Powerpoint Templates and Google slides for Terrorism
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Disaster Recovery Plan For The Business Cyber Terrorism Attacks
Disaster Recovery Plan For The Business Cyber Terrorism AttacksThis slide illustrates the elements that will be taken into account when establishing a recovery plan for company to go back to business swiftly and successfully. Increase audience engagement and knowledge by dispensing information using Disaster Recovery Plan For The Business Cyber Terrorism Attacks. This template helps you present information on three stages. You can also present information on Inventory, Assets, Assessment, Importance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Employee Access Control Protocols Cyber Terrorism Attacks
Employee Access Control Protocols Cyber Terrorism AttacksThis slide highlights how it is critical to limit employee rights and access in order to keep data safe and prevent it from being deleted or manipulated. Introducing Employee Access Control Protocols Cyber Terrorism Attacks to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Physical Assets, Access Control, Sensitive Data, Restricts Access, using this template. Grab it now to reap its full benefits.
-
 Employee Awareness Training Budget Cyber Terrorism Attacks
Employee Awareness Training Budget Cyber Terrorism AttacksThis slide demonstrates the employee awareness training budget against cyber terrorism by a graph that includes the training date, and the degree of capacity. Deliver an outstanding presentation on the topic using this Employee Awareness Training Budget Cyber Terrorism Attacks. Dispense information and present a thorough explanation of Employee Awareness Training Budget Against Cyber Terrorism Fy2020 using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Financial Loss Faced By The Business Cyber Terrorism Attacks
Financial Loss Faced By The Business Cyber Terrorism AttacksThis slide depicts the average financial loss faced by the business when projects of different scales are attacked. Increase audience engagement and knowledge by dispensing information using Financial Loss Faced By The Business Cyber Terrorism Attacks. This template helps you present information on one stages. You can also present information on Financial Loss Faced By The Business using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How To Prevent Ddos Attacks In The Company Cyber Terrorism Attacks
How To Prevent Ddos Attacks In The Company Cyber Terrorism AttacksThis slide represents the ways to prevent DDoS attacks in the company, which include network monitoring, updating security elements, etc. Introducing How To Prevent Ddos Attacks In The Company Cyber Terrorism Attacks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Service, Bandwidth, Capacity, Network Monitoring, Mitigation Technologies, using this template. Grab it now to reap its full benefits.
-
 How To Protect Company From Trojan Attacks Cyber Terrorism Attacks
How To Protect Company From Trojan Attacks Cyber Terrorism AttacksThis slide explains how to protect the company from trojan attacks which include procedures such as installing advanced antivirus software. Increase audience engagement and knowledge by dispensing information using How To Protect Company From Trojan Attacks Cyber Terrorism Attacks. This template helps you present information on five stages. You can also present information on Antivirus Programm, Application Firewall, Reliable Sources, Avoid Third Party Downloads using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Cyber Terrorism Attacks Ppt Slides Background Designs
Icons Slide For Cyber Terrorism Attacks Ppt Slides Background DesignsPresenting our well crafted Icons Slide For Cyber Terrorism Attacks Ppt Slides Background Designs set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.
-
 Implementing Least Privilege Administrative Model Cyber Terrorism Attacks
Implementing Least Privilege Administrative Model Cyber Terrorism AttacksThis slide depicts that administration and employees should have limited access to the information and confidential data. Introducing Implementing Least Privilege Administrative Model Cyber Terrorism Attacks to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Privileges, Control, Risk Levels, Prevent, using this template. Grab it now to reap its full benefits.
