Powerpoint Templates and Google slides for Threats.
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Virus Threat Sources Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Virus Threat Sources Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Virus threat sources colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Virus Threat Sources Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Virus Threat Sources Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Virus threat sources monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Four Workplace Safety And Security Threats
Four Workplace Safety And Security ThreatsThis slide shows the types of workplace security threats. It includes theft, IT failure, cyber attacks and supply chain disruption. Presenting our set of slides with Four Workplace Safety And Security Threats. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Physical Or Intellectual Assets Theft, Cctvs Installation, Communication Network.
-
 Threat Climate Change In Powerpoint And Google Slides Cpb
Threat Climate Change In Powerpoint And Google Slides CpbPresenting Threat Climate Change In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Threat Climate Change. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 In And Out Scope Threat Vectors For Confidential Computing Confidential Cloud Computing
In And Out Scope Threat Vectors For Confidential Computing Confidential Cloud ComputingThis slide represents the in-scope and out-of-scope threat for confidential computing. The purpose of this slide is to showcase the threats that confidential computing handles, such as software, protocol, cryptographic and physical attacks. It also caters to the out of scope threats such as sophisticated physical and upstream hardware supply-chain attacks. Deliver an outstanding presentation on the topic using this In And Out Scope Threat Vectors For Confidential Computing Confidential Cloud Computing. Dispense information and present a thorough explanation of Software Attacks, Protocol Attacks, Cryptographic Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Competitors Threats In Powerpoint And Google Slides Cpb
Competitors Threats In Powerpoint And Google Slides CpbPresenting Competitors Threats In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Competitors Threats. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 E Security Steps To Mitigate Cyber Threats
E Security Steps To Mitigate Cyber ThreatsThis slide mentions the e-security steps implemented to mitigate cyber threats and protect user data. It includes using strong password, device protection, additional authentication, storing essential data and reviewing third party integrations. Introducing our premium set of slides with E Security Steps To Mitigate Cyber Threats. Elucidate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Additional Authentication, Device Protection, Store Essential Data. So download instantly and tailor it with your information.
-
 E Security Threats And Solutions For Ecommerce Business
E Security Threats And Solutions For Ecommerce BusinessThis slide mentions Esecurity threats and solutions for ecommerce business to ensure protection from cyber attacks. The basis include financial frauds, phishing, DdoS attacks and brute force attacks. Presenting our well structured E Security Threats And Solutions For Ecommerce Business. The topics discussed in this slide are Financial Frauds, Phishing, Brute Force Attacks. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
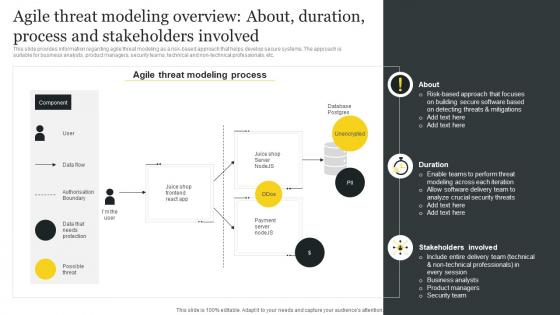 Responsible Tech Playbook To Leverage Agile Threat Modeling Overview About Duration Process
Responsible Tech Playbook To Leverage Agile Threat Modeling Overview About Duration ProcessThis slide provides information regarding agile threat modeling as a risk based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non technical professionals, etc. Present the topic in a bit more detail with this Responsible Tech Playbook To Leverage Agile Threat Modeling Overview About Duration Process. Use it as a tool for discussion and navigation on Stakeholders Involved, Duration, Agile Threat, Modeling Process. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Responsible Tech Playbook To Leverage Checklist To Manage Agile Threat Modelling Ppt Ideas Tips
Responsible Tech Playbook To Leverage Checklist To Manage Agile Threat Modelling Ppt Ideas TipsThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Deliver an outstanding presentation on the topic using this Responsible Tech Playbook To Leverage Checklist To Manage Agile Threat Modelling Ppt Ideas Tips. Dispense information and present a thorough explanation of Collaborate With Delivery Team, Analyze Threats, Prioritization And Resolve Issues using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Responsible Tech Playbook To Leverage Key Principles Associated With Agile Threat Modelling
Responsible Tech Playbook To Leverage Key Principles Associated With Agile Threat ModellingThis slide provides information regarding key principles associated with Agile threat modeling in terms of open up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Introducing Responsible Tech Playbook To Leverage Key Principles Associated With Agile Threat Modelling to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Mitigate Critical Risks, Consider Stakeholder Values, Agile Threat Modelling, using this template. Grab it now to reap its full benefits.
