Powerpoint Templates and Google slides for Securitize
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Checklist To Establish Triage Capability In Cyber Security
Checklist To Establish Triage Capability In Cyber SecurityThis slide represents checklist to establish triage capability in cyber security which assists to analyse threat alerts and effectively response cyber threats. It includes checklist to establish triage capability in cyber security which includes steps such as type of events, skill levels, etc Introducing our Checklist To Establish Triage Capability In Cyber Security set of slides. The topics discussed in these slides are Types Of Events, Skills Levels, Channels Of Support. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Triage For Mitigating Firewall Incidents
Cyber Security Triage For Mitigating Firewall IncidentsThis slide represents working of cyber security triage to mitigate against firewall incidents which assists to strengthen organizations overall cybersecurity posture. It involves cyber security triage for mitigating firewall incidents effectively such as identify and classify, etc Presenting our set of slides with name Cyber Security Triage For Mitigating Firewall Incidents This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify And Classify, Prioritize Based On Severity, Resource Allocation
-
 Different Types Of Triage Cyber Security Incidents
Different Types Of Triage Cyber Security IncidentsThis slide represents different triage cybersecurity incidents which assists to categorize, prioritize and respond to various types of security incidents. It includes different types of triage cybersecurity incidents such as heavy traffic on port 80, etc Introducing our premium set of slides with name Different Types Of Triage Cyber Security Incidents Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Phishing Attempts, Malware Attacks. So download instantly and tailor it with your information.
-
 Managing Cyber Incidents With Triage Security
Managing Cyber Incidents With Triage SecurityThis slide represents management of cyber incidents with triage cyber security which assists to focus on threats encountered on regular basis. It includes managing cyber incidents with triage security such as determine incident technique, etc Presenting our set of slides with name Managing Cyber Incidents With Triage Security This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Determine Incident Technique, Identify Affected Areas, Measure Attack Density
-
 Steps For Effective Triage Cyber Security Process
Steps For Effective Triage Cyber Security ProcessThis slide represents steps for effective triage process which assists security teams to focus on critical threats and allocate resources effectively., It includes steps for effective triage cyber security process such as identify, map and eradicate Introducing our premium set of slides with name Steps For Effective Triage Cyber Security Process Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identify Artifacts, Draw Event Timelines, System From Backup. So download instantly and tailor it with your information.
-
 Steps To Conduct Triage Of Cyber Security Alerts In Soc
Steps To Conduct Triage Of Cyber Security Alerts In SocThis slide represents steps to conduct triage of cyber security alerts in SOC which assists organizations to gather contextual information about potential threats and analyse them to minimize damage. It includes steps to conduct triage of cyber security alerts in SOC such as establish triage process, etc Presenting our set of slides with name Steps To Conduct Triage Of Cyber Security Alerts In Soc This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Establish Triage Process, Prioritize Alerts, Collect Contextual Information
-
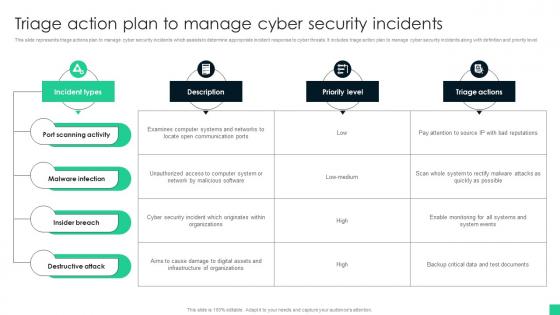 Triage Action Plan To Manage Cyber Security Incidents
Triage Action Plan To Manage Cyber Security IncidentsThis slide represents triage actions plan to manage cyber security incidents which assists to determine appropriate incident response to cyber threats. It includes triage action plan to manage cyber security incidents along with definition and priority level. Introducing our Triage Action Plan To Manage Cyber Security Incidents set of slides. The topics discussed in these slides are Port Scanning Activity, Malware Infection, Insider Breach. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Triage Cyber Security For System Protection Icon
Triage Cyber Security For System Protection IconPresenting our set of slides with name Triage Cyber Security For System Protection Icon This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Triage Cyber Security, System Protection Icon
-
 Triage Cyber Security To Identify Cyber Threats Icon
Triage Cyber Security To Identify Cyber Threats IconIntroducing our premium set of slides with name Triage Cyber Security To Identify Cyber Threats Icon Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Triage Cyber Security, Identify Cyber Threats Icon. So download instantly and tailor it with your information.
