Powerpoint Templates and Google slides for Securitize
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Cyber Security Crime Prevention Icon
Cyber Security Crime Prevention IconIntroducing our Cyber Security Crime Prevention Icon set of slides. The topics discussed in these slides are Cyber Security, Crime Prevention Icon This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Security Crime Prevention Management Flowchart
Data Security Crime Prevention Management FlowchartThis slide depicts the internal data security crime prevention team. Its purpose is to understand duties of the heads to prevent internal crimes. This slide includes data security, technical security, crime prevention, security support, etc. Introducing our Data Security Crime Prevention Management Flowchart set of slides. The topics discussed in these slides are Security Director, Prevention Head, Security Support This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Risk Mitigation Methods Of Collaboration Tools
Cyber Security Risk Mitigation Methods Of Collaboration ToolsThe purpose of this slide is to highlight cyber security risk mitigation solutions of collaboration tools such as training employees on security awareness, contacting source, etc. Introducing our premium set of slides with Cyber Security Risk Mitigation Methods Of Collaboration Tools. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Simulate Phishing Tests, Verify Senders Identity, Use Official Channels . So download instantly and tailor it with your information.
-
 Security Risks Associated With Collaboration Tools
Security Risks Associated With Collaboration ToolsThis slide highlights security risks associated with collaboration tools such as phishing attacks, social engineering, data leakage and unsecure file sharing, etc. Presenting our set of slides with Security Risks Associated With Collaboration Tools. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Phishing Attacks, Social Engineering, Unrestricted Data Flow, Human Manipulation .
-
 Implement Security Systems Icon Using Operating System
Implement Security Systems Icon Using Operating SystemIntroducing our premium set of slides with Implement Security Systems Icon Using Operating System. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Implement Security, Systems Icon, Using Operating System. So download instantly and tailor it with your information.
-
 Secure Your Digital Assets Best Practices For The Security Of Crypto Wallets In Market
Secure Your Digital Assets Best Practices For The Security Of Crypto Wallets In MarketThis slide aims to highlight some broad security aspects of crypto wallets. This slide outlines the general security purposes such as passwords, 2FA accounts, phrases for secure passwords, secure hardware, keeping the seed phrase off devices as well, etc. Introducing Secure Your Digital Assets Best Practices For The Security Of Crypto Wallets In Market to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Security Of Crypto Wallets, Secure Hardware, Special Email Address, Complicated Passwords, using this template. Grab it now to reap its full benefits.
-
 Military IoT Devices Security Evaluation Framework Comprehensive Guide For Applications IoT SS
Military IoT Devices Security Evaluation Framework Comprehensive Guide For Applications IoT SSPresent the topic in a bit more detail with this Military IoT Devices Security Evaluation Framework Comprehensive Guide For Applications IoT SS. Use it as a tool for discussion and navigation on Devices Development Life Cycle, Purchase Process, Propose Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Measures To Protect Wireless Communication
Security Measures To Protect Wireless CommunicationThis slide shows wireless communication security measures for data protection which helps to ensure privacy and integrity of information over wireless networks. It further includes security measures such as wired equivalent privacy, Wi-Fi protected access etc. Presenting our well structured Security Measures To Protect Wireless Communication The topics discussed in this slide are Wired Equivalent, Protected Access, Wireless Networks This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
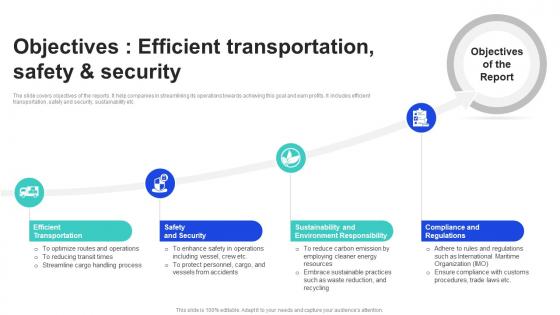 Objectives Efficient Transportation Safety And Security Shipping Industry Report Market Size IR SS
Objectives Efficient Transportation Safety And Security Shipping Industry Report Market Size IR SSThe slide covers objectives of the reports. It help companies in streamlining its operations towards achieving this goal and earn profits. It includes efficient transportation, safety and security, sustainability etc. Introducing Objectives Efficient Transportation Safety And Security Shipping Industry Report Market Size IR SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Efficient Transportation, Safety And Security, Sustainability And Environment Responsibility, using this template. Grab it now to reap its full benefits.
