Powerpoint Templates and Google slides for Threat Management
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Addressing Threat Management Team Training Schedule Managing IT Threats At Workplace Overview
Addressing Threat Management Team Training Schedule Managing IT Threats At Workplace OverviewThe threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Present the topic in a bit more detail with this Addressing Threat Management Team Training Schedule Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Description, Audience, Frequency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices To Ensure Cybersecurity At Workplace Managing IT Threats At Workplace Overview
Best Practices To Ensure Cybersecurity At Workplace Managing IT Threats At Workplace OverviewThis slide provides details regarding best practices to enable cybersecurity at workplace in terms of data backup, enable compliance, phishing simulations, employees training, etc. Introducing Best Practices To Ensure Cybersecurity At Workplace Managing IT Threats At Workplace Overview to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Employees, Develop, Security, using this template. Grab it now to reap its full benefits.
-
 Budget For Effective Threat Management At Workplace Managing IT Threats At Workplace Overview
Budget For Effective Threat Management At Workplace Managing IT Threats At Workplace OverviewFirm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Present the topic in a bit more detail with this Budget For Effective Threat Management At Workplace Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Software, Duration, Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Roadmap To Track Activities Across Firm Managing IT Threats At Workplace Overview
Cybersecurity Roadmap To Track Activities Across Firm Managing IT Threats At Workplace OverviewThis slide provides details regarding roadmap to track cybersecurity activities across firm on monthly basis in terms of security and compliance, backups, staff training. Deliver an outstanding presentation on the topic using this Cybersecurity Roadmap To Track Activities Across Firm Managing IT Threats At Workplace Overview. Dispense information and present a thorough explanation of Security, Backups, Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Staff Training Schedule For Skills Enhancement Managing IT Threats At Workplace Overview
Determine Staff Training Schedule For Skills Enhancement Managing IT Threats At Workplace OverviewThe employees will also require external training which will play important role in their development. The external training will be given by experts of various fields. This training will not be free, and charges will cost the firm per employee. Deliver an outstanding presentation on the topic using this Determine Staff Training Schedule For Skills Enhancement Managing IT Threats At Workplace Overview. Dispense information and present a thorough explanation of Packages, Training, Enhancement using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Threat Management Team Structure Managing IT Threats At Workplace Overview
Determine Threat Management Team Structure Managing IT Threats At Workplace OverviewThe threat management team generally comprise of senior management personnel that have authority and resources to accelerate the company s internal incident response. They will be responsible in managing human impacts both employees and community, company reputation, share values, and corporate assets. Introducing Determine Threat Management Team Structure Managing IT Threats At Workplace Overview to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Determine, Threat Management, Team Structure, using this template. Grab it now to reap its full benefits.
-
 Enable Cybersecurity Compliance At Organization Managing IT Threats At Workplace Overview
Enable Cybersecurity Compliance At Organization Managing IT Threats At Workplace OverviewThis slide provides details regarding role of cybersecurity compliance at workplace. The importance of the security compliance include management of user trust, enhance business efficiency, secure brand reputation, etc. Increase audience engagement and knowledge by dispensing information using Enable Cybersecurity Compliance At Organization Managing IT Threats At Workplace Overview. This template helps you present information on eight stages. You can also present information on Cybersecurity, Confidentiality, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Highlighting Ongoing Cybersecurity Trends Across Globe Managing IT Threats At Workplace Overview
Highlighting Ongoing Cybersecurity Trends Across Globe Managing IT Threats At Workplace OverviewThis slide provides details regarding cybersecurity trends existing across globe in terms of rise in automotive hacking, IoT with 5G, cloud platform as potential vulnerable, etc. Introducing Highlighting Ongoing Cybersecurity Trends Across Globe Managing IT Threats At Workplace Overview to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Automotive, Artificial, Potential, using this template. Grab it now to reap its full benefits.
-
 Impact Analysis For Effective Threat Management In Securing Managing IT Threats At Workplace Overview
Impact Analysis For Effective Threat Management In Securing Managing IT Threats At Workplace OverviewThis slide portrays information regarding how firm is successful in handling security threats and is able in reducing the occurrence of threats. Present the topic in a bit more detail with this Impact Analysis For Effective Threat Management In Securing Managing IT Threats At Workplace Overview. Use it as a tool for discussion and navigation on Analysis, Threat Management, Securing Workplace. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Analysis Of Successful Threat Management Implementation Managing IT Threats At Workplace Overview
Impact Analysis Of Successful Threat Management Implementation Managing IT Threats At Workplace OverviewThis slide depicts the impact of successful implementation of threat management in terms improved incident management and customer satisfaction and depicts that how much the focus area has been improved from the previous state. Introducing Impact Analysis Of Successful Threat Management Implementation Managing IT Threats At Workplace Overview to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Management, Incident, Satisfaction, using this template. Grab it now to reap its full benefits.
