Powerpoint Templates and Google slides for Attacker
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Determine phases of threat attack disrupting project safety contd management to improve project safety it
Determine phases of threat attack disrupting project safety contd management to improve project safety itThis slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. Introducing Determine Phases Of Threat Attack Disrupting Project Safety Contd Management To Improve Project Safety IT to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Installation, Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.
-
 Enterprise security operations insider attacker method and behavior assessment ppt gridlines
Enterprise security operations insider attacker method and behavior assessment ppt gridlinesThis slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Present the topic in a bit more detail with this Enterprise Security Operations Insider Attacker Method And Behavior Assessment Ppt Gridlines. Use it as a tool for discussion and navigation on Insider Attacker Method And Behaviour Assessment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Timeline for casualties of russia attack against ukraine presentation report infographic ppt pdf document
Timeline for casualties of russia attack against ukraine presentation report infographic ppt pdf documentThis is a reformattable Timeline For Casualties Of Russia Attack Against Ukraine Presentation Report Infographic PPT PDF Document. It is crafted with high-quality visuals available for immediate download in A4 size. Everything that this template offers can be accessed in different formats and ratios, including Google Slides and PowerPoint.
-
 Key Statistics Of Cyber Phishing Attack
Key Statistics Of Cyber Phishing AttackMentioned slide showcases major statistics of cyber phishing. Statistics mentioned in the slide are average daily legitimate emails, email volume change, average daily spam volume, change in spam volume percentage etc. Presenting our well structured Key Statistics Of Cyber Phishing Attack. The topics discussed in this slide are Email Volume Change, Average Daily Spam Volume, Change In Spam Volume Percentage. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Major Statistics Of Cyber Phishing Attacks
Major Statistics Of Cyber Phishing AttacksMentioned slide showcases key facts of cyber phishing attack. The facts covered in the slide are loss of confidential data, compromised accounts, ransomware attacks, financial loss and other malware attacks such as trojans. Presenting our well structured Major Statistics Of Cyber Phishing Attacks. The topics discussed in this slide are Other Malware Attack, Financial Loss, Ransomware Attacks. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 One Pager For Global Cyber Security Attack Statistics Report Presentation Infographic PPT PDF Document
One Pager For Global Cyber Security Attack Statistics Report Presentation Infographic PPT PDF DocumentProvides an overview of worldwide critical statistics about cybersecurity threats, and risks within a digital ecosystem. Grab our competent One pager for the global cyber security attack statistics report which includes cyber attacks by category, top malicious files of internet and email, cybersecurity concerns, cyber attack vectors, cybersecurity malware by region, etc. Get access now.
-
 Interlock swords as attacking weapon icon
Interlock swords as attacking weapon iconPresenting this set of slides with name Interlock Swords As Attacking Weapon Icon. The topics discussed in these slides are Interlock, Engagement, Puzzle Icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Insider attacker method and behaviour assessment security operations integration ppt themes
Insider attacker method and behaviour assessment security operations integration ppt themesThis slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Deliver an outstanding presentation on the topic using this Insider Attacker Method And Behaviour Assessment Security Operations Integration Ppt Themes. Dispense information and present a thorough explanation of Insider Behavior, Insider Attack Method, Compromised Insider using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Highest number of malware attacks on departments enterprise cyber security ppt elements
Highest number of malware attacks on departments enterprise cyber security ppt elementsThis slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness Present the topic in a bit more detail with this Highest Number Of Malware Attacks On Departments Enterprise Cyber Security Ppt Elements. Use it as a tool for discussion and navigation on Malware Infections, Highest Computer, Highest Financial. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud security threats malware attacks cloud security it ppt infographics
Cloud security threats malware attacks cloud security it ppt infographicsThis slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss.Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Malware Attacks Cloud Security IT Ppt Infographics. This template helps you present information on one stage. You can also present information on Cloud Security Threats Malware Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Highest number of malware attacks on departments cyber security phishing awareness training ppt tips
Highest number of malware attacks on departments cyber security phishing awareness training ppt tipsThis slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Deliver an outstanding presentation on the topic using this Highest Number Of Malware Attacks On Departments Cyber Security Phishing Awareness Training Ppt Tips. Dispense information and present a thorough explanation of Highest Number Of Malware Attacks On Departments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Corporate data security awareness cyber attacks experienced by the company in previous financial year ppt slides
