Powerpoint Templates and Google slides for Attacker
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle Cyber
Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle CyberThis slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Preventive Measures For Man In The Middle Cyber to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure Connections, Avoid Phishing Emails, Endpoint Security, Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques Employed In Phishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques Employed In Phishing AttacksThis slide demonstrates the ways utilized by phishers to attack victims. The purpose of this slide is to outline the different methods used by attackers to trick victims. The primary means of attacks are text messages, emails and phone calls from unknown sources. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Primary Techniques Employed In Phishing Attacks. This template helps you present information on three stages. You can also present information on Primary Techniques Employed, Phishing Attacks, Phishers To Attack Victims, Attackers To Trick Victims using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples Of Smishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples Of Smishing AttacksThis slide demonstrates the real-world example of smishing cyber attacks which targeted different individuals and organizations. The popular scams are early access apple iPhone 12 scam, USPS and FedEx scams and mandatory online COVID-19 test scam. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Real World Examples Of Smishing Attacks to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Real World Examples, Smishing Attacks, Smishing Cyber Attacks, Individuals And Organizations, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Resources And Training That Companies Can Provide
Phishing Attacks And Strategies To Mitigate Them V2 Resources And Training That Companies Can ProvideThis slide demonstrates the resources and training that can be provided by companies to their staff. These include employee training, check to see if you have already been breached, be aware of the various phishing attacks, invest in security education, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Resources And Training That Companies Can Provide. This template helps you present information on five stages. You can also present information on Employee Training, Security Education, Phishing Attacks, Resources And Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Roadmap To Secure Organizations From Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Roadmap To Secure Organizations From PhishingThis slide represents the roadmap to prevent phishing attacks in organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Roadmap To Secure Organizations From Phishing to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implement Technical Controls, Establish Policies And Procedures, Employee Training, Baseline Security Assessment, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify Whaling Phishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify Whaling Phishing AttacksThis slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Steps To Identify Whaling Phishing Attacks. This template helps you present information on six stages. You can also present information on Flag Emails Received, Near Similar Email Domains, Spot Grammar, Cross Verify Sensitive Requests using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After Spear Phishing Scam
Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After Spear Phishing ScamIntroducing Phishing Attacks And Strategies To Mitigate Them V2 Steps To Take After Spear Phishing Scam to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing Scam, Change Your Passwords, Backup Your Files, Conduct A Hardware Scan, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Strategies To Identify Smishing Cyber Scams
Phishing Attacks And Strategies To Mitigate Them V2 Strategies To Identify Smishing Cyber ScamsThis slide talks about the various methods of identifying smishing cyber attacks. The purpose of this slide is to help users identify smishing scams. These include suspicious texts from unknown numbers, unrequested links and files, money transfer requests, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Strategies To Identify Smishing Cyber Scams. Use it as a tool for discussion and navigation on Smishing Cyber Attacks, Smishing Scams, Unrequested Links And Files, Money Transfer Requests. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Techniques Used By Cybercriminals To Conduct
Phishing Attacks And Strategies To Mitigate Them V2 Techniques Used By Cybercriminals To ConductThis slide demonstrates the techniques used by scammers to conduct watering hole attacks. These methods are cross-site scripting, DMS cache poisoning, drive-by downloads, malvertising, etc. This slide also outlines common intelligence gathering methods. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Techniques Used By Cybercriminals To Conduct. Use it as a tool for discussion and navigation on Social Networking Sites, Demographic Information From Websites, Social Engineering, Keyloggers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Timeline To Secure Organizations From Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Timeline To Secure Organizations From PhishingThis slide shows the timeline to protect organizations from phishing for different organizations. The key steps include conduct a baseline security assessment, employee training, implement technical controls, establish policies and procedures, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Timeline To Secure Organizations From Phishing. This template helps you present information on five stages. You can also present information on Implement Technical Controls, Employee Training, Establish Policies And Procedures, Timely Evaluation And Updates using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Tools Provided By Google To Prevent Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Tools Provided By Google To Prevent PhishingThis slide demonstrates the different tools provided by Google to prevent and report cyber phishing scams. These include to spot phishing mails with the help of Gmail, utilize safe browsing in chrome, look for unsafe saved passwords, password alert for chrome, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Tools Provided By Google To Prevent Phishing. Dispense information and present a thorough explanation of Safe Browsing In Chrome, Phishing Mails Detection With Gmail, Two Step Verification, Password Alert For Chrome using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Tricks Employed By Malicious Websites To Scam
