Powerpoint Templates and Google slides for Security Management
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats
Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Present the topic in a bit more detail with this Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Information Security And Privacy, Physical Assets And Data Security, Web Application Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Patch Management On IT Security
Impact Of Patch Management On IT SecurityThis slide shows multiple potential results of deploying a patch management process in an organization. It includes regular security updates, feature updates, bug fixes, and prioritization. Presenting our set of slides with name Impact Of Patch Management On IT Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Updates, Features Updates, Bug Fixes.
-
 Best Practices Of SaaS Security Risk Management
Best Practices Of SaaS Security Risk ManagementThis slide showcases the practices of SaaS security risk management. Its purpose is to protect critical workloads to ensure compliance. This slide includes vulnerability identification, analysis, risk assessment and remediation. Introducing Best Practices Of SaaS Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability Identification, Remediation, Risk Assessment, Analysis, using this template. Grab it now to reap its full benefits.
-
 Cloud Cyber Security SaaS Risk Management
Cloud Cyber Security SaaS Risk ManagementThis slide showcases the cloud cyber security SaaS risk management. Its aim is to control profile and manage the risk involved. This slide includes authorization, monitor, cloud based, continuously monitor, etc. Introducing Cloud Cyber Security SaaS Risk Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Control Profiles, Cloud Security Risk Management, Security Categorization, using this template. Grab it now to reap its full benefits.
-
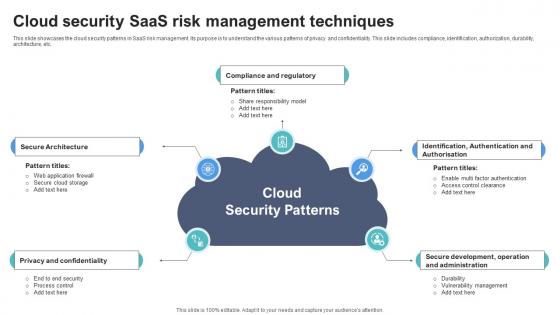 Cloud Security SaaS Risk Management Techniques
Cloud Security SaaS Risk Management TechniquesThis slide showcases the cloud security patterns in SaaS risk management. Its purpose is to understand the various patterns of privacy and confidentiality. This slide includes compliance, identification, authorization, durability, architecture, etc. Introducing Cloud Security SaaS Risk Management Techniques to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Secure Architecture, Privacy And Confidentiality, Cloud Security Patterns, Compliance And Regulatory, using this template. Grab it now to reap its full benefits.
-
 Principles Of SaaS Security Risk Management
Principles Of SaaS Security Risk ManagementThis slide showcases the principles of SaaS risk based security management. Its aim is to secure infrastructure for assessing risk. This slide includes network control, VM management, data protection, incident, reliability, access management, etc. Present the topic in a bit more detail with this Principles Of SaaS Security Risk Management. Use it as a tool for discussion and navigation on Access Management, Network Control, Perimeter Network Control. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
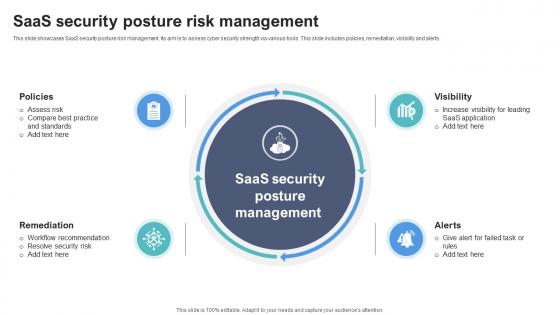 SaaS Security Posture Risk Management
SaaS Security Posture Risk ManagementThis slide showcases SaaS security posture risk management. Its aim is to assess cyber security strength via various tools. This slide includes policies, remediation, visibility and alerts. Increase audience engagement and knowledge by dispensing information using SaaS Security Posture Risk Management. This template helps you present information on four stages. You can also present information on Visibility, Policies, Remediation, Alerts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
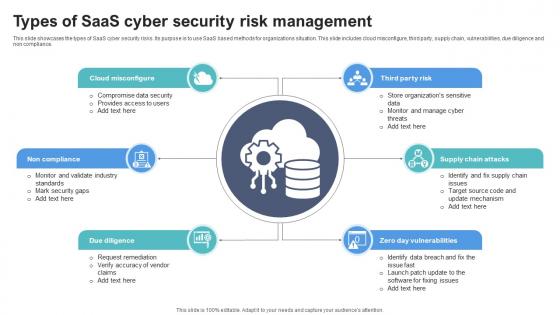 Types Of SaaS Cyber Security Risk Management
Types Of SaaS Cyber Security Risk ManagementThis slide showcases the types of SaaS cyber security risks. Its purpose is to use SaaS based methods for organizations situation. This slide includes cloud misconfigure, third party, supply chain, vulnerabilities, due diligence and non compliance. Increase audience engagement and knowledge by dispensing information using Types Of SaaS Cyber Security Risk Management. This template helps you present information on six stages. You can also present information on Supply Chain Attacks, Zero Day Vulnerabilities, Due Diligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Containerization Technology Container Security Essentials To Manage Risks
Containerization Technology Container Security Essentials To Manage RisksThis slide represents the various important factors of container security to manage environmental risks. The purpose of this slide is to outline the essentials of container security to manage risks, such as configuration, automation, container security solutions, and cloud and network security. Present the topic in a bit more detail with this Containerization Technology Container Security Essentials To Manage Risks. Use it as a tool for discussion and navigation on Dashboard To Retrieve Ongoing, Time Series Data Metrics, Containers Operating,Container Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Shadow IT Management Lifecycle Overview CASB Cloud Security
