Powerpoint Templates and Google slides for Attacker
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Attack Control Dashboard
Cyber Security Attack Control DashboardThis slide highlights the data to track cyber attack attempted on the company to analyze and make strategies to prevent from these attacks and protect sensitive data. It includes various KPIs such as malicious emails, malicious files, malicious websites, etc. Introducing our Cyber Security Attack Control Dashboard set of slides. The topics discussed in these slides are Malicious Emails, Malicious Files, Malicious Websites This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Minimize The Attack Surface Of Your IoT Ecosystem Internet Of Things IoT Security Cybersecurity SS
Minimize The Attack Surface Of Your IoT Ecosystem Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of attack surface minimization on internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about unused points, configuration, etc. Deliver an outstanding presentation on the topic using this Minimize The Attack Surface Of Your IoT Ecosystem Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Eliminate Unused Points, System Security, Exploitation Opportunities, Probability Of Unauthorized Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Attack Statistics Strategic Implementation Of Regression Testing
Attack Statistics Strategic Implementation Of Regression TestingThis slide summarizes security attacks across different organizational departments, such as network operation centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on. Present the topic in a bit more detail with this Attack Statistics Strategic Implementation Of Regression Testing. Use it as a tool for discussion and navigation on Security Concerns, Key Takeaways, Security Operations. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
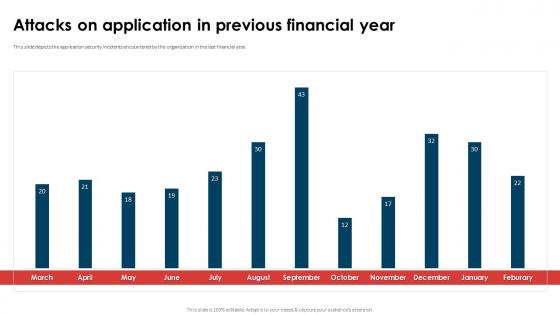 Application Security Implementation Plan Attacks On Application In Previous Financial Year
Application Security Implementation Plan Attacks On Application In Previous Financial YearThis slide depicts the threat scanning dashboard for application security to analyze and monitor vulnerabilities of application. Deliver an outstanding presentation on the topic using this Application Security Implementation Plan Attacks On Application In Previous Financial Year. Dispense information and present a thorough explanation of Attacks On Application, Previous Financial Year, Application Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Statistics Of Existing It Infrastructure Attacks Vpn Implementation Plan
Statistics Of Existing It Infrastructure Attacks Vpn Implementation PlanThis slide discusses the issues faced by the organization due to existing IT infrastructure such as data interception, unauthorized access, etc.Present the topic in a bit more detail with this Statistics Of Existing It Infrastructure Attacks Vpn Implementation Plan. Use it as a tool for discussion and navigation on Sales, Finance, Marketing, Analytics. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Dashboard For Tracking Cyber Security Attack Business Recovery Plan To Overcome Cyber Security Threat
Dashboard For Tracking Cyber Security Attack Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides a graphical presentation of cyber attacks and costs per incident. It includes key elements such as cost per incident, attack rate by month, cost of incident by assets, and time taken to detect and resolve the attack. Deliver an outstanding presentation on the topic using this Dashboard For Tracking Cyber Security Attack Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Dashboard, Reported Incidents, Graphical Presentation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