-
 Malicious Codemalware Misused For Cyber Terrorism Cyber Terrorism Attacks
Malicious Codemalware Misused For Cyber Terrorism Cyber Terrorism AttacksThis slide depicts the malicious code or malware misused for cyber terrorism attacks to hijack or access information from computers. Increase audience engagement and knowledge by dispensing information using Malicious Codemalware Misused For Cyber Terrorism Cyber Terrorism Attacks. This template helps you present information on five stages. You can also present information on Malicious Code Malware Misused For Cyber Terrorism using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Managing Cyber Terrorism 60 Days Plan Cyber Terrorism Attacks
Managing Cyber Terrorism 60 Days Plan Cyber Terrorism AttacksThis slide depicts the plan for the next 60 days after the firm has implemented the cyber security model to tackle cyber terrorism. Deliver an outstanding presentation on the topic using this Managing Cyber Terrorism 60 Days Plan Cyber Terrorism Attacks. Dispense information and present a thorough explanation of Managing Cyber Terrorism 60 Days Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing Cyber Terrorism Attacks 90 Days Plan Cyber Terrorism Attacks
Managing Cyber Terrorism Attacks 90 Days Plan Cyber Terrorism AttacksThis slide demonstrates the cyber security models 90 day strategy in an enterprise, as well as training compliance and communication strategies. Deliver an outstanding presentation on the topic using this Managing Cyber Terrorism Attacks 90 Days Plan Cyber Terrorism Attacks. Dispense information and present a thorough explanation of Managing Cyber Terrorism Attacks 90 Days Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Peroration Of Cyber Terrorism Attacks Cyber Terrorism Attacks
Peroration Of Cyber Terrorism Attacks Cyber Terrorism AttacksThis slide explains the conclusion or peroration of cyber terrorism and how it is different from information warfare as it targets civilians rather than operations. Introducing Peroration Of Cyber Terrorism Attacks Cyber Terrorism Attacks to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Peroration Of Cyber Terrorism Attacks, using this template. Grab it now to reap its full benefits.
-
 Phishing Cyber Terrorism Tool Cyber Terrorism Attacks
Phishing Cyber Terrorism Tool Cyber Terrorism AttacksThis slide describes phishing in which an attacker tricks a victim to open an email, provide card credentials or any sensitive information. Increase audience engagement and knowledge by dispensing information using Phishing Cyber Terrorism Tool Cyber Terrorism Attacks. This template helps you present information on five stages. You can also present information on Obtain, Sensitive, Information, Trustworthy, Convinces using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Techniques Misused For Cyber Assault Cyber Terrorism Attacks
Phishing Techniques Misused For Cyber Assault Cyber Terrorism AttacksThis slide represents phishing techniques used for cyber assaults or cyber terrorism, such as email phishing scams and whaling. Introducing Phishing Techniques Misused For Cyber Assault Cyber Terrorism Attacks to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Techniques Misused For Cyber Assault, using this template. Grab it now to reap its full benefits.
-
 Reputational Loss Faced By The Company Cyber Terrorism Attacks
Reputational Loss Faced By The Company Cyber Terrorism AttacksThis slide demonstrates the reputational loss of the company due to cyber terrorism, which leads to the customers leaving and a decline in sales. Increase audience engagement and knowledge by dispensing information using Reputational Loss Faced By The Company Cyber Terrorism Attacks. This template helps you present information on five stages. You can also present information on Margin Reduces, Cyber Assaults, Influence, Suppliers, Stakeholders using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Roadmap To Implement Cyber Security Cyber Terrorism Attacks
Roadmap To Implement Cyber Security Cyber Terrorism AttacksThis slide depicts the roadmap to implement strategies to mitigate cyber terrorism such as training employees about cyber terrorism, creating personal accounts. Introducing Roadmap To Implement Cyber Security Cyber Terrorism Attacks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Personal Accounts, Awareness Training, Software Updated, using this template. Grab it now to reap its full benefits.
-
 SCADA System Misused For Cyber Terrorism Cyber Terrorism Attacks
SCADA System Misused For Cyber Terrorism Cyber Terrorism AttacksThis slide describes the SCADA system as a tool misused for cyberterrorism and any damage to the SCADA can cause a major physical damage.. Present the topic in a bit more detail with this SCADA System Misused For Cyber Terrorism Cyber Terrorism Attacks. Use it as a tool for discussion and navigation on Scada System Misused For Cyber Terrorism. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Simple Advanced And Complex Types Cyber Terrorism Attacks
Simple Advanced And Complex Types Cyber Terrorism AttacksThis slide explains the simple advanced and complex types of cyber terrorism attacks i.e. simple structure, advanced structure, and complex coordinated around the 128 countries of the world. Increase audience engagement and knowledge by dispensing information using Simple Advanced And Complex Types Cyber Terrorism Attacks. This template helps you present information on three stages. You can also present information on Simple Structured, Advanced Structured, Complex Coordinated using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Strategies To Keep Company Safe From Cyber Terrorism Attacks
Strategies To Keep Company Safe From Cyber Terrorism AttacksThis slide describes the checklist to deal with cyber terrorism threats and counter it such as go after the perpetrators and prosecute them. Introducing Strategies To Keep Company Safe From Cyber Terrorism Attacks to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Technology, Reduce, Implemented, Restoration, Organization, using this template. Grab it now to reap its full benefits.