Shadow IT Management Lifecycle Overview CASB Cloud SecurityThis slide outlines the lifecycle of shadow IT management for safely adopting cloud apps. The purpose of this slide is to showcase the various stages of the lifecycle, such as discovering shadow IT, knowing the risk level of apps, evaluating compliance, analyzing usage, governing cloud apps, and continuous monitoring. Introducing Shadow IT Management Lifecycle Overview CASB Cloud Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Evaluate Compliance, Govern Cloud Apps, Continuous Monitoring, Management Lifecycle Overview, using this template. Grab it now to reap its full benefits.
-
 Manage Investor Relations Beginners Guide To Successfully Launch Security Token BCT SS V
Manage Investor Relations Beginners Guide To Successfully Launch Security Token BCT SS VThe following slide illustrates some ways to maintain effective and healthy relations with investors. It includes elements such as transparent communication, building investor relations team, conducting feedbacks and surveys, ensuring investor integration, etc. Introducing Manage Investor Relations Beginners Guide To Successfully Launch Security Token BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Transparent Communication, Relations Team, Feedback, using this template. Grab it now to reap its full benefits.
-
 Infrastructure Security Management Optimisation Strategies
Infrastructure Security Management Optimisation StrategiesThis slide represents the infrastructure security management utilisation methods. Its aim is to run security tools in a secure, documented with virtual team. This slide includes firewall system, remote access, cloud management and workflow system. Introducing our premium set of slides with Infrastructure Security Management Optimisation Strategies. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Generation, Remote, Management. So download instantly and tailor it with your information.
-
 Key Components Of Cloud Saas Cyber Security Management
Key Components Of Cloud Saas Cyber Security ManagementThis slide represents cloud SaaS cyber security management elements. It aims to focus on SaaS security posture management systems, staff training, data classification depending on security level, etc. It includes various elements such as data protection, identifying access management, etc. Presenting our set of slides with Key Components Of Cloud Saas Cyber Security Management This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Protection, Identify Access Management, Regular Pentests
-
 Action Plan To Enhance Data Security Management
Action Plan To Enhance Data Security ManagementThis slide showcases the action plan assisting businesses to train their employees on data security management to increase knowledge and awareness. It includes various elements such as courses, modules, duration, rating, and deadlines. Introducing our Action Plan To Enhance Data Security Management set of slides. The topics discussed in these slides are Execute Access Control, Responsible Leader, Reduce System Vulnerability. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices To Enhance Data Security Management
Best Practices To Enhance Data Security ManagementThis slide represents the best practices assisting companies to enhance data security management implications. It includes various practices such as data access policy audit, use of data security tools, providing training, etc. Presenting our well structured Best Practices To Enhance Data Security Management. The topics discussed in this slide are Implement Data Access, Security Management Tools, Outside Company Storage. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comparative Assessment For Data Security Management Tools
Comparative Assessment For Data Security Management ToolsThis slide represents the comparative analysis assisting businesses to choose correct tools to enhance data security management. It includes various tools such as oracle data safe, satori data security platform, etc. Introducing our Comparative Assessment For Data Security Management Tools set of slides. The topics discussed in these slides are Oracle Data Safe, Data Security Platform, Manager For Databases. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Customer Data Management Icon To Optimize Information Security
Customer Data Management Icon To Optimize Information SecurityPresenting our set of slides with Customer Data Management Icon To Optimize Information Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Customer Data Management, Icon, Optimize Information Security.