-
 Transforming From Traditional Ethical And Data Security Considerations For Digital Innovation DT SS
Transforming From Traditional Ethical And Data Security Considerations For Digital Innovation DT SSThis slide presents important ethical and legal considerations in the digital landscape. It mentions description, laws necessary for maintaining regulations including data privacy, cybersecurity and intellectual property. Introducing Transforming From Traditional Ethical And Data Security Considerations For Digital Innovation DT SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Data Privacy, Cybersecurity, Intellectual Property using this template. Grab it now to reap its full benefits.
-
 Checklist To Implement Data Breach Security Response Plan
Checklist To Implement Data Breach Security Response PlanThis slide depicts the checklist to execute response plans during data security breaches. The purpose of this checklist is to help the business ensure all suitable actions are implemented in order to prevent data leaks. It includes elements such as activity status, person responsible, etc. Presenting our well structured Checklist To Implement Data Breach Security Response Plan. The topics discussed in this slide are Isolate Affected Systems, Notify Appropriate Stakeholders, Identify The Nature. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
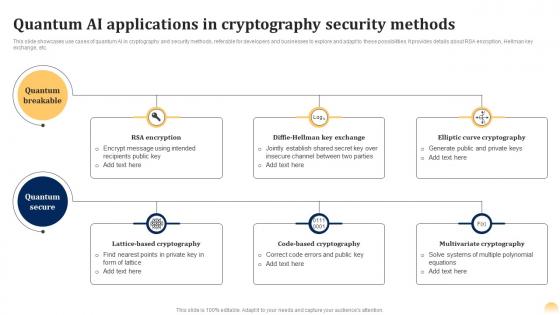 Quantum Cryptography Security Quantum Ai Fusing Quantum Computing With Intelligent Algorithms AI SS
Quantum Cryptography Security Quantum Ai Fusing Quantum Computing With Intelligent Algorithms AI SSThis slide showcases use cases of quantum AI in cryptography and security methods, referable for developers and businesses to explore and adapt to these possibilities. It provides details about RSA encryption, Hellman key exchange, etc. Present the topic in a bit more detail with this Quantum Cryptography Security Quantum Ai Fusing Quantum Computing With Intelligent Algorithms AI SS. Use it as a tool for discussion and navigation on Elliptic Curve Cryptography, Code Based Cryptography, Multivariate Cryptography. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS V
Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS VThe following slide depicts blockchain cybersecurity auditing checklist to minimize probability of frauds. It includes elements such as network, node, smart contract, security, consensus mechanism, data encryption, access management, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Adopt Security Auditing Checklist To Verify Processes BCT SS V Dispense information and present a thorough explanation of Consensus Mechanism, Smart Contract Security, Data Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threats In Blockchain Backing Up Data To Enhance Security And Efficiency BCT SS V
Cyber Threats In Blockchain Backing Up Data To Enhance Security And Efficiency BCT SS VThe following slide illustrates some methods to regularly backing up data to prevent primary data failures. It includes elements such as regularly backing up, offsite, automated backup and constantly monitoring, etc. Introducing Cyber Threats In Blockchain Backing Up Data To Enhance Security And Efficiency BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Regularly Backup, Automated Backup, Track Backup using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS V
Cyber Threats In Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS VThe following slide showcases comparative analysis of blockchain cybersecurity vendors. It includes elements such as experience, services, technical capabilities, response time, costing, offering competitive pricing, reviews, 247 availability, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Comparative Analysis Of Multiple Blockchain Security Vendors BCT SS V Dispense information and present a thorough explanation of Experience, Services, Technical Capabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
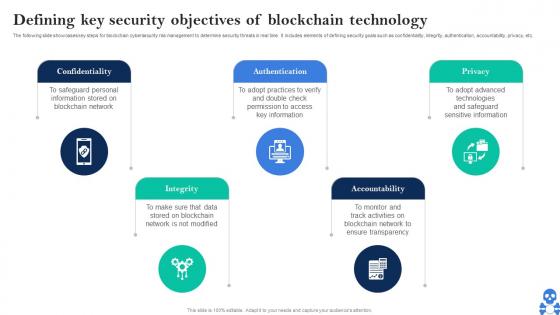 Cyber Threats In Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS V
Cyber Threats In Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS VThe following slide showcases key steps for blockchain cybersecurity risk management to determine security threats in real time. It includes elements of defining security goals such as confidentiality, integrity, authentication, accountability, privacy, etc. Introducing Cyber Threats In Blockchain Defining Key Security Objectives Of Blockchain Technology BCT SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Integrity, Authentication using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Methods To Ensure Smart Contract Security BCT SS V
Cyber Threats In Blockchain Methods To Ensure Smart Contract Security BCT SS VThe following slide showcases some tips and practices to ensure smart contract security. It includes elements such as careful rollouts, keeping them simple, updating and monitoring new developments, reviewing fundamental tradeoffs, etc. Introducing Cyber Threats In Blockchain Methods To Ensure Smart Contract Security BCT SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Careful Rollouts, Contracts Simple, Monitor New Advancements using this template. Grab it now to reap its full benefits.
