Powerpoint Templates and Google slides for Security Risks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Framework For Information Security Risk Management Formulating Cybersecurity Plan
Framework For Information Security Risk Management Formulating Cybersecurity PlanThis slide showcases framework that can help organization to formulate plan for information security risk management. Its key elements are identify risks, analyze risks, evaluate and treat risks. Deliver an outstanding presentation on the topic using this Framework For Information Security Risk Management Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Establish The Context, Identify Risks, Analyze Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Information Security And Risk Management User Spending Formulating Cybersecurity Plan
Information Security And Risk Management User Spending Formulating Cybersecurity PlanThis slide showcases expenses done by organization in different segments of information security and risk management. Key segments include application security, cloud security, data security, identify access management, infrastructure protection, integrated risk management, security services etc. Deliver an outstanding presentation on the topic using this Information Security And Risk Management User Spending Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Application Security, Identity Access Management, Integrated Risk Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 KPIS To Measure Information Security Risk Management Formulating Cybersecurity Plan
KPIS To Measure Information Security Risk Management Formulating Cybersecurity PlanThis slide showcases KPIs that can help organization to measure the impact of cybersecurity risk management programme. It showcases estimated figures before and after implementation of plan. Deliver an outstanding presentation on the topic using this KPIS To Measure Information Security Risk Management Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Intrusion Attempts, Mean Time Between Failures, Mean Time To Resolve using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Process For Information Security Risk Assessment Formulating Cybersecurity Plan
Process For Information Security Risk Assessment Formulating Cybersecurity PlanThis slide showcases process that can help organization to perform information security risk assessment. It can help identify security threats and allocate vulnerability rating to information assets. Introducing Process For Information Security Risk Assessment Formulating Cybersecurity Plan to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Identifying Internal, Information Security Threats, Information Assets, using this template. Grab it now to reap its full benefits.
-
 Reporting Structure For Information Security Risk Management Formulating Cybersecurity Plan
Reporting Structure For Information Security Risk Management Formulating Cybersecurity PlanThis slide showcases plan that can help to communicate the major risks report on regular intervals. Its key components are risk, reported by, frequency, likelihood, criticality and impact. Present the topic in a bit more detail with this Reporting Structure For Information Security Risk Management Formulating Cybersecurity Plan. Use it as a tool for discussion and navigation on Reporting Structure, Information Security, Risk Management. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps For Information Security Risk Management Formulating Cybersecurity Plan
Steps For Information Security Risk Management Formulating Cybersecurity PlanThis slide showcase steps which can help organization to implement information security risk management program in organization. Its key steps are identify, protect, detect and respond. Deliver an outstanding presentation on the topic using this Steps For Information Security Risk Management Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Asset Identification, Risk Assessment, Awareness And Training using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Timeline For Information Security Risk Management Training Formulating Cybersecurity Plan
Timeline For Information Security Risk Management Training Formulating Cybersecurity PlanThis slide showcases timeline that can help organization to conduct training for information security risk management programme. It also showcases weekly and step progress. Deliver an outstanding presentation on the topic using this Timeline For Information Security Risk Management Training Formulating Cybersecurity Plan. Dispense information and present a thorough explanation of Cybersecurity Awareness, Malware Detection, Risk Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Risks In Powerpoint And Google Slides Cpb
Cyber Security Risks In Powerpoint And Google Slides CpbPresenting our Cyber Security Risks In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Cyber Security Risks This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
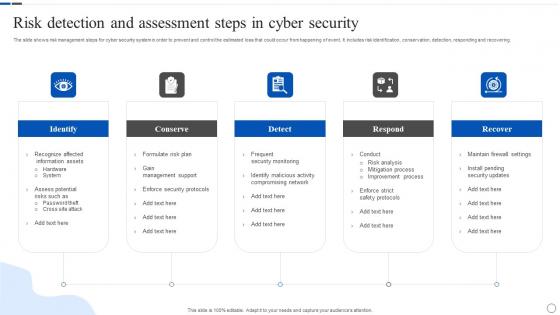 Risk Detection And Assessment Steps In Cyber Security
Risk Detection And Assessment Steps In Cyber SecurityThe slide shows risk management steps for cyber security system in order to prevent and control the estimated loss that could occur from happening of event. It includes risk identification, conservation, detection, responding and recovering. Presenting our set of slides with Risk Detection And Assessment Steps In Cyber Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Conserve, Respond, Recover.
