Powerpoint Templates and Google slides for Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Internal Architecture Of Web Services Security
Internal Architecture Of Web Services SecurityThis slide lays out framework for web services security. The purpose of this slide is to help businesses in modeling security agents regarding authentication and authorization provided by web container. It covers components such as token service, provider plugin, client interface, etc. Presenting our well structured Internal Architecture Of Web Services Security The topics discussed in this slide are Provider Plugin, Web Security Service Client, Web Security Service Provider This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Solutions To Overcome Website Security Audit Challenges
Solutions To Overcome Website Security Audit ChallengesThis template showcases solutions and technological stack to overcome challenges faced by organizations while conducting website security audit. The purpose of this slide is to help organizations streamline auditing process for maintaining data authenticity. It covers tools and strategies to reduce web security risks such as injections, broken authentication, and data exposure. Introducing our Solutions To Overcome Website Security Audit Challenges set of slides. The topics discussed in these slides are Challenges, Solutions This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Steps To Conduct Website Security Audit
Steps To Conduct Website Security AuditThis slide showcases website security audit process. The purpose of this slide is to ensure website safety by conducting deep analysis of server setups, application software and network configurations. It covers steps such as scoping, vulnerability assessment, penetration testing, risk assessment, remediation and monitoring. Presenting our set of slides with Steps To Conduct Website Security Audit This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Scoping, Penetration Testing, Remediation
-
 Techniques To Achieve Web Application Security
Techniques To Achieve Web Application SecurityThis slide showcases approaches to ensure web application security. The purpose of this slide is to help businesses in protecting their data against cyber attacks. It covers techniques such as utilizing heuristic detection, implementing cybersecurity framework, adopting secure software development practices, etc. Introducing our premium set of slides with Techniques To Achieve Web Application Security Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Utilize Heuristic Detection, Implement Cybersecurity Framework, Security Measures So download instantly and tailor it with your information.
-
 Types Of Web Security Technologies To Prevent Cyber Threats
Types Of Web Security Technologies To Prevent Cyber ThreatsThis slide covers various types of web security technologies. The purpose of this slide is to help businesses in preventing cyber threats to ensure business protection and compliance. It covers technologies such as web application firewalls, vulnerability scanners, password cracking technologies, etc. Presenting our set of slides with Types Of Web Security Technologies To Prevent Cyber Threats This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Web Application Firewalls, Vulnerability Scanners, Password Cracking Technologies
-
 Web Application Firewall Icon For Application Security
Web Application Firewall Icon For Application SecurityPresenting our well structured Web Application Firewall Icon For Application Security The topics discussed in this slide are Web Application Firewall Icon, Application Security This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Web Application Security Checklist Icon
Web Application Security Checklist IconIntroducing our premium set of slides with Web Application Security Checklist Icon Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Web Application Security Checklist Icon So download instantly and tailor it with your information.
-
 Web Security Audit Controls To Reduce Threats
Web Security Audit Controls To Reduce ThreatsThis slide represents various security control methods to minimize threats to web security. The purpose of this slide is to help businesses in developing strategy for data protection. It provides techniques to minimize web security threats such as SQL injection, ransomware, denial of service attacks and phishing. Introducing our Web Security Audit Controls To Reduce Threats set of slides. The topics discussed in these slides are Ransomware, Service Attacks, Phishing This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Web Security Icon To Prevent Cyber Attacks
Web Security Icon To Prevent Cyber AttacksPresenting our set of slides with Web Security Icon To Prevent Cyber Attacks This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Web Security Icon, Prevent Cyber Attacks
-
 Web Security Principles For Software Development Companies
Web Security Principles For Software Development CompaniesThis template covers four principles of web security followed by well established software development businesses. The purpose of this slide is to streamline business operations by preventing hackers from data manipulation. It includes principles such as authentication, confidentiality, integrity and availability. Introducing our premium set of slides with Web Security Principles For Software Development Companies Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Confidentiality, Authentication, Integrity So download instantly and tailor it with your information.