Phishing Attacks And Strategies To Mitigate Them V2 Tricks Employed By Malicious Websites To ScamThis slide talks about various tricks utilized by fraudulent websites to scam the visitors. The purpose of this slide is to make users aware of such different tricks such as free or discount offers, low interest rates or free credit cards, employment opportunities, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Tricks Employed By Malicious Websites To Scam to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Employment Opportunities, Emergency Warnings, Malicious Websites, Scam Victims, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Understanding The Process Of E Mail Based Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Understanding The Process Of E Mail Based PhishingThis slide demonstrates the procedure of email-based phishing attacks. The purpose of this slide is to explain how fake websites are used by attackers to get the sensitive data of the users. The key components include database, fake website, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Understanding The Process Of E Mail Based Phishing. Use it as a tool for discussion and navigation on Email Based Phishing Attacks, Fake Website, Phishing Email, Original Website. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And Code
Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And CodeThis slide talks about the techniques which can help in protecting organizations from phishing and vishing attacks. The purpose of this slide is to explain two important methods of preventing cyber scams. These techniques are email signing and code signing. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Vishing Attacks Prevention Email Signing And Code. Dispense information and present a thorough explanation of Vishing Attacks Prevention, Email Signing And Code Signing, Preventing Cyber Scams using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Warning Signs Of Pop Up Phishing Scams
Phishing Attacks And Strategies To Mitigate Them V2 Warning Signs Of Pop Up Phishing ScamsThis slide outlines the various warning signs which helps in identifying pop-up phishing cyber attacks. These include terrible pop-up advertisement, warnings to act fast, immediate scan of computer virus, pop-ups are difficult to close and unpopular company names. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Warning Signs Of Pop Up Phishing Scams to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Terrible Pop Up Advertisement, Pop Up Phishing Cyber Attacks, Install Their Malware, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Why Businesses Fall Victim To Phishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Why Businesses Fall Victim To Phishing AttacksThis slide outlines the various reasons responsible for businesses to fall victim to different phishing attacks. These include inadequate employee training, never evaluate the success of the training, careless browsing habits of the employees, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Why Businesses Fall Victim To Phishing Attacks. This template helps you present information on five stages. You can also present information on Inadequate Employee Training, Training Or Policy Improvement, Organizations Are Unaware, Changing Phishing Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Working Of Phishing Training Programs
Phishing Attacks And Strategies To Mitigate Them V2 Working Of Phishing Training ProgramsIntroducing Phishing Attacks And Strategies To Mitigate Them V2 Working Of Phishing Training Programs to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Start With Employee Training, Make Fictitious Phishing Campaigns, Track Progress And Upgrade, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Working Of Watering Hole Phishing Attack
Phishing Attacks And Strategies To Mitigate Them V2 Working Of Watering Hole Phishing AttackThis slide represents the working process of watering hole phishing attacks. The purpose of this slide is to illustrate the flow diagram of watering hole phishing scams. The key points include research and identification, analysis, preparation and execution. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Working Of Watering Hole Phishing Attack. This template helps you present information on four stages. You can also present information on Analysis, Research And Identification, Preparation, Execution, Phishing Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Working Procedure Of Spear Phishing Attack
Phishing Attacks And Strategies To Mitigate Them V2 Working Procedure Of Spear Phishing AttackThis slide illustrates the structure of spear phishing attack. The purpose of this slide is to explain the working flow of spear phishing attack. The key components include attacker, phishing email, targeted users, exploited system, internal network, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Working Procedure Of Spear Phishing Attack to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Email, Targeted Users, Exploited System, Internal Network, Attacker, using this template. Grab it now to reap its full benefits.
