Powerpoint Templates and Google slides for Access Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cloud Access Security Broker CASB V2 Powerpoint Presentation Slides
Cloud Access Security Broker CASB V2 Powerpoint Presentation SlidesEnthrall your audience with this Cloud Access Security Broker CASB V2 Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising eighty seven slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Cloud Access Security Broker CASB Powerpoint Presentation Slides
Cloud Access Security Broker CASB Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Cloud Access Security Broker CASB Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the eighty seven slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Secure Access Service Edge SASE Powerpoint Presentation Slides
Secure Access Service Edge SASE Powerpoint Presentation SlidesDeliver an informational PPT on various topics by using this Secure Access Service Edge SASE Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with eighty slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
-
 Securing Systems With Identity And Access Management Powerpoint Presentation Slides
Securing Systems With Identity And Access Management Powerpoint Presentation SlidesWhile your presentation may contain top-notch content, if it lacks visual appeal, you are not fully engaging your audience. Introducing our Securing Systems With Identity And Access Management Powerpoint Presentation Slides deck, designed to engage your audience. Our complete deck boasts a seamless blend of Creativity and versatility. You can effortlessly customize elements and color schemes to align with your brand identity. Save precious time with our pre-designed template, compatible with Microsoft versions and Google Slides. Plus, it is downloadable in multiple formats like JPG, JPEG, and PNG. Elevate your presentations and outshine your competitors effortlessly with our visually stunning 100 percent editable deck.
-
 Implementing Identity And Access Management For Operational Security OPSEC Training Ppt
Implementing Identity And Access Management For Operational Security OPSEC Training PptPresenting Implementing Identity and Access Management for Operational Security OPSEC. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Network Access Control As An Element Of Network Security Training Ppt
Network Access Control As An Element Of Network Security Training PptPresenting Network Access Control as an Element of Network Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Cloud Access Security Brokers As An Element Of Network Security Training Ppt
Cloud Access Security Brokers As An Element Of Network Security Training PptPresenting Cloud Access Security Brokers as an Element of Network Security. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Cloud Security Icon Security Computing Data Protection Digital Access
Cloud Security Icon Security Computing Data Protection Digital AccessKeep your audience glued to their seats with professionally designed PPT slides. This deck comprises of total of twelve slides. It has PPT templates with creative visuals and well researched content. Not just this, our PowerPoint professionals have crafted this deck with appropriate diagrams, layouts, icons, graphs, charts and more. This content ready presentation deck is fully editable. Just click the DOWNLOAD button below. Change the colour, text and font size. You can also modify the content as per your need. Get access to this well crafted complete deck presentation and leave your audience stunned.
-
 Multi factor authentication secure access process application server through
Multi factor authentication secure access process application server throughDeliver a lucid presentation by utilizing this Multi Factor Authentication Secure Access Process Application Server Through. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Multi Factor Authentication, Secure, Access, Process, Application. All the twelve slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
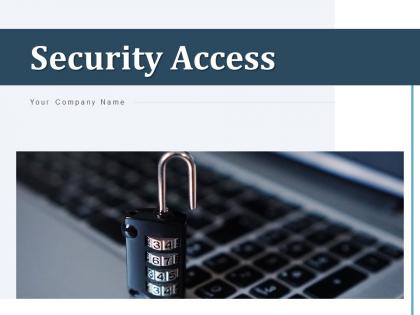 Security Access Protection Fingerprint Information Mobile
Security Access Protection Fingerprint Information MobileDeliver a credible and compelling presentation by deploying this Security Access Protection Fingerprint Information Mobile. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The eleven slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Security Access Protection Fingerprint Information Mobile PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
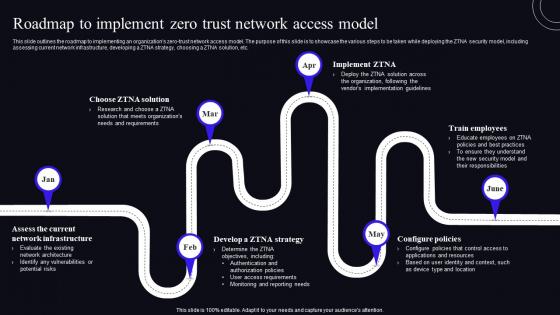 Roadmap To Implement Zero Trust Network Access Model Zero Trust Security Model
Roadmap To Implement Zero Trust Network Access Model Zero Trust Security ModelThis Slide Outlines The Roadmap To Implementing An Organizations Zero-Trust Network Access Model. The Purpose Of This Slide Is To Showcase The Various Steps To Be Taken While Deploying The ZTNA Security Model, Including Assessing Current Network Infrastructure, Developing A ZTNA Strategy, Choosing A ZTNA Solution, Etc. Increase Audience Engagement And Knowledge By Dispensing Information Using Roadmap To Implement Zero Trust Network Access Model Zero Trust Security Model. This Template Helps You Present Information On Six Stages. You Can Also Present Information On Roadmap, Network Infrastructure, Configure Policies Using This PPT Design. This Layout Is Completely Editable So Personaize It Now To Meet Your Audiences Expectations.