-
 Steps Of Security Risk Assessment Method
Steps Of Security Risk Assessment MethodThe below slide illustrates the process to evaluate security risk of IT assets to improve and minimize potential damage. It constitutes of four activities identification, assessment, mitigation and prevention. Introducing our premium set of slides with Steps Of Security Risk Assessment Method. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Prevention, Identification, Assessment, Mitigation. So download instantly and tailor it with your information.
-
 Risk Assessment Cyber Security In Powerpoint And Google Slides Cpb
Risk Assessment Cyber Security In Powerpoint And Google Slides CpbPresenting Risk Assessment Cyber Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Risk Assessment Cyber Security. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber Security Risk Indicators Examples In Powerpoint And Google Slides Cpb
Cyber Security Risk Indicators Examples In Powerpoint And Google Slides CpbPresenting our Cyber Security Risk Indicators Examples In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cyber Security Risk Indicators Examples This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber Security Third Party Risk In Powerpoint And Google Slides Cpb
Cyber Security Third Party Risk In Powerpoint And Google Slides CpbPresenting our Cyber Security Third Party Risk In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Cyber Security Third Party Risk This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Importance Risk Assessment Cyber Security In Powerpoint And Google Slides Cpb
Importance Risk Assessment Cyber Security In Powerpoint And Google Slides CpbPresenting our Importance Risk Assessment Cyber Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases two stages. It is useful to share insightful information on Importance Risk Assessment Cyber Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Manage Security Risks In Powerpoint And Google Slides Cpb
Manage Security Risks In Powerpoint And Google Slides CpbPresenting our Manage Security Risks In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Manage Security Risks This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Mitigating Cyber Security Risks In Powerpoint And Google Slides Cpb
Mitigating Cyber Security Risks In Powerpoint And Google Slides CpbPresenting Mitigating Cyber Security Risks In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Mitigating Cyber Security Risks. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 It Security Gap Analysis With Risk Level
It Security Gap Analysis With Risk LevelThe following slide highlights the gaps in the IT security system to determine the opportunities for improvement. It also reflects the level of risk low, moderate, high and extreme if the gap are not fulfilled. Presenting our well structured It Security Gap Analysis With Risk Level. The topics discussed in this slide are Organization Network, Security Training Sessions, Gap Assessment. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 It Security Risk Assessment Framework
It Security Risk Assessment FrameworkThe following slide highlights the structure to identify best practices to fix risk tolerances. It constitutes of activities such as identify, protect, detect, respond and recover. Presenting our set of slides with It Security Risk Assessment Framework. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identify, Protect, Detect .
-
 It Security Risk Assessment Grid
It Security Risk Assessment GridThe following slide depicts the analysis of IT security to prevent loss of confidentiality and integrity. The matrix constitutes of elements such as risk, likelihood, its impact and overall threat level. Introducing our premium set of slides with It Security Risk Assessment Grid. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Likelihood, Risk, Impact. So download instantly and tailor it with your information.