-
 Real World Examples Of Watering Hole Phishing Attacks And Strategies To Mitigate Them V2
Real World Examples Of Watering Hole Phishing Attacks And Strategies To Mitigate Them V2This slide describes the real-world examples of watering hole phishing scams. These include Facebook, Twitter, Microsoft, and Apple scam, LuckyMouse scam, International Civil Aviation Organization ICAO scam, Ccleaner scam and Holy Water scam. Increase audience engagement and knowledge by dispensing information using Real World Examples Of Watering Hole Phishing Attacks And Strategies To Mitigate Them V2. This template helps you present information on four stages. You can also present information on International Civil Aviation, Organization Scam, Watering Hole Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Content For Phishing Attacks And Strategies To Mitigate Them V2
Table Of Content For Phishing Attacks And Strategies To Mitigate Them V2Introducing Table Of Content For Phishing Attacks And Strategies To Mitigate Them V2 to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Attacks Prevention, Phishing Attacks Awareness Training, Phishing Attacks Introduction, using this template. Grab it now to reap its full benefits.
-
 Man In The Middle Mobile Banking Attacking Methods E Wallets As Emerging Payment Method Fin SS V
Man In The Middle Mobile Banking Attacking Methods E Wallets As Emerging Payment Method Fin SS VThis slide shows overview of popular cyberattack related to mobile banking which is man in the middle MiTM. It also includes popular types of this attack which are WIFI network interception, DNS spoofing, email interception and malware. Present the topic in a bit more detail with this Man In The Middle Mobile Banking Attacking Methods E Wallets As Emerging Payment Method Fin SS V. Use it as a tool for discussion and navigation on Interception, Communication, Web Application. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Emerging Technologies Various Types Of Cyber Attacks On System
Emerging Technologies Various Types Of Cyber Attacks On SystemThis slide explains Various types of cyber attacks on system on a system such as malware, phishing, man in the middle, distributed denial of service, brute force, SQL injection, and domain name system. Increase audience engagement and knowledge by dispensing information using Emerging Technologies Various Types Of Cyber Attacks On System. This template helps you present information on seven stages. You can also present information on Malware, Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Trending Technologies Various Types Of Cyber Attacks On System
Trending Technologies Various Types Of Cyber Attacks On SystemThis slide explains Various types of cyber attacks on system on a system such as malware, phishing, man in the middle, distributed denial of service, brute force, SQL injection, and domain name system. Increase audience engagement and knowledge by dispensing information using Trending Technologies Various Types Of Cyber Attacks On System. This template helps you present information on eight stages. You can also present information on Malware, Phishing, Brute Force using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Governance Attack In Powerpoint And Google Slides Cpb
Governance Attack In Powerpoint And Google Slides CpbPresenting Governance Attack In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Governance Attack This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Fasting Ibs Attack In Powerpoint And Google Slides Cpb
Fasting Ibs Attack In Powerpoint And Google Slides CpbPresenting our Fasting Ibs Attack In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Fasting Ibs Attack This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security Attacks In Powerpoint And Google Slides Cpb
Security Attacks In Powerpoint And Google Slides CpbPresenting Security Attacks In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Attacks. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Small Business Cyber Attack Examples In Powerpoint And Google Slides Cpb
Small Business Cyber Attack Examples In Powerpoint And Google Slides CpbPresenting Small Business Cyber Attack Examples In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Small Business Cyber Attack Examples. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 How Does Dos Attack Work Improving IoT Device Cybersecurity IoT SS
How Does Dos Attack Work Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase working of Denial of Service DoS attack working. It covers information about target identification, exploiting weaknesses, target flooding, exhausting system capabilities Introducing How Does Dos Attack Work Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Target, Exploiting, Flooding, using this template. Grab it now to reap its full benefits.