-
 Top Tenets Of Zero Trust Network Access Model Zero Trust Security Model
Top Tenets Of Zero Trust Network Access Model Zero Trust Security ModelDeliver an outstanding presentation on the topic using this Top Tenets Of Zero Trust Network Access Model Zero Trust Security Model. Dispense information and present a thorough explanation of Continuous Authentication, Data Protection, Facilitate Least Privilege Access using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Working Of Zero Trust Network Access Model Zero Trust Security Model
Working Of Zero Trust Network Access Model Zero Trust Security ModelThis slide outlines the working of zero trust network access. The purpose of this slide is to demonstrate the workflow of ZTNA, including the principles shared by all ZTNA architectures. The principles include no use of MPLS, hiding the IP addresses, securing devices, IDP and SSO platform, and so on. Deliver an outstanding presentation on the topic using this Working Of Zero Trust Network Access Model Zero Trust Security Model. Dispense information and present a thorough explanation of Demonstrate, Architectures, Business using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 CASB Performance Tracking Dashboard
Cloud Access Security Broker CASB V2 CASB Performance Tracking DashboardThis slide outlines the performance tracking dashboard for CASB deployment. The purpose of this slide is to showcase the status of various applications, IP addresses, users, machines, and web traffic. It also includes cloud discovery open alerts, risk levels, and top entities. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 CASB Performance Tracking Dashboard. Dispense information and present a thorough explanation of Performance Tracking Dashboard, Machines And Web Traffic, Cloud Discover Open Alerts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker CASB V2 Use Cases Ppt Ideas Graphics Download
Cloud Access Security Broker CASB V2 Use Cases Ppt Ideas Graphics DownloadThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker CASB V2 Use Cases Ppt Ideas Graphics Download. Dispense information and present a thorough explanation of Protection Against Threats, Secure Data, Upload Prevention And Encryption, Cloud Solutions With Transparency using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Cloud Access Security Broker CASB V2 Ppt Ideas Design Inspiration
Table Of Contents For Cloud Access Security Broker CASB V2 Ppt Ideas Design InspirationIntroducing Table Of Contents For Cloud Access Security Broker CASB V2 Ppt Ideas Design Inspiration to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Shadow IT Management Lifecycle, Threat Protection, Data Security, Emerging Cloud Security Risks And Threats, using this template. Grab it now to reap its full benefits.
