Powerpoint Templates and Google slides for Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Structural Design Of Blockchain Technology On Security Threats
Structural Design Of Blockchain Technology On Security ThreatsIntroducing our Structural Design Of Blockchain Technology On Security Threats set of slides. The topics discussed in these slides are Application Layer, Contract Layer, Incentive Layer. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Types Of Consensus Algorithms In Blockchain Security
Types Of Consensus Algorithms In Blockchain SecurityIntroducing our premium set of slides with Types Of Consensus Algorithms In Blockchain Security. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Proof Stake, Proof Burn, Delegated Proof. So download instantly and tailor it with your information.
-
 Maritime Security Contractor Jobs In Powerpoint And Google Slides Cpp
Maritime Security Contractor Jobs In Powerpoint And Google Slides CppPresenting Maritime Security Contractor Jobs In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Maritime Security Contractor Jobs. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Oil Field Security Jobs In Powerpoint And Google Slides Cpp
Oil Field Security Jobs In Powerpoint And Google Slides CppPresenting our Oil Field Security Jobs In Powerpoint And Google Slides Cpp PowerPoint template design. This PowerPoint slide showcases six stages. It is useful to share insightful information on Oil Field Security Jobs This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cybersecurity Policy Checklist To Secure Sensitive Data
Cybersecurity Policy Checklist To Secure Sensitive DataThis slide showcases the cybersecurity policy checklist protecting sensitive data which helps an organization to secure technology and information assets and control business information. It include details such as prepare, verify, analyze, respond, etc. Introducing our Cybersecurity Policy Checklist To Secure Sensitive Data set of slides. The topics discussed in these slides are Prepare, AnalyzeThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Benefits Of Desktop As A Service Security Architecture
Benefits Of Desktop As A Service Security ArchitectureThis slide highlights the benefits of installing a desktop as a service security architecture. The purpose of this slide is to help the business leverage DaaS to improve its efficiency and profitability. It includes DRaaS, MFA for additional security, etc. Introducing our premium set of slides with Benefits Of Desktop As A Service Security Architecture Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Additional Security, Updates And Security Patches So download instantly and tailor it with your information.
-
 Desktop As A Service Icon For Improving Data Security
Desktop As A Service Icon For Improving Data SecurityPresenting our set of slides with Desktop As A Service Icon For Improving Data Security This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Desktop As A Service Icon, Improving Data Security
-
 Security Considerations Icon For SaaS Implementation
Security Considerations Icon For SaaS ImplementationIntroducing our premium set of slides with Security Considerations Icon For SaaS Implementation Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Considerations, Saas Implementation So download instantly and tailor it with your information.
-
 Security Trends To Mitigate Corporate Cyber Threats
Security Trends To Mitigate Corporate Cyber ThreatsThis slide represents various trends that help companies to enhance security against cyber attacks for effective data protection. It includes various trends such as firewall as a service, extended detection and response, and third-party supply chain risk management. Presenting our well structured Security Trends To Mitigate Corporate Cyber Threats. The topics discussed in this slide are Trends, Overview, Impact. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Effective Methods For Assuring Building Security
Effective Methods For Assuring Building SecurityPresenting our set of slides with Effective Methods For Assuring Building Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Regulate Key Control, Develop Reception Area, Provide Employee Trainings.
-
 Synthetic Biology And Security In Powerpoint And Google Slides Cpp
Synthetic Biology And Security In Powerpoint And Google Slides CppPresenting Synthetic Biology And Security In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Synthetic Biology And Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 E Commerce Subscription Data Security Management Techniques
E Commerce Subscription Data Security Management TechniquesThis slide highlights the techniques to secure e-commerce subscription data to ensure data protection and management for trust building. Key strategies are encryption strategy, hand-on monitoring, and contingency planning. Introducing our premium set of slides with E Commerce Subscription Data Security Management Techniques Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Encryption Strategy, Hands-On Monitoring, Contingency Planning So download instantly and tailor it with your information.
-
 Gateway Integration Security In Powerpoint And Google Slides Cpp
Gateway Integration Security In Powerpoint And Google Slides CppPresenting our Gateway Integration Security In Powerpoint And Google Slides Cpp PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Gateway Integration Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 SaaS Architecture For Security Icon
SaaS Architecture For Security IconIntroducing our premium set of slides with name SaaS Architecture For Security Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like SaaS Architecture, Security. So download instantly and tailor it with your information.