-
 Data Security Management Icon To Protect Organizational Information
Data Security Management Icon To Protect Organizational InformationIntroducing our premium set of slides with Data Security Management Icon To Protect Organizational Information. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Security Management, Icon, Protect Organizational Information. So download instantly and tailor it with your information.
-
 Data Security Management Process Icon For Companies
Data Security Management Process Icon For CompaniesPresenting our set of slides with Data Security Management Process Icon For Companies. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Security, Management Process, Icon.
-
 Employee Training Action Plan On Data Security Management
Employee Training Action Plan On Data Security ManagementThis slide showcases the action plan assisting businesses to train their employees on data security management to increase knowledge and awareness. It includes various elements such as courses, modules, duration, rating and deadlines. Introducing our Employee Training Action Plan On Data Security Management set of slides. The topics discussed in these slides are Cloud Data Security, Security And Privacy, Cloud Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 External Threats To Data Security Management With Solutions
External Threats To Data Security Management With SolutionsThis slide showcases various external threats that affect the data security management of businesses with solutions to mitigate those risks. It includes various threats such as SQL injection, ransomware, phishing, and accidental exposure. Introducing our premium set of slides with External Threats To Data Security Management With Solutions. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Accidental Exposure, Unwanted Operations, Secure Mechanism. So download instantly and tailor it with your information.
-
 Framework To Manage Data Security Center Effectively
Framework To Manage Data Security Center EffectivelyThis slide showcases the framework that assist companies to manage and monitor their data center security effectively against threats. It includes various elements such as security operations, application security, security architecture, etc. Presenting our well structured Framework To Manage Data Security Center Effectively. The topics discussed in this slide are Application Platform, Access Management, Application Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Fundamentals To Enhance Data Security Management
Fundamentals To Enhance Data Security ManagementThis slide represents the fundamentals that help businesses to enhance and scale their data security management planning. It includes various elements such as visibility, security as code, automation, monitoring, and assessment. Presenting our set of slides with Fundamentals To Enhance Data Security Management. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Collaborated Protection, Data Security, External Assessment.
-
 Leveraging Technologies To Enhance Data Security Management
Leveraging Technologies To Enhance Data Security ManagementThis slide represents the multiple technologies that assist companies to upgrade and enhance their data security management from threats. It includes technologies such as encryption, data masking, access control, data loss prevention, etc. Introducing our Leveraging Technologies To Enhance Data Security Management set of slides. The topics discussed in these slides are Data Loss Prevention, Access Control, Data Masking. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Management Framework For Enhancing Data Protection
Security Management Framework For Enhancing Data ProtectionThis slide presents the framework that helps businesses to manage data security against modern attack vectors and network vulnerabilities. It includes various elements such as govern, discover, insights, protect and monitor. Presenting our well structured Security Management Framework For Enhancing Data Protection. The topics discussed in this slide are Privacy Readiness, Risk And Security Analytics, Data Driven Outcomes. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Management Policies To Mitigate Internal Data Threats
Security Management Policies To Mitigate Internal Data ThreatsThis slide focuses on the policies for security management helping companies to mitigate internal data threats efficiently. It includes policies for metadata, backup, internal protocol, emails, etc. Introducing our premium set of slides with Security Management Policies To Mitigate Internal Data Threats. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Protocol For Visitors, Internet Protocol, Security Audit. So download instantly and tailor it with your information.