Corporate data security awareness cyber attacks experienced by the company in previous financial year ppt slidesThis slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Present the topic in a bit more detail with this Corporate Data Security Awareness Cyber Attacks Experienced By The Company In Previous Financial Year Ppt Slides. Use it as a tool for discussion and navigation on Phishing, Network Intrusion, Inadvertent Disclosure, Stolen Or Lost Device Or Records, System Misconfiguration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Corporate data security awareness highest number of malware attacks on departments ppt graphics
Corporate data security awareness highest number of malware attacks on departments ppt graphicsThis slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Present the topic in a bit more detail with this Corporate Data Security Awareness Highest Number Of Malware Attacks On Departments Ppt Graphics. Use it as a tool for discussion and navigation on R And D Department, It Department, Accounts Department, Sales Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Highest number of malware attacks on departments implementing security awareness program ppt tips
Highest number of malware attacks on departments implementing security awareness program ppt tipsThis slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Present the topic in a bit more detail with this Highest Number Of Malware Attacks On Departments Implementing Security Awareness Program Ppt Tips. Use it as a tool for discussion and navigation on Highest Number Of Malware Attacks On Departments. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber attacks experienced by the company in previous financial year system ppt icon
Cyber attacks experienced by the company in previous financial year system ppt iconPresent the topic in a bit more detail with this Cyber Attacks Experienced By The Company In Previous Financial Year System Ppt Icon. Use it as a tool for discussion and navigation on Network Intrusion, Inadvertent Disclosure, System Misconfiguration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Highest number of malware attacks on departments accounts department ppt idea
Highest number of malware attacks on departments accounts department ppt ideaThis slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Present the topic in a bit more detail with this Highest Number Of Malware Attacks On Departments Accounts Department Ppt Idea Accounts Department. Use it as a tool for discussion and navigation on Highest Number Of Malware Attacks On Departments. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 It security operations insider attacker method and behaviour assessment ppt graphics tutorials
It security operations insider attacker method and behaviour assessment ppt graphics tutorialsThis slide portrays information regarding the insider attacker assessment in security operations system by addressing the method they use to attack and analyzing insider behavior. Present the topic in a bit more detail with this IT Security Operations Insider Attacker Method And Behaviour Assessment Ppt Graphics Tutorials. Use it as a tool for discussion and navigation on Insider Attacker Method And Behaviour Assessment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security data management maturity process to mitigate attacks
Security data management maturity process to mitigate attacksPresenting our set of slides with Security Data Management Maturity Process To Mitigate Attacks. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Analytics, Investigate, Qualify.
-
 Cyber attack monitoring ppt powerpoint presentation summary show cpb
Cyber attack monitoring ppt powerpoint presentation summary show cpbPresenting Cyber Attack Monitoring Ppt Powerpoint Presentation Summary Show Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase nine stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Attack Monitoring. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Information security awareness cyber attacks experienced by the company in previous financial year ppt grid
Information security awareness cyber attacks experienced by the company in previous financial year ppt gridThis slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Present the topic in a bit more detail with this Information Security Awareness Cyber Attacks Experienced By The Company In Previous Financial Year Ppt Grid. Use it as a tool for discussion and navigation on Phishing, Network Intrusion, Inadvertent Disclosure, Stolen Or Lost Device Or Records, System Misconfiguration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
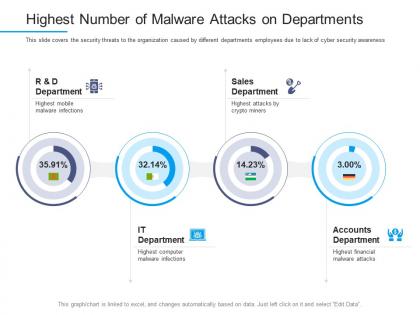 Information security awareness highest number of malware attacks on departments ppt maker
Information security awareness highest number of malware attacks on departments ppt makerThis slide covers the security threats to the organization caused by different departments employees due to lack of cyber security awareness. Present the topic in a bit more detail with this Information Security Awareness Highest Number Of Malware Attacks On Departments Ppt Maker. Use it as a tool for discussion and navigation on R And D Department, It Department, Accounts Department, Sales Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Insider attack ppt powerpoint presentation slides design ideas cpb
Insider attack ppt powerpoint presentation slides design ideas cpbPresenting our Insider Attack Ppt Powerpoint Presentation Slides Design Ideas Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Insider Attack This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber security threat landscape with attacks target and purpose
Cyber security threat landscape with attacks target and purposeIntroducing our premium set of slides with Cyber Security Threat Landscape With Attacks Target And Purpose. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Social And Phishing, Malware, Zero Day And Botnets, Passwords And Configs. So download instantly and tailor it with your information.