-
 Swift Payment Icon For Fast And Secure Transactions
Swift Payment Icon For Fast And Secure TransactionsPresenting our set of slides with name Swift Payment Icon For Fast And Secure Transactions. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Swift Payment, Fast, Secure Transactions.
-
 Swift Payment Icon For Secure Transactions
Swift Payment Icon For Secure TransactionsIntroducing our Swift Payment Icon For Secure Transactions set of slides. The topics discussed in these slides are Swift Payment, Secure Transactions. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Swift Payment Security Features And Impact
Swift Payment Security Features And ImpactThe purpose of this slide is to elucidate how swift payment security features and their impact contribute to robust protection and trust in financial transactions. It includes features, procedure, and its effect. Presenting our set of slides with name Swift Payment Security Features And Impact. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Feature, Use Cases, Impact.
-
 Incident Response And Security Management Training Plan
Incident Response And Security Management Training PlanThe purpose of this slide is to ensure quick and effective response to security incidents. It lays out incident response and security management training plan covering elements such as lesson, date, mode of training, duration and trainer. Presenting our well structured Incident Response And Security Management Training Plan The topics discussed in this slide are Mode Of Training, Duration, TrainerThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
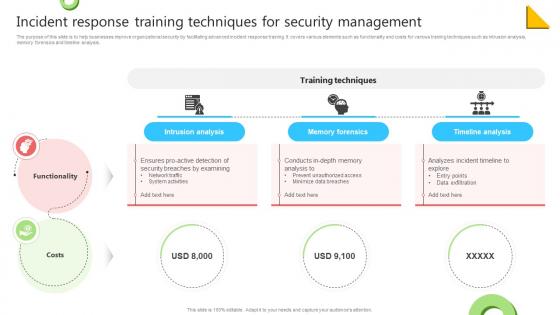 Incident Response Training Techniques For Security Management
Incident Response Training Techniques For Security ManagementThe purpose of this slide is to help businesses improve organizational security by facilitating advanced incident response training. It covers various elements such as functionality and costs for various training techniques such as intrusion analysis, memory forensics and timeline analysis. Introducing our premium set of slides with Incident Response Training Techniques For Security Management Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Intrusion Analysis, Memory Forensics, Timeline Analysis So download instantly and tailor it with your information.
-
 Blockchain Security Trends In Project Management
Blockchain Security Trends In Project ManagementThis slide exhibits the various security trends of blockchain technology in project management that helps to prevent data breaches and optimize the transactional process. The major trends are record management, asset exchange, and performance management. Presenting our set of slides with Blockchain Security Trends In Project Management. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Record Management, Asset Exchange, Performance Optimization.
-
 Encryption Secure Communication In Powerpoint And Google Slides Cpp
Encryption Secure Communication In Powerpoint And Google Slides CppPresenting Encryption Secure Communication In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Encryption Secure Communication. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Ai Network Security Icon Of Lock
Ai Network Security Icon Of LockPresenting our well structured Ai Network Security Icon Of Lock. The topics discussed in this slide are AI Network, Security Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Ai Network Security Icon With Cloud Computing
Ai Network Security Icon With Cloud ComputingIntroducing our Ai Network Security Icon With Cloud Computing set of slides. The topics discussed in these slides are AI Network Security, Cloud Computing. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ai Network Security Icon With Secure Database
Ai Network Security Icon With Secure DatabasePresenting our well structured Ai Network Security Icon With Secure Database. The topics discussed in this slide are AI Network Security, Secure Database. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Ai Network Security Open Source Tools
Ai Network Security Open Source ToolsThis slide depicts the top trending open-source artificial interline network security tools KeePass, Open VAS, Zed attack proxy, and VeraCrypt. Introducing our Ai Network Security Open Source Tools set of slides. The topics discussed in these slides are Identifies Security Weaknesses, Proxy Interception, Unique Passwords. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ai Powered Network Security Threats
Ai Powered Network Security ThreatsThis slide shows the various threats faced by companies after deploying artificial intelligence in cloud computing security networks. The major threats organizations face are advanced phishing attacks, deep fake attacks, credential stuffing Presenting our set of slides with Ai Powered Network Security Threats. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Advanced Phishing Attacks, Deepfake Attacks, Credential Stuffing .