-
 Triage Process For Cyber Security Icon
Triage Process For Cyber Security IconPresenting our set of slides with name Triage Process For Cyber Security Icon This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Triage Process, Cyber Security Icon
-
 Use Cases Of Triage In Cyber Security
Use Cases Of Triage In Cyber SecurityThis slide represents use cases of triage in cyber security which assists to assess, prioritize and respond to cybersecurity events. It includes use cases of triage in cyber security such as security operations teams, incident response teams, etc. Introducing our premium set of slides with name Use Cases Of Triage In Cyber Security Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Operations Teams, Incident Response Teams, Security Analysis. So download instantly and tailor it with your information.
-
 Utilization Of Triage By Cyber Security Operations Teams
Utilization Of Triage By Cyber Security Operations TeamsThis slide represents utilization of triage by cyber security operations teams which assists to assess, prioritize and respond to cybersecurity incidents. It includes key components such as retrieval results, trace, etc Introducing our Utilization Of Triage By Cyber Security Operations Teams set of slides. The topics discussed in these slides are Triage Cyber Security, Network Traffic, Security Incidents. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Utilization Of Triage Cyber Security Process In It
Utilization Of Triage Cyber Security Process In ItThis slide represents utilization of triage cyber security process in IT which assists to handle large number of tickets and increases help desk efficiency. It includes utilization of triage cyber security process in IT such as IT operations, email, etc Presenting our set of slides with name Utilization Of Triage Cyber Security Process In It This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Software Testing, Agile Software Development, IT Operations
-
 Emergency Response Plan Icon For Security Threats
Emergency Response Plan Icon For Security ThreatsPresenting our set of slides with name Emergency Response Plan Icon For Security Threats. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Emergency Response Plan, Icon For Security Threats.
-
 Best Practices For Retail Facility Security
Best Practices For Retail Facility SecurityThe purpose of this slide is to implement comprehensive security measures, including surveillance systems, access control, employee training, and regular audits such as access control systems, cash handling, etc. Presenting our set of slides with name Best Practices For Retail Facility Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cash Handling, Access Control Systems, Surveillance Practices, Emergency Preparedness.
-
 Data Center Facility Security Plan
Data Center Facility Security PlanThe purpose of this slide is to ensure comprehensive protection against unauthorized access, physical threats, and data breaches including security aspects such as data center layout, environmental controls, etc. Introducing our premium set of slides with name Data Center Facility Security Plan. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Environmental Controls, Data Center Layout, Network Security, Vendor And Contractor Access. So download instantly and tailor it with your information.
-
 Digital Facility Security Assessment Checklist
Digital Facility Security Assessment ChecklistThe purpose of this slide is to systematically evaluate and enhance security measures of digital facility by identifying potential vulnerabilities and implementing necessary safeguards. Introducing our Digital Facility Security Assessment Checklist set of slides. The topics discussed in these slides are Access Control Systems, Check Fencing Condition, Monitor Entry Point Systems, Intrusion Detection. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Emerging Security Trends In Facility Management
Emerging Security Trends In Facility ManagementThe purpose of this slide is to to enhance overall security measures and streamline operational processes inclding trends such as IoT and remote monitoring, drone technologies, etc. Presenting our set of slides with name Emerging Security Trends In Facility Management. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Drone Technologies, Emerging Security Trends, Facility Management, Streamline Operational Processes.