-
 Structure Of Malicious Code Misused Cyber Terrorism Attacks
Structure Of Malicious Code Misused Cyber Terrorism AttacksThis slide depicts the structure of malicious code or malware and the four steps of the structure i.e. Probe, Program, Expose and Execute.Increase audience engagement and knowledge by dispensing information using Structure Of Malicious Code Misused Cyber Terrorism Attacks. This template helps you present information on four stages. You can also present information on Structure Of Malicious Code Misused For Cyber Terrorism using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents For Cyber Terrorism Attacks Mitigate
Table Of Contents For Cyber Terrorism Attacks MitigateIntroducing Table Of Contents For Cyber Terrorism Attacks Mitigate to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Assessment Matrix, Security Budget, Security Measures, using this template. Grab it now to reap its full benefits.
-
 Techniques To Protect SCADA Systems From Cyber Terrorism Attacks
Techniques To Protect SCADA Systems From Cyber Terrorism AttacksThis slide depicts the techniques to protect SCADA from cyber attacks which include security training of employees, strict firewalls. Increase audience engagement and knowledge by dispensing information using Techniques To Protect SCADA Systems From Cyber Terrorism Attacks. This template helps you present information on six stages. You can also present information on Security Training, Access Controls, Strict Firewalls, Security Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Three Major Forms Of Cyber Terrorism Attacks Ppt Slides Designs Download
Three Major Forms Of Cyber Terrorism Attacks Ppt Slides Designs DownloadThis slide describes the three major forms of cyber terrorism attacks such as privacy violation, networks damage, and disruptions, and distribution denial of service attack. Introducing Three Major Forms Of Cyber Terrorism Attacks Ppt Slides Designs Download to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Privacy Violation, Damage Disruptions, Distributed Denial, using this template. Grab it now to reap its full benefits.
-
 Timeline For Implementation Cyber Terrorism Attacks
Timeline For Implementation Cyber Terrorism AttacksThis slide shows the timeframe for implementing a cyber security model in a business and the monthly activities that must be completed to fight cyber terrorism. Deliver an outstanding presentation on the topic using this Timeline For Implementation Cyber Terrorism Attacks. Dispense information and present a thorough explanation of Timeline For Implementation Of Cyber Security In The Company using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Trojans As Cyber Terrorism Tool Cyber Terrorism Attacks
Trojans As Cyber Terrorism Tool Cyber Terrorism AttacksThis slide depicts the Trojans as a cyber terrorism attacks tool in which phishing is used to manipulate a user into executing the infected file. Present the topic in a bit more detail with this Trojans As Cyber Terrorism Tool Cyber Terrorism Attacks. Use it as a tool for discussion and navigation on Trojans As Cyber Terrorism Tool. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Types Of Ddos Attacks In The Company Cyber Terrorism Attacks
Types Of Ddos Attacks In The Company Cyber Terrorism AttacksThis slide demonstrates the types of DDoS attacks happening in the company, which include volume based attacks, protocol based attacks, and application layer attacks. Deliver an outstanding presentation on the topic using this Types Of Ddos Attacks In The Company Cyber Terrorism Attacks. Dispense information and present a thorough explanation of Application Layer Attacks, Protocol Based Attacks, Volume Based Attacks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Types Of Trojans Misused In Cyber Terrorism Cyber Terrorism Attacks
Types Of Trojans Misused In Cyber Terrorism Cyber Terrorism AttacksThis slide describes the types of trojans misused in cyber terrorism attacks such as downloader trojan, spyware, backdoor trojan, and rootkit trojans. Increase audience engagement and knowledge by dispensing information using Types Of Trojans Misused In Cyber Terrorism Cyber Terrorism Attacks. This template helps you present information on four stages. You can also present information on Types Of Trojans Misused In Cyber Terrorism using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Updating Hardware And Software In Company Cyber Terrorism Attacks
Updating Hardware And Software In Company Cyber Terrorism AttacksThis slide describes the updating of hardware and software in the company, including upgrading operating systems. Introducing Updating Hardware And Software In Company Cyber Terrorism Attacks to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Required, Necessitates, Installation, Transport, using this template. Grab it now to reap its full benefits.