-
 How Does IoT Botnet Attack Work Improving IoT Device Cybersecurity IoT SS
How Does IoT Botnet Attack Work Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase working of Internet of Things IoT botnet attack. The botnet attack begins with scanning vulnerable IoT devices, gaining access to IoT devices, malware installation, botnet expansion, and conducting malicious activities. Increase audience engagement and knowledge by dispensing information using How Does IoT Botnet Attack Work Improving IoT Device Cybersecurity IoT SS. This template helps you present information on five stages. You can also present information on Devices, Gaining, Installation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does IoT Password Attack Work Improving IoT Device Cybersecurity IoT SS
How Does IoT Password Attack Work Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase working of Internet of Things IoT password attack. It covers information about gaining control of IoT device, records conversation, collects private video recordings, sends sensitive data to malicious user, etc. Present the topic in a bit more detail with this How Does IoT Password Attack Work Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Cybercriminal, Server, Default. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How Does Ransomware Attack Work Improving IoT Device Cybersecurity IoT SS
How Does Ransomware Attack Work Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase the working of ransomware attack. The attack begins with installing malware in IoT devices, identifying files stored on local devices, establishing key exchange with control server, covering instruction files, etc. Increase audience engagement and knowledge by dispensing information using How Does Ransomware Attack Work Improving IoT Device Cybersecurity IoT SS. This template helps you present information on seven stages. You can also present information on Devices, Exchange, Covers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Introduction To Denial Of Service Dos Attack Improving IoT Device Cybersecurity IoT SS
Introduction To Denial Of Service Dos Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to provide glimpse of Denial of Service DoS attack. It also covers information about signs of DoS attack such as poor network performance of IoT devices, specific website doesnt opened, increasing volume of email spam, etc. Increase audience engagement and knowledge by dispensing information using Introduction To Denial Of Service Dos Attack Improving IoT Device Cybersecurity IoT SS. This template helps you present information on four stages. You can also present information on Accessing, Website, Increasing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Introduction To IoT Botnet Attack And Its Improving IoT Device Cybersecurity IoT SS
Introduction To IoT Botnet Attack And Its Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to provide glimpse of Internet of Things IoT botnet attack along with its features. The features mentioned in slide are related to taking advantages of security vulnerabilities, issuing instructions through centralized command, etc. Increase audience engagement and knowledge by dispensing information using Introduction To IoT Botnet Attack And Its Improving IoT Device Cybersecurity IoT SS. This template helps you present information on five stages. You can also present information on Vulnerabilities, Compromised, Centralized using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Introduction To IoT Password Attack And Improving IoT Device Cybersecurity IoT SS
Introduction To IoT Password Attack And Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to provide glimpse of Internet of Things IoT attack and its major characteristics. It covers information about using multiple software, using pre built default wordlist, using compromised login credentials, scanning for open port, etc. Increase audience engagement and knowledge by dispensing information using Introduction To IoT Password Attack And Improving IoT Device Cybersecurity IoT SS. This template helps you present information on seven stages. You can also present information on Software, Credentials, Technique using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Introduction To Ransomware Attack And Improving IoT Device Cybersecurity IoT SS
Introduction To Ransomware Attack And Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to provide glimpse of ransomware attack which can cause deny user to access to files on their system. It also covers information abut ransomware attack features such as focusing on industrial control system, smart home devices, etc. Present the topic in a bit more detail with this Introduction To Ransomware Attack And Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Industrial, Software, Functionalities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Access Points To Malicious Attackers Improving IoT Device Cybersecurity IoT SS
IoT Access Points To Malicious Attackers Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to delineate various Internet of Things IoT access points that can be accessed by hackers. The slide covers information about edge computing, communication network, and cloud computing. Increase audience engagement and knowledge by dispensing information using IoT Access Points To Malicious Attackers Improving IoT Device Cybersecurity IoT SS. This template helps you present information on four stages. You can also present information on Devices, Hardware, Commonly using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IoT Cyber Attack Scenario In Self Automated Improving IoT Device Cybersecurity IoT SS
IoT Cyber Attack Scenario In Self Automated Improving IoT Device Cybersecurity IoT SSPresent the topic in a bit more detail with this IoT Cyber Attack Scenario In Self Automated Improving IoT Device Cybersecurity IoT SS. Use it as a tool for discussion and navigation on Systems, Updates, Connectivity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Cyber Attack Scenario In Smart Home Improving IoT Device Cybersecurity IoT SS
IoT Cyber Attack Scenario In Smart Home Improving IoT Device Cybersecurity IoT SSDeliver an outstanding presentation on the topic using this IoT Cyber Attack Scenario In Smart Home Improving IoT Device Cybersecurity IoT SS. Dispense information and present a thorough explanation of Identification, Temperature, Identity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mirai Botnet Attack Caused By IoT Improving IoT Device Cybersecurity IoT SS
Mirai Botnet Attack Caused By IoT Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline the most common example of IoT cybersecurity attack. The slide covers information about attack type, attack description, impact of Mirai Botnet attack, and key intakes for business leaders. Introducing Mirai Botnet Attack Caused By IoT Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Distributed, Various, Credentials, using this template. Grab it now to reap its full benefits.
