Powerpoint Templates and Google slides for Vulnerable
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Addressing Wireless Lan Security Threats And Vulnerabilities
Addressing Wireless Lan Security Threats And VulnerabilitiesThis slide showcases the security strategies that help companies to mitigate wireless LAN threats and vulnerabilities effectively. It includes threads such as IP, MAC spoofing, DNS cache spoofing, and Rogueevil twin access points. Introducing our Addressing Wireless Lan Security Threats And Vulnerabilities set of slides. The topics discussed in these slides are Threats And Vulnerabilities, Details, Security StrategiesThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Penetration Testing Approaches Steps To Perform Vulnerability Scan Penetration
Penetration Testing Approaches Steps To Perform Vulnerability Scan PenetrationThis slide highlights the various steps of vulnerability scan penetration testing. The purpose of this slide is to showcase the different phases, such as defining the scope, creating a standard procedure, identifying the type of scan needed, and so on. Introducing Penetration Testing Approaches Steps To Perform Vulnerability Scan Penetration to increase your presentation threshold. Encompassed with Eight stages, this template is a great option to educate and entice your audience. Dispence information on Configure The Vulnerability Scan, Initiate The Vulnerability Scan, Analyze The Results, Evaluate Associated Risks, using this template. Grab it now to reap its full benefits.
-
 Icon Showcasing Vulnerability And Patch Management Process
Icon Showcasing Vulnerability And Patch Management ProcessPresenting our set of slides with name Icon Showcasing Vulnerability And Patch Management Process. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Showcasing Vulnerability, Patch Management Process.
-
 Penetration Testing Implementation Plan Vulnerability Scanning Stage Of Penetration Testing
Penetration Testing Implementation Plan Vulnerability Scanning Stage Of Penetration TestingThis slide highlights a checklist to scan vulnerabilities while doing penetration testing. The purpose of this slide is to showcase the components involved, such as finding network topology, identifying OS types of discovered hosts, and so on. Deliver an outstanding presentation on the topic using this Penetration Testing Implementation Plan Vulnerability Scanning Stage Of Penetration Testing. Dispense information and present a thorough explanation of Network Topology, Network Services, Potential Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Top Web Application Security Vulnerabilities
Top Web Application Security VulnerabilitiesIntroducing our premium set of slides with Top Web Application Security Vulnerabilities Ellicudate the Eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Faulty Authentication, Object References So download instantly and tailor it with your information.
-
 Vulnerability Monitoring For Application Security Icon
Vulnerability Monitoring For Application Security IconIntroducing our Vulnerability Monitoring For Application Security Icon set of slides. The topics discussed in these slides are Vulnerability Monitoring, Application Security IconThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Agenda Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS
Agenda Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SSIntroducing Agenda Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Loopholes, Security Vulnerabilities, Vulnerabilities Mitigation Strategies, using this template. Grab it now to reap its full benefits.
-
 Gap Analysis Of Network Vulnerabilities Experienced By Organization Cybersecurity SS
Gap Analysis Of Network Vulnerabilities Experienced By Organization Cybersecurity SSThis slide represents the gap analysis to help organizations understand the gaps so that they could build effective strategies to eliminate these gaps and achieve desired results.Present the topic in a bit more detail with this Gap Analysis Of Network Vulnerabilities Experienced By Organization Cybersecurity SS. Use it as a tool for discussion and navigation on Current State, Gap, Desired State, Strategies To Fill Gap. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icons Slide Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS
Icons Slide Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SSPresenting our well crafted Icons Slide Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.
-
 Impact Of Mitigating Network Vulnerabilities On Organizational Operations Cybersecurity SS
Impact Of Mitigating Network Vulnerabilities On Organizational Operations Cybersecurity SSThis slide highlights the impact of implementing effective strategies to mitigate network vulnerabilities on organizational operations, such as potential revenue loss, customer churn, and other factors.Introducing Impact Of Mitigating Network Vulnerabilities On Organizational Operations Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Potential Annual Revenue, Customer Attrition Rate, Employee Productivity Rates, using this template. Grab it now to reap its full benefits.
