Powerpoint Templates and Google slides for Access Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Identity And Access Management Process In Workplace Securing Systems With Identity
Identity And Access Management Process In Workplace Securing Systems With IdentityThis slide discusses the Identity and Access Management process in the workplace. The purpose of this slide is to highlight the various usages of IAM in the workplace these include increasing the number of applications, managing identity data, and complex access scenarios. Increase audience engagement and knowledge by dispensing information using Identity And Access Management Process In Workplace Securing Systems With Identity This template helps you present information on Three stages. You can also present information on Increasing Number Of Applications, Managing Identity Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Identity And Access Management Technologies And Tools Securing Systems With Identity
Identity And Access Management Technologies And Tools Securing Systems With IdentityThis slide discusses the tools and technologies used in the Identity and Access Management process. The purpose of this slide is to highlight the various tools, which are security assertion markup language, open ID connect, and a system for cross-domain identity management. Present the topic in a bit more detail with this Identity And Access Management Technologies And Tools Securing Systems With Identity Use it as a tool for discussion and navigation on Saml, Oidc, Scim This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Training Schedule For Staff Securing Systems With Identity
Identity And Access Management Training Schedule For Staff Securing Systems With IdentityThis slide represents the training schedule for staff in the Identity and Access Management. The purpose of this slide is to manage and monitor IAM training procedures. It includes the time slots for training, the total days of training, and the modules to be covered in the training. Deliver an outstanding presentation on the topic using this Identity And Access Management Training Schedule For Staff Securing Systems With Identity Dispense information and present a thorough explanation of Policies And Procedures, Infrastructure And Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identity And Access Management Working Functions Securing Systems With Identity
Identity And Access Management Working Functions Securing Systems With IdentityThis slide discusses the working process of Identity and Access Management . The purpose of this slide is to explain the workflow of the IAM this includes identity management that validates login attempts and access management that manages the entitys access. Introducing Identity And Access Management Working Functions Securing Systems With Identity to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Identity Management, Access Management using this template. Grab it now to reap its full benefits.
-
 Impact Of Identity And Access Management On Business Securing Systems With Identity
Impact Of Identity And Access Management On Business Securing Systems With IdentityThis slide represents the Identity and Access Management impact on organization. The purpose of this slide is to highlight the impact associated with IAM for business which are enhances security, regularity compliance and so on. Deliver an outstanding presentation on the topic using this Impact Of Identity And Access Management On Business Securing Systems With Identity Dispense information and present a thorough explanation of Enhanced Security, Cost Savings using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Major Focus Areas Of Identity And Access Management Securing Systems With Identity
Major Focus Areas Of Identity And Access Management Securing Systems With IdentityThis slide discusses the Identity and Access Management focus area. The purpose of this slide is to explain the focus area of IAM these include access management, privilege management, and identity governance. Increase audience engagement and knowledge by dispensing information using Major Focus Areas Of Identity And Access Management Securing Systems With Identity This template helps you present information on Three stages. You can also present information on Access Management, Privilege Management, Identity Governance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Need For The Identity And Access Management Securing Systems With Identity
Need For The Identity And Access Management Securing Systems With IdentityThis slide discusses the requirement for Identity and Access Management process. The purpose of this slide is to highlight the needs these include secure user access, strong authentication, IAM solutions, IAM tasks, an evolving IT environment, etc. Present the topic in a bit more detail with this Need For The Identity And Access Management Securing Systems With Identity Use it as a tool for discussion and navigation on Secure User Access, Strong Authentication This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Associated With Identity And Access Management Process Securing Systems With Identity
Risk Associated With Identity And Access Management Process Securing Systems With IdentityThis slide outlines the potential hazards linked to the Identity and Access Management process. The purpose of this slide is to discuss the risks these include incorrectly defined roles and attributes, infrequent audits, and complex implementations. Introducing Risk Associated With Identity And Access Management Process Securing Systems With Identity to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Roles And Attributes, Infrequent Audits, Complex Implementations using this template. Grab it now to reap its full benefits.