-
 Real Life Example Of Ransomware Attack Improving IoT Device Cybersecurity IoT SS
Real Life Example Of Ransomware Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline illustration of ransomware attack. WannaCry, Crypto Locker, and Fake Flash Player are some of the major attacks which are mentioned in slide along with their impact. Introducing Real Life Example Of Ransomware Attack Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Running, Locker, Player, using this template. Grab it now to reap its full benefits.
-
 Real Life Examples Of Botnet Attack Improving IoT Device Cybersecurity IoT SS
Real Life Examples Of Botnet Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline real life example of Internet of Things IoT botnet attack. The attacks mentioned in slide are Kneber Botnet, Avalanche Botnet, and Sality Botnet along with potential impact of each attack. Increase audience engagement and knowledge by dispensing information using Real Life Examples Of Botnet Attack Improving IoT Device Cybersecurity IoT SS. This template helps you present information on three stages. You can also present information on Botnet, Avalanche, Attachment using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Real Life Examples Of Dos Attack Improving IoT Device Cybersecurity IoT SS
Real Life Examples Of Dos Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to showcase real life illustration of Denial of Service DoS attack. It covers information about attacks such as GitHub attack, PlayStation Network Attack, and Dyn attack along with potential impact of each attack. Introducing Real Life Examples Of Dos Attack Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Attack, Network, Managing, using this template. Grab it now to reap its full benefits.
-
 Real Life Examples Of IoT Password Attack Improving IoT Device Cybersecurity IoT SS
Real Life Examples Of IoT Password Attack Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to outline real life illustrations of Internet of Things IoT password attack. Information covered in this slide attack description, various strategies used to conduct password attack, and potential impact. Increase audience engagement and knowledge by dispensing information using Real Life Examples Of IoT Password Attack Improving IoT Device Cybersecurity IoT SS. This template helps you present information on two stages. You can also present information on Conduct, Techniques, Potential using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Stuxnet Attack Caused By IoT Security Improving IoT Device Cybersecurity IoT SS
Stuxnet Attack Caused By IoT Security Improving IoT Device Cybersecurity IoT SSThe purpose of this slide is to highlight overview of Stuxnet attack caused by Internet of Things IoT security vulnerability. The slide covers information about attack occurred date, its overview, impact of Stuxnet attack, and key takeaways for companies. Introducing Stuxnet Attack Caused By IoT Security Improving IoT Device Cybersecurity IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Efficiency, Reduction, Damage, using this template. Grab it now to reap its full benefits.
-
 Dos Attack Types In Powerpoint And Google Slides Cpb
Dos Attack Types In Powerpoint And Google Slides CpbPresenting Dos Attack Types In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Dos Attack Types. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Types Of Attacks Prevented By Cloud Cryptography Cloud Cryptography
Types Of Attacks Prevented By Cloud Cryptography Cloud CryptographyThis purpose of this slide is to explain how cloud cryptography can help prevent several types of attacks that can compromise the confidentiality, integrity, and availability of data in cloud environments. These include Man-in-the-middle MitM attacks, data breaches, insider attacks, etc. Increase audience engagement and knowledge by dispensing information using Types Of Attacks Prevented By Cloud Cryptography Cloud Cryptography. This template helps you present information on four stages. You can also present information on Data Breaches, Insider Attacks, Denial Of Service using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Attack Bank In Powerpoint And Google Slides Cpb
Cyber Attack Bank In Powerpoint And Google Slides CpbPresenting our Cyber Attack Bank In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases Four stages. It is useful to share insightful information on Cyber Attack Bank This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
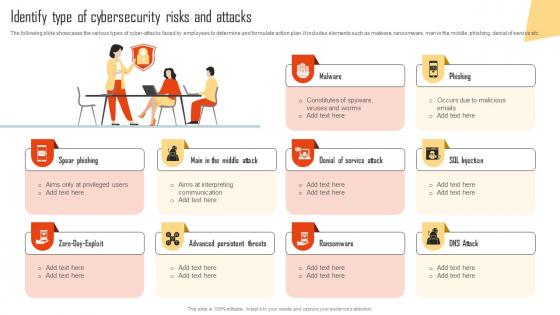 Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks Management
Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks ManagementThe following slide showcases the various types of cyber-attacks faced by employees to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service etc. Introducing Identify Type Of Cybersecurity Risks And Attacks Improving Cyber Security Risks Management to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing, Advanced Persistent Threats, Ransomware, Phishing, using this template. Grab it now to reap its full benefits.