-
 Data Security Strategies To Protect Retail Customer Digital Transformation Of Retail DT SS
Data Security Strategies To Protect Retail Customer Digital Transformation Of Retail DT SSThis slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness. Increase audience engagement and knowledge by dispensing information using Data Security Strategies To Protect Retail Customer Digital Transformation Of Retail DT SS This template helps you present information on six stages. You can also present information on Customer Data Protection, Online Transactions, Management Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Need For Implementing Data Security Across Retail Digital Transformation Of Retail DT SS
Overview Need For Implementing Data Security Across Retail Digital Transformation Of Retail DT SSThis slide analyses the need of implementing data security initiatives to address key customer data challenges in retail industry. It also mentions types of customer data collected such as account, location, browsing, and profile. Deliver an outstanding presentation on the topic using this Overview Need For Implementing Data Security Across Retail Digital Transformation Of Retail DT SS Dispense information and present a thorough explanation of Customer Trust, Sensitive Information, Balancing Personalization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Crypto Wallets Types And Applications Best Practices For The Security Of Crypto Wallets In Market
Crypto Wallets Types And Applications Best Practices For The Security Of Crypto Wallets In MarketThis slide aims to highlight some broad security aspects of crypto wallets. This slide outlines the general security purposes such as passwords, 2FA accounts, phrases for secure passwords, secure hardware, keeping the seed phrase off devices as well, etc. Deliver an outstanding presentation on the topic using this Crypto Wallets Types And Applications Best Practices For The Security Of Crypto Wallets In Market. Dispense information and present a thorough explanation of Storage Mechanism, Network, Crypto Wallets In Market, Multisignature Wallets using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Crypto Wallets Types And Applications Key Security Benefits Of Cryptography
Crypto Wallets Types And Applications Key Security Benefits Of CryptographyThis slide aims to highlight the advantages of cryptography in the market. This slide represents some benefits of crypto, such as access control, secure communication, protection against attacks, compliance with legal requirements, etc. Introducing Crypto Wallets Types And Applications Key Security Benefits Of Cryptography to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Protection Against Attacks, Compliance With Legal Requirements, Secure Communication, using this template. Grab it now to reap its full benefits.
-
 Components Of 5G Security Architecture To Prevent Cyberattacks
Components Of 5G Security Architecture To Prevent CyberattacksThis slide depicts the components of a 5 G security architecture utilized for preventing cyber attacks. The purpose of this slide is to help the business safeguard its networks through proper implementation of critical components such as network security, scaling security, etc. Presenting our set of slides with Components Of 5G Security Architecture To Prevent Cyberattacks. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network, Hardware, Security.
-
 HR Offboarding Process Mapping To Mitigate Security Risks
HR Offboarding Process Mapping To Mitigate Security RisksThis slide represents HR offboarding process mapping to mitigate security risks. It further includes manager request, replacement, job vacancy, preparation of resignation letter and health check, etc. Presenting our well structured HR Offboarding Process Mapping To Mitigate Security Risks. The topics discussed in this slide are Resignation, Documentation, Termination. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Considered Liquid Security Must In Powerpoint And Google Slides Cpb
Considered Liquid Security Must In Powerpoint And Google Slides CpbPresenting our Considered Liquid Security Must In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Considered Liquid Security Must. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Discord Security Issues In Powerpoint And Google Slides Cpb
Discord Security Issues In Powerpoint And Google Slides CpbPresenting Discord Security Issues In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Discord Security Issues. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Build Cyber Security Team Structure Implementing Cyber Risk Management Process
Build Cyber Security Team Structure Implementing Cyber Risk Management ProcessThe following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc. Deliver an outstanding presentation on the topic using this Build Cyber Security Team Structure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Security Analyst, Security Manager, Chief Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management Process
Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management ProcessThe following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Introducing Cyber Security Awareness Facts And Statistics Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Social Engineering, Data Breaches, Mobile Malware Attacks, using this template. Grab it now to reap its full benefits.