-
 Different Types Threats Commerce In Powerpoint And Google Slides Cpb
Different Types Threats Commerce In Powerpoint And Google Slides CpbPresenting our Different Types Threats Commerce In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Different Types Threats Commerce This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cybersecurity In Healthcare To Protect Against Threats
Cybersecurity In Healthcare To Protect Against ThreatsThis slide depicts the flowchart used to provide details related to cybersecurity in healthcare sector. The purpose of this template is to define different threat vectors and security dimensions It includes information related to security dimensions, vulnerabilities and threats. Presenting our well structured Cybersecurity In Healthcare To Protect Against Threats. The topics discussed in this slide are Access Control, Data Confidentiality, Communication Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Against Cyber Threats In Healthcare Sector
Security Against Cyber Threats In Healthcare SectorThis slide covers the details related to the healthcare assets and its security measures. The purpose of this template is to define cyber security in healthcare sector which involves the protection of electronic information and assets from unauthorized access, use and disclosure. It also includes elements such as emails, physical security and legal systems. Introducing our premium set of slides with name Security Against Cyber Threats In Healthcare Sector. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Emails, Physical Security, Legacy Systems. So download instantly and tailor it with your information.
-
 Security Threats Commerce Attacking Methods In Powerpoint And Google Slides Cpb
Security Threats Commerce Attacking Methods In Powerpoint And Google Slides CpbPresenting Security Threats Commerce Attacking Methods In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Threats Commerce Attacking Methods. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Commerce Security Threats In Powerpoint And Google Slides Cpb
Commerce Security Threats In Powerpoint And Google Slides CpbPresenting our Commerce Security Threats In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Commerce Security Threats. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Commerce Threats In Powerpoint And Google Slides Cpb
Commerce Threats In Powerpoint And Google Slides CpbPresenting Commerce Threats In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Commerce Threats. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Competitive Business Threats Analysis Key Strategies For Organization Growth And Development Strategy SS V
Competitive Business Threats Analysis Key Strategies For Organization Growth And Development Strategy SS VThis slide showcases strengths analysis comparison matrix of own business and competitors to identify risks. It assess businesses based on competition, economic downtowns, change in regulations, technology evolution, supply chain disruptions. Present the topic in a bit more detail with this Competitive Business Threats Analysis Key Strategies For Organization Growth And Development Strategy SS V. Use it as a tool for discussion and navigation on Competitive Business, Threats Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Malware Attack Icon To Prevent Threat
Malware Attack Icon To Prevent ThreatPresenting our well structured Malware Attack Icon To Prevent Threat. The topics discussed in this slide are Malware Attack Icon, Prevent Threat. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Emerging Cyber Threats In Powerpoint And Google Slides Cpb
Emerging Cyber Threats In Powerpoint And Google Slides CpbPresenting Emerging Cyber Threats In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Emerging Cyber Threats. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Agile Threat Modeling Overview About Duration Process Stakeholders Ethical Tech Governance Playbook
Agile Threat Modeling Overview About Duration Process Stakeholders Ethical Tech Governance PlaybookThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Present the topic in a bit more detail with this Agile Threat Modeling Overview About Duration Process Stakeholders Ethical Tech Governance Playbook. Use it as a tool for discussion and navigation on Overview, Process, Stakeholders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Manage Agile Threat Modelling Ethical Tech Governance Playbook
Checklist To Manage Agile Threat Modelling Ethical Tech Governance PlaybookThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Deliver an outstanding presentation on the topic using this Checklist To Manage Agile Threat Modelling Ethical Tech Governance Playbook. Dispense information and present a thorough explanation of Analyze Threats, Prioritization And Resolve Issues, Collaborate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Principles Associated With Agile Threat Modelling Ethical Tech Governance Playbook
Key Principles Associated With Agile Threat Modelling Ethical Tech Governance PlaybookThis slide provides information regarding key principles associated with Agile threat modeling in terms of open-up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Increase audience engagement and knowledge by dispensing information using Key Principles Associated With Agile Threat Modelling Ethical Tech Governance Playbook. This template helps you present information on three stages. You can also present information on Open Up Perspectives, Mitigate Critical Risks, Consider Stakeholder Values using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Alternative Threat Of Substitutes Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Alternative Threat Of Substitutes Colored Icon In Powerpoint Pptx Png And Editable Eps FormatA coloured PowerPoint icon depicting the threat of substitutes in a market. Illustrates the competitive pressure on companies from other products and services that can be used as an alternative. Perfect for presentations on market analysis and business strategy.