-
 Impact Of Network Vulnerabilities On Organizational Operations Cybersecurity SS
Impact Of Network Vulnerabilities On Organizational Operations Cybersecurity SSThis slide illustrates the impact of network vulnerabilities experienced by enterprises on organizational operations, such as data corruption, reputational damage, and data theft etc. Increase audience engagement and knowledge by dispensing information using Impact Of Network Vulnerabilities On Organizational Operations Cybersecurity SS. This template helps you present information on four stages. You can also present information on Data Corruptions, Reputational Damage, Operational Disruption, Data Stealing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Implementing Strategies For Mitigating Network Vulnerabilities Table Of Contents Cybersecurity SS
Implementing Strategies For Mitigating Network Vulnerabilities Table Of Contents Cybersecurity SSIntroducing Implementing Strategies For Mitigating Network Vulnerabilities Table Of Contents Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Best Practices, Training Plan For Identification, using this template. Grab it now to reap its full benefits.
-
 Implementing Tools For Immediate Response To Network Vulnerabilities Cybersecurity SS
Implementing Tools For Immediate Response To Network Vulnerabilities Cybersecurity SSThis slide compares tools and technologies necessary to mitigate network vulnerabilities based on different aspects such as the scope of protection, granularity, user experience, and use cases.Present the topic in a bit more detail with this Implementing Tools For Immediate Response To Network Vulnerabilities Cybersecurity SS. Use it as a tool for discussion and navigation on Network Segmentation, End Point Protection, Zero Trust Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Issues Faced By Organization Due To Network Vulnerabilities Cybersecurity SS
Key Issues Faced By Organization Due To Network Vulnerabilities Cybersecurity SSThis slide represents challenges faced by enterprise as a result of network vulnerabilities leading to issues such as lack of privacy, compliance and security and data leakage etc.Introducing Key Issues Faced By Organization Due To Network Vulnerabilities Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Compliance, Security, Personal Devices, Software Encryption, using this template. Grab it now to reap its full benefits.
-
 Network Vulnerabilities Management Key Metrics Dashboard Cybersecurity SS
Network Vulnerabilities Management Key Metrics Dashboard Cybersecurity SSThis dashboard tracks and manages the organizations network vulnerabilities. It includes KPIs such as data access vulnerabilities and exploitable vulnerabilities and a summary of vulnerabilities by severity.Deliver an outstanding presentation on the topic using this Network Vulnerabilities Management Key Metrics Dashboard Cybersecurity SS. Dispense information and present a thorough explanation of Unmitigated, Mitigated, Exploitable, Exploitable Hosts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Overview Strategies For Mitigating Network Vulnerabilities Cybersecurity SS
Overview Strategies For Mitigating Network Vulnerabilities Cybersecurity SSThis slide presents effective techniques for mitigating network vulnerabilities, including anti-phishing training, end-to-end encryption, patch management, strong password policies and authentication protocols.Introducing Overview Strategies For Mitigating Network Vulnerabilities Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Provide Anti Phishing Training, Authentication Protocols, Patch Management, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS
Table Of Contents Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using Table Of Contents Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity SS. This template helps you present information on eight stages. You can also present information on Gap Analysis, Patch Management, Dashboard Tracking, Additional Slides using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Vulnerability management lifecycle diagram powerpoint image
Vulnerability management lifecycle diagram powerpoint imagePresenting vulnerability management lifecycle diagram powerpoint image. This is a vulnerability management lifecycle diagram powerpoint image. This is a four stage process. The stages in this process are discover, verify, remediate, report.
-
 Analytics of vulnerability management solutions diagram powerpoint guide
Analytics of vulnerability management solutions diagram powerpoint guidePresenting analytics of vulnerability management solutions diagram powerpoint guide. This is a analytics of vulnerability management solutions diagram powerpoint guide. This is a six stage process. The stages in this process are discovery, protection, monitoring, reporting, security, risk and compliance.
-
 Vulnerability evaluation layout powerpoint images
Vulnerability evaluation layout powerpoint imagesPresenting vulnerability evaluation layout powerpoint images. This is a vulnerability evaluation layout powerpoint images. This is a four stage process. The stages in this process are device discovery, service enumeration, scanning, validation.
-
 Features of waf application vulnerability prevention web application firewall waf it
Features of waf application vulnerability prevention web application firewall waf itThis slide represents the next feature of WAF, application vulnerability prevention, and how this feature automatically detects and fixes the web application vulnerabilities without changing the web application. Present the topic in a bit more detail with this Features Of Waf Application Vulnerability Prevention Web Application Firewall Waf It. Use it as a tool for discussion and navigation on Automatically, Management, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Current potential implications managing critical threat vulnerabilities and security threats
Current potential implications managing critical threat vulnerabilities and security threatsThis slide provides information regarding the potential implications concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an outstanding presentation on the topic using this Current Potential Implications Managing Critical Threat Vulnerabilities And Security Threats. Dispense information and present a thorough explanation of Increase Security Threats, Employees using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber threats management managing critical threat vulnerabilities and security threats
Cyber threats management managing critical threat vulnerabilities and security threatsThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Present the topic in a bit more detail with this Cyber Threats Management Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Cyber Threats Management Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Financial performance tracking managing critical threat vulnerabilities and security threats
Financial performance tracking managing critical threat vulnerabilities and security threatsThis slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Present the topic in a bit more detail with this Financial Performance Tracking Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Revenue And Expense Trends, Receivables Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
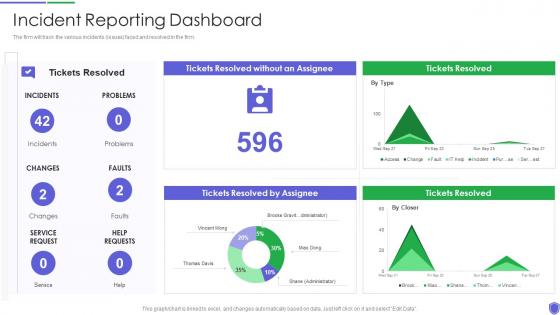 Incident reporting dashboard managing critical threat vulnerabilities and security threats
Incident reporting dashboard managing critical threat vulnerabilities and security threatsThe firm will track the various incidents issues faced and resolved in the firm. Present the topic in a bit more detail with this Incident Reporting Dashboard Managing Critical Threat Vulnerabilities And Security Threats. Use it as a tool for discussion and navigation on Incident Reporting Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk And Vulnerability Management Dashboard Introduction
Risk And Vulnerability Management Dashboard IntroductionThe slide highlights the risk and vulnerability management dashboard introduction representing risk exposure, number of impacted resources and weekly trend, recent risk exposure, risk exposure by resource proportion and type. Presenting our well structured Risk And Vulnerability Management Dashboard Introduction. The topics discussed in this slide are Impacted Resource, Risk Exposure By Resource Proportion, Risk Exposure By Resource Type, Recent Risk Exposure. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Risk Management Framework For Information Security Threat And Vulnerability
Risk Management Framework For Information Security Threat And VulnerabilityFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Risk Management Framework For Information Security Threat And Vulnerability. Use it as a tool for discussion and navigation on Exposure Score, Top Vulnerable Software, Severity Distribution, Active Remediation, Configuration Score. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
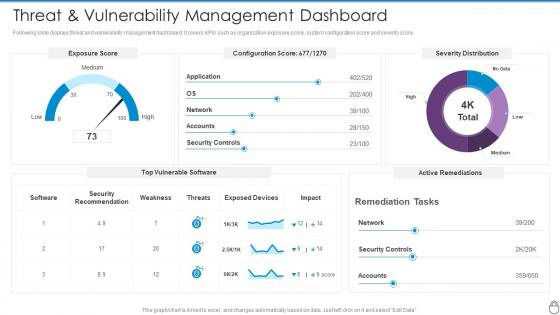 Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard
Cybersecurity Risk Management Framework Threat And Vulnerability Management DashboardFollowing slide displays threat and vulnerability management dashboard. It covers KPIs such as organization exposure score, system configuration score and severity score. Present the topic in a bit more detail with this Cybersecurity Risk Management Framework Threat And Vulnerability Management Dashboard. Use it as a tool for discussion and navigation on Exposure Score, Configuration Score, Severity Distribution, Weakness, Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security information event management dashboard improve security vulnerability management
Security information event management dashboard improve security vulnerability managementThis slide covers the SIEM dashboard which focuses on server status, log sources, total logs, last log, collectors, log sources etc. Deliver an outstanding presentation on the topic using this Security Information Event Management Dashboard Improve Security Vulnerability Management. Dispense information and present a thorough explanation of Management, Dashboard, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Technology assessment scorecard highlighting recent vulnerabilities
Technology assessment scorecard highlighting recent vulnerabilitiesThis graph or chart is linked to excel, and changes automatically based on data. Just left click on it and select Edit Data Deliver an outstanding presentation on the topic using this Technology Assessment Scorecard Highlighting Recent Vulnerabilities. Dispense information and present a thorough explanation of Weekly Trend, Resources Impacted, Data Centre, Number Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Improve it security vulnerability security information event management dashboard
