Powerpoint Templates and Google slides for Access Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Training Program For Cloud Access Security Broker Next Generation CASB
Training Program For Cloud Access Security Broker Next Generation CASBThis slide describes the training program for employees to implement cloud access security broke in an organization. The purpose of this slide is to highlight the training schedule for CASB deployment and the main components include agenda, system requirements, mode and cost of the training. Present the topic in a bit more detail with this Training Program For Cloud Access Security Broker Next Generation CASB Use it as a tool for discussion and navigation on Agenda, System Requirements, Deployment Options This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Use Cases Of Cloud Access Security Broker Next Generation CASB
Use Cases Of Cloud Access Security Broker Next Generation CASBPresent the topic in a bit more detail with this Use Cases Of Cloud Access Security Broker Next Generation CASB Use it as a tool for discussion and navigation on Unsanctioned Apps, Sanctioned Apps, Cloud Threats This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Firewall Network Security Firewall Techniques To Restrict Access And Ensure Web Client Security
Firewall Network Security Firewall Techniques To Restrict Access And Ensure Web Client SecurityThis slide outlines the many ways to control access and guarantee web client security policy. The purpose of this slide is to highlight the firewall techniques to limit user access and confirm web user security, such as service control, direction control, user control and behavior control. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Firewall Techniques To Restrict Access And Ensure Web Client Security This template helps you present information on Four stages. You can also present information on Market By Deployment, Market By Solution using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Benefits Of Secure Access Service Edge Sase
SD WAN Model Benefits Of Secure Access Service Edge SaseThis slide outlines the key benefits of secure access service edge. The purpose of this slide is to showcase the advantages of the SASE model, such as flexibility, cost savings, reduced complexity, increased performance, threat and data protection and increased network performance. Present the topic in a bit more detail with this SD WAN Model Benefits Of Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Data Protection, Increased Network Performance, Cost Savings, Secure Access Service Edge. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Best Practices To Implement Cloud Access Security Broker
SD WAN Model Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this SD WAN Model Best Practices To Implement Cloud Access Security Broker. Dispense information and present a thorough explanation of Network And Cloud Infrastructure Monitoring, Protection Against Risks, Specific Risk Prototypes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Budget To Implement Secure Access Service Edge
SD WAN Model Budget To Implement Secure Access Service EdgeThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD-WAN, SWG, ZTNA, CASB, and FWaaS. Present the topic in a bit more detail with this SD WAN Model Budget To Implement Secure Access Service Edge. Use it as a tool for discussion and navigation on Secure Web Gateway, Cloud Access Security Broker, Zero Trust Network Access, Firewall As A Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Checklist To Implement Secure Access Service Edge
SD WAN Model Checklist To Implement Secure Access Service EdgePresent the topic in a bit more detail with this SD WAN Model Checklist To Implement Secure Access Service Edge. Use it as a tool for discussion and navigation on Test And Troubleshoot, Incorporate Zero Trust Solutions, Goals And Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Cloud Access Security Broker Casb Overview
SD WAN Model Cloud Access Security Broker Casb OverviewThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Introducing SD WAN Model Cloud Access Security Broker Casb Overview to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Granular Cloud Usage Control, Data Loss Prevention, Cloud Access Security Broker, Risk Visibility, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Cloud Access Security Broker Implementation Models
SD WAN Model Cloud Access Security Broker Implementation ModelsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using SD WAN Model Cloud Access Security Broker Implementation Models. This template helps you present information on three stages. You can also present information on Cloud Access Security Broker, Api Scanning, Forward Proxy, Reverse Proxy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Cloud Access Security Broker Use Cases
SD WAN Model Cloud Access Security Broker Use CasesThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Present the topic in a bit more detail with this SD WAN Model Cloud Access Security Broker Use Cases. Use it as a tool for discussion and navigation on Cloud Access Security Broker, Covering Protection Against Threats, Governing Usage, Securing Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Cloud Access Security Broker Working Process
