Powerpoint Templates and Google slides for Security Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Secure Client Connection To Proxy And Secure Proxy Connection Reverse Proxy It
Secure Client Connection To Proxy And Secure Proxy Connection Reverse Proxy ItThis slide represents the secure client to proxy and secure proxy to the content server and how it can be used for the information that needs to be transmitted securely. Deliver an outstanding presentation on the topic using this Secure Client Connection To Proxy And Secure Proxy Connection Reverse Proxy It. Dispense information and present a thorough explanation of Encrypted, Secure, Connection, Server using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Cybersecurity Checklist Effectively Managing Asset Security
Information Security Program Cybersecurity Checklist Effectively Managing Asset SecurityFollowing slide displays system management checklist that company will use for effectively managing asset security. It also includes system management activities and frequency of performing them. Present the topic in a bit more detail with this Information Security Program Cybersecurity Checklist Effectively Managing Asset Security. Use it as a tool for discussion and navigation on Checklist For Effectively Managing Asset Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security Program Cybersecurity Information Security Program Values To Business
Information Security Program Cybersecurity Information Security Program Values To BusinessFollowing slide displays the major program values to companys business. Values here are divided in two areas namely detection and response and attack surface management. Deliver an outstanding presentation on the topic using this Information Security Program Cybersecurity Information Security Program Values To Business. Dispense information and present a thorough explanation of Information, Business, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Cybersecurity Management Security Lifecycle
Information Security Program Cybersecurity Management Security LifecycleIncrease audience engagement and knowledge by dispensing information using Information Security Program Cybersecurity Management Security Lifecycle. This template helps you present information on six stages. You can also present information on Categorize, Implement, Authorize using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Program Defining Business Priorities To Ensure Information Security
Information Security Program Defining Business Priorities To Ensure Information SecurityThis slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security. Increase audience engagement and knowledge by dispensing information using Information Security Program Defining Business Priorities To Ensure Information Security. This template helps you present information on three stages. You can also present information on Efficient Risk Management, Transparent Communication, Management Process using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Program Eliminating Manual Security Processes Through Automation
Information Security Program Eliminating Manual Security Processes Through AutomationMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools. Deliver an outstanding presentation on the topic using this Information Security Program Eliminating Manual Security Processes Through Automation. Dispense information and present a thorough explanation of Processes, Automation, Vulnerabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Framework Key Components information Security Program
Information Security Program Framework Key Components information Security ProgramMentioned slide portrays the key components of companys information security framework. Components covered are context and leadership, evaluation and direction, prevention, detection etc. Deliver an outstanding presentation on the topic using this Information Security Program Framework Key Components information Security Program. Dispense information and present a thorough explanation of Information, Framework, Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security Program Key Security Controls To Be Addressed In The Program
Information Security Program Key Security Controls To Be Addressed In The ProgramPurpose of this slide is to provide information about key security controls that are to be addressed in companys information security program. Security controls covered are user application hardening, daily backups and patch applications. Deliver an outstanding presentation on the topic using this Information Security Program Key Security Controls To Be Addressed In The Program. Dispense information and present a thorough explanation of Prevents Attacks, Limits Extent Of Attacks, Data Recovery using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Framework For Information Security Budget For Information Security
Risk Management Framework For Information Security Budget For Information SecurityMentioned slide shows budget for managing information security. It includes information such as functional area, software name, training duration, training cost, number of employees and total training cost. Deliver an outstanding presentation on the topic using this Risk Management Framework For Information Security Budget For Information Security. Dispense information and present a thorough explanation of Risk Management, Incident Management, Asset Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Framework For Information Security Introducing Information Security Risk
