Powerpoint Templates and Google slides for Threat Management
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Vulnerability Administration At Workplace Budget For Effective Threat Management At Workplace
Vulnerability Administration At Workplace Budget For Effective Threat Management At WorkplaceFirm has prepared a budget for managing cybersecurity by optimizing various functional areas. It also provides information about the software used and the duration required for implementation. Deliver an outstanding presentation on the topic using this Vulnerability Administration At Workplace Budget For Effective Threat Management At Workplace. Dispense information and present a thorough explanation of Management, Workplace, Implementation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Vulnerability Administration At Workplace Selecting Secured Threat Management Software
Vulnerability Administration At Workplace Selecting Secured Threat Management SoftwareThis slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Present the topic in a bit more detail with this Vulnerability Administration At Workplace Selecting Secured Threat Management Software. Use it as a tool for discussion and navigation on Management, Software, Workflows. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Vulnerability Administration At Workplace Threat Management Action Plan
Vulnerability Administration At Workplace Threat Management Action Planthem. The person responsible in handling the threat will keep track of the threat resolve duration and will check whether the threat is treated or not. Present the topic in a bit more detail with this Vulnerability Administration At Workplace Threat Management Action Plan. Use it as a tool for discussion and navigation on Threat Management Action Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Vulnerability Administration At Workplace Threat Management Team Training Schedule
Vulnerability Administration At Workplace Threat Management Team Training ScheduleThe threat management team needs to have strong critical and creative thinking skills so that they become capable in taking key decisions without complete or conflicting information under immense tensed situations. The team will be trained by experts who will also use scenario based activities and costing will be per employee basis. Deliver an outstanding presentation on the topic using this Vulnerability Administration At Workplace Threat Management Team Training Schedule. Dispense information and present a thorough explanation of Management, Schedule, Employee using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enhancing overall project security it contingency plan for managing threats to ensure
Enhancing overall project security it contingency plan for managing threats to ensureThis slide provides information regarding contingency plan for managing threats to ensure IT project safety with aid of technical equipment ensuring contingency plans. Deliver an outstanding presentation on the topic using this Enhancing Overall Project Security It Contingency Plan For Managing Threats To Ensure. Dispense information and present a thorough explanation of Contingency Plan For Managing Threats To Ensure IT Project Safety using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
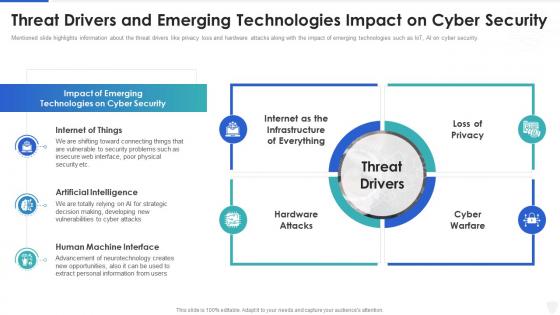 Cybersecurity and digital business risk management threat drivers and emerging technologies
Cybersecurity and digital business risk management threat drivers and emerging technologiesMentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Threat Drivers And Emerging Technologies. Dispense information and present a thorough explanation of Internet Of Things, Artificial Intelligence, Human Machine Interface using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
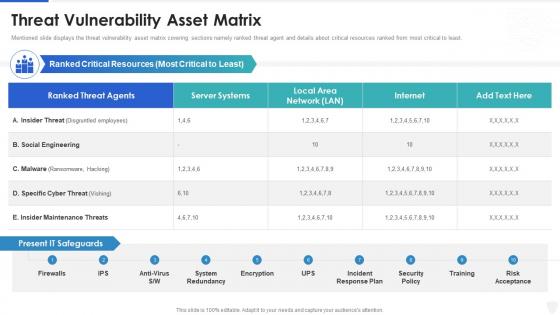 Cybersecurity and digital business risk management threat vulnerability asset matrix
Cybersecurity and digital business risk management threat vulnerability asset matrixMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Threat Vulnerability Asset Matrix. Dispense information and present a thorough explanation of Threat Vulnerability Asset Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Plan For Management Of Cyber Terrorism
Strategic Plan For Management Of Cyber TerrorismThis slide represents the plan to manage the attacks of cyber terrorism. It includes details related to metrics, what is measured, how is it measured and by whom the metrics are measured. Introducing our Strategic Plan For Management Of Cyber Terrorism set of slides. The topics discussed in these slides are Policy Violations, Training Completion, Strategic Plan. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Five Step Cybersecurity Threat Management Roadmap
Five Step Cybersecurity Threat Management RoadmapThis slide depicts cybersecurity roadmap for threat management illustrating five steps such as identification, analyzing, evaluation, responding and monitoring for identifying and analyzing potential cyber risk. Presenting our set of slides with name Five Step Cybersecurity Threat Management Roadmap. This exhibits information on five stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Analyzing, Identification, Responding, Monitoring, Evaluation.