SD WAN Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing SD WAN Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Classification And Remediation, Control And Transparency Across Data, Risks In The Cloud, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Comparison Between Secure Access Service Edge And Sd Wan
SD WAN Model Comparison Between Secure Access Service Edge And Sd WanThis slide compares secure access service edge and software-defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD-WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Present the topic in a bit more detail with this SD WAN Model Comparison Between Secure Access Service Edge And Sd Wan. Use it as a tool for discussion and navigation on Deployment And Architecture, Traffic And Connectivity, Security, Secure Access Service Edge. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Introduction To Secure Access Service Edge Sase
SD WAN Model Introduction To Secure Access Service Edge SaseThis slide represents the introduction of SASE cloud security technology. The purpose of this slide is to demonstrate the core capabilities, benefits and key components of SASE. The key components include SD-WAN, FWaaS, ZTNA, CASB, SWG, and unified management. Present the topic in a bit more detail with this SD WAN Model Introduction To Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Software Defined Wan, Firewall As A Service, Zero Trust Network Access, Cloud Access Security Broker. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Pillars Of Cloud Access Security Broker Ppt Icon Design Ideas
SD WAN Model Pillars Of Cloud Access Security Broker Ppt Icon Design IdeasThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Increase audience engagement and knowledge by dispensing information using SD WAN Model Pillars Of Cloud Access Security Broker Ppt Icon Design Ideas. This template helps you present information on four stages. You can also present information on Cloud Access Security Broker, Compliance, Visibility, Threat Protection, Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Roadmap To Implement Secure Access Service Edge
SD WAN Model Roadmap To Implement Secure Access Service EdgeThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Introducing SD WAN Model Roadmap To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Regularly, Transition, Troubleshooting And Assistance, Secure Access Service Edge, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Secure Access Service Edge Architecture Characteristics
SD WAN Model Secure Access Service Edge Architecture CharacteristicsThis slide represents the architectural characteristics of a secure access service edge. The purpose of this slide is to showcase the features of SASE architecture that include identity-driven, cloud-native, support for all edges, and global distribution. Introducing SD WAN Model Secure Access Service Edge Architecture Characteristics to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure Access Service Edge, Architecture Characteristics, Cloud Native, Global Distribution, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Secure Access Service Edge Implementation Steps
SD WAN Model Secure Access Service Edge Implementation StepsThis slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD-WAN backbone, incorporating zero-trust solutions, etc. Increase audience engagement and knowledge by dispensing information using SD WAN Model Secure Access Service Edge Implementation Steps. This template helps you present information on five stages. You can also present information on Incorporate Zero Trust Solutions, Test And Troubleshoot, Secure Access Service Edge, Infrastructure Gaps using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Secure Access Service Edge Importance
SD WAN Model Secure Access Service Edge ImportanceThis slide represents the importance of secure access service edge. This slides purpose is to demonstrate why businesses need the SASE model. The main reasons include scaling with business needs, encouraging work from anywhere environment, standing up for cyber threats, and offering a base for IoT adoption. Introducing SD WAN Model Secure Access Service Edge Importance to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Scales With Business, Encourage Work From Anywhere, Network And Security, Compromising Business Security, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Secure Access Service Edge Sase Architecture
SD WAN Model Secure Access Service Edge Sase ArchitectureThis slide represents the SASE architecture overview and its goals. The purpose of this slide is to demonstrate the secure access service edge architecture and its goals. The building blocks of SASE architecture include SWG, CASB, ZTNA, FWaaS, SD-WAN, Thin Edge, and so on. Deliver an outstanding presentation on the topic using this SD WAN Model Secure Access Service Edge Sase Architecture. Dispense information and present a thorough explanation of Secure Access Service Edge, Architecture And Its Goals, Geographic Distribution using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Secure Access Service Edge Training Program