-
 Selecting Secured Threat Management Software Managing IT Threats At Workplace Overview
Selecting Secured Threat Management Software Managing IT Threats At Workplace OverviewThis slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Deliver an outstanding presentation on the topic using this Selecting Secured Threat Management Software Managing IT Threats At Workplace Overview. Dispense information and present a thorough explanation of Secured, Management, Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Management Capabilities Managing It Threats At Workplace Overview Technological Assessment Of Firm Current
Management Capabilities Managing It Threats At Workplace Overview Technological Assessment Of Firm CurrentThis slide provides details regarding present management capabilities assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Present the topic in a bit more detail with this Management Capabilities Managing It Threats At Workplace Overview Technological Assessment Of Firm Current. Use it as a tool for discussion and navigation on Management, Capabilities, Technological. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Table Of Contents Managing It Threats At Workplace Overview
Table Of Contents Managing It Threats At Workplace OverviewIntroducing Table Of Contents Managing It Threats At Workplace Overview to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Threat, Leveraging, Budget, using this template. Grab it now to reap its full benefits.
-
 Strategic Initiatives Playbook IT Risk Management Framework To Manage Security Threats
Strategic Initiatives Playbook IT Risk Management Framework To Manage Security ThreatsThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Deliver an outstanding presentation on the topic using this Strategic Initiatives Playbook IT Risk Management Framework To Manage Security Threats. Dispense information and present a thorough explanation of IT Risk Management, Framework To Manage, Security Threats, Platform Upgradation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Initiatives Playbook Risk Management Plan To Manage Cyber Threats
Strategic Initiatives Playbook Risk Management Plan To Manage Cyber ThreatsThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Deliver an outstanding presentation on the topic using this Strategic Initiatives Playbook Risk Management Plan To Manage Cyber Threats. Dispense information and present a thorough explanation of Risk Management Plan, Manage Cyber Threats, Firewall Configurations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Operational Risk Management Risk Register To Assess Operational Threats
Operational Risk Management Risk Register To Assess Operational ThreatsThis slide shows the risk register to identify and analyze the probability and impact of the risks associated with day to day business operations of the organization. It includes details related to risk category, description, probability, impact etc. Present the topic in a bit more detail with this Operational Risk Management Risk Register To Assess Operational Threats. Use it as a tool for discussion and navigation on Risk Register, Assess Operational Threats, Consequence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Risk Management Framework To Manage Security Threats IT Cost Optimization And Management Strategy SS
IT Risk Management Framework To Manage Security Threats IT Cost Optimization And Management Strategy SSThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Present the topic in a bit more detail with this IT Risk Management Framework To Manage Security Threats IT Cost Optimization And Management Strategy SS. Use it as a tool for discussion and navigation on Implement Control Environment, Implement Security Processes, Enterprise Security Program. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Plan To Manage Cyber Threats IT Cost Optimization And Management Strategy SS
Risk Management Plan To Manage Cyber Threats IT Cost Optimization And Management Strategy SSThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Deliver an outstanding presentation on the topic using this Risk Management Plan To Manage Cyber Threats IT Cost Optimization And Management Strategy SS. Dispense information and present a thorough explanation of Threat, Vulnerability, Cyber Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Threats Detection Techniques Development And Implementation Of Security Incident Management
Cyber Security Threats Detection Techniques Development And Implementation Of Security Incident ManagementThis slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc. Present the topic in a bit more detail with this Cyber Security Threats Detection Techniques Development And Implementation Of Security Incident Management. Use it as a tool for discussion and navigation on Intruder Traps, Attacker And User Behavior Analytics, Threat Intelligence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Risk Management Framework To Manage Security Threats Develop Business Aligned IT Strategy
IT Risk Management Framework To Manage Security Threats Develop Business Aligned IT StrategyThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Increase audience engagement and knowledge by dispensing information using IT Risk Management Framework To Manage Security Threats Develop Business Aligned IT Strategy. This template helps you present information on three stages. You can also present information on Enterprise Security Program, Control Environment, Security Processes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Risk Management Plan To Manage Cyber Threats Develop Business Aligned IT Strategy
Risk Management Plan To Manage Cyber Threats Develop Business Aligned IT StrategyThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Deliver an outstanding presentation on the topic using this Risk Management Plan To Manage Cyber Threats Develop Business Aligned IT Strategy. Dispense information and present a thorough explanation of Vulnerability, Likelihood, Control Initiative, Natural Disaster using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Framework To Manage IT Risk Management Framework To Manage Security Threats Strategy SS