-
 Ai Revolutionizing Network Security Systems In Organisation
Ai Revolutionizing Network Security Systems In OrganisationThis slide shows how AI benefits the organization in multiple ways. The major benefits are they provide real-time threat detection, increase automation, and behavioral analysis. Introducing our premium set of slides with Ai Revolutionizing Network Security Systems In Organisation. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Real Time Threat Detection, Email Filtering, Behavioural Analysis. So download instantly and tailor it with your information.
-
 Benefits Of Deploying Ai In Network Security
Benefits Of Deploying Ai In Network SecurityThis slide shows the major benefits of using artificial intelligence for security purposes. The major benefits are faster threat detection, improved accuracy, improved scalability and cost-saving Presenting our set of slides with Benefits Of Deploying Ai In Network Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Faster Threat Detection, Improved Accuracy, Scalability And Cost Saving .
-
 Deploying Ai Network Security In Defence Sector
Deploying Ai Network Security In Defence SectorThis slide shows how artificial intelligence is deployed in the defense sector to build strong network security. The major reasons for deploying AI are to analyse network threats, malware detection, insider threat detection and mitigation Introducing our premium set of slides with Deploying Ai Network Security In Defence Sector. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Threat Analysis, Malware Detection, Insider Threat Detection And Mitigation. So download instantly and tailor it with your information.
-
 Future Of Artificial Intelligence In Network Security
Future Of Artificial Intelligence In Network SecurityThis slide shows the future perspective of deploying artificial intelligence in cyber security networks. It assists in multiple ways such as automating threat response, enhance encryption, and adaptive security framework. Presenting our set of slides with Future Of Artificial Intelligence In Network Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Automate Threat Response, Enhanced Encryption, Adaptive Security Framework.
-
 Malicious Uses Of Ai In Network Security
Malicious Uses Of Ai In Network SecurityThis slide shows the major activities that are malicious in natures face after deploying artificial intelligence for cyber security. The top malicious activities tracks are password cracking, defender-aware malware, data poisoning, and bots. Presenting our set of slides with Malicious Uses Of Ai In Network Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Password Cracking, Data Poisoning And Bots, Defender Aware Malware.
-
 Top Ai Network Security Company Matrix
Top Ai Network Security Company MatrixThis slide shows the top AI cybersecurity network companies that provide safe AI algorithms. These companies are Darktrace, Cisco, Fortinet, CrowdStrike. Presenting our well structured Top Ai Network Security Company Matrix. The topics discussed in this slide are Customer Churn Rate, Palo Alto Networks, Crowdstrike. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Best Practices For Devops Security Automation
Best Practices For Devops Security AutomationThe slide highlights best practices for incorporating DevOps model into daily business operations, It include tips such as agile project management, automation, Continuous integration, security assessment etc. Presenting our set of slides with name Best Practices For Devops Security Automation. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Container Orchestration Platforms, Implement App Security Testing, Define Security Metrics.
-
 Best Practices To Secure Blockchain Networks Using Devops
Best Practices To Secure Blockchain Networks Using DevopsThe slide highlights optimal strategies to secure blockchain networks using devOps. It cover points such as testing, automated deployment pipelines, immutable infrastructure, and patch management. Presenting our set of slides with name Best Practices To Secure Blockchain Networks Using Devops. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Patch Management, Network Security And Access Control, Immutable Infrastructure.
-
 Devops Security Best Practices For Saas Application
Devops Security Best Practices For Saas ApplicationThe slide outlines DevOps security strategies for SaaS application. It cover practices such as securing IT resources, deploying firewall, vulnerability assessment along with impact. Presenting our well structured Devops Security Best Practices For Saas Application. The topics discussed in this slide are Vulnerability Assessment, Strong Password Policy, Multi Factor Authentication. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Devops Security Best Practices To Mitigate Threat
Devops Security Best Practices To Mitigate ThreatThe slide represents release management best practices for DevOps. It cover strategies such as identifying success metrics, automate CD pipeline, maintaining staging environment, review launches etc. Presenting our set of slides with name Devops Security Best Practices To Mitigate Threat. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Security, Secrets Management, Access Control, Microsoft Defender, Crowdstrike Falcon Horizon.
