Powerpoint Templates and Google slides for Security Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
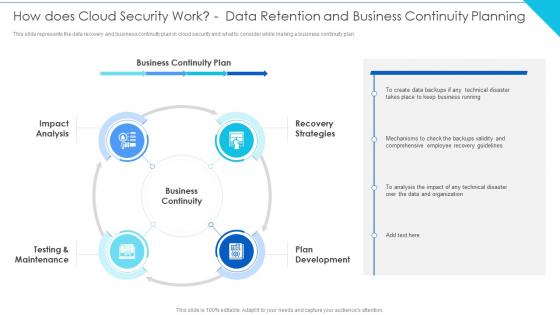 Cloud Information Security How Does Cloud Security Work Data Planning
Cloud Information Security How Does Cloud Security Work Data PlanningThis slide represents the data recovery and business continuity plan in cloud security and what to consider while making a business continuity plan.Increase audience engagement and knowledge by dispensing information using Cloud Information Security How Does Cloud Security Work Data Planning This template helps you present information on five stages. You can also present information on Implement Information, Authentication Process, Data Encryption using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Best Practices Cloud Information Security
Cloud Security Best Practices Cloud Information SecurityThis slide defines the best practices of cloud security, including understanding cloud utilization and risk, protection of cloud, and responding to cloud protection issues.Present the topic in a bit more detail with this Cloud Security Best Practices Cloud Information Security Use it as a tool for discussion and navigation on Control Identity, Administrative Rights, Access Systems This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cloud Security Checklist Access Control Cloud Information Security
Cloud Security Checklist Access Control Cloud Information SecurityThis slide depicts the access control under the cloud security checklist and how it affects the organizations when data breaches happen due to poor access control management.Introducing Cloud Security Checklist Access Control Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Service Provider, Physical Access, Natural Disasters using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Backup And Data Recovery Cloud Information Security
Cloud Security Checklist Backup And Data Recovery Cloud Information SecurityThis slide represents the importance of data backup and data recovery in cloud security. It also shows how organizations should know about the data backup policies of service providers before investing in them.Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Backup And Data Recovery Cloud Information Security This template helps you present information on five stages. You can also present information on Sensitive Information, Encode Sensitive, Encrypted Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Data Encryption Cloud Information Security
Cloud Security Checklist Data Encryption Cloud Information SecurityThis slide represents the importance of data encryption in cloud security and what type of data should always be encrypted through private keys.Introducing Cloud Security Checklist Data Encryption Cloud Information Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Future Evaluation, Device Is Detected, Change Activities using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Logging And Monitoring Cloud Information Security
Cloud Security Checklist Logging And Monitoring Cloud Information SecurityThis slide defines the importance of logging and monitoring activities on data in a network and how it could be beneficial in future analysis.Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Logging And Monitoring Cloud Information Security This template helps you present information on five stages. You can also present information on Data Supposed, Malware Mechanisms, Security Precautions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Networking Cloud Information Security
Cloud Security Checklist Networking Cloud Information SecurityThis slide defines the importance of network security under cloud security. It also shows how data should transfer over a network to protect it from malicious attacks.Introducing Cloud Security Checklist Networking Cloud Information Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implement Policies, Security Solutions, Boarding Employees using this template. Grab it now to reap its full benefits.
-
 Cloud Security Checklist Policies And Procedures Cloud Information Security
Cloud Security Checklist Policies And Procedures Cloud Information SecurityThis slide depicts the policies and procedures of the cloud security checklist. It also represents how it is essential to create new and update the current policies in an organization.Increase audience engagement and knowledge by dispensing information using Cloud Security Checklist Policies And Procedures Cloud Information Security This template helps you present information on four stages. You can also present information on Measures Organization, Technologies Security, Latest Advanced using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Checklist Security Patches And Updates Cloud Information Security
Cloud Security Checklist Security Patches And Updates Cloud Information SecurityThis slide depicts the importance of security patches and timely updates of security technologies. It also shows how it is crucial to scan systems, servers, and frameworks regularly.Introducing Cloud Security Checklist Security Patches And Updates Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Revenue Losses, Compliance Violations, Malware Attacks using this template. Grab it now to reap its full benefits.
