Powerpoint Templates and Google slides for Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Table Of Contents For Mobile Device Security For Data Protection Cybersecurity SS
Table Of Contents For Mobile Device Security For Data Protection Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Mobile Device Security For Data Protection Cybersecurity SS This template helps you present information on Five stages. You can also present information on Financial Companies, Million Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Virtual Private Network Software Comparison Mobile Device Security Cybersecurity SS
Virtual Private Network Software Comparison Mobile Device Security Cybersecurity SSThis slide showcases comparison of various VPN solutions available in market. Its key elements are mobile VPN, simultaneous connections, ratings, free trial and starting price Introducing Virtual Private Network Software Comparison Mobile Device Security Cybersecurity SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Simultaneous Connections, Free Trial, Starting Price using this template. Grab it now to reap its full benefits.
-
 Create Secure Workplace For Employee Well Being And Safety Practicing Inclusive Leadership DTE SS
Create Secure Workplace For Employee Well Being And Safety Practicing Inclusive Leadership DTE SSThis slide covers major strategies for establishing a secure workplace, such as diverse safety committee involvement, address unconscious bias, and flexible work arrangements. Introducing Create Secure Workplace For Employee Well Being And Safety Practicing Inclusive Leadership DTE SS to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Deloitte, Google, Facebook using this template. Grab it now to reap its full benefits.
-
 Firewall Monitoring Information Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Firewall Monitoring Information Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is designed to represent Firewall Audit, a crucial process for ensuring network security. With a bold and eye-catching design, this icon is perfect for presentations and documents related to network security, providing a visual representation of the importance of conducting regular audits to maintain a secure network.
-
 Firewall Monitoring Information Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Firewall Monitoring Information Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is the perfect visual representation for Firewall Audit Ensuring Network Security. It showcases the importance of conducting regular audits to ensure the safety and protection of your network. With its sleek and modern design, this icon will enhance any presentation on network security.
-
 Information Security Audit Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Information Security Audit Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentations on information security with this eye-catching PowerPoint icon. Featuring a bold and vibrant color, this icon represents the crucial aspect of information security audits. Perfect for IT professionals, consultants, and businesses looking to showcase their expertise in protecting sensitive data. Download now and make a lasting impression.
-
 Information Security Audit Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Information Security Audit Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentation with our Monotone PowerPoint icon on Information Security Audit. This sleek and professional icon represents the importance of safeguarding sensitive data and conducting thorough audits. Perfect for presentations on cyber security, compliance, and risk management. Grab your audiences attention and convey a message of security and diligence.
-
 Analyzing Cloud Based Service Offerings Best Practices To Improve Data Security
Analyzing Cloud Based Service Offerings Best Practices To Improve Data SecurityThis slide showcases various tips which can be adopted by business to enhance data security of SAAs application. It provides information regarding end to end encryption, application testing, data deletion policy and VPN. Introducing Analyzing Cloud Based Service Offerings Best Practices To Improve Data Security to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on End To End Encryption, Application Testing, Data Deletion Policy, Vpn, using this template. Grab it now to reap its full benefits.
-
 Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SS
Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SSThis slide provides glimpse about utilizing homomorphic encryption approach that can help businesses in privacy preservation. It includes stages such as encryption, computation, decryption, etc. Increase audience engagement and knowledge by dispensing information using Adopting Homomorphic Encryption To Secure Cloud Computing Implementing Digital Transformation And Ai DT SS. This template helps you present information on three stages. You can also present information on Privacy Preservation, Secure Cloud Computing, Model Owner using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SS
Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SSThis slide provides glimpse about utilizing secure multi party computation SMPC approach that can help businesses in boosting data confidentiality. It includes stages such as input sharing, secure computation, output reconstruction, etc. Increase audience engagement and knowledge by dispensing information using Incorporating Secure Multi Party Computation To Boost Data Implementing Digital Transformation And Ai DT SS. This template helps you present information on three stages. You can also present information on Increase Security Against Attacks, Boost Data Confidentiality, Input Sharing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SS
United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SSThis slide showcases the United nations and cyber security initiatives. It includes initiatives such as UN general assembly resolutions, UNODA, UNIDIR, CTC and UNODC.Increase audience engagement and knowledge by dispensing information using United Nations And Cyber Security Initiatives Strategic Guide To Implement Strategy SS. This template helps you present information on five stages. You can also present information on General Assembly Resolutions, Disarmament Affairs, Disarmament Research using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 User Based Security Training Model Strategic Guide To Implement Strategy SS
User Based Security Training Model Strategic Guide To Implement Strategy SSIntroducing User Based Security Training Model Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Compromised System, Compromised Network, Critical Assets, Exfiltrate Sensitive Data, using this template. Grab it now to reap its full benefits.