-
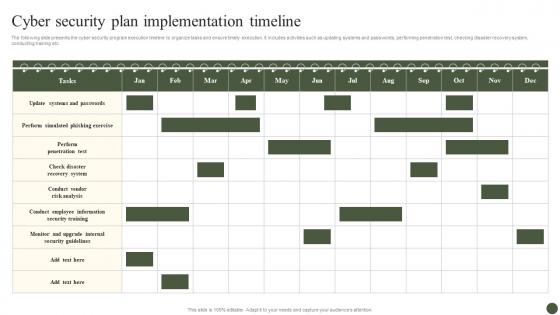 Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process
Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management ProcessThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Present the topic in a bit more detail with this Cyber Security Plan Implementation Timeline Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Security Plan, Implementation Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management Process
Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management ProcessThe following slide depicts some figures to analyse the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Increase audience engagement and knowledge by dispensing information using Data Highlighting Cyber Security Unawareness Among Implementing Cyber Risk Management Process. This template helps you present information on five stages. You can also present information on Malware Infection, Systems With Passwords, Employees Feels, Allow Official Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process
Determine Cyber Security Risks And Threats Implementing Cyber Risk Management ProcessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Objectives, Issue Identifier. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Global Cyber Security Trend Analysis Implementing Cyber Risk Management Process
Global Cyber Security Trend Analysis Implementing Cyber Risk Management ProcessThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber-attacks etc. Introducing Global Cyber Security Trend Analysis Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Businesses Targeted, Ransomware Attack, Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management Process
Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management ProcessThe following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Present the topic in a bit more detail with this Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Attack Type, Remarks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process
Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management ProcessThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions. Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Background Check using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management Process
KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management ProcessThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Before, After. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management Process
Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management ProcessThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Present the topic in a bit more detail with this Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Target Audience, Trainer Name, Mode. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management Process
Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management ProcessThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Present the topic in a bit more detail with this Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Rare, Unlikely, Possible. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process
Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management ProcessThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Parameters, Tasks, Status, Reviews. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process
Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management ProcessThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Deliver an outstanding presentation on the topic using this Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Features, Free Trial, Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Risk Management Training Program
Information Security And Risk Management Training ProgramThis slide showcases the successful information security and risk management training outline. It include details such as threats and vulnerabilities, etc. Presenting our well structured Information Security And Risk Management Training Program. The topics discussed in this slide are Training, Vulnerabilities, Information. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Implementing Byod Policy To Enhance Develop Security Policies For Data Protection
Implementing Byod Policy To Enhance Develop Security Policies For Data ProtectionThis slide shows major data protection policies for handling sensitive data of corporate. It include policies such as device security, network and data handling, etc. Introducing Implementing Byod Policy To Enhance Develop Security Policies For Data Protection to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Network Security, Data Handling, Device Security, Data Protection, using this template. Grab it now to reap its full benefits.
-
 Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod Policy
Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod PolicyThis slide shows essential considerations for protecting crucial data of company in organization. It include security areas such as device security, network security and software updates, etc. Increase audience engagement and knowledge by dispensing information using Implementing Byod Policy To Enhance Security Considerations For Data Protection Under Byod Policy. This template helps you present information on five stages. You can also present information on Device Security, Mobile Device Management, Network Security, Malware Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices For Healthcare Iot Security How Iomt Is Transforming Medical Industry IoT SS V
Best Practices For Healthcare Iot Security How Iomt Is Transforming Medical Industry IoT SS VFollowing slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc. Present the topic in a bit more detail with this Best Practices For Healthcare Iot Security How Iomt Is Transforming Medical Industry IoT SS V. Use it as a tool for discussion and navigation on Attack Surface Visibility, Segregated Internal Networking, Zero Trust Approach. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ransomware In Digital Age How To Enhance Supply Chain Security Against Ransomware