SD WAN Model Secure Access Service Edge Training ProgramThis slide represents the training program for the secure access service edge model. The purpose of this slide is to demonstrate the teams eligible for training, the modules to be covered during the training, the schedule and venue of the training. Present the topic in a bit more detail with this SD WAN Model Secure Access Service Edge Training Program. Use it as a tool for discussion and navigation on Training Program, Secure Access Service Edge, Teams Eligible For Training, Modules To Be Covered. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Secure Access Service Edge Use Cases
SD WAN Model Secure Access Service Edge Use CasesThis slide represents the use cases of secure access service edge within an organization. The purpose of this slide is to demonstrate the various use cases of the SASE model, including rapid response to network demand, support for IoT and edge computing, VPN replacement, performance assurance and so on. Increase audience engagement and knowledge by dispensing information using SD WAN Model Secure Access Service Edge Use Cases. This template helps you present information on six stages. You can also present information on Performance Assurance, Support For Multiple Operating Systems, Controlled Move To Cloud Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
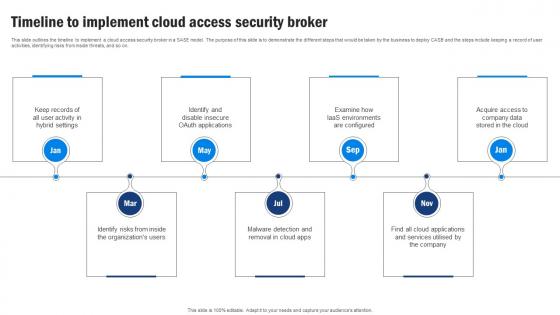 SD WAN Model Timeline To Implement Cloud Access Security Broker
SD WAN Model Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using SD WAN Model Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Cloud Access Security Broker, Environments Are Configured, Identify Risks, Malware Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
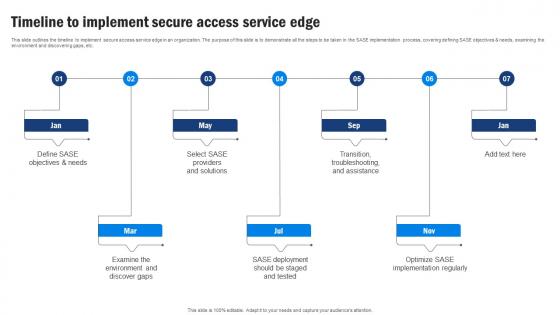 SD WAN Model Timeline To Implement Secure Access Service Edge
SD WAN Model Timeline To Implement Secure Access Service EdgeThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing SD WAN Model Timeline To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Secure Access Service Edge, Examining The Environment, Discovering Gaps, Timeline, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Working Of Secure Access Service Edge
SD WAN Model Working Of Secure Access Service EdgeThis slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. Present the topic in a bit more detail with this SD WAN Model Working Of Secure Access Service Edge. Use it as a tool for discussion and navigation on Precise Amount Of Performance, Dependability, Security, Cost For Each Network Connection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ensure Secure Access Icon Using Multi Factor Authentication Tool
Ensure Secure Access Icon Using Multi Factor Authentication ToolPresenting our set of slides with Ensure Secure Access Icon Using Multi Factor Authentication Tool. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure, Factor, Authentication.
-
 Ethical Hacking And Network Security Ethical Hacking Phase 3 Gaining Access
Ethical Hacking And Network Security Ethical Hacking Phase 3 Gaining AccessThis slide represents the gaining access phase of ethical hacking and how access can be gained through a phishing attack, man in the middle, brute force attack, and so on. Introducing Ethical Hacking And Network Security Ethical Hacking Phase 3 Gaining Access to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Attack, Brute Force Attack, Spoofing Attack, Dos Attack, Buffer Overflow Attack, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Ethical Hacking Phase 4 Maintaining Access
Ethical Hacking And Network Security Ethical Hacking Phase 4 Maintaining AccessThis slide represents the maintaining access phase of ethical hacking and how ethical hackers take advantage of it to detect any malicious activities and prevent them. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Ethical Hacking Phase 4 Maintaining Access. This template helps you present information on six stages. You can also present information on Whole Firms Infrastructure, Malicious Activity, Prevent The Systems, Ethical Hacking using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Benefits Of Secure Access Service Edge Sase
Sase Model Benefits Of Secure Access Service Edge SaseThis slide outlines the key benefits of secure access service edge. The purpose of this slide is to showcase the advantages of the SASE model, such as flexibility, cost savings, reduced complexity, increased performance, threat and data protection and increased network performance. Deliver an outstanding presentation on the topic using this Sase Model Benefits Of Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Benefits, Description, Impact using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Best Practices To Implement Cloud Access Security Broker