-
 Cloud Security Risks Or Threats Cloud Information Security
Cloud Security Risks Or Threats Cloud Information SecurityThis slide represents the list of threats or risks that can impact the security of a cloud these risks include loss of intellectual property, compliance violations, malware attacks, and so on.Increase audience engagement and knowledge by dispensing information using Cloud Security Risks Or Threats Cloud Information Security This template helps you present information on eight stages. You can also present information on Serious Repercussions, Organizations Should, Authentication Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Threats Compliance Violations Cloud Information Security
Cloud Security Threats Compliance Violations Cloud Information SecurityThis slide depicts the value of compliance violations threat of cloud security in a business and how fast an organization can switch to a non compliance state.Introducing Cloud Security Threats Compliance Violations Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Needed Information, Against Organization, Business Partners using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Contract Breaches With Clients Cloud Information Security
Cloud Security Threats Contract Breaches With Clients Cloud Information SecurityThis slide defines the contract breaches with clients and customers that could be the biggest threat to the organizational data.Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Contract Breaches With Clients Cloud Information Security This template helps you present information on four stages. You can also present information on Organizations Cybercriminals, Customers OR Clients, Contact Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Threats End User Control Cloud Information Security
Cloud Security Threats End User Control Cloud Information SecurityThis slide represents the end user threat in cloud security and how an organization needs to control user access and be aware of potential threats.Introducing Cloud Security Threats End User Control Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Wisely Considering, Storage Location, Procedures Strategies using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Loss Of Data Cloud Information Security
Cloud Security Threats Loss Of Data Cloud Information SecurityThis slide represents the data loss threat of cloud security it is essential to secure organization data and create backups.Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Loss Of Data Cloud Information Security This template helps you present information on four stages. You can also present information on Cloud Administrations, Protection Frameworks, Technology Advances using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Threats Malware Attacks Cloud Information Security
Cloud Security Threats Malware Attacks Cloud Information SecurityThis slide represents the malware threat of cloud security and how it can affect data stored on the cloud, further leading to company loss.Introducing Cloud Security Threats Malware Attacks Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Clients OR Customers, Organizations Experienced, Companies Organizations using this template. Grab it now to reap its full benefits.
-
 Cloud Security Threats Revenue Losses Cloud Information Security
Cloud Security Threats Revenue Losses Cloud Information SecurityThis slide represents the revenue loss threat of cloud security and how an organization could lose customers trust and loyalty when it doesnt have a good recovery plan.Increase audience engagement and knowledge by dispensing information using Cloud Security Threats Revenue Losses Cloud Information Security This template helps you present information on five stages. You can also present information on Password Security, Clients Responsibility, Service Providers using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cloud Security Threats Shared Vulnerabilities Cloud Information Security
Cloud Security Threats Shared Vulnerabilities Cloud Information SecurityThis slide describes how organizations and providers share vulnerabilities of a system, so each party must take precautions to protect data.Introducing Cloud Security Threats Shared Vulnerabilities Cloud Information Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Information Centers, Reduced Upfront, Diminished Opportunity using this template. Grab it now to reap its full benefits.
-
 Difference Between Cloud Security Solutions It Solutions Cloud Information Security
Difference Between Cloud Security Solutions It Solutions Cloud Information SecurityThis slide represents the difference between cloud security solutions and traditional IT solutions based on information centers, cost, scalability, and expenses.Deliver an outstanding presentation on the topic using this Difference Between Cloud Security Solutions It Solutions Cloud Information Security Dispense information and present a thorough explanation of Manage Accounts, Services Proactively, Business Operation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Cloud Security Solutions Cloud Information Security
Enterprise Cloud Security Solutions Cloud Information SecurityThis slide describes the enterprise cloud security solutions, including multi factor authentication, managing accounts and service proactively, being careful about shadow IT, and analyzing the cost benefits of hybrid cloud.Introducing Enterprise Cloud Security Solutions Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Visibility Consistency, Process Security, Identity Security using this template. Grab it now to reap its full benefits.