-
 Strategies And Tools To Enhance Big Data Security Management
Strategies And Tools To Enhance Big Data Security ManagementThis slide showcases the strategies and tools helping companies to effectively manage and monitor big data security from cyber threats. It includes strategies such as cloud security monitoring, centralized key management, incident investigation, etc. Introducing our Strategies And Tools To Enhance Big Data Security Management set of slides. The topics discussed in these slides are Cloud Security Monitoring, Centralized Key Management, Network Traffic Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Incident Management Workflow
Cyber Security Incident Management WorkflowThis slide highlights workflow for handlingdigital safety incident. The purpose of this template is to assist businesses in mitigating threats for safeguarding sensitive data and maintain integrity of digital systems. It includes elements such as prepare, detect, analyze, etc. Presenting our set of slides with Cyber Security Incident Management Workflow. This exhibits information on Seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Prepare, Detect, Analyze, Contain
-
 Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access Management
Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access ManagementThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Present the topic in a bit more detail with this Implementing Strategies To Mitigate Cyber Security Reduce Attack Surface With Privilege Access Management Use it as a tool for discussion and navigation on Access Request, Approval Rules, Session Proxy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Strategies For Data Management
Cyber Security Strategies For Data ManagementThe mentioned slide underscores critical strategies, including updated software, firewall protection, awareness of phishing scams, safeguarding sensitive information, and securing mobile devices. These cybersecurity measures collectively contribute to effective data management and protection against potential threats. Introducing our premium set of slides with Cyber Security Strategies For Data Management. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Keep Software Up To Date, Reduced Data Breach Risk, Empowered User Vigilance. So download instantly and tailor it with your information.
-
 Essential Crisis Management Security Tips For Businesses
Essential Crisis Management Security Tips For BusinessesThe purpose of this slide is to outline essential crisis management security tips for businesses, offering proactive strategies to mitigate risks, safeguard assets, and ensure operational resilience in the face of unforeseen challenges. Introducing our premium set of slides with Essential Crisis Management Security Tips For Businesses. Ellicudate the nine stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Learn From Experience, Backup And Recovery Systems, Emergency Response Team, Conduct Risk Assessment.So download instantly and tailor it with your information.
-
 Best Practices For Managing ATP Cyber Security
Best Practices For Managing ATP Cyber SecurityThis slide covers the best practices for ATP cyber security. Its aim is to use the best practice available for anti threat protection for cyber security. This slide includes practices such as evaluation of security, training staff, choose effective solution, evaluate existing security, etc. Introducing our Best Practices For Managing ATP Cyber Security set of slides. The topics discussed in these slides are Assess Organisation Needs, Identify Vulnerabilities, Evaluate Existing Security, Choose Effective Solution. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Threat Detection Icon To Manage Security Gap
Threat Detection Icon To Manage Security GapPresenting our set of slides with name Threat Detection Icon To Manage Security Gap. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Threat Detection Icon, Manage Security Gap.
-
 Cloud Storage Practices For Data Security And Management
Cloud Storage Practices For Data Security And ManagementThis slide highlights ways for managing cloud storage to ensure data protection. The purpose of this slide is to aid businesses in implementing measures for protecting sensitive information from potential threats. It includes elements such as encryption, access control, etc. Presenting our set of slides with Cloud Storage Practices For Data Security And Management. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Encryption, Access Control, Security Training.
-
 Capturing Security Events For Log Management Application Security
Capturing Security Events For Log Management Application SecurityThis slide discusses the selection of security events that need to be logged for application security to ensure user accountability. Introducing Capturing Security Events For Log Management Application Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Authentication Events, User Privilege Changes, Configuration Settings Changes, using this template. Grab it now to reap its full benefits.
-
 Log Management Process In Application Security
Log Management Process In Application SecurityThis slide showcases the introduction of log management in application security for decreasing the security threats. Increase audience engagement and knowledge by dispensing information using Log Management Process In Application Security. This template helps you present information on five stages. You can also present information on Handling Security Logs, Non Compliance Risks Attacks, Ensure Data Security, Log Management Process using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Log Management Best Practices Application Security
Security Log Management Best Practices Application SecurityThis slide highlights the best approaches of logging implementation which include preventing inappropriate actions, employ logging tools, etc. Increase audience engagement and knowledge by dispensing information using Security Log Management Best Practices Application Security. This template helps you present information on five stages. You can also present information on Scrutinize Admin And Operators, Prevent Inappropriate Actions, Ensure Authorized Activities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Identity And Access Management Function As Security Tool IAM Process For Effective Access
Identity And Access Management Function As Security Tool IAM Process For Effective AccessThis slide showcases function of Identity and Access Management as a security tool. The purpose of this slide is to explain the function of IAM as an essential security tool these include context awareness, identity and access governance, and so on. Present the topic in a bit more detail with this Identity And Access Management Function As Security Tool IAM Process For Effective Access. Use it as a tool for discussion and navigation on Context Awareness, Identity And Access Governance, Management Function. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Security Issue IAM Process For Effective Access