-
 Roadmap For Identity And Access Management Implementation Securing Systems With Identity
Roadmap For Identity And Access Management Implementation Securing Systems With IdentityThis slide highlights the project roadmap to implement the Identity and Access Management process. The purpose of this slide is to showcase the different phases of the IAM implementation plan, such as implementing emerging IAM technologies, BYOI adoption, etc. Increase audience engagement and knowledge by dispensing information using Roadmap For Identity And Access Management Implementation Securing Systems With Identity This template helps you present information on Four stages. You can also present information on Iam Technologies, Byoi Adoption, Testing And Security Assurance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Role Of Identity And Access Management In Data Security Securing Systems With Identity
Role Of Identity And Access Management In Data Security Securing Systems With IdentityThis slide discusses the Identity and Access Management importance in data security. The purpose of this slide is to highlight the importance, including protecting business data, addressing new challenges, beyond perimeter security, combatting compromised credentials, and so on. Deliver an outstanding presentation on the topic using this Role Of Identity And Access Management In Data Security Securing Systems With Identity Dispense information and present a thorough explanation of Protecting Business Data, Combatting Compromised Credentials using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Securing Systems With Identity And Access Management Table Of Content
Securing Systems With Identity And Access Management Table Of ContentIntroducing Securing Systems With Identity And Access Management Table Of Content to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Introduction And Functions, Biometric Authentication using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Identity And Access Management In Enterprises Securing Systems With Identity
Steps To Implement Identity And Access Management In Enterprises Securing Systems With IdentityThis slide discusses the Identity and Access Management implementing process in enterprises. The purpose of this slide is to highlight the implementation process, including usage assessment, environment understanding, key IAM considerations, and so on. Introducing Steps To Implement Identity And Access Management In Enterprises Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Usage Assessment, Environment Understanding using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Identity And Access Management Securing Systems With Identity
Steps To Implement Identity And Access Management Securing Systems With IdentityThis slide discusses the Identity and Access Management implementing program. The purpose of this slide is to highlight the implementation process of IAM, including scope identification, evaluating the right IAM approach, finding the best solution, and so on. Increase audience engagement and knowledge by dispensing information using Steps To Implement Identity And Access Management Securing Systems With Identity This template helps you present information on Six stages. You can also present information on Scope Identification, Define A Strategy, Assess Cost Factors using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Content For Securing Systems With Identity And Access Management
Table Of Content For Securing Systems With Identity And Access ManagementIncrease audience engagement and knowledge by dispensing information using Table Of Content For Securing Systems With Identity And Access Management This template helps you present information on One stages. You can also present information on Iam Overview, Training And Budget using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline To Implement Identity And Access Management Plan Securing Systems With Identity
Timeline To Implement Identity And Access Management Plan Securing Systems With IdentityThis slide shows the timeline for implementing the Identity and Access Management plan. The key steps include defining the project objective, identifying key stakeholders, determining compliance, integrating IAM with the existing system, etc. Introducing Timeline To Implement Identity And Access Management Plan Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Applications And Data, Public Cloud Platforms using this template. Grab it now to reap its full benefits.
-
 Understanding Of Identity And Access Management Securing Systems With Identity
Understanding Of Identity And Access Management Securing Systems With IdentityThis slide discusses the concepts of the Identity and Access Management process. The purpose of this slide is to explain the key components of IAM, including authentication, authorization, user management, and central user repository. Introducing Understanding Of Identity And Access Management Securing Systems With Identity to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Access Management, Identity Mgmt using this template. Grab it now to reap its full benefits.
