Powerpoint Templates and Google slides for Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Email Security Risks And Mitigation Plan
Email Security Risks And Mitigation PlanThis slide covers email security risks and its mitigation plan which includes risks such as phishing, evolving phishing, domain squatting and malware. Presenting our set of slides with Email Security Risks And Mitigation Plan. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Email Security, Risks, Mitigation Plan.
-
 Filter Spam Detection In Email Security
Filter Spam Detection In Email SecurityThis slide explains the process of filter spam detection which includes red flag analysis, bad IP address, poor domain reputation, bulk sending and suspicious languages. Introducing our premium set of slides with Filter Spam Detection In Email Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Flag Analysis, IP Address, Bulk Sending. So download instantly and tailor it with your information.
-
 Icon For Email Security And Spam Protection
Icon For Email Security And Spam ProtectionPresenting our set of slides with Icon For Email Security And Spam Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon, Email Security, Spam Protection.
-
 Icon For Email Security Threats And Attacks
Icon For Email Security Threats And AttacksIntroducing our premium set of slides with Icon For Email Security Threats And Attacks. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon, Email Security, Threats And Attacks. So download instantly and tailor it with your information.
-
 Objectives Of Email Security Filter Techniques
Objectives Of Email Security Filter TechniquesThis slide provides an outline of objectives of email security filter techniques which include stop spam by filtering out spammers, allow legitimate emails, etc. Presenting our set of slides with Objectives Of Email Security Filter Techniques. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Stop Spam, Control, Emails.
-
 Primary Protocols Used In Email Security
Primary Protocols Used In Email SecurityThis slide is an overview of different protocols used in email security which includes simple mail transfer protocol secure and sender policy framework. Introducing our premium set of slides with Primary Protocols Used In Email Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Mail Transfer, Policy Framework, Layer Security. So download instantly and tailor it with your information.
-
 Prime Responses In Sender Policy Framework Of Email Security
Prime Responses In Sender Policy Framework Of Email SecurityThis slide is an overview of different responses under sender policy framework with descriptions and include pass, hard fail, soft fail, none and neutral. Presenting our set of slides with Prime Responses In Sender Policy Framework Of Email Security. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Prime Responses, Sender Policy Framework, Email Security.
-
 Recent Trends In Email Security Attacks
Recent Trends In Email Security AttacksThis slide is an outline of infographics on recent trends in email security attacks and gives statistical information on malicious files distributed by email. Presenting our well structured Recent Trends In Email Security Attacks. The topics discussed in this slide are Recent Trends, Email Security Attacks. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Methods For Implementing Email Encryption
Security Methods For Implementing Email EncryptionThis slide outlines the security methods for implementing email encryption which includes encrypted PDFs secure attachments, web portal encryption, etc. Introducing our premium set of slides with Security Methods For Implementing Email Encryption. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Secure Attachments, Web Portal, Gateway Software. So download instantly and tailor it with your information.
-
 Trending Email Security Best Practices
Trending Email Security Best PracticesThis slide outlines best practices followed in email security which includes use strong passwords, use proxies, regularly back up files and keep software updated. Presenting our set of slides with Trending Email Security Best Practices. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Trending Email Security, Best Practices.
-
 Types Of Filter Spam In Email Security
Types Of Filter Spam In Email SecurityThis slide outlines different types of email filter spam which includes content filter, block list filter, header filter, language and rule based filter and Bayesian filter. Introducing our premium set of slides with Types Of Filter Spam In Email Security. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Types, Filter Spam, Email Security. So download instantly and tailor it with your information.
-
 Types Of Filtering Techniques In Email Security
Types Of Filtering Techniques In Email SecurityThis slide provides an outline of types of filtering techniques used in email security such as reputation-based email filters, safe listing and grey listing. Presenting our set of slides with Types Of Filtering Techniques In Email Security. This exhibits information on two stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Types, Filtering Techniques, Email Security.