-
 It Security Risk Management Action Plan
It Security Risk Management Action PlanThe following slide depicts the plan to administer IT security for unexpected change and contingencies. It includes elements such as threat, vulnerability, consequences, risk and possible solution etc. Introducing our It Security Risk Management Action Plan set of slides. The topics discussed in these slides are Threat, Vuinerability, Consequences. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cyber security risk assessment matrix ppt powerpoint presentation file guidelines cpb
Cyber security risk assessment matrix ppt powerpoint presentation file guidelines cpbPresenting this set of slides with name Cyber Security Risk Assessment Matrix Ppt Powerpoint Presentation File Guidelines Cpb. This is an editable Powerpoint four stages graphic that deals with topics like Cyber Security Risk Assessment Matrix to help convey your message better graphically. This product is a premium product available for immediate download, and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Cyber security risk management ppt powerpoint presentation file background image cpb
Cyber security risk management ppt powerpoint presentation file background image cpbPresenting this set of slides with name Cyber Security Risk Management Ppt Powerpoint Presentation File Background Image Cpb. This is an editable Powerpoint three stages graphic that deals with topics like Cyber Security Risk Management to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
-
 Security Controls To Reduce The Risk Of Ransomware Cybersecurity Incident And Vulnerability
Security Controls To Reduce The Risk Of Ransomware Cybersecurity Incident And VulnerabilityMentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Deliver an outstanding presentation on the topic using this Security Controls To Reduce The Risk Of Ransomware Cybersecurity Incident And Vulnerability. Dispense information and present a thorough explanation of Gains Access, Takes Control, Impacts Organization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Security Governance Risk And Compliance Model
Cloud Security Governance Risk And Compliance ModelThe following slide presents a GRC model to manage and control cloud cyber security operations and reduce the impact of risk events. It includes key components such as governance, risk and compliance. Introducing our Cloud Security Governance Risk And Compliance Model set of slides. The topics discussed in these slides are Governance, Compliance, Update And Publish Policies. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 It Risk Management Framework To Manage Security Guide To Build It Strategy Plan For Organizational Growth
It Risk Management Framework To Manage Security Guide To Build It Strategy Plan For Organizational GrowthThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Present the topic in a bit more detail with this It Risk Management Framework To Manage Security Guide To Build It Strategy Plan For Organizational Growth. Use it as a tool for discussion and navigation on Management, Framework, Environment. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Controls To Reduce The Risk Of Ransomware Upgrading Cybersecurity With Incident Response Playbook
Security Controls To Reduce The Risk Of Ransomware Upgrading Cybersecurity With Incident Response PlaybookMentioned slide depicts the incident workflow diagram of a ransomware event along with security controls implemented to mitigate it. The diagram starts with the threat actors entry and ends with the threat actor demanding ransom. Present the topic in a bit more detail with this Security Controls To Reduce The Risk Of Ransomware Upgrading Cybersecurity With Incident Response Playbook. Use it as a tool for discussion and navigation on Ransomware, Informational Impact, Recoverability Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
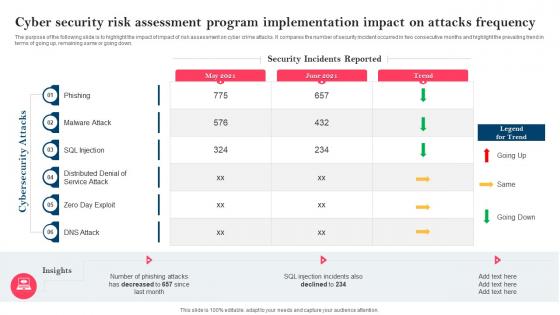 Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program Implementation
Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program ImplementationThe purpose of the following slide is to highlight the impact of impact of risk assessment on cyber crime attacks. It compares the number of security incident occurred in two consecutive months and highlight the prevailing trend in terms of going up, remaining same or going down. Present the topic in a bit more detail with this Strategy To Minimize Cyber Attacks Risks Cyber Security Risk Assessment Program Implementation. Use it as a tool for discussion and navigation on Cyber Security, Risk Assessment, Program Implementation, Impact On Attacks Frequency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Application For Security And Risk Management
IoT Application For Security And Risk ManagementThis template shows risk management using IoT. The purpose of this slide is to use IoT devices for collecting and transferring data through the internet. It includes as cloud layer, connectivity layer, physical layer Presenting our well structured IoT Application For Security And Risk Management. The topics discussed in this slide are Application, Security, Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Serverless Computing Serverless Computing Security Problems And Risks
Serverless Computing Serverless Computing Security Problems And RisksThe purpose of this slide is to outline the security challenges and risks of serverless computing. These problems are vulnerable configuration, permissions for too powerful functions, infusion of event data, insufficient function recording and monitoring, etc. Present the topic in a bit more detail with this Serverless Computing Serverless Computing Security Problems And Risks. Use it as a tool for discussion and navigation on Serverless Computing, Security Problems And Risks, Insufficient Function, Recording And Monitoring. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Risk Management Committee Diagram
Cyber Security Risk Management Committee DiagramThis slide shows flow chart of cyber security risk management team of an organization. It includes cyber security system deployment team, data center management, network member, etc. Presenting our well structured Cyber Security Risk Management Committee Diagram. The topics discussed in this slide are Management, Organization, Deployment. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Risk Management Cycle
Cyber Security Risk Management CycleThis slide shows five stages which can be used to manage cyber security risks. It includes steps such as identify risk, measure, examine, implement and monitor. Introducing our premium set of slides with Cyber Security Risk Management Cycle. Elucidate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Measure, Examine, Implement . So download instantly and tailor it with your information.