-
 Essential Pillars Of Cloud Security Cloud Information Security
Essential Pillars Of Cloud Security Cloud Information SecurityThis slide shows the four essential pillars of cloud security, namely visibility and consistency, process based security, network security, and identity security.Introducing Essential Pillars Of Cloud Security Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Access Management, Continuity Planning, Legal Compliance using this template. Grab it now to reap its full benefits.
-
 How Does Cloud Security Work Cloud Information Security
How Does Cloud Security Work Cloud Information SecurityThis slide describes how a cloud security system works and what controls or measures are implemented to secure the data over the cloud.Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Cloud Information Security This template helps you present information on five stages. You can also present information on Information Security, Wireless Security, Endpoint Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does Cloud Security Work Data Security Cloud Information Security
How Does Cloud Security Work Data Security Cloud Information SecurityThis slide represents the data security under the cloud security work process, and it also shows the various factors that cover data security.Introducing How Does Cloud Security Work Data Security Cloud Information Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Accessibility, Knowledge, Organized Documented using this template. Grab it now to reap its full benefits.
-
 How Does Cloud Security Work Governance Cloud Information Security
How Does Cloud Security Work Governance Cloud Information SecurityThis slide depicts the governance policy under the cloud security system and how users, processes, and technology are monitored.Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Governance Cloud Information Security This template helps you present information on four stages. You can also present information on Authentication, Access Management, Verification Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 How Does Cloud Security Work Identity And IAM Cloud Information Security
How Does Cloud Security Work Identity And IAM Cloud Information SecurityThis slide represents the identity and access management in a cloud security system that is based on authentication, authorization, access control, and central user repository.Present the topic in a bit more detail with this How Does Cloud Security Work Identity And IAM Cloud Information Security Use it as a tool for discussion and navigation on Requirements, Transparency, Governance This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How Does Cloud Security Work Legal Compliance Cloud Information Security
How Does Cloud Security Work Legal Compliance Cloud Information SecurityThis slide depicts the process of legal compliance in cloud security, and it also represents that organizations are bound to keep customers data private across the cloud.Increase audience engagement and knowledge by dispensing information using How Does Cloud Security Work Legal Compliance Cloud Information Security This template helps you present information on eight stages. You can also present information on Firewalls Ensure, Organization Security, Permitting Limited using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Hybrid Cloud Security Solutions Cloud Information Security
Hybrid Cloud Security Solutions Cloud Information SecurityThis slide describes the hybrid cloud security solutions, which include categorization of services and redundancy.Increase audience engagement and knowledge by dispensing information using Hybrid Cloud Security Solutions Cloud Information Security This template helps you present information on one stage. You can also present information on Automotive Industries, Availability Throughout, Financial Organizations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Industries That Can Benefit From Cloud Security Cloud Information Security
Industries That Can Benefit From Cloud Security Cloud Information SecurityThis slide shows the industries categorized as automotive, education, financial, healthcare, insurance, and others that can take advantage of cloud security by storing data on clouds.Increase audience engagement and knowledge by dispensing information using Industries That Can Benefit From Cloud Security Cloud Information Security This template helps you present information on seven stages. You can also present information on Compliance Violations, Access Control, Daniel Of Service using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Challenges In Cloud Security Cloud Information Security