-
 What Is Cyber Terrorism Ppt Slides Infographic Template
What Is Cyber Terrorism Ppt Slides Infographic TemplateThis slide describes cyber terrorism and how it is used to access sensitive information and political or psychological aimed attacks. Increase audience engagement and knowledge by dispensing information using What Is Cyber Terrorism Ppt Slides Infographic Template. This template helps you present information on four stages. You can also present information on Confidential, Information, Violating, Networks, Ideological using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Small Business Cyber Security Threats Ppt Powerpoint Presentation Inspiration Themes Cpb
Small Business Cyber Security Threats Ppt Powerpoint Presentation Inspiration Themes CpbPresenting our Small Business Cyber Security Threats Ppt Powerpoint Presentation Inspiration Themes Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Small Business Cyber Security Threats This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Building organizational security strategy plan contingency plan for threat handling at workplace
Building organizational security strategy plan contingency plan for threat handling at workplaceThis slide portrays information contingency plan for handling threats at workplace with the help of technical equipment that assist contingency solution and considerations. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Contingency Plan For Threat Handling At Workplace. Use it as a tool for discussion and navigation on Workplace, Information, Equipment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan how firm handle various insider threats at workplace
Building organizational security strategy plan how firm handle various insider threats at workplaceThis slide provides information regarding how firm will handle insider threats through employee training, IT security and HR coordination, etc. Introducing Building Organizational Security Strategy Plan How Firm Handle Various Insider Threats At Workplace to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Workplace, Information, Coordination, using this template. Grab it now to reap its full benefits.
-
 Determine phases of threat attack disrupting it project safety enhancing overall project security it
Determine phases of threat attack disrupting it project safety enhancing overall project security itThis slide provides information regarding various phases for threat attack disrupting IT project safety in terms of reconnaissance, weaponization, delivery and exploitation. Introducing Determine Phases Of Threat Attack Disrupting It Project Safety Enhancing Overall Project Security It to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reconnaissance, Weaponization, Exploitation, using this template. Grab it now to reap its full benefits.
-
 Enhancing overall project security it addressing various threats affecting it project safety
Enhancing overall project security it addressing various threats affecting it project safetyThis slide provides information regarding various IT threats existing at workplace disrupting IT project safety such as general and criminal IT threats. Deliver an outstanding presentation on the topic using this Enhancing Overall Project Security It Addressing Various Threats Affecting It Project Safety. Dispense information and present a thorough explanation of Service, Operations, Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enhancing overall project security it comparative assessment of various threat agents affecting
Enhancing overall project security it comparative assessment of various threat agents affectingThis slide provides information regarding comparative assessment of different threat agents impacting IT project safety comparing on various parameters such as data loss impact, skills required to handle threat, etc. Present the topic in a bit more detail with this Enhancing Overall Project Security It Comparative Assessment Of Various Threat Agents Affecting. Use it as a tool for discussion and navigation on Assessment, Operations, Maintenance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enhancing overall project security it contingency plan for managing threats to ensure
Enhancing overall project security it contingency plan for managing threats to ensureThis slide provides information regarding contingency plan for managing threats to ensure IT project safety with aid of technical equipment ensuring contingency plans. Deliver an outstanding presentation on the topic using this Enhancing Overall Project Security It Contingency Plan For Managing Threats To Ensure. Dispense information and present a thorough explanation of Contingency Plan For Managing Threats To Ensure IT Project Safety using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enhancing overall project security it determine phases of threat attack disrupting project safety contd
Enhancing overall project security it determine phases of threat attack disrupting project safety contdThis slide provides information regarding various phases for threat attack disrupting IT project safety in terms of installation, command and control, actions and objectives, covering tracks. Introducing Enhancing Overall Project Security It Determine Phases Of Threat Attack Disrupting Project Safety Contd to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Command And Control, Actions And Objectives, Covering Tracks, using this template. Grab it now to reap its full benefits.