Risk Management Framework For Information Security Introducing Information Security RiskFollowing slide illustrates information security risk assessment process workflow. It covers 6 stages namely system characterization, threat identification, vulnerability identification, risk analysis, risk remedies and documented results. Increase audience engagement and knowledge by dispensing information using Risk Management Framework For Information Security Introducing Information Security Risk. This template helps you present information on six stages. You can also present information on Identify Threats, Incident Reports, Identify Vulnerabilities, Characterize System, Recommend Remediation Measures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Risk Management Framework For Information Security Present Security Management Capabilities
Risk Management Framework For Information Security Present Security Management CapabilitiesFollowing slide shows the current security management capabilities of the firm. It covers details about core functions, its description, key enablers, required and actual standard ratings. Deliver an outstanding presentation on the topic using this Risk Management Framework For Information Security Present Security Management Capabilities. Dispense information and present a thorough explanation of Core Functions, Incident Occurrence Identification, Asset Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Risk Management Framework For Information Security Setting Scenario For Security Control
Risk Management Framework For Information Security Setting Scenario For Security ControlFollowing slide displays security control scenario setting. It includes scenario detail, category of security controls and controls description. Present the topic in a bit more detail with this Risk Management Framework For Information Security Setting Scenario For Security Control. Use it as a tool for discussion and navigation on Category Security Controls, Controls Description, Operational Controls, Management Controls, Technical Controls. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Defining Business Security Introducing A Risk Based Approach To Cyber Security
Defining Business Security Introducing A Risk Based Approach To Cyber SecurityThis slide illustrates the key business priorities of the organization such as efficient risk management, standardized incident management process to ensure information security.Introducing Defining Business Security Introducing A Risk Based Approach To Cyber Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Efficient Risk Management, Standardized Incident, Management Process using this template. Grab it now to reap its full benefits.
-
 Eliminating Manual Security Introducing A Risk Based Approach To Cyber Security
Eliminating Manual Security Introducing A Risk Based Approach To Cyber SecurityMentioned slide displays the workflow process of how company will eliminate its existing manual security processes through automation tools.Present the topic in a bit more detail with this Eliminating Manual Security Introducing A Risk Based Approach To Cyber Security Use it as a tool for discussion and navigation on Manual Vulnerability, Scanning And Resolution, Automation Vulnerability This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan information security process to manage firms sensitive
Building organizational security strategy plan information security process to manage firms sensitiveThis slide provides information about information security process in order to manage firms sensitive data in terms of firewall audit checklist, VPN configuration, penetrating testing. Present the topic in a bit more detail with this Building Organizational Security Strategy Plan Information Security Process To Manage Firms Sensitive. Use it as a tool for discussion and navigation on Information, Process, Sensitive. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Building organizational security strategy plan security process to manage firms
Building organizational security strategy plan security process to manage firmsThis slide provides information about information security process in order to manage firms sensitive data in terms of privileged password management, network security audit checklist, etc. Deliver an outstanding presentation on the topic using this Building Organizational Security Strategy Plan Security Process To Manage Firms. Dispense information and present a thorough explanation of Information, Process, Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Performance indicators to determine security building organizational security strategy plan
Performance indicators to determine security building organizational security strategy planThis slide provides information about performance indicators in order to determine security standards at workplace in terms of staff and customer satisfaction, financial and staff. Deliver an outstanding presentation on the topic using this Performance Indicators To Determine Security Building Organizational Security Strategy Plan. Dispense information and present a thorough explanation of Performance, Satisfaction, Financial using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber security risk management addressing asset security categorization
Cyber security risk management addressing asset security categorizationThis slide provides details regarding asset security categorization on certain parameters such as ownership, location, confidentiality, integrity and availability. Introducing Cyber Security Risk Management Addressing Asset Security Categorization to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Position, Ownership, Location, Security Categorization, Integrity, Confidentiality, Availability, Value , using this template. Grab it now to reap its full benefits.