-
 Employee Training Program On Facility Security
Employee Training Program On Facility SecurityThe purpose of this slide is to enhance staff awareness, skills, and adherence to security protocols, ensuring a secure and protected work environment including training modules such as access control, secure locks, etc. Presenting our well structured Employee Training Program On Facility Security. The topics discussed in this slide are Access Control, Secure Locks, Individual Unit Alarms, Emergency Response. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Facility Security Icon For Asset Protection
Facility Security Icon For Asset ProtectionIntroducing our premium set of slides with name Facility Security Icon For Asset Protection. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Facility Security, Icon For Asset Protection. So download instantly and tailor it with your information.
-
 Facility Security Icon For Quick Response To Incidents
Facility Security Icon For Quick Response To IncidentsIntroducing our Facility Security Icon For Quick Response To Incidents set of slides. The topics discussed in these slides are Facility Security, Icon For Quick, Response To Incidents. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Facility Security Icon To Ensure Employee Safety
Facility Security Icon To Ensure Employee SafetyPresenting our well structured Facility Security Icon To Ensure Employee Safety. The topics discussed in this slide are Facility Security, Icon To Ensure, Employee Safety. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Facility Security Officer Roles And Responsibilities
Facility Security Officer Roles And ResponsibilitiesThe purpose of this slide is to safeguard physical and personnel assets of a facility, ensuring compliance with security protocols including roles such as security program management, security clearance management, etc. Introducing our Facility Security Officer Roles And Responsibilities set of slides. The topics discussed in these slides are Security Program Management, Security Clearance Management, Training And Awareness, Document Control. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Facility Security Recovery Management Plan For Transportation Hubs
Facility Security Recovery Management Plan For Transportation HubsThe purpose of this slide is to develop a comprehensive facility security recovery management plan for transportation hubs to ensure rapid response, resilience, and restoration of operations including aspects such as cargo tracking, vehicle inspection, etc. Presenting our well structured Facility Security Recovery Management Plan For Transportation Hubs. The topics discussed in this slide are Physical Access Control, Vehicle Inspection, Cargo Tracking, Training And Drills. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Food Plant Security Measures To Enhance Facility Safety
Food Plant Security Measures To Enhance Facility SafetyThe purpose of this slide is to implement comprehensive access control systems, surveillance cameras, and employee training to safeguard food plant facilities through fencing, single entrance, security cameras, etc. Presenting our set of slides with name Food Plant Security Measures To Enhance Facility Safety. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Fencing, Single Entrance, Security Cameras, Enhance Facility Safety.
-
 Food Security Mitigation Strategies For Secure Facility
Food Security Mitigation Strategies For Secure FacilityThe purpose of this slide is to safeguard facilities and prevent unauthorized access, contamination, and theft including strategies such as physical secruity systems, emergency response plan, etc. Introducing our Food Security Mitigation Strategies For Secure Facility set of slides. The topics discussed in these slides are Employee Training Program, Physical Security Systems, Emergency Response Plan, Visitor Management System. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Key Focus Areas In Healthcare Facility Security For Clients
Key Focus Areas In Healthcare Facility Security For ClientsThe purpose of this slide is to safeguard sensitive areas, deploying advanced surveillance systems for real-time monitoring, and establishing comprehensive training programs for staff via inpatient facilities, emergency departments, etc. Introducing our premium set of slides with name Key Focus Areas In Healthcare Facility Security For Clients. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Key Focus Areas In Healthcare, Facility Security For Clients, Safeguard Sensitive Areas, Deploying Advanced Surveillance Systems. So download instantly and tailor it with your information.
-
 Recent Developments In Healthcare Facility Security
Recent Developments In Healthcare Facility SecurityThe purpose of this slide is to focus on integrating advanced technologies to enhance overall safety and protect sensitive patient information via visitor management systems, social media monitoring, etc. Presenting our set of slides with name Recent Developments In Healthcare Facility Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Social Media Monitoring, Visitor Management Systems, Interactive Access Control, Turnstiles And Anti Tailgating Tech.
