Powerpoint Templates and Google slides for Threats.
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Addressing Threats Associated With Apple That Negatively Strategic Brand Plan Apple
Addressing Threats Associated With Apple That Negatively Strategic Brand Plan AppleThis slide provides information regarding threats of brand that impose negative impact over firms success. Key Apples threats include rigorous competition, lawsuits, pandemic, etc. Introducing Addressing Threats Associated With Apple That Negatively Strategic Brand Plan Apple to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Rigorous Competition, Lawsuits, Pandemic, using this template. Grab it now to reap its full benefits.
-
 Attributes And Motivation Drivers Of Cyber Security Threat Actors
Attributes And Motivation Drivers Of Cyber Security Threat ActorsThis slide illustrates major features and motivation drivers of cyber security hijackers who attack with an intention to gain from such activities. The major cyber security risk actors are nation states, cyber criminals, terrorist groups and insider threats Introducing our Attributes And Motivation Drivers Of Cyber Security Threat Actors set of slides. The topics discussed in these slides are Nation States, Cybercriminals . This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis Of Cyber Security Threat Assessment Tools
Comparative Analysis Of Cyber Security Threat Assessment ToolsThis slide provides a comparative analysis of various tools to detect and assess cyber security threats in the industry to gain insights about which tool to implement. The major tools are Nessus home, GFI Languard, QualysGuard and n Circle IP 360 Presenting our well structured Comparative Analysis Of Cyber Security Threat Assessment Tools. The topics discussed in this slide are Nessus Home, Compatible Mechanisms. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Controlling Insider And Outsider Cyber Security Threats
Controlling Insider And Outsider Cyber Security ThreatsThis slide brings forth strategic dimensions to control insider and outsider cyber security threats by business managers in order to bring about efficiency in business operations. Key steps covered are identify, monitor, encrypt, restrict, train and extend Presenting our set of slides with Controlling Insider And Outsider Cyber Security Threats. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Monitor, Encrypt.
-
 Cyber Security Threat And Network Hacking Icon
Cyber Security Threat And Network Hacking IconIntroducing our premium set of slides with Cyber Security Threat And Network Hacking Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Security, Network Hacking. So download instantly and tailor it with your information.
-
 Cyber Security Threat Detection And Response
Cyber Security Threat Detection And ResponseThis slide illustrates ways to detect cyber security risks that emerge in business organizations and provides techniques to respond to such attacks. The response techniques are to reduce access time, optimize operations of security centre, adopt proactive cybersecurity and set intruder traps Presenting our set of slides with Cyber Security Threat Detection And Response. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Reduce Access Time, Set Intruder Traps.
-
 Cyber Security Threat Management Flow Chart
Cyber Security Threat Management Flow ChartThis slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are Introducing our Cyber Security Threat Management Flow Chart set of slides. The topics discussed in these slides are Threat Analysis, Residual Risk Acceptable. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Threats Faced By Business Organizations
Cyber Security Threats Faced By Business OrganizationsThis slide covers various types of cyber security threats as faced by many organizations in their day to day working. The major cyber security risks are malware, phishing, denial of service attack, advanced persistent threats and ransomware Presenting our well structured Cyber Security Threats Faced By Business Organizations. The topics discussed in this slide are Malware, Phishing, Denial Of Service Attack. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Employee Training To Control Cyber Security Threats
Employee Training To Control Cyber Security ThreatsFollowing slide comprises of a list of training that can be imparted by human resource managers an information technology managers in order to reduce risk of cyber security threats. The trainings are in domain of document management, strong password, internet links and email Presenting our set of slides with Employee Training To Control Cyber Security Threats. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Document Management, Internet Links.
-
 Major Target Areas Of Cyber Security Threats
Major Target Areas Of Cyber Security ThreatsThe following slide consists of major target points of cyber security attacks aimed at accessing, changing, or destroying sensitive information extorting money from users or interrupting normal business processes. The major targets are electronic devices, critical information, financial resources and public opinion Presenting our set of slides with Major Target Areas Of Cyber Security Threats. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Critical Information, Financial Resources.
-
 Strategies To Reduce Cyber Security Threats
Strategies To Reduce Cyber Security ThreatsThis slide highlights major strategies as used by business organizations to reduce cyber security threats which hamper the functioning of business processes. The various strategies are to encrypt data, update software, monitor physical security, use strong passwords and install firewalls Introducing our premium set of slides with Strategies To Reduce Cyber Security Threats. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Encrypt Data, Install Firewalls. So download instantly and tailor it with your information.
