Powerpoint Templates and Google slides for Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 SD WAN Model Secure Web Gateway Swg Importance For Businesses
SD WAN Model Secure Web Gateway Swg Importance For BusinessesThis slide outlines the importance of secure web gateways to businesses. The purpose of this slide is to demonstrate the need for SWGs for companies to protect their critical data and applications from malicious activities and actors. Introducing SD WAN Model Secure Web Gateway Swg Importance For Businesses to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Secure Web Gateway, Critical Data And Applications, Outdated Technologies, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Secure Web Gateway Swg Introduction And Features
SD WAN Model Secure Web Gateway Swg Introduction And FeaturesThis slide describes the overview and features of the secure gateway. The purpose of this slide is to demonstrate the SWG and its benefits to businesses. The features include URL filtering, application control, data loss prevention, antivirus, and HTTPS inspection. Increase audience engagement and knowledge by dispensing information using SD WAN Model Secure Web Gateway Swg Introduction And Features. This template helps you present information on two stages. You can also present information on Application Control, Data Loss Prevention, Antivirus, Secure Web Gateway using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Secure Web Gateways Swg Setup And Working
SD WAN Model Secure Web Gateways Swg Setup And WorkingThis slide depicts the methods to setup the secure web gateways and their working. The purpose of this slide is to demonstrate the various ways in which organizations can install the SWGs. It also caters to the working and functions performed by SWGs to protect data and safe browsing on the internet. Introducing SD WAN Model Secure Web Gateways Swg Setup And Working to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Cost Effective Alternative, Secure Web Gateways, Setup And Working, Preventing Restricted Data Sources, using this template. Grab it now to reap its full benefits.
-
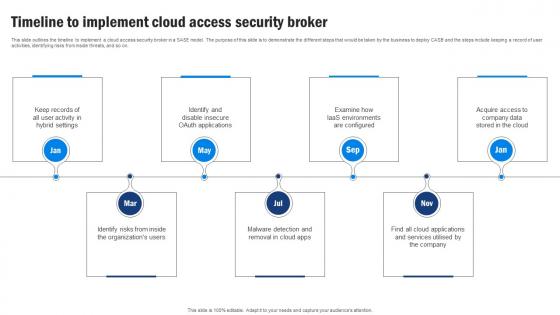 SD WAN Model Timeline To Implement Cloud Access Security Broker
SD WAN Model Timeline To Implement Cloud Access Security BrokerThis slide outlines the timeline to implement a cloud access security broker in a SASE model. The purpose of this slide is to demonstrate the different steps that would be taken by the business to deploy CASB and the steps include keeping a record of user activities, identifying risks from inside threats, and so on. Increase audience engagement and knowledge by dispensing information using SD WAN Model Timeline To Implement Cloud Access Security Broker. This template helps you present information on seven stages. You can also present information on Cloud Access Security Broker, Environments Are Configured, Identify Risks, Malware Detection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
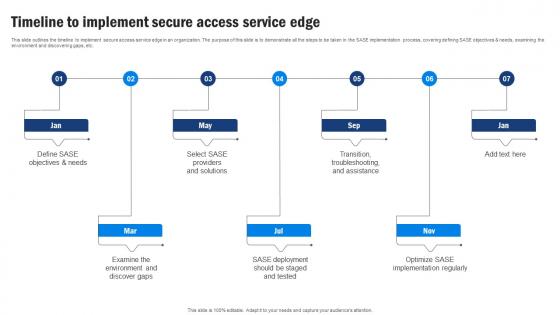 SD WAN Model Timeline To Implement Secure Access Service Edge
SD WAN Model Timeline To Implement Secure Access Service EdgeThis slide outlines the timeline to implement secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and discovering gaps, etc. Introducing SD WAN Model Timeline To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Secure Access Service Edge, Examining The Environment, Discovering Gaps, Timeline, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Traditional Networking Security Problems And Sase Solutions
SD WAN Model Traditional Networking Security Problems And Sase SolutionsThis slide describes the traditional networking security problems and how SASE model can overcome those problems. The main problems include, remote access to on-premises resources, access to cloud resources, network access controls etc. Deliver an outstanding presentation on the topic using this SD WAN Model Traditional Networking Security Problems And Sase Solutions. Dispense information and present a thorough explanation of Traditional Networking Security Problems, On Premises Resources, Access To Cloud Resources, Network Access Controls using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Working Of Secure Access Service Edge
SD WAN Model Working Of Secure Access Service EdgeThis slide represents the working of the secure access service edge model. The purpose of this slide is to demonstrate the working of the SASE model, comparing it to the traditional network security model. The components include cloud platforms, the internet, corporate network and so on. Present the topic in a bit more detail with this SD WAN Model Working Of Secure Access Service Edge. Use it as a tool for discussion and navigation on Precise Amount Of Performance, Dependability, Security, Cost For Each Network Connection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Firewall Audit Icon