-
 Uniting Identity And Access Management Processes Securing Systems With Identity
Uniting Identity And Access Management Processes Securing Systems With IdentityThis slide discusses the Identity and Access Management uniting process. The purpose of this slide is to explain the Identity and Access Management unit, which involves users, access management, resources, identity management, and ID sources. Increase audience engagement and knowledge by dispensing information using Uniting Identity And Access Management Processes Securing Systems With Identity This template helps you present information on Four stages. You can also present information on Key Takeaways, Iam Market Size using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Use Cases Of Identity And Access Management Securing Systems With Identity
Use Cases Of Identity And Access Management Securing Systems With IdentityThis slide highlights the Identity and Access Management process use cases. The purpose of this slide is to discuss the cases these include IAM for zero trust at better.com and IAM for streamlined onboarding at hearst. Introducing Use Cases Of Identity And Access Management Securing Systems With Identity to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Loss Prevention, Compromising Security using this template. Grab it now to reap its full benefits.
-
 Near Field Communication NFC For Access Control Mobile Security
Near Field Communication NFC For Access Control Mobile SecurityThis slide represents the introduction of near field communication for access control which is based on radio frequency identification technology. Introducing Near Field Communication NFC For Access Control Mobile Security to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Relay Attack, Data Interception, Data Tampering using this template. Grab it now to reap its full benefits.
-
 Pam Cybersecurity Lifecycle For Securing Account Access
Pam Cybersecurity Lifecycle For Securing Account AccessThis slide represents lifecycle of PAM cybersecurity that assists companies to enhance their account protection by access management. It includes various steps such as defining, discovering, managing, protecting, monitoring, detecting abnormal usage, etc. Presenting our set of slides with Pam Cybersecurity Lifecycle For Securing Account Access. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Respond To Incidents, Detect Abnormal Usage, Manage Protect.
-
 Establishing Privilege Access Management Building Next Generation Endpoint Security Cybersecurity SS
Establishing Privilege Access Management Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases how to establish privilege access management process. It provides details about prepare, protect, operate, monitor, etc.Present the topic in a bit more detail with this Establishing Privilege Access Management Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Prepare, Protect, Operate, Monitor. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices And Email Security Policies To Avoid Unauthorized Access
Email Security Best Practices And Email Security Policies To Avoid Unauthorized AccessThis slide outlines the different email security practices opted by organizations. These policies are strong password requirements, multifactor authentication, email encryption, email attachments, data retention, regular software updates, etc. Introducing Email Security Best Practices And Email Security Policies To Avoid Unauthorized Access to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Strong Password Requirements, Secure Email Gateway, Data Retention, using this template. Grab it now to reap its full benefits.
-
 Wireless Access Points WAP Best Practices To Secure WAP
Wireless Access Points WAP Best Practices To Secure WAPThis slide outlines the steps for Wireless Access Points security. The purpose of this slide is to highlight the best practices to secure WAP from unauthorized access, and these are enabling firewall and firmware, using VPN and guest network, disabling remote access and WPS, etc. Deliver an outstanding presentation on the topic using this Wireless Access Points WAP Best Practices To Secure WAP. Dispense information and present a thorough explanation of Enable Firewall And Firmware, Use Vpn And Guest Network, Change Default Settings using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Icon For Securing Remote Access
Network Security Icon For Securing Remote AccessPresenting our set of slides with name Network Security Icon For Securing Remote Access. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Security, Securing Remote Access.
-
 Download security directory service security access example of ppt
Download security directory service security access example of pptPresenting download security directory service security access example of ppt. This is a security directory service security access example of ppt. This is a four stage process. The stages in this process are security directory service, streaming computing, security access, info sphere streams.
-
 Security Dashboard To Manage User Access
Security Dashboard To Manage User AccessPresenting our well structured Security Dashboard To Manage User Access. The topics discussed in this slide are Migration, Security Dashboard, Manage User Access. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 SASE IT Global Market Of Secure Access Service Edge Ppt Powerpoint Slides
SASE IT Global Market Of Secure Access Service Edge Ppt Powerpoint SlidesThis slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work-from-anywhere culture, and so on. Present the topic in a bit more detail with this SASE IT Global Market Of Secure Access Service Edge Ppt Powerpoint Slides. Use it as a tool for discussion and navigation on Changing Work Culture, Security Framework, Computing Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SASE IT Secure Access Service Edge Performance Tracking Dashboard Ppt Powerpoint Topics
SASE IT Secure Access Service Edge Performance Tracking Dashboard Ppt Powerpoint TopicsThis slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Present the topic in a bit more detail with this SASE IT Secure Access Service Edge Performance Tracking Dashboard Ppt Powerpoint Topics. Use it as a tool for discussion and navigation on SASE Connections, Critical Network Alarms, Critical Security Alerts. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Cloud Access Security Broker CASB Ppt Visual Aids Diagrams
Table Of Contents Cloud Access Security Broker CASB Ppt Visual Aids DiagramsIntroducing Table Of Contents Cloud Access Security Broker CASB Ppt Visual Aids Diagrams. to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Casb Overview, Need For Casb, Casb Pillars, using this template. Grab it now to reap its full benefits.
