Powerpoint Templates and Google slides for Technology Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Market Positioning With Technology And Service Wireless Home Security Systems Company Profile
Market Positioning With Technology And Service Wireless Home Security Systems Company ProfileThis slide highlights the smart home security company market positioning model on the basis of digital technology and physical service capabilities of organization. Increase audience engagement and knowledge by dispensing information using Market Positioning With Technology And Service Wireless Home Security Systems Company Profile. This template helps you present information on four stages. You can also present information on Digital Technology, Physical Service Capabilities using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Information Technology Security Policy In Business Organization
Information Technology Security Policy In Business OrganizationThis slide depicts the IT security policies that shape organizations preparedness and response to security incidents within the organization. Certain policies include acceptable, use policy, access control policy, security training policy, incident response policy, and remote access policy. Introducing our premium set of slides with Information Technology Security Policy In Business Organization. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Acceptable Use Policy, Access Control Policy, Remote Access Policy. So download instantly and tailor it with your information.
-
 Cyber Security Reporting Tools For Business
Cyber Security Reporting Tools For BusinessThis slide shows comparative analysis of business cyber security reporting software. It includes features, compatibility, price and ratings.Presenting our well structured Cyber Security Reporting Tools For Business. The topics discussed in this slide are Threat Notification, Threat Monitoring, Attacks Blocking. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Checklist To Improve Information Technology Security
Checklist To Improve Information Technology SecurityThis slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Presenting our set of slides with Checklist To Improve Information Technology Security. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Change Passwords Frequently, Email Phishing Training, Regular Firewall Holes Checking.
-
 Information Technology Security Icon To Reduce Threats
Information Technology Security Icon To Reduce ThreatsIntroducing our premium set of slides with Information Technology Security Icon To Reduce Threats. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Technology Security Icon, Reduce Threats. So download instantly and tailor it with your information.
-
 Agenda Enterprise Risk Management And Information Technology Security
Agenda Enterprise Risk Management And Information Technology SecurityIntroducing Agenda Enterprise Risk Management And Information Technology Security to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Organization, IT Networks, IT Risk Management, using this template. Grab it now to reap its full benefits.
-
 Enterprise Risk Management And Information Technology Security Table Of Contents
Enterprise Risk Management And Information Technology Security Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Enterprise Risk Management And Information Technology Security Table Of Contents. This template helps you present information on one stages. You can also present information on Security Criteria, Control Measures, IT System Vulnerabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Enterprise Risk Management And Information Technology Security
Icons Slide For Enterprise Risk Management And Information Technology SecurityIntroducing our well researched set of slides titled Icons Slide For Enterprise Risk Management And Information Technology Security. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Table Of Contents For Enterprise Risk Management And Information Technology Security
Table Of Contents For Enterprise Risk Management And Information Technology SecurityIntroducing Table Of Contents For Enterprise Risk Management And Information Technology Security to increase your presentation threshold. Encompassed with eleven stages, this template is a great option to educate and entice your audience. Dispence information on IT Risks, Threat Evaluation, IT Risk Management, Cost Estimation, using this template. Grab it now to reap its full benefits.