Improve it security vulnerability security information event management dashboardThis slide covers the SIEM dashboard which focuses on threat activity, log and event trend, log source, impacted hosts, log classification, Deliver an outstanding presentation on the topic using this Improve It Security Vulnerability Security Information Event Management Dashboard. Dispense information and present a thorough explanation of Information, Management, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Improve it security with vulnerability event management dashboard snapshot
Improve it security with vulnerability event management dashboard snapshotThis slide covers the SIEM dashboard which focuses on security events, event categories, data sources, logger event, multiple events, etc. Deliver an outstanding presentation on the topic using this Improve It Security With Vulnerability Event Management Dashboard snapshot. Dispense information and present a thorough explanation of Information, Management, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Coronavirus Mitigation Strategies Food Service Industry Jobs Vulnerable Layoffs During Covid 19
Coronavirus Mitigation Strategies Food Service Industry Jobs Vulnerable Layoffs During Covid 19Mentioned slide portrays key statistics of job vulnerable to laid off due to COVID 19 crisis in various industries of US. It indicates that food and beverage services industry will have the highest impact of pandemic. Present the topic in a bit more detail with this Coronavirus Mitigation Strategies Food Service Industry Jobs Vulnerable Layoffs During Covid 19. Use it as a tool for discussion and navigation on Industry Wise Jobs Vulnerable To Layoffs During COVID 19 In US. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Incident Reporting Dashboard Snapshot Vulnerability Administration At Workplace
Incident Reporting Dashboard Snapshot Vulnerability Administration At WorkplaceThe firm will track the various incidents issues faced and resolved in the firm. Deliver an outstanding presentation on the topic using this Incident Reporting Dashboard Snapshot Vulnerability Administration At Workplace. Dispense information and present a thorough explanation of Incident Reporting Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Vulnerability Administration At Workplace Current Potential Implications Faced By Firm As Threats
Vulnerability Administration At Workplace Current Potential Implications Faced By Firm As ThreatsThis slide provides information regarding the potential implications or concerns existing in firm in terms of increase in issues related to employees such as lack of expertise, ineffectiveness in handling issues, reported financial losses due to financial threats and data breaches with records exposed. Deliver an outstanding presentation on the topic using this Vulnerability Administration At Workplace Current Potential Implications Faced By Firm As Threats. Dispense information and present a thorough explanation of Potential, Implications, Ineffectiveness using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Vulnerability Administration At Workplace Cyber Threats Management Dashboard
Vulnerability Administration At Workplace Cyber Threats Management DashboardThis slide portrays information regarding the dashboard that firm will use to manage cyber threats. The dashboard will provide clear picture of threats risks prevailing and how they are treated to technical engineers and board level executives. Deliver an outstanding presentation on the topic using this Vulnerability Administration At Workplace Cyber Threats Management Dashboard. Dispense information and present a thorough explanation of Management, Dashboard, Portrays Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Vulnerability Administration At Workplace Financial Performance Tracking Dashboard
Vulnerability Administration At Workplace Financial Performance Tracking DashboardThis slide presents the dashboard which will help firm in tracking the fiscal performance. This dashboard displays revenues and expenses trends and payment received analysis. Deliver an outstanding presentation on the topic using this Vulnerability Administration At Workplace Financial Performance Tracking Dashboard. Dispense information and present a thorough explanation of Financial, Performance, Dashboard using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Vulnerability Administration At Workplace Statistics Associated To Workplace Threats
Vulnerability Administration At Workplace Statistics Associated To Workplace ThreatsThis slide provides details regarding statistics associated to workplace threats that firms face in terms of data records theft, workplace violence, financial phishing, etc. Present the topic in a bit more detail with this Vulnerability Administration At Workplace Statistics Associated To Workplace Threats. Use it as a tool for discussion and navigation on Cyber Attacks Costs, Organizations, Organizations Have. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Supply Chain Data Analytics And Vulnerability Assessment Report
Supply Chain Data Analytics And Vulnerability Assessment ReportThis slide shows the assessment report prepared through data analytics showing the weaknesses identified in management of supply chain risks. It includes details related to vulnerability comparison to industry benchmark and financial resiliency scores. Introducing our Supply Chain Data Analytics And Vulnerability Assessment Report set of slides. The topics discussed in these slides are Planning And Supplier Network, Transportation And Logistics, Financial Flexibility. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Risk Acceptance Dashboard With System Severity And Vulnerability
Risk Acceptance Dashboard With System Severity And VulnerabilityThis slide showcase risk acceptance dashboard with system severity and vulnerability which includes accepted risks by severity, highly severe risks, summarized severity, etc. Presenting our well-structured Risk Acceptance Dashboard With System Severity And Vulnerability. The topics discussed in this slide are Risk Acceptance, Dashboard, System Severity, Vulnerability. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Application Firewall Features of WAF Application Vulnerability Prevention
Application Firewall Features of WAF Application Vulnerability PreventionThis slide represents the next feature of WAF, application vulnerability prevention, and how this feature automatically detects and fixes the web application vulnerabilities without changing the web application. Present the topic in a bit more detail with this Application Firewall Features of WAF Application Vulnerability Prevention. Use it as a tool for discussion and navigation on Identity Management, Incident Management, Application Scanner. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Management Program Dashboard For Vulnerability Analysis
Management Program Dashboard For Vulnerability AnalysisThis slide defines the dashboard for analyzing the vulnerabilities. It includes information related to the severity and vulnerability age matrix. Introducing our Management Program Dashboard For Vulnerability Analysis set of slides. The topics discussed in these slides are Total Vulnerabilities, Fixable Vulnerabilities, Vulnerabilities With Manual Resolution. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Threat And Vulnerability Management Program Analysis Dashboard
Threat And Vulnerability Management Program Analysis DashboardThis slide defines the dashboard for analyzing the threat and vulnerability program. It includes information related to the exposure, configuration and severity score. Presenting our well structured Threat And Vulnerability Management Program Analysis Dashboard. The topics discussed in this slide are Exposure Score, Top Vulnerable Software, Severity Distribution. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Clustered Column Cybersecurity Incident And Vulnerability Response Playbook
Clustered Column Cybersecurity Incident And Vulnerability Response PlaybookDeliver an outstanding presentation on the topic using this Clustered Column Cybersecurity Incident And Vulnerability Response Playbook. Dispense information and present a thorough explanation of Product, Clustered Column, Sales using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determining The Ransom Payment Paid By Organizations Over Cybersecurity Incident And Vulnerability
Determining The Ransom Payment Paid By Organizations Over Cybersecurity Incident And VulnerabilityDeliver an outstanding presentation on the topic using this Determining The Ransom Payment Paid By Organizations Over Cybersecurity Incident And Vulnerability. Dispense information and present a thorough explanation of Payments, Response Approaches using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPI Dashboard To Track Department Wise Security Incidents Cybersecurity Incident And Vulnerability
KPI Dashboard To Track Department Wise Security Incidents Cybersecurity Incident And VulnerabilityMentioned slide portrays KPI dashboard that can be used to monitor department wise security incidents. KPIs covered are new cases, total cases, resolved and pending cases. Present the topic in a bit more detail with this KPI Dashboard To Track Department Wise Security Incidents Cybersecurity Incident And Vulnerability. Use it as a tool for discussion and navigation on New Cases, In Progress, IT Department. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Line Chart Cybersecurity Incident And Vulnerability Response Playbook
Line Chart Cybersecurity Incident And Vulnerability Response PlaybookDeliver an outstanding presentation on the topic using this Line Chart Cybersecurity Incident And Vulnerability Response Playbook. Dispense information and present a thorough explanation of Line Chart using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Real Time Incident Management Dashboard Cybersecurity Incident And Vulnerability
Real Time Incident Management Dashboard Cybersecurity Incident And VulnerabilityFollowing slide illustrate KPI dashboard that can be used by organizations to track real time incident data. KPIs covered are number of tickets, average resolution time per customer, incidents registered per month. Present the topic in a bit more detail with this Real Time Incident Management Dashboard Cybersecurity Incident And Vulnerability. Use it as a tool for discussion and navigation on Average Resolution, Customer, Incidents Registered. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Vulnerabilities Assessment Approach
Network Security Vulnerabilities Assessment ApproachThis slide illustrates network security vulnerabilities assessment results that help the organization to secure network security loop holes to mitigate vulnerabilities. It key components are unpatched security, patched security and total number of vulnerabilities. Introducing our Network Security Vulnerabilities Assessment Approach set of slides. The topics discussed in these slides are Sion And Configuration. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Top Vulnerable Industries To Cyber Security Threats And Data Breaches
Top Vulnerable Industries To Cyber Security Threats And Data BreachesThis slide provides useful insights about most vulnerable industries to cyber security attacks and data breaches. The major industries are government, banking, communications, healthcare, e commerce, shipping and logistics and cryptocurrency Introducing our Top Vulnerable Industries To Cyber Security Threats And Data Breaches set of slides. The topics discussed in these slides are Government, Department. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Vulnerabilities Tracking Dashboard For Secops Ppt Powerpoint Presentation Layouts Topics