-
 Opportunities and threats entering new markets new geos finalizing initial target
Opportunities and threats entering new markets new geos finalizing initial targetIntroducing Opportunities And Threats Entering New Markets New Geos Finalizing Initial Target to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Finalizing Initial Target Geographies, using this template. Grab it now to reap its full benefits.
-
 Opportunities and threats entering new markets new geos focus markets
Opportunities and threats entering new markets new geos focus marketsIncrease audience engagement and knowledge by dispensing information using Opportunities And Threats Entering New Markets New Geos Focus Markets. This template helps you present information on five stages. You can also present information on Focus Markets using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Opportunities and threats entering new markets new geos functional requirements
Opportunities and threats entering new markets new geos functional requirementsIntroducing Opportunities And Threats Entering New Markets New Geos Functional Requirements to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Location, Infrastructure, Process, using this template. Grab it now to reap its full benefits.
-
 Opportunities and threats entering new markets new geos local partner selection
Opportunities and threats entering new markets new geos local partner selectionDeliver an outstanding presentation on the topic using this Opportunities And Threats Entering New Markets New Geos Local Partner Selection. Dispense information and present a thorough explanation of Local Partner Selection using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Opportunities and threats entering new markets new geos market research pestle
Opportunities and threats entering new markets new geos market research pestleIncrease audience engagement and knowledge by dispensing information using Opportunities And Threats Entering New Markets New Geos Market Research Pestle. This template helps you present information on six stages. You can also present information on Sociological, Political, Economic, Technological using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Opportunities and threats entering new markets new geos porters five forces analysis
Opportunities and threats entering new markets new geos porters five forces analysisIntroducing Opportunities And Threats Entering New Markets New Geos Porters Five Forces Analysis to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Entrants, Power Of Buyers, Substitute, using this template. Grab it now to reap its full benefits.
-
 Opportunities and threats entering new markets new geos product strategy
Opportunities and threats entering new markets new geos product strategyIncrease audience engagement and knowledge by dispensing information using Opportunities And Threats Entering New Markets New Geos Product Strategy. This template helps you present information on six stages. You can also present information on Product Benefits, Product Economics, Product Budget using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Opportunities and threats entering new markets new geos score potential target geos
Opportunities and threats entering new markets new geos score potential target geosPresent the topic in a bit more detail with this Opportunities And Threats Entering New Markets New Geos Score Potential Target Geos. Use it as a tool for discussion and navigation on Market Access, Growth Potential, Competition Level. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Opportunities and threats entering new markets new geos summary geographic plan
Opportunities and threats entering new markets new geos summary geographic planIncrease audience engagement and knowledge by dispensing information using Opportunities And Threats Entering New Markets New Geos Summary Geographic Plan. This template helps you present information on five stages. You can also present information on Goals, Budget, Proposition using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Opportunities and threats entering new markets new geos table of contents
Opportunities and threats entering new markets new geos table of contentsIntroducing Opportunities And Threats Entering New Markets New Geos Table Of Contents to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Geographic, Strategic, Strategy Steps, using this template. Grab it now to reap its full benefits.