-
 Wi Fi Security To Protect Network And Connected Devices Strategic Guide To Implement Strategy SS
Wi Fi Security To Protect Network And Connected Devices Strategic Guide To Implement Strategy SSThis slide showcases the Wi-Fi security to protect network and connected devices. It includes strategies such as strong passwords, encryption, firewall and intrusion detection systems IDS and two-factor authentication 2FA.Introducing Wi Fi Security To Protect Network And Connected Devices Strategic Guide To Implement Strategy SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Two Factor Authentication, Intrusion Detection Systems, Encryption, Strong Passwords, using this template. Grab it now to reap its full benefits.
-
 Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Agenda Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Suspicious Activities And Prevent Threats, Protect Organizations Networks, Filter Out Malicious Activities, Security Devices Or Controls, using this template. Grab it now to reap its full benefits.
-
 Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing our well researched set of slides titled Icons Slide Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SS
Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SSThis slide represents the impact of outdated cybersecurity solutions on organizational operations which leads to compromised data security, data leakage, and damage to the organizations reputation. Introducing Implementing Intrusion Prevention Impact Of Inefficient Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Compromised Data Integrity, Increase In Risk Of Data Leakage, Increase In Recovery Costs, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security
Table Of Contents For Implementing Intrusion Prevention System For Effective Network SecurityIntroducing Table Of Contents For Implementing Intrusion Prevention System For Effective Network Security to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Issues Experienced Due Inefficient Network Security, Impact On Organizational Operations, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS
Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SSIntroducing Table Of Contents Implementing Intrusion Prevention System For Effective Network Security Cybersecurity SS to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Budget Plan, Impact Assessment, Dashboards, Case Study Analysis, using this template. Grab it now to reap its full benefits.
-
 Best Practices Of Effective Network Security
Best Practices Of Effective Network SecurityThis slide displays best practices for companies to deploy network security including multi factor authentication, security awareness training, and cybersecurity risk assessment. Presenting our set of slides with name Best Practices Of Effective Network Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Multi Factor Authentication, Security Awareness Training, Cybersecurity Risk Assessment.
-
 Categorize Network Security To Ensure Confidentiality
Categorize Network Security To Ensure ConfidentialityThis slide represents various types of network security to protect sensitive data including types, potential benefits and outcomes. Introducing our premium set of slides with name Categorize Network Security To Ensure Confidentiality. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Potential Benefits, Types, Outcomes. So download instantly and tailor it with your information.
-
 Cloud Based Network Security Services Icon
Cloud Based Network Security Services IconPresenting our set of slides with name Cloud Based Network Security Services Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cloud Based, Network Security Services.
-
 Corporate Network Security Minimal Protection Level
Corporate Network Security Minimal Protection LevelThis slide represents ensuring protection of network security including level, cyberthreat, and department. Introducing our Corporate Network Security Minimal Protection Level set of slides. The topics discussed in these slides are Small Businesses, Non Regulated Industries, IT Department. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 IT Network Security Audit Checklist
IT Network Security Audit ChecklistThis slide exhibits systematic assessment of security postures of organizations IT infrastructure to protect against various threats. It includdes aspects such as access control, network security measures, incident response, etc. Introducing our IT Network Security Audit Checklist set of slides. The topics discussed in these slides are Tasks, Aspects, Applicable. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Key Network Security Policies And Procedures
Key Network Security Policies And ProceduresThis slide demonstrates network security policies including access control, device control, account management, network usage and remote access policy. Presenting our set of slides with name Key Network Security Policies And Procedures. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Access Control Policy, Device Control Policy, Account Management Policy.