-
 Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems
Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology SystemsThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Present the topic in a bit more detail with this Prioritized Cyber Security Threats With Risk Risk Management Guide For Information Technology Systems. Use it as a tool for discussion and navigation on Threat Risk, Risk Mitigation Plan, Risk Owner. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Technical Security Control Model With Isk Management Guide For Information Technology Systems
Technical Security Control Model With Isk Management Guide For Information Technology SystemsThe following slide highlights the technical security control model which showcases different relationships and also includes supporting technical control function for protection and security. Deliver an outstanding presentation on the topic using this Technical Security Control Model With Isk Management Guide For Information Technology Systems. Dispense information and present a thorough explanation of Technical Security, Control Model, Supporting Technical, Control Function using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Project Management Timeline With Security And Technology
Project Management Timeline With Security And TechnologyThis slide shows the monthly project management timeline for website development which includes two teams such as UX and Backend team whose main tasks are system designing, getting approval from client, creating wireframes of pages, defining website policies, etc. Presenting our well structured Project Management Timeline With Security And Technology. The topics discussed in this slide are Security, Technology, People. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Elements IT Tools Used For Cyber Security Goals Ppt Brochure
Cyber Security Elements IT Tools Used For Cyber Security Goals Ppt BrochureThis slide outlines the tools used to achieve cyber security goals such as confidentiality, integrity, and availability. The tools for confidentiality include encryption, access control, authentication, authentication, authorization, and physical security. Increase audience engagement and knowledge by dispensing information using Cyber Security Elements IT Tools Used For Cyber Security Goals Ppt Brochure. This template helps you present information on one stage. You can also present information on Tools For Confidentiality, Tools For Integrity, Tools For Availability using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Risk Management Icon In Information Technology
Cyber Security Risk Management Icon In Information TechnologyPresent the topic in a bit more detail with this Cyber Security Risk Management Icon In Information Technology. Use it as a tool for discussion and navigation on Cyber Security, Risk Management, Icon In Information Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security And Risk Management With Capabilities
Information Technology Security And Risk Management With CapabilitiesThis slide focuses on the information technology security and risk management which covers capabilities such as enterprise security strategy, compliance, vulnerability management, security architecture, data leakage protection, identify management, etc. Deliver an outstanding presentation on the topic using this Information Technology Security And Risk Management With Capabilities. Dispense information and present a thorough explanation of Security Policy Compliance, Compliance, Enterprise Security Strategy using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Model For Information Technology Security Risk Management
Model For Information Technology Security Risk ManagementThis slide shows the model that depicts IT security risk management which focuses on identification, protection, detection, response and recovery planning with security asset management, governance, data security, detection processes, risk analysis and planning, etc. Introducing Model For Information Technology Security Risk Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Identifying, Protecting, Detecting, using this template. Grab it now to reap its full benefits.
-
 Risk Management Matrix For Information Technology Security
Risk Management Matrix For Information Technology SecurityThis slide shows the risk management matrix for information technology security which covers the business workflow and technical systems with IT risks and threats such as software security, business controls, control risk modelling, penetration testing, attack modelling, etc. Present the topic in a bit more detail with this Risk Management Matrix For Information Technology Security. Use it as a tool for discussion and navigation on Corporate Workflow, Risks, Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Risk Management Methodology In Information Technology Security
Risk Management Methodology In Information Technology SecurityThis slide focuses on the risk management methodology in information technology security which includes three different phases such as assessment, mitigation and continual evaluation assessment that are helpful in effective management of security risks and hazards. Deliver an outstanding presentation on the topic using this Risk Management Methodology In Information Technology Security. Dispense information and present a thorough explanation of Assessment, Mitigation, Continual Evaluation Assessment using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
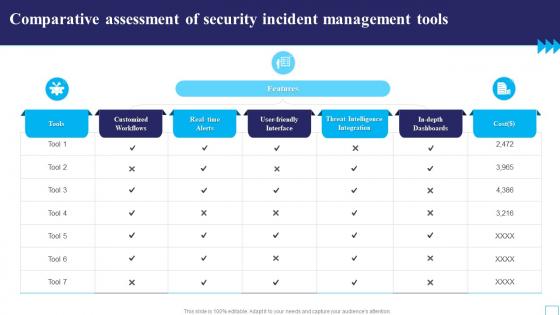 Comparative Assessment Of Security Incident Management Tools
Comparative Assessment Of Security Incident Management ToolsPresenting our well structured Comparative Assessment Of Security Incident Management Tools. The topics discussed in this slide are Customized Workflows, User Friendly Interface, Threat Intelligence Integration. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Icon Showing Data Security Through Blockchain Technology In Supply Chain
Icon Showing Data Security Through Blockchain Technology In Supply ChainPresenting our well structured Icon Showing Data Security Through Blockchain Technology In Supply Chain. The topics discussed in this slide are Icon Showing Data Security, Blockchain Technology, Supply Chain. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 IOT Security Through Blockchain Technology
IOT Security Through Blockchain TechnologyThis slide covers steps for processing crypto currency transactions using block chain P2P technology. The purpose of this slide is to provide information on securing financial transactions. It includes steps from requesting transaction, transferring it on P2P network, validating transactions, creation of new data block, etc. Introducing our premium set of slides with IOT Security Through Blockchain Technology. Elucidate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like IOT Security Through, Blockchain Technology. So download instantly and tailor it with your information.