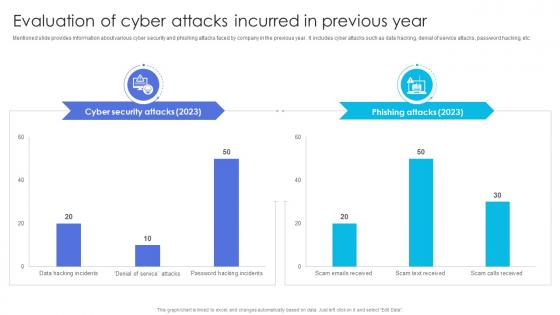 Evaluation Attacks Incurred In Previous Year Business Recovery Plan To Overcome Cyber Security Threat
Evaluation Attacks Incurred In Previous Year Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various cyber security and phishing attacks faced by company in the previous year. It includes cyber attacks such as data hacking, denial of service attacks, password hacking, etc. Deliver an outstanding presentation on the topic using this Evaluation Attacks Incurred In Previous Year Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Information, Service, Evaluation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Current Frauds Attacks Faced By Ecommerce Business Implementing E Commerce Security Measures
Current Frauds Attacks Faced By Ecommerce Business Implementing E Commerce Security MeasuresThis slide portrays the common types of fraud attacks experienced by ecommerce businesses in recent years. It include frauds such as card testing, phishing, account takeover and the reason of attacks. Deliver an outstanding presentation on the topic using this Current Frauds Attacks Faced By Ecommerce Business Implementing E Commerce Security Measures. Dispense information and present a thorough explanation of Poor Website Security, In Frequent Monitoring, Secure Payment Verification using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Financial Impact Of Endpoint Security Attacks Building Next Generation Endpoint Security Cybersecurity SS
Financial Impact Of Endpoint Security Attacks Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases financial impact of endpoint attacks, which can help organizations assess their costs and plan recovery strategies of system downtime, information assets, etc.Deliver an outstanding presentation on the topic using this Financial Impact Of Endpoint Security Attacks Building Next Generation Endpoint Security Cybersecurity SS. Dispense information and present a thorough explanation of Zero Day, Polymorphic Malware, Malicious Code using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
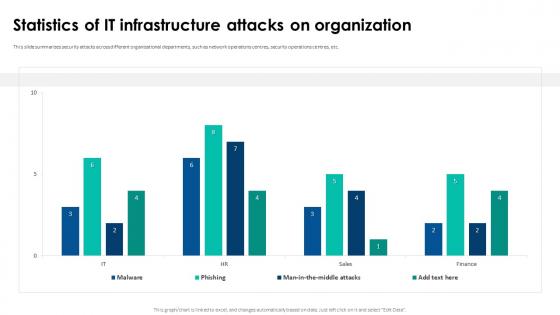 Web Security Upgradation Statistics Of It Infrastructure Attacks On Organization
Web Security Upgradation Statistics Of It Infrastructure Attacks On OrganizationThis slide summarizes security attacks across different organizational departments, such as network operations centres, security operations centres, etc. Present the topic in a bit more detail with this Web Security Upgradation Statistics Of It Infrastructure Attacks On Organization. Use it as a tool for discussion and navigation on Statistics Of IT Infrastructure, Attacks On Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Web Security Upgradation Web Attacks Experienced By Company In Previous Financial Year
Web Security Upgradation Web Attacks Experienced By Company In Previous Financial YearThis slide depicts the web security incidents encountered by the organization in the last financial year. Present the topic in a bit more detail with this Web Security Upgradation Web Attacks Experienced By Company In Previous Financial Year. Use it as a tool for discussion and navigation on Web Attacks Experienced By Company, Previous Financial Year. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Common Types Of Email Security Attacks
Email Security Best Practices Common Types Of Email Security AttacksThe purpose of this slide is to discuss the different types of email security threats in current digital era. These email security attacks are phishing, social engineering, spear phishing, ransomware, malware and spoofing. Introducing Email Security Best Practices Common Types Of Email Security Attacks to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Phishing, Social Engineering, Spear Phishing, Ransomware, using this template. Grab it now to reap its full benefits.
