Powerpoint Templates and Google slides for Technology Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Information Technology Security Hardware And Software Update In Company
Information Technology Security Hardware And Software Update In CompanyThis slide depicts the hardware or software update measure under the cyber security model. It also tells the current status of the devices that need to update in the organization. Increase audience engagement and knowledge by dispensing information using Information Technology Security Hardware And Software Update In Company. This template helps you present information on three stages. You can also present information on Hardware And Software Update In Company using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security How Is Automation Used In Information Technology Security
Information Technology Security How Is Automation Used In Information Technology SecurityThis slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Introducing Information Technology Security How Is Automation Used In Information Technology Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Threat Detection, Threat Response, Human Augmentation, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Information Technology Security Elements
Information Technology Security Information Technology Security ElementsThis slide represents the different elements of cyber security such as application security, network security, information security, etc. Introducing Information Technology Security Information Technology Security Elements to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on End User Education, Operational Security, Information Security, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security It Infrastructure Information Budget For Fy2022
Information Technology Security It Infrastructure Information Budget For Fy2022This slide represents the budget for IT infrastructure after implementing cyber security, and it also shows the amount each task will cost the company. Present the topic in a bit more detail with this Information Technology Security It Infrastructure Information Budget For Fy2022. Use it as a tool for discussion and navigation on Infrastructure, Information, Technology. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Latest Threats In Information Technology Security
Information Technology Security Latest Threats In Information Technology SecurityThis slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Deliver an outstanding presentation on the topic using this Information Technology Security Latest Threats In Information Technology Security. Dispense information and present a thorough explanation of Latest Threats In Information Technology Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Main Steps Of Operational Security
Information Technology Security Main Steps Of Operational SecurityThis slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Present the topic in a bit more detail with this Information Technology Security Main Steps Of Operational Security. Use it as a tool for discussion and navigation on Assessment Of Risks, Define Sensitive Information, Identify Potential Threats This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Managing Information Technology Security 90 Days Plan
Information Technology Security Managing Information Technology Security 90 Days PlanThis slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an outstanding presentation on the topic using this Information Technology Security Managing Information Technology Security 90 Days Plan. Dispense information and present a thorough explanation of Managing, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Minimize Administrative And Staff Privileges
Information Technology Security Minimize Administrative And Staff PrivilegesThis slide shows the importance of minimizing the administrative and staff privilege by showing its benefits for the company. Introducing Information Technology Security Minimize Administrative And Staff Privileges to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Minimize Administrative And Staff Privileges, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Network Security
Information Technology Security Network SecurityThis slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Increase audience engagement and knowledge by dispensing information using Information Technology Security Network Security. This template helps you present information on seven stages. You can also present information on Information, Technology, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Of Information Technology Security Disaster Recovery Planning
Information Technology Security Of Information Technology Security Disaster Recovery PlanningThis slide depicts the disaster recovery plan in the cyber security model and what strategies an organization needs to adopt to recover from an attack or natural disaster. Introducing Information Technology Security Of Information Technology Security Disaster Recovery Planning to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Information, Technology, Security using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Operational Security
Information Technology Security Operational SecurityThis slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Increase audience engagement and knowledge by dispensing information using Information Technology Security Operational Security. This template helps you present information on five stages. You can also present information on Change Management, Processes, Deploy Automation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Process Of Disaster Recovery Planning
Information Technology Security Process Of Disaster Recovery PlanningThis slide represents the detailed process of a disaster recovery plan, how it should work, what points to keep in mind, and what steps to be performed to build the best recovery plan. Introducing Information Technology Security Process Of Disaster Recovery Planning to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Process Of Disaster Recovery Planning, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Roadmap For Information Technology Security Training
Information Technology Security Roadmap For Information Technology Security TrainingThis slide depicts the cyber security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Introducing Information Technology Security Roadmap For Information Technology Security Training to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Roadmap, Information, Technology, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Safety Tips Protection Against Cyberattacks
Information Technology Security Safety Tips Protection Against CyberattacksThis slide represents various tips or procedures that can be followed to prevent an organizations cyber security from cyberattacks or cybercriminals. Increase audience engagement and knowledge by dispensing information using Information Technology Security Safety Tips Protection Against Cyberattacks. This template helps you present information on five stages. You can also present information on Cyber Safety Tips Protection Against Cyberattacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Set Measures For Secure Communication
Information Technology Security Set Measures For Secure CommunicationThis slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. Introducing Information Technology Security Set Measures For Secure Communication to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Organization, Measures, Communication, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Strategies To Manage Cyber Risks
Information Technology Security Strategies To Manage Cyber RisksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Increase audience engagement and knowledge by dispensing information using Information Technology Security Strategies To Manage Cyber Risks. This template helps you present information on four stages. You can also present information on Strategic, Structures, Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Table Of Contents
Information Technology Security Table Of ContentsIntroducing Information Technology Security Table Of Contents to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Information, Technology, Security, using this template. Grab it now to reap its full benefits.
