Powerpoint Templates and Google slides for Threats.
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Threat Of Substitute Product Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Of Substitute Product Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Threat of substitute product monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Threat Of Substitute Products Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Of Substitute Products Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Threat of substitute products colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Threat Of Substitute Products Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Of Substitute Products Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Threat of substitute products monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Risk Management Plan To Mitigate Threats Implement Merchandise Improve Sales
Risk Management Plan To Mitigate Threats Implement Merchandise Improve SalesThis slide shows the risk management plan for retailers which includes status, description, probability, impact in terms of scope, quality, schedule and cost with mitigation actions, contingency funds and time, etc. Present the topic in a bit more detail with this Risk Management Plan To Mitigate Threats Implement Merchandise Improve Sales. Use it as a tool for discussion and navigation on Management, Contingency, Probability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist To Ensure Asset Protection From Internal Threats Security Incident Response Playbook
Checklist To Ensure Asset Protection From Internal Threats Security Incident Response PlaybookFollowing slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Deliver an outstanding presentation on the topic using this Checklist To Ensure Asset Protection From Internal Threats Security Incident Response Playbook. Dispense information and present a thorough explanation of Protection, Measures, Ensure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threat Facts Figures And Statistics Security Incident Response Playbook
Cyber Threat Facts Figures And Statistics Security Incident Response PlaybookThis slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack. Increase audience engagement and knowledge by dispensing information using Cyber Threat Facts Figures And Statistics Security Incident Response Playbook. This template helps you present information on six stages. You can also present information on Cyberattacks, Ransomware, Statistics using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Threat Vulnerability And Risk Mitigation Table
Threat Vulnerability And Risk Mitigation TableThis slide covers the risks assessment of companys information security to improve the clients safety and anticipate data vulnerability. It also includes threats, risks, assets and consequences with solutions. Introducing our Threat Vulnerability And Risk Mitigation Table set of slides. The topics discussed in these slides are Threat, Vulnerability, Risk, Solution. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Attack Threat On Web Applications
Cyber Attack Threat On Web ApplicationsThis slide defines the cyber attack threat on web applications. It includes information related to the attacks effecting the confidential data of users like malware, eavesdropping, password and session hijacking attack. Introducing our premium set of slides with Cyber Attack Threat On Web Applications. Elucidate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Password Attack, Malware Attack, Eavesdropping Attack, Session Hijacking Attacks. So download instantly and tailor it with your information.
-
 Strategic Tactical Operational Cyber Threat Intelligence
Strategic Tactical Operational Cyber Threat IntelligenceThis slide exhibits strategic tactical and operational levels of cyber threat intelligence to ensure data and software protection from threats. It includes identify reason, assist extent of breach, alert and identify prevention system and ensure safety in advance. Presenting our set of slides with Strategic Tactical Operational Cyber Threat Intelligence. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Strategic Cyber, Threat Intelligence, Tactical Cyber.
-
 B132 Table Of Contents For Enterprise Mobile Security For On Device Threat Detection
B132 Table Of Contents For Enterprise Mobile Security For On Device Threat DetectionIntroducing B132 Table Of Contents For Enterprise Mobile Security For On Device Threat Detection to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Determine Standard, Various Configuration, Features Associated, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Enterprise Mobile Security For On Device Threat Detection
Icons Slide For Enterprise Mobile Security For On Device Threat DetectionPresenting our well crafted Icons Slide For Enterprise Mobile Security For On Device Threat Detection set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly
-
 Table Of Contents For Enterprise Mobile Security For On Device Threat Detection
Table Of Contents For Enterprise Mobile Security For On Device Threat DetectionPresent the topic in a bit more detail with this Table Of Contents For Enterprise Mobile Security For On Device Threat Detection. Use it as a tool for discussion and navigation on Impact Assessment, Dashboard Assessment, Device Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
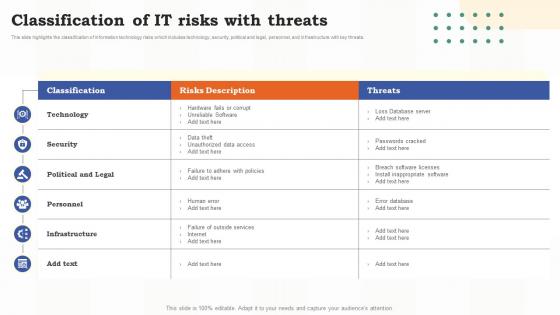 Classification Of It Risks With Threats Risk Assessment Of It Systems Ppt Slides Backgrounds
Classification Of It Risks With Threats Risk Assessment Of It Systems Ppt Slides BackgroundsThis slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Present the topic in a bit more detail with this Classification Of It Risks With Threats Risk Assessment Of It Systems Ppt Slides Backgrounds. Use it as a tool for discussion and navigation on Technology, Political And Legal, Infrastructure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Risks Form Human Threat Source Risk Assessment Of It Systems
Information Technology Risks Form Human Threat Source Risk Assessment Of It SystemsThis slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Present the topic in a bit more detail with this Information Technology Risks Form Human Threat Source Risk Assessment Of It Systems. Use it as a tool for discussion and navigation on Information, Technology, Source. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 It Vulnerabilities With Threat Source And Action Risk Assessment Of It Systems Ppt Slides Introduction