-
 Cyber security risk management selecting secured threat management software
Cyber security risk management selecting secured threat management softwareThis slide will help firm in choosing the suitable automated threat management software which is to handle existing security and privacy issues and predict upcoming threats. The firm will choose effective software with features such as automated workflows, centralized platform, etc. Present the topic in a bit more detail with this Cyber Security Risk Management Selecting Secured Threat Management Software. Use it as a tool for discussion and navigation on Centralized Platform, Security Incident Forms, Access Rights, API Integration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Improve it security with vulnerability benchmarking security operations maturity model
Improve it security with vulnerability benchmarking security operations maturity modelThis slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Introducing Improve It Security With Vulnerability Benchmarking Security Operations Maturity Model to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Improve Visibility, Quickly Identify Threats, Decrease Response Time, using this template. Grab it now to reap its full benefits.
-
 Improve it security with vulnerability management security intelligence services
Improve it security with vulnerability management security intelligence servicesThis slide covers the security intelligence services such as cyber threat intelligence, incident and response management, cyber analytics, vulnerability management, etc. Deliver an outstanding presentation on the topic using this Improve It Security With Vulnerability Management Security Intelligence Services. Dispense information and present a thorough explanation of Management, Analytics, Infrastructure using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Current Security Management Capabilities Overview
Information Security And Iso 27001 Current Security Management Capabilities OverviewFollowing slide illustrates present information security management capabilities overview of the company. Sections covered in the slide are core functions, description, key enablers, required and actual standard rating. Deliver an outstanding presentation on the topic using this Information Security And Iso 27001 Current Security Management Capabilities Overview. Dispense information and present a thorough explanation of Security, Management, Capabilities using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Iso 27001 Iso 27001 Information Security Management Standard
Information Security And Iso 27001 Iso 27001 Information Security Management StandardPresent the topic in a bit more detail with this Information Security And Iso 27001 Iso 27001 Information Security Management Standard. Use it as a tool for discussion and navigation on Information, Security, Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Performance Indicators To Measure Information Security Controls
Information Security And Iso 27001 Performance Indicators To Measure Information Security ControlsFollowing slide illustrates performance indicators for measuring information security controls. It includes controls details, performance indicator formula, target and periodicity. Present the topic in a bit more detail with this Information Security And Iso 27001 Performance Indicators To Measure Information Security Controls. Use it as a tool for discussion and navigation on Performance, Indicators, Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Security And Iso 27001 Security Domains That Will Be Addressed By Isms
Information Security And Iso 27001 Security Domains That Will Be Addressed By IsmsThis slide portrays different security domains that will be addressed by ISMS. Domains covered are security policy, asset management, physical and environmental security, cryptography and human resource security. Introducing Information Security And Iso 27001 Security Domains That Will Be Addressed By Isms to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Organization Of Information, Access Control, Cryptography, using this template. Grab it now to reap its full benefits.
-
 Network Security VS Cyber Security Ppt Powerpoint Presentation Slides Diagrams Cpb
Network Security VS Cyber Security Ppt Powerpoint Presentation Slides Diagrams CpbPresenting Network Security VS Cyber Security Ppt Powerpoint Presentation Slides Diagrams Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Network Security VS Cyber Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Security Metrics Information Security Ppt Powerpoint Presentation Portfolio Grid Cpb
Security Metrics Information Security Ppt Powerpoint Presentation Portfolio Grid CpbPresenting our Security Metrics Information Security Ppt Powerpoint Presentation Portfolio Grid Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Security Metrics Information Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Network Security Best Practices For Cloud Security
Network Security Best Practices For Cloud SecurityThis slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Deliver an outstanding presentation on the topic using this Network Security Best Practices For Cloud Security. Dispense information and present a thorough explanation of Best Practices For Cloud Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Common Methods Used To Threaten Network Security
Network Security Common Methods Used To Threaten Network SecurityThis slide depicts the standard methods used to threaten network security by cybercriminals attackers. It also shows the reasons for these threats and preventions from these threats. Increase audience engagement and knowledge by dispensing information using Network Security Common Methods Used To Threaten Network Security. This template helps you present information on five stages. You can also present information on Malicious, Necessary, Perform, Unavailable, Operations using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Network Security Complete Network Security Implementation Checklist
Network Security Complete Network Security Implementation ChecklistThis slide depicts the network security checklist and measures an organization should take to protect data and company assets from network attacks or natural disasters. Introducing Network Security Complete Network Security Implementation Checklist to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Complete Network Security Implementation Checklist, using this template. Grab it now to reap its full benefits.