-
 Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks Management
Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks ManagementThe following slide illustrates some best practices to execute preventive actions for cyber attacks. It includes elements such as train employees, updating systems and software, developing incident response plan, backing up data, maintaining compliance etc. Increase audience engagement and knowledge by dispensing information using Implement Best Practices To Prevent Cyber Attacks Improving Cyber Security Risks Management. This template helps you present information on six stages. You can also present information on Train Employees, Maintain Compliance, Develop Incident Response Plan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Attacks Government In Powerpoint And Google Slides Cpb
Cyber Attacks Government In Powerpoint And Google Slides CpbPresenting our Cyber Attacks Government In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cyber Attacks Government This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Ultimate Guide For Blockchain Threats Imposed By Sybil Attack On Blockchain Network BCT SS
Ultimate Guide For Blockchain Threats Imposed By Sybil Attack On Blockchain Network BCT SSThe following slide represents the number of cryptocurrencies theft incidents by total amount to prevent attackers from unauthorized access. It includes elements such as ronin, poly network, wormhole, bitmart, venus, cream finance, along with key insights, etc. Deliver an outstanding presentation on the topic using this Ultimate Guide For Blockchain Threats Imposed By Sybil Attack On Blockchain Network BCT SS Dispense information and present a thorough explanation of Breach Of Privacy, Block Users From Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Various Types Of Cyber Attacks On System Modern Technologies
Various Types Of Cyber Attacks On System Modern TechnologiesThis slide explains Various types of cyber attacks on system on a system such as malware,phishing,man in the middle,distributed denial of service,brute force,SQL injection,and domain name system. Introducing Various Types Of Cyber Attacks On System Modern Technologies to increase your presentation threshold. Encompassed with seven stages,this template is a great option to educate and entice your audience. Dispence information on Information Found,Conceivable Using,Cryptographic Trick,using this template. Grab it now to reap its full benefits.
-
 Insider Attack Cyber Security In Powerpoint And Google Slides Cpb
Insider Attack Cyber Security In Powerpoint And Google Slides CpbPresenting our Insider Attack Cyber Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Insider Attack Cyber Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber Attack Banks In Powerpoint And Google Slides Cpb
Cyber Attack Banks In Powerpoint And Google Slides CpbPresenting Cyber Attack Banks In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Attack Banks. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber Attacks Research Paper In Powerpoint And Google Slides Cpb
Cyber Attacks Research Paper In Powerpoint And Google Slides CpbPresenting our Cyber Attacks Research Paper In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Cyber Attacks Research Paper This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Anxiety Attack Help Tips In Powerpoint And Google Slides Cpb
Anxiety Attack Help Tips In Powerpoint And Google Slides CpbPresenting Anxiety Attack Help Tips In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Anxiety Attack Help Tips. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Crypto Attack In Powerpoint And Google Slides Cpb
Crypto Attack In Powerpoint And Google Slides CpbPresenting Crypto Attack In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Crypto Attack. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 News Reporter Attacked In Powerpoint And Google Slides Cpb
News Reporter Attacked In Powerpoint And Google Slides CpbPresenting News Reporter Attacked In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like News Reporter Attacked This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 How Does Phishing Attack Works On Blockchain Network Hands On Blockchain Security Risk BCT SS V
How Does Phishing Attack Works On Blockchain Network Hands On Blockchain Security Risk BCT SS VThe following slide depicts the workflow model of phishing attack carried out on blockchain network. It includes activities such as attackers sending emails to users, opening up emails, obtaining information from system, stealing data from user, etc. Present the topic in a bit more detail with this How Does Phishing Attack Works On Blockchain Network Hands On Blockchain Security Risk BCT SS V. Use it as a tool for discussion and navigation on Attacker, Phishing Email, Internet Network. This template is free to edit as deemed fit for your organization. Therefore download it now.





