Powerpoint Templates and Google slides for Security Risks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process
Determine Cyber Security Risks And Threats Implementing Cyber Risk Management ProcessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Objectives, Issue Identifier. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Global Cyber Security Trend Analysis Implementing Cyber Risk Management Process
Global Cyber Security Trend Analysis Implementing Cyber Risk Management ProcessThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber-attacks etc. Introducing Global Cyber Security Trend Analysis Implementing Cyber Risk Management Process to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Businesses Targeted, Ransomware Attack, Cyber Attacks, using this template. Grab it now to reap its full benefits.
-
 Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management Process
Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management ProcessThe following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Present the topic in a bit more detail with this Impact Of Cyber Safety Security Measures Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Cyber Attack Type, Remarks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process
Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management ProcessThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions. Deliver an outstanding presentation on the topic using this Impact Of Cyber Security Policies And Practices Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Inadequate Security Guidelines, Inappropriate Privacy Policies, Insufficient Background Check using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management Process
KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management ProcessThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIs To Evaluate Cyber Security Risk Management Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Details, Before, After. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management Process
Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management ProcessThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Present the topic in a bit more detail with this Organize Cyber Security Training For Employees Regularly Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Target Audience, Trainer Name, Mode. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management Process
Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management ProcessThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Present the topic in a bit more detail with this Prioritize Cyber Security Risk With Severity Matrix Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Rare, Unlikely, Possible. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process
Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management ProcessThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Implementing Cyber Risk Management Process. Use it as a tool for discussion and navigation on Parameters, Tasks, Status, Reviews. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process
Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management ProcessThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Deliver an outstanding presentation on the topic using this Select Tools To Reduce Cyber Security Failure Implementing Cyber Risk Management Process. Dispense information and present a thorough explanation of Features, Free Trial, Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Risk Management Training Program
Information Security And Risk Management Training ProgramThis slide showcases the successful information security and risk management training outline. It include details such as threats and vulnerabilities, etc. Presenting our well structured Information Security And Risk Management Training Program. The topics discussed in this slide are Training, Vulnerabilities, Information. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Emerging Cloud Security Risks And Threats Next Generation CASB
Emerging Cloud Security Risks And Threats Next Generation CASBThis slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Present the topic in a bit more detail with this Emerging Cloud Security Risks And Threats Next Generation CASB Use it as a tool for discussion and navigation on Virtual Private Networks, System Misconfigurations, Perimeter Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organizational Security Risk Analysis And Management
Organizational Security Risk Analysis And ManagementThis slide shows organizational risk analysis by reviewing security threats and audit findings. The purpose of this slide is to help businesses in strengthening their security management system. Analysis is conducting by reviewing security threats, risk factors and management techniques. Presenting our well structured Organizational Security Risk Analysis And Management. The topics discussed in this slide are Security, Factors, Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Firewall Network Security Understanding Critical Risks Of Firewall Absence
Firewall Network Security Understanding Critical Risks Of Firewall AbsenceThis slide highlights some significant threats that businesses can face without firewall protection. The purpose of this slide is to showcase the critical risks that anyone or organizations can experience if they lack firewall deployment. Risks are open access to all, lost or compromised data, and network crashes. Increase audience engagement and knowledge by dispensing information using Firewall Network Security Understanding Critical Risks Of Firewall Absence This template helps you present information on Three stages. You can also present information on Open Access, Lost Or Comprised Data, Network Crashes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Y196 Hands On Blockchain Security Risk Management And Best Practices Table Of Contents BCT SS V
Y196 Hands On Blockchain Security Risk Management And Best Practices Table Of Contents BCT SS VIntroducing Y196 Hands On Blockchain Security Risk Management And Best Practices Table Of Contents BCT SS V to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Blockchain Cyber Security, Risk Management Process, using this template. Grab it now to reap its full benefits.