Cyber Security Firewall Audit IconPresenting our well structured Cyber Security Firewall Audit Icon. The topics discussed in this slide are Cyber Security, Firewall Audit Icon. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Evaluating Security Capabilities For Firewall Auditing
Evaluating Security Capabilities For Firewall AuditingThis slide covers various techniques to evaluate security of information system for firewall auditing. The purpose of this slide is to help organizations in ensuring reliable and secure network. It covers techniques such as defining assessment scope, conducting security audit, implementing changes, evaluating risks, etc. Presenting our set of slides with Evaluating Security Capabilities For Firewall Auditing. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Conduct Security Audit, Implement Changes, Define Assessment Scope.
-
 Firewall Audit For Ensuring Network Infrastructure Security
Firewall Audit For Ensuring Network Infrastructure SecurityThis slide shows reasons for implementing firewall audit in an organization. The purpose of this slide is to help security professionals in maintaining integrity and security of network infrastructure. It covers various reasons such as ensuring network security, risk management, rules optimization and access control mechanism.Introducing our premium set of slides with Firewall Audit For Ensuring Network Infrastructure Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Security, Risk Management, Access Control Mechanism. So download instantly and tailor it with your information.
-
 Firewall Audit Icon For Network Security
Firewall Audit Icon For Network SecurityIntroducing our Firewall Audit Icon For Network Security set of slides. The topics discussed in these slides are Firewall Audit Icon, Network Security. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Firewall Audit Software Solutions For Security Compliance
Firewall Audit Software Solutions For Security ComplianceThis slide shows major features offered by firewall audit software that helps in maintaining a strong network security posture by complying with organizational regulatory standards. It covers solutions such as rule analysis, workflow automation and configuration management.Presenting our set of slides with Firewall Audit Software Solutions For Security Compliance. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Workflow Automation, Configuration Management, Firewall Rule Analysis.
-
 Social Engineering Attacks Prevention Checklist To Secure Organizations From Social Engineering
Social Engineering Attacks Prevention Checklist To Secure Organizations From Social EngineeringThis slide outlines the steps to be taken to protect the organization and its employees from social engineering attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan. Present the topic in a bit more detail with this Social Engineering Attacks Prevention Checklist To Secure Organizations From Social Engineering. Use it as a tool for discussion and navigation on Provide Staff Training, Multi Factor Authentication, Develop An Incident Response Plan. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Encryption Algorithms Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Security Encryption Algorithms Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a great visual aid for representing folder password protection. It is a modern and vibrant design that will add a professional touch to any presentation. The icon is easy to use and can be used to quickly and effectively communicate the importance of password security.
-
 Cyber Security Encryption Algorithms Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Cyber Security Encryption Algorithms Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Folder Password is a simple yet effective way to protect your confidential data. It is easy to use and provides a secure encryption for your files. It is an ideal solution for those who want to keep their documents safe and secure.
-
 Folder Security File Protection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Folder Security File Protection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a great visual aid for representing folder password protection. It is a modern and vibrant design that will add a professional touch to any presentation. The icon is easy to use and can be used to quickly and effectively communicate the importance of password security.
-
 Folder Security File Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Folder Security File Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Folder Password is a simple yet effective way to protect your confidential data. It is easy to use and provides a secure encryption for your files. It is an ideal solution for those who want to keep their documents safe and secure.