-
 Cyber Security Risk Management Diagram
Cyber Security Risk Management DiagramThis slide shows flow chart which can be used by IT departments for managing information security risk. It includes risk assessment, risk evaluation, risk communication, etc. Presenting our well structured Cyber Security Risk Management Diagram. The topics discussed in this slide are Management, Assessment, Satisfactory. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Cyber Security Risk Management Plan Implementation
Cyber Security Risk Management Plan ImplementationThis slide shows risk management plan which can be used by companies for IT security. It includes various steps such as current state analysis, assessment, target state and roadmap. Presenting our set of slides with name Cyber Security Risk Management Plan Implementation. This exhibits information on four stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Implementation, Management, Opportunities.
-
 Icon For Cyber Security Risk Management
Icon For Cyber Security Risk ManagementIntroducing our premium set of slides with Icon For Cyber Security Risk Management. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Management, Cyber Security. So download instantly and tailor it with your information.
-
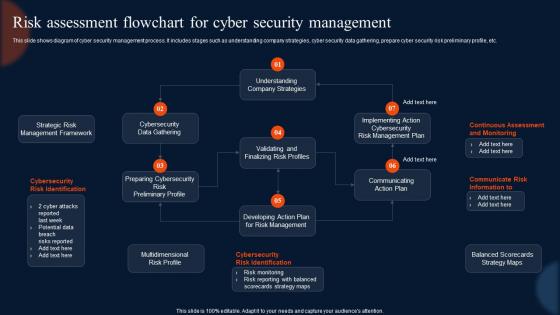 Risk Assessment Flowchart For Cyber Security Management
Risk Assessment Flowchart For Cyber Security ManagementThis slide shows diagram of cyber security management process. It includes stages such as understanding company strategies, cyber security data gathering, prepare cyber security risk preliminary profile, etc. Introducing our Risk Assessment Flowchart For Cyber Security Management set of slides. The topics discussed in these slides are Assessment, Flowchart, Management. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Risk Management Plan For Cyber Security
Risk Management Plan For Cyber SecurityThis slide signifies the cyber security risk management plan. It covers information about tasks, owner, priorities, and date. Presenting our well structured Risk Management Plan For Cyber Security. The topics discussed in this slide are Management, Information, Cyber Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Six Step Process For Risk Management In Cyber Security Project
Six Step Process For Risk Management In Cyber Security ProjectThis slide signifies the six step process for risk assessment in cyber security project. It covers information about stages like identify, analyse, evaluate, prioritize, treat and monitor Presenting our set of slides with name Six Step Process For Risk Management In Cyber Security Project. This exhibits information on six stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Management, Process, Computing Software.
-
 Strategic Framework To Manage Cyber Security Risk
Strategic Framework To Manage Cyber Security RiskThis slide shows framework which can be used by IT organizations for managing cyber security related risk. It includes step such as categorize system, security controls, implementation, assess, etc. Introducing our premium set of slides with Strategic Framework To Manage Cyber Security Risk. Elucidate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Strategic, Framework, Security Risk. So download instantly and tailor it with your information.
-
 Minimizing Security Risks In Healthcare Sector
Minimizing Security Risks In Healthcare SectorThis slide covers the details related to implementing security measures in healthcare sector to overcome risk. The purpose of this template is to define the methods adopted to maintain healthcare security. It includes information related to cybersecurity assessment, securing and educating. Presenting our well structured Minimizing Security Risks In Healthcare Sector. The topics discussed in this slide are Cybersecurity Assessment, Medical Devices, Train Clinical Staff. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 AI Security Risks In Powerpoint And Google Slides Cpb
AI Security Risks In Powerpoint And Google Slides CpbPresenting our AI Security Risks In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on AI Security Risks. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Risk Procedure Compliance Security Illustration
Risk Procedure Compliance Security IllustrationThis colourful PowerPoint Illustration is a visual representation of the Risk Procedure. It is a helpful tool for quickly understanding the process and for making the procedure easier to remember.