-
 Alternative Threat Of Substitutes Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Alternative Threat Of Substitutes Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is an essential visual aid for any presentation on the threat of substitutes. It is a simple yet effective illustration of the concept, providing a clear and concise representation of the concept. It is a great way to effectively communicate the concept to an audience.
-
 Person Threat Of Substitutes Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Person Threat Of Substitutes Colored Icon In Powerpoint Pptx Png And Editable Eps FormatA coloured PowerPoint icon depicting the threat of substitutes in a market. Illustrates the competitive pressure on companies from other products and services that can be used as an alternative. Perfect for presentations on market analysis and business strategy.
-
 Person Threat Of Substitutes Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Person Threat Of Substitutes Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is an essential visual aid for any presentation on the threat of substitutes. It is a simple yet effective illustration of the concept, providing a clear and concise representation of the concept. It is a great way to effectively communicate the concept to an audience.
-
 Substitute Goods Threat Substitutes Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Substitute Goods Threat Substitutes Colored Icon In Powerpoint Pptx Png And Editable Eps FormatA coloured PowerPoint icon depicting the threat of substitutes in a market. Illustrates the competitive pressure on companies from other products and services that can be used as an alternative. Perfect for presentations on market analysis and business strategy.
-
 Substitute Goods Threat Substitutes Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Substitute Goods Threat Substitutes Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is an essential visual aid for any presentation on the threat of substitutes. It is a simple yet effective illustration of the concept, providing a clear and concise representation of the concept. It is a great way to effectively communicate the concept to an audience.
-
 Smart Home System Security Threats Iot Smart Homes Automation IOT SS
Smart Home System Security Threats Iot Smart Homes Automation IOT SSThis slide provides an overview of the threats to smart house systems and their solution. Major threats covered are device hacking, distributed denial of service, data and identity theft. Present the topic in a bit more detail with this Smart Home System Security Threats Iot Smart Homes Automation IOT SS. Use it as a tool for discussion and navigation on Fraudulent, Transactions, Interrupting. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comprehensive Guide For Successful Types Of Website Security Threats And Vulnerabilities
Comprehensive Guide For Successful Types Of Website Security Threats And VulnerabilitiesFollowing slide exhibits types of security threats that negatively affect website operational efficiency and goodwill. It include types such as malware, viruses, spam links, DDoS with examples, impact and mitigation tools. Increase audience engagement and knowledge by dispensing information using Comprehensive Guide For Successful Types Of Website Security Threats And Vulnerabilities. This template helps you present information on three stages. You can also present information on Malware And Viruses, Spam Links, Denial Of Service Attacks, Website Security Threats, Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Web Browser Threat Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Web Browser Threat Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is a great way to visually represent danger on your website. It features a bright red triangle with an exclamation mark in the middle, making it easy to spot and understand the message of danger. Perfect for any website that needs to warn users of potential risks.
-
 Web Browser Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Web Browser Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is perfect for presentations, websites, and other digital projects. It features a simple, modern design that is sure to make a statement. It is easy to use and will add a professional touch to your work. It is also available in multiple sizes to fit any project.
-
 Website Online Threats Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Website Online Threats Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is a great way to visually represent danger on your website. It features a bright red triangle with an exclamation mark in the middle, making it easy to spot and understand the message of danger. Perfect for any website that needs to warn users of potential risks.
-
 Website Online Threats Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Website Online Threats Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is perfect for presentations, websites, and other digital projects. It features a simple, modern design that is sure to make a statement. It is easy to use and will add a professional touch to your work. It is also available in multiple sizes to fit any project.
-
 Website Threats Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Website Threats Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis colourful PowerPoint icon is a great way to visually represent danger on your website. It features a bright red triangle with an exclamation mark in the middle, making it easy to spot and understand the message of danger. Perfect for any website that needs to warn users of potential risks.
-
 Website Threats Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Website Threats Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is perfect for presentations, websites, and other digital projects. It features a simple, modern design that is sure to make a statement. It is easy to use and will add a professional touch to your work. It is also available in multiple sizes to fit any project.
-
 Potential Supply Chain Security Threats
Potential Supply Chain Security ThreatsThe following slide highlights potential threats hampering supply chain securityleading to failure of critical information technology systems and data breaches. It includes threats such as unauthorized access, internal fraud in international supply chain and internal fraud in software. Introducing our premium set of slides with Potential Supply Chain Security Threats Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Track Container Compliance, Track Container Compliance. So download instantly and tailor it with your information.