-
 Web Security Solutions For SQL Injection Attacks
Web Security Solutions For SQL Injection AttacksThis template presents solutions to tackle web security issue of SQL injection attacks. The purpose of this slide is to help businesses in managing and securing information stored in SQL database. It covers illustration of SQL injection attack and its web security solutions such as restricting searches, setting legitimate format, performing data validation, etc. Introducing our Web Security Solutions For SQL Injection Attacks set of slides. The topics discussed in these slides are Creates Profile, Web Server, Processes Malicious Commands This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Web Security Solutions To Prevent Misconfiguration Related Issues
Web Security Solutions To Prevent Misconfiguration Related IssuesThis slide covers solutions to prevent issues related with website configuration. The purpose of this slide is to help organizations in securing their networks and web applications safe from cyberthreats. It covers solutions such as verifying security procedures, updating software and hardware policies, conducting regular audits, etc. Presenting our well structured Web Security Solutions To Prevent Misconfiguration Related Issues The topics discussed in this slide are Verify Security Procedures, Conduct Regular Audits, Change Login Information This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Web Security Solutions To Prevent XSS Attacks
Web Security Solutions To Prevent XSS AttacksThis template presents various tips to minimize cross site scripting attacks. The purpose of this slide is to help businesses in preventing malicious executions and patching vulnerabilities. It covers web security solutions such as checking client side inputs, using firewall configurations, utilizing content security policy an updating software. Presenting our set of slides with Web Security Solutions To Prevent XSS Attacks This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Client Side Inputs, Firewall Configuration, Content Security Policy
-
 Web Security Vulnerabilities And Their Prevention Strategies
Web Security Vulnerabilities And Their Prevention StrategiesThis slide covers common web security pitfalls and their mitigation strategies. The purpose of this slide is to help businesses in minimizing web related IT security pitfalls. It covers various prevention strategies to address web security vulnerabilities such as injection flaws, broken authentication, cross site scripting and security misconfiguration. Introducing our premium set of slides with Web Security Vulnerabilities And Their Prevention Strategies Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Injection Flaws, Broken Authentication, Cross Site Scripting So download instantly and tailor it with your information.
-
 Agenda Internet Of Things IoT Security Ppt Ideas Background Images Cybersecurity SS
Agenda Internet Of Things IoT Security Ppt Ideas Background Images Cybersecurity SSIntroducing Agenda Internet Of Things IoT Security Ppt Ideas Background Images Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Businesses Worldwide, Implementing Strategies, Threat Intelligence, using this template. Grab it now to reap its full benefits.
-
 Apply Authentication And Access Control Mechanisms Internet Of Things IoT Security Cybersecurity SS
Apply Authentication And Access Control Mechanisms Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of authentication and access control for internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about trust boundaries, identity authentication, etc. Increase audience engagement and knowledge by dispensing information using Apply Authentication And Access Control Mechanisms Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on three stages. You can also present information on Trust Boundaries, Identity Authentication, Access Protection Measures using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Arm Based IoT Cyber Security Framework Internet Of Things IoT Security Cybersecurity SS
Arm Based IoT Cyber Security Framework Internet Of Things IoT Security Cybersecurity SSPresent the topic in a bit more detail with this Arm Based IoT Cyber Security Framework Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on Management, Service Organization, Communication, Cyber Security Framework. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Comparative Analysis Of IoT Security Software Internet Of Things IoT Security Cybersecurity SS
Comparative Analysis Of IoT Security Software Internet Of Things IoT Security Cybersecurity SSThis slide showcases comparative analysis for internet of things IoT security tools. It provides details about secure cryptographic key provisioning, identity, access and relationship management, IoT device provisioning, etc. Deliver an outstanding presentation on the topic using this Comparative Analysis Of IoT Security Software Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Comparative Analysis, IoT Security Software, IoT Device Provisioning, Secure Cryptographic using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Create Continuous Update And Deployment Mechanisms Internet Of Things IoT Security Cybersecurity SS
Create Continuous Update And Deployment Mechanisms Internet Of Things IoT Security Cybersecurity SSThis slide showcases comparative analysis for internet of things IoT security tools. It provides details about secure cryptographic key provisioning, identity, access and relationship management, IoT device provisioning, etc. Introducing Create Continuous Update And Deployment Mechanisms Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Secure Deployment, Cryptographic Protocols, Automated Security Update Deployment, Monitoring And Response Mechanisms, using this template. Grab it now to reap its full benefits.