-
 Adopt Cyber Security Data Policies Cyber Attack Risks Mitigation
Adopt Cyber Security Data Policies Cyber Attack Risks MitigationThe following slide highlights various cyber security policies to manage data control and breach. It includes elements such as network security, data, workstations, remote access etc. Introducing Adopt Cyber Security Data Policies Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Network Security Policies, Data Security Policies, Workstation Policies, using this template. Grab it now to reap its full benefits.
-
 Impact Of Cyber Security Policies And Practices Cyber Attack Risks Mitigation
Impact Of Cyber Security Policies And Practices Cyber Attack Risks MitigationThe following slide focuses on drafting cyber security policies to manage data control and breach. It mainly includes elements such as impact of existing cyber safety policies, mitigation actions, etc. Present the topic in a bit more detail with this Impact Of Cyber Security Policies And Practices Cyber Attack Risks Mitigation. Use it as a tool for discussion and navigation on Inadequate Security Guidelines, Inappropriate Privacy Policies. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Multiple Strategic Cyber Security Approaches Cyber Attack Risks Mitigation
Multiple Strategic Cyber Security Approaches Cyber Attack Risks MitigationThe following slide depicts various cyber safety approaches to encrypt and back up key data to avoid information loss and improved accessibility. It includes elements such as data, application, infrastructure, network, devices, automation etc. Increase audience engagement and knowledge by dispensing information using Multiple Strategic Cyber Security Approaches Cyber Attack Risks Mitigation. This template helps you present information on one stage. You can also present information on Identities, Organization Policy, Threat Intelligence using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Organize Cyber Security Training For Employees Regularly Cyber Attack Risks Mitigation
Organize Cyber Security Training For Employees Regularly Cyber Attack Risks MitigationThe following slide depicts the staff cyber security training plan to educate them regarding technology threats and practices. It mainly includes elements such as topics to be covered, target audience, trainer name, mode, proposed date, timings etc. Introducing Organize Cyber Security Training For Employees Regularly Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with one stage, this template is a great option to educate and entice your audience. Dispence information on Document Management, Response Process, Social Media Policy, using this template. Grab it now to reap its full benefits.
-
 Passive Active And Offensive Cyber Security Strategies Cyber Attack Risks Mitigation
Passive Active And Offensive Cyber Security Strategies Cyber Attack Risks MitigationThe following slide showcases passive, active and offensive cyber safety techniques to ensure customer data safety. It includes elements such as inspecting vulnerabilities, penetration testing, deception technology, threat hunting etc. Increase audience engagement and knowledge by dispensing information using Passive Active And Offensive Cyber Security Strategies Cyber Attack Risks Mitigation. This template helps you present information on three stages. You can also present information on Passive Safety, Active Safety, Offensive Safety using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Proactive And Reactive Phases Of Cyber Security Cyber Attack Risks Mitigation
Proactive And Reactive Phases Of Cyber Security Cyber Attack Risks MitigationThe following slide depicts the stages of cyber security to avoid information loss and improved accessibility. It includes elements such as managing attack surface, optimizing process, stakeholder engagement etc. Introducing Proactive And Reactive Phases Of Cyber Security Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Proactive, Managing Attack Surface, Optimize Process, Stakeholder Engagement, using this template. Grab it now to reap its full benefits.
-
 Stages Of Implementing Cyber Security Strategies Cyber Attack Risks Mitigation
Stages Of Implementing Cyber Security Strategies Cyber Attack Risks MitigationThe following slide highlights major stages of executing cyber security techniques to ensure effective implementation. It includes elements such as plan, analyze, upgrade, continuous improvement etc. Increase audience engagement and knowledge by dispensing information using Stages Of Implementing Cyber Security Strategies Cyber Attack Risks Mitigation. This template helps you present information on four stages. You can also present information on Plan Strategy, Implement Strategy, Analyse Strategy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Steps To Create Cyber Security Strategies Cyber Attack Risks Mitigation
Steps To Create Cyber Security Strategies Cyber Attack Risks MitigationThe following slide illustrates some steps to create and implement cybersecurity techniques. It includes elements such as determining threat type, selecting security framework, optimizing plan, implementing strategy etc. Introducing Steps To Create Cyber Security Strategies Cyber Attack Risks Mitigation to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Comprehend Threat Landscape, Evaluate Cybersecurity Maturity, Optimize Cybersecurity Program, using this template. Grab it now to reap its full benefits.