-
 Network Security Cyber Threat Landscape In Network Security
Network Security Cyber Threat Landscape In Network SecurityThis slide depicts the cyber threat landscape based on cybercriminal roles actors and the impacts of successful cyberattacks on business. Deliver an outstanding presentation on the topic using this Network Security Cyber Threat Landscape In Network Security. Dispense information and present a thorough explanation of Cyber Threat Landscape In Network Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security It Infrastructure Network Security Budget For Fy2020
Network Security It Infrastructure Network Security Budget For Fy2020This slide represents the budget for IT infrastructure after implementing network security, and it also shows the amount each task will cost the company. Present the topic in a bit more detail with this Network Security It Infrastructure Network Security Budget For Fy2020. Use it as a tool for discussion and navigation on It Infrastructure Network Security Budget For Fy2020. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Key Elements Of Network Security
Network Security Key Elements Of Network SecurityThis slide represents the different elements of Network security such as application security, network security, information security, etc.Increase audience engagement and knowledge by dispensing information using Network Security Key Elements Of Network Security. This template helps you present information on seven stages. You can also present information on Elements, Network, Security, Planning, Recovery, Operational Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Network Security Latest Threats In Network Security
Network Security Latest Threats In Network SecurityThis slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Introducing Network Security Latest Threats In Network Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Financial, Fraudulent, Information, Business, using this template. Grab it now to reap its full benefits.
-
 Network Security Main Principle Of Information Security
Network Security Main Principle Of Information SecurityThis slide represents the main principles of information security such as confidentiality, integrity, and availability and how it makes data confidential and consistent, and available to authorized users. Deliver an outstanding presentation on the topic using this Network Security Main Principle Of Information Security. Dispense information and present a thorough explanation of Main Principle Of Information Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Main Steps Of Operational Security
Network Security Main Steps Of Operational SecurityThis slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Increase audience engagement and knowledge by dispensing information using Network Security Main Steps Of Operational Security. This template helps you present information on five stages. You can also present information on Sensitive Information, Potential Threats, Vulnerabilities, Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Network Security Managing Network Security 30 Days Plan
Network Security Managing Network Security 30 Days PlanThis slide depicts how the network security model will work in the first 30 days and the tasks the organization should focus on. Present the topic in a bit more detail with this Network Security Managing Network Security 30 Days Plan. Use it as a tool for discussion and navigation on Managing Network Security 30 Days Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Managing Network Security 60 Days Plan
Network Security Managing Network Security 60 Days PlanThis slide depicts how the network security model will work in the first 30 days and the tasks the organization should focus on. Deliver an outstanding presentation on the topic using this Network Security Managing Network Security 60 Days Plan. Dispense information and present a thorough explanation of Managing Network Security 60 Days Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Network Security Managing Network Security 60 Days Plan Methods
Network Security Managing Network Security 60 Days Plan MethodsThis slide depicts how the network security model will work in the first 30 days and the tasks the organization should focus on. Present the topic in a bit more detail with this Network Security Managing Network Security 60 Days Plan Methods. Use it as a tool for discussion and navigation on Managing Network Security 60 Days Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Roadmap For Network Security Training
Network Security Roadmap For Network Security TrainingThis slide depicts the network security training roadmap. It also shows the plan and guidelines to conduct an effective training program. Increase audience engagement and knowledge by dispensing information using Network Security Roadmap For Network Security Training. This template helps you present information on six stages. You can also present information on Information, Physical Security, Data Security, Practices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Network Security Security Framework In Cloud Computing
Network Security Security Framework In Cloud ComputingThis slide depicts how tasks are performed under cloud security through the framework. The framework consists of different stages such as identity, protection, detection, response, and recovery. Introducing Network Security Security Framework In Cloud Computing to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Business, Requirements, Technology, Processes, Strategy, using this template. Grab it now to reap its full benefits.