-
 Current IoT Security Business Challenges Internet Of Things IoT Security Cybersecurity SS
Current IoT Security Business Challenges Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security challenges faced by businesses. It provides details about IoT malware and ransomware, user privacy risks, insecure interfaces, remove work environments, etc. Deliver an outstanding presentation on the topic using this Current IoT Security Business Challenges Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of IoT Security Business Challenges, Internet Of Things, IoT Malware And Ransomware, User Privacy Risks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cybersecurity Team Organizational Chart For IoT Internet Of Things IoT Security Cybersecurity SS
Cybersecurity Team Organizational Chart For IoT Internet Of Things IoT Security Cybersecurity SSThis slide showcases cybersecurity team hierarchy chart specific for internet of things IoT operations. It provides details about CEO, CISO, director, manager, security engineer, etc. Present the topic in a bit more detail with this Cybersecurity Team Organizational Chart For IoT Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on Cybersecurity Team, Organizational Chart, Security Engineer, Hierarchy Chart. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SS
Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of auditing and monitoring for internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about response plan, etc. Increase audience engagement and knowledge by dispensing information using Deploy Security Auditing And Monitoring Mechanisms Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on three stages. You can also present information on Auditing And Reporting, Incident Response Planning, Record Of Security Actions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Internet Of Things IoT Security Ppt Ideas Infographic Template Cybersecurity SS
Icons Slide For Internet Of Things IoT Security Ppt Ideas Infographic Template Cybersecurity SSPresenting our well crafted Icons Slide For Internet Of Things IoT Security Ppt Ideas Infographic Template Cybersecurity SS set of slides. The slides include icons that are innovatively designed by our team of experts. The icons are easy to edit so you can conveniently increase or decrease their size without any loss in resolution. Therefore, grab them instantly.
-
 Internet Of Things IoT Security For Table Of Contents Cybersecurity SS
Internet Of Things IoT Security For Table Of Contents Cybersecurity SSIntroducing Internet Of Things IoT Security For Table Of Contents Cybersecurity SS to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Business Success, IoT Security, Market Size Analysis, Overview With Key Benefits, using this template. Grab it now to reap its full benefits.
-
 IoT Cyber Security Architecture With Layers Internet Of Things IoT Security Cybersecurity SS
IoT Cyber Security Architecture With Layers Internet Of Things IoT Security Cybersecurity SSDeliver an outstanding presentation on the topic using this IoT Cyber Security Architecture With Layers Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Secure Communications, Secure Cloud, Secure Device, Messaging Control using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IoT Device Identity Platform Implementation Internet Of Things IoT Security Cybersecurity SS
IoT Device Identity Platform Implementation Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT device identity platform deployment, referable for businesses in developing mitigation process. It provides details about APIs, architecture, device client, etc. Deliver an outstanding presentation on the topic using this IoT Device Identity Platform Implementation Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of IoT Device, Platform Deployment, Developing Mitigation Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IoT Security Needs And Gap Analysis Internet Of Things IoT Security Cybersecurity SS
IoT Security Needs And Gap Analysis Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security gap analysis for organization, referable for related businesses wanting to improve operations. It provides details about single factor authentication, data in transit, incident response, etc. Deliver an outstanding presentation on the topic using this IoT Security Needs And Gap Analysis Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Comprehensive Security Training, Upgrade Encryption Protocols, Gap Analysis using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 IoT Security Overview With Key Benefits Internet Of Things IoT Security Cybersecurity SS
IoT Security Overview With Key Benefits Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security introduction with its major benefits, referable for companies dealing with related vulnerabilities. It provides details about security protocols, device protection, encryption, etc. Increase audience engagement and knowledge by dispensing information using IoT Security Overview With Key Benefits Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on two stages. You can also present information on Protection Of Devices, Encryption Of Networks, Secured Data Handling using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 IoT Security Sdlc Yearly Timeline Internet Of Things IoT Security Cybersecurity SS
IoT Security Sdlc Yearly Timeline Internet Of Things IoT Security Cybersecurity SSThis slide showcases software development lifecycle SDLC in IoT security , referable for developers in software programming of connected devices. It provides details about training, requirements, implementation, verification, etc. Present the topic in a bit more detail with this IoT Security Sdlc Yearly Timeline Internet Of Things IoT Security Cybersecurity SS. Use it as a tool for discussion and navigation on Training, Requirements And Design, Verification, Release And Respond. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Monitor Vulnerability Disclosure And Threat Intelligence Internet Of Things IoT Security Cybersecurity SS
Monitor Vulnerability Disclosure And Threat Intelligence Internet Of Things IoT Security Cybersecurity SSThis slide showcases vulnerability assessment disclosure and threat intelligence on internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about continuous monitoring, correlation, disclosure, etc. Introducing Monitor Vulnerability Disclosure And Threat Intelligence Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Continuous Monitoring, Correlation With Metadata, Disclosure Implementation, using this template. Grab it now to reap its full benefits.