-
 Methods Of Cloud Data Network Security
Methods Of Cloud Data Network SecurityThis slide focuses on cloud data network security techniques including methods, strategic actions, and illustrations. Introducing our Methods Of Cloud Data Network Security set of slides. The topics discussed in these slides are Strategic Actions, Illustrations, Methods. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Monitoring Network Resources Icon For Security Incident
Monitoring Network Resources Icon For Security IncidentIntroducing our premium set of slides with name Monitoring Network Resources Icon For Security Incident. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Monitoring Network Resources, Security Incident. So download instantly and tailor it with your information.
-
 Network Security Icon For Securing Remote Access
Network Security Icon For Securing Remote AccessPresenting our set of slides with name Network Security Icon For Securing Remote Access. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Security, Securing Remote Access.
-
 Network Security Situational Awareness Flowchart
Network Security Situational Awareness FlowchartThis slide illustrates improving network security prevention and response capabilities including data collection, environmental monitoring, data extraction, operational data, etc. Introducing our premium set of slides with name Network Security Situational Awareness Flowchart. Ellicudate the one stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Collection, Environmental Monitoring, Data Extraction, Environment Assessment. So download instantly and tailor it with your information.
-
 Network Security Software Solution Tools
Network Security Software Solution ToolsThis slide covers software tools for network security to ensure adequate protection of IT infrastructure and system from various threats and vulnerabilities. It includes software, features, pricing, and rating. Introducing our Network Security Software Solution Tools set of slides. The topics discussed in these slides are Pricing, Rating, Features, Tools. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Network Security To Secure IOT Devices
Network Security To Secure IOT DevicesThis slide depicts IoT devices elements of network security including user, devices, gateway, connection, cloud, and applications. Introducing our Network Security To Secure IOT Devices set of slides. The topics discussed in these slides are Devices, Gateway, Connection, Cloud. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Protecting Sensitive Data From Network Security Threats
Protecting Sensitive Data From Network Security ThreatsThis slide highlights network security threats to protect from unauthorized access including trojan viruses, malware, and computer worms. Introducing our premium set of slides with name Protecting Sensitive Data From Network Security Threats. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Trojan Virus, Malware, Computer Worms. So download instantly and tailor it with your information.
-
 Securing Wireless Network Security Icon
Securing Wireless Network Security IconPresenting our set of slides with name Securing Wireless Network Security Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Securing Wireless, Network Security.
-
 Tools And Techniques Used In Network Security
Tools And Techniques Used In Network SecurityThis slide showcases common tools of network security used in business including Metasploit, nessus, argus, wire shark, and air crack.Introducing our premium set of slides with name Tools And Techniques Used In Network Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Metasploit, Argus, Nessus, Wireshark, Aircrack. So download instantly and tailor it with your information.
-
 Growth Hacking Icon With Security Lock
Growth Hacking Icon With Security LockPresenting our set of slides with name Growth Hacking Icon With Security Lock. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Growth hacking icon,security lock.
-
 Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS
Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide shows the cost-benefit analysis of implementing network vulnerability management strategies, including the costs incurred in end-to-end encryption and phishing awareness training, etc.Deliver an outstanding presentation on the topic using this Cost Benefit Analysis For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Costs, Benefits, Description, Initial Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS
Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide details the costs associated with deploying network vulnerability management solutions for an enterprise. It includes expenses for implementing E2E software, IT talent acquisition costs etc.Deliver an outstanding presentation on the topic using this Investment Plan For Enhancing Network Security Implementing Strategies For Mitigating Cybersecurity SS. Dispense information and present a thorough explanation of Parameters, Forecasted Budget, Actual Costs, Variance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
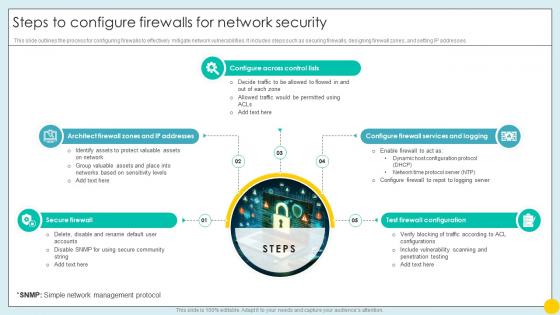 Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SS
Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SSThis slide outlines the process for configuring firewalls to effectively mitigate network vulnerabilities. It includes steps such as securing firewalls, designing firewall zones, and setting IP addresses.Increase audience engagement and knowledge by dispensing information using Steps To Configure Firewalls For Network Security Implementing Strategies For Mitigating Cybersecurity SS. This template helps you present information on five stages. You can also present information on Secure Firewall, Configure Across Control Lists, Test Firewall Configuration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data Security Incident Investigation Icon
Data Security Incident Investigation IconIntroducing our Data Security Incident Investigation Icon set of slides. The topics discussed in these slides are Data Security Incident, Investigation Icon. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Chainlink Oracle Services To Increase Security Of DEX Crypto
Chainlink Oracle Services To Increase Security Of DEX CryptoThis template presents use of chainlink by DEX crypto exchanges for improving security and introducing advanced features for development of cryptocurrency ecosystem. Introducing our premium set of slides with Chainlink Oracle Services To Increase Security Of DEX Crypto Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Financial Markets, Price Conversions, Collateral Assets So download instantly and tailor it with your information.