-
 Impact Of DDoS Attack On Targeted Servers Hands On Blockchain Security Risk BCT SS V
Impact Of DDoS Attack On Targeted Servers Hands On Blockchain Security Risk BCT SS VThe following slide depicts the adverse impact of denial of service DDOS attack to determine malicious attempt to hamper targeted server. It includes elements such as software crashes, node failure, network congestion, bloated ledger, etc. Increase audience engagement and knowledge by dispensing information using Impact Of Impact Of DDoS Attack On Targeted Servers Hands On Blockchain Security Risk BCT SS V. This template helps you present information on four stages. You can also present information on Software Crashes, Node Failures, Network Congestion using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various Types Of DDoS Attacks Impacting Internet Traffic Hands On Blockchain Security Risk BCT SS V
Various Types Of DDoS Attacks Impacting Internet Traffic Hands On Blockchain Security Risk BCT SS VThe following slide showcases various types of denial of service DDOS attack to reduce abnormal traffic and lessen the impact. It includes elements such as volumetric, applications, protocol, fragmentation attacks, etc. Introducing Various Types Of DDoS Attacks Impacting Internet Traffic Hands On Blockchain Security Risk BCT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Volumetric Attacks, Protocol Attacks, Application Attacks, using this template. Grab it now to reap its full benefits.
-
 Devsecops Best Practices For Secure Risks Associated With Neglecting Security In Devops
Devsecops Best Practices For Secure Risks Associated With Neglecting Security In DevopsThis slide showcases the various challenges associated with DevOps for neglecting security. The purpose of this slide is to explain the risks related to security, these include elevated exposure to cyber threats, compliance and legal concerns, and so on. Increase audience engagement and knowledge by dispensing information using Devsecops Best Practices For Secure Risks Associated With Neglecting Security In Devops. This template helps you present information on nine stages. You can also present information on Greater Potential For Data Breaches, Escalated Remediation Expenses, Operational Disruptions, Downtime Interruptions In Regular using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Analyzing Risk Probabilities Securing Blockchain Transactions A Beginners Guide BCT SS V
Analyzing Risk Probabilities Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide showcases blockchain cybersecurity risk probabilities matrix . It includes elements such as likelihood, impact, loss of private key, accessibility to digital wallets, sensitive data loss, misuse of smart contracts, breakdown of servers, data breach, etc. Deliver an outstanding presentation on the topic using this Analyzing Risk Probabilities Securing Blockchain Transactions A Beginners Guide BCT SS V. Dispense information and present a thorough explanation of Phishing Attack Leading, Unauthorized Accessibility, Ransomware Attack Leading using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
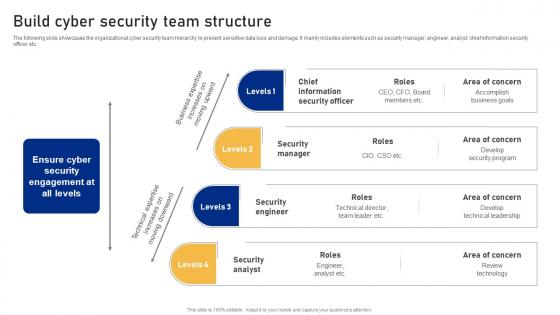 Build Cyber Security Team Structure Cyber Risk Assessment
Build Cyber Security Team Structure Cyber Risk AssessmentThe following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc. Increase audience engagement and knowledge by dispensing information using Build Cyber Security Team Structure Cyber Risk Assessment This template helps you present information on four stages. You can also present information on Information Security Officer, Security Manager, Security Engineer using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Awareness Facts And Statistics Cyber Risk Assessment
Cyber Security Awareness Facts And Statistics Cyber Risk AssessmentThe following slide showcases some facts and figures to generate awareness about cyber-crimes. It includes elements such as hike in ransomware attacks, more employees are expected to be target of malware attacks, increasing cost of data breaches etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Awareness Facts And Statistics Cyber Risk Assessment This template helps you present information on four stages. You can also present information on Malware Attacks, Company, Social Engineering using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Plan Implementation Timeline Cyber Risk Assessment
Cyber Security Plan Implementation Timeline Cyber Risk AssessmentThe following slide presents the cyber security program execution timeline to organize tasks and ensure timely execution. It includes activities such as updating systems and passwords, performing penetration test, checking disaster recovery system, conducting training etc. Introducing Cyber Security Plan Implementation Timeline Cyber Risk Assessment to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Systems And Passwords, Cyber Security Plan, Implementation Timeline using this template. Grab it now to reap its full benefits.