-
 CASB Performance Tracking Dashboard Cloud Access Security Broker CASB
CASB Performance Tracking Dashboard Cloud Access Security Broker CASBThis slide outlines the performance tracking dashboard for CASB deployment. The purpose of this slide is to showcase the status of various applications, IP addresses, users, machines, and web traffic. It also includes cloud discovery open alerts, risk levels, and top entities. Present the topic in a bit more detail with this CASB Performance Tracking Dashboard Cloud Access Security Broker CASB. Use it as a tool for discussion and navigation on Dashboard, Discovered Apps, Ip Addresses. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Access rights business security lock image
Access rights business security lock imagePresenting this set of slides with name - Access Rights Business Security Lock Image. Fully creative and editable Access Rights Business Security Lock Image PPT template, you can modify font, color, background of the presentation. You can use your company logo and name in PPT slides. The slides are compatible with Google Slides and Microsoft software and can be downloaded as JPEG or PDF format. The PPT quality is good; quality remains unchanged even on wide screen view. High quality visuals make PPT more effective.
-
 Access rights security image
Access rights security imagePresenting this set of slides with name - Access Rights Security Image. This is a one stage. The stage in this process are Access Rights, Access Privilege, Access Management.
-
 Access rights security lock image
Access rights security lock imagePresenting this set of slides with name - Access Rights Security Lock Image. This is a one stage. The stage in this process are Access Rights, Access Privilege, Access Management.
-
 Security check access rights iris scan image
Security check access rights iris scan imagePresenting this set of slides with name - Security Check Access Rights Iris Scan Image. This is a one stage. The stage in this process are Access Rights, Access Privilege, Access Management.
-
 Wireless security to prevent unauthorized access to internet
Wireless security to prevent unauthorized access to internetIntroducing our premium set of slides with Wireless Security To Prevent Unauthorized Access To Internet. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Wireless Security To Prevent Unauthorized Access To Internet. So download instantly and tailor it with your information.
-
 Electronic information security define access control measures employees
Electronic information security define access control measures employeesThis slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Introducing Electronic Information Security Define Access Control Measures Employees to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Organization, Data Or Networks, Personnel According, Responsibilities, using this template. Grab it now to reap its full benefits.
-
 Secure Access Gateway Ppt Powerpoint Presentation Inspiration Design Ideas Cpb
Secure Access Gateway Ppt Powerpoint Presentation Inspiration Design Ideas CpbPresenting Secure Access Gateway Ppt Powerpoint Presentation Inspiration Design Ideas Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Secure Access Gateway. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Information Security Define Access Control Measures For Employees
Information Security Define Access Control Measures For EmployeesThis slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Introducing Information Security Define Access Control Measures For Employees to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Control, Measures, Employees, using this template. Grab it now to reap its full benefits.