-
 Firewall Implementation For Cyber Security Department Wise Incident Analysis Of Malware Attacks
Firewall Implementation For Cyber Security Department Wise Incident Analysis Of Malware AttacksThis slide represents the number of attacks on each department in an organization. The purpose of this slide is to showcase the department-wise incident analysis of cyber-attacks on different departments such as finance, R and D, sales and marketing HR, IT, and others. Deliver an outstanding presentation on the topic using this Firewall Implementation For Cyber Security Department Wise Incident Analysis Of Malware Attacks. Dispense information and present a thorough explanation of Research And Development, Sales And Marketing, Incident Analysis, Malware Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Implementation For Cyber Security Malware Attacks Experienced By Company In Previous Year
Firewall Implementation For Cyber Security Malware Attacks Experienced By Company In Previous YearThis slide depicts the number of malware attack incidents faced by the organization in the previous year. The purpose of this slide is to showcase the monthly malware attacks experienced by the company in the absence of a firewall mechanism. Present the topic in a bit more detail with this Firewall Implementation For Cyber Security Malware Attacks Experienced By Company In Previous Year. Use it as a tool for discussion and navigation on Malware Attacks Experienced, Firewall Mechanism. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Attacks Impact On Employees
Email Security Attacks Impact On EmployeesThe purpose of this slide is to highlight and analyze the impact of different email security attacks on employees, shedding light on their perceptions and vulnerabilities. Introducing our Email Security Attacks Impact On Employees set of slides. The topics discussed in these slides are Perceptions, Vulnerabilities, Analyze. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Social Engineering Methods And Mitigation Social Engineering Attacks Tracking Dashboard
Social Engineering Methods And Mitigation Social Engineering Attacks Tracking DashboardThis slide represents the dashboard to track social engineering attacks. The purpose of this slide is to provide a graphical representation of cyber attacks occurred in a specific time span. It also depicts the overview of different types of attacks. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Social Engineering Attacks Tracking Dashboard. Dispense information and present a thorough explanation of Social Engineering Attacks, Tracking Dashboard, Unique Suspicious Emails using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Security Issues And Phishing Attacks Implementing Organizational Security Training
Cloud Security Issues And Phishing Attacks Implementing Organizational Security TrainingThe slide portrays security incidents reported by the organization over a period of time. It includes a graph showing cloud security issues, phishing attacks, etc. Deliver an outstanding presentation on the topic using this Cloud Security Issues And Phishing Attacks Implementing Organizational Security Training. Dispense information and present a thorough explanation of Graph Evaluating Cloud Security Issues, Graph Evaluating Phishing Attacks, Evaluation Graphs using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Current Analysis Of Security Attacks Faced Implementing Organizational Security Training
Current Analysis Of Security Attacks Faced Implementing Organizational Security TrainingThe slide showcases analysis of current situation occurred in organization regarding IT and cloud security attacks. It includes graph, key objective and key takeaways. Present the topic in a bit more detail with this Current Analysis Of Security Attacks Faced Implementing Organizational Security Training. Use it as a tool for discussion and navigation on Graph Projecting Current Analysis, Security Attacks, Key Objective. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Anti Phishing Software To Prevent Cyber Attack
Comparative Assessment Of Anti Phishing Software To Prevent Cyber AttackMentioned slide showcases comparison of various softwares which can be used to prevent cyber phishing attacks. The key features of softwares are spam filters, customizable filtering, malicious file integration, integration, report attacks etc. Introducing our Comparative Assessment Of Anti Phishing Software To Prevent Cyber Attack set of slides. The topics discussed in these slides are Customizable Filtering, Malicious File Identification, Integration. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Multi Layered Approach To Prevent Cyber Phishing Attack
Multi Layered Approach To Prevent Cyber Phishing AttackMentioned slide showcases approaches which can be implemented by organization to prevent cyber phishing attack. The approaches covered in the slide are attack prevention techniques, recognizing phishing emails, protecting firm from undetected emails etc. Presenting our set of slides with name Multi Layered Approach To Prevent Cyber Phishing Attack. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Attack Prevention Techniques, Recognize Phishing Emails, Protecting Organization From Undetected Phishing Emails.