-
 Building Responsible Organization Agile Threat Modeling Overview About Duration Process
Building Responsible Organization Agile Threat Modeling Overview About Duration ProcessThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Introducing Building Responsible Organization Agile Threat Modeling Overview About Duration Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Agile Threat Modeling Overview, Stakeholders Involved, Security Teams, Technical And Non Technical Professionals , using this template. Grab it now to reap its full benefits.
-
 Building Responsible Organization Checklist To Manage Agile Threat Modelling
Building Responsible Organization Checklist To Manage Agile Threat ModellingThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Present the topic in a bit more detail with this Building Responsible Organization Checklist To Manage Agile Threat Modelling. Use it as a tool for discussion and navigation on Threat Modeling Sessions, Technical Diagram Highlighting, Agile Threat Modelling. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building Responsible Organization Key Principles Associated With Agile Threat Modelling
Building Responsible Organization Key Principles Associated With Agile Threat ModellingThis slide provides information regarding key principles associated with Agile threat modeling in terms of open-up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Introducing Building Responsible Organization Key Principles Associated With Agile Threat Modelling to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Open Up Perspectives, Mitigate Critical Risks, Consider Stakeholder Values, using this template. Grab it now to reap its full benefits.
-
 Data Loss Threat Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Loss Threat Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is perfect for presentations on data loss. It features a colourful depiction of a broken hard drive, symbolizing the potential consequences of data loss. Use it to emphasize the importance of data security and backup solutions.
-
 Data Loss Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Loss Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is a perfect visual representation of data loss. It is a simple yet powerful graphic that conveys the message of data loss in a clear and concise way. It is the perfect addition to any presentation on data security and data loss prevention.
-
 Strength Weakness Opportunity Threat Of Affiliate Marketing
Strength Weakness Opportunity Threat Of Affiliate MarketingThis slide covers SWOT analysis of affiliate marketing to evaluate future growth and customer engagement over websites through affiliates. It includes strength, weakness, opportunity and threats of affiliate marketing in promotion of products Introducing our Strength Weakness Opportunity Threat Of Affiliate Marketing set of slides. The topics discussed in these slides are Threat, Opportunity, Strength. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Security Threats Detection Techniques Incident Response Strategies Deployment
Cyber Security Threats Detection Techniques Incident Response Strategies DeploymentThis slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Introducing Cyber Security Threats Detection Techniques Incident Response Strategies Deployment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Threat, Analytics, Intruder, using this template. Grab it now to reap its full benefits.
-
 Addressing Threat Management Team Training Schedule Managing IT Threats At Workplace Overview
Addressing Threat Management Team Training Schedule Managing IT Threats At Workplace OverviewThe threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Present the topic in a bit more detail with this Addressing Threat Management Team Training Schedule Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Description, Audience, Frequency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices To Ensure Cybersecurity At Workplace Managing IT Threats At Workplace Overview
Best Practices To Ensure Cybersecurity At Workplace Managing IT Threats At Workplace OverviewThis slide provides details regarding best practices to enable cybersecurity at workplace in terms of data backup, enable compliance, phishing simulations, employees training, etc. Introducing Best Practices To Ensure Cybersecurity At Workplace Managing IT Threats At Workplace Overview to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Employees, Develop, Security, using this template. Grab it now to reap its full benefits.
-
 Budget For Effective Threat Management At Workplace Managing IT Threats At Workplace Overview
Budget For Effective Threat Management At Workplace Managing IT Threats At Workplace OverviewFirm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Present the topic in a bit more detail with this Budget For Effective Threat Management At Workplace Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Software, Duration, Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Roadmap To Track Activities Across Firm Managing IT Threats At Workplace Overview
Cybersecurity Roadmap To Track Activities Across Firm Managing IT Threats At Workplace OverviewThis slide provides details regarding roadmap to track cybersecurity activities across firm on monthly basis in terms of security and compliance, backups, staff training. Deliver an outstanding presentation on the topic using this Cybersecurity Roadmap To Track Activities Across Firm Managing IT Threats At Workplace Overview. Dispense information and present a thorough explanation of Security, Backups, Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Staff Training Schedule For Skills Enhancement Managing IT Threats At Workplace Overview
Determine Staff Training Schedule For Skills Enhancement Managing IT Threats At Workplace OverviewThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an outstanding presentation on the topic using this Determine Staff Training Schedule For Skills Enhancement Managing IT Threats At Workplace Overview. Dispense information and present a thorough explanation of Packages, Training, Enhancement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Threat Management Team Structure Managing IT Threats At Workplace Overview
Determine Threat Management Team Structure Managing IT Threats At Workplace OverviewThe threat management team generally comprise of senior management personnel that have authority and resources to accelerate the company s internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Introducing Determine Threat Management Team Structure Managing IT Threats At Workplace Overview to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Determine, Threat Management, Team Structure, using this template. Grab it now to reap its full benefits.