-
 Network Security Define Access Control Measures For Employees
Network Security Define Access Control Measures For EmployeesThis slide represents how it is essential to minimize the rights access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Increase audience engagement and knowledge by dispensing information using Network Security Define Access Control Measures For Employees. This template helps you present information on four stages. You can also present information on Organization, Duties, Roles, Permissions, Personnel using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Define Access Control Measures For Employees
Information Technology Security Define Access Control Measures For EmployeesThis slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Increase audience engagement and knowledge by dispensing information using Information Technology Security Define Access Control Measures For Employees. This template helps you present information on four stages. You can also present information on Organization, Permissions, Responsibilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Access Control Methods Information Security Ppt Powerpoint Presentation Pictures Visual Aids Cpb
Access Control Methods Information Security Ppt Powerpoint Presentation Pictures Visual Aids CpbPresenting our Access Control Methods Information Security Ppt Powerpoint Presentation Pictures Visual Aids Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Access Control Methods Information Security. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Building organizational security strategy plan determine user access controls levels
Building organizational security strategy plan determine user access controls levelsThis slide provides information about information user access controls levels for access critical assets and information associated to firm and levels of access for administrator, maintainer, guest or disabled. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Determine User Access Controls Levels. Use it as a tool for discussion and navigation on Information, Administrator, Associated. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Access Levels Ppt Powerpoint Presentation Professional Templates Cpb
Security Access Levels Ppt Powerpoint Presentation Professional Templates CpbPresenting our Security Access Levels Ppt Powerpoint Presentation Professional Templates Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Security Access Levels This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cloud Security Checklist Access Control Cloud Information Security
Cloud Security Checklist Access Control Cloud Information SecurityThis slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management.Introducing Cloud Security Checklist Access Control Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Service Provider, Physical Access, Natural Disasters using this template. Grab it now to reap its full benefits.
-
 Cloud Computing Security How Does Cloud Security Work Identity And Access Management
Cloud Computing Security How Does Cloud Security Work Identity And Access ManagementThis slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Introducing Cloud Computing Security How Does Cloud Security Work Identity And Access Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Authentication, Authorization, Access Management, Central User Repository, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Access Control Cloud Computing Security
Cloud Security Checklist Access Control Cloud Computing SecurityThis slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Introducing Cloud Security Checklist Access Control Cloud Computing Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Multi Factor Authorization, Cloud Services, Networks, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Access Control Cloud Data Protection
Cloud Security Checklist Access Control Cloud Data ProtectionThis slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management. Introducing Cloud Security Checklist Access Control Cloud Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispense information on Cloud Services, Information, Data Servers, using this template. Grab it now to reap its full benefits.
-
 How Does Cloud Security Work Identity And Access Management Cloud Data Protection
How Does Cloud Security Work Identity And Access Management Cloud Data ProtectionThis slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository. Introducing How Does Cloud Security Work Identity And Access Management Cloud Data Protection to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispense information on Access Management, Authentication, Authorization, Central User Repository, using this template. Grab it now to reap its full benefits.
-
 NaaS And Secure Access Service Edge Sase Ppt Powerpoint Presentation Infographics Styles
NaaS And Secure Access Service Edge Sase Ppt Powerpoint Presentation Infographics StylesThis slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti malware, file sandboxing, cloud delivered firewall, app visibility and control, and so on. Increase audience engagement and knowledge by dispensing information using NaaS And Secure Access Service Edge Sase Ppt Powerpoint Presentation Infographics Styles. This template helps you present information on two stages. You can also present information on Network Service, Security Service using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Naas And Secure Access Service Edge Sase Network As A Service Naas It
Naas And Secure Access Service Edge Sase Network As A Service Naas ItThis slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti-malware, file sandboxing, cloud-delivered firewall, app visibility and control, and so on. Present the topic in a bit more detail with this Naas And Secure Access Service Edge Sase Network As A Service Naas It. Use it as a tool for discussion and navigation on Information, Operations, Appropriate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Naas And Secure Access Service Edge Sase Naas Service Models Ppt Powerpoint Presentation Pictures Themes
Naas And Secure Access Service Edge Sase Naas Service Models Ppt Powerpoint Presentation Pictures ThemesThis slide talks about the relationship between network as a service and secure access service edge.The SAFE provides DNS filtering, secure web gateway, anti malware, file sandboxing, cloud delivered firewall, app visibility and control, and so on.Introducing Naas And Secure Access Service Edge Sase Naas Service Models Ppt Powerpoint Presentation Pictures Themes to increase your presentation threshold.Encompassed with two stages, this template is a great option to educate and entice your audience.Dispence information on Performance Optimization, Secure Direct, Loss Prevention, using this template.Grab it now to reap its full benefits.