-
 Data Highlighting Cyber Security Unawareness Among Employees Cyber Risk Assessment
Data Highlighting Cyber Security Unawareness Among Employees Cyber Risk AssessmentThe following slide depicts some figures to analyze the awareness gap among staff regarding cyber safety. It includes statistics such as clicking suspicious links, transferring data over personal cloud, securing systems with weak passwords etc. Introducing Data Highlighting Cyber Security Unawareness Among Employees Cyber Risk Assessment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Data Highlighting, Cyber Security Unawareness using this template. Grab it now to reap its full benefits.
-
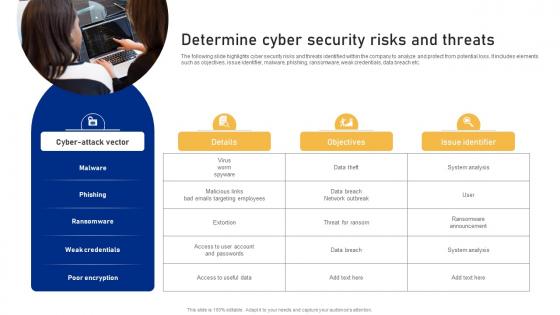 Determine Cyber Security Risks And Threats Cyber Risk Assessment
Determine Cyber Security Risks And Threats Cyber Risk AssessmentThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Increase audience engagement and knowledge by dispensing information using Determine Cyber Security Risks And Threats Cyber Risk Assessment This template helps you present information on three stages. You can also present information on Malware, Phishing, Ransomware, Weak Credentials using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Global Cyber Security Trend Analysis Cyber Risk Assessment
Global Cyber Security Trend Analysis Cyber Risk AssessmentThe following slide depicts the key statistics about cyber security trends to project future performance. It mainly includes elements such as increase in ransomware attacks, average data breach costs, approximate number of businesses prone to cyber attacks etc. Deliver an outstanding presentation on the topic using this Global Cyber Security Trend Analysis Cyber Risk Assessment Dispense information and present a thorough explanation of Global Cyber Security, Trend Analysis using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
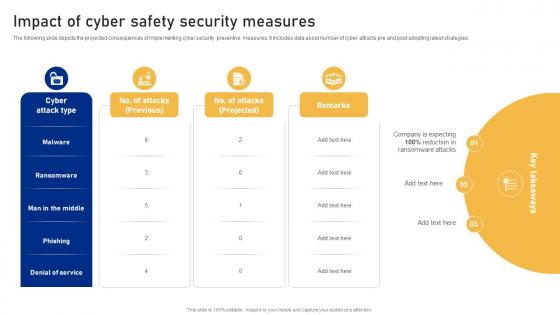 Impact Of Cyber Safety Security Measures Cyber Risk Assessment
Impact Of Cyber Safety Security Measures Cyber Risk AssessmentThe following slide depicts the projected consequences of implementing cyber security preventive measures. It includes data about number of cyber attracts pre and post adopting latest strategies. Present the topic in a bit more detail with this Impact Of Cyber Safety Security Measures Cyber Risk Assessment Use it as a tool for discussion and navigation on Cyber Attack, Ransomware, Projected This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Impact Of Cyber Security Policies And Practices Cyber Risk Assessment
Impact Of Cyber Security Policies And Practices Cyber Risk AssessmentThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, Introducing Impact Of Cyber Security Policies And Practices Cyber Risk Assessment to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Security Guidelines, Management, Privacy Policies using this template. Grab it now to reap its full benefits.