-
 Enable Cybersecurity Compliance At Organization Managing IT Threats At Workplace Overview
Enable Cybersecurity Compliance At Organization Managing IT Threats At Workplace OverviewThis slide provides details regarding role of cybersecurity compliance at workplace. The importance of the security compliance include management of user trust, enhance business efficiency, secure brand reputation, etc. Increase audience engagement and knowledge by dispensing information using Enable Cybersecurity Compliance At Organization Managing IT Threats At Workplace Overview. This template helps you present information on eight stages. You can also present information on Cybersecurity, Confidentiality, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Highlighting Ongoing Cybersecurity Trends Across Globe Managing IT Threats At Workplace Overview
Highlighting Ongoing Cybersecurity Trends Across Globe Managing IT Threats At Workplace OverviewThis slide provides details regarding cybersecurity trends existing across globe in terms of rise in automotive hacking, IoT with 5G, cloud platform as potential vulnerable, etc. Introducing Highlighting Ongoing Cybersecurity Trends Across Globe Managing IT Threats At Workplace Overview to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Automotive, Artificial, Potential, using this template. Grab it now to reap its full benefits.
-
 Impact Analysis For Effective Threat Management In Securing Managing IT Threats At Workplace Overview
Impact Analysis For Effective Threat Management In Securing Managing IT Threats At Workplace OverviewThis slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Present the topic in a bit more detail with this Impact Analysis For Effective Threat Management In Securing Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Analysis, Threat Management, Securing Workplace. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Analysis Of Successful Threat Management Implementation Managing IT Threats At Workplace Overview
Impact Analysis Of Successful Threat Management Implementation Managing IT Threats At Workplace OverviewThis slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Introducing Impact Analysis Of Successful Threat Management Implementation Managing IT Threats At Workplace Overview to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Management, Incident, Satisfaction, using this template. Grab it now to reap its full benefits.
-
 Selecting Secured Threat Management Software Managing IT Threats At Workplace Overview
Selecting Secured Threat Management Software Managing IT Threats At Workplace OverviewThis slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an outstanding presentation on the topic using this Selecting Secured Threat Management Software Managing IT Threats At Workplace Overview. Dispense information and present a thorough explanation of Secured, Management, Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Major Threats That Creates Obstacles In Firm How Amazon Generates Revenues Across Globe
Major Threats That Creates Obstacles In Firm How Amazon Generates Revenues Across GlobeThis slide provides information regarding SWOT analysis technique utilized by Amazon to evaluate its competitive positioning. The slide highlighting threats faced by Amazon causing potential issues in terms of data and online privacy risk, aggressive pricing strategies, etc. Increase audience engagement and knowledge by dispensing information using Major Threats That Creates Obstacles In Firm How Amazon Generates Revenues Across Globe. This template helps you present information on four stages. You can also present information on Legislations And Regulations, Aggressive Pricing Strategies, Stiff Competition using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Management Capabilities Managing It Threats At Workplace Overview Technological Assessment Of Firm Current
Management Capabilities Managing It Threats At Workplace Overview Technological Assessment Of Firm CurrentThis slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Present the topic in a bit more detail with this Management Capabilities Managing It Threats At Workplace Overview Technological Assessment Of Firm Current. Use it as a tool for discussion and navigation on Management, Capabilities, Technological. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Managing It Threats At Workplace Overview
Table Of Contents Managing It Threats At Workplace OverviewIntroducing Table Of Contents Managing It Threats At Workplace Overview to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Threat, Leveraging, Budget, using this template. Grab it now to reap its full benefits.
-
 Amazon Strategic Plan To Emerge As Market Leader Major Threats That Creates Obstacles In Firm Growth
Amazon Strategic Plan To Emerge As Market Leader Major Threats That Creates Obstacles In Firm GrowthThis slide provides information regarding SWOT analysis technique utilized by Amazon to evaluate its competitive positioning. The slide highlighting threats faced by Amazon causing potential issues in terms of data and online privacy risk, aggressive pricing strategies, etc. Deliver an outstanding presentation on the topic using this Amazon Strategic Plan To Emerge As Market Leader Major Threats That Creates Obstacles In Firm Growth. Dispense information and present a thorough explanation of Aggressive Pricing Strategies, Stiff Competition, Growth using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