-
 Folder Security Password Protection Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Folder Security Password Protection Colored Icon In Powerpoint Pptx Png And Editable Eps FormatThis coloured powerpoint icon is a great visual aid for representing folder password protection. It is a modern and vibrant design that will add a professional touch to any presentation. The icon is easy to use and can be used to quickly and effectively communicate the importance of password security.
-
 Folder Security Password Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Folder Security Password Protection Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatThis Monotone Powerpoint Icon on Folder Password is a simple yet effective way to protect your confidential data. It is easy to use and provides a secure encryption for your files. It is an ideal solution for those who want to keep their documents safe and secure.
-
 National Securities Depository Limited In Powerpoint And Google Slides Cpb
National Securities Depository Limited In Powerpoint And Google Slides CpbPresenting National Securities Depository Limited In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase eight stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like National Securities Depository Limited This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 National Security Threat In Powerpoint And Google Slides Cpb
National Security Threat In Powerpoint And Google Slides CpbPresenting our National Security Threat In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on National Security Threat This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Essential Guide To Database Marketing Data Security Best Practices To Protect Customer Information MKT SS V
Essential Guide To Database Marketing Data Security Best Practices To Protect Customer Information MKT SS VThe purpose of this slide is to delineate various techniques through which companies can protect confidential client data and maintain trust. Data usage policy, data encryption, and endpoint security are major practices which are mentioned in slide along with key advantages of each practice. Deliver an outstanding presentation on the topic using this Essential Guide To Database Marketing Data Security Best Practices To Protect Customer Information MKT SS V Dispense information and present a thorough explanation of Data Usage Policy, Data Encryption, Endpoint Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Clear Security Stock Price In Powerpoint And Google Slides Cpb
Clear Security Stock Price In Powerpoint And Google Slides CpbPresenting our Clear Security Stock Price In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Clear Security Stock Price This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber Security Banking Industry In Powerpoint And Google Slides Cpb
Cyber Security Banking Industry In Powerpoint And Google Slides CpbPresenting Cyber Security Banking Industry In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Security Banking Industry. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Facebook Security Breach In Powerpoint And Google Slides Cpb
Facebook Security Breach In Powerpoint And Google Slides CpbPresenting our Facebook Security Breach In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Facebook Security Breach This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Former National Security Advisors In Powerpoint And Google Slides Cpb
Former National Security Advisors In Powerpoint And Google Slides CpbPresenting Former National Security Advisors In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Former National Security Advisors. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Iot 5g Security Network Icon
Iot 5g Security Network IconPresenting our set of slides with Iot 5g Security Network Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Network Icon, Security.
-
 Checklist To Ensure Secure Mobile Smartphone Banking For Transferring Funds Digitally Fin SS V
Checklist To Ensure Secure Mobile Smartphone Banking For Transferring Funds Digitally Fin SS VThis slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Deliver an outstanding presentation on the topic using this Checklist To Ensure Secure Mobile Smartphone Banking For Transferring Funds Digitally Fin SS V. Dispense information and present a thorough explanation of Change Passwords Frequently, Monitor Regular Transactions History, Set Account Alerts using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Mobile Banking Application Security Smartphone Banking For Transferring Funds Digitally Fin SS V
Mobile Banking Application Security Smartphone Banking For Transferring Funds Digitally Fin SS VThis slide shows various tools which can be used to evaluate or analyze the security level of mobile banking apps. It includes features and ratings of applications. It also contains various tools such as ImmuniWeb MobileSuite, CodifiedSecurity, QARK, etc. Present the topic in a bit more detail with this Mobile Banking Application Security Smartphone Banking For Transferring Funds Digitally Fin SS V. Use it as a tool for discussion and navigation on Mobile App Backend Testing, Access Security Analysts, Actionable Remediation Guidelines. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Two Securitized Financing In Powerpoint And Google Slides Cpb
Two Securitized Financing In Powerpoint And Google Slides CpbPresenting our Two Securitized Financing In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases two stages. It is useful to share insightful information on Two Securitized Financing This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Current Trending Technologies Cyber Security Technology Market Overview
Current Trending Technologies Cyber Security Technology Market OverviewThis slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Deliver an outstanding presentation on the topic using this Current Trending Technologies Cyber Security Technology Market Overview. Dispense information and present a thorough explanation of Cyber Security Technology, Market Growth, Compound Annual Growth Rate, Business Continuity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Current Trending Technologies Need For Cyber Security Technology
Current Trending Technologies Need For Cyber Security TechnologyThis slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Increase audience engagement and knowledge by dispensing information using Current Trending Technologies Need For Cyber Security Technology. This template helps you present information on three stages. You can also present information on Cyber Security Technology, Prevention Of Cybercrime, Protection Of Sensitive Information using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Current Trending Technologies Objectives Of Cyber Security Technology
Current Trending Technologies Objectives Of Cyber Security TechnologyThis slide explains the objectives of cyber security technology such as confidentiality, integrity and availability. It also talks about the three goals and how they collectively ensures the data protection. Introducing Current Trending Technologies Objectives Of Cyber Security Technology to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Cyber Security Technology, Data Protection, Integrity And Availability, using this template. Grab it now to reap its full benefits.