-
 Network Security Security Of Employees Devices
Network Security Security Of Employees DevicesThis slide depicts that the security of employees hardware or devices is also essential while applying the network security model. Increase audience engagement and knowledge by dispensing information using Network Security Security Of Employees Devices. This template helps you present information on five stages. You can also present information on Security Of Employees Devices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Network Security Set Measures For Secure Communication
Network Security Set Measures For Secure CommunicationThis slide depicts secure communication within an organization and the technology to encrypt emails or data while sending or receiving them. Introducing Network Security Set Measures For Secure Communication to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Tools, Training, Technology, Sensitive, Organization, using this template. Grab it now to reap its full benefits.
-
 Network Security Timeline For The Implementation Of Network Security
Network Security Timeline For The Implementation Of Network SecurityThis slide shows the timeline for network security model implementation in an organization and the tasks to be performed every month. Present the topic in a bit more detail with this Network Security Timeline For The Implementation Of Network Security. Use it as a tool for discussion and navigation on Timeline For The Implementation Of Network Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Network Security Types Of Threats In Network Security
Network Security Types Of Threats In Network SecurityThis slide depicts the main types of threats in network security, such as network crime, network terrorism, and cyberattacks to an organization and the purpose of each category threat. Increase audience engagement and knowledge by dispensing information using Network Security Types Of Threats In Network Security. This template helps you present information on three stages. You can also present information on Cyber Crime, Cyber Terrorism, Cyber Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Network Security What Is Network Security And How Does It Work
Network Security What Is Network Security And How Does It WorkThis slide defines the meaning of network security and how it helps to prevent data through different methods and techniques. Increase audience engagement and knowledge by dispensing information using Network Security What Is Network Security And How Does It Work. This template helps you present information on five stages. You can also present information on Approach, Methods, Techniques, Procedures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 5 Operational Technology Security Controls To Improve It Security
5 Operational Technology Security Controls To Improve It SecurityFollowing slide depict operational technology OT security controls ways that can be used by an organization. Organization can enhance the security of IT infrastructure by using security controls such as update asset inventory, training, managing portable media, backup and restore and implementing secure configuration. Present the topic in a bit more detail with this 5 Operational Technology Security Controls To Improve IT Security. Use it as a tool for discussion and navigation on Update Asset Inventory, Training Manage, Portable Media, Backup And Restore, Secure Configuration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Elements Of Information Technology Security Application Security Information Technology Security
Elements Of Information Technology Security Application Security Information Technology SecurityThis slide defines application security and categories of application threats and tools to perform application security to prevent cyberattacks. Increase audience engagement and knowledge by dispensing information using Elements Of Information Technology Security Application Security Information Technology Security. This template helps you present information on five stages. You can also present information on Session Management, Parameter Tampering, Authorization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Best Practices For Cloud Security
Information Technology Security Best Practices For Cloud SecurityThis slide represents the best practices for cloud security, such as the shared responsibility model, operations management, building controls, and processes and data encryption. Present the topic in a bit more detail with this Information Technology Security Best Practices For Cloud Security. Use it as a tool for discussion and navigation on Operations, Management, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Common Methods Used Threaten Information Security
Information Technology Security Common Methods Used Threaten Information SecurityThis slide depicts the standard methods used to threaten cyber security by cybercriminals or attackers. It also shows the reasons for these threats and preventions from these threats. Introducing Information Technology Security Common Methods Used Threaten Information Security to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Daniel Of Service, Man In The Middle, SQL Injection , using this template. Grab it now to reap its full benefits.