-
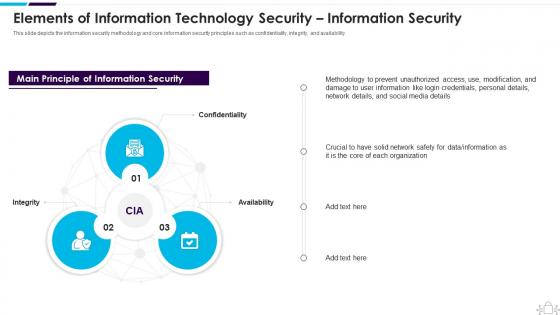 Information Technology Security Technology Security Information Security
Information Technology Security Technology Security Information SecurityThis slide depicts the information security methodology and core information security principles such as confidentiality, integrity, and availability. Increase audience engagement and knowledge by dispensing information using Information Technology Security Technology Security Information Security. This template helps you present information on three stages. You can also present information on Confidentiality, Availability, Integrity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Threats In Information Technology Security
Information Technology Security Threats In Information Technology SecurityThis slide depicts the main types of threats in cyber security, such as cybercrime, cyber terrorism, and cyberattacks to an organization and the purpose of each category threat. Introducing Information Technology Security Threats In Information Technology Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Types Of Threats In Information Technology Security, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Types Of Disaster Recovery Plan
Information Technology Security Types Of Disaster Recovery PlanThis slide defines the different categories of disaster recovery plans, namely as data center disaster recovery plans, cloud based disaster recovery plans, etc. Increase audience engagement and knowledge by dispensing information using Information Technology Security Types Of Disaster Recovery Plan. This template helps you present information on four stages. You can also present information on Disaster, Recovery, Virtualization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security What Is Information Technology Security And How Does It Work
Information Technology Security What Is Information Technology Security And How Does It WorkThis slide defines the meaning of cyber security and how it helps to prevent data through different methods and techniques. Introducing Information Technology Security What Is Information Technology Security And How Does It Work to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Information, Technology, Security, using this template. Grab it now to reap its full benefits.
-
 Main Principle Of Information Security Information Technology Security
Main Principle Of Information Security Information Technology SecurityThis slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver an outstanding presentation on the topic using this Main Principle Of Information Security Information Technology Security. Dispense information and present a thorough explanation of Main Principle Of Information Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managing Information Technology Security 30 Days Plan Information Technology Security
Managing Information Technology Security 30 Days Plan Information Technology SecurityThis slide depicts how the cyber security model will work in the first 30 days and the tasks the organization should focus on. Present the topic in a bit more detail with this Managing Information Technology Security 30 Days Plan Information Technology Security. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prepare A Disaster Recovery Plan Information Technology Security
Prepare A Disaster Recovery Plan Information Technology SecurityThis slide depicts what factors will be considered while preparing a recovery planning of an organization to come back to business quickly and effectively. Introducing Prepare A Disaster Recovery Plan Information Technology Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Assessment Report, Importance Of Assets, Recovery Plan, using this template. Grab it now to reap its full benefits.