-
 Social Security Life Expectancy In Powerpoint And Google Slides Cpb
Social Security Life Expectancy In Powerpoint And Google Slides CpbPresenting our Social Security Life Expectancy In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases two stages. It is useful to share insightful information on Social Security Life Expectancy This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Icon For Endpoint Security In Blackberry Cyber Security
Icon For Endpoint Security In Blackberry Cyber SecurityPresenting our well structured Icon For Endpoint Security In Blackberry Cyber Security. The topics discussed in this slide are Endpoint, Security, Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Icon For Financial Sector Security With Blackberry Cybersecurity
Icon For Financial Sector Security With Blackberry CybersecurityIntroducing our premium set of slides with Icon For Financial Sector Security With Blackberry Cybersecurity. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Sector, Security, Financial. So download instantly and tailor it with your information.
-
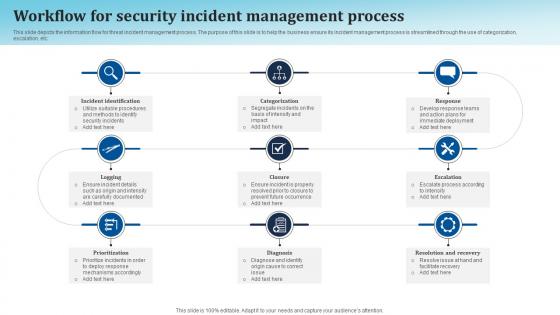 Workflow For Security Incident Management Process
Workflow For Security Incident Management ProcessThis slide depicts the information flow for threat incident management process. The purpose of this slide is to help the business ensure its incident management process is streamlined through the use of categorization, escalation, etc. Presenting our set of slides with Workflow For Security Incident Management Process. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Identification, Categorization, Escalation.
-
 Banking Solutions For Improving Customer Checklist To Ensure Secure Mobile Banking Fin SS V
Banking Solutions For Improving Customer Checklist To Ensure Secure Mobile Banking Fin SS VThis slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Deliver an outstanding presentation on the topic using this Banking Solutions For Improving Customer Checklist To Ensure Secure Mobile Banking Fin SS V. Dispense information and present a thorough explanation of Mobile Banking, Change Passwords Frequently, Monitor Transactions, Avoid Using Public Networks using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Banking Solutions For Improving Customer Mobile Banking Application Security Testing Tools Fin SS V
Banking Solutions For Improving Customer Mobile Banking Application Security Testing Tools Fin SS VThis slide shows various tools which can be used to evaluate or analyze the security level of mobile banking apps. It includes features and ratings of applications. It also contains various tools such as ImmuniWeb MobileSuite, CodifiedSecurity, QARK, etc. Present the topic in a bit more detail with this Banking Solutions For Improving Customer Mobile Banking Application Security Testing Tools Fin SS V. Use it as a tool for discussion and navigation on Mobile Banking Application, Security Testing Tools, Mobile Banking Apps, Real Time Bot Protection. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ensure Secure Access Icon Using Multi Factor Authentication Tool
Ensure Secure Access Icon Using Multi Factor Authentication ToolPresenting our set of slides with Ensure Secure Access Icon Using Multi Factor Authentication Tool. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Secure, Factor, Authentication.