-
 Reverse Proxy Server Side Technology Security Reverse Proxy Load Balancer Ppt Elements
Reverse Proxy Server Side Technology Security Reverse Proxy Load Balancer Ppt ElementsThis slide explains the reverse proxy server side technology, that is security, and how data is transmitted securely in the presence of a proxy server that hides the actual servers identity. Present the topic in a bit more detail with this Reverse Proxy Server Side Technology Security Reverse Proxy Load Balancer Ppt Elements. Use it as a tool for discussion and navigation on Security Proxy Session, Reverse Proxy Server, Technology Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security Operations
Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security OperationsThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Present the topic in a bit more detail with this Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Information, Management, Automation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security Operations
Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security OperationsThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Increase audience engagement and knowledge by dispensing information using Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security Operations. This template helps you present information on four stages. You can also present information on Ineffective, Information, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations
Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security OperationsThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Present the topic in a bit more detail with this Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Automation, Integrates, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F651 Security Automation In Information Technology Security Automation Architecture With Key Elements
F651 Security Automation In Information Technology Security Automation Architecture With Key ElementsThis slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Present the topic in a bit more detail with this F651 Security Automation In Information Technology Security Automation Architecture With Key Elements. Use it as a tool for discussion and navigation on Security, Automation, Architecture. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 F653 Security Automation In Information Technology Security Automation Stages With Maturity Level
F653 Security Automation In Information Technology Security Automation Stages With Maturity LevelThis slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Present the topic in a bit more detail with this F653 Security Automation In Information Technology Security Automation Stages With Maturity Level. Use it as a tool for discussion and navigation on Systematic Stage, Institutionalized Stage, Opportunistic Stage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security And Privacy Roadmap
Information Technology Security And Privacy RoadmapThe following slide showcases IT security and privacy roadmap to protect digital information from severe threats. It includes elements such as assess, build, select, deploy, train and test. Introducing our premium set of slides with name Information Technology Security And Privacy Roadmap. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Categorize Assets, Security Tool, Software Required. So download instantly and tailor it with your information.
-
 Security And Privacy Issues In Cloud Technology
Security And Privacy Issues In Cloud TechnologyThe following slide depicts some security and privacy concerns associated with clout network to meet compliance and protect individual interest. It includes elements such as underdeveloped saas safety, infrastructure, control etc. Introducing our premium set of slides with name Security And Privacy Issues In Cloud Technology. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Underdeveloped Laas And Saas Security, Rapid Changes And Delivery, Responsibility Security Model. So download instantly and tailor it with your information.
-
 Technologies To Ensure Data Security And Privacy
Technologies To Ensure Data Security And PrivacyThe following slide showcases some technologies to administer organizational data privacy and security concerns. It includes elements such as data encryption, change management and auditing, user and behavior analytics UEBA, backup and recovery etc. Introducing our premium set of slides with name Technologies To Ensure Data Security And Privacy. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Encryption, Change Management And Auditing, Backup And Recovery. So download instantly and tailor it with your information.