-
 Strategic Cyber Security Action Plan Cyber Attack Risks Mitigation
Strategic Cyber Security Action Plan Cyber Attack Risks MitigationThe following slide depicts action plan to minimize impact of cyber attacks. It includes elements such as understand, develop, deliver, assess organizational principles, evaluate alternatives, examine possible alternatives, execute actions etc. Increase audience engagement and knowledge by dispensing information using Strategic Cyber Security Action Plan Cyber Attack Risks Mitigation. This template helps you present information on three stages. You can also present information on Understand, Develop, Deliver, Organizational Principles using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Social Security Risk Management In Powerpoint And Google Slides Cpb
Social Security Risk Management In Powerpoint And Google Slides CpbPresenting our Social Security Risk Management In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Social Security Risk Management This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Mitigating Supply Chain Security Risks
Mitigating Supply Chain Security RisksThe following slide highlights strategies to mitigate supply chain security risks to protect business from hackers and susceptible targets. It includes strategies such as inspection, automation, manage vulnerabilities and risk reduction. Presenting our set of slides with Mitigating Supply Chain Security Risks This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Unauthorized Access, International Supply Chain
-
 Supply Chain Security Risk Management Process
Supply Chain Security Risk Management ProcessThis slide showcases process that can help organization to manage supply chain security risks. Its key steps are document risks, develop framework, monitor risk and regular review. Introducing our premium set of slides with Supply Chain Security Risk Management Process Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Document Risks, Develop Framework. So download instantly and tailor it with your information.
-
 Digital Security Risk In Powerpoint And Google Slides Cpb
Digital Security Risk In Powerpoint And Google Slides CpbPresenting Digital Security Risk In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Digital Security Risk. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Browser Extension Security Risk In Powerpoint And Google Slides Cpb
Browser Extension Security Risk In Powerpoint And Google Slides CpbPresenting our Browser Extension Security Risk In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Browser Extension Security Risk. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Mitigate Security Risk In Powerpoint And Google Slides Cpb
Mitigate Security Risk In Powerpoint And Google Slides CpbPresenting Mitigate Security Risk In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Mitigate Security Risk. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber Security Risk Assessment And Management Matrix Incident Response Strategies Deployment
Cyber Security Risk Assessment And Management Matrix Incident Response Strategies DeploymentThis slide represents the assessment of vulnerability and consequences of the cyber security incidents on the operations of the company. It includes details related to threat, vulnerability, consequences, risk and solution. Deliver an outstanding presentation on the topic using this Cyber Security Risk Assessment And Management Matrix Incident Response Strategies Deployment. Dispense information and present a thorough explanation of Vulnerability, Consequences, Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategic Initiatives Playbook IT Risk Management Framework To Manage Security Threats
Strategic Initiatives Playbook IT Risk Management Framework To Manage Security ThreatsThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Deliver an outstanding presentation on the topic using this Strategic Initiatives Playbook IT Risk Management Framework To Manage Security Threats. Dispense information and present a thorough explanation of IT Risk Management, Framework To Manage, Security Threats, Platform Upgradation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IT Risk Management Framework To Manage Security Threats IT Cost Optimization And Management Strategy SS
IT Risk Management Framework To Manage Security Threats IT Cost Optimization And Management Strategy SSThis slide provides information regarding the implementation of IT risk management framework to monitor security threats. The initiatives include the implementation of an enterprise security program, deploy a control environment, etc. Present the topic in a bit more detail with this IT Risk Management Framework To Manage Security Threats IT Cost Optimization And Management Strategy SS. Use it as a tool for discussion and navigation on Implement Control Environment, Implement Security Processes, Enterprise Security Program. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 RPA Security Best Practices To Minimize Cybercrime Risk
RPA Security Best Practices To Minimize Cybercrime RiskThis slide outlines strategies to minimize security failure in RPA projects. Some of the best practices such as maintain accountability for BOT actions, prevent fraud and abuse, preserve log integrity, and authorize secure RPA development. Introducing our premium set of slides with RPA Security Best Practices To Minimize Cybercrime Risk. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Preserve Log Integrity, Development , Prevent Fraud. So download instantly and tailor it with your information.