Strategic Framework To Manage IT Risk Management Framework To Manage Security Threats Strategy SSThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy. Deliver an outstanding presentation on the topic using this Strategic Framework To Manage IT Risk Management Framework To Manage Security Threats Strategy SS. Dispense information and present a thorough explanation of Implement Enterprise Security Program, Implement Control Environment, Implement Security Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Framework To Manage IT Risk Management Plan To Manage Cyber Threats Strategy SS
Strategic Framework To Manage IT Risk Management Plan To Manage Cyber Threats Strategy SSThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Present the topic in a bit more detail with this Strategic Framework To Manage IT Risk Management Plan To Manage Cyber Threats Strategy SS. Use it as a tool for discussion and navigation on Risk Management Plan, Manage Cyber Threats, Vulnerability, Control Initiative. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Threats Detection Techniques Deploying Computer Security Incident Management
Cyber Security Threats Detection Techniques Deploying Computer Security Incident ManagementThis slide represents the strategies to help incident management team to effectively detect the incidents faced by the organization. It includes threat detection techniques such as threat intelligence, intruder traps etc.Present the topic in a bit more detail with this Cyber Security Threats Detection Techniques Deploying Computer Security Incident Management. Use it as a tool for discussion and navigation on Threat Intelligence, Access Regularly, Undercovers Intruders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Plan To Manage Cyber Threats Comprehensive Plan To Ensure It And Business
Risk Management Plan To Manage Cyber Threats Comprehensive Plan To Ensure It And BusinessThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Present the topic in a bit more detail with this Risk Management Plan To Manage Cyber Threats Comprehensive Plan To Ensure It And Business. Use it as a tool for discussion and navigation on Management, Information, Vulnerability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Threats Risk Management Plan Handling Pivotal Assets Associated With Firm
Cyber Threats Risk Management Plan Handling Pivotal Assets Associated With FirmThis slide provides information regarding cyber threats risk management plan including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Present the topic in a bit more detail with this Cyber Threats Risk Management Plan Handling Pivotal Assets Associated With Firm. Use it as a tool for discussion and navigation on Management, Vulnerability, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Essential Initiatives To Safeguard Various It Threats Risk Management Plan
Essential Initiatives To Safeguard Various It Threats Risk Management PlanThis slide provides information regarding several IT threats risk management plan including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Present the topic in a bit more detail with this Essential Initiatives To Safeguard Various It Threats Risk Management Plan. Use it as a tool for discussion and navigation on Malicious Human Attack, Vulnerability, It Threats, Risk Management Plan This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Framework Checklist To Manage Threats
Cybersecurity Framework Checklist To Manage ThreatsMentioned slide depicts the comparison of cybersecurity framework tools such as nikto,cain and abel,nmap,acunetix,metasploit. It compare differences on the basis of tool category, features and cost etc. Introducing our Cybersecurity Framework Checklist To Manage Threats set of slides. The topics discussed in these slides are Identify, Protect, Respond. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 IT Strategy Planning Guide IT Risk Management Framework To Manage Security Threats Strategy SS V
IT Strategy Planning Guide IT Risk Management Framework To Manage Security Threats Strategy SS VThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Deliver an outstanding presentation on the topic using this IT Strategy Planning Guide IT Risk Management Framework To Manage Security Threats Strategy SS V. Dispense information and present a thorough explanation of IT Risk Management, Framework To Manage, Security Threats using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Strategy Planning Guide Risk Management Plan To Manage Cyber Threats Strategy SS V
IT Strategy Planning Guide Risk Management Plan To Manage Cyber Threats Strategy SS VThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Present the topic in a bit more detail with this IT Strategy Planning Guide Risk Management Plan To Manage Cyber Threats Strategy SS V. Use it as a tool for discussion and navigation on Risk Management Plan, Manage Cyber Threats, Natural Disaster, Website Resources Unavailability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Plan To Manage Cyber Threats Blueprint Develop Information It Roadmap Strategy Ss
Risk Management Plan To Manage Cyber Threats Blueprint Develop Information It Roadmap Strategy SsThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Present the topic in a bit more detail with this Risk Management Plan To Manage Cyber Threats Blueprint Develop Information It Roadmap Strategy Ss. Use it as a tool for discussion and navigation on Management, Information, Vulnerability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing Asset Security Categorization Cyber Threats Management To Enable Digital Assets Security
Addressing Asset Security Categorization Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Present the topic in a bit more detail with this Addressing Asset Security Categorization Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Categorization, Confidentiality, Availability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing Cyber Threats In Various Cyber Threats Management To Enable Digital Assets Security
