Powerpoint Templates and Google slides for Vulnerable
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Managing critical threat vulnerabilities and security threats powerpoint presentation slides
Managing critical threat vulnerabilities and security threats powerpoint presentation slidesDeliver an informational PPT on various topics by using this Managing Critical Threat Vulnerabilities And Security Threats Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with seventy slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
-
 Vulnerability Administration At Workplace Powerpoint Presentation Slides
Vulnerability Administration At Workplace Powerpoint Presentation SlidesEnthrall your audience with this Vulnerability Administration At Workplace Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising seventy slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity CD
Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity CDStep up your game with our enchanting Implementing Strategies For Mitigating Network Vulnerabilities Cybersecurity CD deck, guaranteed to leave a lasting impression on your audience. Crafted with a perfect balance of simplicity, and innovation, our deck empowers you to alter it to your specific needs. You can also change the color theme of the slide to mold it to your companys specific needs. Save time with our ready-made design, compatible with Microsoft versions and Google Slides. Additionally, it is available for download in various formats including JPG, JPEG, and PNG. Outshine your competitors with our fully editable and customized deck.
-
 Improve it security with vulnerability management powerpoint presentation slides
Improve it security with vulnerability management powerpoint presentation slidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Improve IT Security With Vulnerability Management Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the sixty one slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 ChatGPT For Threat Intelligence And Vulnerability Assessment AI CD V
ChatGPT For Threat Intelligence And Vulnerability Assessment AI CD VDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this ChatGPT For Threat Intelligence And Vulnerability Assessment AI CD V is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fifty one slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Cybersecurity Incident And Vulnerability Response Playbook Powerpoint Presentation Slides
Cybersecurity Incident And Vulnerability Response Playbook Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Cybersecurity Incident And Vulnerability Response Playbook Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the fifty slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Vulnerability Management Whitepaper Powerpoint Presentation Slides
Vulnerability Management Whitepaper Powerpoint Presentation SlidesIntroducing Vulnerability Management Whitepaper PowerPoint Presentation Slides. By downloading this complete PPT deck you will get access to 46 professional slides. Since they feature 100% customizability, you can edit any element including font, text, and color as per your choice. This PowerPoint slideshow can be viewed on Google Slides and converted to file formats like PDF, PNG, and JPG. Our PPT template deck is also available in dual screen formats, standard and widescreen.
-
 Enterprise Vulnerability Management Powerpoint Presentation Slides
Enterprise Vulnerability Management Powerpoint Presentation SlidesThis complete presentation has PPT slides on wide range of topics highlighting the core areas of your business needs. It has professionally designed templates with relevant visuals and subject driven content. This presentation deck has total of fourty six slides. Get access to the customizable templates. Our designers have created editable templates for your convenience. You can edit the colour, text and font size as per your need. You can add or delete the content if required. You are just a click to away to have this ready-made presentation. Click the download button now.
-
 Vulnerability Assessment Plan Powerpoint Presentation Slides
Vulnerability Assessment Plan Powerpoint Presentation SlidesPresenting Vulnerability Assessment Plan Powerpoint Presentation Slides. Make modifications in the font color, font size, and font style of the slide as it is entirely customizable. Its compatibility with Google Slides makes it accessible at once. You can transform and save the slide in PDF and JPG formats as well. Get this high-quality slide to present it in front of thousands of people on a standard screen and widescreen.
-
 Security Vulnerability Powerpoint Ppt Template Bundles
Security Vulnerability Powerpoint Ppt Template BundlesEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Security Vulnerability Powerpoint Ppt Template Bundles is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With Eighteen slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
 Vulnerability Management Program Powerpoint Ppt Template Bundles
Vulnerability Management Program Powerpoint Ppt Template BundlesDeliver a lucid presentation by utilizing this Vulnerability Management Program Powerpoint Ppt Template Bundles. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Threat And Vulnerability Management, Vulnerability Analysis, Risk Management Program, Vulnerability Identification Checklist, Threat Detection. All the seventeen slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
 Blockchain Technology Vulnerabilities User Wallet Attack Training Ppt
Blockchain Technology Vulnerabilities User Wallet Attack Training PptPresenting Blockchain Technology Vulnerabilities User Wallet Attack. This slide is well crafted and designed by our PowerPoint specialists. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. You can add or delete the content as per your need.