-
 IOT Security Dashboard To Track Attack Status
IOT Security Dashboard To Track Attack StatusThis provides an overview of the dashboard to determine number of potential threats. It includes events triggered, new and unique devices, DDoS threats, ransomware and miners threat. Introducing our IOT Security Dashboard To Track Attack Status set of slides. The topics discussed in these slides are New Device, Hotspot Active, Insecure Device. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Penetration Testing Implementation Plan Statistics Of It Infrastructure Attacks In Organization
Penetration Testing Implementation Plan Statistics Of It Infrastructure Attacks In OrganizationThis slide summarizes security attacks across different organizational departments, such as network operations centres, security operations centres, etc. The outlined departments such as network operations centre, security operation centre and so on. Deliver an outstanding presentation on the topic using this Penetration Testing Implementation Plan Statistics Of It Infrastructure Attacks In Organization. Dispense information and present a thorough explanation of Security Operations Center, Network Operations Center, Security Concerns using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Attacks On Employee Mobile Devices Mobile Device Security Cybersecurity SS
Cyber Attacks On Employee Mobile Devices Mobile Device Security Cybersecurity SSThis slide showcases cyber threats faced by workforce on mobile devices. It highlights data regarding malware, phishing attacks, ransomware etc. Present the topic in a bit more detail with this Cyber Attacks On Employee Mobile Devices Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Awareness Training, Weak Security Measures This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SS
Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SSThis slide showcases decrease in cyber attacks after implementation of mobile security. Its key elements are malware, phishing attacks and ransomware Deliver an outstanding presentation on the topic using this Cyber Attacks Reduction After Implementing Mobile Security Techniques Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Advanced Persistent Threats, Diverse Cyber Threat Landscape using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Decrease In Cyber Attacks On Different Mobile Devices Mobile Device Security Cybersecurity SS
Decrease In Cyber Attacks On Different Mobile Devices Mobile Device Security Cybersecurity SSThis slide showcases decline in cyber attacks after implementation of mobile security techniques. It highlights decrease in cyber attacks on android and iOS devices Deliver an outstanding presentation on the topic using this Decrease In Cyber Attacks On Different Mobile Devices Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Security Attacks, Mobile Devices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mobile Cyber Attacks Occurrence Globally Mobile Device Security Cybersecurity SS
Mobile Cyber Attacks Occurrence Globally Mobile Device Security Cybersecurity SSThis slide showcases number of cyber attacks faced by mobile users around the world. It highlights data regarding attacks faced in last three years Deliver an outstanding presentation on the topic using this Mobile Cyber Attacks Occurrence Globally Mobile Device Security Cybersecurity SS Dispense information and present a thorough explanation of Fingerprint Scanner, Facial Recognition, Voice Recognition using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mobile Malware Attacks By Country Share Mobile Device Security Cybersecurity SS
Mobile Malware Attacks By Country Share Mobile Device Security Cybersecurity SSThis slide showcases percentage share of mobile malware attacks faced in different countries. It highlights share of China, Iran, Yemen, Switzerland, Kenya etc. Present the topic in a bit more detail with this Mobile Malware Attacks By Country Share Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Purpose, Scope, Loss And Theft This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Introduction To Types Of Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS
Introduction To Types Of Attacks In Cyberterrorism Strategic Guide To Implement Strategy SSThis slide showcases the different types of attacks in cyber terrorism. It includes attacks such as DoS and DDoS attack, Man-in-the-Middle MITM attack, Phishing attack, Whale phishing attack, Spear phishing attack and Ransomware attack.Increase audience engagement and knowledge by dispensing information using Introduction To Types Of Attacks In Cyberterrorism Strategic Guide To Implement Strategy SS. This template helps you present information on six stages. You can also present information on Whale Phishing Attack, Spear Phishing Attack, Ransomware Attack, Phishing Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Password Authentication For Protection Against Brute Force Attacks Cybersecurity SS
Password Authentication For Protection Against Brute Force Attacks Cybersecurity SSThis slide outlines strategies for protecting networks from brute-force attacks, including password authentication methods such as limiting the number of login attempts and password requests etc.Deliver an outstanding presentation on the topic using this Password Authentication For Protection Against Brute Force Attacks Cybersecurity SS. Dispense information and present a thorough explanation of Password Authentication, Solutions, Login Attempts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SS
Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SSThis slide shows the impact of strategies implemented by IT and security professionals to prevent and mitigate network vulnerabilities, including phishing attacks, malware attacks, insider attacks and software vulnerabilities.Deliver an outstanding presentation on the topic using this Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SS. Dispense information and present a thorough explanation of Cyber Attacks, Secure Passwords, Compliant Monitoring And Auditing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Dashboard For Supply Chain Attack Management For Data Protection
Dashboard For Supply Chain Attack Management For Data ProtectionThis slide represents dashboard that helps companies to manage supply chain attacks for improving security management measures. It includes various components such a policy and compliance, resource security hygiene, and threat protection. Presenting our well structured Dashboard For Supply Chain Attack Management For Data Protection. The topics discussed in this slide are Policy And Compliance, Resource Security Hygiene, Threat Protection. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Tools To Address Supply Chain Cybersecurity Attacks For Data Protection
Tools To Address Supply Chain Cybersecurity Attacks For Data ProtectionThis slide graphically represents use of various tools and approaches that assist companies in addressing various supply chain cybersecurity attacks and optimizing data protection. It includes tools such as IT vendor risk management tools, supply chain risk management tools, etc. Presenting our well structured Tools To Address Supply Chain Cybersecurity Attacks For Data Protection. The topics discussed in this slide are Audits Of Suppliers, Manufacturers, Logistics Partners. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Example active cyber attack ppt powerpoint presentation file samples cpb
Example active cyber attack ppt powerpoint presentation file samples cpbPresenting our Example Active Cyber Attack Ppt Powerpoint Presentation File Samples Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Example Active Cyber Attack This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Reverse engineering attack ppt powerpoint presentation show slide download cpb
Reverse engineering attack ppt powerpoint presentation show slide download cpbPresenting our Reverse Engineering Attack Ppt Powerpoint Presentation Show Slide Download Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Reverse Engineering Attack This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber security attacks examples ppt powerpoint presentation infographics examples cpb
Cyber security attacks examples ppt powerpoint presentation infographics examples cpbPresenting Cyber Security Attacks Examples Ppt Powerpoint Presentation Infographics Examples Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Security Attacks Examples. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Responding Cyber Attacks In Powerpoint And Google Slides Cpb
Responding Cyber Attacks In Powerpoint And Google Slides CpbPresenting our Responding Cyber Attacks In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Responding Cyber Attacks. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Ransomware Attack In Powerpoint And Google Slides Cpb
Ransomware Attack In Powerpoint And Google Slides CpbPresenting our Ransomware Attack In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Ransomware Attack This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Types Of Cyber Attacks Faced By How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS
Types Of Cyber Attacks Faced By How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SSThis slide showcases various types of cyber attacks that significantly damage the organization resources and reputation. Different types of attacks faced are Malware, Phishing, Man in middle attack, SQL injection etc. Introducing Types Of Cyber Attacks Faced By How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Software, Financial, Results, using this template. Grab it now to reap its full benefits.
-
 Data Breach Prevention And Mitigation Checklist For Responding To A Data Breach Attack
Data Breach Prevention And Mitigation Checklist For Responding To A Data Breach AttackThis slide represents the checklist for implementing a data breach response plan. The fundamental approaches are identify and isolate impacted systems or networks, perform a formal risk assessment, restore systems and address security flaws, notify affected parties, etc. Present the topic in a bit more detail with this Data Breach Prevention And Mitigation Checklist For Responding To A Data Breach Attack. Use it as a tool for discussion and navigation on Data Breach Response Plan, Fundamental Approaches, Systems Or Networks, Perform A Formal Risk Assessment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention And Mitigation Common Data Breach Attack Vectors
Data Breach Prevention And Mitigation Common Data Breach Attack VectorsThis slide represents several data breach attack vectors. The main components are stolen or compromised credentials, social engineering attacks, ransomware, system vulnerabilities, human error and IT failures, physical or site security errors, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention And Mitigation Common Data Breach Attack Vectors. Dispense information and present a thorough explanation of Brute Force Attacks, Purchasing Stolen Credentials, Phishing Scams, Fraudulent Emails, Deceptive Websites using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention And Mitigation Data Breach Attacks Experienced By Major Business