-
 Security Architecture In 5G Technology Architecture And Functioning Of 5G
Security Architecture In 5G Technology Architecture And Functioning Of 5GThis slide represents the security architecture in 5G technology, including the system-wide security tasks and 5G function element deployments or vertical security. The components include devices, global wireless solutions, access and network, applications and cloud infrastructure, and user ID administration. Deliver an outstanding presentation on the topic using this Security Architecture In 5G Technology Architecture And Functioning Of 5G. Dispense information and present a thorough explanation of User ID Administration, Apps And Cloud Infrastructure, Access And Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security In 5G Technology Architecture Architecture And Functioning Of 5G
Security In 5G Technology Architecture Architecture And Functioning Of 5GThis slide depicts the security in 5G architecture, including the standards detailed by 3GPP 3rd Generation Partnership Project, such as SUPI, unified authentication, extensible authentication standards, and flexible security policies. Present the topic in a bit more detail with this Security In 5G Technology Architecture Architecture And Functioning Of 5G. Use it as a tool for discussion and navigation on Service Delivery Process, Mobile Technologys, Security Procedures. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Reverse Proxy Server Side Technology Security Ppt Powerpoint Presentation Infographic Template Examples
Reverse Proxy Server Side Technology Security Ppt Powerpoint Presentation Infographic Template ExamplesThis slide explains the reverse proxy server side technology, that is security, and how data is transmitted securely in the presence of a proxy server that hides the actual servers identity. Present the topic in a bit more detail with this Reverse Proxy Server Side Technology Security Ppt Powerpoint Presentation Infographic Template Examples. Use it as a tool for discussion and navigation on Security Proxy, Reverse Proxy, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation In Information Technology Domain Security Controls That Can Be Automated
Security Automation In Information Technology Domain Security Controls That Can Be AutomatedThis slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Present the topic in a bit more detail with this Security Automation In Information Technology Domain Security Controls That Can Be Automated. Use it as a tool for discussion and navigation on Information Security, Organization, Operations Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
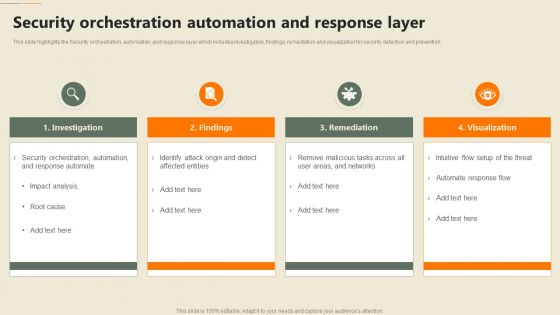 Security Automation In Information Technology Security Orchestration Automation And Response Layer
Security Automation In Information Technology Security Orchestration Automation And Response LayerThis slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention Increase audience engagement and knowledge by dispensing information using Security Automation In Information Technology Security Orchestration Automation And Response Layer. This template helps you present information on four stages. You can also present information on Investigation, Remediation, Visualization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Different Security Automation Tools With Pros Security Automation To Investigate And Remediate Cyberthreats
Different Security Automation Tools With Pros Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Present the topic in a bit more detail with this Different Security Automation Tools With Pros Security Automation To Investigate And Remediate Cyberthreats. Use it as a tool for discussion and navigation on Automation, Security Orchestration, Response. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impacts Of Ineffective Information Technology Security Automation To Investigate And Remediate Cyberthreats
Impacts Of Ineffective Information Technology Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Increase audience engagement and knowledge by dispensing information using Impacts Of Ineffective Information Technology Security Automation To Investigate And Remediate Cyberthreats. This template helps you present information on five stages. You can also present information on Ineffective, Information, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Automation Integrates Tools Systems And Security Automation To Investigate And Remediate Cyberthreats
Security Automation Integrates Tools Systems And Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Increase audience engagement and knowledge by dispensing information using Security Automation Integrates Tools Systems And Security Automation To Investigate And Remediate Cyberthreats. This template helps you present information on eight stages. You can also present information on Automation, Processes, System Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda For Security Automation In Information Technology
Agenda For Security Automation In Information TechnologyIncrease audience engagement and knowledge by dispensing information using Agenda For Security Automation In Information Technology. This template helps you present information on six stages. You can also present information on Business, Process, Importance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Determine Ideal Tasks For Security Automation Security Automation In Information Technology