-
 Techniques Used By Cyber Security Threat Actors
Techniques Used By Cyber Security Threat ActorsFollowing template depicts various techniques as deployed by cyber security risk hijackers to steal or leak information that might be critical for organizations success. The major techniques are bots, code injection, password cracking and person in the middle Presenting our set of slides with Techniques Used By Cyber Security Threat Actors. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Bots, Code Injection, Password Cracking.
-
 Top Rising Cyber Security Threats In 2023
Top Rising Cyber Security Threats In 2023This slide illustrates top threats which are emerging in the field of cyber security from the year 2023 onwards. The cyber security risks as covered in this template are crypto jacking, IoT attacks, smart medical devices, connected cars and third party attacks Introducing our premium set of slides with Top Rising Cyber Security Threats In 2023. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Crypto Jacking, Iot Attacks, Smart Medical Devices. So download instantly and tailor it with your information.
-
 Unauthorized Computer Access Icon Causing Cyber Security Threat
Unauthorized Computer Access Icon Causing Cyber Security ThreatPresenting our set of slides with Unauthorized Computer Access Icon Causing Cyber Security Threat. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Unauthorized, Computer Access.
-
 Business Threat Prevention Detection Correction Icon
Business Threat Prevention Detection Correction IconPresenting our set of slides with Business Threat Prevention Detection Correction Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Business Threat Prevention, Detection Correction Icon.
-
 Cyber Threat Prevention Detection Correction Icon
Cyber Threat Prevention Detection Correction IconIntroducing our premium set of slides with Cyber Threat Prevention Detection Correction Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Cyber Threat Prevention, Detection Correction Icon. So download instantly and tailor it with your information.
-
 Cyber Threat Prevention Detection Correction Plan
Cyber Threat Prevention Detection Correction PlanThis slide presents prevention, detection and correction plan for cybersecurity and management that helps in avoiding critical situations and data loss. It includes plan for technology, processes and human activity that takes place in organisation. Presenting our set of slides with Cyber Threat Prevention Detection Correction Plan. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Vulnerability, Prevention, Detection, Correction.
-
 Data Threats Prevention Detection Correction
Data Threats Prevention Detection CorrectionThis slide presents threat prevention detection and correction plan for data management that could help in avoiding serious outcomes and protecting data from ongoing security issues. It includes RBAC implementation, audits and backup API for data management. Introducing our premium set of slides with Data Threats Prevention Detection Correction. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Prevention, Detection, Correction. So download instantly and tailor it with your information.
-
 Prevention Detection Correction For Insider Threats
Prevention Detection Correction For Insider ThreatsThis slide presents prevention detection and correction plan for insider threats faced by companies that could help in determining potential vulnerabilities. It includes source, threat, risk, motivation, domain, indicators, protective, detective and corrective controls. Introducing our Prevention Detection Correction For Insider Threats set of slides. The topics discussed in these slides are Prevention Detection, Correction For Insider Threats. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 System Threat Prevention Detection Correction
System Threat Prevention Detection CorrectionPresenting our set of slides with System Threat Prevention Detection Correction. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on System Threat Prevention, Detection Correction.
-
 Apples Aspirational Storytelling Addressing Threats Associated With Apple Branding SS
Apples Aspirational Storytelling Addressing Threats Associated With Apple Branding SSThis slide provides information regarding threats of brand that impose negative impact over firms success. Key Apples threats include rigorous competition, lawsuits, pandemic, etc. Introducing Apples Aspirational Storytelling Addressing Threats Associated With Apple Branding SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Rigorous Competition, Technology Reform, Threat Of Counterfeits, using this template. Grab it now to reap its full benefits.