-
 Global Market Of Secure Access Service Edge Cloud Security Model
Global Market Of Secure Access Service Edge Cloud Security ModelThis slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work from anywhere culture, and so on. Deliver an outstanding presentation on the topic using this Global Market Of Secure Access Service Edge Cloud Security Model. Dispense information and present a thorough explanation of Global, Market, Secure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Access Service Edge Performance Tracking Dashboard Cloud Security Model
Secure Access Service Edge Performance Tracking Dashboard Cloud Security ModelThis slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Deliver an outstanding presentation on the topic using this Secure Access Service Edge Performance Tracking Dashboard Cloud Security Model. Dispense information and present a thorough explanation of Service, Secure, Performance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Sase Security Global Market Of Secure Access Service Edge
Sase Security Global Market Of Secure Access Service EdgeThis slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work-from-anywhere culture, and so on. Present the topic in a bit more detail with this Sase Security Global Market Of Secure Access Service Edge. Use it as a tool for discussion and navigation on Service, Technologies, Advancements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Security Secure Access Service Edge Performance Tracking Dashboard
Sase Security Secure Access Service Edge Performance Tracking DashboardThis slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Deliver an outstanding presentation on the topic using this Sase Security Secure Access Service Edge Performance Tracking Dashboard. Dispense information and present a thorough explanation of Performance, Dashboard, Critical Network Alarms using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Global Market Of Secure Access Service Edge Secure Access Service Edge Sase
Global Market Of Secure Access Service Edge Secure Access Service Edge SaseThis slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work-from-anywhere culture, and so on. Present the topic in a bit more detail with this Global Market Of Secure Access Service Edge Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Framework, Requirements, Advancements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Secure Performance Tracking Dashboard Secure Access Service Edge Sase
Secure Performance Tracking Dashboard Secure Access Service Edge SaseThis slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Deliver an outstanding presentation on the topic using this Secure Performance Tracking Dashboard Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Performance, Dashboard, Service using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents For Secure Access Service Edge Sase
Table Of Contents For Secure Access Service Edge SaseDeliver an outstanding presentation on the topic using this Table Of Contents For Secure Access Service Edge Sase. Dispense information and present a thorough explanation of Traditional Network Security Problems, SASE Architecture And Working, Importance Of SASE Model using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SASE Network Security Global Market Of Secure Access Service Edge
SASE Network Security Global Market Of Secure Access Service EdgeThis slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work from anywhere culture, and so on. Deliver an outstanding presentation on the topic using this SASE Network Security Global Market Of Secure Access Service Edge. Dispense information and present a thorough explanation of Service, Secure, Global using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Secure Access Service Edge Performance Tracking Dashboard SASE Network Security
Secure Access Service Edge Performance Tracking Dashboard SASE Network SecurityThis slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Deliver an outstanding presentation on the topic using this Secure Access Service Edge Performance Tracking Dashboard SASE Network Security. Dispense information and present a thorough explanation of Service, Performance, Tracking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker Use Cases Next Generation CASB
Cloud Access Security Broker Use Cases Next Generation CASBThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Use Cases Next Generation CASB Dispense information and present a thorough explanation of Protection Against Threats, Govern Usage, Secure Data using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Global Market Of Secure Access Service Edge
SD WAN Model Global Market Of Secure Access Service EdgeThis slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work-from-anywhere culture, and so on. Present the topic in a bit more detail with this SD WAN Model Global Market Of Secure Access Service Edge. Use it as a tool for discussion and navigation on Rapid Adoption Of Cloud Native, Strong Security Framework Requirements, Cloud Computing Technologies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Global Market Of Secure Access Service Edge
Sase Model Global Market Of Secure Access Service EdgeThis slide depicts the global market size of the SASE market by components such as platforms and services. The purpose of this slide is to showcase the compound annual growth rate for the SASE model, including its growth drivers, such as cloud adoption, work-from-anywhere culture, and so on. Present the topic in a bit more detail with this Sase Model Global Market Of Secure Access Service Edge. Use it as a tool for discussion and navigation on Secure Access Service Edge. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Sase Model Secure Access Service Edge Performance Tracking Dashboard