-
 Security Measures For Manufacturing Plants And Industrial Facility
Security Measures For Manufacturing Plants And Industrial FacilityThe purpose of this slide is to enhance physical security, prevent unauthorized access, and mitigate potential threats in manufacturing plants and industrial facilities such as contingency plan, integrated approach, etc. Presenting our well structured Security Measures For Manufacturing Plants And Industrial Facility. The topics discussed in this slide are Layers Of Defense, Contingency Plan, Preparation, Integrated Approach. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
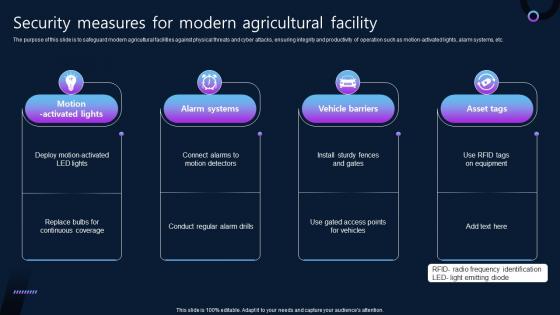 Security Measures For Modern Agricultural Facility
Security Measures For Modern Agricultural FacilityThe purpose of this slide is to safeguard modern agricultural facilities against physical threats and cyber attacks, ensuring integrity and productivity of operation such as motion-activated lights, alarm systems, etc. Introducing our premium set of slides with name Security Measures For Modern Agricultural Facility. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Conduct Regular Alarm Drills, Modern Agricultural Facility, Vehicle Barriers. So download instantly and tailor it with your information.
-
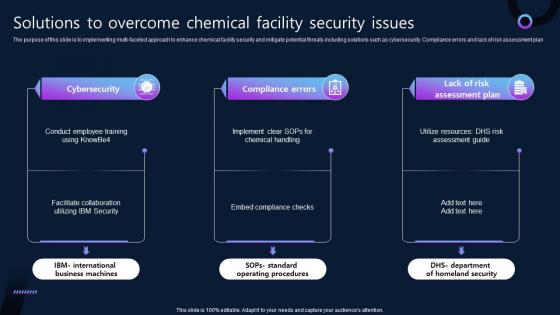 Solutions To Overcome Chemical Facility Security Issues
Solutions To Overcome Chemical Facility Security IssuesThe purpose of this slide is to implementing multi-faceted approach to enhance chemical facility security and mitigate potential threats including solutions such as cybersecurity. Compliance errors and lack of risk assessment plan. Presenting our set of slides with name Solutions To Overcome Chemical Facility Security Issues. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Compliance Errors, Lack Of Risk Assessment Plan, Cybersecurity, Chemical Facility Security Issues.
-
 Steps To Create Security Strategy For Industrial Facility
Steps To Create Security Strategy For Industrial FacilityThe purpose of this slide is to develop a comprehensive security strategy for an industrial facility to safeguard personnel, assets, and operations through assessing facility vulnerabilities, developing contingency plan, etc. Introducing our premium set of slides with name Steps To Create Security Strategy For Industrial Facility. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Establish Robust Security Protocols, Regular Updates And Maintenance, Develop Contingency Plan. So download instantly and tailor it with your information.
