Powerpoint Templates and Google slides for Terrorism
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
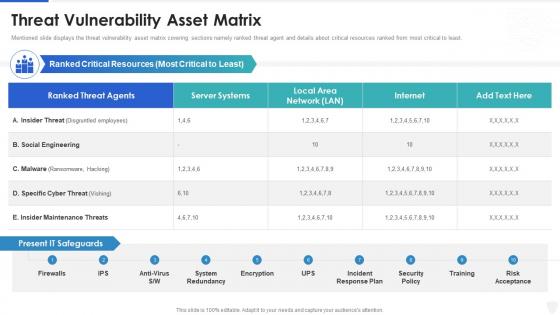 Cybersecurity and digital business risk management threat vulnerability asset matrix
Cybersecurity and digital business risk management threat vulnerability asset matrixMentioned slide displays the threat vulnerability asset matrix covering sections namely ranked threat agent and details about critical resources ranked from most critical to least. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Threat Vulnerability Asset Matrix. Dispense information and present a thorough explanation of Threat Vulnerability Asset Matrix using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Threat intelligence platform ppt powerpoint presentation inspiration portfolio cpb
Threat intelligence platform ppt powerpoint presentation inspiration portfolio cpbPresenting Threat Intelligence Platform Ppt Powerpoint Presentation Inspiration Portfolio Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Threat Intelligence Platform. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Psychological bullying work diagram ppt powerpoint presentation file deck cpb
Psychological bullying work diagram ppt powerpoint presentation file deck cpbPresenting Psychological Bullying Work Diagram Ppt Powerpoint Presentation File Deck Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Psychological Bullying Work Diagram. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cloud Backup And Disaster Recovery Program With Key Threats
Cloud Backup And Disaster Recovery Program With Key ThreatsThe following slide illustrates the virtual cloud disaster recovery solution which include also include disaster avoidance with pros and cons. Presenting our well structured Cloud Backup And Disaster Recovery Program With Key Threats. The topics discussed in this slide are Virtual Cloud Disaster Recovery Solutions With Pros And Cons. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 F212 Pharmaceutical Company Swot Analysis Threats Strategies Sustainable Development
F212 Pharmaceutical Company Swot Analysis Threats Strategies Sustainable DevelopmentThis slide shows the various threats related to pharmaceutical company such as high level of competition, suppliers, regulations on international trade and many more. Increase audience engagement and knowledge by dispensing information using F212 Pharmaceutical Company Swot Analysis Threats Strategies Sustainable Development. This template helps you present information on four stages. You can also present information on High Competition, Analysis, International Trade, Suppliers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Debt Collectors Harassment Ppt Powerpoint Presentation Summary Aids Cpb
Debt Collectors Harassment Ppt Powerpoint Presentation Summary Aids CpbPresenting our Debt Collectors Harassment Ppt Powerpoint Presentation Summary Aids Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Debt Collectors Harassment. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Strength Weakness Opportunity And Threat Of Affiliate Marketing
Strength Weakness Opportunity And Threat Of Affiliate MarketingThis slide covers the SWOT of affiliate which is used in marketing in businesses to analyze exactly what it intends to do, which is looking at where your opportunities are and what competition you would have with your competitors or the industry. Introducing our premium set of slides with name Strength Weakness Opportunity And Threat Of Affiliate Marketing. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Strength, Opportunities, Weakness, Threats. So download instantly and tailor it with your information.
-
 Supply Chain Strength Weakness Opportunity Threat Analysis
Supply Chain Strength Weakness Opportunity Threat AnalysisThis slide showcases the SWOT analysis of the supply chain of n organization to provide better customer experience and deliver the goods at a fast pace. Presenting our set of slides with name Supply Chain Strength Weakness Opportunity Threat Analysis. This exhibits information on one stage of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Strengths, Weaknesses, Threats.
-
 Average Financial Loss Of Companies Per Cyber Terrorism Incident
Average Financial Loss Of Companies Per Cyber Terrorism IncidentThis slide represents the financial losses faced by the companies per cyber terrorism incident. It shows the average financial loss faced by small, medium and large companies per cyber terrorism incident. Presenting our set of slides with name Average Financial Loss Of Companies Per Cyber Terrorism Incident. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Financial Loss, Cyber Terrorism, Revenue.
-
 Classification Of Cyber Terrorism Activities Framework
Classification Of Cyber Terrorism Activities FrameworkThis slide represents the framework showing the classification of various activities of cyber terrorism. It includes classification of activities into traditional, cyber enabled and cyber dependent terrorism. Introducing our premium set of slides with name Classification Of Cyber Terrorism Activities Framework. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Recruitment, Organization And Planning, Traditional Terrorism, Cyber Dependent Terrorism. So download instantly and tailor it with your information.