-
 Regular Security Audits And Patch Management B2b Ecommerce Service Challenges
Regular Security Audits And Patch Management B2b Ecommerce Service ChallengesThis slide showcases various cybersecurity management techniques implemented as security audits and patch management. This slide is designed to assist the businesses in actions taken and potential impact.Present the topic in a bit more detail with this Regular Security Audits And Patch Management B2b Ecommerce Service Challenges. Use it as a tool for discussion and navigation on Cybersecurity Management Techniques, Actions Taken, Potential Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Third Party Apis And Integration Points B2b Ecommerce Service Challenges
Securing Third Party Apis And Integration Points B2b Ecommerce Service ChallengesThis slide showcases the API security workflow and the best practices that can be implemented. The purpose is to provide insights into conducting effective authentication and authorization techniques.Deliver an outstanding presentation on the topic using this Securing Third Party Apis And Integration Points B2b Ecommerce Service Challenges. Dispense information and present a thorough explanation of Implement Access Control, Encrypt Request And Response, Authenticate And Authorize using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Online Gambling Security In Powerpoint And Google Slides Cpp
Online Gambling Security In Powerpoint And Google Slides CppPresenting our Online Gambling Security In Powerpoint And Google Slides Cpp PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Online Gambling Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Supply Chain Security Checklist To Prevent Cyber Attacks
Supply Chain Security Checklist To Prevent Cyber AttacksThis slide represents checklist that helps companies to enhance their supply chain security and prevent suppliers from potential cyberattacks effectively. It includes various parameters such as documenting supply chain security plan, conducting suppliers meeting, etc. Presenting our well structured Supply Chain Security Checklist To Prevent Cyber Attacks. The topics discussed in this slide are Supply Chain Security Plan, Network, Evaluation Processes. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Role Of Game Theory In Enhancing Cryptoeconomics Security
Role Of Game Theory In Enhancing Cryptoeconomics SecurityThe purpose of this slide is to show how integrating game theory with crypto economics increases fund security. It covers three key elements such as parameters, role and impact. Presenting our set of slides with name Role Of Game Theory In Enhancing Cryptoeconomics Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Parameter, Role, Impact.
-
 Asymmetric Data Encryption For Secure Communication
Asymmetric Data Encryption For Secure CommunicationThe purpose of this slide is to elucidate how asymmetric data encryption enhances secure communication through the use of key pairs. It ensures robust protection against unauthorized access and interception. Introducing our Asymmetric Data Encryption For Secure Communication set of slides. The topics discussed in these slides are Device, Securing, Communication Channels, Cloud Server. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Cloud Encryption Essentials For Robust Data Security
Cloud Encryption Essentials For Robust Data SecurityThe purpose of this slide is to highlight how cloud encryption essentials bolster robust data security. It safeguard sensitive information stored in cloud environments through cryptographic techniques. Presenting our set of slides with name Cloud Encryption Essentials For Robust Data Security. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Insider Threat Defense, Secure Data Transfers, Organizational Integrity.