-
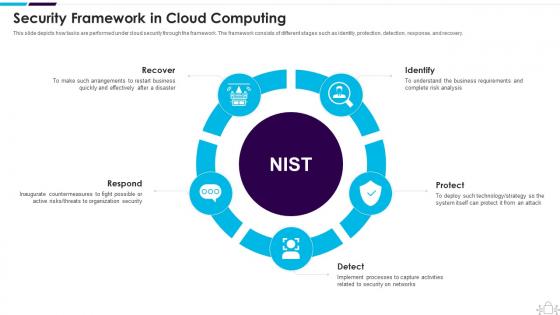 Security Framework In Cloud Computing Information Technology Security
Security Framework In Cloud Computing Information Technology SecurityThis slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. Increase audience engagement and knowledge by dispensing information using Security Framework In Cloud Computing Information Technology Security. This template helps you present information on five stages. You can also present information on Recover, Respond, Identify using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents For Information Technology Security
Table Of Contents For Information Technology SecurityIntroducing Table Of Contents For Information Technology Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Information, Technology, Security, using this template. Grab it now to reap its full benefits.
-
 Timeline For The Implementation Of Information Technology Security
Timeline For The Implementation Of Information Technology SecurityThis slide shows the timeline for cyber security model implementation in an organization and the tasks to be performed every month. Deliver an outstanding presentation on the topic using this Timeline For The Implementation Of Information Technology Security. Dispense information and present a thorough explanation of Implementation, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 What Are The Benefits Of Information Technology Security
What Are The Benefits Of Information Technology SecurityThis slide depicts the different benefits of deploying a cyber security model in an organization and how it can minimize the risk and save a companys time, money, and efforts. Introducing What Are The Benefits Of Information Technology Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on What Are The Benefits Of Information Technology Security, using this template. Grab it now to reap its full benefits.
-
 Blockchain technology it is blockchain technology secure
Blockchain technology it is blockchain technology secureThis slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. Introducing Blockchain Technology It Is Blockchain Technology Secure to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain, Technology, Secure, using this template. Grab it now to reap its full benefits.
-
 Enhancing overall project security it technological assessment of firm current
Enhancing overall project security it technological assessment of firm currentThis slide provides information regarding present management capabilities technological assessment based on several parameters such as incidents and service requests handling rate, service failure rate, customer satisfaction score, etc. Present the topic in a bit more detail with this Enhancing Overall Project Security It Technological Assessment Of Firm Current. Use it as a tool for discussion and navigation on Technological, Assessment, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber security apps ppt powerpoint presentation professional background designs cpb
Cyber security apps ppt powerpoint presentation professional background designs cpbPresenting our Cyber Security Apps Ppt Powerpoint Presentation Professional Background Designs Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Cyber Security Apps This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Is Digital Ledger Technology Secure Ppt Ideas Skills
Is Digital Ledger Technology Secure Ppt Ideas SkillsThis slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. Introducing Is Digital Ledger Technology Secure Ppt Ideas Skills to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on is digital ledger technology secure, using this template. Grab it now to reap its full benefits.
-
 Configure Network Security Technologies Ppt Powerpoint Presentation Inspiration Show Cpb
Configure Network Security Technologies Ppt Powerpoint Presentation Inspiration Show CpbPresenting Configure Network Security Technologies Ppt Powerpoint Presentation Inspiration Show Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Configure Network Security Technologies. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Need Of Cyber Security In Organization Integration Of Digital Technology In Business
Need Of Cyber Security In Organization Integration Of Digital Technology In BusinessThis slide covers the need of introducing cybersecurity in the business and how can organization integrate cybersecurity with digital transformation.Introducing Need Of Cyber Security In Organization Integration Of Digital Technology In Business to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Security For Confidential Data, Protection Phishing Scams, Protection Against Malware using this template. Grab it now to reap its full benefits.
-
 Market Positioning With Technology And Service Capabilities Home Security Systems Company Profile
Market Positioning With Technology And Service Capabilities Home Security Systems Company ProfileThis slide highlights the smart home security company market positioning model on the basis of digital technology and physical service capabilities of organization. Present the topic in a bit more detail with this Market Positioning With Technology And Service Capabilities Home Security Systems Company Profile . Use it as a tool for discussion and navigation on Technology, Service, Capabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Is Blockchain Technology Secure Blockchain And Distributed Ledger Technology
Is Blockchain Technology Secure Blockchain And Distributed Ledger TechnologyThis slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain. Introducing Is Blockchain Technology Secure Blockchain And Distributed Ledger Technology to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Is Blockchain Technology Secure, using this template. Grab it now to reap its full benefits.