Ransomware In Digital Age How To Enhance Supply Chain Security Against RansomwareThis slide examines how to strengthen Supply Chain security against ransomware by implementing measures such as multi-factor authentication, regular patching, and updates. This slide also represents the essential factors that an organization should always consider, such as employee training, incident response plan, and regular security audits. Deliver an outstanding presentation on the topic using this Ransomware In Digital Age How To Enhance Supply Chain Security Against Ransomware. Dispense information and present a thorough explanation of Secure Communication Channels, Important Factors In Consideration, Regular Patching And Updates, Data Backup And Recovery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ransomware In Digital Age Ransomware Prevention Checklist For Security Teams
Ransomware In Digital Age Ransomware Prevention Checklist For Security TeamsThis slide represents the current status of ransomware prevention measures in an organization. The purpose of this slide is to showcase the status of different security measures such as data backups, antivirus software upgradation, network segmentation, etc. Present the topic in a bit more detail with this Ransomware In Digital Age Ransomware Prevention Checklist For Security Teams. Use it as a tool for discussion and navigation on Email Protection, Vulnerability Scanning And Patching, Backup Testing And Data Restoration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ransomware In Digital Age Strengthening Supply Chain Security Against Ransomware
Ransomware In Digital Age Strengthening Supply Chain Security Against RansomwareThis slide examines how to strengthen supply chain security against ransomware by implementing crucial measures, including vendor assessment, secure communication channels, multi-factor authentication, and regular patching and updates. These steps are vital in mitigating the risk of ransomware attacks and safeguarding the integrity of the supply chain. Introducing Ransomware In Digital Age Strengthening Supply Chain Security Against Ransomware to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Supply Chain Framework, Incident Response Plan, Regular Security Audits, Data Backup And Recovery, using this template. Grab it now to reap its full benefits.
-
 Advantages Of SAP Cyber Security To Safeguard Company Networks
Advantages Of SAP Cyber Security To Safeguard Company NetworksThis slide highlights the advantages of SAP cybersecurity to safeguard company networks. The purpose of this template is to help the company leverage SAP cybersecurity to prevent malware infections. It includes advantages such as identification of risks and vulnerabilities, protection of application data, etc. Presenting our set of slides with Advantages Of SAP Cyber Security To Safeguard Company Networks. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify Risks And Vulnerabilities, Protect Application Data, Identify Anomalies.
-
 Elements Of Systems Applications And Products Cyber Security
Elements Of Systems Applications And Products Cyber SecurityThis slide depicts the components of SAP cybersecurity. The purpose of this template is to help understand the areas of business networks that can be safeguarded with the help of SAP cybersecurity elements. It includes data base security, infrastructure security, etc. Presenting our set of slides with Elements Of Systems Applications And Products Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Database Security, Operating System Security, Network Security, Infrastructure Security.
-
 Information Security And Trust Model Under SAP
Information Security And Trust Model Under SAPThis template depicts the data security and trust model under SAP. The purpose of this slide is to help the business ensure it protects its network and data through the implementation of information security and trust models. It includes elements such as audits and compliance, business resilience, etc. Presenting our set of slides with Information Security And Trust Model Under SAP. This exhibits information on seven stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Governance Policies, Audits And Compliance, Business Resilience.
-
 Product Services Offered By SAP Security Solutions
Product Services Offered By SAP Security SolutionsThis template showcases the SAP product services offered by the organization. The purpose of this slide is to help the business ensure it utilizes suitable services in order to meet its business needs. It includes services such as SAP cloud identity access governance, SAP enterprise detection, etc. Introducing our premium set of slides with Product Services Offered By SAP Security Solutio. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like SAPenterprise Detections, SAP Data Custodian, Streamlining Governance Procedures. So download instantly and tailor it with your information.
-
 SAP Security Measures To Prevent Cyber Attacks
SAP Security Measures To Prevent Cyber AttacksPresenting our set of slides with SAP Security Measures To Prevent Cyber Attacks. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on SAP Security, Measures To Prevent, Cyber Attacks.
-
 Techniques Employed Under SAP Cyber Security To Safeguard Company Networks
Techniques Employed Under SAP Cyber Security To Safeguard Company NetworksThis slide showcases the strategies employed under SAP cybersecurity to secure company networks. The purpose of this template is to help the business implement SAP cybersecurity measures through the use of techniques such as roles and authorizations, patch management, etc. Introducing our premium set of slides with Techniques Employed Under SAP Cyber Security To Safeguard Company Networks. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Roles And Authorizations, Patch Management, Transaction Monitoring. So download instantly and tailor it with your information.