Key Challenges In Cloud Security Cloud Information SecurityThis slide describes the critical challenges in the cloud security system, such as compliance violations, access control, Daniel of service, and unsecured APIs.Increase audience engagement and knowledge by dispensing information using Key Challenges In Cloud Security Cloud Information Security This template helps you present information on four stages. You can also present information on Corrective Control, Detective Control, Preventive Control using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key Cloud Security Use Cases Cloud Information Security
Key Cloud Security Use Cases Cloud Information SecurityThis slide represents the key use cases of cloud security namely privileged account access, data exfiltration, suspicious network connections, man in the cloud attack, and unsecured storage containers.Present the topic in a bit more detail with this Key Cloud Security Use Cases Cloud Information Security Use it as a tool for discussion and navigation on Review Specifications, Discover Malicious, Vulnerabilities This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Measures And Controls In Cloud Security Cloud Information Security
Measures And Controls In Cloud Security Cloud Information SecurityThis slide depicts the measures and controls taken in cloud security systems, namely preventive controls, deterrent controls, detective controls, and corrective controls.Increase audience engagement and knowledge by dispensing information using Measures And Controls In Cloud Security Cloud Information Security This template helps you present information on four stages. You can also present information on Implement Information, Restrict Data, Implement Advanced using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phase 2 Secure Your Cloud Information Security
Phase 2 Secure Your Cloud Information SecurityThis slide depicts how organizations could secure their cloud and what factors should keep under consideration while protecting the cloud.Deliver an outstanding presentation on the topic using this Phase 2 Secure Your Cloud Information Security Dispense information and present a thorough explanation of Service Permissions, Information Applications, Devices Accomplish using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Pillars Of Cloud Security Identity Security Cloud Information Security
Pillars Of Cloud Security Identity Security Cloud Information SecurityThis slide depicts the identity security pillar of cloud security. It also shows how it could be beneficial to protect data from loss.Increase audience engagement and knowledge by dispensing information using Pillars Of Cloud Security Identity Security Cloud Information Security This template helps you present information on four stages. You can also present information on Controlled Operations, Vulnerability Management, Persistently Identify using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Pillars Of Cloud Security Network Security Cloud Information Security
Pillars Of Cloud Security Network Security Cloud Information SecurityThis slide defines the network security pillar of cloud security and what precautions are taken to protect networks from attacks.Introducing Pillars Of Cloud Security Network Security Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Asset Inventory, Cloud Framework, Data Security using this template. Grab it now to reap its full benefits.
-
 Pillars Of Cloud Security Process Based Security Cloud Information Security
Pillars Of Cloud Security Process Based Security Cloud Information SecurityThis slide represents the process based security pillar of cloud security. It also shows how it works and what precautions does it take.Increase audience engagement and knowledge by dispensing information using Pillars Of Cloud Security Process Based Security Cloud Information Security This template helps you present information on four stages. You can also present information on Platform Customers, Different Locations, Adaptable Structure using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Pillars Of Cloud Security Visibility And Consistency Cloud Information Security
Pillars Of Cloud Security Visibility And Consistency Cloud Information SecurityThis slide depicts the visibility and consistency pillar of cloud security, and it further includes asset inventory, best cloud framework, and data security.Introducing Pillars Of Cloud Security Visibility And Consistency Cloud Information Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Managed Administrations, Business Resilient, Security Measures using this template. Grab it now to reap its full benefits.
-
 Precautions Need To Take In Cloud Security Cloud Information Security
Precautions Need To Take In Cloud Security Cloud Information SecurityThis slide depicts the cloud security precautions that one organization should take while signing up for a cloud service.Introducing Precautions Need To Take In Cloud Security Cloud Information Security to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Responsibilities, Service Type, Three Types using this template. Grab it now to reap its full benefits.