-
 Automatic Technology Steps To Ensure Robotic Process Automation Security
Automatic Technology Steps To Ensure Robotic Process Automation SecurityThis slide defines steps to ensure the security of robotic process automation, and it covers guarantee accountability for bot activities, protection from abuse, frauds, logs and bot development. Introducing Automatic Technology Steps To Ensure Robotic Process Automation Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Guarantee Accountability, Protect Log Respectability, RPA Development, using this template. Grab it now to reap its full benefits.
-
 Benefit Of Block Chain Technology For Securing Confidential Data Icon
Benefit Of Block Chain Technology For Securing Confidential Data IconPresenting our set of slides with Benefit Of Block Chain Technology For Securing Confidential Data Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Block Chain Technology, Securing Confidential Data.
-
 Tools Used In Cloud Security Cloud Information Security
Tools Used In Cloud Security Cloud Information SecurityThis slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud.Introducing Tools Used In Cloud Security Cloud Information Security to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Security, Access Control, Threat Detection using this template. Grab it now to reap its full benefits.
-
 Most Effective It Security Tools For Protection Against Insider Threat
Most Effective It Security Tools For Protection Against Insider ThreatThis slide shows most effective IT security tools for protection against insider threats. It provides information about data loss prevention DLP, user and entity behavior UEBA, identity and access management IAM and security information and event management SIEM Introducing our premium set of slides with Most Effective It Security Tools For Protection Against Insider Threat. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Loss Prevention, User Entity Behavior, Identity Access Management. So download instantly and tailor it with your information.
-
 Is Blockchain Technology Secure Cryptographic Ledger
Is Blockchain Technology Secure Cryptographic LedgerThis slide defines the security of blockchain technology and how hash codes are helpful to maintain data integrity and security in blockchain.Introducing Is Blockchain Technology Secure Cryptographic Ledger to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Bitcoins Blockchain, Blockchain Technology, Weaknesses In Blockchain, using this template. Grab it now to reap its full benefits.
-
 Cloud Computing Security Tools Used In Cloud Security Ppt Infographics
Cloud Computing Security Tools Used In Cloud Security Ppt InfographicsThis slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. Increase audience engagement and knowledge by dispensing information using Cloud Computing Security Tools Used In Cloud Security Ppt Infographics. This template helps you present information on ten stages. You can also present information on Cloud Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Market Positioning With Technology And Service Capabilities Smart Security Systems Company Profile
Market Positioning With Technology And Service Capabilities Smart Security Systems Company ProfileThis slide highlights the smart home security company market positioning model on the basis of digital technology and physical service capabilities of organization. Present the topic in a bit more detail with this Market Positioning With Technology And Service Capabilities Smart Security Systems Company Profile. Use it as a tool for discussion and navigation on Technology, Service, Capabilities . This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Market Positioning With Technology And Service Security Alarm And Monitoring Systems Company Profile
Market Positioning With Technology And Service Security Alarm And Monitoring Systems Company ProfileThis slide highlights the smart home security company market positioning model on the basis of digital technology and physical service capabilities of organization. Present the topic in a bit more detail with this Market Positioning With Technology And Service Security Alarm And Monitoring Systems Company Profile. Use it as a tool for discussion and navigation on Technology, Service, Capabilities. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Approaches Technologies In Powerpoint And Google Slides Cpb
Cyber Security Approaches Technologies In Powerpoint And Google Slides CpbPresenting our Cyber Security Approaches Technologies In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cyber Security Approaches Technologies. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Information Technology Security Analysis For Small Business
Information Technology Security Analysis For Small BusinessThis slide covers the information related tot the security analysis of the IT department to know the risk involved in the assets and the required actions to be taken to control them. It also includes the impact and risk level with the risk and threat of security. Introducing our Information Technology Security Analysis For Small Business set of slides. The topics discussed in these slides are IT Assets, Security Risk, Security Threat. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Top Four Network Security Analysis Tools
Top Four Network Security Analysis ToolsThis slide covers the tools used for the security analysis of the networks with their usage according to their needs on different occasions. It also includes the price or cost of these tools. Presenting our set of slides with Top Four Network Security Analysis Tools. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Tools, Price, Crafting Packets, Set Customized Filters.