Sase Model Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Present the topic in a bit more detail with this Sase Model Best Practices To Implement Cloud Access Security Broker. Use it as a tool for discussion and navigation on Best Practices, Description, Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Budget To Implement Secure Access Service Edge
Sase Model Budget To Implement Secure Access Service EdgeThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD-WAN, SWG, ZTNA, CASB, and FWaaS. Deliver an outstanding presentation on the topic using this Sase Model Budget To Implement Secure Access Service Edge. Dispense information and present a thorough explanation of Components, Estimated Cost, Actual Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Checklist To Implement Secure Access Service Edge
Sase Model Checklist To Implement Secure Access Service EdgeDeliver an outstanding presentation on the topic using this Sase Model Checklist To Implement Secure Access Service Edge. Dispense information and present a thorough explanation of Steps, Responsible Person, Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Cloud Access Security Broker Casb Overview
Sase Model Cloud Access Security Broker Casb OverviewThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Increase audience engagement and knowledge by dispensing information using Sase Model Cloud Access Security Broker Casb Overview. This template helps you present information on five stages. You can also present information on Risk Visibility, Threat Prevention, Granular Cloud using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Cloud Access Security Broker Implementation Models
Sase Model Cloud Access Security Broker Implementation ModelsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Introducing Sase Model Cloud Access Security Broker Implementation Models to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Scanning, Forward Proxy, Reverse Proxy, using this template. Grab it now to reap its full benefits.
-
 Sase Model Cloud Access Security Broker Use Cases
Sase Model Cloud Access Security Broker Use CasesThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Present the topic in a bit more detail with this Sase Model Cloud Access Security Broker Use Cases. Use it as a tool for discussion and navigation on Protection Against Threats, Govern Usage, Secure Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Cloud Access Security Broker Working Process
Sase Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing Sase Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Discovery, Classification, Remediation, using this template. Grab it now to reap its full benefits.
-
 Sase Model Comparison Between Secure Access Service Edge And Sd Wan
Sase Model Comparison Between Secure Access Service Edge And Sd WanThis slide compares secure access service edge and software-defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD-WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Deliver an outstanding presentation on the topic using this Sase Model Comparison Between Secure Access Service Edge And Sd Wan. Dispense information and present a thorough explanation of Factors, Sd Wan, Sase using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Introduction To Secure Access Service Edge Sase
Sase Model Introduction To Secure Access Service Edge SaseThis slide represents the introduction of SASE cloud security technology. The purpose of this slide is to demonstrate the core capabilities, benefits and key components of SASE. The key components include SD-WAN, FWaaS, ZTNA, CASB, SWG, and unified management. Present the topic in a bit more detail with this Sase Model Introduction To Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Key Components, Benefits. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Pillars Of Cloud Access Security Broker
Sase Model Pillars Of Cloud Access Security BrokerThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Increase audience engagement and knowledge by dispensing information using Sase Model Pillars Of Cloud Access Security Broker. This template helps you present information on four stages. You can also present information on Compliance, Visibility, Threat Prevention using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Roadmap To Implement Secure Access Service Edge
Sase Model Roadmap To Implement Secure Access Service EdgeThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Introducing Sase Model Roadmap To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Examine The Environment, Providers And Solutions, Implementation Regularly, using this template. Grab it now to reap its full benefits.
-
 Sase Model Secure Access Service Edge Architecture Characteristics
Sase Model Secure Access Service Edge Architecture CharacteristicsThis slide represents the architectural characteristics of a secure access service edge. The purpose of this slide is to showcase the features of SASE architecture that include identity-driven, cloud-native, support for all edges, and global distribution. Introducing Sase Model Secure Access Service Edge Architecture Characteristics to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identity Driven, Support For All Edges, Globally Distributed, using this template. Grab it now to reap its full benefits.