-
 Provide Adaptive Security Icon Based On Multi Factor Authentication
Provide Adaptive Security Icon Based On Multi Factor AuthenticationPresenting our set of slides with Provide Adaptive Security Icon Based On Multi Factor Authentication. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Adaptive, Factor, Security.
-
 Reinforce Multi Factor Authentication Security For Unauthorized Use
Reinforce Multi Factor Authentication Security For Unauthorized UseThis slide showcases multi factor authentication practices for mitigating common security risks associated with relying solely on passwords. It includes aspects such as detailed multi factor authentication plan, configurable authentication factors, forgotten password plans, etc. Introducing our premium set of slides with Reinforce Multi Factor Authentication Security For Unauthorized Use. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Authentication, Configurable, Compatibility. So download instantly and tailor it with your information.
-
 Nist Cybersecurity Framework For Saas Security Compliance
Nist Cybersecurity Framework For Saas Security ComplianceThis slide illustrates NIST cybersecurity and compliance framework for SaaS businesses. The purpose of this slide is to help businesses improve security of critical infrastructure by protecting business assets and data from potential thefts. It covers elements such as recognize, secure, detect, respond and repair. Presenting our set of slides with Nist Cybersecurity Framework For Saas Security Compliance. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Recognize, Secure, Detect, Respond.
-
 Saas Compliance Checklist For Organizational Security
Saas Compliance Checklist For Organizational SecurityThis slide presents organizational security checklist to manage governance and compliance requirements for SaaS businesses. It aims to provide assistance during the SaaS compliance journey for securing cloud-based applications. It covers elements such as determining compliance requirements, evaluating risks, assessing compliance level, formulating strategy, implementing controls, etc. Introducing our Saas Compliance Checklist For Organizational Security set of slides. The topics discussed in these slides are Data Handling Processes, Security Risks, Resource Requirements. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 SOC 2 Certifications For Saas Security And Compliance
SOC 2 Certifications For Saas Security And ComplianceThis slide highlights cybersecurity compliance principles for SaaS companies under Service Organization Control 2 certification. It aims to mitigate the risks of unauthorized third-party access by meeting regulatory requirements. It covers principles such as security, availability, confidentiality, etc. Presenting our set of slides with SOC 2 Certifications For Saas Security And Compliance. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security, Availability, Confidentiality.
-
 Best Practices For Healthcare IoT Security IoMT Applications In Medical Industry IoT SS V
Best Practices For Healthcare IoT Security IoMT Applications In Medical Industry IoT SS VFollowing slide exhibits best practices to ensure cyber security while implementing internet of things IoT in health care. It includes pointers such as attack surface visibility, zero trust approach, etc. Introducing Best Practices For Healthcare IoT Security IoMT Applications In Medical Industry IoT SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Attack Surface Visibility, Segregated Internal Networking, Zero Trust Approach, using this template. Grab it now to reap its full benefits.
-
 New Technologies Cyber Security Technology Market Overview
New Technologies Cyber Security Technology Market OverviewThis slide explains Cyber security technology market overview with top players in the year 2021. It also predicts market growth and compound annual growth rate from year 2021 till 2028. Present the topic in a bit more detail with this New Technologies Cyber Security Technology Market Overview. Use it as a tool for discussion and navigation on Technology, Overview, Cyber Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 New Technologies Need For Cyber Security Technology
New Technologies Need For Cyber Security TechnologyThis slide gives an overview of cyber security technology. It also gives an idea about which industries are most venerable for a cyber attack and why cyber security is needed. Deliver an outstanding presentation on the topic using this New Technologies Need For Cyber Security Technology. Dispense information and present a thorough explanation of Technology, Information, Protecting using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
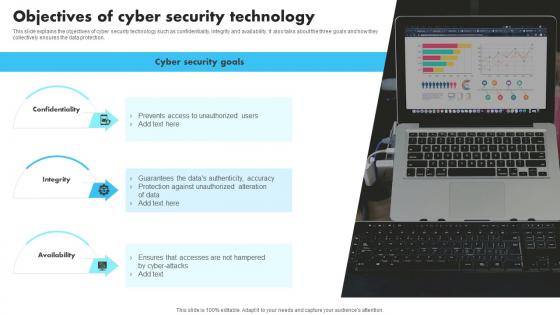 New Technologies Objectives Of Cyber Security Technology
New Technologies Objectives Of Cyber Security TechnologyThis slide explains the objectives of cyber security technology such as confidentiality, integrity and availability. It also talks about the three goals and how they collectively ensures the data protection. Introducing New Technologies Objectives Of Cyber Security Technology to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Confidentiality, Technology, Availability, using this template. Grab it now to reap its full benefits.