Determine Ideal Tasks For Security Automation Security Automation In Information Technologyslide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Present the topic in a bit more detail with this Determine Ideal Tasks For Security Automation Security Automation In Information Technology. Use it as a tool for discussion and navigation on Security Automation, Determine, Sensitive Tasks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Security Automation Tools With Pros And Cons Security Automation In Information Technology
Different Security Automation Tools With Pros And Cons Security Automation In Information TechnologyThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM Deliver an outstanding presentation on the topic using this Different Security Automation Tools With Pros And Cons Security Automation In Information Technology. Dispense information and present a thorough explanation of Automation, Security Orchestration, Process Automation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Network It Security Automation Security Automation In Information Technology
Enterprise Network It Security Automation Security Automation In Information TechnologyThis slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Increase audience engagement and knowledge by dispensing information using Enterprise Network It Security Automation Security Automation In Information Technology. This template helps you present information on six stages. You can also present information on Orchestrating Network Security, Security Policy Automation, Infrastructure using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
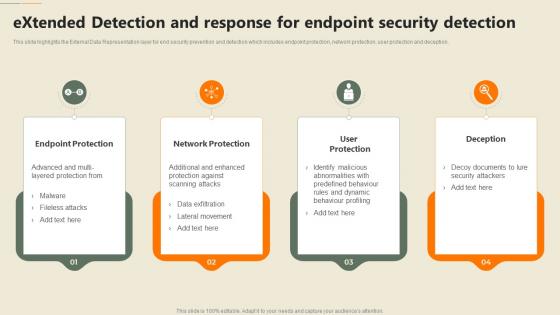 Extended Detection And Response For Endpoint Security Detection Security Automation In Information Technology
Extended Detection And Response For Endpoint Security Detection Security Automation In Information TechnologyThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deception. Increase audience engagement and knowledge by dispensing information using Extended Detection And Response For Endpoint Security Detection Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Endpoint Protection, Network Protection, Deception using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide Security Automation In Information Technology
Icons Slide Security Automation In Information TechnologyPresent the topic in a bit more detail with this Icons Slide Security Automation In Information Technology. Use it as a tool for discussion and navigation on Icons. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
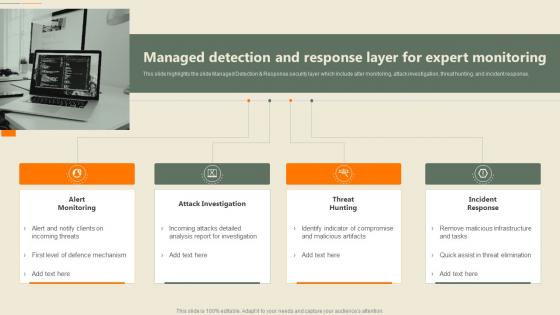 Managed Detection And Response Layer For Expert Monitoring Security Automation In Information Technology
Managed Detection And Response Layer For Expert Monitoring Security Automation In Information TechnologyThis slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response Increase audience engagement and knowledge by dispensing information using Managed Detection And Response Layer For Expert Monitoring Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Attack Investigation, Incident Response, Threat Hunting using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Measure Security Automation Metrics For Operations Efficiency Security Automation In Information Technology
Measure Security Automation Metrics For Operations Efficiency Security Automation In Information TechnologyThis slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Present the topic in a bit more detail with this Measure Security Automation Metrics For Operations Efficiency Security Automation In Information Technology. Use it as a tool for discussion and navigation on Automation, Operations Efficiency, Performance Improvements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Right Time To Add Automation In Security Security Automation In Information Technology
Right Time To Add Automation In Security Security Automation In Information TechnologyThis slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Deliver an outstanding presentation on the topic using this Right Time To Add Automation In Security Security Automation In Information Technology. Dispense information and present a thorough explanation of Individual, Insights, Automation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
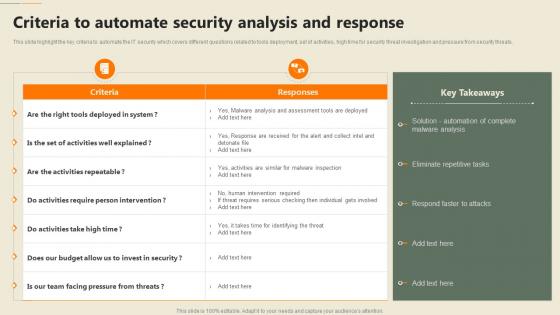 Security Automation In Information Technology Criteria To Automate Security Analysis And Response
Security Automation In Information Technology Criteria To Automate Security Analysis And ResponseThis slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Present the topic in a bit more detail with this Security Automation In Information Technology Criteria To Automate Security Analysis And Response. Use it as a tool for discussion and navigation on Analysis, Eliminate Repetitive Tasks, Respond Faster To Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation In Information Technology Impacts Of Ineffective Information Technology Security
Security Automation In Information Technology Impacts Of Ineffective Information Technology SecurityThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Increase audience engagement and knowledge by dispensing information using Security Automation In Information Technology Impacts Of Ineffective Information Technology Security. This template helps you present information on five stages. You can also present information on Information, Technology, Automation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Security Automation In Information Technology Table Of Contents