-
 Identifying Vulnerabilities As A Step For Cybersecurity Risk Identification Training Ppt
Identifying Vulnerabilities As A Step For Cybersecurity Risk Identification Training PptPresenting Identifying Vulnerabilities as a Step for Cybersecurity Risk Identification. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Signs That Your Business May Be Vulnerable To Cyber Threats Training Ppt
Signs That Your Business May Be Vulnerable To Cyber Threats Training PptPresenting Signs that your Business may be Vulnerable to Cyber Threats. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Identifying Vulnerabilities For Operational Security Training Ppt
Identifying Vulnerabilities For Operational Security Training PptPresenting Identifying Vulnerabilities for Operational Security. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Coordinated Vulnerability Platform As An Application Security Approach Training Ppt
Coordinated Vulnerability Platform As An Application Security Approach Training PptPresenting Coordinated Vulnerability Platform as an Application Security Approach. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Money Laundering And Terrorist Financing Vulnerabilities In Banking Training Ppt
Money Laundering And Terrorist Financing Vulnerabilities In Banking Training PptPresenting Money Laundering and Terrorist Financing Vulnerabilities in Banking. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Identifying Vulnerabilities Arising From Risks Training Ppt
Identifying Vulnerabilities Arising From Risks Training PptPresenting Identifying Vulnerabilities arising from Business and Regulatory Risks in AML. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Blockchain Vulnerabilities Routing Attack Training Ppt
Blockchain Vulnerabilities Routing Attack Training PptPresenting Blockchain Vulnerabilities Routing Attack. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Enterprise Vulnerability Management Powerpoint PPT Template Bundles
Enterprise Vulnerability Management Powerpoint PPT Template BundlesDeliver a credible and compelling presentation by deploying this Enterprise Vulnerability Management Powerpoint PPT Template Bundles. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The thirteen slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Enterprise Vulnerability Management Powerpoint PPT Template Bundles Industry Comparison PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Vulnerability Management Process Flow Powerpoint Ppt Template Bundles
Vulnerability Management Process Flow Powerpoint Ppt Template BundlesIntroduce your topic and host expert discussion sessions with this Vulnerability Management Process Flow Powerpoint Ppt Template Bundles. This template is designed using high-quality visuals, images, graphics, etc, that can be used to showcase your expertise. Different topics can be tackled using the Twelve slides included in this template. You can present each topic on a different slide to help your audience interpret the information more effectively. Apart from this, this PPT slideshow is available in two screen sizes, standard and widescreen making its delivery more impactful. This will not only help in presenting a birds-eye view of the topic but also keep your audience engaged. Since this PPT slideshow utilizes well-researched content, it induces strategic thinking and helps you convey your message in the best possible manner. The biggest feature of this design is that it comes with a host of editable features like color, font, background, etc. So, grab it now to deliver a unique presentation every time.
-
 Identifying Vulnerable People For Fire Risk Assessment Approach Training Ppt
Identifying Vulnerable People For Fire Risk Assessment Approach Training PptPresenting Identifying Vulnerable People for Fire Risk Assessment Approach. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support is available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Crisis Management Strategy Business Vulnerability Assessment Improvement Framework
Crisis Management Strategy Business Vulnerability Assessment Improvement FrameworkEngage buyer personas and boost brand awareness by pitching yourself using this prefabricated set. This Crisis Management Strategy Business Vulnerability Assessment Improvement Framework is a great tool to connect with your audience as it contains high-quality content and graphics. This helps in conveying your thoughts in a well-structured manner. It also helps you attain a competitive advantage because of its unique design and aesthetics. In addition to this, you can use this PPT design to portray information and educate your audience on various topics. With twelve slides, this is a great design to use for your upcoming presentations. Not only is it cost-effective but also easily pliable depending on your needs and requirements. As such color, font, or any other design component can be altered. It is also available for immediate download in different formats such as PNG, JPG, etc. So, without any further ado, download it now.