Data Breach Prevention And Mitigation Data Breach Attacks Experienced By Major BusinessThis slide highlights the top data breach victims based on different industrial sectors. These industries include email service providers, social media websites, online auction websites, retail services, government agencies, file-sharing and hosting services, etc. Present the topic in a bit more detail with this Data Breach Prevention And Mitigation Data Breach Attacks Experienced By Major Business. Use it as a tool for discussion and navigation on Heartland Payment Systems, Email Service Provider, Social Media Website, Online Auction Website. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Breach Prevention And Mitigation Different Modes Of Data Breach Attack
Data Breach Prevention And Mitigation Different Modes Of Data Breach AttackThis slide discusses the unintentional and intentional methods of data breach attacks. The examples outlined in this slide are accessing unsecured websites, downloading compromised software, losing work devices in a public place, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention And Mitigation Different Modes Of Data Breach Attack. Dispense information and present a thorough explanation of Unintentional And Intentional Methods, Data Breach Attacks, Unsecured Websites, Downloading Compromised Software, Losing Work Devices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention Major Consequences Of Data Breach Cyber Attack
Data Breach Prevention Major Consequences Of Data Breach Cyber AttackThis slide demonstrates the impact of data breach attacks on individuals and organizations. The main consequences of the data breach are financial loss, reputational damage, legal matters, identity theft, and intellectual property loss. Introducing Data Breach Prevention Major Consequences Of Data Breach Cyber Attack to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Intellectual Property Loss, Financial Loss, Reputational Damage, Legal Consequences, using this template. Grab it now to reap its full benefits.
-
 Data Breach Prevention Phases Of Data Breach Attack Cycle
Data Breach Prevention Phases Of Data Breach Attack CycleThis slide represents the flow diagram of the data breach attack cycle. The major components of this slide are research, stage attack, exfiltrate, social engineering, attacker, weak infrastructure, database, server, accessed data, HTTP, FTP, email, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention Phases Of Data Breach Attack Cycle. Dispense information and present a thorough explanation of Infrastructure Weakness, Accessed Data, Social Engineering, Attacker Transfers Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention Vulnerabilities Targeted In Data Breach Attacks
Data Breach Prevention Vulnerabilities Targeted In Data Breach AttacksThe purpose of this slide is to discuss the most vulnerable target points of data breach attacks. The significant vulnerabilities include weak credentials, stolen information, compromised assets, payment card fraud, third-party access, mobile devices, etc. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention Vulnerabilities Targeted In Data Breach Attacks. This template helps you present information on five stages. You can also present information on Payment Card Fraud, Mobile Devices, Weak Credentials, Compromised Assets, Data Breach Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Breach Prevention Working Steps Of Data Breach Attack Cycle
Data Breach Prevention Working Steps Of Data Breach Attack CycleThis slide explains the phases of the data breach attack cycle to gain unauthorized access to sensitive information. The steps involved are reconnaissance, intrusion and presence, lateral migration, using data for personal benefits, demanding a ransom, etc. Introducing Data Breach Prevention Working Steps Of Data Breach Attack Cycle to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reconnaissance, Intrusion And Presence, Lateral Migration, Exfiltration , using this template. Grab it now to reap its full benefits.
-
 Encirclement Attack Strategy In Powerpoint And Google Slides Cpb
Encirclement Attack Strategy In Powerpoint And Google Slides CpbPresenting Encirclement Attack Strategy In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Encirclement Attack Strategy. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber Attack Continuity Plan In Powerpoint And Google Slides Cpb
Cyber Attack Continuity Plan In Powerpoint And Google Slides CpbPresenting our Cyber Attack Continuity Plan In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Cyber Attack Continuity Plan. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Agenda For Security Plan To Prevent Cyber Attacks Ppt Icon Design Inspiration
Agenda For Security Plan To Prevent Cyber Attacks Ppt Icon Design InspirationIntroducing Agenda For Security Plan To Prevent Cyber Attacks Ppt Icon Design Inspiration to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Risk Assessment, Attacks Frequency, Assessment Program For Organization, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Security Plan To Prevent Cyber Attacks Ppt Icon Elements
Icons Slide Security Plan To Prevent Cyber Attacks Ppt Icon ElementsPresenting our well crafted Icons Slide Security Plan To Prevent Cyber Attacks Ppt Icon Elements set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.