-
 Conceptual Framework Of Cyber Terrorism With Impact
Conceptual Framework Of Cyber Terrorism With ImpactThis slide covers the framework for cyberterrorism whose main objective is to destroy target organization, industry or economy. It represents the target, motivation, tools of attack, domain, method of action and impact of the cyber terrorism in a country. Presenting our set of slides with name Conceptual Framework Of Cyber Terrorism With Impact. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Motivation, Ideological, Network Warfare, Psychological Operation.
-
 Cyber Crime And Terrorism Security Strategic Vision
Cyber Crime And Terrorism Security Strategic VisionThis slide represents the cyber crime and security strategies formulated by the United Kingdom. It includes details related to strategic vision and four objectives of the UK cyber terrorism security team. Introducing our premium set of slides with name Cyber Crime And Terrorism Security Strategic Vision. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Strategic Vision, Protection Promotion, Protection Of Interests In Cyberspace. So download instantly and tailor it with your information.
-
 Cyber Crime And Terrorism Strategies Icon
Cyber Crime And Terrorism Strategies IconPresenting our set of slides with name Cyber Crime And Terrorism Strategies Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Crime And Terrorism Strategies Icon.
-
 Cyber Terrorism Model Showcasing Target Motive And Intent
Cyber Terrorism Model Showcasing Target Motive And IntentThis slide represents the model of the cyber terrorism. It includes features of cyber terrorism such as its targets, actors, motive, intent, means and its effect on a region or country. Introducing our premium set of slides with name Cyber Terrorism Model Showcasing Target Motive And Intent. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Targets, Intent, Motive, Data Information, Digital Properties. So download instantly and tailor it with your information.
-
 Cyber Terrorism Prevention Tools Comparative Analysis
Cyber Terrorism Prevention Tools Comparative AnalysisThis slide represents the comparison between various cyber terrorism prevention tools on the basis of their top features, bottom line and the free trials provided. It includes features such as multiple server support, breach severity insights, anti-exploit module etc. Introducing our Cyber Terrorism Prevention Tools Comparative Analysis set of slides. The topics discussed in these slides are Analysis Of Event Logs, Detection Of SQL Injection Attacks, Highly Automated, Comprehensive. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber Terrorism Threats And Safeguard Assessment Matrix
Cyber Terrorism Threats And Safeguard Assessment MatrixThis slide represents the assessment matrix for cyber terrorism threats and its functions and safeguards. It includes functions such as identify, protect, detect, respond and recover and threats such as phishing, ransomware, web app attacks and vendor and partner data loss. Presenting our well structured Cyber Terrorism Threats And Safeguard Assessment Matrix. The topics discussed in this slide are Phishing, Ransomware, Deception Technology. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Four Attributes Of Cyber Terrorism Phenomenon
Four Attributes Of Cyber Terrorism PhenomenonThis slide represents the key attributes of the cyber terrorism phenomenon. It includes four attributes of cyber terrorism such as computer as weapon and target, pursuing political, social or religious aims , produces physical violence etc. Introducing our Four Attributes Of Cyber Terrorism Phenomenon set of slides. The topics discussed in these slides are Cyber Attack, Cyberwarfare, Cyberterrorism. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Global Cyber Terrorism Attacks Icon
Global Cyber Terrorism Attacks IconPresenting our set of slides with name Global Cyber Terrorism Attacks Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Global Cyber Terrorism Attacks Icon.
-
 Qualitative Analysis Of Collected Cyber Terrorism Primary Data
Qualitative Analysis Of Collected Cyber Terrorism Primary DataThis slide represents the analysis of the collected cyber terrorism data. It includes details related to victims of cyber terrorism, increase of terrorism online presence, regulation and stakeholder understanding and defining cyber terrorism. Introducing our premium set of slides with name Qualitative Analysis Of Collected Cyber Terrorism Primary Data. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Regulation And Stakeholder Understanding, Defining Cyber Terrorism, Terrorism Online Presence. So download instantly and tailor it with your information.
-
 Strategic Plan For Management Of Cyber Terrorism
Strategic Plan For Management Of Cyber TerrorismThis slide represents the plan to manage the attacks of cyber terrorism. It includes details related to metrics, what is measured, how is it measured and by whom the metrics are measured. Introducing our Strategic Plan For Management Of Cyber Terrorism set of slides. The topics discussed in these slides are Policy Violations, Training Completion, Strategic Plan. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Survey Insights On Cyber Terrorism Attacks Icons
Survey Insights On Cyber Terrorism Attacks IconsIntroducing our premium set of slides with name Survey Insights On Cyber Terrorism Attacks Icons. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Survey Insights On Cyber Terrorism Attacks Icons. So download instantly and tailor it with your information.