Sase Model Secure Access Service Edge Performance Tracking DashboardThis slide demonstrates the performance tracking dashboard for secure access service edge. The purpose of this slide is to showcase the overall performance of the SASE model, including connections, critical network alarms, critical security alerts, application volume, risky applications, and unblocked security threats. Present the topic in a bit more detail with this Sase Model Secure Access Service Edge Performance Tracking Dashboard. Use it as a tool for discussion and navigation on Critical Network Alarms, Risky Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Use Cases CASB Cloud Security
Cloud Access Security Broker Use Cases CASB Cloud SecurityThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Present the topic in a bit more detail with this Cloud Access Security Broker Use Cases CASB Cloud Security. Use it as a tool for discussion and navigation on Protection Against Threats, Compliance Policies, Cloud Access Security Broker. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
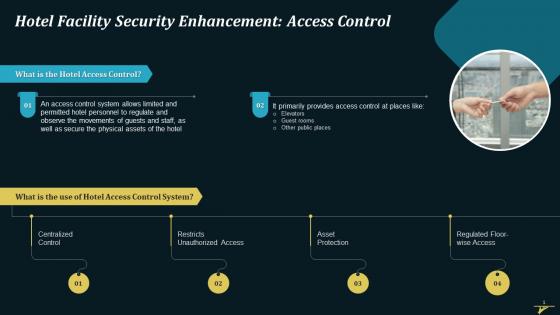 Enhanced Hotel Facility Security With Access Control Training Ppt
Enhanced Hotel Facility Security With Access Control Training PptPresenting Enhanced Hotel Facility Security with Access Control. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizablealter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Avoid Unnecessary Data Access Storage And Transmission Internet Of Things IoT Security Cybersecurity SS
Avoid Unnecessary Data Access Storage And Transmission Internet Of Things IoT Security Cybersecurity SSThis slide showcases avoiding unnecessary resources on internet of things IoT devices, helping developers avoid transmission and storage costs. It provides details about data classification, compliance, etc. Deliver an outstanding presentation on the topic using this Avoid Unnecessary Data Access Storage And Transmission Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Privacy And Compliance Considerations, Data Privacy And Compliance, Data Access Storage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Budget For Identity And Access Management Training Securing Systems With Identity
Budget For Identity And Access Management Training Securing Systems With IdentityThis slide showcases the breakdown cost for the IAM installation and management training for the customers. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor cost, training cost, etc. Present the topic in a bit more detail with this Budget For Identity And Access Management Training Securing Systems With Identity Use it as a tool for discussion and navigation on Components, Training Cost Distribution This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Insights Reporting Dashboard Securing Systems With Identity
Identity And Access Management Insights Reporting Dashboard Securing Systems With IdentityThis slide represents the reporting dashboard of the Identity and Access Management process. The purpose of this slide is to showcase the IAM insights reporting dashboard, and the components include syslog errors, system checks, failed task results, etc. Deliver an outstanding presentation on the topic using this Identity And Access Management Insights Reporting Dashboard Securing Systems With Identity Dispense information and present a thorough explanation of Failed Task Results, Syslog Errors, Certifications Trends using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Us Identity And Access Management Market Size Securing Systems With Identity
Us Identity And Access Management Market Size Securing Systems With IdentityThis slide depicts the US IAM market size in global market. The purpose of this slide is to highlight the US market size of the IAM process in terms of revenue generation and compound annual growth rate. Deliver an outstanding presentation on the topic using this Us Identity And Access Management Market Size Securing Systems With Identity Dispense information and present a thorough explanation of Provisioning Access, Compromising Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SS
Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases managing endpoint security access management through just in time method. It provides details about access request, permission duration, etc.Present the topic in a bit more detail with this Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Access Request, Our Process, Potential Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building Access Control Security Market Snapshot
Building Access Control Security Market SnapshotThis slide showcases the building access control security market size referable for users,investors and business owners for making relevant decisions. It include details such as increase in the demand for advanced technologies and rise of 5g networks. Introducing our Building Access Control Security Market Snapshot set of slides. The topics discussed in these slides are Market Size,Projections USD Bn,Top Companies. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data security it define access control measures for employees
Data security it define access control measures for employeesThis slide represents how it is essential to minimize the rights or access of employees in an organization to keep data safe and prevent it from deletion, manipulation. Increase audience engagement and knowledge by dispensing information using Data Security IT Define Access Control Measures For Employees. This template helps you present information on four stages. You can also present information on Data, Networks, Roles, Organization, Data Or Networks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Computer system security define access control measures for employees
Computer system security define access control measures for employeesThis slide represents how it is essential to minimize the rights oraccess of employees in an organization to keep data safe and prevent it from deletion, manipulation. Introducing Computer System Security Define Access Control Measures For Employees to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Organization, Responsibilities, Access, using this template. Grab it now to reap its full benefits.