-
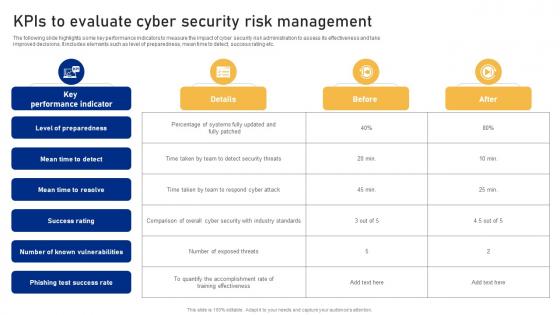 KPIS To Evaluate Cyber Security Risk Management Cyber Risk Assessment
KPIS To Evaluate Cyber Security Risk Management Cyber Risk AssessmentThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIS To Evaluate Cyber Security Risk Management Cyber Risk Assessment Use it as a tool for discussion and navigation on Performance Indicator, Success Rating, Risk Management This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Organize Cyber Security Training For Employees Regularly Cyber Risk Assessment
Organize Cyber Security Training For Employees Regularly Cyber Risk AssessmentThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Present the topic in a bit more detail with this Organize Cyber Security Training For Employees Regularly Cyber Risk Assessment Use it as a tool for discussion and navigation on Document Management, Passwords, Social Media Policy This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Prioritize Cyber Security Risk With Severity Matrix Cyber Risk Assessment
Prioritize Cyber Security Risk With Severity Matrix Cyber Risk AssessmentThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Present the topic in a bit more detail with this Prioritize Cyber Security Risk With Severity Matrix Cyber Risk Assessment Use it as a tool for discussion and navigation on Prioritize, Cyber Security Risk, Severity Matrix This template is free to edit as deemed fit for your organization. Therefore download it now.
-
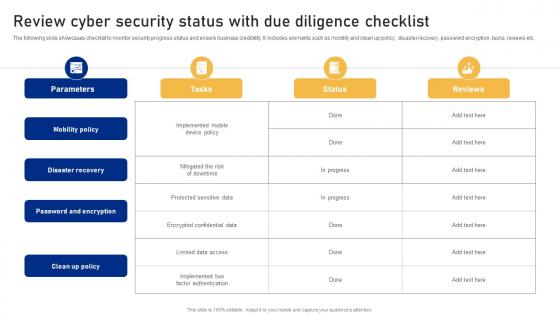 Review Cyber Security Status With Due Diligence Checklist Cyber Risk Assessment
Review Cyber Security Status With Due Diligence Checklist Cyber Risk AssessmentThe following slide showcases checklist to monitor security progress status and ensure business credibility. It includes elements such as mobility and clean up policy, disaster recovery, password encryption, tasks, reviews etc. Present the topic in a bit more detail with this Review Cyber Security Status With Due Diligence Checklist Cyber Risk Assessment Use it as a tool for discussion and navigation on Mobility Policy, Disaster Recovery, Password And Encryption This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Select Tools To Reduce Cyber Security Failure Cyber Risk Assessment
Select Tools To Reduce Cyber Security Failure Cyber Risk AssessmentThe following slide highlights some best tools to track and minimize the impact of cyber risks. It includes elements such as tool anme, features, trial period, cost and reviews etc. Introducing Select Tools To Reduce Cyber Security Failure Cyber Risk Assessment to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Suspicious Activities, Select Tools, Cyber Security Failure using this template. Grab it now to reap its full benefits.
-
 Mitigating Cloning Risks In Cyber Security
Mitigating Cloning Risks In Cyber SecurityThis slide shows strategies to counter cloning attacks. The purpose of this slide is to help cybersecurity experts in identifying and preventing cybersecurity threats. It covers mitigating measures such as security awareness training, email credentials security, link authentication, etc. Introducing our premium set of slides with name Mitigating Cloning Risks In Cyber Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Awareness, Link Authentication, Security Solutions. So download instantly and tailor it with your information.