It Vulnerabilities With Threat Source And Action Risk Assessment Of It Systems Ppt Slides IntroductionThe following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Present the topic in a bit more detail with this It Vulnerabilities With Threat Source And Action Risk Assessment Of It Systems Ppt Slides Introduction. Use it as a tool for discussion and navigation on Vulnerabilities, Source, Information Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It Systems
Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It SystemsThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Prioritized Cyber Security Threats With Risk Mitigation Plan Risk Assessment Of It Systems. Use it as a tool for discussion and navigation on Mitigation Plan, Prioritized, Security Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Risk And Threat Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Information Risk And Threat Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Information risk and threat colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Information Risk And Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Information Risk And Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Information risk and threat monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Project Risk Management Plan With Opportunities And Threats
Project Risk Management Plan With Opportunities And ThreatsThis slide shows the risk management plan for managing project which includes identification of risk, performing qualitative and quantitative analysis, risk response planning, controlling and communicating risk with opportunities and threats. Introducing our Project Risk Management Plan With Opportunities And Threats set of slides. The topics discussed in these slides are Risk Management, Opportunities, Plan Risk Response. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Major Types Of E Banking Security Threats E Banking Management And Services
Major Types Of E Banking Security Threats E Banking Management And ServicesThis slide represents types of e banking security threats. It includes brute force, phishing, pharming, cross site scripting and trojan horse. Present the topic in a bit more detail with this Major Types Of E Banking Security Threats E Banking Management And Services. Use it as a tool for discussion and navigation on Pharming, Mitigation Strategies, E Banking Security Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Threats Challenges In Powerpoint And Google Slides Cpb
Cyber Security Threats Challenges In Powerpoint And Google Slides CpbPresenting Cyber Security Threats Challenges In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Security Threats Challenges. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Banks Threat Management In Powerpoint And Google Slides Cpb
Banks Threat Management In Powerpoint And Google Slides CpbPresenting Banks Threat Management In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Banks Threat Management. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Data Security Threats Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Threats Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Data security threats colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Data Security Threats Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Threats Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Data security threats monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Data Folder Security Threats Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Folder Security Threats Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Data folder security threats colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Data Folder Security Threats Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Folder Security Threats Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Data folder security threats monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Data Security Lock Threats Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Lock Threats Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Data security lock threats colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Data Security Lock Threats Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Security Lock Threats Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Data security lock threats monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Future Cyber Security Threats In Powerpoint And Google Slides Cpb
Future Cyber Security Threats In Powerpoint And Google Slides CpbPresenting Future Cyber Security Threats In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Future Cyber Security Threats. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Strength Weakness Opportunity Threat Analysis For Market Competitors
Strength Weakness Opportunity Threat Analysis For Market CompetitorsThis Slide illustrates strength weakness opportunity threat SWOT analysis for market competitors which contains distinctions and themes. Presenting our well-structured Strength Weakness Opportunity Threat Analysis For Market Competitors. The topics discussed in this slide are Strength, Weakness, Competitor. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Opportunity Threat In Powerpoint And Google Slides Cpb
Opportunity Threat In Powerpoint And Google Slides CpbPresenting our Opportunity Threat In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Opportunity Threat This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Key Security Considerations For 5g For Threat Handling Developing 5g Transformative Technology
Key Security Considerations For 5g For Threat Handling Developing 5g Transformative TechnologyThis slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an outstanding presentation on the topic using this Key Security Considerations For 5g For Threat Handling Developing 5g Transformative Technology. Dispense information and present a thorough explanation of Considerations, Unauthorized Activities, Unauthorized Activities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Current Cyber Threats In Powerpoint And Google Slides Cpb
Current Cyber Threats In Powerpoint And Google Slides CpbPresenting our Current Cyber Threats In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Current Cyber Threats This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Risk And Threats Landscape In Business Cybersecurity
Risk And Threats Landscape In Business CybersecurityThis slide showcases risk and threats landscape which can be referred by businesses to be aware of cybersecurity issues and attacks. It contains information about phishing, malware and blackmail hacking. Presenting our set of slides with Risk And Threats Landscape In Business Cybersecurity. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Phishing, Malware, Blackmail Hacking.