-
 Twitter Account Hacked Social Media Security In Powerpoint And Google Slides Cpp
Twitter Account Hacked Social Media Security In Powerpoint And Google Slides CppPresenting Twitter Account Hacked Social Media Security In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Twitter Account Hacked Social Media Security This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
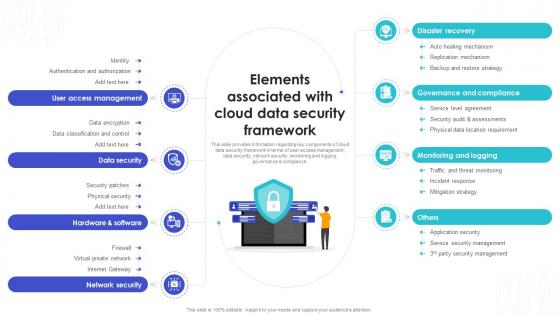 Elements Associated With Cloud Data Security Safeguarding Business With Data Loss Cybersecurity SS
Elements Associated With Cloud Data Security Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding key components of cloud data security framework in terms of user access management, data security, network security, monitoring and logging, governance and compliance.Increase audience engagement and knowledge by dispensing information using Elements Associated With Cloud Data Security Safeguarding Business With Data Loss Cybersecurity SS. This template helps you present information on eight stages. You can also present information on Disaster Recovery, User Access Management, Data Security, Network Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SS
Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding training program to ensure information security at workplace by considering focus areas such as data security and encryption, network security, incident response, etc.Deliver an outstanding presentation on the topic using this Information Security Training Program For Workforce Safeguarding Business With Data Loss Cybersecurity SS. Dispense information and present a thorough explanation of Duration, Delivery Method, Assessment, Cost, Modules using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phase 4 Of Dlp Success Focus On Proactive Security Safeguarding Business With Data Loss Cybersecurity SS
Phase 4 Of Dlp Success Focus On Proactive Security Safeguarding Business With Data Loss Cybersecurity SSThis slide provides information regarding focusing on proactive security for successful data loss prevention execution. It will include initiatives such as infiltration, exfiltration, automated protection, etc.Increase audience engagement and knowledge by dispensing information using Phase 4 Of Dlp Success Focus On Proactive Security Safeguarding Business With Data Loss Cybersecurity SS. This template helps you present information on one stages. You can also present information on Exhibited Behavior, Objective, Customization, High Risk Events using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Best Way Secure Passwords In Powerpoint And Google Slides Cpp
Best Way Secure Passwords In Powerpoint And Google Slides CppPresenting Best Way Secure Passwords In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Best Way Secure Passwords This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Security Flow Chart In Powerpoint And Google Slides Cpp
Security Flow Chart In Powerpoint And Google Slides CppPresenting Security Flow Chart In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Flow Chart. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Security Solution In Powerpoint And Google Slides Cpp
Security Solution In Powerpoint And Google Slides CppPresenting our Security Solution In Powerpoint And Google Slides Cpp PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Security Solution This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Server Security Data In Powerpoint And Google Slides Cpp
Server Security Data In Powerpoint And Google Slides CppPresenting our Server Security Data In Powerpoint And Google Slides Cpp PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Server Security Data This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Best Practices To Ensure Customer Analytics Platform Security
Best Practices To Ensure Customer Analytics Platform SecurityThe below slide provides the use of various technologies to prevent cybersecurity attacks in customer data platforms. The different practices implemented are password authentication, data encryption, etc. Introducing our Best Practices To Ensure Customer Analytics Platform Security set of slides. The topics discussed in these slides are Password Authentication, Data Encryption, Platform SecurityThis is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Ways To Secure Contactless Shopping Payments
Ways To Secure Contactless Shopping PaymentsThis slide showcases ways to ensure safe payments post-shopping. It includes encryption, tokenization and transaction limits. Introducing our premium set of slides with Ways To Secure Contactless Shopping Payments. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Encryption, Tokenization, Transaction Limits. So download instantly and tailor it with your information.
-
 Security Best Practices In Devops Icon
Security Best Practices In Devops IconIntroducing our premium set of slides with name Security Best Practices In Devops Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Security Best Practices, Devops Icon. So download instantly and tailor it with your information.