-
 Firewall As A Service Fwaas Overview Of Secure Access Service Edge
Firewall As A Service Fwaas Overview Of Secure Access Service EdgeThis slide talks about the role of Firewall-as-a-Service inside a secure access service edge framework. The purpose of this slide is to explain how FWaaS and SASE work together to provide network security. The components include SASE, Cloudflare Magic Firewall, etc. Increase audience engagement and knowledge by dispensing information using Firewall As A Service Fwaas Overview Of Secure Access Service Edge. This template helps you present information on three stages. You can also present information on Cloudflare Global Network, Cloud Infrastructure, Cloud Access Security Broker, Secure Web Gateways, Zero Trust Network Access using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Before Vs After Zero Trust Network Access Implementation Zero Trust Security Model
Before Vs After Zero Trust Network Access Implementation Zero Trust Security ModelThis slide outlines the problems with the legacy virtual private network security model and how ZTNA can overcome those challenges. The purpose of this slide is to showcase the various VPN challenges and ZTNA solutions for those problems. Deliver an outstanding presentation on the topic using this Before Vs After Zero Trust Network Access Implementation Zero Trust Security Model. Dispense information and present a thorough explanation of Implementation, Distributed, Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Benefits Of Zero Trust Network Access ZTNA Zero Trust Security Model
Benefits Of Zero Trust Network Access ZTNA Zero Trust Security ModelThis Slide Represents The Benefits Of Zero Trust Network Access, A Component Of SASE Technology. The Purpose Of This Slide Is To Demonstrate The Multiple Benefits Of ZTNA To Businesses And Users. It Also Caters To The Security Benefits Such As Increased Control And Visibility, Invisible Infrastructure, And Simple App Segmentation. Present The Topic In A Bit More Detail With This Benefits Of Zero Trust Network Access ZTNA Zero Trust Security Model. Use It As A Tool For Discussion And Navigation On Deployment, Experiences, Appliances. This Template Is Free To Edit As Deemed Fit For Your Organization. Therefore Download It Now.
-
 Challenges Of VPN Based Remote Access Solutions Zero Trust Security Model
Challenges Of VPN Based Remote Access Solutions Zero Trust Security ModelThis slide outlines the limitations of virtual private network-based remote access services. The purpose of this slide is to showcase the various challenges of the VPN network system and how the zero trust network model can overcome those issues. Present the topic in a bit more detail with this Challenges Of VPN Based Remote Access Solutions Zero Trust Security Model. Use it as a tool for discussion and navigation on Extreme Implicit Trust, Performance Problems, Insufficient Granular. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Build Zero Trust Network Access Architecture Zero Trust Security Model
Checklist To Build Zero Trust Network Access Architecture Zero Trust Security ModelThis slide outlines the checklist to develop a zero-trust network access architecture. The purpose of this slide is to define the various measures organizations should take while building a ZTNA architecture. The measures include knowing the architecture, creating a strong device identity, and so on. Deliver an outstanding presentation on the topic using this Checklist To Build Zero Trust Network Access Architecture Zero Trust Security Model. Dispense information and present a thorough explanation of Architecture, Measures, Organizations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparison Between ZTNA And Secure Access Service Edge Zero Trust Security Model
Comparison Between ZTNA And Secure Access Service Edge Zero Trust Security ModelThis slide compares the two security models, such as zero trust network architecture and secure access service edge. The purpose of this slide is to highlight the difference between ZTNA and SASE based on definition, key features, deployment, use cases, benefits and challenges. Deliver an outstanding presentation on the topic using this Comparison Between ZTNA And Secure Access Service Edge Zero Trust Security Model. Dispense information and present a thorough explanation of Comparison, Architecture, Service using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Critical Principles Of Zero Trust Network Access Model Zero Trust Security Model
Critical Principles Of Zero Trust Network Access Model Zero Trust Security ModelThis slide illustrates the key principles of zero trust network access model, including their impact. The purpose of this slide is to highlight the primary principles of the ZTNA model, including least privilege access, micro-segmentation, MFA, device validation, and monitoring everything. Present the topic in a bit more detail with this Critical Principles Of Zero Trust Network Access Model Zero Trust Security Model. Use it as a tool for discussion and navigation on Description, Segmentation, Validation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1585 Zero Trust Network Access Architectural Models Zero Trust Security Model
F1585 Zero Trust Network Access Architectural Models Zero Trust Security ModelThis slide describes the main models of ZTNA architecture. The purpose of this slide is to showcase the two essential models of zero trust network access architecture, including client-based and browser-based. Both models perform security functions, including identity verification, access control, and data encryption. Introducing F1585 Zero Trust Network Access Architectural Models Zero Trust Security Model to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Architectural, Resources, Verification, using this template. Grab it now to reap its full benefits.