-
 Risk Landscape Icon For Financial Threat
Risk Landscape Icon For Financial ThreatPresenting our well structured Risk Landscape Icon For Financial Threat. The topics discussed in this slide are Risk Landscape Icon, Market Downfall. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Addressing Threats Associated With Apple That Negatively Impacts Business
Addressing Threats Associated With Apple That Negatively Impacts BusinessThis slide provides information regarding threats of brand that impose negative impact over firms success.Key Apples threats include rigorous competition, lawsuits, pandemic, etc.Introducing Addressing Threats Associated With Apple That Negatively Impacts Business to increase your presentation threshold.Encompassed with four stages, this template is a great option to educate and entice your audience.Dispence information on Rigorous Competition, Threat Counterfeits, Lawsuits, using this template.Grab it now to reap its full benefits.
-
 Business Cyber Security Program For Threat Prevention
Business Cyber Security Program For Threat PreventionThis slide covers business cyber security program for threat prevention which includes identify, protect, detect, respond and recover. Presenting our well structured Business Cyber Security Program For Threat Prevention. The topics discussed in this slide are Business Cyber, Security Program, Threat Prevention. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Business Integrated Security Control For Threat Prevention
Business Integrated Security Control For Threat PreventionThis slide covers business integrated security control for threat prevention which includes Business process and security system. Introducing our Business Integrated Security Control For Threat Prevention set of slides. The topics discussed in these slides are Integrated Security, Detection, Analysis. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Threats Supply Chain In Powerpoint And Google Slides Cpb
Threats Supply Chain In Powerpoint And Google Slides CpbPresenting our Threats Supply Chain In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Threats Supply Chain This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Personal Swot Threats In Powerpoint And Google Slides Cpb
Personal Swot Threats In Powerpoint And Google Slides CpbPresenting our Personal Swot Threats In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Personal Swot Threats. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Insider Threats Information Security In Powerpoint And Google Slides Cpb
Insider Threats Information Security In Powerpoint And Google Slides CpbPresenting our Insider Threats Information Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Insider Threats Information Security. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cybersecurity Threats Businesses In Powerpoint And Google Slides Cpb
Cybersecurity Threats Businesses In Powerpoint And Google Slides CpbPresenting our Cybersecurity Threats Businesses In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Cybersecurity Threats Businesses This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Strength Weakness Opportunities Threats In Powerpoint And Google Slides Cpb
Strength Weakness Opportunities Threats In Powerpoint And Google Slides CpbPresenting our Strength Weakness Opportunities Threats In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Strength Weakness Opportunities Threats. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Information System Security And Risk Administration Plan Identifying Information Security Threats And Impact
Information System Security And Risk Administration Plan Identifying Information Security Threats And ImpactThis slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. Increase audience engagement and knowledge by dispensing information using Information System Security And Risk Administration Plan Identifying Information Security Threats And Impact. This template helps you present information on one stages. You can also present information on Employee Sabotage, Physical Infrastructure Loss, Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information System Security And Risk Administration Risk Assessment Matrix With Vulnerability And Threat Level
Information System Security And Risk Administration Risk Assessment Matrix With Vulnerability And Threat LevelThis slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Present the topic in a bit more detail with this Information System Security And Risk Administration Risk Assessment Matrix With Vulnerability And Threat Level. Use it as a tool for discussion and navigation on Treat Level, Vulnerability Level, Risk Assessment Matrix. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Analysing The Impact Of Security Threats Information System Security And Risk Administration Plan
Analysing The Impact Of Security Threats Information System Security And Risk Administration PlanIncrease audience engagement and knowledge by dispensing information using Analysing The Impact Of Security Threats Information System Security And Risk Administration Plan. This template helps you present information on one stages. You can also present information on Security Threats, Malware, Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Matrix For Threat Solution And Risk Management Information System Security And Risk Administration Plan
Matrix For Threat Solution And Risk Management Information System Security And Risk Administration PlanThis slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Deliver an outstanding presentation on the topic using this Matrix For Threat Solution And Risk Management Information System Security And Risk Administration Plan. Dispense information and present a thorough explanation of Monitor Database Activity, Validate Database Protocols, Capture Detailed Transactions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mitigation Plan For Resolving Encountered Threat Information System Security And Risk Administration Plan