-
 Value proposition customer opportunities and threats entering new markets new geos
Value proposition customer opportunities and threats entering new markets new geosPresent the topic in a bit more detail with this Value Proposition Customer Opportunities And Threats Entering New Markets New Geos. Use it as a tool for discussion and navigation on Value Proposition Analysis. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Insider threat protection ppt powerpoint presentation professional graphic images cpb
Insider threat protection ppt powerpoint presentation professional graphic images cpbPresenting our Insider Threat Protection Ppt Powerpoint Presentation Professional Graphic Images Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Insider Threat Protection This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Swot analysis threats high staff turnover rate in technology firm
Swot analysis threats high staff turnover rate in technology firmThe slide explains the attrition rate of the employees on the monthly basis with total numbers of employees in the begging and end of the months. Deliver an outstanding presentation on the topic using this SWOT Analysis Threats High Staff Turnover Rate In Technology Firm. Dispense information and present a thorough explanation of Monthly Employee Attrition Rate Membership using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Purpose threat assessment ppt powerpoint presentation infographic template portfolio cpb
Purpose threat assessment ppt powerpoint presentation infographic template portfolio cpbPresenting Purpose Threat Assessment Ppt Powerpoint Presentation Infographic Template Portfolio Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Purpose Threat Assessment. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Risk threat vulnerability matrix ppt powerpoint presentation icon aids cpb
Risk threat vulnerability matrix ppt powerpoint presentation icon aids cpbPresenting Risk Threat Vulnerability Matrix Ppt Powerpoint Presentation Icon Aids Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Risk Threat Vulnerability Matrix. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Computer threats ppt powerpoint presentation ideas visuals cpb
Computer threats ppt powerpoint presentation ideas visuals cpbPresenting our Computer Threats Ppt Powerpoint Presentation Ideas Visuals Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Computer Threats This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Insider threat cybersecurity ppt powerpoint presentation summary outfit cpb
Insider threat cybersecurity ppt powerpoint presentation summary outfit cpbPresenting our Insider Threat Cybersecurity Ppt Powerpoint Presentation Summary Outfit Cpb PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Insider Threat Cybersecurity. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Attributable threats vs relative threats ppt powerpoint presentation ideas slideshow cpb
Attributable threats vs relative threats ppt powerpoint presentation ideas slideshow cpbPresenting Attributable Threats Vs Relative Threats Ppt Powerpoint Presentation Ideas Slideshow Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Attributable Threats Vs Relative Threats. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Threat assessment workplace ppt powerpoint presentation inspiration format cpb
Threat assessment workplace ppt powerpoint presentation inspiration format cpbPresenting Threat Assessment Workplace Ppt Powerpoint Presentation Inspiration Format Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Threat Assessment Workplace. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Threat assessments tests ppt powerpoint presentation ideas graphics pictures cpb
Threat assessments tests ppt powerpoint presentation ideas graphics pictures cpbPresenting our Threat Assessments Tests Ppt Powerpoint Presentation Ideas Graphics Pictures Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Threat Assessments Tests This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Threat monitoring response ppt powerpoint presentation model icons cpb
Threat monitoring response ppt powerpoint presentation model icons cpbPresenting Threat Monitoring Response Ppt Powerpoint Presentation Model Icons Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Threat Monitoring Response. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Threat notification system ppt powerpoint presentation gallery icon cpb
Threat notification system ppt powerpoint presentation gallery icon cpbPresenting our Threat Notification System Ppt Powerpoint Presentation Gallery Icon Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Threat Notification System This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
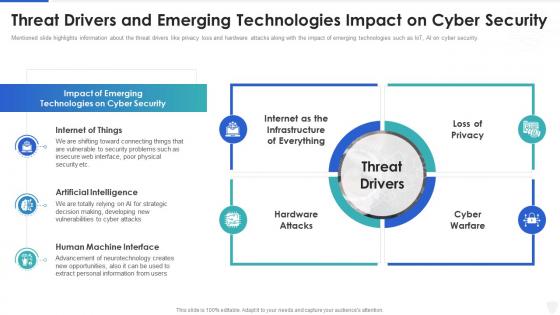 Cybersecurity and digital business risk management threat drivers and emerging technologies
Cybersecurity and digital business risk management threat drivers and emerging technologiesMentioned slide highlights information about the threat drivers like privacy loss and hardware attacks along with the impact of emerging technologies such as IoT, AI on cyber security. Deliver an outstanding presentation on the topic using this Cybersecurity And Digital Business Risk Management Threat Drivers And Emerging Technologies. Dispense information and present a thorough explanation of Internet Of Things, Artificial Intelligence, Human Machine Interface using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