-
 Vulnerability Analyzing Dashboard For Cyber Threat Intelligence
Vulnerability Analyzing Dashboard For Cyber Threat IntelligenceThis slide showcases the vulnerability analyzing dashboard for cyber threat intelligence based on various parameters such as issue status, severity, etc. Present the topic in a bit more detail with this Vulnerability Analyzing Dashboard For Cyber Threat Intelligence. Use it as a tool for discussion and navigation on Vulnerability Analyzing Dashboard, Cyber Threat Intelligence, Issue Status, Severity. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Vulnerabilities Logged Off In Previous Years Implementing Strategies For Mitigating Cybersecurity SS
Network Vulnerabilities Logged Off In Previous Years Implementing Strategies For Mitigating Cybersecurity SSThis slide represents network vulnerabilities faced by the organization, which led to the theft of confidential and sensitive information due to opening of infected email attachments etc.Deliver an outstanding presentation on the topic using this Network Vulnerabilities Logged Off In Previous Years Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Phishing Attacks, Malware Attacks, Reasons, Key Insights using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Vulnerabilities Tracking Dashboard For Secops V2 Ppt Icon Graphics Template
Vulnerabilities Tracking Dashboard For Secops V2 Ppt Icon Graphics TemplateThis slide represents the vulnerabilities tracking dashboard for SecOps. The purpose of this slide is to demonstrate the tracking of vulnerabilities of an organizations assets, services with the most vulnerabilities, mean time to remediate, and the average age of vulnerabilities. Deliver an outstanding presentation on the topic using this Vulnerabilities Tracking Dashboard For Secops V2 Ppt Icon Graphics Template. Dispense information and present a thorough explanation of Vulnerabilities Tracking, Dashboard For Secops, Age Of Vulnerabilities, Mean Time To Remediate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Triage Cyber Security For Vulnerability Management Dashboard
Triage Cyber Security For Vulnerability Management DashboardThis slide represents triage cyber security for vulnerability management dashboard which assist to identify and prevent system vulnerabilities. It includes key components such as latest scans, tracker, etc Introducing our Triage Cyber Security For Vulnerability Management Dashboard set of slides. The topics discussed in these slides are Most Vulnerable Hosts, Vulnerabilities Status This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Testing Assessment And Vulnerabilities Dashboard
Security Testing Assessment And Vulnerabilities DashboardThis slide depicts the security testing assessment components such as CVSS score, severity, current risk levels for security index, business impact, technical impacts, etc. Present the topic in a bit more detail with this Security Testing Assessment And Vulnerabilities Dashboard. Use it as a tool for discussion and navigation on Security Testing Assessment, Vulnerabilities Dashboard, Business Impact, Technical Impacts. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Application Security Implementation Plan Application Security Vulnerability Scanning Dashboard
Application Security Implementation Plan Application Security Vulnerability Scanning DashboardThis slide depicts the threat scanning dashboard for application security to analyze and monitor vulnerabilities of application. Present the topic in a bit more detail with this Application Security Implementation Plan Application Security Vulnerability Scanning Dashboard. Use it as a tool for discussion and navigation on Application Security Vulnerability, Scanning Dashboard, Monitor Vulnerabilities Of Application. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Kpi Dashboard To Measure Security Vulnerabilities Software Performance
Kpi Dashboard To Measure Security Vulnerabilities Software PerformanceFollowing slide showcases security vulnerabilities measutequal toring KPI dashboard to assess software performance. It further covers vulnerability status, days awaiting approval, days awaiting execution, days to close alongside vulnerabilities per stage, etc. Presenting our well structured Kpi Dashboard To Measure Security Vulnerabilities Software Performance The topics discussed in this slide are Days Awaiting Execution, Awaiting Execution, Awaiting ApprovalThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Survey Analysis Of Major Network Security Vulnerabilities
Survey Analysis Of Major Network Security VulnerabilitiesFollowing slide represents vulnerabilities to network security with survey. It further includes survey on 50 companies showcasing results such as broken access control, broken authentication, sensitive data exposure, etc. Presenting our well structured Survey Analysis Of Major Network Security Vulnerabilities The topics discussed in this slide are Users Web Applications, Data Breach, High SeverityThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Ai Network Security Vulnerabilities By Country
Ai Network Security Vulnerabilities By CountryThis slide shows various countries using AI-driven technology for security through, which they have to favor multiple vulnerabilities.Some vulnerabilities are manipulation of algorithms, stealing confidential information of clients or customers Presenting our well structured Ai Network Security Vulnerabilities By Country. The topics discussed in this slide are Growing Vulnerabilities, Manipulation Of AI Algorithms, Information Of Registered Clients. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Vulnerability Analyzing Dashboard For Exploratory Testing
Vulnerability Analyzing Dashboard For Exploratory TestingThis slide showcases the vulnerability analyzing dashboard for exploratory testing based on various parameters such as issue status, ID, etc. Present the topic in a bit more detail with this Vulnerability Analyzing Dashboard For Exploratory Testing Use it as a tool for discussion and navigation on Vulnerability Analyzing Dashboard, Exploratory Testing This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building Security Dashboard Illustrating Vulnerability Status
Building Security Dashboard Illustrating Vulnerability StatusThis slide showcases the building security dashboard representing vulnerability status which helps an organization to improve customer service by offering quick response time. It include details such as per stage vulnerabilities,awaiting execution average days,etc. Introducing our Building Security Dashboard Illustrating Vulnerability Status set of slides. The topics discussed in these slides are Vulnerability Status,Awaiting Attention,Per Stage Vulnerabilities. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Network Vulnerabilities Assessment KPI Dashboard Implementing Strategies For Mitigating Cybersecurity SS
Network Vulnerabilities Assessment KPI Dashboard Implementing Strategies For Mitigating Cybersecurity SSThis dashboard tracks and assesses the network vulnerabilities faced by the organization. It includes KPIs such as critical vulnerabilities, new vulnerabilities, and unresolved vulnerabilities etc.Present the topic in a bit more detail with this Network Vulnerabilities Assessment KPI Dashboard Implementing Strategies For Mitigating Cybersecurity SS. Use it as a tool for discussion and navigation on New Vulnerabilities, Unresolved Vulnerabilities, Activity, Insecure Libraries. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SS
Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SSThis slide shows the impact of strategies implemented by IT and security professionals to prevent and mitigate network vulnerabilities, including phishing attacks, malware attacks, insider attacks and software vulnerabilities.Deliver an outstanding presentation on the topic using this Potential Impact Of Mitigating Network Vulnerabilities On Cyber Attacks Cybersecurity SS. Dispense information and present a thorough explanation of Cyber Attacks, Secure Passwords, Compliant Monitoring And Auditing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Potential Roi After Implementing Tools And Technologies To Reduce Network Vulnerabilities Cybersecurity SS
Potential Roi After Implementing Tools And Technologies To Reduce Network Vulnerabilities Cybersecurity SSThis slide demonstrates the positive impact of implementing network vulnerability management solutions on returns on investments. The graph depicts an increase in ROI and savings over time..Deliver an outstanding presentation on the topic using this Potential Roi After Implementing Tools And Technologies To Reduce Network Vulnerabilities Cybersecurity SS. Dispense information and present a thorough explanation of Key Insights, Improved Compliance, Password Hacking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Internal vulnerability scanning services ppt powerpoint presentation professional cpb
Internal vulnerability scanning services ppt powerpoint presentation professional cpbPresenting our Internal Vulnerability Scanning Services Ppt Powerpoint Presentation Professional Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Internal Vulnerability Scanning Services This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security Threats Vulnerabilities In Powerpoint And Google Slides Cpb
Security Threats Vulnerabilities In Powerpoint And Google Slides CpbPresenting our Security Threats Vulnerabilities In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Security Threats Vulnerabilities. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Vulnerabilities Cloud Computing Servers In Powerpoint And Google Slides Cpb
Vulnerabilities Cloud Computing Servers In Powerpoint And Google Slides CpbPresenting Vulnerabilities Cloud Computing Servers In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Vulnerabilities Cloud Computing Servers. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Challenges Faced By ChatGPT In Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS
Challenges Faced By ChatGPT In Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SSThis slide showcases various challenges faced by ChatGPT for effective vulnerability assessment and tackling cyber attacks. Key challenges faced are requirement of training data, difficulty in identifying assets and ethical implications. Increase audience engagement and knowledge by dispensing information using Challenges Faced By ChatGPT In Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS. This template helps you present information on three stages. You can also present information on Amount, Legal, Sensitive using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 ChatGPT Opportunities For Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS
ChatGPT Opportunities For Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SSThis slide showcases various ChatGPT opportunities for vulnerability assessment which can help to tackle cyber attack. Its key elements are automation of security tasks, improved efficiency and identification of new vulnerabilities. Increase audience engagement and knowledge by dispensing information using ChatGPT Opportunities For Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS. This template helps you present information on three stages. You can also present information on Security, Improved, Identify using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview And Importance Of Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS
Overview And Importance Of Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SSThis slide showcases vulnerability assessment overview which can help organization to prevent cyber attacks. It also highlights various importance of vulnerability assessment such as identifying security flaws, optimize security investments, reduced likelihood of security breach etc. Increase audience engagement and knowledge by dispensing information using Overview And Importance Of Vulnerability How ChatGPT Is Revolutionizing Cybersecurity ChatGPT SS. This template helps you present information on three stages. You can also present information on Reduce, Security, Organization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Breach Prevention And Mitigation Data Breach Response Plan Fix Vulnerabilities
Data Breach Prevention And Mitigation Data Breach Response Plan Fix VulnerabilitiesThis slide represents actions to be taken, the responsible team, the deadline, and tasks for fixing vulnerabilities after a data breach. The action items include assessing Service Providers access privileges, reviewing network segmentation, monitoring, etc. Deliver an outstanding presentation on the topic using this Data Breach Prevention And Mitigation Data Breach Response Plan Fix Vulnerabilities. Dispense information and present a thorough explanation of Collaborate With Forensics Experts, Review Network Segmentation, Communicate Transparently using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Breach Prevention Vulnerabilities Targeted In Data Breach Attacks
Data Breach Prevention Vulnerabilities Targeted In Data Breach AttacksThe purpose of this slide is to discuss the most vulnerable target points of data breach attacks. The significant vulnerabilities include weak credentials, stolen information, compromised assets, payment card fraud, third-party access, mobile devices, etc. Increase audience engagement and knowledge by dispensing information using Data Breach Prevention Vulnerabilities Targeted In Data Breach Attacks. This template helps you present information on five stages. You can also present information on Payment Card Fraud, Mobile Devices, Weak Credentials, Compromised Assets, Data Breach Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Vulnerability Management Broken Shield Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Vulnerability Management Broken Shield Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon features a broken shield with a distressed texture. It is perfect for conveying a sense of vulnerability, fragility, or failure in presentations. It is available in a range of vibrant colours and can be used to highlight key points or draw attention to important concepts.
-
 Vulnerability Management Broken Shield Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Vulnerability Management Broken Shield Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint icon depicts a broken shield, representing a lack of protection or security. It is perfect for conveying a sense of vulnerability, fragility, or danger in presentations. It can also be used to illustrate a lack of trust or loyalty.
-
 Identifying Potential Areas Of Risk And Vulnerability Within Strategies To Comply Strategy SS V
Identifying Potential Areas Of Risk And Vulnerability Within Strategies To Comply Strategy SS VThis slide presents key methods for locating compliances weak spots and risky places in business. It includes methods such as risk assessment, compliance audits, incident and complaint analysis, benchmarking and expert opinion. Introducing Identifying Potential Areas Of Risk And Vulnerability Within Strategies To Comply Strategy SS V to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Risk Assessment, Compliance Audits, Incident And Complaint Analysis, using this template. Grab it now to reap its full benefits.
-
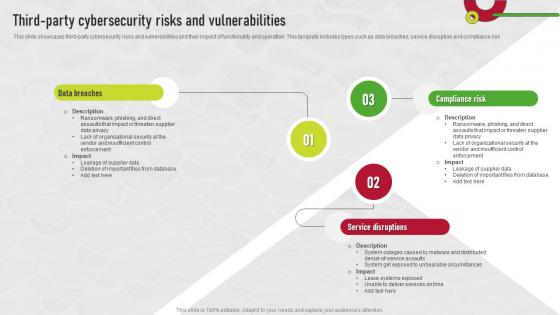 Third Party Cybersecurity Risks And Vulnerabilities Supplier Risk Management
Third Party Cybersecurity Risks And Vulnerabilities Supplier Risk ManagementThis slide showcases third party cybersecurity risks and vulnerabilities and their impact of functionality and operation. This template includes types such as data breaches, service disruption and compliance risk. Increase audience engagement and knowledge by dispensing information using Third Party Cybersecurity Risks And Vulnerabilities Supplier Risk Management. This template helps you present information on three stages. You can also present information on Data Breaches, Service Disruptions, Compliance Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Vulnerable Populations Health In Powerpoint And Google Slides Cpb
Vulnerable Populations Health In Powerpoint And Google Slides CpbPresenting Vulnerable Populations Health In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Vulnerable Populations Health. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Identifying Potential Areas Of Risk And Vulnerability Corporate Regulatory Compliance Strategy SS V
Identifying Potential Areas Of Risk And Vulnerability Corporate Regulatory Compliance Strategy SS VThis slide presents key methods for locating compliances weak spots and risky places in business. It includes methods such as risk assessment, compliance audits, incident and complaint analysis, benchmarking and expert opinion. Deliver an outstanding presentation on the topic using this Identifying Potential Areas Of Risk And Vulnerability Corporate Regulatory Compliance Strategy SS V. Dispense information and present a thorough explanation of Risk Assessment, Compliance Audits using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Plan To Prevent Cyber Risk Register To Measure Cyber Attacks Vulnerabilities
Security Plan To Prevent Cyber Risk Register To Measure Cyber Attacks VulnerabilitiesThis slide indicates the risk register to measure the cyber attack risk vulnerabilities faced by an organization. It includes information regarding the multiple risks in terms of vulnerability exploited, impact level, likelihood of occurrence and control recommended. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Risk Register To Measure Cyber Attacks Vulnerabilities. Use it as a tool for discussion and navigation on Financial Transactions, Credentials Compromised, Cloud Network, Compromised. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Action Plan To Combat Cyber Crimes Risk Register To Measure Cyber Attacks Vulnerabilities
Action Plan To Combat Cyber Crimes Risk Register To Measure Cyber Attacks VulnerabilitiesThis slide indicates the risk register to measure the cyber attack risk vulnerabilities faced by an organization. It includes information regarding the multiple risks in terms of vulnerability exploited, impact level, likelihood of occurrence and control recommended. Present the topic in a bit more detail with this Action Plan To Combat Cyber Crimes Risk Register To Measure Cyber Attacks Vulnerabilities. Use it as a tool for discussion and navigation on Cloud Network Compromised, Financial Transactions, Credentials Compromised. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Compressive Planning Guide Risk Register To Measure Cyber Attacks Vulnerabilities
Compressive Planning Guide Risk Register To Measure Cyber Attacks VulnerabilitiesThis slide indicates the risk register to measure the cyber attack risk vulnerabilities faced by an organization. It includes information regarding the multiple risks in terms of vulnerability exploited, impact level, likelihood of occurrence and control recommended. Present the topic in a bit more detail with this Compressive Planning Guide Risk Register To Measure Cyber Attacks Vulnerabilities. Use it as a tool for discussion and navigation on Cyber Attack Risk Vulnerabilities, Vulnerability Exploited, Occurrence And Control Recommended. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Vulnerabilities Threats In Powerpoint And Google Slides Cpb
Information Security Vulnerabilities Threats In Powerpoint And Google Slides CpbPresenting Information Security Vulnerabilities Threats In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase Eight stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Information Security Vulnerabilities Threats. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cybersecurity Threats Vulnerabilities In Powerpoint And Google Slides Cpb
Cybersecurity Threats Vulnerabilities In Powerpoint And Google Slides CpbPresenting Cybersecurity Threats Vulnerabilities In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cybersecurity Threats Vulnerabilities. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Recent Cyber Security Vulnerabilities In Powerpoint And Google Slides Cpb
Recent Cyber Security Vulnerabilities In Powerpoint And Google Slides CpbPresenting our Recent Cyber Security Vulnerabilities In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Recent Cyber Security Vulnerabilities This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Corporate Compliance Strategy Identifying Potential Areas Of Risk And Vulnerability Strategy SS V
Corporate Compliance Strategy Identifying Potential Areas Of Risk And Vulnerability Strategy SS VThis slide presents key methods for locatingcompliancesweakspotsandriskyplaces in business. It includes methods such as risk assessment, compliance audits, incident and complaint analysis, benchmarking and expert opinion. Increase audience engagement and knowledge by dispensing information using Corporate Compliance Strategy Identifying Potential Areas Of Risk And Vulnerability Strategy SS V This template helps you present information on Five stages. You can also present information on Establishing Regulatory Policies, Establishing Code Of Conducts, Compliance Risk Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Smart Contract Vulnerabilities In Powerpoint And Google Slides Cpb
Smart Contract Vulnerabilities In Powerpoint And Google Slides CpbPresenting our Smart Contract Vulnerabilities In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Smart Contract Vulnerabilities. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Employee And Workplace Identifying Potential Areas Of Risk And Vulnerability Within Strategy SS V
Employee And Workplace Identifying Potential Areas Of Risk And Vulnerability Within Strategy SS VThis slide presents key methods for locatingcompliancesweakspotsandriskyplaces in business. It includes methods such as risk assessment, compliance audits, incident and complaint analysis, benchmarking and expert opinion. Introducing Employee And Workplace Identifying Potential Areas Of Risk And Vulnerability Within Strategy SS V to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on HR Compliance Examples, Compliance Requirements, Legislative Changes using this template. Grab it now to reap its full benefits.