Addressing Cyber Threats In Various Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding insider threats identified in various industries such as healthcare, manufacturing, government, energy, etc. Deliver an outstanding presentation on the topic using this Addressing Cyber Threats In Various Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Manufacturing, Government, Healthcare using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Addressing Indicators Associated Cyber Threats Management To Enable Digital Assets Security
Addressing Indicators Associated Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding indicators associated to insider threats in terms of traits, demeanor and goals, etc. Present the topic in a bit more detail with this Addressing Indicators Associated Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Unauthorized, Business, Authentication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets Security
Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding internal and external sources of threat data gathering with threat intelligence category. Deliver an outstanding presentation on the topic using this Addressing Internal And External Sources Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Targeted Intelligence, Malware Intelligence, Reputation Intelligence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Categorizing System Risk Associated With Cyber Threats Management To Enable Digital Assets Security
Categorizing System Risk Associated With Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information regarding system risk categorizations to enable cyber security. The categories assigned to system category is based on system confidentiality, integrity and availability. Deliver an outstanding presentation on the topic using this Categorizing System Risk Associated With Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Categorizing, Confidentiality, Information using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Track Cyber Risk Management Cyber Threats Management To Enable Digital Assets Security
Checklist To Track Cyber Risk Management Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information regarding checklist to monitor risk management plan initiatives in terms of detect valuable digital assets, assess security and threat levels, staff training, development of incident response plan, etc. Present the topic in a bit more detail with this Checklist To Track Cyber Risk Management Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Management, Initiatives, Development. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Various Cyber Threats Management To Enable Digital Assets Security
Comparative Assessment Of Various Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding comparative assessment of different threat agents on various parameters such as data loss impact, skills required to handle threat, etc. Deliver an outstanding presentation on the topic using this Comparative Assessment Of Various Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Comparative, Assessment, Parameters using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Contingency Plan For Cyber Threat Cyber Threats Management To Enable Digital Assets Security
Contingency Plan For Cyber Threat Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information contingency plan for handling threats with the help of technical equipment that assist contingency solution and considerations. Present the topic in a bit more detail with this Contingency Plan For Cyber Threat Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Contingency Solutions, Contingency Considerations, Information . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Several Threat Actors Profile Cyber Threats Management To Enable Digital Assets Security
Determine Several Threat Actors Profile Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding several threat actors profile such as cyber criminal and hacktivists and addressing them on parameters such as motive, intent, capability, action, target victim, etc. Present the topic in a bit more detail with this Determine Several Threat Actors Profile Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Parameters, Capability, Determine . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Determine Threat Scenario Analysis Cyber Threats Management To Enable Digital Assets Security
Determine Threat Scenario Analysis Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding threat scenario assessment by understanding various phases of threat actor attack on victim. Deliver an outstanding presentation on the topic using this Determine Threat Scenario Analysis Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Reconnaissance, Weaponization, Installation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Different Kinds Of Insider Digital Threats Cyber Threats Management To Enable Digital Assets Security
Different Kinds Of Insider Digital Threats Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding various kinds of insider digital threats such as malicious insider, negligent insider, third party insider, etc. Present the topic in a bit more detail with this Different Kinds Of Insider Digital Threats Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Malicious Insider, Negligent Or Careless Insider, Third Party Insider . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ensuring Collaboration Among Various Cyber Threats Management To Enable Digital Assets Security
Ensuring Collaboration Among Various Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding ensuring collaboration among various functional areas in order to minimize insider cyber threats. Introducing Ensuring Collaboration Among Various Cyber Threats Management To Enable Digital Assets Security to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Finance, Corporate Security, Business Division, using this template. Grab it now to reap its full benefits.