Identity And Access Management Security Issue IAM Process For Effective AccessThis slide discusses the security issue of the Identity and Access Management process. The purpose of this slide is to explain the security challenges of IAM these include impractical security policies, inconsistent security policies, slow de-provision, etc. Deliver an outstanding presentation on the topic using this Identity And Access Management Security Issue IAM Process For Effective Access. Dispense information and present a thorough explanation of Impractical Security Policies, Inconsistent Security Policies, Inconsistent Identity Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secured Credit Cards For Boosting Guide To Use And Manage Credit Cards Effectively Fin SS
Secured Credit Cards For Boosting Guide To Use And Manage Credit Cards Effectively Fin SSThis slide shows details regarding secured credit cards which can be used by individuals to increase or develop good credit history. It also includes information related to key points such as credit building, fees and credit limit. Increase audience engagement and knowledge by dispensing information using Secured Credit Cards For Boosting Guide To Use And Manage Credit Cards Effectively Fin SS. This template helps you present information on three stages. You can also present information on Credit Building, Fees, Credit Limit using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Future Trends In Managing Information Security
Future Trends In Managing Information SecurityThis slide highlights future advances in information security management. The purpose of this slide is to provide businesses with innovative security strategies for staying competitive in the market. It includes elements such as cloud security, automation, etc.Introducing our premium set of slides with Future Trends In Managing Information Security. Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cloud Security, Automation, Privacy Regulations. So download instantly and tailor it with your information.
-
 Regulatory Considerations For Managing Information Security
Regulatory Considerations For Managing Information SecurityThis slide highlights compliance aspects for safeguarding data security. The purpose of this template is to assist businesses in adhering to relevant laws and industry standards for building users trust and image in digital world. It includes elements such as GDPR, HIPAA, etc. Introducing our premium set of slides with Regulatory Considerations For Managing Information Security. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Threat Detection, Predictive Analysis, Phishing Detection. So download instantly and tailor it with your information.
-
 Third Party Risk Management Methods In Information Security
Third Party Risk Management Methods In Information SecurityThis slide highlights strategies to control third-party risk in information security. The purpose of this slide is to aid organizations in identifying areas for improvement in their security practices. It includes elements such as vendor assessment, risk classification, etc. Presenting our set of slides with Third Party Risk Management Methods In Information Security. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Vendor Assessment, Contractual Agreements, Maintain Records, Risk Classification
-
 IoT Security Features For Network Management
IoT Security Features For Network ManagementThis slide covers IoT security features introduced in PAN-OS 11.0 with an aim to protect connected devices and network in IoT system. Presenting our set of slides with IoT Security Features For Network Management. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Policy Rule, Traffic Visibility, Alto Networks.
-
 Information Security System Icon For Business Management
Information Security System Icon For Business ManagementIntroducing our premium set of slides with Information Security System Icon For Business Management. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Security System, Business Management. So download instantly and tailor it with your information.
-
 Web Based Software Security Implementation Checklist For Managers
Web Based Software Security Implementation Checklist For ManagersThis slide showcases checklist for SaaS security implementation and assessment. This includes activities such as running security tests, trAIning staff for safety practices, and planning backups for new threats, cloud sources, and security alert systems. Introducing our Web Based Software Security Implementation Checklist For Managers set of slides. The topics discussed in these slides are Run Security Test, Monitoring And Logging, Checklist For Managers. This is an immediately avAIlable PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Endpoint Security Patch Management Technique For Endpoint Security
Endpoint Security Patch Management Technique For Endpoint SecurityThis slide outlines the overview of patch management technique in endpoint security to scan, identify, download, and deploy patches. Introducing Endpoint Security Patch Management Technique For Endpoint Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Fresh Network Security Approach, Works For Windows And Mac, Quick Threat Response, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 IP Security Architecture For Key Management
IP Security Architecture For Key ManagementThis slide showcase model IP security. The main purpose of this template is to showcase encryption algorithm. This includes architecture, ESP protocol, AH Protocol, encryption algorithm, key management, etc. Presenting our well structured IP Security Architecture For Key Management. The topics discussed in this slide are Encryption Algorithm, Authentication Algorithm, Key Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Key Features Of IP Security For Managing Services
Key Features Of IP Security For Managing ServicesThis slide showcases various aspects of IP security. The main purpose of this template is to showcase various ways in which businesses can protect digital assets. This includes authentication, confidentiality, integrity, flexibility, etc. Introducing our premium set of slides with name Key Features Of IP Security For Managing Services. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Authentication, Confidentiality, Key Management, Tunnelling, Flexibility. So download instantly and tailor it with your information.