Security Automation In Information Technology Table Of ContentsIncrease audience engagement and knowledge by dispensing information using Security Automation In Information Technology Table Of Contents. This template helps you present information on one stages. You can also present information on Security Automation, Processes, Security Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Security Automation Integrates Tools Systems And Processes Security Automation In Information Technology
Security Automation Integrates Tools Systems And Processes Security Automation In Information TechnologyThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Increase audience engagement and knowledge by dispensing information using Security Automation Integrates Tools Systems And Processes Security Automation In Information Technology. This template helps you present information on eight stages. You can also present information on Automation, Integrates, Processes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Security Processes That Cant Be Automated Security Automation In Information Technology
Security Processes That Cant Be Automated Security Automation In Information TechnologyThe following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Increase audience engagement and knowledge by dispensing information using Security Processes That Cant Be Automated Security Automation In Information Technology. This template helps you present information on three stages. You can also present information on Threat Modeling, Penetration Testing, Bug Bounty using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents Security Automation In Information Technology
Table Of Contents Security Automation In Information TechnologyPresent the topic in a bit more detail with this Table Of Contents Security Automation In Information Technology. Use it as a tool for discussion and navigation on Security Automation, Architecture And Importance, Automation Dashboards. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Unified Platform Integration For Security Automation Security Automation In Information Technology
Unified Platform Integration For Security Automation Security Automation In Information TechnologyThis slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Increase audience engagement and knowledge by dispensing information using Unified Platform Integration For Security Automation Security Automation In Information Technology. This template helps you present information on four stages. You can also present information on Access Management, Security Automation, Firewalls using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations
-
 Why To Automate The It Security Process Security Automation In Information Technology
Why To Automate The It Security Process Security Automation In Information TechnologyThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Security Automation In Information Technology. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Risks Associated With EDI Technology
Security Risks Associated With EDI TechnologyThis slide provides glimpse about different risks compromising security that are associated with Electronic Data Interchange technology. It includes risks such as disclosure, message modification, sequence modification, etc. Introducing our Security Risks Associated With EDI Technology set of slides. The topics discussed in these slides are Security Risks Associated, EDI Technology. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Future Cyber Security Technologies In Powerpoint And Google Slides Cpb
Future Cyber Security Technologies In Powerpoint And Google Slides CpbPresenting our Future Cyber Security Technologies In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Future Cyber Security Technologies This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 IOT Security Lock For Safe Fleet Management Using IOT Technologies For Better Logistics
IOT Security Lock For Safe Fleet Management Using IOT Technologies For Better LogisticsThe following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Present the topic in a bit more detail with this IOT Security Lock For Safe Fleet Management Using IOT Technologies For Better Logistics. Use it as a tool for discussion and navigation on Multiple Positioning, Multiple Alarm, Behavior Alarm. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Operations Of Logistics Through Integrated IOT Using IOT Technologies For Better Logistics
Securing Operations Of Logistics Through Integrated IOT Using IOT Technologies For Better LogisticsThis slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc.Deliver an outstanding presentation on the topic using this Securing Operations Of Logistics Through Integrated IOT Using IOT Technologies For Better Logistics. Dispense information and present a thorough explanation of System Integration, Management Capabilities, Quicker Decision using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategy To Provide Layered Security Across Networks Using IOT Technologies For Better Logistics
Strategy To Provide Layered Security Across Networks Using IOT Technologies For Better LogisticsThis slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Present the topic in a bit more detail with this Strategy To Provide Layered Security Across Networks Using IOT Technologies For Better Logistics. Use it as a tool for discussion and navigation on Profile Authentication, Allocation Appropriate, Particular Applications. This template is free to edit as deemed fit for your organization. Therefore download it now.