-
 Security Plan To Prevent Cyber Key Approaches To Minimize Cyber Attacks Risks
Security Plan To Prevent Cyber Key Approaches To Minimize Cyber Attacks RisksThis slide indicates the key approaches to minimize the risk associated with cyber attacks. The approaches discussed are update and upgrade outdated software, control accounts access, introduce signed software execution policies, regularly track network intrusions and use multifactor authentication. Increase audience engagement and knowledge by dispensing information using Security Plan To Prevent Cyber Key Approaches To Minimize Cyber Attacks Risks. This template helps you present information on five stages. You can also present information on Use Multifactor Authentication, Regularly Track Network Intrusions, Control Accounts Access using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Plan To Prevent Cyber Major Cyber Attacks Faced By Organization
Security Plan To Prevent Cyber Major Cyber Attacks Faced By OrganizationThis purpose of this slide is to showcase the major cyber attacks faced by business organization. The key attacks listed are phishing, malware attack, denial of service attacks, SQL injections, and ransomware. It also provides details regarding the major IT assets impacted and primary objective of each of the attacks. Introducing Security Plan To Prevent Cyber Major Cyber Attacks Faced By Organization to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Network And Application Infrastructure, Database Servers, Cause Operational Disruption, using this template. Grab it now to reap its full benefits.
-
 Security Plan To Prevent Cyber Mapping Of Multiple Cyber Attacks Using Risk Heat Map
Security Plan To Prevent Cyber Mapping Of Multiple Cyber Attacks Using Risk Heat MapThis slide shows the mapping of cyber attacks based on the likelihood of risk occurrence and its impact. It also contains details of attacks segmentation and the control actions that must be taken such as track, monitor and mitigate against such cyber attacks. Deliver an outstanding presentation on the topic using this Security Plan To Prevent Cyber Mapping Of Multiple Cyber Attacks Using Risk Heat Map. Dispense information and present a thorough explanation of Cyber Attacks, Risk Occurrence, Attacks Segmentation, Monitor And Mitigate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Plan To Prevent Cyber Risk Register To Measure Cyber Attacks Vulnerabilities
Security Plan To Prevent Cyber Risk Register To Measure Cyber Attacks VulnerabilitiesThis slide indicates the risk register to measure the cyber attack risk vulnerabilities faced by an organization. It includes information regarding the multiple risks in terms of vulnerability exploited, impact level, likelihood of occurrence and control recommended. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Risk Register To Measure Cyber Attacks Vulnerabilities. Use it as a tool for discussion and navigation on Financial Transactions, Credentials Compromised, Cloud Network, Compromised. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Plan To Prevent Cyber Strategic Plan To Mitigate Cyber Attacks
Security Plan To Prevent Cyber Strategic Plan To Mitigate Cyber AttacksThe slide indicates the risk mitigation plan for the multiple cyber attacks. It also includes details of cost involved and implementation time required for each mitigation approach. Increase audience engagement and knowledge by dispensing information using Security Plan To Prevent Cyber Strategic Plan To Mitigate Cyber Attacks. This template helps you present information on four stages. You can also present information on Cybersecurity Attacks, Recommended Mitigation Strategy, Strategy Implementation Time Required using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents For Security Plan To Prevent Cyber Attacks
Table Of Contents For Security Plan To Prevent Cyber AttacksIntroducing Table Of Contents For Security Plan To Prevent Cyber Attacks to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Risk Assessment Program, Cyber Attacks Identification, Cyber Attacks Faced By Organization, Cyber Attacks Risk Assessment, using this template. Grab it now to reap its full benefits.