-
 Advanced Technologies In Automotive Sector For Cyber Security Management
Advanced Technologies In Automotive Sector For Cyber Security ManagementFollowing slide exhibits embedded advanced software and tools used by automotive manufacturer for securing embedded systems against cyber-attacks. It includes gateways, body electronics, dashboard, connected car, hybrid electric vehicle, powertrain and chassis, etc. Presenting our set of slides with Advanced Technologies In Automotive Sector For Cyber Security Management. This exhibits information on ten stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Advanced Driver Assistance System, Hybrid Electric Vehicle, Connected Car.
-
 Best Practices In Cyber Security Risk Management
Best Practices In Cyber Security Risk ManagementThis slide exhibits cyber risk management practices which enable businesses to prioritize risks and apply the right kinds of security controls to minimize impact. It include adaptive and continuous risk management, strict security protocols, cyber security risk management strategy. Introducing our premium set of slides with Best Practices In Cyber Security Risk Management. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Know Organizations IT Environment And Assets. Impose Strict Security Protocols, Adaptive And Continuous Risk Management . So download instantly and tailor it with your information.
-
 Computer Security Icon For Cyber Risk Management
Computer Security Icon For Cyber Risk ManagementPresenting our set of slides with Computer Security Icon For Cyber Risk Management. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Computer Security Icon, Cyber Risk Management.
-
 Cyber Security Management Strategies To Mitigate Threats
Cyber Security Management Strategies To Mitigate ThreatsThis slide highlights different strategies that can help businesses in reducing cyber security threats. It further covers attributes such as priority level, description, mitigating strategies, etc. Presenting our well structured Cyber Security Management Strategies To Mitigate Threats. The topics discussed in this slide are Information Disclosure, Service Denial, Tampering. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Monitoring And Management Icon
Cyber Security Monitoring And Management IconPresenting our set of slides with Cyber Security Monitoring And Management Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security, Monitoring And Management Icon.
-
 Cyber Security Risk Management Lifecycle
Cyber Security Risk Management LifecycleFollowing slide highlights risk management lifecycle of cyber security for maintaining customer trust. It further covers evaluate, analyse, implement and decision and further includes preparing cyber security policy, risk in data collection, etc. Introducing our premium set of slides with Cyber Security Risk Management Lifecycle. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Implement, Evaluate, Decision. So download instantly and tailor it with your information.
-
 Cyber Security Risk Management Plan With Prevention Strategies
Cyber Security Risk Management Plan With Prevention StrategiesFollowing slide includes cyber security plan to systematically assess and mitigation cyber risk within organisation. It further covers, description, risk level, responsible manager, threats and prevention strategies. Introducing our Cyber Security Risk Management Plan With Prevention Strategies set of slides. The topics discussed in these slides are Risk Level, Responsible Manager, Prevention Strategies. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Effective Cyber Security Management Process
Effective Cyber Security Management ProcessFollowing slide showcases process that can help businesses in mitigating cyber security threats. It includes steps such as pinpoint cyber security risks, evaluate cybersecurity risks, mitigation measures, monitoring, etc. Presenting our well structured Effective Cyber Security Management Process. The topics discussed in this slide are Identify The Cybersecurity Risks, Identify Cybersecurity Risks, Mitigation Measures. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Enterprise Network Cyber Security Management
Enterprise Network Cyber Security ManagementFollowing slide represents cyber security management enterprise network for financial protection. It further covers network deployment, feature configuration, network security management, network monitoring and network maintenance, etc. Presenting our set of slides with Enterprise Network Cyber Security Management. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Deployment, Feature Configuration, Network Security Management.
-
 Network Encryption Protection Icon For Cyber Security Management
Network Encryption Protection Icon For Cyber Security ManagementPresenting our set of slides with Network Encryption Protection Icon For Cyber Security Management. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Encryption Protection Icon, Cyber Security Management.
-
 SEO And Web Cyber Security Management Icon
SEO And Web Cyber Security Management IconIntroducing our premium set of slides with SEO And Web Cyber Security Management Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like SEO And Web Cyber, Security Management Icon. So download instantly and tailor it with your information.