-
 Sase Model Secure Access Service Edge Implementation Steps
Sase Model Secure Access Service Edge Implementation StepsThis slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD-WAN backbone, incorporating zero-trust solutions, etc. Increase audience engagement and knowledge by dispensing information using Sase Model Secure Access Service Edge Implementation Steps. This template helps you present information on five stages. You can also present information on Goals And Requirements, Incorporate Zero Trust Solutions, Test And Troubleshoot using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Secure Access Service Edge Importance
Sase Model Secure Access Service Edge ImportanceThis slide represents the importance of secure access service edge. This slides purpose is to demonstrate why businesses need the SASE model. The main reasons include scaling with business needs, encouraging work from anywhere environment, standing up for cyber threats, and offering a base for IoT adoption. Introducing Sase Model Secure Access Service Edge Importance to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Scales With Business, Cyberthreat Evolution, Provides Base Iot Adoption, using this template. Grab it now to reap its full benefits.
-
 Sase Model Secure Access Service Edge Sase Architecture
Sase Model Secure Access Service Edge Sase ArchitectureThis slide represents the SASE architecture overview and its goals. The purpose of this slide is to demonstrate the secure access service edge architecture and its goals. The building blocks of SASE Architecture include SWG, CASB, ZTNA, FWaaS, SD-WAN, Thin Edge, and so on. Deliver an outstanding presentation on the topic using this Sase Model Secure Access Service Edge Sase Architecture. Dispense information and present a thorough explanation of Secure Access Service, Edge Sase Architecture using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Model Secure Access Service Edge Training Program
Sase Model Secure Access Service Edge Training ProgramThis slide represents the training program for the secure access service edge model. The purpose of this slide is to demonstrate the teams eligible for training, the modules to be covered during the training, the schedule and venue of the training. Present the topic in a bit more detail with this Sase Model Secure Access Service Edge Training Program. Use it as a tool for discussion and navigation on . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Secure Access Service Edge Use Cases
Sase Model Secure Access Service Edge Use CasesThis slide represents the use cases of secure access service edge within an organization. The purpose of this slide is to demonstrate the various use cases of the SASE model, including rapid response to network demand, support for IoT and edge computing, VPN replacement, performance assurance and so on. Introducing Sase Model Secure Access Service Edge Use Cases to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Rapid Response, Edge Computing, Performance Assurance, using this template. Grab it now to reap its full benefits.
-
 Sase Model Timeline To Implement Cloud Access Security Broker
Sase Model Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using Sase Model Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Hybrid Settings, Environments Are Configured, Cloud App using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Sase Model Timeline To Implement Secure Access Service Edge
Sase Model Timeline To Implement Secure Access Service EdgeThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing Sase Model Timeline To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Jan, Mar, May, Jul, using this template. Grab it now to reap its full benefits.
-
 Sase Model Working Of Secure Access Service Edge
Sase Model Working Of Secure Access Service EdgeThis slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. Present the topic in a bit more detail with this Sase Model Working Of Secure Access Service Edge. Use it as a tool for discussion and navigation on Traditional Network Security Model, Network Security Model. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Reduce Attack Surface With Privilege Access Management Creating Cyber Security Awareness
Reduce Attack Surface With Privilege Access Management Creating Cyber Security AwarenessThe following slide depicts the privilege access management PAM workflow to protect against suspicious events. It includes elements such as user access request, password retrieval, session proxy, record sessions, audit logs, servers etc. Deliver an outstanding presentation on the topic using this Reduce Attack Surface With Privilege Access Management Creating Cyber Security Awareness Dispense information and present a thorough explanation of Time Consuming Process, Incremental Backup using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Icon For Unauthorised Access
Cyber Security Icon For Unauthorised AccessPresenting our set of slides with Cyber Security Icon For Unauthorised Access. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Security Icon, Unauthorised Access.
