Assessment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Role Of Management In Security Governance Across Firm Revamping Corporate Strategy
Role Of Management In Security Governance Across Firm Revamping Corporate StrategyThis slide provides information regarding importance of management in to enable security governance across firm to ensure strategic alignment, risk management, integration, value delivery, resource management, etc. Deliver an outstanding presentation on the topic using this Role Of Management In Security Governance Across Firm Revamping Corporate Strategy. Dispense information and present a thorough explanation of Risk Management, Value Delivery, Integration, Managing Resource using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mitigation Plan For Cyber Security Risk Scenario Management
Mitigation Plan For Cyber Security Risk Scenario ManagementThis slide covers the mitigation plan for cybersecurity risk scenario management which includes threat, risk, priority level, risk mitigation plan, risk owner and risk reduction timeline. Presenting our well structured Mitigation Plan For Cyber Security Risk Scenario Management. The topics discussed in this slide are Risk, Risk Priority, Risk Mitigation Plan. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Agenda For Information Security Risk Management And Mitigation Plan Ppt Tips
Agenda For Information Security Risk Management And Mitigation Plan Ppt TipsIntroducing Agenda For Information Security Risk Management And Mitigation Plan Ppt Tips to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Organization, Information Security, Risk Management, using this template. Grab it now to reap its full benefits.
-
 Allocating Budget For Information Security Risk Management Programme
Allocating Budget For Information Security Risk Management ProgrammeThis slide showcase budget to be allocated for conducting training for information security risk management. It showcases budget for area like cybersecurity awareness, threat detection and risk management. Increase audience engagement and knowledge by dispensing information using Allocating Budget For Information Security Risk Management Programme. This template helps you present information on three stages. You can also present information on Functional Areas, Description, Training Cost using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Analysing The Impact Of Security Threats On Organization Information Security Risk Management
Analysing The Impact Of Security Threats On Organization Information Security Risk ManagementDeliver an outstanding presentation on the topic using this Analysing The Impact Of Security Threats On Organization Information Security Risk Management. Dispense information and present a thorough explanation of Analysing, Security Threats, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Analyzing The Impact On Assets Due To Information Breach Information Security Risk Management
Analyzing The Impact On Assets Due To Information Breach Information Security Risk ManagementThis slide showcases impact of information breach on different assets which can help organization in formulating risk monitoring policy. Its key components are criterion, criterion weight and information assets. Present the topic in a bit more detail with this Analyzing The Impact On Assets Due To Information Breach Information Security Risk Management. Use it as a tool for discussion and navigation on Impact On Revenue, Analyzing, Information Breach. This template is free to edit as deemed fit for your organization. Therefore download it now
-
 Asset Identification For Information Security Risk Management Ppt Slides
Asset Identification For Information Security Risk Management Ppt SlidesThis slide showcases identification of asset which can help organization to formulate risk monitoring plan. It can help to monitor the asset in real time for any data breach or cyber attack. Present the topic in a bit more detail with this Asset Identification For Information Security Risk Management Ppt Slides. Use it as a tool for discussion and navigation on Sales Records, Customers Database, Products Database. This template is free to edit as deemed fit for your organization. Therefore download it now
-
 Assigning Criticality Rating To Information Assets Information Security Risk Management
Assigning Criticality Rating To Information Assets Information Security Risk ManagementThis slide showcases criticality rating that can be allocation to assets for identifying critical assets. Its key elements are asset, failure cost, failure impact and criticality rating. Introducing Assigning Criticality Rating To Information Assets Information Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Sales Records, Customer Database, Product Database, using this template. Grab it now to reap its full benefits.
-
 Budget For Information Security Risk Management Ppt Microsoft
Budget For Information Security Risk Management Ppt MicrosoftThis slide showcases budget that can should be allocated for different information security risk management activities. It provides information about employees training, software implementation, risk monitoring and data backup. Increase audience engagement and knowledge by dispensing information using Budget For Information Security Risk Management Ppt Microsoft. This template helps you present information on one stage. You can also present information on Budget, Information Security, Risk Management using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Challenges And Solutions In Information Security Risk Management
Challenges And Solutions In Information Security Risk ManagementThis slide showcases challenges involved in formulating risk management program for information security. It also shows solutions to tackle the challenges and impact of implementing them. Introducing Challenges And Solutions In Information Security Risk Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispense information on Fighting Frauds, Internal Vulnerabilities, Employee Awareness, using this template. Grab it now to reap its full benefits.
-
 Checklist For Information Security Risk Management Ppt Microsoft
Checklist For Information Security Risk Management Ppt MicrosoftThis slide showcases checklist that can help to ensure formulate and implementing data security risk management program in organization. Its key components are activity, assigned to and status. Deliver an outstanding presentation on the topic using this Checklist For Information Security Risk Management Ppt Microsoft. Dispense information and present a thorough explanation of Checklist, Information Security, Risk Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Current Information And Data Security Capabilities Of Firm Information Security Risk Management
Current Information And Data Security Capabilities Of Firm Information Security Risk ManagementThis slide showcases current capabilities of organization regarding information and data security. Its key component are risk management functions, required standard rating and actual standard rating. Introducing Current Information And Data Security Capabilities Of Firm Information Security Risk Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispense information on Risk Management Functions, Required Standard Rating, Actual Standard Rating, using this template. Grab it now to reap its full benefits.