-
 Cyber Attacks Small Business Ppt Powerpoint Presentation Outline Infographic Cpb
Cyber Attacks Small Business Ppt Powerpoint Presentation Outline Infographic CpbPresenting Cyber Attacks Small Business Ppt Powerpoint Presentation Outline Infographic Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Attacks Small Business. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Denial Service Attack In Powerpoint And Google Slides Cpb
Denial Service Attack In Powerpoint And Google Slides CpbPresenting our Denial Service Attack In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Denial Service Attack. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Attack Symptoms In Powerpoint And Google Slides Cpb
Attack Symptoms In Powerpoint And Google Slides CpbPresenting our Attack Symptoms In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Attack Symptoms This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Analytics Service Attacks In Powerpoint And Google Slides Cpb
Analytics Service Attacks In Powerpoint And Google Slides CpbPresenting our Analytics Service Attacks In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Analytics Service Attacks This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Email Security Icon To Protect Phishing Attack
Email Security Icon To Protect Phishing AttackPresenting our well structured Email Security Icon To Protect Phishing Attack. The topics discussed in this slide are Email Security, Protect Phishing Attack. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Various Types Of Email Attacks With Security Tips
Various Types Of Email Attacks With Security TipsThe purpose of this slide is to highlight various types of email attacks along with corresponding security tips, empowering users to enhance email security and protect sensitive information effectively. Presenting our well structured Various Types Of Email Attacks With Security Tips. The topics discussed in this slide are Spear Phishing, Malware Attack, Social Engineering. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Social Engineering Methods And Mitigation About Baiting Attack Overview And Techniques
Social Engineering Methods And Mitigation About Baiting Attack Overview And TechniquesThis slide discusses baiting technique of social engineering attacks. The purpose of this slide is to outline the methods used by attackers to conduct baiting scam. These are online downloads, malware-infected devices and tempting offers. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation About Baiting Attack Overview And Techniques. Use it as a tool for discussion and navigation on Online Downloads, Malware Infected Devices, Baiting Attack, Malicious Attachment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation About Impersonation Attacks Overview And Examples
Social Engineering Methods And Mitigation About Impersonation Attacks Overview And ExamplesThis slide discusses social engineering attacks using impersonation method. The purpose of this slide is to outline various examples of impersonation scams, such as email spoofing attack, cousin domain, account takeover, forged header or envelope, etc. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation About Impersonation Attacks Overview And Examples. Dispense information and present a thorough explanation of Email Spoofing Attack, Cousin Domain, Fraudulent Applications, Impersonation Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation About Phishing Attacks Overview And Impact
Social Engineering Methods And Mitigation About Phishing Attacks Overview And ImpactThis slide demonstrates the overview of cyber phishing attacks. The purpose of this slide is to talk about the effectiveness of phishing scams. This slide also outlines the issues which can be caused by phishing attacks such as disclosure of private data, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation About Phishing Attacks Overview And Impact. This template helps you present information on five stages. You can also present information on Compromised Accounts, Malware Injections, Financial Penalties, Financial Access using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Methods And Mitigation About Smishing Attacks Overview And Types
Social Engineering Methods And Mitigation About Smishing Attacks Overview And TypesThis slide talks about the smishing cyber attacks conducted by sending text messages to the targets. The purpose of this slide is to illustrate how fraudulent texts are sent to the users which contains malicious links and other mis-leading information. Introducing Social Engineering Methods And Mitigation About Smishing Attacks Overview And Types to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Smishing Scams, Financial Services Smishing, Gift Smishing, Customer Support Smishing, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Methods And Mitigation About Tailgating Attacks Overview And Techniques
Social Engineering Methods And Mitigation About Tailgating Attacks Overview And TechniquesThis slide demonstrates the procedure of tailgating attack with the help of an illustrative example. The purpose of this slide is to provide the overview of tailgating social engineering attack and the techniques used to implement it in organizations. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation About Tailgating Attacks Overview And Techniques. Dispense information and present a thorough explanation of Procedure Of Tailgating Attack, Tailgating Social Engineering Attack, Subcontractors Identity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation About Vishing Attacks Overview And Identification
Social Engineering Methods And Mitigation About Vishing Attacks Overview And IdentificationThis slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation About Vishing Attacks Overview And Identification. Use it as a tool for discussion and navigation on Vishing Cyber Attacks, Vishing Technique, Phishers To Scam Victims, Internal Revenue Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation Classification Of Different Social Engineering Attacks