-
 Storage Area Network Attacks Sniffing Storage Area Network San
Storage Area Network Attacks Sniffing Storage Area Network SanThis Slide Outlines The Sniffing Attack That Can Impact A Storage Area Network. The Purpose Of This Slide Is To Represent The Overview And Method To Control The Sniffing, Which Is Encryption. It Also Includes Sniffing Preventive Protocols For Fiber Channel And Ethernet Traffic, Such As ESP And SSL. Present The Topic In A Bit More Detail With This Storage Area Network Attacks Sniffing Storage Area Network San. Use It As A Tool For Discussion And Navigation On Encryption, Techniques, Confidentiality. This Template Is Free To Edit As Deemed Fit For Your Organization. Therefore Download It Now.
-
 Storage Area Network San Storage Area Network Attacks Spoofing
Storage Area Network San Storage Area Network Attacks SpoofingThis Slide Outlines The Spoofing Attacks That Compromise Storage Area Network Security. The Purpose Of This Slide Is To Provide An Overview Of Spoofing And Different Control Points That Can Prevent Spoofing Attacks, Including Out-Of And In-Band Management Apps, Device-To-Device, A Device To Fabric, And So On. Deliver An Outstanding Presentation On The Topic Using This Storage Area Network San Storage Area Network Attacks Spoofing. Dispense Information And Present A Thorough Explanation Of Impersonation, Masquerading, Storage Using The Slides Given. This Template Can Be Altered And Personalized To Fit Your Needs. It Is Also Available For Immediate Download. So Grab It Now.
-
 Storage Area Network San Storage Area Network Attacks Unauthorized Access
Storage Area Network San Storage Area Network Attacks Unauthorized AccessThis Slide Represents The Unauthorized Type Of SAN Attack, Including Its Control Points. This Slide Aims To Give An Overview Of Unauthorized Access And The Various Control Points That Can Prevent Unauthorized Access, Including Out-Of-Band And In-Band Management Apps, Device-To-Device, Device-To-Fabric, And So On. Present The Topic In A Bit More Detail With This Storage Area Network San Storage Area Network Attacks Unauthorized Access. Use It As A Tool For Discussion And Navigation On Unauthorized, Overview, Service. This Template Is Free To Edit As Deemed Fit For Your Organization. Therefore Download It Now.
-
 Action Plan To Combat Cyber Crimes Key Approaches To Minimize Cyber Attacks Risks
Action Plan To Combat Cyber Crimes Key Approaches To Minimize Cyber Attacks RisksThis slide indicates the key approaches to minimize the risk associated with cyber attacks. The approaches discussed are update and upgrade outdated software, control accounts access, introduce signed software execution policies, regularly track network intrusions and use multifactor authentication. Introducing Action Plan To Combat Cyber Crimes Key Approaches To Minimize Cyber Attacks Risks to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Regularly Track Network Intrusions, Use Multifactor Authentication, Control Accounts Access, Update And Upgrade Outdated Software, using this template. Grab it now to reap its full benefits.