Mitigation Plan For Resolving Encountered Threat Information System Security And Risk Administration PlanMentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Present the topic in a bit more detail with this Mitigation Plan For Resolving Encountered Threat Information System Security And Risk Administration Plan. Use it as a tool for discussion and navigation on Risk Mitigation Plan, Customer Data, Web Servers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Identification And Vulnerability Assessment For Information System Security And Risk Administration Plan
Threat Identification And Vulnerability Assessment For Information System Security And Risk Administration PlanThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Deliver an outstanding presentation on the topic using this Threat Identification And Vulnerability Assessment For Information System Security And Risk Administration Plan. Dispense information and present a thorough explanation of Vulnerability Severity, Threat Source, Risk Rating using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Globalization Threats In Powerpoint And Google Slides Cpb
Globalization Threats In Powerpoint And Google Slides CpbPresenting our Globalization Threats In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Globalization Threats. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 New Cyber Security Threats In Powerpoint And Google Slides Cpb
New Cyber Security Threats In Powerpoint And Google Slides CpbPresenting our New Cyber Security Threats In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on New Cyber Security Threats This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber Security Threats Detection Techniques Ppt Powerpoint Presentation Professional Background
Cyber Security Threats Detection Techniques Ppt Powerpoint Presentation Professional BackgroundThis slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Introducing Cyber Security Threats Detection Techniques Ppt Powerpoint Presentation Professional Background to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Threat Intelligence, Intruder Traps, Threat Hunting, using this template. Grab it now to reap its full benefits.
-
 Enterprise Internal And External Threats Management Overview Of Enterprise Risk Management
Enterprise Internal And External Threats Management Overview Of Enterprise Risk ManagementThis slide represents details related to the risks faced by the organization due to internal factors and external factors. It includes details related to management of internal and external failures of the enterprise. Present the topic in a bit more detail with this Enterprise Internal And External Threats Management Overview Of Enterprise Risk Management. Use it as a tool for discussion and navigation on Management, Enterprise, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices For Threat Modeling Process
Best Practices For Threat Modeling ProcessThis slide shows best practices to assure efficiency in threat modeling process. It contains points such as documentation, develop schedule, set time frame, use existing resources, integration and suitable method. Presenting our set of slides with name Best Practices For Threat Modeling Process. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Documentation, Threat Modeling, Suitable Method.
-
 Business Application Threat Modeling Process
Business Application Threat Modeling ProcessThis slide contains application threat modeling process to evaluate and manage risks. It includes four steps identify fundamentals, data flow, security profile and recommendations. Introducing our premium set of slides with name Business Application Threat Modeling Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Determine, Security Profiles, Recommendations, Data Flow. So download instantly and tailor it with your information.
-
 Business Threat Modeling Process Icon
Business Threat Modeling Process IconPresenting our set of slides with name Business Threat Modeling Process Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Business, Threat, Modeling, Process Icon.
-
 Cyber Threat Prevention And Security Process
Cyber Threat Prevention And Security ProcessThis slide shows four steps to provide and assure protection against cyber threats. It includes steps secure perimeter, protect users, network segmentation, determine and control risks. Introducing our premium set of slides with name Cyber Threat Prevention And Security Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Secure Perimeter, Smart Network Segmentation, Determine And Control. So download instantly and tailor it with your information.
-
 Five Step Process Of Cyber Threat Hunting
Five Step Process Of Cyber Threat HuntingThis slide shows steps for effective and successful cyber security systems to prevent from threats.it contains steps hypothesis, process data, trigger, investigation and resolution. Presenting our set of slides with name Five Step Process Of Cyber Threat Hunting. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Hypothesis, Trigger, Resolution, Investigation.
-
 Insider Threat Mitigation And Protection Process
Insider Threat Mitigation And Protection ProcessThis slide includes steps to identify, manage and mitigate potential cyber threats. It includes four steps define, detect, assess and manage. Introducing our premium set of slides with name Insider Threat Mitigation And Protection Process. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Detect, Manage, Assess, Define. So download instantly and tailor it with your information.
-
 Key Steps Of Threat Modelling Process
Key Steps Of Threat Modelling ProcessThis slide exhibits steps of threat modelling process to identify security requirements in business systems. It includes five steps determine objectives, visualize, analyse risks, mitigate and validate. Presenting our set of slides with name Key Steps Of Threat Modelling Process. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Visualize, Validate, Analyse Risks, Mitigate.