-
 Storage Facility Security Solutions For Businesses
Storage Facility Security Solutions For BusinessesThe purpose of this slide is to implement comprehensive security measures such as advanced access control systems, surveillance cameras, and alarm systems to safeguard business storage facilities such as perimeter security, access control, etc. Introducing our Storage Facility Security Solutions For Businesses set of slides. The topics discussed in these slides are Insurance And Legal Protection, Individual Unit Alarms, Access Control, Perimeter Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
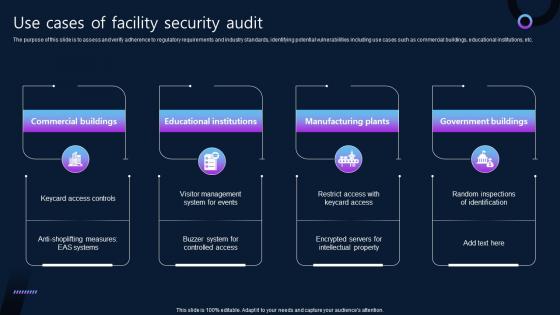 Use Cases Of Facility Security Audit
Use Cases Of Facility Security AuditThe purpose of this slide is to assess and verify adherence to regulatory requirements and industry standards, identifying potential vulnerabilities including use cases such as commercial buildings, educational institutions, etc. Presenting our set of slides with name Use Cases Of Facility Security Audit. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Government Buildings, Manufacturing Plants, Educational Institutions, Commercial Buildings.
-
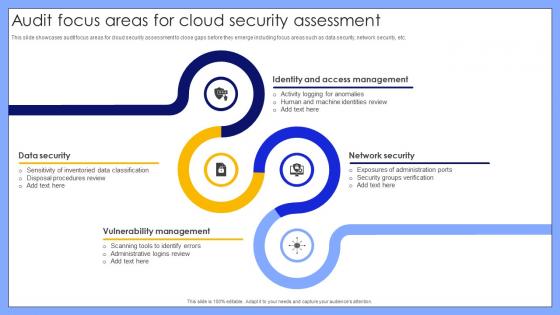 Audit Focus Areas For Cloud Security Assessment
Audit Focus Areas For Cloud Security AssessmentThis slide showcases audit focus areas for cloud security assessment to close gaps before they emerge including focus areas such as data security, network security, etc. Introducing our premium set of slides with name Audit Focus Areas For Cloud Security Assessment. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Security, Vulnerability Management, Network Security, Identity And Access Management. So download instantly and tailor it with your information.
-
 Cloud Security Audit Checklist For Businesses
Cloud Security Audit Checklist For BusinessesThis slide showcases checklist for cloud security audit to fix loopholes including checkpoints such as identifying cloud providers and services, access level management in cloud, etc. Introducing our Cloud Security Audit Checklist For Businesses set of slides. The topics discussed in these slides are Identify Cloud Providers And Services, Encrypt Data In Transit, Detecting Unusual Or Suspicious Activity. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Security Audit Techniques For Operational Efficiency
Cloud Security Audit Techniques For Operational EfficiencyThis slide showcases cloud security audit techniques to analyze data retention such as configuration review, access controls assessments, etc. Introducing our premium set of slides with name Cloud Security Audit Techniques For Operational Efficiency. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Configuration Review, Access Controls Assessment, Patch Management Review, Vendor Security Evaluation. So download instantly and tailor it with your information.
-
 Cloud Security Challenges And Solutions For Internal Audit
Cloud Security Challenges And Solutions For Internal AuditThis slide showcases solutions to overcome cloud security challenges for internal audit to ensure data protection such as lack of visibility, compliance, shared responsibility, etc. Presenting our well structured Cloud Security Challenges And Solutions For Internal Audit. The topics discussed in this slide are Lack Of Visibility, Compliance, Shared Responsibility, Identity And Access Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cloud Security Configuration Audit Icon
Cloud Security Configuration Audit IconPresenting our set of slides with name Cloud Security Configuration Audit Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Security, Configuration Audit Icon.
-
 Comparative Analysis Of Open Source Cloud Security Audit Tools
Comparative Analysis Of Open Source Cloud Security Audit ToolsThis slide showcases open source cloud security audit tools comparison to improve organizational position such as. Introducing our Comparative Analysis Of Open Source Cloud Security Audit Tools set of slides. The topics discussed in these slides are Comparative Analysis, Cloud Security Audit Tools, Audit Tools Comparison, Organizational Position. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Solutions To Overcome Cloud Security Audit Challenges
Solutions To Overcome Cloud Security Audit ChallengesThis slide showcases challenges and solutions of cloud security audit to standardize workloads including challenges such as effective communication, encryption strategy, etc. Presenting our set of slides with name Solutions To Overcome Cloud Security Audit Challenges. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Effective Communication, Encryption Strategy, Address Colocation, Scale And Complexity.