Vulnerabilities Tracking Dashboard For Secops Ppt Powerpoint Presentation Layouts TopicsThis slide represents the vulnerabilities tracking dashboard for SecOps. The purpose of this slide is to demonstrate the tracking of vulnerabilities of an organizations assets, services with the most vulnerabilities, mean time to remediate, and the average age of vulnerabilities. Present the topic in a bit more detail with this Vulnerabilities Tracking Dashboard For Secops Ppt Powerpoint Presentation Layouts Topics. Use it as a tool for discussion and navigation on Average Vulnerabilities Asset, Average Age Vulnerabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Features Of WAF Application Vulnerability Prevention Ppt Information
Features Of WAF Application Vulnerability Prevention Ppt InformationThis slide represents the next feature of WAF, application vulnerability prevention, and how this feature automatically detects and fixes the web application vulnerabilities without changing the web application. Deliver an outstanding presentation on the topic using this Features Of WAF Application Vulnerability Prevention Ppt Information. Dispense information and present a thorough explanation of Application, Vulnerability, Prevention using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk governance network vulnerabilities strategy implementation software development cpb
Risk governance network vulnerabilities strategy implementation software development cpbPresenting this set of slides with name - Risk Governance Network Vulnerabilities Strategy Implementation Software Development Cpb. This is an editable three stages graphic that deals with topics like Risk Governance, Network Vulnerabilities, Strategy Implementation, Software Development to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Vulnerability management system workforce diversity marketing communications planning cpb
Vulnerability management system workforce diversity marketing communications planning cpbPresenting this set of slides with name - Vulnerability Management System Workforce Diversity Marketing Communications Planning Cpb. This is an editable four stages graphic that deals with topics like Vulnerability Management System, Workforce Diversity, Marketing Communications Planning to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Vulnerability management icons slide
Vulnerability management icons slidePresenting our premium Vulnerability Management Icons Slide set of slides with flexible icons. The icons are designed by our group of professionals. Add these Vulnerability Management Icons Slide to your presentation to make it visually appealing. Also, edit them according to your requirement. Download it and captive your audience.
-
 Vulnerability management whitepaper analyze root causes ppt slides role
Vulnerability management whitepaper analyze root causes ppt slides roleIncrease audience engagement and knowledge by dispensing information using Vulnerability Management Whitepaper Analyze Root Causes Ppt Slides Role. This template helps you present information on four stages. You can also present information on Monitor Effect, Corrective Actions, Update Vulnerability Repository, Perform Root Cause Analysis, Develop Corrective Actions To Address Root Cause using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Vulnerability management whitepaper categorize and prioritize vulnerabilities
Vulnerability management whitepaper categorize and prioritize vulnerabilitiesIntroducing Vulnerability Management Whitepaper Categorize And Prioritize Vulnerabilities to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Analyze Relevance, Determine Responsibility, Prioritize, Produce Wealth Information, Technology, using this template. Grab it now to reap its full benefits.
-
 Vulnerability management whitepaper collect and analyze program information
Vulnerability management whitepaper collect and analyze program informationIncrease audience engagement and knowledge by dispensing information using Vulnerability Management Whitepaper Collect And Analyze Program Information. This template helps you present information on four stages. You can also present information on Gather Process Outputs, Gather Process Policy, Gather Process Plan, Analyze Measures Effectiveness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Vulnerability management whitepaper conduct vulnerability assessment activities
Vulnerability management whitepaper conduct vulnerability assessment activitiesIntroducing Vulnerability Management Whitepaper Conduct Vulnerability Assessment Activities to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Execute Vulnerability Scans, Execute Vulnerability Assessments, Organizations, Physical Vulnerabilities, using this template. Grab it now to reap its full benefits.
-
 Vulnerability management whitepaper define and document the plan ppt styles inspiration
Vulnerability management whitepaper define and document the plan ppt styles inspirationIncrease audience engagement and knowledge by dispensing information using Vulnerability Management Whitepaper Define And Document The Plan Ppt Styles Inspiration. This template helps you present information on five stages. You can also present information on Build Vulnerability Management Team, Coordinate Risk Management, Define Standard Remediation Timelines, Define Vulnerabilities Should Documented, Define Periodic Activities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