-
 Comparison Between ZTNA And Secure Access Service Edge Identity Defined Networking
Comparison Between ZTNA And Secure Access Service Edge Identity Defined NetworkingThis slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Present the topic in a bit more detail with this Comparison Between ZTNA And Secure Access Service Edge Identity Defined Networking Use it as a tool for discussion and navigation on Key Features, Deployment, Benefits, Challenges This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Features Of Zero Trust Network Access Security Model Identity Defined Networking
Features Of Zero Trust Network Access Security Model Identity Defined NetworkingThis slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Deliver an outstanding presentation on the topic using this Features Of Zero Trust Network Access Security Model Identity Defined Networking Dispense information and present a thorough explanation of Safeguards Private, Restriction Of Access, Hazards Quickly using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Traditional Security Models Vs Zero Trust Network Access Identity Defined Networking
Traditional Security Models Vs Zero Trust Network Access Identity Defined NetworkingThis slide represents the comparative analysis between traditional security models and ZTNA. This slide highlights the main differences between ZTNA and conventional security models based on trust, foundation, dependence, visibility, attack surface and scaling. Deliver an outstanding presentation on the topic using this Traditional Security Models Vs Zero Trust Network Access Identity Defined Networking Dispense information and present a thorough explanation of Traditional Security Model, Foundation, Dependence, Visibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Of Secure Access Service Edge Firewall Virtualization
Overview Of Secure Access Service Edge Firewall VirtualizationThis slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc. Introducing Overview Of Secure Access Service Edge Firewall Virtualization to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on SASE, Cloud Firewalls, Magic Firewall, using this template. Grab it now to reap its full benefits.
-
 Internet Gateway Security IT Relationship Between Secure Access Service
Internet Gateway Security IT Relationship Between Secure Access ServiceThis slide describes the integration of SASE and SWG to provide more reliable security solutions for cloud applications. The purpose of this slide is to explain the various domains where these two can collaborate such as microservices in distributed environment, etc. Introducing Internet Gateway Security IT Relationship Between Secure Access Service to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Administration Of Microservices, Distributed Environment, Visibility Control Over Traffic Passing, Cloud-Native Application, using this template. Grab it now to reap its full benefits.
-
 Server Security Maintenance Timeline For Preventing Unauthorized Access
Server Security Maintenance Timeline For Preventing Unauthorized AccessFollowing slide highlights timeline for server security maintenance by preventing unauthorized access, also including tasks such as installation of new package, updates of other applications, review server accessibility, etc. Presenting our well structured Server Security Maintenance Timeline For Preventing Unauthorized Access. The topics discussed in this slide are Review Server Accessibility, Firewall Rules, User Password Change. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comparison Between ZTNA And Secure Access Service Edge Ppt File Diagrams
Comparison Between ZTNA And Secure Access Service Edge Ppt File DiagramsThis slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Present the topic in a bit more detail with this Comparison Between ZTNA And Secure Access Service Edge Ppt File Diagrams. Use it as a tool for discussion and navigation on Key Features, Deployment, Benefits. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Features Of Zero Trust Network Access Security Model Ppt File Files
Features Of Zero Trust Network Access Security Model Ppt File FilesThis slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Present the topic in a bit more detail with this Features Of Zero Trust Network Access Security Model Ppt File Files. Use it as a tool for discussion and navigation on Safeguards Private Apps, Features, Description. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Benefits Of Cloud Access Security Broker 2 0 CASB Cloud Security
Benefits Of Cloud Access Security Broker 2 0 CASB Cloud SecurityThis slide represents the advantages of cloud access security broker version 2.0. The purpose of this slide is to highlight the main benefits of CASB 2.0, including comprehensive coverage, cost-effectiveness, enhanced security efficacy, improved visibility, app database, and so on. Increase audience engagement and knowledge by dispensing information using Benefits Of Cloud Access Security Broker 2 0 CASB Cloud Security. This template helps you present information on six stages. You can also present information on Enhanced Security Efficacy, Improved Visibility, Comprehensive Coverage, Cloud Access Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Benefits Of Cloud Access Security Broker CASB Cloud Security
Benefits Of Cloud Access Security Broker CASB Cloud SecurityThis slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. Present the topic in a bit more detail with this Benefits Of Cloud Access Security Broker CASB Cloud Security. Use it as a tool for discussion and navigation on Cyber Threat Prevention, Granular Cloud Usage Control, Data Loss Prevention, Controlled External File Sharing. This template is free to edit as deemed fit for your organization. Therefore download it now.