-
 Types And Techniques Of Cloning Risks In Cyber Security
Types And Techniques Of Cloning Risks In Cyber SecurityThis slide covers different types of cloning and techniques that provides attackers an unauthorized access to confidential data. It covers three types of cloning such as device, software and identity cloning. Introducing our Types And Techniques Of Cloning Risks In Cyber Security set of slides. The topics discussed in these slides are Device Cloning, Software Cloning, Identity Cloning. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Conduct Third Party Risk Assessment Creating Cyber Security Awareness
Conduct Third Party Risk Assessment Creating Cyber Security AwarenessThe following slide illustrates checklist to evaluate third party risk assessment to eliminate unnecessary threats. It includes elements such as cyber security policies, patch management process, physical security guidelines, information safety etc. Deliver an outstanding presentation on the topic using this Conduct Third Party Risk Assessment Creating Cyber Security Awareness Dispense information and present a thorough explanation of Response, Status, Notes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Cyber Security Risks And Threats Creating Cyber Security Awareness
Determine Cyber Security Risks And Threats Creating Cyber Security AwarenessThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Present the topic in a bit more detail with this Determine Cyber Security Risks And Threats Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Human Errors, Factor Authentication This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Evaluate Impact And Probability Of Risk Occurrence Creating Cyber Security Awareness
Evaluate Impact And Probability Of Risk Occurrence Creating Cyber Security AwarenessThe following slide depicts the potential risk score of identified cyber risks to communicate and level threats. It includes key elements such as human and general errors, outdated security policy, selling companys confidential information, system failure etc. Deliver an outstanding presentation on the topic using this Evaluate Impact And Probability Of Risk Occurrence Creating Cyber Security Awareness Dispense information and present a thorough explanation of Data Backup Methods, Network Attached Storage, Cloud Storage Services using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Kpis To Evaluate Cyber Security Risk Management Creating Cyber Security Awareness
Kpis To Evaluate Cyber Security Risk Management Creating Cyber Security AwarenessThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this Kpis To Evaluate Cyber Security Risk Management Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Minimizes Malware Infection, Security Requirements, Internal Risks This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Monitor And Assess Vendor Risk Management Creating Cyber Security Awareness
Monitor And Assess Vendor Risk Management Creating Cyber Security AwarenessThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Deliver an outstanding presentation on the topic using this Monitor And Assess Vendor Risk Management Creating Cyber Security Awareness Dispense information and present a thorough explanation of Select Strong Password, Conduct Password Test, Password Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Prioritize Cyber Security Risk With Severity Matrix Creating Cyber Security Awareness
Prioritize Cyber Security Risk With Severity Matrix Creating Cyber Security AwarenessThe following slide depicts cyber security risk assessment grid to prioritize and eliminate occurrence of threats. It includes elements such as moderate, severe, minor, negligible, rate, possible, likely, unlikely etc. Present the topic in a bit more detail with this Prioritize Cyber Security Risk With Severity Matrix Creating Cyber Security Awareness Use it as a tool for discussion and navigation on Target Audience, Document Management This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Run Penetration Testing To Review Risk Creating Cyber Security Awareness
Run Penetration Testing To Review Risk Creating Cyber Security AwarenessThe following slide showcases various methods to review cyber risks to determine probability and impact of risks. It includes elements such as penetration, red team and risk based testing along with objectives, features, cost, outcomes, duration etc. Deliver an outstanding presentation on the topic using this Run Penetration Testing To Review Risk Creating Cyber Security Awareness Dispense information and present a thorough explanation of Minimizes Data Breaches, Controls User Access, Improves Tracking Visibility using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
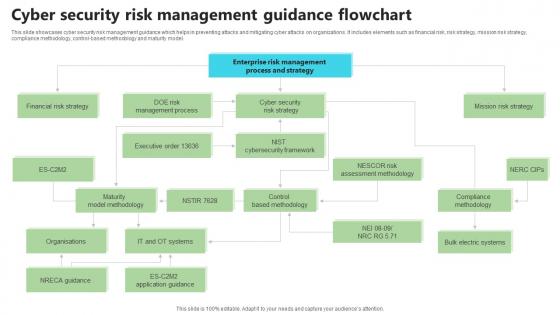 Cyber Security Risk Management Guidance Flowchart