-
 IoT Cloud Features Icon For Ensuring Global Security
IoT Cloud Features Icon For Ensuring Global SecurityIntroducing our IoT Cloud Features Icon For Ensuring Global Security set of slides. The topics discussed in these slides are Iot Cloud Features, Icon, Ensuring Global Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 IoT Security Features For Network Management
IoT Security Features For Network ManagementThis slide covers IoT security features introduced in PAN-OS 11.0 with an aim to protect connected devices and network in IoT system. Presenting our set of slides with IoT Security Features For Network Management. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Policy Rule, Traffic Visibility, Alto Networks.
-
 Bitcoin Crypto Wallet Security Icon
Bitcoin Crypto Wallet Security IconPresenting our set of slides with name Bitcoin Crypto Wallet Security Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Bitcoin Crypto, Wallet Security Icon.
-
 Crypto Wallet Security And Best Practices
Crypto Wallet Security And Best PracticesThis slide outlines the crypto wallet security and best practices which include choose a secure wallet, use strong passwords, regular wallet backups, etc. Presenting our set of slides with name Crypto Wallet Security And Best Practices. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Crypto Wallet, Security And Best Practices, Regular Wallet Backups.
-
 Data Analytics And Integration Security Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Data Analytics And Integration Security Colored Icon In Powerpoint Pptx Png And Editable Eps FormatEnhance your presentations with our vibrant PowerPoint icon on big data storage solutions. This eye-catching icon features a bold color scheme and represents the latest advancements in data storage technology. Perfect for showcasing your expertise in big data management and storage solutions.
-
 Data Analytics And Integration Security Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Data Analytics And Integration Security Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone powerpoint icon represents the efficient and reliable storage solutions for big data. With its sleek design and bold color, it conveys the message of simplicity and effectiveness in managing large volumes of data. Perfect for presentations on data storage and management in the modern era.
-
 Implement Robust Security Measures Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Implement Robust Security Measures Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured PowerPoint icon features a powerful and secure lock symbol, representing the implementation of robust security measures for big data platforms. It is perfect for presentations and documents related to data security, providing a visual representation of the importance of protecting sensitive information.
-
 Implement Robust Security Measures Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Implement Robust Security Measures Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis monotone PowerPoint icon represents the implementation of robust security measures for big data platforms. It is designed to convey the importance of protecting sensitive data in a professional and efficient manner. With its clean and simple design, it is perfect for use in presentations, reports, and other materials related to big data security.
-
 Existing IT Security Strategic Implementation Of Regression Testing
Existing IT Security Strategic Implementation Of Regression TestingThis slide highlights the components of the current IT security infrastructure, which are prone to several functionality concerns. These constituents are vulnerability scanners, improper functioning, functional disrupt, and so on. Deliver an outstanding presentation on the topic using this Existing IT Security Strategic Implementation Of Regression Testing. Dispense information and present a thorough explanation of Existing IT Security, Infrastructure Constituents using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
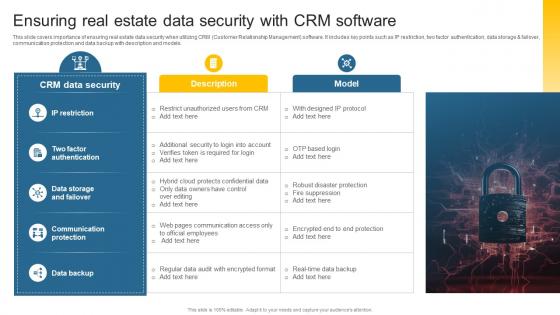 Ensuring Real Estate Data Security With CRM Leveraging Effective CRM Tool In Real Estate Company
Ensuring Real Estate Data Security With CRM Leveraging Effective CRM Tool In Real Estate CompanyThis slide covers importance of ensuring real estate data security when utilizing CRM Customer Relationship Management software. It includes key points such as IP restriction, two factor authentication, data storage and failover, communication protection and data backup with description and models. Introducing Ensuring Real Estate Data Security With CRM Leveraging Effective CRM Tool In Real Estate Company to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Data Storage And Failover, Communication Protection, Data Backup, using this template. Grab it now to reap its full benefits.
-
 30 60 90 Day Plan For Cyber Security Framework Implementation
30 60 90 Day Plan For Cyber Security Framework ImplementationThis slide discusses the 30-60-90-day plan for cyber security framework implementation which include stakeholder alignment, awareness training and so on. Introducing 30 60 90 Day Plan For Cyber Security Framework Implementation to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Stakeholder Alignment, Conduct Initial Gap Analysis, Conduct Awareness Training, using this template. Grab it now to reap its full benefits.
-
 Agenda For Cyber Security Frameworks
Agenda For Cyber Security FrameworksIncrease audience engagement and knowledge by dispensing information using Agenda For Cyber Security Frameworks. This template helps you present information on five stages. You can also present information on Cyber Security Frameworks, Benefits And Components, Response Functions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Before Vs After Of Cyber Security Framework Implementation
Before Vs After Of Cyber Security Framework ImplementationThis slide discusses the before vs after impact of cyber security framework implementation based on aspects like security posture, incident response, etc. Present the topic in a bit more detail with this Before Vs After Of Cyber Security Framework Implementation. Use it as a tool for discussion and navigation on Incident Response, Cyber Security, Framework Implementation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Center For Internet Security Control Framework
Center For Internet Security Control FrameworkThis slide overviews the CIS Control framework which includes three major categories that are basic controls, foundational controls and organizational controls. Introducing Center For Internet Security Control Framework to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Foundational Controls, Organizational Controls, Internet Security, Control Framework , using this template. Grab it now to reap its full benefits.
-
 Cyber Security Framework Common Patterns Of Use
Cyber Security Framework Common Patterns Of UseThis slide highlights the cyber security framework common patterns of use in an organization which include integrate functions, optimize risk management, etc. Increase audience engagement and knowledge by dispensing information using Cyber Security Framework Common Patterns Of Use. This template helps you present information on five stages. You can also present information on Cyber Security Framework, Integrate Functions, Optimize Risk Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Framework Implementation Budget
Cyber Security Framework Implementation BudgetThis slide discusses the implementation budget for cyber security framework which includes compliance requirements, risk assessments and security training. Deliver an outstanding presentation on the topic using this Cyber Security Framework Implementation Budget. Dispense information and present a thorough explanation of Compliance Requirements, Risk Assessments, Security Training, Security Requirements For Business Initiatives using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Security Framework Implementation Challenges
Cyber Security Framework Implementation ChallengesThis slide discusses the major challenges of cyber security framework implementation which include budget constraints, lack of integration and so on. Introducing Cyber Security Framework Implementation Challenges to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Insufficiently Trained Personnel, Budget Constraints, Cyber Security Framework, Implementation Challenges, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Framework Training Schedule
Cyber Security Framework Training ScheduleThis slide outlines the schedule for training for cyber security frameworks which include foundation and planning, policy development and training kickoff, etc. Present the topic in a bit more detail with this Cyber Security Framework Training Schedule. Use it as a tool for discussion and navigation on Foundation And Planning, Policy Development, Training Kickoff, Incident Response Finalization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Frameworks For Table Of Contents
Cyber Security Frameworks For Table Of ContentsDeliver an outstanding presentation on the topic using this Cyber Security Frameworks For Table Of Contents. Dispense information and present a thorough explanation of Cyber Security Frameworks, Benefits, Applications, Challenges, Mitigation Plan using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Different Categories Of Cobit Cyber Security Framework
Different Categories Of Cobit Cyber Security FrameworkThis slide discusses the different categories of COBIT which includes plan and organize, acquire and implement, deliver and support, monitor and evaluate, etc. Increase audience engagement and knowledge by dispensing information using Different Categories Of Cobit Cyber Security Framework. This template helps you present information on five stages. You can also present information on Acquire And Implement, Monitor And Evaluate, Plan And Organize, Cyber Security Framework using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Distinct Types Of Cyber Security Frameworks
Distinct Types Of Cyber Security FrameworksThis slide discusses the different types of cyber security framework which includes control frameworks, program frameworks and risk frameworks. Introducing Distinct Types Of Cyber Security Frameworks to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Control Frameworks, Program Frameworks, Risk Frameworks, Cyber Security Frameworks, using this template. Grab it now to reap its full benefits.
-
 Essential Components Of Cyber Security Frameworks
Essential Components Of Cyber Security FrameworksThis slide highlights the key components of cyber security framework which includes framework core, implementation tiers, profiles and so on. Introducing Essential Components Of Cyber Security Frameworks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Framework Core, Implementation Tiers, Guides Vulnerability Reduction , using this template. Grab it now to reap its full benefits.
-
 Identify Function Activities In Cyber Security Framework
Identify Function Activities In Cyber Security FrameworkThis slide is an introduction to the key activities of identify function in cyber security framework which includes identify physical and software assets. Increase audience engagement and knowledge by dispensing information using Identify Function Activities In Cyber Security Framework. This template helps you present information on five stages. You can also present information on Identify Physical And Software Assets, Assess Asset Vulnerabilities, Conduct Risk Response Activities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Introduction To Cobit Cyber Security Framework
Introduction To Cobit Cyber Security FrameworkThis slide gives an overview of COBIT cyber security framework which provides principles, practices, tools and model to aligning IT strategies with objectives. Introducing Introduction To Cobit Cyber Security Framework to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Emphasizes Risk Management, Cyber Security Framework, Optimizing IT Performance, using this template. Grab it now to reap its full benefits.
-
 Introduction To Cyber Security Frameworks Series
Introduction To Cyber Security Frameworks SeriesThis slide gives an overview to cyber security framework and defines it as a set of documents with guidelines and best practices used for risk management. Increase audience engagement and knowledge by dispensing information using Introduction To Cyber Security Frameworks Series. This template helps you present information on five stages. You can also present information on Organizations Security Methodologies, Used For Risk Management, Guidelines And Best Practices using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Iso 27000 Series In Cyber Security Framework
Iso 27000 Series In Cyber Security FrameworkThis slide highlights the ISO 27000 series in cyber security framework which comprises 60 standards addressing various information security issues. Introducing Iso 27000 Series In Cyber Security Framework to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Focuses On Cloud Computing, Protection Of Digital Evidence, Deals With Storage Security, Security In Healthcare, using this template. Grab it now to reap its full benefits.
-
 Iso 27001 And 27002 Cyber Security Frameworks
Iso 27001 And 27002 Cyber Security FrameworksThis slide discusses the concept of two major cyber security frameworks which are ISO 27001 and ISO 27002 following code of practice. Increase audience engagement and knowledge by dispensing information using Iso 27001 And 27002 Cyber Security Frameworks. This template helps you present information on three stages. You can also present information on Code Of Practice, Detailed Security Controls, Systematic Approach To Risk Assessment
-
 Main Applications Of Cyber Security Framework
Main Applications Of Cyber Security FrameworkThis slide outlines the main applications of cyber security framework which includes enhance cybersecurity program, prioritize improvement tasks, etc. Introducing Main Applications Of Cyber Security Framework to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Enhance Cybersecurity Program, Prioritize Improvement Tasks, Know Security Status, Guide Investment Decisions, using this template. Grab it now to reap its full benefits.
-
 Main Components Of Cobit Framework In Cyber Security
Main Components Of Cobit Framework In Cyber SecurityThis slide gives an overview of key components of COBIT which includes process descriptions, control objectives, maturity models and management guidelines. Increase audience engagement and knowledge by dispensing information using Main Components Of Cobit Framework In Cyber Security. This template helps you present information on five stages. You can also present information on Process Descriptions, Maturity Models, Management Guidelines, Control Objectives using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Mitigation Plan For Cyber Security Frameworks
Mitigation Plan For Cyber Security FrameworksThis slide depicts the mitigation plan for cyber security frameworks which include identify and prioritize vulnerabilities, allocate budget and skilled personnel. Increase audience engagement and knowledge by dispensing information using Mitigation Plan For Cyber Security Frameworks. This template helps you present information on five stages. You can also present information on Cyber Security Frameworks, Prioritize Vulnerabilities, Allocate Budget, Skilled Personnel using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Need For Implementing Cyber Security Framework
Need For Implementing Cyber Security FrameworkThis slide highlights the need for implementing cyber security framework which includes easily adaptable and cost efficient, collaboration opportunities, etc. Introducing Need For Implementing Cyber Security Framework to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Collaboration Opportunities, Easily Maintain Compliance, Secure Supply Chain, using this template. Grab it now to reap its full benefits.
-
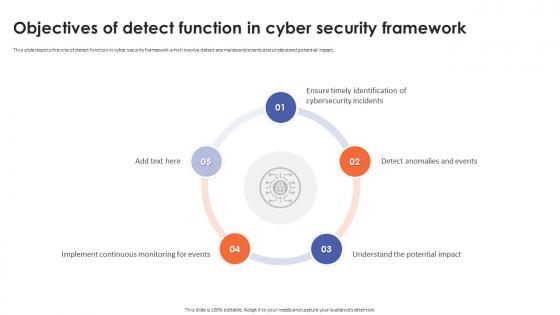 Objectives Of Detect Function In Cyber Security Framework
Objectives Of Detect Function In Cyber Security FrameworkThis slide depicts the role of detect function in cyber security framework which involve detect anomalies and events and understand potential impact. Introducing Objectives Of Detect Function In Cyber Security Framework to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Implement Continuous Monitoring For Events, Understand The Potential Impact, Detect Anomalies And Events, using this template. Grab it now to reap its full benefits.
-
 Overview Of Coso Cyber Security Framework
Overview Of Coso Cyber Security FrameworkThis slide gives an overview of COSO cyber security framework based on key components such as control environment, risk assessment and management. Increase audience engagement and knowledge by dispensing information using Overview Of Coso Cyber Security Framework. This template helps you present information on six stages. You can also present information on Control Environment, Risk Assessment And Management, Control Activities, Information And Communications using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Parameters Of Cobit Framework In Cyber Security
Parameters Of Cobit Framework In Cyber SecurityThis slide highlights the two main parameters of COBIT in cyber security framework which includes control and IT Control objective. Introducing Parameters Of Cobit Framework In Cyber Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Guides Practices And Policies, Ensures Goal Achievement Assurance, Framework In Cyber Security, using this template. Grab it now to reap its full benefits.
-
 Primary Benefits Of Cyber Security Framework
Primary Benefits Of Cyber Security FrameworkThis slide represents the key benefits of cyber security framework which include meet contractual obligations, quantifiable enhancements in security, etc. Increase audience engagement and knowledge by dispensing information using Primary Benefits Of Cyber Security Framework. This template helps you present information on five stages. You can also present information on Meet Contractual Obligations, Cyber Security Framework, Maturity And Effectiveness Of Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Purpose Of Response Function In Cyber Security Framework
Purpose Of Response Function In Cyber Security FrameworkThis slide highlights the functions of response in cyber security framework which includes execute response plans, manage communications, analyze incidents, etc. Introducing Purpose Of Response Function In Cyber Security Framework to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Prevent Event Expansion, Coordinate Communications, Cyber Security Framework, using this template. Grab it now to reap its full benefits.
-
 Recovery Function In Cyber Security Framework
Recovery Function In Cyber Security FrameworkThis slide gives an overview of role of recovery function which includes implement recovery plans, improve strategies and coordinate communications. Increase audience engagement and knowledge by dispensing information using Recovery Function In Cyber Security Framework. This template helps you present information on four stages. You can also present information on Coordinate Communications, Implement Recovery Plans, Cyber Security Framework using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Reference Architecture For Next Generation Cyber Security Framework
Reference Architecture For Next Generation Cyber Security FrameworkThis slide illustrates the reference architecture for next generation cyber security framework which includes identity management, user interface, etc. Deliver an outstanding presentation on the topic using this Reference Architecture For Next Generation Cyber Security Framework. Dispense information and present a thorough explanation of Reference Architecture, Cyber Security Framework, Identity Management, Context Repository using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Role Of Protect Function In Cyber Security Framework
Role Of Protect Function In Cyber Security FrameworkThis slide gives an outline of role of protect function in cyber security framework which controls identity management and secure resources. Introducing Role Of Protect Function In Cyber Security Framework to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Security Awareness Training, Data Security With Risk Strategy, Maintain Information System Protections, using this template. Grab it now to reap its full benefits.
-
 Table Of Contents For Cyber Security Frameworks
Table Of Contents For Cyber Security FrameworksIncrease audience engagement and knowledge by dispensing information using Table Of Contents For Cyber Security Frameworks. This template helps you present information on seven stages. You can also present information on Types Of Frameworks, Training And Budget, Execution Plan, Cyber Security Frameworks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Vital Functions Of Cyber Security Framework
Vital Functions Of Cyber Security FrameworkThis slide gives an overview of the vital functions of cyber security framework which includes identify, protect, detect and respond. Introducing Vital Functions Of Cyber Security Framework to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Recognizes Cybersecurity Incidents, Potential Threats, Structured Cybersecurity Approach, using this template. Grab it now to reap its full benefits.
-
 Network Security Breach Incident Report
Network Security Breach Incident ReportThe slide serves as a detailed overview, guiding the audience through the incidents context, impact, and the organizations proactive measures and future steps to address the security breach and protect customer privacy. Presenting our well structured Network Security Breach Incident Report. The topics discussed in this slide are Network Security Breach, Incident Report. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Comparative Analysis Of Information Security System Software
Comparative Analysis Of Information Security System SoftwareThis slide mentions software comparison chart for information security system to identify threat easily and manage risk. It involves comparison on basis of business size, features, free trial, price and ratings. Presenting our well structured Comparative Analysis Of Information Security System Software. The topics discussed in this slide are Rating, Tools, Business Size. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Information Security System Icon For Business Management
Information Security System Icon For Business ManagementIntroducing our premium set of slides with Information Security System Icon For Business Management. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Security System, Business Management. So download instantly and tailor it with your information.
-
 Roadmap For Robust Information Security System Plan
Roadmap For Robust Information Security System PlanThis slide highlights roadmap for a strategic information system plan to manage threats and to avoid misuse of critical information of business. Presenting our set of slides with Roadmap For Robust Information Security System Plan. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Build Strong Recovery Plan, Manage Data, Assess Risk.
-
 Website Penetration Testing Techniques For Cyber Security
Website Penetration Testing Techniques For Cyber SecurityThis slide covers two major techniques of website penetration testing. It provides overview of both techniques on the basis of their functionality, testing approach and tools. Introducing our premium set of slides with Website Penetration Testing Techniques For Cyber Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Functionality, Testing Approach, Tools. So download instantly and tailor it with your information.
-
 Website Security Risks And Penetration Testing Report
Website Security Risks And Penetration Testing ReportThis template showcases advanced penetration testing report for organization website. It covers factors such as vulnerabilities, severity and risk level. Presenting our well structured Website Security Risks And Penetration Testing Report. The topics discussed in this slide are Website Security Risks, Penetration Testing Report. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Strategies For Implementing AI Powered Global Technology In Cyber Security
Strategies For Implementing AI Powered Global Technology In Cyber SecurityThis slide shows strategic approaches for implementing AI in cyber security. The purpose of this slide is to strengthen organizations defence against potential cyber attacks to maximize effectiveness of global technological solutions. It covers strategies such as resource allocation, training data, internal processes, etc. Presenting our set of slides with Strategies For Implementing AI Powered Global Technology In Cyber Security. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Resource Allocation, Training Data, Internal Processes.