-
 Risk Management Plan To Manage Cyber Threats Strategic Initiatives To Boost IT Strategy SS V
Risk Management Plan To Manage Cyber Threats Strategic Initiatives To Boost IT Strategy SS VThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Increase audience engagement and knowledge by dispensing information using Risk Management Plan To Manage Cyber Threats Strategic Initiatives To Boost IT Strategy SS V. This template helps you present information on seven stages. You can also present information on Plan, Management, Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Market Analysis Pest Analysis To Understand Market Opportunities And Threats
Market Analysis Pest Analysis To Understand Market Opportunities And ThreatsThis slide provides a framework for understanding the external environment and identifying potential opportunities and threats to help make informed decisions. The slide covers political, economic, technological and socio cultural factors. Increase audience engagement and knowledge by dispensing information using Market Analysis Pest Analysis To Understand Market Opportunities And Threats This template helps you present information on four stages. You can also present information on Political Factors, Economic Factors, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Threats Employees In Powerpoint And Google Slides Cpb
Threats Employees In Powerpoint And Google Slides CpbPresenting our Threats Employees In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Threats Employees. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security Threat Examples In Powerpoint And Google Slides Cpb
Security Threat Examples In Powerpoint And Google Slides CpbPresenting Security Threat Examples In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Threat Examples This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Examples Internal Threats In Powerpoint And Google Slides Cpb
Examples Internal Threats In Powerpoint And Google Slides CpbPresenting our Examples Internal Threats In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Examples Internal Threats. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Insider Threat Program Example In Powerpoint And Google Slides Cpb
Insider Threat Program Example In Powerpoint And Google Slides CpbPresenting Insider Threat Program Example In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Insider Threat Program Example. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 SecOps Security Operations Threat Management Process Ppt Professional
SecOps Security Operations Threat Management Process Ppt ProfessionalThis slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. Present the topic in a bit more detail with this SecOps Security Operations Threat Management Process Ppt Professional. Use it as a tool for discussion and navigation on External Threat Intelligance, Behavioral Analytics . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SecOps Software Tools Based On Threats Ppt Powerpoint Presentation Infographics Show
SecOps Software Tools Based On Threats Ppt Powerpoint Presentation Infographics ShowThis slide talks about categorizing primary SecOps software tools based on threats. The purpose of this slide is to showcase the top software solutions for SecOps, including DNS security, network detection and response, anti phishing, data discovery, and packet level visibility. Introducing SecOps Software Tools Based On Threats Ppt Powerpoint Presentation Infographics Show to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Dns Security, Network Detectin Response, using this template. Grab it now to reap its full benefits.
-
 Recent Network Threats In Powerpoint And Google Slides Cpb
Recent Network Threats In Powerpoint And Google Slides CpbPresenting Recent Network Threats In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Recent Network Threats. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 General Mills Threats Rte Food Industry Report Part 1 Ppt Show Graphics Tutorials
General Mills Threats Rte Food Industry Report Part 1 Ppt Show Graphics TutorialsIncrease audience engagement and knowledge by dispensing information using General Mills Threats Rte Food Industry Report Part 1 Ppt Show Graphics Tutorials. This template helps you present information on two stages. You can also present information on Revenues, Convenience, Weakness using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Kellogg Threats Rte Food Industry Report Part 1 Ppt Show Graphics Download
Kellogg Threats Rte Food Industry Report Part 1 Ppt Show Graphics DownloadIncrease audience engagement and knowledge by dispensing information using Kellogg Threats Rte Food Industry Report Part 1 Ppt Show Graphics Download. This template helps you present information on three stages. You can also present information on Competition, Perception, Government using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
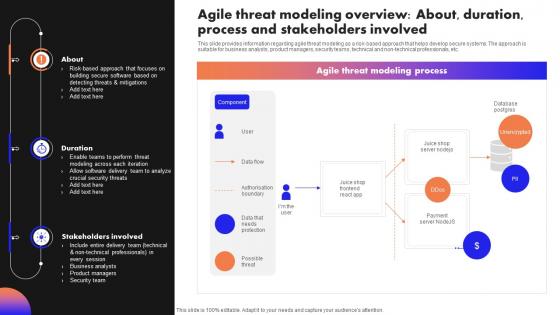 Ultimate Guide To Handle Business Agile Threat Modeling Overview About Duration Process
Ultimate Guide To Handle Business Agile Threat Modeling Overview About Duration ProcessThis slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Deliver an outstanding presentation on the topic using this Ultimate Guide To Handle Business Agile Threat Modeling Overview About Duration Process. Dispense information and present a thorough explanation of Database Postgres, Unencrypted, Stakeholders Involved, Crucial Security Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ultimate Guide To Handle Business Key Principles Associated With Agile Threat Modelling
Ultimate Guide To Handle Business Key Principles Associated With Agile Threat ModellingThis slide provides information regarding key principles associated with Agile threat modeling in terms of open up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Increase audience engagement and knowledge by dispensing information using Ultimate Guide To Handle Business Key Principles Associated With Agile Threat Modelling. This template helps you present information on three stages. You can also present information on Consider Stakeholder Values, Mitigate Critical Risks, Open Up Perspectives using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Smart Home Security Steps To Eliminate Threat
Smart Home Security Steps To Eliminate ThreatThis side showcase the steps to reduce the threats of smart home by creating solid defense for burglary and provides cybersecurity. It includes key elements such as door security, window reinforcement, save energy, garage protection and cybersecurity.Presenting our set of slides with Smart Home Security Steps To Eliminate Threat. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Door Security, Garage Protection, Customized Security.