Social Engineering Methods And Mitigation Classification Of Different Social Engineering AttacksThis slide represents the different types of social engineering attacks based on technology and human interaction. These include impersonation, tailgating, baiting, pretexting, scareware, quid pro quo, reverse social engineering, phishing, email phishing, spear phishing, whaling, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation Classification Of Different Social Engineering Attacks. This template helps you present information on two stages. You can also present information on Human Based Attacks, Social Engineering Attacks, Technology Based Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Methods And Mitigation Common Tactics Used In Scareware Attacks
Social Engineering Methods And Mitigation Common Tactics Used In Scareware AttacksThe purpose of this slide is to outline the several techniques used in scareware scams. The major points discussed in this slide are fake virus scans, fake tech support, Malvertising using legitimate advertisements and online law enforcement scams. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation Common Tactics Used In Scareware Attacks. Use it as a tool for discussion and navigation on Fake Virus Scams, Malvertising, Law Enforcement Scams, Fake Tech Support. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation Defensive Strategies Against Tailgating Attacks
Social Engineering Methods And Mitigation Defensive Strategies Against Tailgating AttacksThis slide highlights the best practices to avoid tailgating social engineering attacks. These include beware of surroundings, implement biometric scanners, issue smart badges or cards with RFID technology, install AI-based video surveillance, etc. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation Defensive Strategies Against Tailgating Attacks. Use it as a tool for discussion and navigation on Implement Biometric Scanners, Be Aware Of Surroundings, Unique Physical Features. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation Difference Between Baiting And Phishing Attacks
Social Engineering Methods And Mitigation Difference Between Baiting And Phishing AttacksThis slide compares the two major techniques of social engineering attacks, known as baiting and phishing. The comparison is based on several factors such as impersonation, communication, malware, identity theft, presentation, etc. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Difference Between Baiting And Phishing Attacks. Dispense information and present a thorough explanation of Impersonation, Communication, Identity Theft, Presentation, Malware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation Different Types Of Vishing Cyber Attacks
Social Engineering Methods And Mitigation Different Types Of Vishing Cyber AttacksThis slide talks about the various types of vishing cyber attacks. The purpose of this slide is to briefly explain different techniques of vishing scams used by the attackers to scam users. These are caller ID spoofing, dumpster diving, wardialing, etc. Introducing Social Engineering Methods And Mitigation Different Types Of Vishing Cyber Attacks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Vishing Cyber Attacks, Dumpster Diving, Wardialing, Techniques Of Vishing Scams, using this template. Grab it now to reap its full benefits.
-
 Social Engineering Methods And Mitigation Execution Of Man In The Middle Cyber Attacks
Social Engineering Methods And Mitigation Execution Of Man In The Middle Cyber AttacksThis slide illustrates the process of executing man-in-the-middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Execution Of Man In The Middle Cyber Attacks. Dispense information and present a thorough explanation of Cyber Attacks, Intercepting User Traffic, Malicious Wi Fi Hotspots using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation How To Protect Users From Vishing Attacks
Social Engineering Methods And Mitigation How To Protect Users From Vishing AttacksThis slide talks about the ways to protect users from vishing attacks. These include avoid calls from robots, never respond to audio-automated calls, verify the identity of the caller, never share personal information over the call, use multi-factor authentication, etc. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation Guidelines To Stay Safe From Phishing Scams. Use it as a tool for discussion and navigation on Facto Authentication, Government Organizations, Identity Of The Caller, Avoid Calls From Robots. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation Man In The Middlemitm Phishing Attack Diagram
Social Engineering Methods And Mitigation Man In The Middlemitm Phishing Attack DiagramThis slide demonstrates the working flow of man-in-the-middle phishing attacks using MITM phishing toolkit cloud server. This slide also elaborates the various real-world examples of MITM attacks such as Equifaxs mobile application, superfish and DigiNotar. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Man In The Middlemitm Phishing Attack Diagram. Dispense information and present a thorough explanation of Equifaxs Mobile Application, Superfish, Phishing Attack Diagram, Financial Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation Methods To Prevent Reverse Social Engineering Attacks
Social Engineering Methods And Mitigation Methods To Prevent Reverse Social Engineering AttacksThis slide outlines the strategies to avoid reverse social engineering scams. The methods discussed in this slide are identify technical support specialists, use separate internal identifiers, provide regular security awareness training to employees, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation Methods To Prevent Reverse Social Engineering Attacks. This template helps you present information on three stages. You can also present information on Identify Technical Support Specialists, Use Separate Internal Identifiers, Provide Regular Security Awareness Training using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Methods And Mitigation Precaution Measures Against Pretexting Attacks