-
 Roadmap Of Cloud Security Implementation Cloud Information Security
Roadmap Of Cloud Security Implementation Cloud Information SecurityThis slide defines the roadmap of cloud security implementation in an organization and what tasks would be performed in each months interval starting from January.Increase audience engagement and knowledge by dispensing information using Roadmap Of Cloud Security Implementation Cloud Information Security This template helps you present information on seven stages. You can also present information on Information Division, Access Control, Data Compliance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Segmentation Of Cloud Security Responsibilities Cloud Information Security
Segmentation Of Cloud Security Responsibilities Cloud Information SecurityThis slide shows cloud security responsibilities based on service type, namely Software-as-a-Service SaaS, Platform as a service PaaS, Infrastructure as a Service IaaS.Introducing Segmentation Of Cloud Security Responsibilities Cloud Information Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Advantages, Disadvantages, Software Hardware using this template. Grab it now to reap its full benefits.
-
 SMB Cloud Security Solutions Cloud Information Security
SMB Cloud Security Solutions Cloud Information SecurityThis slide shows the small and midsized business cloud security solutions, including multi tenant information division, access control, legitimate data compliance, and cautious scaling of cloud frameworks.Increase audience engagement and knowledge by dispensing information using SMB Cloud Security Solutions Cloud Information Security This template helps you present information on four stages. You can also present information on Cloud Security, Threats Involved, Security Solutions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Tools Used In Cloud Security Cloud Information Security
Tools Used In Cloud Security Cloud Information SecurityThis slide represents the list of tools utilized under cloud security systems to protect, manage, store and control data on the cloud.Introducing Tools Used In Cloud Security Cloud Information Security to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Security, Access Control, Threat Detection using this template. Grab it now to reap its full benefits.
-
 Top Advanced Cloud Security Challenges Cloud Information Security
Top Advanced Cloud Security Challenges Cloud Information SecurityThis slide shows the top challenges cloud security faces expanded attack surface, absence of visibility, always changing tracking, access management, complex frameworks, and cloud compliance and governancePresent the topic in a bit more detail with this Top Advanced Cloud Security Challenges Cloud Information Security Use it as a tool for discussion and navigation on Security Solutions, Enterprise Cloud, Manage Accounts This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Topics That Fall Under The Umbrella Of Cloud Security Cloud Information Security
Topics That Fall Under The Umbrella Of Cloud Security Cloud Information SecurityThis slide shows the various topics that fall under the umbrella of cloud security, namely data center security, access control, threat prevention, threat detection, threat mitigation, redundancy, and legal compliance.Introducing Topics That Fall Under The Umbrella Of Cloud Security Cloud Information Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Efficient Recovery, Service Infrastructure, Recovery Mastermind using this template. Grab it now to reap its full benefits.
-
 Types Of Cloud Security Solutions Cloud Information Security
Types Of Cloud Security Solutions Cloud Information SecurityThis slide represents the cloud security solutions such as hybrid cloud security solutions, SMB cloud security solutions, and enterprise cloud security solutions.Increase audience engagement and knowledge by dispensing information using Types Of Cloud Security Solutions Cloud Information Security This template helps you present information on three stages. You can also present information on Loss Of Control, Data Breaches, Company Employees using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 What Are The Benefits Of A Cloud Security System Cloud Information Security
What Are The Benefits Of A Cloud Security System Cloud Information SecurityThis slide represents the benefits of a cloud security system, such as efficient recovery, openness, no hardware requirement, DDOS protection, and data security.Deliver an outstanding presentation on the topic using this What Are The Benefits Of A Cloud Security System Cloud Information Security Dispense information and present a thorough explanation of Cloud Security, Computing Systems, Business Coherence using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 What Are The Downsides Of A Cloud Security Cloud Information Security
What Are The Downsides Of A Cloud Security Cloud Information SecurityThis slide describes the downsides of the cloud security system, including loss of control over data, data loss, insider theft, and data breaches.Increase audience engagement and knowledge by dispensing information using What Are The Downsides Of A Cloud Security Cloud Information Security This template helps you present information on four stages. You can also present information on Development Permitted, Industry Security, Information Penetrates using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 What Is Cloud Security Cloud Information Security
What Is Cloud Security Cloud Information SecurityThis slide depicts the meaning of cloud security, and parties involve in a cloud security framework, such as customers and service providers.Introducing What Is Cloud Security Cloud Information Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Centralized Security, Diminished Administration, Cost Effective using this template. Grab it now to reap its full benefits.