-
 Insider Threat Management Plan With Case Status
Insider Threat Management Plan With Case StatusThis slide shows plan for managing insider risk with case status. It provides information about users, alert, status, severity, time detected, action plan, etc. Presenting our well-structured Insider Threat Management Plan With Case Status. The topics discussed in this slide are Insider Threat, Management Plan, Case Status. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Role Of Insider Threat Management Technologies In Banking Industry
Role Of Insider Threat Management Technologies In Banking IndustryThis slide shows role of insider threat management technologies in banking industry. It provides information about identifying user risk, protecting from data loss and accelerating threat response. Introducing our premium set of slides with Role Of Insider Threat Management Technologies In Banking Industry. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Identifying User Risk, Accelerating Threat Response, Protecting Data Loss. So download instantly and tailor it with your information.
-
 Product Planning Process Risk Management Plan To Mitigate Threats
Product Planning Process Risk Management Plan To Mitigate ThreatsThis slide shows the risk management plan for retailers which includes status, description, probability, impact in terms of scope, quality, schedule and cost with mitigation actions, contingency funds and time, etc. Present the topic in a bit more detail with this Product Planning Process Risk Management Plan To Mitigate Threats. Use it as a tool for discussion and navigation on Risk Description, Mitigation Actions, Medium, Low, High. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Managed Security Service Threat Detection Process
Managed Security Service Threat Detection ProcessThe following slide highlights multistep process of managed security service to mitigate IT risks. It covers step such as operational readiness review, use cases, email notification, security analysis and event resolution. Introducing our premium set of slides with Managed Security Service Threat Detection Process. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Event Resolution, Operational Readiness Review, Email Notification, Security Analysis. So download instantly and tailor it with your information.
-
 Various Cyber Security Threats And Strategies To Manage Network Service
Various Cyber Security Threats And Strategies To Manage Network ServiceThis slide highlights different types of cybersecurity threat such as malware, phishing, trojan horse and rootkit. The template also provides information about various strategies which will assist IT department to manage its network services. Introducing our premium set of slides with Various Cyber Security Threats And Strategies To Manage Network Service. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Strategies Overcome Threats, IT Security Services, Provide Security Awareness. So download instantly and tailor it with your information.
-
 F415 Risk Assessment And Management Plan For Information Security Analyzing Impact Security Threats
F415 Risk Assessment And Management Plan For Information Security Analyzing Impact Security ThreatsDeliver an outstanding presentation on the topic using this F415 Risk Assessment And Management Plan For Information Security Analyzing Impact Security Threats. Dispense information and present a thorough explanation of Analyzing, Organization, Financial using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identifying Information Security Threats And Risk Assessment And Management Plan For Information Security
Identifying Information Security Threats And Risk Assessment And Management Plan For Information SecurityThis slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization Deliver an outstanding presentation on the topic using this Identifying Information Security Threats And Risk Assessment And Management Plan For Information Security. Dispense information and present a thorough explanation of Organization, Errors And Omissions, Employee Sabotage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Matrix For Threat Solution And Risk Assessment And Management Plan For Information Security
Matrix For Threat Solution And Risk Assessment And Management Plan For Information SecurityThis slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack Present the topic in a bit more detail with this Matrix For Threat Solution And Risk Assessment And Management Plan For Information Security. Use it as a tool for discussion and navigation on Protocols, Management, Transactions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Plan To Mitigate Threats Retail Merchandising Plan
Risk Management Plan To Mitigate Threats Retail Merchandising PlanThis slide shows the risk management plan for retailers which includes status, description, probability, impact in terms of scope, quality, schedule and cost with mitigation actions, contingency funds and time, etc. Deliver an outstanding presentation on the topic using this Risk Management Plan To Mitigate Threats Retail Merchandising Plan. Dispense information and present a thorough explanation of Residual Risk, Cost, Revised Probability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Process Of Merchandise Planning In Retail Risk Management Plan To Mitigate Threats
Process Of Merchandise Planning In Retail Risk Management Plan To Mitigate ThreatsThis slide shows the risk management plan for retailers which includes status, description, probability, impact in terms of scope, quality, schedule and cost with mitigation actions, contingency funds and time, etc. Deliver an outstanding presentation on the topic using this Process Of Merchandise Planning In Retail Risk Management Plan To Mitigate Threats. Dispense information and present a thorough explanation of Cost, Quality, Secondary Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Risk Management Strategies Classification Of IT Risks With Threats