-
 Organization Connected Devices Life Cycle Internet Of Things IoT Security Cybersecurity SS
Organization Connected Devices Life Cycle Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT devices lifecycle, referable for businesses in determining mitigation process. It provides details about audit, compliance, resale, reset, object pairing, etc. Increase audience engagement and knowledge by dispensing information using Organization Connected Devices Life Cycle Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on five stages. You can also present information on Reset And Repackaging, Organization Connected, Devices Life Cycle, Identity And Access Management using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Proactively Assess The Impact Of Potential Security Internet Of Things IoT Security Cybersecurity SS
Proactively Assess The Impact Of Potential Security Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of impact assessment on internet of things IoT device security events, referable for businesses in developing mitigation process. It provides details about threat model, security layers, etc. Introducing Proactively Assess The Impact Of Potential Security Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Comprehensive Security, Assessment And Security Layers, Credential Provisioning, using this template. Grab it now to reap its full benefits.
-
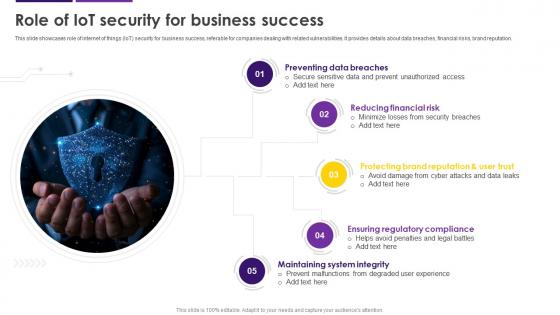 Role Of IoT Security For Business Success Internet Of Things IoT Security Cybersecurity SS
Role Of IoT Security For Business Success Internet Of Things IoT Security Cybersecurity SSThis slide showcases role of internet of things IoT security for business success, referable for companies dealing with related vulnerabilities. It provides details about data breaches, financial risks, brand reputation. Increase audience engagement and knowledge by dispensing information using Role Of IoT Security For Business Success Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on five stages. You can also present information on Preventing Data Breaches, Reducing Financial Risk, Ensuring Regulatory Compliance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Roles And Responsibilities Of IoT Security Team Internet Of Things IoT Security Cybersecurity SS
Roles And Responsibilities Of IoT Security Team Internet Of Things IoT Security Cybersecurity SSThis slide showcases cybersecurity team roles and responsibilities specific for internet of things IoT operations. It provides details about CEO, CISO, Director, manager, security engineer, etc. Introducing Roles And Responsibilities Of IoT Security Team Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Roles And Responsibilities, IoT Security Team, Security, Internet Of Things Operations, using this template. Grab it now to reap its full benefits.
-
 Root Cause Analysis Of IoT Password Attacks Internet Of Things IoT Security Cybersecurity SS
Root Cause Analysis Of IoT Password Attacks Internet Of Things IoT Security Cybersecurity SSThis slide showcases root cause analysis of internet of things IoT password attacks, referable for related businesses. It provides details about cybercriminal, login page, IoT device, video recordings, etc. Increase audience engagement and knowledge by dispensing information using Root Cause Analysis Of IoT Password Attacks Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on two stages. You can also present information on Record Conversation, Password Attack, Cyber Criminal, Root Cause Analysis using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Secure Remote Access IoT Device Internet Of Things IoT Security Cybersecurity SS
Secure Remote Access IoT Device Internet Of Things IoT Security Cybersecurity SSThis slide showcases secure remote access for internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about AWS IoT core, windows 10, VPNs, SSH, etc. Introducing Secure Remote Access IoT Device Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Virtual Private Networks, Network Privacy And Security, Service Communication, using this template. Grab it now to reap its full benefits.
-
 Shared Security Model For Internet Of Things Internet Of Things IoT Security Cybersecurity SS
Shared Security Model For Internet Of Things Internet Of Things IoT Security Cybersecurity SSDeliver an outstanding presentation on the topic using this Shared Security Model For Internet Of Things Internet Of Things IoT Security Cybersecurity SS. Dispense information and present a thorough explanation of Device Management, Account Management, Configuration, Virtualization Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Table Of Contents Internet Of Things IoT Security Cybersecurity SS
Table Of Contents Internet Of Things IoT Security Cybersecurity SSIncrease audience engagement and knowledge by dispensing information using Table Of Contents Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on seven stages. You can also present information on Current Cybersecurity Scenario, Cybersecurity Team For IoT Security, Impact Of IoT Security Strategy, IoT Security Costs Analysis using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SS
Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SSThis slide showcases internet of things IoT security strategy timeline, referable for developers and businesses in protection of connected devices. It provides details about credentials, authentication, cryptography, etc. Introducing Timeline For Implementing IoT Security Strategy Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Avoid Unnecessary Data Handling, Cryptographic Network Protocol Usage, Enforce Authentication Controls, using this template. Grab it now to reap its full benefits.