Social Engineering Methods And Mitigation Precaution Measures Against Pretexting AttacksThis slide outlines the preventive measures to stay safe from pretexting attacks, These are Domain-based Message Authentication Reporting DMARC, AI-powered email filters, Endpoint Detection and Response EDR, and Network Detection and Response NDR. Present the topic in a bit more detail with this Social Engineering Methods And Mitigation Precaution Measures Against Pretexting Attacks. Use it as a tool for discussion and navigation on Endpoint Detection And Response, Network Detection And Response, Pretexting Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Social Engineering Methods And Mitigation Preventive Measures For Man In The Middle Cyber Attacks
Social Engineering Methods And Mitigation Preventive Measures For Man In The Middle Cyber AttacksThis slide outlines the various methods of preventing man-in-the-middle cyber attacks. The purpose of this slide is to explain how users can protect themselves from MITM scams. These include secure connections, avoid phishing emails, endpoint security, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation Preventive Measures For Man In The Middle Cyber Attacks. This template helps you present information on four stages. You can also present information on Secure Connections, Avoid Phishing Emails, Endpoint Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Methods And Mitigation Preventive Strategies For Baiting Cyber Attacks
Social Engineering Methods And Mitigation Preventive Strategies For Baiting Cyber AttacksThis slide outlines the methods to prevent baiting attacks. These are employee training, dont follow links blindly, use anti-virus and anti-malware software, avoid use of external devices without scanning and hold organized simulated attacks. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Preventive Strategies For Baiting Cyber Attacks. Dispense information and present a thorough explanation of Vulnerability Scanning, Security Patches, Input Vulnerability, Bug Bounty Programs using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation Steps To Identify Whaling Phishing Attacks
Social Engineering Methods And Mitigation Steps To Identify Whaling Phishing AttacksThis slide talks about the various methods of identifying whale phishing cyber attacks. The purpose of this slide is to help users identify CEO phishing scams. These include flag emails received from external domains, cross-verify sensitive requests, etc. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation Steps To Identify Whaling Phishing Attacks. This template helps you present information on six stages. You can also present information on Phishing Cyber Attacks, Phishing Scams, External Domains, Cross Verify Sensitive Requests using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Methods And Mitigation Understanding The Process Of E Mail Based Phishing Attacks
Social Engineering Methods And Mitigation Understanding The Process Of E Mail Based Phishing AttacksThis slide demonstrates the procedure of email-based phishing attacks. The purpose of this slide is to explain how fake websites are used by attackers to get the sensitive data of the users. The key components include database, fake website, etc. Deliver an outstanding presentation on the topic using this Social Engineering Methods And Mitigation Understanding The Process Of E Mail Based Phishing Attacks. Dispense information and present a thorough explanation of Phishing Attacks, Fake Website, Email Based Phishing Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Social Engineering Methods And Mitigation Working Of Watering Hole Phishing Attack
Social Engineering Methods And Mitigation Working Of Watering Hole Phishing AttackThis slide represents the working process of watering hole phishing attacks. The purpose of this slide is to illustrate the flow diagram of watering hole phishing scams. The key points include research and identification, analysis, preparation and execution. Increase audience engagement and knowledge by dispensing information using Social Engineering Methods And Mitigation Working Of Watering Hole Phishing Attack. This template helps you present information on four stages. You can also present information on Research And Identification, Analysis, Preparation, Domain And Subdomain Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Engineering Methods And Mitigation Working Procedure Of Spear Phishing Attack
Social Engineering Methods And Mitigation Working Procedure Of Spear Phishing AttackThis slide illustrates the structure of spear phishing attack. The purpose of this slide is to explain the working flow of spear phishing attack. The key components include attacker, phishing email, targeted users, exploited system, internal network, etc. Introducing Social Engineering Methods And Mitigation Working Procedure Of Spear Phishing Attack to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Email, Targeted Users, Exploited System, Internal Network, using this template. Grab it now to reap its full benefits.
-
 CBD Oil Panic Attacks In Powerpoint And Google Slides Cpp
CBD Oil Panic Attacks In Powerpoint And Google Slides CppIntroducing our well-designed CBD Oil Panic Attacks In Powerpoint And Google Slides Cpp. This PowerPoint design presents information on topics like CBD Oil Panic Attacks. As it is predesigned it helps boost your confidence level. It also makes you a better presenter because of its high-quality content and graphics. This PPT layout can be downloaded and used in different formats like PDF, PNG, and JPG. Not only this, it is available in both Standard Screen and Widescreen aspect ratios for your convenience. Therefore, click on the download button now to persuade and impress your audience.