-
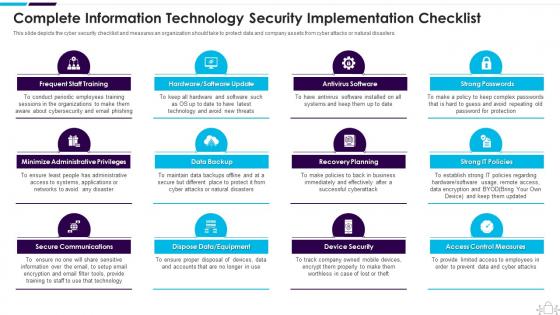 Information Technology Security Complete Information Security Implementation Checklist
Information Technology Security Complete Information Security Implementation ChecklistThis slide depicts the cyber security checklist and measures an organization should take to protect data and company assets from cyber attacks or natural disasters. Introducing Information Technology Security Complete Information Security Implementation Checklist to increase your presentation threshold. Encompassed with twelve stages, this template is a great option to educate and entice your audience. Dispence information on Frequent Staff Training, Administrative Privileges, Data Backup, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Cyber Threat Landscape In Information Technology Security
Information Technology Security Cyber Threat Landscape In Information Technology SecurityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Deliver an outstanding presentation on the topic using this Information Technology Security Cyber Threat Landscape In Information Technology Security. Dispense information and present a thorough explanation of Landscape, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Elements Information Technology Security Cloud Security
Information Technology Security Elements Information Technology Security Cloud SecurityThis slide defines the cloud security element of cyber security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Introducing Information Technology Security Elements Information Technology Security Cloud Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Elements, Information, Technology, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security End User Education Information Technology Security
Information Technology Security End User Education Information Technology SecurityThis slide shows the end user education within the cyber security model. It also represents various factors that effective training plans should involve. Introducing Information Technology Security End User Education Information Technology Security to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Assessment, Microlearning, Opportunities, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security How Is Automation Used In Information Technology Security
Information Technology Security How Is Automation Used In Information Technology SecurityThis slide depicts the cyber protection of an organization through artificial intelligence and how it can be helpful in threat detection, threat response, and human augmentation. Introducing Information Technology Security How Is Automation Used In Information Technology Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Threat Detection, Threat Response, Human Augmentation, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Information Technology Security Elements
Information Technology Security Information Technology Security ElementsThis slide represents the different elements of cyber security such as application security, network security, information security, etc. Introducing Information Technology Security Information Technology Security Elements to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on End User Education, Operational Security, Information Security, using this template. Grab it now to reap its full benefits.
-
 Information Technology Security Latest Threats In Information Technology Security
Information Technology Security Latest Threats In Information Technology SecurityThis slide depicts the categories of recent threats that recently emerged in the United States, United Kingdom, and Australia in previous years. Deliver an outstanding presentation on the topic using this Information Technology Security Latest Threats In Information Technology Security. Dispense information and present a thorough explanation of Latest Threats In Information Technology Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Main Steps Of Operational Security
Information Technology Security Main Steps Of Operational SecurityThis slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Present the topic in a bit more detail with this Information Technology Security Main Steps Of Operational Security. Use it as a tool for discussion and navigation on Assessment Of Risks, Define Sensitive Information, Identify Potential Threats This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Managing Information Technology Security 90 Days Plan
Information Technology Security Managing Information Technology Security 90 Days PlanThis slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an outstanding presentation on the topic using this Information Technology Security Managing Information Technology Security 90 Days Plan. Dispense information and present a thorough explanation of Managing, Information, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Technology Security Network Security
Information Technology Security Network SecurityThis slide represents the network security element of cyber security and different network security methods such as firewalls, email security, web security, and antivirus software. Increase audience engagement and knowledge by dispensing information using Information Technology Security Network Security. This template helps you present information on seven stages. You can also present information on Information, Technology, Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