-
 Key Activities Checklist Associated To Insider Cyber Threats Management To Enable Digital Assets Security
Key Activities Checklist Associated To Insider Cyber Threats Management To Enable Digital Assets SecurityThis slide provides details regarding checklist associated to insider threat program in terms of plan and collect, review and analyze and strategic framework development. Increase audience engagement and knowledge by dispensing information using Key Activities Checklist Associated To Insider Cyber Threats Management To Enable Digital Assets Security. This template helps you present information on three stages. You can also present information on Plan And Collect, Review And Analyze, Strategic Framework using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets Security
Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets SecurityThis slide portrays information regarding potential technologies implemented to secure vulnerable systems. The systems include communication systems, bridge systems, access control system, core infrastructure system, etc. Deliver an outstanding presentation on the topic using this Potential Technologies Deployed To Secure Cyber Threats Management To Enable Digital Assets Security. Dispense information and present a thorough explanation of Potential, Technologies, Communication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents Cyber Threats Management To Enable Digital Assets Security
Table Of Contents Cyber Threats Management To Enable Digital Assets SecurityPresent the topic in a bit more detail with this Table Of Contents Cyber Threats Management To Enable Digital Assets Security. Use it as a tool for discussion and navigation on Categorizing, Associated, Determine Sequence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Communication Plan For Effective Threat Management
Communication Plan For Effective Threat ManagementThe slide exhibits risk communication plan to provide meaningful and relevant information to reduce the impact of threats that arise in business. It includes communication channel, content, duration etc to convey risk status. Introducing our Communication Plan For Effective Threat Management set of slides. The topics discussed in these slides are Management, Communication, Plan. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Several Threat Communication Barriers That Hinder Effective Management
Several Threat Communication Barriers That Hinder Effective ManagementThe following slide highlights various challenges in communicating so that management can eliminate these barriers and improve stakeholder opinion to promote accountability. The challenges are stakeholder diversification, Improper communication plan, Use of non standard language and Unsynchronized risk data. Presenting our set of slides with Several Threat Communication Barriers That Hinder Effective Management. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Stakeholder Diversification, Unsynchronized Risk Data, Improper Communication Plan.
-
 Threat Communication Timeline For Efficient Management
Threat Communication Timeline For Efficient ManagementThe following slide outlines communication timeline for effective risk assessment and helps in controlling crises and providing useful suggestions to eliminate them. It contains gathering risk information, accurate understanding, believing, restrictions, choosing alternative options etc. Presenting our well structured Threat Communication Timeline For Efficient Management. The topics discussed in this slide are Timeline, Communication, Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Ways To Minimize Communication Threat In Project Management
Ways To Minimize Communication Threat In Project ManagementThis slide showcases methods to communicate risk status to all shareholders foe effective project management. Its key methods are understanding communication tools, audience, stakeholders, setting objectives and staying positive. Introducing our premium set of slides with Ways To Minimize Communication Threat In Project Management. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Understand Stakeholders, Stay Positive, Set Objectives. So download instantly and tailor it with your information.