-
 Access Control In Secured Database Management System
Access Control In Secured Database Management SystemThis slide represents the block diagram representing the access control in secured database management system. It includes details related to database and security administrator, authorization system, database schemas, application programs etc. Presenting our well structured Access Control In Secured Database Management System. The topics discussed in this slide are Access Control, Secured Database, Management System. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Role Based Access Control RBAC Securities Icon
Role Based Access Control RBAC Securities IconIntroducing our premium set of slides with name Role Based Access Control RBAC Securities Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Access Control, Securities Icon, Audiences Attention. So download instantly and tailor it with your information.
-
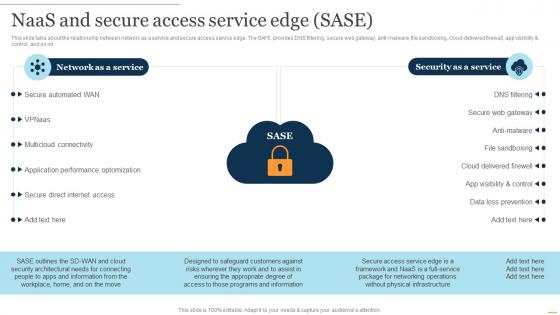 NaaS Architecture NaaS And Secure Access Service Edge SASE Ppt Presentation Infographic Template Shapes
NaaS Architecture NaaS And Secure Access Service Edge SASE Ppt Presentation Infographic Template ShapesThis slide talks about the relationship between network as a service and secure access service edge. The SAFE provides DNS filtering, secure web gateway, anti malware, file sandboxing, cloud delivered firewall, app visibility and control, and so on. Increase audience engagement and knowledge by dispensing information using NaaS Architecture NaaS And Secure Access Service Edge SASE Ppt Presentation Infographic Template Shapes. This template helps you present information on two stages. You can also present information on Network As A Service, Security As A Service, Secure Automated Wan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Access Security Measures For Businesses
Data Access Security Measures For BusinessesThis slide represents the security measures for data access within an organization. This template aims to demonstrate secure data access techniques and their benefits. The components include workforce training, implementing a data centric security plan, deploying a multi factor authentication policy, etc. Presenting our well structured Data Access Security Measures For Businesses. The topics discussed in this slide are Workforce Training, Data Centric Security, Stricter Permissions. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Secure Computer Data Access Icon
Secure Computer Data Access IconIntroducing our premium set of slides with name Secure Computer Data Access Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Secure Computer, Data Access Icon. So download instantly and tailor it with your information.
-
 Secure Data Access Methods For Cloud Computing
Secure Data Access Methods For Cloud ComputingThis slide describes the various methods to access the data stored in a cloud environment securely. The purpose of this slide is to represent secure data access for cloud computing users. The methods include cloud based access through a relational database management system, cloud based data warehousing and a cloud data lake. Introducing our Secure Data Access Methods For Cloud Computing set of slides. The topics discussed in these slides are Data Storage Updates, Encrypted Data, Data Access Request. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 WIFI Security Access Control Colored Icon In Powerpoint Pptx Png And Editable Eps Format
WIFI Security Access Control Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a visual representation of WIFI security. It features a shield with a lock to represent the protection of your WIFI network. It is a great visual aid for presentations on WIFI security and can be used to highlight the importance of keeping your network secure.
-
 WIFI Security Access Control Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
WIFI Security Access Control Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is perfect for illustrating the concept of WIFI Security. It features a simple, modern design that is sure to make your presentation stand out. It is perfect for any project related to WIFI Security, from educational materials to corporate presentations.
-
 Secure Cloud Access Data Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Secure Cloud Access Data Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis powerpoint icon is a colourful representation of secure cloud data, perfect for any presentation. It displays a cloud with a secure padlock, signifying the safety and security of the data stored within.