IT Risk Management Strategies Classification Of IT Risks With ThreatsThis slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Present the topic in a bit more detail with this IT Risk Management Strategies Classification Of IT Risks With Threats. Use it as a tool for discussion and navigation on Technology, Security, Political And Legal. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Plan To Mitigate Threats Approaches To Merchandise Planning
Risk Management Plan To Mitigate Threats Approaches To Merchandise PlanningThis slide shows the risk management plan for retailers which includes status, description, probability, impact in terms of scope, quality, schedule and cost with mitigation actions, contingency funds and time, etc. Deliver an outstanding presentation on the topic using this Risk Management Plan To Mitigate Threats Approaches To Merchandise Planning. Dispense information and present a thorough explanation of Mitigation Actions, Probability, Residual Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Risk Management Strategies Information Technology Risks Form Human Threat Source
IT Risk Management Strategies Information Technology Risks Form Human Threat SourceThis slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Present the topic in a bit more detail with this IT Risk Management Strategies Information Technology Risks Form Human Threat Source. Use it as a tool for discussion and navigation on Computer Criminal, Terrorist, Industrial Espionage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Risk Management Strategies IT Vulnerabilities With Threat Source And Action
IT Risk Management Strategies IT Vulnerabilities With Threat Source And ActionThe following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Present the topic in a bit more detail with this IT Risk Management Strategies IT Vulnerabilities With Threat Source And Action. Use it as a tool for discussion and navigation on Vulnerabilities, Threat Source, Threat Action. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation Plan
IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation PlanThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Increase audience engagement and knowledge by dispensing information using IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation Plan. This template helps you present information on one stages. You can also present information on Threat, Risk, Risk Priority, Risk Reduction Timeline using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Enterprise Risk Management Classification Of IT Risks With Threats
Enterprise Risk Management Classification Of IT Risks With ThreatsThis slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Present the topic in a bit more detail with this Enterprise Risk Management Classification Of IT Risks With Threats. Use it as a tool for discussion and navigation on Technology, Security, Political And Legal. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
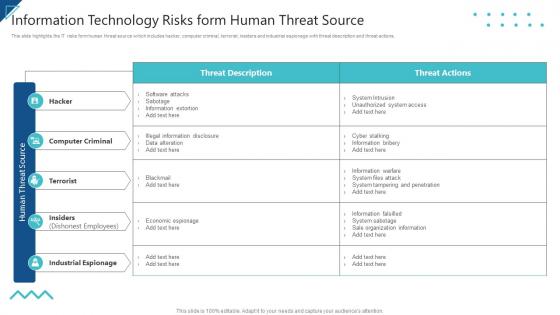 Enterprise Risk Management Information Technology Risks Form Human Threat Source
Enterprise Risk Management Information Technology Risks Form Human Threat SourceThis slide highlights the IT risks form human threat source which includes hacker, computer criminal, terrorist, insiders and industrial espionage with threat description and threat actions. Present the topic in a bit more detail with this Enterprise Risk Management Information Technology Risks Form Human Threat Source. Use it as a tool for discussion and navigation on Computer Criminal, Terrorist, Industrial Espionage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Risk Management IT Vulnerabilities With Threat Source And Action
Enterprise Risk Management IT Vulnerabilities With Threat Source And ActionThe following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Present the topic in a bit more detail with this Enterprise Risk Management IT Vulnerabilities With Threat Source And Action. Use it as a tool for discussion and navigation on Vulnerabilities, Threat Source, Threat Action. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation Plan
Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation PlanThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Enterprise Risk Management Prioritized Cyber Security Threats With Risk Mitigation Plan. Use it as a tool for discussion and navigation on Threat, Risk, Risk Priority, Risk Reduction Timeline. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Classification Of IT Risks With Threats Risk Management Guide For Information Technology Systems
Classification Of IT Risks With Threats Risk Management Guide For Information Technology SystemsThis slide highlights the classification of information technology risks which includes technology, security, political and legal, personnel, and infrastructure with key threats. Present the topic in a bit more detail with this Classification Of IT Risks With Threats Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Technology, Security, Political And Legal. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IT Vulnerabilities With Threat Source Risk Management Guide For Information Technology Systems
IT Vulnerabilities With Threat Source Risk Management Guide For Information Technology SystemsThe following slide highlights the information technology vulnerabilities which includes the thread source from terminated employees and unauthorized users and threat action. Present the topic in a bit more detail with this IT Vulnerabilities With Threat Source Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Vulnerabilities, Threat Source, Threat Action. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems
Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology SystemsThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Threat Risk, Risk Mitigation Plan, Risk Owner. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Analysing The Impact Of Security Threats On Organization Information Security Risk Management
Analysing The Impact Of Security Threats On Organization Information Security Risk ManagementDeliver an outstanding presentation on the topic using this Analysing The Impact Of Security Threats On Organization Information Security Risk Management. Dispense information and present a thorough explanation of Analysing, Security Threats, Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identifying Information Security Threats And Impact Information Security Risk Management
Identifying Information Security Threats And Impact Information Security Risk ManagementThis slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization. Increase audience engagement and knowledge by dispensing information using Identifying Information Security Threats And Impact Information Security Risk Management. This template helps you present information on one stage. You can also present information on Errors And Omissions, Employee Sabotage, Physical Infrastructure Loss using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Matrix For Threat Solution And Risk Management Information Security Risk Management
Matrix For Threat Solution And Risk Management Information Security Risk ManagementThis slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Introducing Matrix For Threat Solution And Risk Management Information Security Risk Management to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispense information on Monitor Database Activity, Validate Database Protocols, Capture Detailed Transactions, using this template. Grab it now to reap its full benefits.
-
 Mitigation Plan For Resolving Encountered Threat Information Security Risk Management
Mitigation Plan For Resolving Encountered Threat Information Security Risk ManagementMentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver an outstanding presentation on the topic using this Mitigation Plan For Resolving Encountered Threat Information Security Risk Management. Dispense information and present a thorough explanation of Risk Mitigation Plan, Expected Resolution Time, Mitigation Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mitigation Strategies To Tackle Information Security Threats Information Security Risk Management
Mitigation Strategies To Tackle Information Security Threats Information Security Risk ManagementThis slide showcases mitigation strategies that can help organization to tackle the cybersecurity attacks. It can help organization to minimize the financial loss and maintain reputation of business. Increase audience engagement and knowledge by dispensing information using Mitigation Strategies To Tackle Information Security Threats Information Security Risk Management. This template helps you present information on five stages. You can also present information on Mitigation Strategies, Tackle Information, Security Threats using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Management
Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk ManagementThis slide showcases assessment matrix to identify risk associate with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level. Deliver an outstanding presentation on the topic using this Risk Assessment Matrix With Vulnerability And Threat Level Information Security Risk Management. Dispense information and present a thorough explanation of Risk Assessment Matrix, Vulnerability Level, Threat Level using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat Identification And Vulnerability Assessment Information Security Risk Management
Threat Identification And Vulnerability Assessment Information Security Risk ManagementThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating. Present the topic in a bit more detail with this Threat Identification And Vulnerability Assessment Information Security Risk Management. Use it as a tool for discussion and navigation on Threat Identification, Vulnerability Assessment, Risk Identification. This template is free to edit as deemed fit for your organization. Therefore download it now
-
 Risk Management Plan To Mitigate Threats Implement Merchandise Improve Sales
Risk Management Plan To Mitigate Threats Implement Merchandise Improve SalesThis slide shows the risk management plan for retailers which includes status, description, probability, impact in terms of scope, quality, schedule and cost with mitigation actions, contingency funds and time, etc. Present the topic in a bit more detail with this Risk Management Plan To Mitigate Threats Implement Merchandise Improve Sales. Use it as a tool for discussion and navigation on Management, Contingency, Probability. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Project Risk Management Plan With Opportunities And Threats
Project Risk Management Plan With Opportunities And ThreatsThis slide shows the risk management plan for managing project which includes identification of risk, performing qualitative and quantitative analysis, risk response planning, controlling and communicating risk with opportunities and threats. Introducing our Project Risk Management Plan With Opportunities And Threats set of slides. The topics discussed in these slides are Risk Management, Opportunities, Plan Risk Response. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Communication Plan To Ensure Zero Harassment Diversity Management To Create Positive Workplace Environment
Communication Plan To Ensure Zero Harassment Diversity Management To Create Positive Workplace EnvironmentThis slides shows the communication plan to ensure zero harassment reporting in the organization. It provides information regarding trigger, priority, compliant format, first response etc. Present the topic in a bit more detail with this Communication Plan To Ensure Zero Harassment Diversity Management To Create Positive Workplace Environment. Use it as a tool for discussion and navigation on Physical Appearance, Identify Employee, Content Screenshot. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Major Types Of E Banking Security Threats E Banking Management And Services
Major Types Of E Banking Security Threats E Banking Management And ServicesThis slide represents types of e banking security threats. It includes brute force, phishing, pharming, cross site scripting and trojan horse. Present the topic in a bit more detail with this Major Types Of E Banking Security Threats E Banking Management And Services. Use it as a tool for discussion and navigation on Pharming, Mitigation Strategies, E Banking Security Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Banks Threat Management In Powerpoint And Google Slides Cpb
Banks Threat Management In Powerpoint And Google Slides CpbPresenting Banks Threat Management In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Banks Threat Management. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Matrix For Threat Solution And Risk Management Information System Security And Risk Administration Plan
Matrix For Threat Solution And Risk Management Information System Security And Risk Administration PlanThis slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Deliver an outstanding presentation on the topic using this Matrix For Threat Solution And Risk Management Information System Security And Risk Administration Plan. Dispense information and present a thorough explanation of Monitor Database Activity, Validate Database Protocols, Capture Detailed Transactions using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Internal And External Threats Management Overview Of Enterprise Risk Management
Enterprise Internal And External Threats Management Overview Of Enterprise Risk ManagementThis slide represents details related to the risks faced by the organization due to internal factors and external factors. It includes details related to management of internal and external failures of the enterprise. Present the topic in a bit more detail with this Enterprise Internal And External Threats Management Overview Of Enterprise Risk Management. Use it as a tool for discussion and navigation on Management, Enterprise, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Analysis And Management Plan Analysing The Impact Of Security Threats
Cybersecurity Risk Analysis And Management Plan Analysing The Impact Of Security ThreatsPresent the topic in a bit more detail with this Cybersecurity Risk Analysis And Management Plan Analysing The Impact Of Security Threats. Use it as a tool for discussion and navigation on Analysing, Organization, Security Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cybersecurity Risk Analysis And Management Plan Mitigation Plan For Resolving Encountered Threat
Cybersecurity Risk Analysis And Management Plan Mitigation Plan For Resolving Encountered ThreatMentioned slide shows mitigation plan for resolving encountered threat. It covers details about encountered threat, its description, risk level, mitigation plan, resources required, responsible person, expected resolution time and communication mode. Deliver an outstanding presentation on the topic using this Cybersecurity Risk Analysis And Management Plan Mitigation Plan For Resolving Encountered Threat. Dispense information and present a thorough explanation of Encountered Threat, Description, Resources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Risk Analysis And Management Plan Risk Assessment Matrix With Vulnerability And Threat
Cybersecurity Risk Analysis And Management Plan Risk Assessment Matrix With Vulnerability And ThreatThis slide showcases assessment matrix to identify risk associated with different class of information assets. It calculates severity of risk on the basis of threat and vulnerability level Deliver an outstanding presentation on the topic using this Cybersecurity Risk Analysis And Management Plan Risk Assessment Matrix With Vulnerability And Threat. Dispense information and present a thorough explanation of Assessment, Vulnerability, Threat Level using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identifying Information Security Threats And Impact Cybersecurity Risk Analysis And Management Plan
Identifying Information Security Threats And Impact Cybersecurity Risk Analysis And Management PlanThis slide showcases various threats that can be faced by organization and can result in financial plus reputational loss. It also showcases impact of threats on operational capability of organization Present the topic in a bit more detail with this Identifying Information Security Threats And Impact Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Identifying, Information, Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Matrix For Threat Solution And Risk Management Cybersecurity Risk Analysis And Management Plan
Matrix For Threat Solution And Risk Management Cybersecurity Risk Analysis And Management PlanThis slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack Present the topic in a bit more detail with this Matrix For Threat Solution And Risk Management Cybersecurity Risk Analysis And Management Plan. Use it as a tool for discussion and navigation on Management, Solution, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management Plan
Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management PlanThis slide showcases identification of threat and assessment of vulnerability and can help organization to identify the information breach risk. Its key components are vulnerability, severity, threat, threat source, likelihood, impact and risk rating Deliver an outstanding presentation on the topic using this Threat Identification And Vulnerability Assessment For Cybersecurity Risk Analysis And Management Plan. Dispense information and present a thorough explanation of Identification, Assessment, Vulnerability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat And Vulnerability Management Model To Measure Program Maturity
Threat And Vulnerability Management Model To Measure Program MaturityThis slide defines the vulnerability management model adopted to measure the maturity of program. It includes information related to different levels from scanning to risk management. Introducing our premium set of slides with Threat And Vulnerability Management Model To Measure Program Maturity. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Non Existent, Scanning, Assessment. So download instantly and tailor it with your information.