-
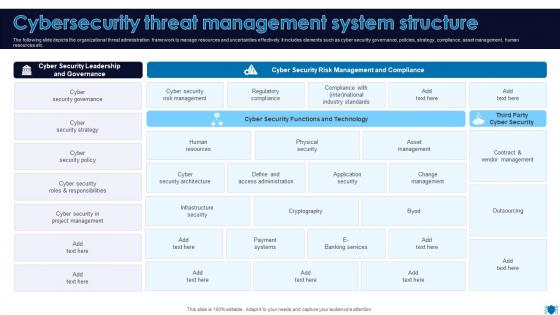 Cybersecurity Threat Management System Structure
Cybersecurity Threat Management System StructureThe following slide depicts the organizational threat administration framework to manage resources and uncertainties effectively. It includes elements such as cyber security governance, policies, strategy, compliance, asset management, human resources etc. Presenting our well structured Cybersecurity Threat Management System Structure. The topics discussed in this slide are Cyber Security Governance, Cyber Security Strategy, Cyber Security Policy. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Threat Management Flow Chart
Cyber Security Threat Management Flow ChartThis slide brings forth a diagrammatic representation of cyber security threat management model which can be used by business managers in order to counter advanced attacks by cybercriminals and take timely action. Key steps covered are Introducing our Cyber Security Threat Management Flow Chart set of slides. The topics discussed in these slides are Threat Analysis, Residual Risk Acceptable. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Risk Management Plan To Manage Cyber Threats Strategic Initiatives To Boost IT Strategy SS V
Risk Management Plan To Manage Cyber Threats Strategic Initiatives To Boost IT Strategy SS VThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Increase audience engagement and knowledge by dispensing information using Risk Management Plan To Manage Cyber Threats Strategic Initiatives To Boost IT Strategy SS V. This template helps you present information on seven stages. You can also present information on Plan, Management, Risk using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SecOps Security Operations Threat Management Process Ppt Professional
SecOps Security Operations Threat Management Process Ppt ProfessionalThis slide depicts the security operations threat management process. The purpose of this slide is to showcase the various stages and operations included in the security operations threat management process. The steps include discovery, preliminary investigation, triage, extended investigation, and contain and respond. Present the topic in a bit more detail with this SecOps Security Operations Threat Management Process Ppt Professional. Use it as a tool for discussion and navigation on External Threat Intelligance, Behavioral Analytics . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Agile Threat Modeling Overview About Guide To Manage Responsible Technology Playbook
Agile Threat Modeling Overview About Guide To Manage Responsible Technology PlaybookThis slide provides information regarding agile threat modeling as a risk-based approach that helps develop secure systems. The approach is suitable for business analysts, product managers, security teams, technical and non-technical professionals, etc. Deliver an outstanding presentation on the topic using this Agile Threat Modeling Overview About Guide To Manage Responsible Technology Playbook. Dispense information and present a thorough explanation of Overview, Stakeholders, Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Manage Agile Threat Modelling Guide To Manage Responsible Technology Playbook
Checklist To Manage Agile Threat Modelling Guide To Manage Responsible Technology PlaybookThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Present the topic in a bit more detail with this Checklist To Manage Agile Threat Modelling Guide To Manage Responsible Technology Playbook. Use it as a tool for discussion and navigation on Analysis, Collaboration, Resolution. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Principles Associated With Agile Threat Modelling Guide To Manage Responsible Technology Playbook
Key Principles Associated With Agile Threat Modelling Guide To Manage Responsible Technology PlaybookThis slide provides information regarding key principles associated with Agile threat modeling in terms of open-up perspectives, mitigating critical risks, considering stakeholders values. The purpose of principles is to develop technology in alignment with meeting stakeholders requirements, etc. Increase audience engagement and knowledge by dispensing information using Key Principles Associated With Agile Threat Modelling Guide To Manage Responsible Technology Playbook. This template helps you present information on three stages. You can also present information on Open Up Perspectives, Mitigate Critical Risks, Consider Stakeholder Values using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Stages Of Crisis Management Stage 1 Pre Crisis Analysis For Identifying Potential Threats
Key Stages Of Crisis Management Stage 1 Pre Crisis Analysis For Identifying Potential ThreatsThe slide illustrates the steps involved in pre crisis stage to minimize the potential threats. Various steps included are crisis anticipation, crisis communication team, selection and training of spokesperson, etc Introducing Key Stages Of Crisis Management Stage 1 Pre Crisis Analysis For Identifying Potential Threats to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Communication, Potential, Analysis, using this template. Grab it now to reap its full benefits.
-
 IT Risk Management Framework To Manage Security Threats Definitive Guide To Manage Strategy SS V
IT Risk Management Framework To Manage Security Threats Definitive Guide To Manage Strategy SS VThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Introducing IT Risk Management Framework To Manage Security Threats Definitive Guide To Manage Strategy SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Implement Enterprise Security Program, Implement Control Environment, Implement Security Processes, using this template. Grab it now to reap its full benefits.
-
 Risk Management Plan To Manage Cyber Threats Definitive Guide To Manage Strategy SS V
Risk Management Plan To Manage Cyber Threats Definitive Guide To Manage Strategy SS VThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Deliver an outstanding presentation on the topic using this Risk Management Plan To Manage Cyber Threats Definitive Guide To Manage Strategy SS V. Dispense information and present a thorough explanation of Management, Threat, Asset using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