-
 Data Encryption Algorithms For Security Solutions
Data Encryption Algorithms For Security SolutionsThe purpose of this slide is to demonstrate how data encryption algorithms for security solutions enhance protection. It encode data to prevent unauthorized access or manipulation. Introducing our Data Encryption Algorithms For Security Solutions set of slides. The topics discussed in these slides are Advanced Encryption Standard, Rivest Shamir Adleman, Elliptic Curve Cryptography. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Data Encryption Icon For Secure Messaging
Data Encryption Icon For Secure MessagingPresenting our set of slides with name Data Encryption Icon For Secure Messaging. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Data Encryption Icon, Secure Messaging.
-
 Data Encryption Working Model For Security
Data Encryption Working Model For SecurityThe purpose of this slide is to elucidate how data encryption working model for security offers insight into safeguarding sensitive data through encryption mechanisms. It helps thwart unauthorized access or breaches. Introducing our Data Encryption Working Model For Security set of slides. The topics discussed in these slides are Sender, Plaintext, Ciphertext. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Strategies To Implement Encryption Trends In Data Security
Strategies To Implement Encryption Trends In Data SecurityThe purpose of this slide is to guide and inform on effective strategies for implementing encryption trends in data security. It provides actionable insights to enhance data protection and address evolving cyber threats. Introducing our Strategies To Implement Encryption Trends In Data Security set of slides. The topics discussed in these slides are Biometric Authentication, Multi-Factor Authentication, Cloud Encryption, Blockchain Encryption. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Computer Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Network Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your SEO and web security with our eye-catching PowerPoint icon. Featuring vibrant colours and a sleek design, this icon represents the importance of managing cyber security while optimizing your website for search engines. Perfect for presentations and training materials, its a must-have for any business or individual focused on online success.
-
 Computer Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Network Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is a must-have for any presentation on SEO and web cyber security management. With a sleek and professional design, it conveys the importance of protecting your online presence. Use it to enhance your slides and emphasize the crucial role of security in todays digital landscape.
-
 Computer Security Data Protection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Security Data Protection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentations on cyber risk management with our vibrant Computer Security PowerPoint icon. This eye-catching icon features a lock symbol in bold colors, representing the importance of safeguarding your data and systems. Perfect for showcasing the importance of cyber security in todays digital age.
-
 Computer Security Data Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Computer Security Data Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents the importance of computer security in cyber risk management. It is a visual representation of the need for safeguarding sensitive information and protecting against potential cyber threats. Use this icon to enhance presentations on cyber security and emphasize the significance of risk management in the digital world.
-
 Cyber Vehicle Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Vehicle Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon is designed to represent incident response in automotive cyber security. With a vibrant and eye-catching design, it is perfect for use in presentations, reports, and other materials related to this topic. The icon is sure to enhance the visual appeal and effectiveness of your content.
-
 Cyber Vehicle Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Vehicle Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon is the perfect visual aid for presentations on incident response in automotive cyber security. With its sleek and modern design, it effectively conveys the importance of protecting vehicles from cyber attacks. Use it to educate and inform audiences about the crucial role of incident response in the automotive industry.
-
 Gear Electronic Cyber Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Gear Electronic Cyber Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentations on cyber security with our eye-catching coloured PowerPoint icon. Representing the crucial aspect of monitoring and management, this icon is perfect for showcasing the importance of safeguarding your digital assets. With its vibrant colours and sleek design, it will capture your audiences attention and add a professional touch to your slides.
-
 Gear Electronic Cyber Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Gear Electronic Cyber Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon features a sleek and modern design, perfect for presentations on cyber security monitoring and management. With its bold lines and minimalist style, it conveys a sense of professionalism and expertise in the field. Use it to enhance your slides and effectively communicate your message on this crucial topic.
-
 Agroecology And Food Security In Powerpoint And Google Slides Cpp
Agroecology And Food Security In Powerpoint And Google Slides CppPresenting Agroecology And Food Security In Powerpoint And Google Slides Cpp slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Agroecology And Food Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Value Investing Checklist To Manage Securities
Value Investing Checklist To Manage SecuritiesThis slide showcases stock marketers value investment checklist. It includes steps to look out such as fundamental analysis, analyse financial reports, ratio analysis and final evaluation. Presenting our well structured Value Investing Checklist To Manage Securities The topics discussed in this slide are Investment Option, Real Estate AssetsThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.