-
 Use Cases Of System Application And Product Cyber Security
Use Cases Of System Application And Product Cyber SecurityThis template depicts the applications of SAP cyber security. The purpose of this slide is to help the business leverage SAP cybersecurity to improve its internal network safety. It includes use cases such as ensuring data integrity, identification of unauthorized access, etc. Presenting our well structured Use Cases Of System Application And Product Cyber Security. The topics discussed in this slide are Prevent Exploitation And Fraud, Ensuring Data Integrity, Continuous Results. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Benefits Of Cloud Access Security Broker 2 0 Next Generation CASB
Benefits Of Cloud Access Security Broker 2 0 Next Generation CASBThis slide represents the advantages of cloud access security broker version 2.0. The purpose of this slide is to highlight the main benefits of CASB 2.0, including comprehensive coverage, cost-effectiveness, enhanced security efficacy, improved visibility, app database, and so on. Introducing Benefits Of Cloud Access Security Broker 2 0 Next Generation CASB to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Comprehensive Coverage, Cost Effective, Improved Visibility using this template. Grab it now to reap its full benefits.
-
 Benefits Of Cloud Access Security Broker Next Generation CASB
Benefits Of Cloud Access Security Broker Next Generation CASBThis slide outlines the different advantages of cloud access security broker technology. This slide highlights the pros of CASB technology, including risk visibility, cyber threat prevention, granular cloud usage control, shadow IT assessment and management, DLP, managing privileged accounts and admin and controlled data sharing. Present the topic in a bit more detail with this Benefits Of Cloud Access Security Broker Next Generation CASB Use it as a tool for discussion and navigation on Risk Visibility, Threat Prevention, Assessment And Management This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices To Implement Cloud Access Security Broker Next Generation CASB
Best Practices To Implement Cloud Access Security Broker Next Generation CASBThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this Best Practices To Implement Cloud Access Security Broker Next Generation CASB Dispense information and present a thorough explanation of Build Visibility, Forecast Risk, Release CASB, Best Practices using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Adopt A Cloud Access Security Broker Next Generation CASB
Checklist To Adopt A Cloud Access Security Broker Next Generation CASBThis slide represents the main points to consider before adopting a cloud access security broker. The purpose of this slide is to showcase the key measures that organizations should keep in mind before choosing a CASB solution and the measures include conducting the trial, outlining CASB roles, and so on. Deliver an outstanding presentation on the topic using this Checklist To Adopt A Cloud Access Security Broker Next Generation CASB Dispense information and present a thorough explanation of Vendor Landscape, Conduct A Trial, Functionalities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker And Encryption Next Generation CASB
Cloud Access Security Broker And Encryption Next Generation CASBThis slide describes the improved encryption with CASB version 2.0. The purpose of this slide is to showcase the various encryption features of cloud access security broker version 2.0, including security that follows the data, content access that can be revoked at any time, and multi-platform compatibility. Present the topic in a bit more detail with this Cloud Access Security Broker And Encryption Next Generation CASB Use it as a tool for discussion and navigation on Security That Tracks Data, Terminated Moment, Content Access This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker And Secure Web Gateway Next Generation CASB
Cloud Access Security Broker And Secure Web Gateway Next Generation CASBThis slide represents how CASB 2.0 not just discovers the shadow IT but helps to control it too. The purpose of this slide is to showcase how CASB 2.0 improves the SWG model by empowering it with rich cloud app data, getting dynamic control of shadow IT and simplifying deployment. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker And Secure Web Gateway Next Generation CASB Dispense information and present a thorough explanation of Cloud App Data, Get Dynamic Control, Simplify Deployment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Access Security Broker And User Authentication Next Generation CASB
Cloud Access Security Broker And User Authentication Next Generation CASBThis slide represents the improved user authentication method in cloud access security broker version 2.0. The purpose of this slide is to showcase how the user authentication process can be enhanced by integrating CASB 2.0. Present the topic in a bit more detail with this Cloud Access Security Broker And User Authentication Next Generation CASB Use it as a tool for discussion and navigation on Cloud Apps, Transaction Detail, User Threat Data This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Access Security Broker Architectural Components Next Generation CASB
Cloud Access Security Broker Architectural Components Next Generation CASBThis slide outlines the main components of cloud access security broker architecture. The purpose of this slide is to showcase the primary elements of CASB architecture, including immediate enterprise core, secondary enterprise core, PaaS, IaaS, PaaS, connectivity gateway, and so on. Deliver an outstanding presentation on the topic using this Cloud Access Security Broker Architectural Components Next Generation CASB Dispense information and present a thorough explanation of Secondary Enterprise Core, Platform As A Service, Connectivity Gateway using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