Cyber Security Risk Management Guidance FlowchartThis slide showcases cyber security risk management guidance which helps in preventing attacks and mitigating cyber attacks on organizations. It includes elements such as financial risk, risk strategy, mission risk strategy, compliance methodology, control-based methodology and maturity model. Introducing our Cyber Security Risk Management Guidance Flowchart set of slides. The topics discussed in these slides are Financial Risk Strategy, Compliance Methodology, Mission Risk Strategy. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Opsec Cyber Security To Eliminate Business Risks
Opsec Cyber Security To Eliminate Business RisksThis slide showcases the multiple threats eliminated by opsec cybersecurity measures. This slide aims to help the business understand the importance of opsec security measures. It includes elements such as third party risks, social engineering, etc. Introducing our premium set of slides with Opsec Cyber Security To Eliminate Business Risks. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Social Engineering,Patch Management,Malware And Ransomware. So download instantly and tailor it with your information.
-
 Security Standards And Framework For IoT Risk Mitigation IoT Security And Privacy Safeguarding IoT SS
Security Standards And Framework For IoT Risk Mitigation IoT Security And Privacy Safeguarding IoT SSThis side presents IoT security standards and framework that help organisation for risk mitigation. It incudes security standards such as ISO 27000 series, NIST SP 800 53, and NIST CSF controls. Introducing Security Standards And Framework For IoT Risk Mitigation IoT Security And Privacy Safeguarding IoT SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on International Organization, Information Security Issues, Management System, using this template. Grab it now to reap its full benefits.
-
 Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats
Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates checklist to evaluate third party risk assessment to eliminate unnecessary threats. It includes elements such as cyber security policies, patch management process, physical security guidelines, information safety etc. Deliver an outstanding presentation on the topic using this Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Parameters, Response, Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security Threats
Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights cyber security risks and threats identified within the company to analyze and protect from potential loss. It includes elements such as objectives, issue identifier, malware, phishing, ransomware, weak credentials, data breach etc. Deliver an outstanding presentation on the topic using this Determine Cyber Security Risks And Threats Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Malware, Phishing, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security Threats
KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights some key performance indicators to measure the impact of cyber security risk administration to assess its effectiveness and take improved decisions. It includes elements such as level of preparedness, mean time to detect, success rating etc. Present the topic in a bit more detail with this KPIs To Evaluate Cyber Security Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Level Of Preparedness, Mean Time To Detect, Mean Time To Resolve This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats
Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases vendor risk analysis checklist to ensure customer data safety. It includes key elements such as information security and privacy, physical assets, web application, infrastructure security etc. Present the topic in a bit more detail with this Monitor And Assess Vendor Risk Management Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Information Security And Privacy, Physical Assets And Data Security, Web Application Security This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security Threats
Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases various methods to review cyber risks to determine probability and impact of risks. It includes elements such as penetration, red team and risk based testing along with objectives, features, cost, outcomes, duration etc. Present the topic in a bit more detail with this Run Penetration Testing To Review Risk Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Objectives, Features, Duration This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Best Practices Of SaaS Security Risk Management
Best Practices Of SaaS Security Risk ManagementThis slide showcases the practices of SaaS security risk management. Its purpose is to protect critical workloads to ensure compliance. This slide includes vulnerability identification, analysis, risk assessment and remediation. Introducing Best Practices Of SaaS Security Risk Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Vulnerability Identification, Remediation, Risk Assessment, Analysis, using this template. Grab it now to reap its full benefits.