-
 Network Security Wire In Powerpoint And Google Slides CPP
Network Security Wire In Powerpoint And Google Slides CPPPresenting Network Security Wire In Powerpoint And Google Slides CPP slide which is completely adaptable. The graphics in this PowerPoint slide showcase five stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Network Security Wire. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Synthetic Biology Security In Powerpoint And Google Slides Cpp
Synthetic Biology Security In Powerpoint And Google Slides CppPresenting Synthetic Biology Security In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Synthetic Biology Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Hackers Information Security In Powerpoint And Google Slides Cpp
Hackers Information Security In Powerpoint And Google Slides CppPresenting Hackers Information Security In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Hackers Information Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Home Security Consulting In Powerpoint And Google Slides Cpp
Home Security Consulting In Powerpoint And Google Slides CppPresenting Home Security Consulting In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Home Security Consulting. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Information Security In Powerpoint And Google Slides Cpp
Information Security In Powerpoint And Google Slides CppPresenting our Information Security In Powerpoint And Google Slides Cpp PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Information Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Data Security Analysis In Powerpoint And Google Slides Cpp
Data Security Analysis In Powerpoint And Google Slides CppPresenting our Data Security Analysis In Powerpoint And Google Slides Cpp PowerPoint template design. This PowerPoint slide showcases Three stages. It is useful to share insightful information on Data Security Analysis This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Blockchain Applications To Secure Medical Records Revolutionizing Health Services With Blockchain BCT SS
Blockchain Applications To Secure Medical Records Revolutionizing Health Services With Blockchain BCT SSThis slide covers of how blockchain technology is applied in managing healthcare records such as secure and decentralized electronic health records, efficient claims adjudication,etc. Introducing Blockchain Applications To Secure Medical Records Revolutionizing Health Services With Blockchain BCT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Clinical Trials And Research, Fraud Detection And Prevention, Health Information Exchange, using this template. Grab it now to reap its full benefits.
-
 Best Practices To Implement Ethics In Data Cyber Security
Best Practices To Implement Ethics In Data Cyber SecurityThis slide represents various best practices that assist companies to implement ethics to enhance their data cybersecurity. It include various best practices such as ethical code of conduct, ethical hacking and testing, third-party ethics. Introducing our Best Practices To Implement Ethics In Data Cyber Security set of slides. The topics discussed in these slides are Best Practices, Details, Impact. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Checklist To Implement Ethics In Corporate Cyber Security
Checklist To Implement Ethics In Corporate Cyber SecurityThis slide represents checklist that assist companies to implement ethical considerations in information cyber security effectively. It includes various actions such as developing incident response plan, executing safeguard system, etc. Presenting our well structured Checklist To Implement Ethics In Corporate Cyber Security. The topics discussed in this slide are Collect Informed Consent, Data Collection, Processing. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Employee Training Schedule On Ethics In Cyber Security
Employee Training Schedule On Ethics In Cyber SecurityThis slide represents employee training schedule that assist companies to train their employee on cybersecurity ethics enhancing information protection. It includes various components such as course, details, platform, duration, rating, and deadlines. Introducing our Employee Training Schedule On Ethics In Cyber Security set of slides. The topics discussed in these slides are Course, Details, Platform. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Mitigating Ethical Challenges For Cyber Security Professional
Mitigating Ethical Challenges For Cyber Security ProfessionalThis slide represents various strategies that assist cyber security professionals to mitigate ethical challenges enhancing companies data protection. It includes various challenges such as confidentiality, threat response, network monitoring, etc. Presenting our set of slides with Mitigating Ethical Challenges For Cyber Security Professional. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Challenges, Mitigation Strategies, Confidentiality.
-
 Rationale Of Implementing Ethics In Cyber Security
Rationale Of Implementing Ethics In Cyber SecurityThis slide represents various rationales of implementing ethics that assist companies in enhancing their cybersecurity practices effectively. It includes various rationales such as protection of privacy and data, trust and reputation, etc. Introducing our premium set of slides with Rationale Of Implementing Ethics In Cyber Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Trust And Reputation, Long Term Sustainability, Protection Privacy Data. So download instantly and tailor it with your information.
-
 Strategies To Train Employees On Cyber Security Ethics
Strategies To Train Employees On Cyber Security EthicsThis slide represents various strategies that assists corporate companies to provide training on ethical cyber security for enhancing data protection. It includes strategies such as assessment and planning, establishing ethical guidelines, etc. Introducing our Strategies To Train Employees On Cyber Security Ethics set of slides. The topics discussed in these slides are Strategies, Assessment And Planning, Establish Ethical Guidelines. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.