-
 General Mills Threats Frozen Foods Detailed Industry Report Part 1 Ppt Icon Guidelines
General Mills Threats Frozen Foods Detailed Industry Report Part 1 Ppt Icon GuidelinesDeliver an outstanding presentation on the topic using this General Mills Threats Frozen Foods Detailed Industry Report Part 1 Ppt Icon Guidelines. Dispense information and present a thorough explanation of Concerns For Health, Competition, General Mills Threats, Pre Cooked Food Consumption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Kellogg Threats Frozen Foods Detailed Industry Report Part 1 Ppt Icon Designs Download
Kellogg Threats Frozen Foods Detailed Industry Report Part 1 Ppt Icon Designs DownloadIntroducing Kellogg Threats Frozen Foods Detailed Industry Report Part 1 Ppt Icon Designs Download to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Intense Competition, Everchanging Regulations, Meals And Processed Food, using this template. Grab it now to reap its full benefits.
-
 Competitive Business Threats Market And Product Development Strategies Strategy SS
Competitive Business Threats Market And Product Development Strategies Strategy SSThis slide showcases strengths analysis comparison matrix of own business and competitors to identify risks. It assess businesses based on competition, economic downtowns, change in regulations, technology evolution, supply chain disruptions. Introducing Competitive Business Threats Market And Product Development Strategies Strategy SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Industry, Customer, Opportunities, using this template. Grab it now to reap its full benefits.
-
 Agile Threat Modeling Overview About Guide To Manage Responsible Technology Playbook
Agile Threat Modeling Overview About Guide To Manage Responsible Technology PlaybookThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Deliver an outstanding presentation on the topic using this Agile Threat Modeling Overview About Guide To Manage Responsible Technology Playbook. Dispense information and present a thorough explanation of Overview, Stakeholders, Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Manage Agile Threat Modelling Guide To Manage Responsible Technology Playbook
Checklist To Manage Agile Threat Modelling Guide To Manage Responsible Technology PlaybookThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Present the topic in a bit more detail with this Checklist To Manage Agile Threat Modelling Guide To Manage Responsible Technology Playbook. Use it as a tool for discussion and navigation on Analysis, Collaboration, Resolution. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Principles Associated With Agile Threat Modelling Guide To Manage Responsible Technology Playbook
Key Principles Associated With Agile Threat Modelling Guide To Manage Responsible Technology PlaybookThis slide provides information regarding key principles associated with Agile threat modeling in terms of open-up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Increase audience engagement and knowledge by dispensing information using Key Principles Associated With Agile Threat Modelling Guide To Manage Responsible Technology Playbook. This template helps you present information on three stages. You can also present information on Open Up Perspectives, Mitigate Critical Risks, Consider Stakeholder Values using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Business Threats Examples In Powerpoint And Google Slides Cpb
Business Threats Examples In Powerpoint And Google Slides CpbPresenting our Business Threats Examples In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Business Threats Examples This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 General Mills Threats Convenience Food Industry Report Ppt Microsoft
General Mills Threats Convenience Food Industry Report Ppt MicrosoftIntroducing General Mills Threats Convenience Food Industry Report Ppt Microsoft to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Competition, Increased Concerns For Health, Threats, using this template. Grab it now to reap its full benefits.
-
 Kellogg Threats Convenience Food Industry Report Ppt Mockup
Kellogg Threats Convenience Food Industry Report Ppt MockupIntroducing Kellogg Threats Convenience Food Industry Report Ppt Mockup to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Intense Competition, Consumer Perception, Everchanging Regulations, using this template. Grab it now to reap its full benefits.
-
 Visibility And Threat Data Protection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Visibility And Threat Data Protection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon depicts visibility and threat detection, helping you to clearly identify any potential threats and take appropriate action. It is an effective visual aid for presentations, making it easier to explain complex concepts in a simple and straightforward way.
-
 Visibility And Threat Data Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Visibility And Threat Data Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is perfect for presentations on Visibility and Threat Detection. It features a silhouette of a person with a magnifying glass, representing the need to identify potential risks and threats. This icon is sure to help communicate your message in a visually appealing way.
-
 Visibility And Threat Detection Access Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Visibility And Threat Detection Access Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon depicts visibility and threat detection, helping you to clearly identify any potential threats and take appropriate action. It is an effective visual aid for presentations, making it easier to explain complex concepts in a simple and straightforward way.
-
 Visibility And Threat Detection Access Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Visibility And Threat Detection Access Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is perfect for presentations on Visibility and Threat Detection. It features a silhouette of a person with a magnifying glass, representing the need to identify potential risks and threats. This icon is sure to help communicate your message in a visually appealing way.