-
 F1586 Zero Trust Network Access Architecture Overview Zero Trust Security Model
F1586 Zero Trust Network Access Architecture Overview Zero Trust Security ModelThis slide gives an overview of zero trust network access architecture. The purpose of this slide is to showcase the ZTNA architecture and its benefits, covering granting safe and fast access, protecting reliable remote access, protecting sensitive data and apps, stopping insider threats, and so on. Present the topic in a bit more detail with this F1586 Zero Trust Network Access Architecture Overview Zero Trust Security Model. Use it as a tool for discussion and navigation on Resources, Architecture, Overview. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security Model
F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security ModelThis slide outlines the workflow of zero trust network access architecture. The purpose of this slide is to showcase the various steps of the ZTNA model workflow, including user authentication, grant access, monitoring of user sessions, and threat response. Increase audience engagement and knowledge by dispensing information using F1587 Zero Trust Network Access Architecture Workflow Zero Trust Security Model. This template helps you present information on six stages. You can also present information on Architecture, Workflow, Resources using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 F1588 Zero Trust Network Access Implementation Challenges Zero Trust Security Model
F1588 Zero Trust Network Access Implementation Challenges Zero Trust Security ModelThis slide outlines the main challenges of ZTNA implementation. The purpose of this slide is to highlight the primary challenges that organizations face while deploying ZTNA. The challenges include continual management and maintenance, low productivity, security risks, and so on Present the topic in a bit more detail with this F1588 Zero Trust Network Access Implementation Challenges Zero Trust Security Model. Use it as a tool for discussion and navigation on Implementation, Organizations, Productivity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1589 Zero Trust Network Access Performance Tracking Dashboard Zero Trust Security Model
F1589 Zero Trust Network Access Performance Tracking Dashboard Zero Trust Security ModelThis slide represents the performance tracking dashboard for zero trust network access. The purpose of this slide is to showcase the level of request modes, connected users, daily usage of the network, security rating, device risk and threat flow. Deliver an outstanding presentation on the topic using this F1589 Zero Trust Network Access Performance Tracking Dashboard Zero Trust Security Model. Dispense information and present a thorough explanation of Performance, Dashboard, Represents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F1590 Zero Trust Network Access System Use Cases Zero Trust Security Model
F1590 Zero Trust Network Access System Use Cases Zero Trust Security ModelThis slide outlines multiple use cases of zero-trust network access systems. The purpose of this slide is to showcase the main use cases of the ZTNA model, which are replacing VPN and MPLS connections, internal firewall replacement, securing remote access to private apps, limiting user access, and so on. Present the topic in a bit more detail with this F1590 Zero Trust Network Access System Use Cases Zero Trust Security Model. Use it as a tool for discussion and navigation on Internal Firewall Replacement, Limiting User Access, Network Access Control Replacement. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1591 Zero Trust Network Access User Flow Overview Zero Trust Security Model
F1591 Zero Trust Network Access User Flow Overview Zero Trust Security ModelThis slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Deliver an outstanding presentation on the topic using this F1591 Zero Trust Network Access User Flow Overview Zero Trust Security Model. Dispense information and present a thorough explanation of Authentication, Process, Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F1592 Zero Trust Network Access ZTNA Introduction Zero Trust Security Model