-
 Action Plan To Combat Cyber Crimes Major Cyber Attacks Faced By Organization
Action Plan To Combat Cyber Crimes Major Cyber Attacks Faced By OrganizationThis purpose of this slide is to showcase the major cyber attacks faced by business organization. The key attacks listed are phishing, malware attack, denial of service attacks, SQL injections, and ransomware. It also provides details regarding the major IT assets impacted and primary objective of each of the attacks. Deliver an outstanding presentation on the topic using this Action Plan To Combat Cyber Crimes Major Cyber Attacks Faced By Organization. Dispense information and present a thorough explanation of Major Cyber Attacks, Malware Attack, Denial Of Service Attacks, SQL Injections, IT Assets using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Action Plan To Combat Cyber Crimes Mapping Of Multiple Cyber Attacks Using Risk Heat Map
Action Plan To Combat Cyber Crimes Mapping Of Multiple Cyber Attacks Using Risk Heat MapThis slide shows the mapping of cyber attacks based on the likelihood of risk occurrence and its impact. It also contains details of attacks segmentation and the control actions that must be taken such as track, monitor and mitigate against such cyber attacks. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Mapping Of Multiple Cyber Attacks Using Risk Heat Map. Use it as a tool for discussion and navigation on Mapping Of Multiple Cyber Attacks, Risk Heat Map, Risk Occurrence, Attacks Segmentation And The Control Actions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Action Plan To Combat Cyber Crimes Risk Register To Measure Cyber Attacks Vulnerabilities
Action Plan To Combat Cyber Crimes Risk Register To Measure Cyber Attacks VulnerabilitiesThis slide indicates the risk register to measure the cyber attack risk vulnerabilities faced by an organization. It includes information regarding the multiple risks in terms of vulnerability exploited, impact level, likelihood of occurrence and control recommended. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Risk Register To Measure Cyber Attacks Vulnerabilities. Use it as a tool for discussion and navigation on Cloud Network Compromised, Financial Transactions, Credentials Compromised. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Action Plan To Combat Cyber Crimes Strategic Plan To Mitigate Cyber Attacks
Action Plan To Combat Cyber Crimes Strategic Plan To Mitigate Cyber AttacksThe slide indicates the risk mitigation plan for the multiple cyber attacks. It also includes details of cost involved and implementation time required for each mitigation approach. Deliver an outstanding presentation on the topic using this Action Plan To Combat Cyber Crimes Strategic Plan To Mitigate Cyber Attacks. Dispense information and present a thorough explanation of Risk Mitigation Plan, Multiple Cyber Attacks, Mitigation Approach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Of Attacks On Proof Of Work System Complete Guide On How Blockchain BCT SS
Types Of Attacks On Proof Of Work System Complete Guide On How Blockchain BCT SSThis slide mentions the various types of attacks that can be encountered on proof of work system used for blockchain mining and their corresponding description and solutions. Attacks mentioned include Sybil attacks and Denial of Service attacks. Present the topic in a bit more detail with this Types Of Attacks On Proof Of Work System Complete Guide On How Blockchain BCT SS. Use it as a tool for discussion and navigation on Description, Solutions, Denial Of Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Compressive Planning Guide Key Approaches To Minimize Cyber Attacks Risks
Compressive Planning Guide Key Approaches To Minimize Cyber Attacks RisksThis slide indicates the key approaches to minimize the risk associated with cyber attacks. The approaches discussed are update and upgrade outdated software, control accounts access, introduce signed software execution policies, regularly track network intrusions and use multifactor authentication. Increase audience engagement and knowledge by dispensing information using Compressive Planning Guide Key Approaches To Minimize Cyber Attacks Risks. This template helps you present information on five stages. You can also present information on Control Accounts Access, Regularly Track Network Intrusions, Use Multifactor Authentication, Introduce Signed Software Execution Policies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Compressive Planning Guide Major Cyber Attacks Faced By Organization
Compressive Planning Guide Major Cyber Attacks Faced By OrganizationThis purpose of this slide is to showcase the major cyber attacks faced by business organization. The key attacks listed are phishing, malware attack, denial of service attacks, SQL injections, and ransomware. It also provides details regarding the major IT assets impacted and primary objective of each of the attacks. Present the topic in a bit more detail with this Compressive Planning Guide Major Cyber Attacks Faced By Organization. Use it as a tool for discussion and navigation on Database Servers, Network And Application Infrastructure, Denial Of Service Attack, Malware Attack. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Compressive Planning Guide Mapping Of Multiple Cyber Attacks Using Risk Heat Map
Compressive Planning Guide Mapping Of Multiple Cyber Attacks Using Risk Heat MapThis slide shows the mapping of cyber attacks based on the likelihood of risk occurrence and its impact. It also contains details of attacks segmentation and the control actions that must be taken such as track, monitor and mitigate against such cyber attacks. Deliver an outstanding presentation on the topic using this Compressive Planning Guide Mapping Of Multiple Cyber Attacks Using Risk Heat Map. Dispense information and present a thorough explanation of Cyber Attacks Segmentation, Phishing Attack, Fraudulently Obtain Sensitive Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