-
 Types Of Internet Of Things Security Internet Of Things IoT Security Cybersecurity SS
Types Of Internet Of Things Security Internet Of Things IoT Security Cybersecurity SSThis slide showcases types of internet of things IoT security along with its brief explanation, referable for companies dealing with related vulnerabilities. It provides details about communication attacks, lifecycle attacks, etc. Increase audience engagement and knowledge by dispensing information using Types Of Internet Of Things Security Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on four stages. You can also present information on Communication Attacks, Lifecycle Attacks, Physical Attacks, Internet Of Things Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Unique IoT Device Ids And Credentials Internet Of Things IoT Security Cybersecurity SS
Unique IoT Device Ids And Credentials Internet Of Things IoT Security Cybersecurity SSThis slide showcases unique internet of things IoT identification and credentials, referable for businesses in developing mitigation process. It provides details about secure access, hardware, X.509, etc. Introducing Unique IoT Device Ids And Credentials Internet Of Things IoT Security Cybersecurity SS to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Unique Identities, Secure Access, Entire Device Collection, Trusted Platform Modules, using this template. Grab it now to reap its full benefits.
-
 Use IoT Cryptographic Network Protocols Internet Of Things IoT Security Cybersecurity SS
Use IoT Cryptographic Network Protocols Internet Of Things IoT Security Cybersecurity SSThis slide showcases application of cryptographic network protocols for internet of things IoT devices, referable for businesses in developing mitigation process. It provides details about secure connectivity, updates, etc. Increase audience engagement and knowledge by dispensing information using Use IoT Cryptographic Network Protocols Internet Of Things IoT Security Cybersecurity SS. This template helps you present information on three stages. You can also present information on Secure Connectivity, Network Protocols Usage, Continuous Updates, Cryptographic Network Protocols using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ways To Overcome Cloud Data Security Challenges
Ways To Overcome Cloud Data Security ChallengesThis slide highlights solutions for cloud data security issues. The purpose of this template is assist organizations in balancing data protection and accessibility for addressing multiple problems. It includes elements such as data breaches, lack of control, etc. Introducing our premium set of slides with Ways To Overcome Cloud Data Security Challenges. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Breaches, Insufficient Cloud Provider Security, Lack Of Control. So download instantly and tailor it with your information.
-
 Data Privacy Training Icon For Securing Information
Data Privacy Training Icon For Securing InformationIntroducing our premium set of slides with Data Privacy Training Icon For Securing Information. Ellicudate the two stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Privacy Training, Securing Information. So download instantly and tailor it with your information.
-
 Benefits Of Implementing NIPS Cyber Security
Benefits Of Implementing NIPS Cyber SecurityThis slide depicts the advantages of executing NIPS cybersecurity. This slide aims to help the business leverage NIPS cybersecurity to prevent external attacks. It includes advantages such as reducing the likelihood of cyber attacks, increasing threat protection, etc. Introducing our Benefits Of Implementing NIPS Cyber Security set of slides. The topics discussed in these slides are Advantages, Description, Impact This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Comparative Analysis For Network Intrusion Protection Cyber Security Tools
Comparative Analysis For Network Intrusion Protection Cyber Security ToolsThis slide depicts the comparative evaluation of NIPS security tools. The purpose of this slide is to help the business make a well informed purchase decision. It includes comparison on the basis of the free trial period, features, ratings, etc. Introducing our premium set of slides with Comparative Analysis For Network Intrusion Protection Cyber Security Tools Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Distinctive Features, Free Trial, Tools So download instantly and tailor it with your information.
-
 Critical Elements Of NIPS Cyber Security
Critical Elements Of NIPS Cyber SecurityThis slide highlights the key components of NIPS cybersecurity. The purpose of this slide is to help business ensure all elements are correctly observed in order to establish NIPS cybersecurity. It includes elements such as network firewalls, access control to networks, etc. Introducing our premium set of slides with Critical Elements Of NIPS Cyber Security Ellicudate the nine stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Firewalls, Intrusion Prevention Systems, Management Systems So download instantly and tailor it with your information.