-
 Cloud Cyber Security SaaS Risk Management
Cloud Cyber Security SaaS Risk ManagementThis slide showcases the cloud cyber security SaaS risk management. Its aim is to control profile and manage the risk involved. This slide includes authorization, monitor, cloud based, continuously monitor, etc. Introducing Cloud Cyber Security SaaS Risk Management to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Control Profiles, Cloud Security Risk Management, Security Categorization, using this template. Grab it now to reap its full benefits.
-
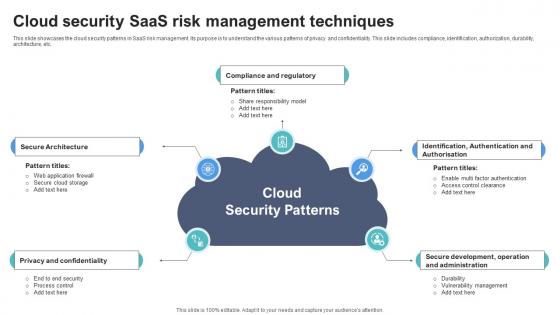 Cloud Security SaaS Risk Management Techniques
Cloud Security SaaS Risk Management TechniquesThis slide showcases the cloud security patterns in SaaS risk management. Its purpose is to understand the various patterns of privacy and confidentiality. This slide includes compliance, identification, authorization, durability, architecture, etc. Introducing Cloud Security SaaS Risk Management Techniques to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Secure Architecture, Privacy And Confidentiality, Cloud Security Patterns, Compliance And Regulatory, using this template. Grab it now to reap its full benefits.
-
 Principles Of SaaS Security Risk Management
Principles Of SaaS Security Risk ManagementThis slide showcases the principles of SaaS risk based security management. Its aim is to secure infrastructure for assessing risk. This slide includes network control, VM management, data protection, incident, reliability, access management, etc. Present the topic in a bit more detail with this Principles Of SaaS Security Risk Management. Use it as a tool for discussion and navigation on Access Management, Network Control, Perimeter Network Control. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
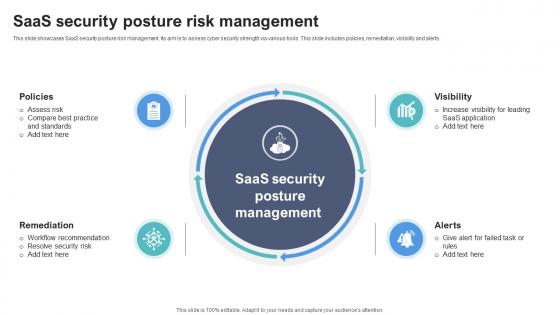 SaaS Security Posture Risk Management
SaaS Security Posture Risk ManagementThis slide showcases SaaS security posture risk management. Its aim is to assess cyber security strength via various tools. This slide includes policies, remediation, visibility and alerts. Increase audience engagement and knowledge by dispensing information using SaaS Security Posture Risk Management. This template helps you present information on four stages. You can also present information on Visibility, Policies, Remediation, Alerts using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
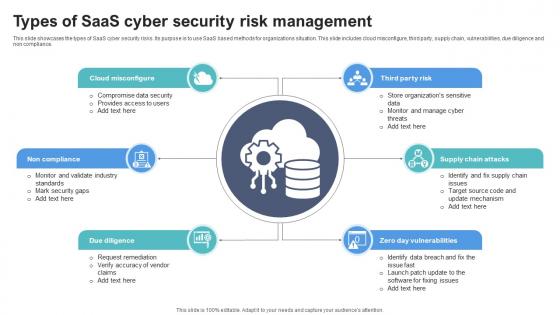 Types Of SaaS Cyber Security Risk Management
Types Of SaaS Cyber Security Risk ManagementThis slide showcases the types of SaaS cyber security risks. Its purpose is to use SaaS based methods for organizations situation. This slide includes cloud misconfigure, third party, supply chain, vulnerabilities, due diligence and non compliance. Increase audience engagement and knowledge by dispensing information using Types Of SaaS Cyber Security Risk Management. This template helps you present information on six stages. You can also present information on Supply Chain Attacks, Zero Day Vulnerabilities, Due Diligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Monitoring Cyber Risk Icon For Computer Security
Monitoring Cyber Risk Icon For Computer SecurityIntroducing our premium set of slides with Monitoring Cyber Risk Icon For Computer Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Monitoring Cyber Risk, Computer Security. So download instantly and tailor it with your information.