F1592 Zero Trust Network Access ZTNA Introduction Zero Trust Security ModelThis slide represents the overview of zero trust network access, including its, benefits and principles. The purpose of this slide is to demonstrate the overview, principles and benefits of ZTNA. The primary benefits include seamless user experience, effortless scale, no need for legacy applications, etc. Present the topic in a bit more detail with this F1592 Zero Trust Network Access ZTNA Introduction Zero Trust Security Model. Use it as a tool for discussion and navigation on Introduction, Appliances, Infrastructure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F1593 Zero Trust Network Access Vs Virtual Private Network Zero Trust Security Model
F1593 Zero Trust Network Access Vs Virtual Private Network Zero Trust Security ModelThis slide describes the difference between zero trust network access and a virtual private network. The purpose of this slide is to showcase the flow of remote users in both networks. The comparison is based on user experience, cost savings, and network vs. application-level access. Deliver an outstanding presentation on the topic using this F1593 Zero Trust Network Access Vs Virtual Private Network Zero Trust Security Model. Dispense information and present a thorough explanation of Infrastructure, Configuration, Equipment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Features Of Zero Trust Network Access Security Model Zero Trust Security Model
Features Of Zero Trust Network Access Security Model Zero Trust Security ModelThis slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Present the topic in a bit more detail with this Features Of Zero Trust Network Access Security Model Zero Trust Security Model. Use it as a tool for discussion and navigation on Organizations, Applications, Infrastructure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Main Pillars Of Zero Network Trust Access Zero Trust Security Model
Main Pillars Of Zero Network Trust Access Zero Trust Security ModelThis slide outlines the critical pillars of the zero network trust access model. The purpose of this slide is to showcase the primary pillars of ZTNA, including users, devices, networks, infrastructure, applications, data, visibility and analytics, and orchestration and automation. Present the topic in a bit more detail with this Main Pillars Of Zero Network Trust Access Zero Trust Security Model. Use it as a tool for discussion and navigation on Application, Infrastructure, Orchestration Automation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Reasons To Adopt Zero Trust Network Access Model Zero Trust Security Model
Reasons To Adopt Zero Trust Network Access Model Zero Trust Security ModelThis slide represents the importance of implementing the zero-trust network access model. This slide aims to highlight the main reasons businesses should adopt the ZTNA model, including work-from-home culture, revealing IP addresses, network transparency, and so on. Introducing Reasons To Adopt Zero Trust Network Access Model Zero Trust Security Model to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Businesses, Resources, Organizations, using this template. Grab it now to reap its full benefits.
-
 Steps To Implement Zero Trust Network Access Model Zero Trust Security Model
Steps To Implement Zero Trust Network Access Model Zero Trust Security ModelThis slide outlines the crucial steps to implement the zero trust network access model in an organization. The purpose of this slide is to highlight the key steps to perform to deploy the ZTNA model. The steps include identifying assets, defining protection surface, understanding the businesss security model, etc. Present the topic in a bit more detail with this Steps To Implement Zero Trust Network Access Model Zero Trust Security Model. Use it as a tool for discussion and navigation on Architecture, Protection, Monitor The Network. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technologies Used In Zero Trust Network Access Zero Trust Security Model
Technologies Used In Zero Trust Network Access Zero Trust Security ModelThis slide represents the techniques used in the zero-trust network access model. The purpose of this slide is to showcase the multiple technologies used in the ZTNA model, including their functions and the network protection they offer. Deliver an outstanding presentation on the topic using this Technologies Used In Zero Trust Network Access Zero Trust Security Model. Dispense information and present a thorough explanation of Technologies, Techniques, Protection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.