-
 Intrusion Prevention VS Detection Under NIPS Cyber Security
Intrusion Prevention VS Detection Under NIPS Cyber SecurityThis slide highlights the comparison between intrusion detection systems and intrusion prevention systems. The purpose of this slide is to help the business determine its business needs and implement suitable processes. It includes comparison on the basis of location, use, etc. Presenting our well structured Intrusion Prevention VS Detection Under NIPS Cyber Security The topics discussed in this slide are Description, Location, False Positive This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Network Intrusion And Prevention Cyber Security Icon
Network Intrusion And Prevention Cyber Security IconPresenting our set of slides with Network Intrusion And Prevention Cyber Security Icon This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Intrusion, Prevention Cyber Security Icon
-
 Network Intrusion Prevention Cyber Security System
Network Intrusion Prevention Cyber Security SystemThis slide highlights the network intrusion prevention system cybersecurity. The purpose of this slide is to help ensure that suitable processes are undertaken during security incidents. It includes elements such as network perimeters, internet, LAN, etc. Introducing our Network Intrusion Prevention Cyber Security System set of slides. The topics discussed in these slides are Internet, Network Perimeter, Prevention Systems This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Major Security Risks Associated Comprehensive Bitcoin Guide To Boost Cryptocurrency BCT SS
Major Security Risks Associated Comprehensive Bitcoin Guide To Boost Cryptocurrency BCT SSThe following slide showcases major security risks related to Bitcoin crypto wallets. It includes elements such as phishing attacks, malware, exchange hacks, user error, fake links, credential theft, infected attachments karma forgot passwords, private keys, etc. Introducing Major Security Risks Associated Comprehensive Bitcoin Guide To Boost Cryptocurrency BCT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Attacks, Malware, Exchange Hacks, using this template. Grab it now to reap its full benefits.
-
 Third Party Risk Management Methods In Information Security
Third Party Risk Management Methods In Information SecurityThis slide highlights strategies to control third-party risk in information security. The purpose of this slide is to aid organizations in identifying areas for improvement in their security practices. It includes elements such as vendor assessment, risk classification, etc. Presenting our set of slides with Third Party Risk Management Methods In Information Security. This exhibits information on Five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Vendor Assessment, Contractual Agreements, Maintain Records, Risk Classification
-
 Icon For Ensuring Security By Containerization Technology
Icon For Ensuring Security By Containerization TechnologyPresenting our well structured Icon For Ensuring Security By Containerization Technology. The topics discussed in this slide are Icon, Ensuring Security, Containerization Technology. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Secure Containerization For Cloud Framework Icon
Secure Containerization For Cloud Framework IconPresenting our well structured Secure Containerization For Cloud Framework Icon. The topics discussed in this slide are Secure Containerization, Cloud Framework Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Benefits Of Filtering Techniques In Email Security
Benefits Of Filtering Techniques In Email SecurityThis slide provides an outline of key benefits of filtering techniques in email security which include reputation-based email filters, safe listing and blocklisting. Introducing our Benefits Of Filtering Techniques In Email Security set of slides. The topics discussed in these slides are Benefits, Filtering Techniques, Email Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Best Practices For Email Domain Security
Best Practices For Email Domain SecurityThis slide is an overview of the best practices for email domain security which include secure email provider, strong, unique passwords and security audits. Introducing our premium set of slides with Best Practices For Email Domain Security. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Email Provider, Unique Passwords, Access Controls. So download instantly and tailor it with your information.
-
 Email Authentication And Security Working Process
Email Authentication And Security Working ProcessThis slide highlights the email authentication and security working process which includes sender establishes authentication rules, and sender configuration. Presenting our set of slides with Email Authentication And Security Working Process. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Email Infrastructure, Authentication Rules, Authentication Results.
-
 Email Security Encryption And Authentication Icon
Email Security Encryption And Authentication IconIntroducing our premium set of slides with Email Security Encryption And Authentication Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Email Security, Encryption And Authentication, Icon. So download instantly and tailor it with your information.
-
 Email Security Gateway Workflow Process
Email Security Gateway Workflow ProcessThis slide outlines the workflow process of email gateway which involves incoming emails, validate sender, validate content, advanced threat detection, etc. Presenting our well structured Email Security Gateway Workflow Process. The topics discussed in this slide are Email Gateway, Protection Against, Validate Sender. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Email Security Guard Gateway Architecture
Email Security Guard Gateway ArchitectureThis slide is an overview of architecture of email security guard gateway which include components like cloud protection layer, message center, internet, etc. Introducing our Email Security Guard Gateway Architecture set of slides. The topics discussed in these slides are Email Security, Guard Gateway, Architecture. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.