-
 Standards Covering Cloud Security Audit
Standards Covering Cloud Security AuditThis slide showcases standards related to cloud security audit to safeguard data and systems such as implementation, CIS foundation benchmarks, etc. Introducing our premium set of slides with name Standards Covering Cloud Security Audit. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Policies For Governance, Cloud Control Matrix, Cloud Security Audit. So download instantly and tailor it with your information.
-
 Steps To Conduct Cloud Security Audit
Steps To Conduct Cloud Security AuditThis slide showcases process to conduct cloud security audit for risk assessment such as evaluating cloud provider security, determining attack surface, etc. Presenting our well structured Steps To Conduct Cloud Security Audit. The topics discussed in this slide are Evaluate Cloud Provider Security, Determine Attack Surface, Automate Patching, Cloud Security Audit. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comparative Assessment Of EDR Security Solutions Tools
Comparative Assessment Of EDR Security Solutions ToolsThis slide represents EDR software tools and includes tools, solution scope, delivery model, features, pricing, and rating. Presenting our well structured Comparative Assessment Of EDR Security Solutions Tools. The topics discussed in this slide are Symantec Endpoint Protection, Crowd Strike Falcon Insight, Threat Intelligence, Detect Hidden Packages. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 EDR Security Tools Matrix For Process Efficiency
EDR Security Tools Matrix For Process EfficiencyThis slide depicts EDR security tools and includes anomaly detection, real-time data visibility, threat processing, logs collection from network, and detecting vulnerabilities. Presenting our well structured EDR Security Tools Matrix For Process Efficiency. The topics discussed in this slide are Anomaly Detection, Real Time Data Visibility, Threat Processing, Detecting Vulnerabilities. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 EDR Work Flowchart For Managing Security Incidents
EDR Work Flowchart For Managing Security IncidentsThis slide highlights EDR working flowchart and includes endpoints, database, restoration, IT analysts, and attackers. Introducing our EDR Work Flowchart For Managing Security Incidents set of slides. The topics discussed in these slides are Realtime Endpoint Behavior, Restoration, Behavioral Data, Managing Security Incidents. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Essential EDR Capabilities Security Components
Essential EDR Capabilities Security ComponentsThis slide showcases EDR capabilities including components, authorized head, impact, status, and improvement areas. Presenting our well structured Essential EDR Capabilities Security Components. The topics discussed in this slide are Behavioral Analytics, Actionable Threat Intelligence, Managed Threat Hunting. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Features Of Virtual Private Cloud
Security Features Of Virtual Private CloudThis slide covers four essential security features of a Virtual Private Cloud VPC The purpose of this template is to educate the audience about the robust security measures available in VPCs, including examples of their real-life applications. It includes Access control lists ACLs, Security groups, Network isolation, and Data encryption. Presenting our set of slides with Security Features Of Virtual Private Cloud. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Isolation, Data Encryption, Security Groups.
-
 Virtual Private Cloud Icon Representing Data Security
Virtual Private Cloud Icon Representing Data SecurityPresenting our set of slides with Virtual Private Cloud Icon Representing Data Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Security, Representing, Cloud Icon.
-
 Revolutionizing International Transactions Blockchain Security Practices For Cross Border Payments BCT SS
Revolutionizing International Transactions Blockchain Security Practices For Cross Border Payments BCT SSThe following slide illustrates various blockchain safety practices for international payments. It includes elements such as multi-signature wallets, smart contract security, authentication, private key protection, etc. Introducing Revolutionizing International Transactions Blockchain Security Practices For Cross Border Payments BCT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Multi Signature Wallets, Private Key Protection, Smart Contract Security, using this template. Grab it now to reap its full benefits.