-
 Three Stages Of Cyber Terrorism Attack
Three Stages Of Cyber Terrorism AttackThis slide shows details related to the stages of the attacks through cyber terrorism. It includes three stages of pre attack and opening moves, attack and end game and post attack. Presenting our set of slides with name Three Stages Of Cyber Terrorism Attack. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Social Engineering, Identify Vulnerabilities, Exploitation Of Vulnerabilities, Data Stolen.
-
 Various Cyber Terrorism Threats With Risk Priority
Various Cyber Terrorism Threats With Risk PriorityThis slide represents the five major threats caused by cyber terrorism along with their risk priorities. It includes threats such as malware, phishing, spear fishing, SQL injection and advanced persistent threats. Presenting our well structured Various Cyber Terrorism Threats With Risk Priority. The topics discussed in this slide are Phishing, Malicious Software, Threat. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Discrimination Harassment Workplace Ppt Powerpoint Presentation Model Cpb
Discrimination Harassment Workplace Ppt Powerpoint Presentation Model CpbPresenting our Discrimination Harassment Workplace Ppt Powerpoint Presentation Model Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Discrimination Harassment Workplace. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 External Threats Ppt Powerpoint Presentation Visual Aids Deck Cpb
External Threats Ppt Powerpoint Presentation Visual Aids Deck CpbPresenting our External Threats Ppt Powerpoint Presentation Visual Aids Deck Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on External Threats This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Insider Threat VS Outsider Threat Ppt Powerpoint Presentation Design Ideas Cpb
Insider Threat VS Outsider Threat Ppt Powerpoint Presentation Design Ideas CpbPresenting our Insider Threat VS Outsider Threat Ppt Powerpoint Presentation Design Ideas Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Insider Threat VS Outsider Threat This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Outsider Threat Protection Ppt Powerpoint Presentation Ideas File Formats Cpb
Outsider Threat Protection Ppt Powerpoint Presentation Ideas File Formats CpbPresenting our Outsider Threat Protection Ppt Powerpoint Presentation Ideas File Formats Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Outsider Threat Protection. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Discrimination Harassment Policy Ppt Powerpoint Presentation Slides Outline Cpb
Discrimination Harassment Policy Ppt Powerpoint Presentation Slides Outline CpbPresenting Discrimination Harassment Policy Ppt Powerpoint Presentation Slides Outline Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Discrimination Harassment Policy. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Risk Acceptance Icon For Threat Avoidance
Risk Acceptance Icon For Threat AvoidanceIntroducing our premium set of slides with Risk Acceptance Icon For Threat Avoidance. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Risk Acceptance, Icon, Threat Avoidance. So download instantly and tailor it with your information.
-
 Risk Acceptance Icon Indicating Threat Assessment
Risk Acceptance Icon Indicating Threat AssessmentPresenting our set of slides with name Risk Acceptance Icon Indicating Threat Assessment. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Risk Acceptance, Icon, Indicating Threat Assessment.
-
 Bomb Blast Threat Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Bomb Blast Threat Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Bomb blast threat colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Bomb Blast Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Bomb Blast Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Bomb blast threat monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Bug Bite Threat Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Bug Bite Threat Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Bug bite threat colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Bug Bite Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Bug Bite Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Bug bite threat monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Threat Sign Board Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Sign Board Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Threat sign board colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Threat Sign Board Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Sign Board Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Threat sign board monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Investment Risk And Threat Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Investment Risk And Threat Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Investment risk and threat colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Investment Risk And Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Investment Risk And Threat Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Investment risk and threat monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats
Incident Response Playbook Checklist To Ensure Asset Protection From Internal ThreatsFollowing slide displays checklist having security control measures that can be used by members to ensure the safety of companys assets from any insider threat. Introducing Incident Response Playbook Checklist To Ensure Asset Protection From Internal Threats to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Mobile Devices, Company Assets, Employees, using this template. Grab it now to reap its full benefits.
-
 Incident Response Playbook Cyber Threat Facts Figures And Statistics
Incident Response Playbook Cyber Threat Facts Figures And StatisticsThis slide portrays statistical information about cyber threats. Information covered is related data breach, ransomware attacks, cyberthreat complaints and phishing attack. Increase audience engagement and knowledge by dispensing information using Incident Response Playbook Cyber Threat Facts Figures And Statistics. This template helps you present information on six stages. You can also present information on Ransomware Attacks, Security Professional, Phishing Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Ways To Secure Cloud Infrastructure From Security Threats Optimization Of Cloud Computing
Key Ways To Secure Cloud Infrastructure From Security Threats Optimization Of Cloud ComputingMentioned slide provides key ways to secure cloud infrastructure from security threats. It covers encryption services, security design, internet of things and internal security.Introducing Key Ways To Secure Cloud Infrastructure From Security Threats Optimization Of Cloud Computing to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Key Takeaways, Hardware Maintenance, Improvement In Service using this template. Grab it now to reap its full benefits.