-
 Threats And Vulnerability Management Program Process
Threats And Vulnerability Management Program ProcessThis slide defines the functions and process adopted by the threats and vulnerability management program. It includes information related to identifying, evaluating, treating and reporting vulnerabilities. Presenting our set of slides with Threats And Vulnerability Management Program Process. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identifying Vulnerabilities, Treating Vulnerabilities, Evaluating Vulnerabilities.
-
 Threats And Vulnerability Management Program Requirement Icon
Threats And Vulnerability Management Program Requirement IconIntroducing our premium set of slides with Threats And Vulnerability Management Program Requirement Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Threats And Vulnerability Management, Program Requirement Icon. So download instantly and tailor it with your information.
-
 Matrix For Threat Solution And Risk Management Formulating Cybersecurity Plan
Matrix For Threat Solution And Risk Management Formulating Cybersecurity PlanThis slide showcases matrix that can help organization to formulate solutions for different types of information security attacks. It can help organization to mitigate the risks and safeguard information in case of any attack. Deliver an outstanding presentation on the topic using this Matrix For Threat Solution And Risk Management Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Block Malicious, Monitor Database Activity, Validate Database Protocols using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Plan To Manage Cyber Threats Guide To Build It Strategy Plan For Organizational Growth
Risk Management Plan To Manage Cyber Threats Guide To Build It Strategy Plan For Organizational GrowthThis slide provides information regarding risk management plan to monitor cyber threats including details about threat, vulnerability, asset, impact, likelihood, risk and control initiatives. Deliver an outstanding presentation on the topic using this Risk Management Plan To Manage Cyber Threats Guide To Build It Strategy Plan For Organizational Growth. Dispense information and present a thorough explanation of Management, Information, Vulnerability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Procurement Risk Review Scorecard For Strategic Threat Management
Procurement Risk Review Scorecard For Strategic Threat ManagementFollowing slide demonstrates scorecard for procurement risk assessment used by organizations to eliminate potential threats. This slide provides data regarding area, scorecard criteria, risk rating scale, remarks, area wise weight and rating, week to date rating and overall rating. Introducing our Procurement Risk Review Scorecard For Strategic Threat Management set of slides. The topics discussed in these slides are Industry Factors, Supplier Assessment, Scorecard Criteria. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Responsible Tech Playbook To Leverage Checklist To Manage Agile Threat Modelling Ppt Ideas Tips
Responsible Tech Playbook To Leverage Checklist To Manage Agile Threat Modelling Ppt Ideas TipsThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Deliver an outstanding presentation on the topic using this Responsible Tech Playbook To Leverage Checklist To Manage Agile Threat Modelling Ppt Ideas Tips. Dispense information and present a thorough explanation of Collaborate With Delivery Team, Analyze Threats, Prioritization And Resolve Issues using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Manage Agile Threat Modelling Ethical Tech Governance Playbook
Checklist To Manage Agile Threat Modelling Ethical Tech Governance PlaybookThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Deliver an outstanding presentation on the topic using this Checklist To Manage Agile Threat Modelling Ethical Tech Governance Playbook. Dispense information and present a thorough explanation of Analyze Threats, Prioritization And Resolve Issues, Collaborate using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Building Responsible Organization Checklist To Manage Agile Threat Modelling
Building Responsible Organization Checklist To Manage Agile Threat ModellingThis slide provides information regarding checklist to handle the agile threat model by managing focus areas such as threat analysis, collaboration with delivery team, issues prioritization and resolution, project wrapping up and closure, etc. Present the topic in a bit more detail with this Building Responsible Organization Checklist To Manage Agile Threat Modelling. Use it as a tool for discussion and navigation on Threat Modeling Sessions, Technical Diagram Highlighting, Agile Threat Modelling. This template is free to edit as deemed fit for your organization. Therefore download it now.