-
 What Makes Cloud Security Different Cloud Information Security
What Makes Cloud Security Different Cloud Information SecurityThis slide shows two factors that make cloud security different, and these factors are, convenience over security, and centralization and multi tenant storage system.Increase audience engagement and knowledge by dispensing information using What Makes Cloud Security Different Cloud Information Security This template helps you present information on one stage. You can also present information on Authentication, Device Validation, Restrict Access using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Why Cloud Security Is Important Cloud Information Security
Why Cloud Security Is Important Cloud Information SecurityThis slide defines why cloud security is essential based on data centralization, cost, diminished control, and data reliability.Present the topic in a bit more detail with this Why Cloud Security Is Important Cloud Information Security Use it as a tool for discussion and navigation on Cloud security, concentrates protection, managing shadow This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Assessment Of Security Building A Security Awareness Program
Comparative Assessment Of Security Building A Security Awareness ProgramThe purpose of this slide is to showcase comparison of various advance cyber security training courses. The comparison is drawn on the basis of course description, level, duration, no. of companies enrolled for this course etc. Present the topic in a bit more detail with this Comparative Assessment Of Security Building A Security Awareness Program. Use it as a tool for discussion and navigation on Course Description, Comparative Assessment, Online Courses. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparison Of Various Security Building A Security Awareness Program
Comparison Of Various Security Building A Security Awareness ProgramThe purpose of this slide is to drawn comparison of multiple software which can be used to provide cyber security training to the key stakeholders. Information covered in this slide is related to phishing simulations, security reporting, individualized security training plan etc. Deliver an outstanding presentation on the topic using this Comparison Of Various Security Building A Security Awareness Program. Dispense information and present a thorough explanation of Software, Comparison, Various Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Awareness Checklist Building A Security Awareness Program
Cyber Security Awareness Checklist Building A Security Awareness ProgramThe purpose of this slide is to outline a comprehensive checklist which can be used to ensure information technology IT asset protection. It cover points such as operating system is up to date, employees are using strong password policy etc. Introducing Cyber Security Awareness Checklist Building A Security Awareness Program to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Operating System, Programs Automatically, Asset Protection, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Awareness Trends In 2022 Building A Security Awareness Program
Cyber Security Awareness Trends In 2022 Building A Security Awareness ProgramThe purpose of this slide is to showcase security awareness trends which the organization has to look out for in 2022. increase in malware and ransomware attack, more employees will be targeted by mobile malware attack and advancement of phishing attack are some of the major trends mentioned in the slide. Present the topic in a bit more detail with this Cyber Security Awareness Trends In 2022 Building A Security Awareness Program. Use it as a tool for discussion and navigation on Ransomware Attack, Security Awareness. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Evaluating It System Security Using Swot Analysis Building A Security Awareness Program
Evaluating It System Security Using Swot Analysis Building A Security Awareness ProgramThe purpose of this slide is to outline the strength, weakness, opportunities and threat SWOT evaluation of organization cyber security. Organization can detect the potential risks and opportunities in the cyber security using SWOT model. Increase audience engagement and knowledge by dispensing information using Evaluating It System Security Using Swot Analysis Building A Security Awareness Program. This template helps you present information on four stages. You can also present information on Strengths, Weakness, Opportunities, Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Functional Chart Of Cyber Security Team Building A Security Awareness Program
Functional Chart Of Cyber Security Team Building A Security Awareness ProgramThe purpose of this slide is to provide glimpse of cyber security team in the form of org chart. The key stakeholders mentioned in the slide are chief information security officer CISO, cyber risk committee, cyber security director, cyber risk manager, security operations manager etc. Present the topic in a bit more detail with this Functional Chart Of Cyber Security Team Building A Security Awareness Program. Use it as a tool for discussion and navigation on Security Operations, Threat Intelligence, Cyber Business Liaison. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 How Much Employees Are Aware Of Cyber Security Building A Security Awareness Program
How Much Employees Are Aware Of Cyber Security Building A Security Awareness ProgramThe purpose of this slide is to showcase the cyber security assessment test result. It covers information about the pass fail rate of employees who received the security awareness training and fail rate by age. Present the topic in a bit more detail with this How Much Employees Are Aware Of Cyber Security Building A Security Awareness Program. Use it as a tool for discussion and navigation on Employees, Cyber Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Security Breach Building A Security Awareness Program
Impact Of Cyber Security Breach Building A Security Awareness ProgramThe purpose of this slide is to outline the impact of cyber security breach on the organization. The cyber attack make a significant impact on reputational damage, intellectual property IP theft, monetary penalty and operational disruption. Introducing Impact Of Cyber Security Breach Building A Security Awareness Program to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reputational Damage, Monetary Penalty, Operational Disruption, using this template. Grab it now to reap its full benefits.