-
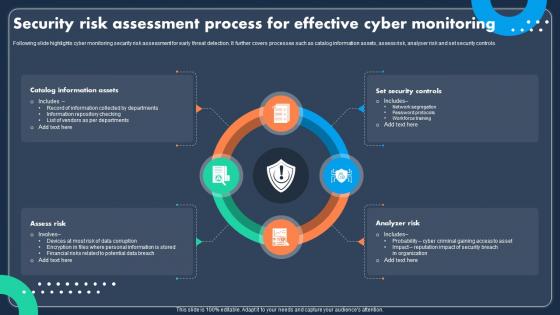 Security Risk Assessment Process For Effective Cyber Monitoring
Security Risk Assessment Process For Effective Cyber MonitoringFollowing slide highlights cyber monitoring security risk assessment for early threat detection. It further covers processes such as catalog information assets, assess risk, analyser risk and set security controls. Introducing our premium set of slides with Security Risk Assessment Process For Effective Cyber Monitoring Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Assets, Security Controls, Analyzer Risk. So download instantly and tailor it with your information.
-
 Containerization Technology Container Security Essentials To Manage Risks
Containerization Technology Container Security Essentials To Manage RisksThis slide represents the various important factors of container security to manage environmental risks. The purpose of this slide is to outline the essentials of container security to manage risks, such as configuration, automation, container security solutions, and cloud and network security. Present the topic in a bit more detail with this Containerization Technology Container Security Essentials To Manage Risks. Use it as a tool for discussion and navigation on Dashboard To Retrieve Ongoing, Time Series Data Metrics, Containers Operating,Container Dashboard. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Emerging Cloud Security Risks And Threats CASB Cloud Security
Emerging Cloud Security Risks And Threats CASB Cloud SecurityThis slide represents the emerging cloud security risks, and threats organizations can encounter. The purpose of this slide is to highlight the various threats that CASB deployment can help overcome, including VPNs, system misconfiguration, non-zero security permissions, and so on. Present the topic in a bit more detail with this Emerging Cloud Security Risks And Threats CASB Cloud Security. Use it as a tool for discussion and navigation on System Misconfigurations, Lack Of Edge Or Perimeter Security, Risks And Threats. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies To Mitigate Saas Cyber Security Risks
Strategies To Mitigate Saas Cyber Security RisksThis slide represents tips to boost SaaS cyber security by reducing risks. It aims to implement effective measures collectively to reduce cyber security risks for SaaS platform. It includes various approaches such as continuous SaaS discovery, consistent SaaS risk management, etc. Introducing our premium set of slides with Strategies To Mitigate Saas Cyber Security Risks Ellicudate the Five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Continuous Saas Discovery, Risk Management, Mitigate Vulnerabilities. So download instantly and tailor it with your information.
-
 Types Of Saas Cyber Security Risks
Types Of Saas Cyber Security RisksThis slide represents various risks associated with SaaS cyber security. It aims to protect organization against risks and proactive monitoring of systems and user activities. It includes various approaches such as cloud misconfigurations, third party risks, etc. Presenting our well structured Types Of Saas Cyber Security Risks The topics discussed in this slide are Cloud Misconfigurations, Third Party Risks, Supply Chain Attacks. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience





