Powerpoint Templates and Google slides for Securitize
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Classify Assets Vulnerable To Cyber Attack Implementing Strategies To Mitigate Cyber Security Threats
Classify Assets Vulnerable To Cyber Attack Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts some major assets that are more prone to cyber attack. It mainly includes elements such as sales record, sales lead record, company internal database, customer and product information etc. Present the topic in a bit more detail with this Classify Assets Vulnerable To Cyber Attack Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Sales Record, Customer Database, Product Database This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats
Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates checklist to evaluate third party risk assessment to eliminate unnecessary threats. It includes elements such as cyber security policies, patch management process, physical security guidelines, information safety etc. Deliver an outstanding presentation on the topic using this Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Parameters, Response, Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Incident Escalation Response Flowchart Implementing Strategies To Mitigate Cyber Security Threats
Cyber Incident Escalation Response Flowchart Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the incident response chart to determine actions to be taken to escalate issue and manage security. It includes elements such as incident identification, informing security team, performing initial analysis, communicating to key members etc. Deliver an outstanding presentation on the topic using this Cyber Incident Escalation Response Flowchart Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Incident Identified, Initial Assessment, Classify Incident using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Awareness Facts And Statistics Implementing Strategies To Mitigate Cyber Security Threats
Cyber Security Awareness Facts And Statistics Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases some facts and figures to generate awareness about cyber crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc Introducing Cyber Security Awareness Facts And Statistics Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Malware Attacks, Employees, Social Engineering Attacks using this template. Grab it now to reap its full benefits.
-
 Cyber Security Plan Implementation Timeline Implementing Strategies To Mitigate Cyber Security Threats
Cyber Security Plan Implementation Timeline Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Plan Implementation Timeline Implementing Strategies To Mitigate Cyber Security Threats This template helps you present information on one stages. You can also present information on Update Systems And Passwords, Perform Simulated Phishing Exercise, Perform Penetration Test using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security Threats
Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Deliver an outstanding presentation on the topic using this Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Malware, Phishing, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Develop RACI Chart For Team Collaboration Implementing Strategies To Mitigate Cyber Security Threats
Develop RACI Chart For Team Collaboration Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the RACI accountable, consulted, responsible, informed plan to facilitate and ensure speedy communication during cyber issue management. It includes activities such as overall coordination, media messaging, internal communication, technical assistance etc. Present the topic in a bit more detail with this Develop RACI Chart For Team Collaboration Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Accountable, Consulted, Responsible This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Encrypt And Create Backup Of Useful Data Implementing Strategies To Mitigate Cyber Security Threats
Encrypt And Create Backup Of Useful Data Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates various methods to encrypt and back up key data to avoid information loss and improved accessibility. It includes elements such as network attached storage, cloud storage services, flat backup system, details, advantages, disadvantages, cost, Deliver an outstanding presentation on the topic using this Encrypt And Create Backup Of Useful Data Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Network Attached Storage, Cloud Storage Services, Flat Backup System using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Global Cyber Security Trend Analysis Implementing Strategies To Mitigate Cyber Security Threats
Global Cyber Security Trend Analysis Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber attacks etc. Increase audience engagement and knowledge by dispensing information using Global Cyber Security Trend Analysis Implementing Strategies To Mitigate Cyber Security Threats This template helps you present information on six stages. You can also present information on Attack, Data Breaches, Cyber Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide Implementing Strategies To Mitigate Cyber Security Threats
Icons Slide Implementing Strategies To Mitigate Cyber Security ThreatsIntroducing our well researched set of slides titled Icons Slide Implementing Strategies To Mitigate Cyber Security Threats It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber Security
Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber SecurityThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Deliver an outstanding presentation on the topic using this Identify Threat And Vulnerabilities Within Information System Implementing Strategies To Mitigate Cyber Security Dispense information and present a thorough explanation of Vulnerability, Threat, Threat Source using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security Threats
Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the negative impact of cyber crimes on business to build control actions and strategies. It includes key elements such as rising costs, reputational damage, operational disruption, loss of revenue etc. Introducing Identifying Impact Of Cyber Attack On Business Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Rising Cost, Reputational Damage, Operational Disruption using this template. Grab it now to reap its full benefits.
-
 Impact Of Cyber Safety Security Measures Implementing Strategies To Mitigate Cyber Security Threats
Impact Of Cyber Safety Security Measures Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies Present the topic in a bit more detail with this Impact Of Cyber Safety Security Measures Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Cyber Attack Type, Malware, Ransomware This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Security Policies And Practices Implementing Strategies To Mitigate Cyber Security Threats
Impact Of Cyber Security Policies And Practices Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Policies And Practices Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Background Check using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Implement Automated Patch Management Solution Implementing Strategies To Mitigate Cyber Security Threats
Implement Automated Patch Management Solution Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the automated patch management process to fix software vulnerabilities and ensure smooth functioning of systems. It includes activities such as scanning of systems, requesting to take back up etc. Present the topic in a bit more detail with this Implement Automated Patch Management Solution Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Vulnerability Assessment, Request Cancelled, Asset Inventory This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Implementing Strategies To Mitigate Cyber Security Threats Table Of Content
Implementing Strategies To Mitigate Cyber Security Threats Table Of ContentIncrease audience engagement and knowledge by dispensing information using Implementing Strategies To Mitigate Cyber Security Threats Table Of Content This template helps you present information on one stages. You can also present information on Cyber Security, Cyber Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security Threats
KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Level Of Preparedness, Mean Time To Detect, Mean Time To Resolve This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Leverage Strong And Complex Password Management Implementing Strategies To Mitigate Cyber Security Threats
Leverage Strong And Complex Password Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates some practices to ensure strong password management and restrict access to data. It includes activities such as avoiding weak passwords, encryption, multi factor authentication, conducting test etc. Introducing Leverage Strong And Complex Password Management Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Conduct Password Test, Password Encryption, Multi Factor Authentication using this template. Grab it now to reap its full benefits.
-
 Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats
Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Present the topic in a bit more detail with this Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Information Security And Privacy, Physical Assets And Data Security, Web Application Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organize Cyber Security Training For Employees Implementing Strategies To Mitigate Cyber Security Threats
Organize Cyber Security Training For Employees Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Deliver an outstanding presentation on the topic using this Organize Cyber Security Training For Employees Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Document Management, Target Audience, Proposed Date using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Plan Useful Data Backup Schedule Implementing Strategies To Mitigate Cyber Security Threats
Plan Useful Data Backup Schedule Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the monthly calendar for data backup to advance cybersecurity protection and loss of information. It mainly includes techniques such as fully and incremental data backup etc. Increase audience engagement and knowledge by dispensing information using Plan Useful Data Backup Schedule Implementing Strategies To Mitigate Cyber Security Threats This template helps you present information on one stages. You can also present information on Time Consuming Process, Speedy Process, Incremental Backup using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security Threats
Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases various methods to review cyber risks to determine probability and impact of risks. It includes elements such as penetration, red team and risk based testing along with objectives, features, cost, outcomes, duration etc. Present the topic in a bit more detail with this Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Objectives, Features, Duration This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Select Cybersecurity Training Program Courses Implementing Strategies To Mitigate Cyber Security Threats
Select Cybersecurity Training Program Courses Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the best cybersecurity training courses to educate employees and minimize the possibility of cyber attacks. It includes cloud, disaster recovery, hardware, information security programs, duration, mode and cost Deliver an outstanding presentation on the topic using this Select Cybersecurity Training Program Courses Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Cloud Security, Information Security, Disaster Recovery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Select Tools To Reduce Cyber Security Failure Implementing Strategies To Mitigate Cyber Security Threats
Select Tools To Reduce Cyber Security Failure Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Present the topic in a bit more detail with this Select Tools To Reduce Cyber Security Failure Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Features, Free Trial, Cost This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Implementing Strategies To Mitigate Cyber Security Threats
Table Of Contents Implementing Strategies To Mitigate Cyber Security ThreatsIncrease audience engagement and knowledge by dispensing information using Table Of Contents Implementing Strategies To Mitigate Cyber Security Threats This template helps you present information on one stages. You can also present information on Industry Overview, Current Scenario Analysis, Cyber Security Plan using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Types Of Cyber Attacks Encountered By Employees Implementing Strategies To Mitigate Cyber Security Threats
Types Of Cyber Attacks Encountered By Employees Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the various types of cyber attacks faced by staff to determine and formulate action plan. It includes elements such as malware, ransomware, man in the middle, phishing, denial of service tec. Introducing Types Of Cyber Attacks Encountered By Employees Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Malware, Ransomware, Phishing using this template. Grab it now to reap its full benefits.
-
 Hypervisor security considerations to maintain virtualized environment
Hypervisor security considerations to maintain virtualized environmentThis slide covers security considerations for hypervisor such as hypervisor vulnerabilities, access control, network security etc. to manage virtualization process.Presenting our set of slides with Hypervisor security considerations to maintain virtualized environment This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Hypervisor Vulnerabilities, Secure Management Interfaces, Network Security.
-
 Aerospace Big Data Security Metrics Checklist
Aerospace Big Data Security Metrics ChecklistThis slide represents checklist for security metrics of aerospace big data. It aims to help organization to effectively engage with different departments of organization by determining risk and threats. It includes various elements such as risks signed off, adequate resolution of internal compliance, etc. Presenting our set of slides with Aerospace Big Data Security Metrics Checklist. This exhibits information on nine stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Risks Signed Off, Post Awareness Initiatives, Security Occurrences.
-
 Cyber Hazard Mitigation Plan For Data Security
Cyber Hazard Mitigation Plan For Data SecurityThis slide represents hazard mitigation plan to enhance cybersecurity and data protection including risks such as malware, phishing attack, and DDoS attack. Presenting our well structured Cyber Hazard Mitigation Plan For Data Security. The topics discussed in this slide are Malware, Phishing Attack, Ddos Attack. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Network Virtualization Icon To Enhance Data Security
Network Virtualization Icon To Enhance Data SecurityIntroducing our Network Virtualization Icon To Enhance Data Security set of slides. The topics discussed in these slides are Network Virtualization, Data Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Technology Project Goals Icon To Strength Data Security
Technology Project Goals Icon To Strength Data SecurityPresenting our set of slides with Technology Project Goals Icon To Strength Data Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Technology, Goals, Strength.
-
 Impact Of Patch Management On IT Security
Impact Of Patch Management On IT SecurityThis slide shows multiple potential results of deploying a patch management process in an organization. It includes regular security updates, feature updates, bug fixes, and prioritization. Presenting our set of slides with name Impact Of Patch Management On IT Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Updates, Features Updates, Bug Fixes.
-
 Industry Leading Crypto Ledger Security Insights
Industry Leading Crypto Ledger Security InsightsThis slide presents industrial insights regarding security features provided by crypto ledgers for securing digital currencies. Introducing Industry Leading Crypto Ledger Security Insights to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Cybersecurity Certification, Customized Operating System, Integrated Chip, using this template. Grab it now to reap its full benefits.
-
 Key Components Of Crypto Ledger Security Model
Key Components Of Crypto Ledger Security ModelThis template aims to cover core elements of crypto ledger security model for asset protection. It covers elements such as offline storage, security, trusted display, etc. Deliver an outstanding presentation on the topic using this Key Components Of Crypto Ledger Security Model. Dispense information and present a thorough explanation of Offline Storage, Security, Trusted Display using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Best Practices For Healthcare IoT Security Comprehensive Guide To Networks IoT SS
Best Practices For Healthcare IoT Security Comprehensive Guide To Networks IoT SSFollowing slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc. Deliver an outstanding presentation on the topic using this Best Practices For Healthcare IoT Security Comprehensive Guide To Networks IoT SS. Dispense information and present a thorough explanation of Attack Surface Visibility, Segregated Internal Networking, Zero Trust Approach using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mobile POS Security Concerns For Retailers
Mobile POS Security Concerns For RetailersThe purpose of this slide is to highlight security risks hindering transactions and safety of customer data including concerns such as unauthorized access to POS application, malware targeting POS application, etc. Increase audience engagement and knowledge by dispensing information using Mobile POS Security Concerns For Retailers. This template helps you present information on three stages. You can also present information on Unauthorized Access, Malware Targeting POS, Cyberattacks Against Backend System using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Practices Of SaaS Security Risk Management
Best Practices Of SaaS Security Risk ManagementThis slide showcases the practices of SaaS security risk management. Its purpose is to protect critical workloads to ensure compliance. This slide includes vulnerability identification, analysis, risk assessment and remediation. Introducing Best Practices Of SaaS Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability Identification, Remediation, Risk Assessment, Analysis, using this template. Grab it now to reap its full benefits.
-
 Cloud Cyber Security SaaS Risk Management
Cloud Cyber Security SaaS Risk ManagementThis slide showcases the cloud cyber security SaaS risk management. Its aim is to control profile and manage the risk involved. This slide includes authorization, monitor, cloud based, continuously monitor, etc. Introducing Cloud Cyber Security SaaS Risk Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Control Profiles, Cloud Security Risk Management, Security Categorization, using this template. Grab it now to reap its full benefits.
-
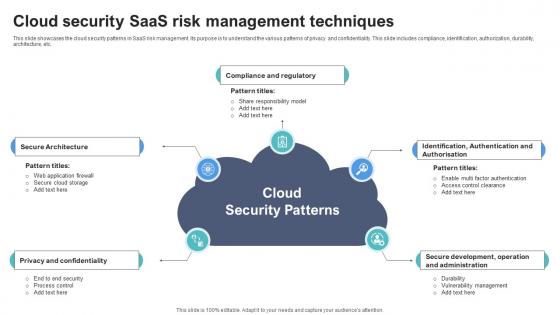 Cloud Security SaaS Risk Management Techniques
Cloud Security SaaS Risk Management TechniquesThis slide showcases the cloud security patterns in SaaS risk management. Its purpose is to understand the various patterns of privacy and confidentiality. This slide includes compliance, identification, authorization, durability, architecture, etc. Introducing Cloud Security SaaS Risk Management Techniques to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Secure Architecture, Privacy And Confidentiality, Cloud Security Patterns, Compliance And Regulatory, using this template. Grab it now to reap its full benefits.
-
 Principles Of SaaS Security Risk Management
Principles Of SaaS Security Risk ManagementThis slide showcases the principles of SaaS risk based security management. Its aim is to secure infrastructure for assessing risk. This slide includes network control, VM management, data protection, incident, reliability, access management, etc. Present the topic in a bit more detail with this Principles Of SaaS Security Risk Management. Use it as a tool for discussion and navigation on Access Management, Network Control, Perimeter Network Control. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
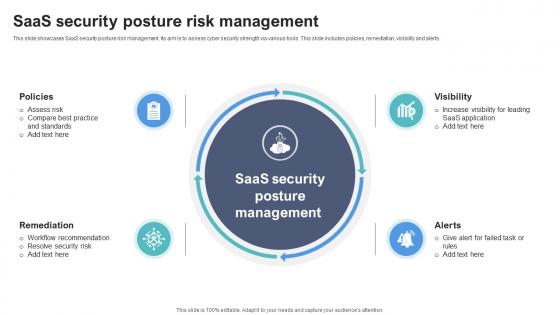 SaaS Security Posture Risk Management
SaaS Security Posture Risk ManagementThis slide showcases SaaS security posture risk management. Its aim is to assess cyber security strength via various tools. This slide includes policies, remediation, visibility and alerts. Increase audience engagement and knowledge by dispensing information using SaaS Security Posture Risk Management. This template helps you present information on four stages. You can also present information on Visibility, Policies, Remediation, Alerts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
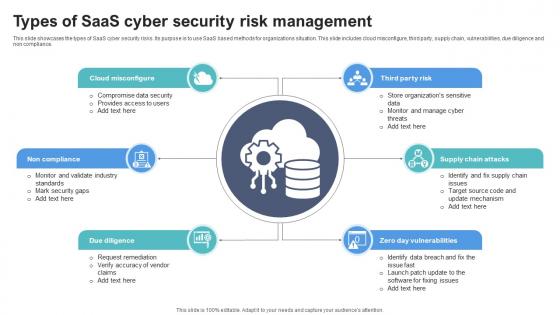 Types Of SaaS Cyber Security Risk Management
Types Of SaaS Cyber Security Risk ManagementThis slide showcases the types of SaaS cyber security risks. Its purpose is to use SaaS based methods for organizations situation. This slide includes cloud misconfigure, third party, supply chain, vulnerabilities, due diligence and non compliance. Increase audience engagement and knowledge by dispensing information using Types Of SaaS Cyber Security Risk Management. This template helps you present information on six stages. You can also present information on Supply Chain Attacks, Zero Day Vulnerabilities, Due Diligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Vehicular Ad Hoc Network Security
Vehicular Ad Hoc Network SecurityThis slide focuses on important points such as keeping information private, making sure data is real, verifying who sends it, delivering it on time, and being eco-friendly i networks. It helps make the network safer and more efficient. Deliver an outstanding presentation on the topic using this Vehicular Ad Hoc Network Security. Dispense information and present a thorough explanation of Data Authenticity, Authenticated Senders, Timely Delivery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Firewall Security Icon Protecting From Cyber Threats
Firewall Security Icon Protecting From Cyber ThreatsIntroducing our Firewall Security Icon Protecting From Cyber Threats set of slides. The topics discussed in these slides are Firewall Security, Protecting. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Architecture Of Cyber Security Monitoring
Architecture Of Cyber Security MonitoringFollowing slide showcases cyber security monitoring architecture for enhanced incident investigation. It further covers monitoring servers, wireless connections, web applications, web server, network monitoring, firewall configuration and allowed or blocked connections etc. Presenting our set of slides with Architecture Of Cyber Security Monitoring This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Firewall Configurations, Network Monitoring, Web Server.
-
 Cyber Security Monitoring Framework In Organization
Cyber Security Monitoring Framework In OrganizationFollowing slide showcases organization framework of cyber security monitoring for improved network protection posture. It further covers identify, protect, detect, respond and recover, etc. Presenting our set of slides with Cyber Security Monitoring Framework In Organization This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Recovery Planning, Responsive Planning, Business Environment.
-
 Monitoring Computer Safety Lock Icon For Cyber Security
Monitoring Computer Safety Lock Icon For Cyber SecurityPresenting our set of slides with Monitoring Computer Safety Lock Icon For Cyber Security This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Monitoring Computer Safety, Cyber Security.
-
 Monitoring Cyber Risk Icon For Computer Security
Monitoring Cyber Risk Icon For Computer SecurityIntroducing our premium set of slides with Monitoring Cyber Risk Icon For Computer Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Monitoring Cyber Risk, Computer Security. So download instantly and tailor it with your information.
-
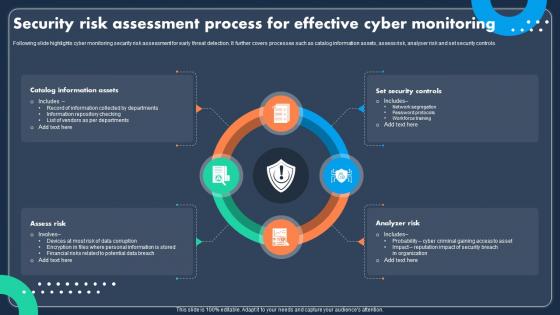 Security Risk Assessment Process For Effective Cyber Monitoring
Security Risk Assessment Process For Effective Cyber MonitoringFollowing slide highlights cyber monitoring security risk assessment for early threat detection. It further covers processes such as catalog information assets, assess risk, analyser risk and set security controls. Introducing our premium set of slides with Security Risk Assessment Process For Effective Cyber Monitoring Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Assets, Security Controls, Analyzer Risk. So download instantly and tailor it with your information.
-
 Emerging Encryption Trends For Enhancing Data Security
Emerging Encryption Trends For Enhancing Data SecurityThis slide represents latest trends in encryption which assists to scramble data into a secret code which can be unlocked with unique digital key. It includes latest trends in encryption such as homomorphic encryption, quantum encryption, etc. Presenting our set of slides with name Emerging Encryption Trends For Enhancing Data Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Quantum Cryptography, Homomorphic Encryption, Moving Target Defense.
-
 Endpoint Encryption Architecture For Comprehensive Security
Endpoint Encryption Architecture For Comprehensive SecurityThis slide represents architecture of endpoint encryption which assists to provide advance levels of security to valuable corporate data and make it unreadable to unauthorised users. It includes endpoint architecture components such as server, database, manager, etc. Introducing our premium set of slides with name Endpoint Encryption Architecture For Comprehensive Security. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Endpoint Encryption Server, Endpoint Database, Security Center. So download instantly and tailor it with your information.
-
 Best Practices To Maintain Digital Wallet Security Improve Transaction Speed By Leveraging
Best Practices To Maintain Digital Wallet Security Improve Transaction Speed By LeveragingMentioned slide exhibits various best practices which can be implemented by followed by businesses to secure e wallets. It includes best practices such as enable passwords, secure network connections, install reliable applications, secure login credentials, and keep personal data private. Introducing Best Practices To Maintain Digital Wallet Security Improve Transaction Speed By Leveraging to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Secure Network Connection, Secure Login Credentials, Keep Personal Data Private using this template. Grab it now to reap its full benefits.
-
 Containerization Technology Container Security Essentials To Manage Risks
Containerization Technology Container Security Essentials To Manage RisksThis slide represents the various important factors of container security to manage environmental risks. The purpose of this slide is to outline the essentials of container security to manage risks, such as configuration, automation, container security solutions, and cloud and network security. Present the topic in a bit more detail with this Containerization Technology Container Security Essentials To Manage Risks. Use it as a tool for discussion and navigation on Dashboard To Retrieve Ongoing, Time Series Data Metrics, Containers Operating,Container Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Containerization Technology Security Best Practices To Protect Containerized Environments
Containerization Technology Security Best Practices To Protect Containerized EnvironmentsThis slide outlines the best practices for securing containerized environments. The purpose of this slide is to define the security best practices for organizations to protect containerized environments, and these are securing images, securing registries, securing deployments, and so on. Deliver an outstanding presentation on the topic using this Containerization Technology Security Best Practices To Protect Containerized Environments. Dispense information and present a thorough explanation of Securing Registries, Securing Deployment, Securing Container Runtime, Securing Kubernetes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Business Model Smart Farming Technology Pitch Deck For Food Security
Business Model Smart Farming Technology Pitch Deck For Food SecurityFollowing slide showcases business and operational model of company. It includes elements such as key partners, resources, channels, value preposition, customer relationships, segments etc. Deliver an outstanding presentation on the topic using this Business Model Smart Farming Technology Pitch Deck For Food Security Dispense information and present a thorough explanation of Value Propositions, Customer Relationship, Customer Segments using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Client Testimonials Smart Farming Technology Pitch Deck For Food Security
Client Testimonials Smart Farming Technology Pitch Deck For Food SecurityFollowing slide exhibits customer reviews and testimonials about company services. It includes viewpoints of happy clients such as Nurwali, James and Ryan. Increase audience engagement and knowledge by dispensing information using Client Testimonials Smart Farming Technology Pitch Deck For Food Security This template helps you present information on Three stages. You can also present information on Develop Better Surroundings, Sustainable Practices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Company Introduction Smart Farming Technology Pitch Deck For Food Security
Company Introduction Smart Farming Technology Pitch Deck For Food SecurityFollowing slide provides comprehensive overview of company. It includes elements such as founders, legal name, website, business model, industries etc. Present the topic in a bit more detail with this Company Introduction Smart Farming Technology Pitch Deck For Food Security Use it as a tool for discussion and navigation on Generate Food Income, Business Model This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Competitive Analysis Smart Farming Technology Pitch Deck For Food Security
Competitive Analysis Smart Farming Technology Pitch Deck For Food SecurityFollowing slide represents competitive analysis of company. It includes information about company names, founded year, growth score, location, total funding etc.Deliver an outstanding presentation on the topic using this Competitive Analysis Smart Farming Technology Pitch Deck For Food Security Dispense information and present a thorough explanation of Description, Founded Year, Growth Score using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Core Team Smart Farming Technology Pitch Deck For Food Security
Core Team Smart Farming Technology Pitch Deck For Food SecurityFollowing slide exhibits key members associated with company. It includes members such as CEO, COO and Community based development organization CBDO with experience and designation details. Introducing Core Team Smart Farming Technology Pitch Deck For Food Security to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Develop Better Surroundings, Sustainable Practices using this template. Grab it now to reap its full benefits.
-
 Esteemed Clientele Smart Farming Technology Pitch Deck For Food Security
Esteemed Clientele Smart Farming Technology Pitch Deck For Food SecurityFollowing slide showcases major customers that require company services. It includes clients such as skilled farmers, land owners and investors. Increase audience engagement and knowledge by dispensing information using Esteemed Clientele Smart Farming Technology Pitch Deck For Food Security This template helps you present information on Three stages. You can also present information on Land And Money, Land Owners, Investors With Money using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