-
 Major Tools For Managed Security Service
Major Tools For Managed Security ServiceMentioned slide outlines various tools for managed security service. Email security software, endpoint protection and firewall are some of the comprehensive tools which will assist the organization in closely monitoring the advance threats. Introducing our Major Tools For Managed Security Service set of slides. The topics discussed in these slides are Email Security Software, Endpoint Protection, Email Security Software. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Data Protection Tools Used In Cloud Security
Cloud Data Protection Tools Used In Cloud SecurityThis slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud. Increase audience engagement and knowledge by dispensing information using Cloud Data Protection Tools Used In Cloud Security. This template helps you present information on one stage. You can also present information on Cloud Solutions, Security, Networks using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Key Security Considerations Road To 5G Era Technology And Architecture
Key Security Considerations Road To 5G Era Technology And ArchitectureThis slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an outstanding presentation on the topic using this Key Security Considerations Road To 5G Era Technology And Architecture. Dispense information and present a thorough explanation of Threat Handling Initiatives, Denial Service, Information Interception using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Key Security Considerations For 5g For Threat Handling 5g Mobile Technology Guidelines Operators
Key Security Considerations For 5g For Threat Handling 5g Mobile Technology Guidelines OperatorsThis slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an outstanding presentation on the topic using this Key Security Considerations For 5g For Threat Handling 5g Mobile Technology Guidelines Operators. Dispense information and present a thorough explanation of Unauthorized Activities, Virtualization Threats, Information Interception using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Four Information Technology Security Processes
Four Information Technology Security ProcessesThis slide shows the four step by step processes used in information technology security. It includes penetration testing, VPN configuration, network security audit checklist and privileged password management. Presenting our set of slides with Four Information Technology Security Processes. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Penetration Testing, VPNConfiguration, Network Security Audit.
-
 Four Information Technology Security Threats
Four Information Technology Security ThreatsIntroducing our premium set of slides with Four Information Technology Security Threats. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Phishing Attacks, Cloud Jacking, Insider Threats. So download instantly and tailor it with your information.
-
 Impact Of Cybercrime On Information Technology Security
Impact Of Cybercrime On Information Technology SecurityThis slide shows the adverse impact of cybercrime on information technology company. These impacts are increased costs, operational disruption, revenue loss and stolen intellectual property. Presenting our set of slides with Impact Of Cybercrime On Information Technology Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Increased Costs, Operational Disruption, Revenue Loss.
-
 Information Technology Cyber Security Icon
Information Technology Cyber Security IconIntroducing our premium set of slides with Information Technology Cyber Security Icon. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Technology, Cyber Security. So download instantly and tailor it with your information.
-
 Information Technology Safety And Security Icon
Information Technology Safety And Security IconPresenting our set of slides with Information Technology Safety And Security Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Information Technology, Safety And Security.
-
 Multipoint Checklist To Improve Information Technology Security
Multipoint Checklist To Improve Information Technology SecurityThis slide shows comprehensive checklist used to enhance information technology security. It includes email phishing training, anti virus and malware use, password changes etc. Presenting our well structured Multipoint Checklist To Improve Information Technology Security. The topics discussed in this slide are Control Administrative, Antivirus And Anti Malware, Email Phishing Training. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Three Types Of Information Technology Security
Three Types Of Information Technology SecurityIntroducing our premium set of slides with Three Types Of Information Technology Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Security, End Point Security, Internet Security. So download instantly and tailor it with your information.
-
 Various KPIs To Measure Information Technology Security System
Various KPIs To Measure Information Technology Security SystemThis slide shows the different KPIs used to measure IT security system. These are level of preparedness, intrusion attempts, days to patch, incidents reported etc. Presenting our set of slides with Various KPIs To Measure Information Technology Security System. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Key Performance Indicators, Excepted Results, Actual Results.
-
 5G Technology Enabling Key Security Considerations For 5G For Threat Handling
5G Technology Enabling Key Security Considerations For 5G For Threat HandlingThis slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an outstanding presentation on the topic using this 5G Technology Enabling Key Security Considerations For 5G For Threat Handling. Dispense information and present a thorough explanation of Threat Handling Initiatives, Concerns To Catered, Assets Managed using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