-
 Visibility And Threat Detection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Visibility And Threat Detection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon depicts visibility and threat detection, helping you to clearly identify any potential threats and take appropriate action. It is an effective visual aid for presentations, making it easier to explain complex concepts in a simple and straightforward way.
-
 Visibility And Threat Detection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Visibility And Threat Detection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is perfect for presentations on Visibility and Threat Detection. It features a silhouette of a person with a magnifying glass, representing the need to identify potential risks and threats. This icon is sure to help communicate your message in a visually appealing way.
-
 Key Stages Of Crisis Management Stage 1 Pre Crisis Analysis For Identifying Potential Threats
Key Stages Of Crisis Management Stage 1 Pre Crisis Analysis For Identifying Potential ThreatsThe slide illustrates the steps involved in pre crisis stage to minimize the potential threats. Various steps included are crisis anticipation, crisis communication team, selection and training of spokesperson, etc Introducing Key Stages Of Crisis Management Stage 1 Pre Crisis Analysis For Identifying Potential Threats to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Communication, Potential, Analysis, using this template. Grab it now to reap its full benefits.
-
 IT Risk Management Framework To Manage Security Threats Definitive Guide To Manage Strategy SS V
IT Risk Management Framework To Manage Security Threats Definitive Guide To Manage Strategy SS VThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Introducing IT Risk Management Framework To Manage Security Threats Definitive Guide To Manage Strategy SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Implement Enterprise Security Program, Implement Control Environment, Implement Security Processes, using this template. Grab it now to reap its full benefits.
-
 Risk Management Plan To Manage Cyber Threats Definitive Guide To Manage Strategy SS V
Risk Management Plan To Manage Cyber Threats Definitive Guide To Manage Strategy SS VThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Deliver an outstanding presentation on the topic using this Risk Management Plan To Manage Cyber Threats Definitive Guide To Manage Strategy SS V. Dispense information and present a thorough explanation of Management, Threat, Asset using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identify Threat And Generating Security Awareness Among Employees To Reduce
Identify Threat And Generating Security Awareness Among Employees To ReduceThe following slide highlights threats and vulnerabilities within companys information system to prevent adverse impact and severity. It includes elements such as unclear storage mechanism, inappropriate structure to privilege access, no framework to monitor user behavior etc. Deliver an outstanding presentation on the topic using this Identify Threat And Generating Security Awareness Among Employees To Reduce Dispense information and present a thorough explanation of Unclear Storage Mechanism, Monitor User Behaviour using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Communication Plan For It Asset Security Threats
Communication Plan For It Asset Security ThreatsThis slide consists of a communication plan that can be implemented by managers to safeguard IT assets from cyber threats and create an effective response plan. Major elements covered are IT security assets, risk, threat, risk impact, etc. Presenting our set of slides with Communication Plan For It Asset Security Threats This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on IT Security Assets, IT Servers
-
 Risk Threat Vulnerability Consequence In Powerpoint And Google Slides Cpb
Risk Threat Vulnerability Consequence In Powerpoint And Google Slides CpbPresenting Risk Threat Vulnerability Consequence In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Risk Threat Vulnerability Consequence. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Risk Identification To Reduce Threat Impact Ppt Powerpoint Presentation Portfolio Deck
Risk Identification To Reduce Threat Impact Ppt Powerpoint Presentation Portfolio DeckThis slide provides an overview of the risk identification to create a mitigation plan. The slide includes risk identification, assessment, prioritization analysis and mitigation. Present the topic in a bit more detail with this Risk Identification To Reduce Threat Impact Ppt Powerpoint Presentation Portfolio Deck Use it as a tool for discussion and navigation on Risk Identification, Risk Impact Assessment This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threat Intelligence Analyst Job Description In Powerpoint And Google Slides Cpb
Cyber Threat Intelligence Analyst Job Description In Powerpoint And Google Slides CpbPresenting our Cyber Threat Intelligence Analyst Job Description In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cyber Threat Intelligence Analyst Job Description. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cybersecurity Threats In Powerpoint And Google Slides Cpb
Cybersecurity Threats In Powerpoint And Google Slides CpbPresenting our Cybersecurity Threats In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases Two stages. It is useful to share insightful information on Cybersecurity Threats This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Global Cyber Threats In Powerpoint And Google Slides Cpb
Global Cyber Threats In Powerpoint And Google Slides CpbPresenting our Global Cyber Threats In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Global Cyber Threats. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.