-
 Cloud Security Risks Or Threats Cloud Information Security
Cloud Security Risks Or Threats Cloud Information SecurityThis slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on.Increase audience engagement and knowledge by dispensing information using Cloud Security Risks Or Threats Cloud Information Security This template helps you present information on eight stages. You can also present information on Serious Repercussions, Organizations Should, Authentication Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Threats Compliance Violations Cloud Information Security
Cloud Security Threats Compliance Violations Cloud Information SecurityThis slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non compliance state.Introducing Cloud Security Threats Compliance Violations Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Needed Information, Against Organization, Business Partners using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Contract Breaches With Clients Cloud Information Security
Cloud Security Threats Contract Breaches With Clients Cloud Information SecurityThis slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data.Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Contract Breaches With Clients Cloud Information Security This template helps you present information on four stages. You can also present information on Organizations Cybercriminals, Customers OR Clients, Contact Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Threats End User Control Cloud Information Security
Cloud Security Threats End User Control Cloud Information SecurityThis slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats.Introducing Cloud Security Threats End User Control Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Wisely Considering, Storage Location, Procedures Strategies using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Loss Of Data Cloud Information Security
Cloud Security Threats Loss Of Data Cloud Information SecurityThis slide represents the data loss threat of cloud security it is essential to secure organization data and create backups.Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Loss Of Data Cloud Information Security This template helps you present information on four stages. You can also present information on Cloud Administrations, Protection Frameworks, Technology Advances using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Threats Malware Attacks Cloud Information Security
Cloud Security Threats Malware Attacks Cloud Information SecurityThis slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss.Introducing Cloud Security Threats Malware Attacks Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Clients OR Customers, Organizations Experienced, Companies Organizations using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Revenue Losses Cloud Information Security
Cloud Security Threats Revenue Losses Cloud Information SecurityThis slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan.Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Revenue Losses Cloud Information Security This template helps you present information on five stages. You can also present information on Password Security, Clients Responsibility, Service Providers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Threats Shared Vulnerabilities Cloud Information Security
Cloud Security Threats Shared Vulnerabilities Cloud Information SecurityThis slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data.Introducing Cloud Security Threats Shared Vulnerabilities Cloud Information Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Information Centers, Reduced Upfront, Diminished Opportunity using this template. Grab it now to reap its full benefits.
-
 Agenda For Building A Security Awareness Program To Educate Employees About Cyber Threats
Agenda For Building A Security Awareness Program To Educate Employees About Cyber ThreatsIntroducing Agenda For Building A Security Awareness Program To Educate Employees About Cyber Threats to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Amongst Employees, Awareness Program, Department Plan, using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Building A Security Awareness Program To Educate Employees About Cyber Threats
Icons Slide For Building A Security Awareness Program To Educate Employees About Cyber ThreatsIntroducing our well researched set of slides titled Icons Slide For Building A Security Awareness Program To Educate Employees About Cyber Threats. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 5g Network Architecture Guidelines Key Security Considerations For 5g For Threat Handling
5g Network Architecture Guidelines Key Security Considerations For 5g For Threat HandlingThis slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Present the topic in a bit more detail with this 5g Network Architecture Guidelines Key Security Considerations For 5g For Threat Handling. Use it as a tool for discussion and navigation on Considerations, Associated, Unauthorized. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Five Step Cybersecurity Threat Management Roadmap
Five Step Cybersecurity Threat Management RoadmapThis slide depicts cybersecurity roadmap for threat management illustrating five steps such as identification, analyzing, evaluation, responding and monitoring for identifying and analyzing potential cyber risk. Presenting our set of slides with name Five Step Cybersecurity Threat Management Roadmap. This exhibits information on five stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Analyzing, Identification, Responding, Monitoring, Evaluation.
-
 Bug Threat Hunting Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Bug Threat Hunting Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Bug threat hunting colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Bug Threat Hunting Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Bug Threat Hunting Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Bug threat hunting monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Computer Threat Hunting Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Threat Hunting Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Computer threat hunting colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Computer Threat Hunting Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Threat Hunting Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Computer threat hunting monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Threat Hunting And Gear Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Hunting And Gear Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Threat hunting and gear colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Threat Hunting And Gear Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Threat Hunting And Gear Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Threat hunting and gear monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Difference Between Weakness Threat In Powerpoint And Google Slides Cpb
Difference Between Weakness Threat In Powerpoint And Google Slides CpbPresenting Difference Between Weakness Threat In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase two stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Difference Between Weakness Threat. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.