-
 Revolutionizing International Blockchain Solutions For International Payments Security Enhancement BCT SS
Revolutionizing International Blockchain Solutions For International Payments Security Enhancement BCT SSThe following slide focusses on how blockchain based cross border payments enhances transaction security. It includes elements such as cryptography, immutability, consensus mechanism, smart contracts, permissioned access, decentralization, etc. Increase audience engagement and knowledge by dispensing information using Revolutionizing International Blockchain Solutions For International Payments Security Enhancement BCT SS. This template helps you present information on six stages. You can also present information on Consensus Mechanism, Permissioned Access, Decentralization, Cryptography using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS V
Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Deliver an outstanding presentation on the topic using this Data Security Best Practices To Protect Customer Information Database Marketing Techniques MKT SS V. Dispense information and present a thorough explanation of Data Usage Policy, Data Encryption, Endpoint Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Maintain Digital Wallet Security Implementation Of Cashless Payment
Best Practices To Maintain Digital Wallet Security Implementation Of Cashless PaymentMentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private.Increase audience engagement and knowledge by dispensing information using Best Practices To Maintain Digital Wallet Security Implementation Of Cashless Payment This template helps you present information on five stages. You can also present information on Responsible Managers, Segregate Duties, Bank Statements using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Features Of Zero Trust Network Access Security Model Ppt File Files
Features Of Zero Trust Network Access Security Model Ppt File FilesThis slide represents the main features of ZTNA. The purpose of this slide is to showcase the various features of zero trust network access, including safeguarding private apps, connecting security controls to apps more closely, restriction of access, recognizing internal app use, and so on. Present the topic in a bit more detail with this Features Of Zero Trust Network Access Security Model Ppt File Files. Use it as a tool for discussion and navigation on Safeguards Private Apps, Features, Description. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agenda Implementing Strategies To Mitigate Cyber Security Threats
Agenda Implementing Strategies To Mitigate Cyber Security ThreatsIntroducing Agenda Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Security Awareness, Risk Management Process, Cyber Risk using this template. Grab it now to reap its full benefits.
-
 Allocate Team Roles And Responsibilities Implementing Strategies To Mitigate Cyber Security Threats
Allocate Team Roles And Responsibilities Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the key roles and responsibilities of cyber security team to enhance decision making and goal accomplishment. It includes activities such as developing information security strategies, managing security architecture, planning disaster recovery etc. Deliver an outstanding presentation on the topic using this Allocate Team Roles And Responsibilities Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Technical Directors, Team Leads, Engineers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Analyse And Rank Impact Of Cyber Threat Implementing Strategies To Mitigate Cyber Security Threats
Analyse And Rank Impact Of Cyber Threat Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Present the topic in a bit more detail with this Analyse And Rank Impact Of Cyber Threat Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Vulnerability, Threat, Threat Source This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Analyse Impact Of Cyber Attack On Valuable Implementing Strategies To Mitigate Cyber Security Threats
Analyse Impact Of Cyber Attack On Valuable Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the consequences of data breach threats to prevent information leakage. It mainly includes elements such as impact on revenue, protection cost, liability if lost, weightage criteria, asset importance etc. Deliver an outstanding presentation on the topic using this Analyse Impact Of Cyber Attack On Valuable Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Criteria, Impact On Revenue, Protection Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security Threats
Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates some activities to minimize the probability of cybercrimes within the organization. It includes elements such as utilizing anti virus, preventing to open suspicious emails, keeping systems up to date etc. Introducing Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Leverage Firewalls, Prevent Opening Suspicious Emails using this template. Grab it now to reap its full benefits.
-
 Build Cyber Security Team Structure Implementing Strategies To Mitigate Cyber Security Threats
Build Cyber Security Team Structure Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc Increase audience engagement and knowledge by dispensing information using Build Cyber Security Team Structure Implementing Strategies To Mitigate Cyber Security Threats This template helps you present information on four stages. You can also present information on Security Manager, Security Engineer, Security Analyst using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