-
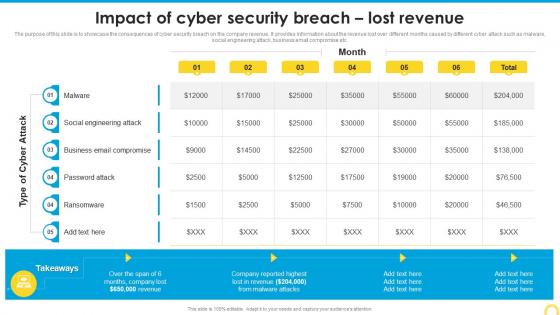 Impact Of Cyber Security Breach Lost Revenue Building A Security Awareness Program
Impact Of Cyber Security Breach Lost Revenue Building A Security Awareness ProgramThe purpose of this slide is to showcase the consequences of cyber security breach on the company revenue. It provides information about the revenue lost over different months caused by different cyber attack such as malware, social engineering attack, business email compromise etc. Present the topic in a bit more detail with this Impact Of Cyber Security Breach Lost Revenue Building A Security Awareness Program. Use it as a tool for discussion and navigation on Social Engineering Attack, Business Email Compromise, Ransomware. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Key Benefits Of Cyber Security Awareness Training Building A Security Awareness Program
Key Benefits Of Cyber Security Awareness Training Building A Security Awareness ProgramThe purpose of this slide is to delineate several advantages of security awareness training. Driving awareness, reducing data breach threat, prevention of downtime and improving the customer confidence are some of the key benefits which are highlighted in the slide. Introducing Key Benefits Of Cyber Security Awareness Training Building A Security Awareness Program to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Prevent Downtime, Improves Customer Confidence, Awareness Training, using this template. Grab it now to reap its full benefits.
-
 Key Stakeholders Of Cyber Security Awareness Training Building A Security Awareness Program
Key Stakeholders Of Cyber Security Awareness Training Building A Security Awareness ProgramIncrease audience engagement and knowledge by dispensing information using Key Stakeholders Of Cyber Security Awareness Training Building A Security Awareness Program. This template helps you present information on three stages. You can also present information on Senior Mangers, Line Managers, Employees using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Measuring Security Awareness Building A Security Awareness Program
Measuring Security Awareness Building A Security Awareness ProgramThe purpose of this slide is to showcase various key performance indicator KPIs which can assist the company to effectively track cyber security awareness campaign results. The KPIs are phishing rate, self reported incidents, security breaches, cost of security breach and campaign participation rate. Present the topic in a bit more detail with this Measuring Security Awareness Building A Security Awareness Program. Use it as a tool for discussion and navigation on Campaign Participation Rate, Measuring Security, Awareness Campaign. This template is free to edit as deemed fit for your organization. Therefore download it now.