-
 Cloud Security Event Monitoring Icon
Cloud Security Event Monitoring IconIncrease audience engagement and knowledge by dispensing information using Cloud Security Event Monitoring Icon. This template helps you present information on Three stages. You can also present information on Cloud Security Event Monitoring Icon using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Improved Framework For Event Monitoring And Security
Improved Framework For Event Monitoring And SecurityThis slide contains the framework for monitoring events. Its objective is to track and evaluate monitoring events. This slide includes capturing data, analysing data, taking action, etc. Introducing Improved Framework For Event Monitoring And Security to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Capture Data, Analyse Data, Take Action, using this template. Grab it now to reap its full benefits.
-
 Security Monitoring Event Monitoring Roadmap
Security Monitoring Event Monitoring RoadmapThis slide contains the roadmap for enhancing security event roadmap. Its objective is to control the amount of users and reduce attacks on the network. This slide includes transaction security, monitoring, limit event, data leakage, etc. Increase audience engagement and knowledge by dispensing information using Security Monitoring Event Monitoring Roadmap. This template helps you present information on Four stages. You can also present information on Digital Twin Construction, Network Construction, Monitoring Centres using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda For Ethical Hacking And Network Security Ppt Icon Master Slide
Agenda For Ethical Hacking And Network Security Ppt Icon Master SlideIntroducing Agenda For Ethical Hacking And Network Security Ppt Icon Master Slide to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Ethical Hacking, Network Security, Ethical Hacking Training Program, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Acunetix Ethical Hacking Tool
Ethical Hacking And Network Security Acunetix Ethical Hacking ToolThis slide represents the Acunetix tool used for ethical hacking, including its features such as scalable and fast, on-premise and cloud-based structure, and rapid speed of webpage scans. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Acunetix Ethical Hacking Tool. This template helps you present information on three stages. You can also present information on Acunetix Ethical Hacking Tool, Cloud Based Structure, Web Application Security Scanner using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Advantages Of Ethical Hacking
Ethical Hacking And Network Security Advantages Of Ethical HackingThis slide depicts the benefits of ethical hacking, such as unraveling the hacker mindset, development and quality assurance, transition to the cloud, and employment. Introducing Ethical Hacking And Network Security Advantages Of Ethical Hacking to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Unraveling The Hacker Mindset, Development And Quality Assurance, Transition To Cloud, Employment, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Benefits Of Ethical Hacking To Companies
Ethical Hacking And Network Security Benefits Of Ethical Hacking To CompaniesThis slide represents the benefits of ethical hacking to the companies, including testing security, identifying weaknesses, understanding hacker methods, and being ready for a hacker attack. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Benefits Of Ethical Hacking To Companies. This template helps you present information on four stages. You can also present information on Security Measures Testing, Identifying Weaknesses, Ethical Hacking, Understanding Hacker Methods using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Black Hat Hackers Crackers
Ethical Hacking And Network Security Black Hat Hackers CrackersThis slide describes the black hat hackers and how they can take advantage of a vulnerability in a software, network, and computer system. Introducing Ethical Hacking And Network Security Black Hat Hackers Crackers to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Weakness For Illegal Purposes, Black Hat Hackers, Computer System, Network, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Burp Suite Ethical Hacking Tool
Ethical Hacking And Network Security Burp Suite Ethical Hacking ToolThis slide depicts the burp suite ethical hacking tool, including its features such as open-source and custom-built software, easy-to-use login sequence recorder, crawl, and scan automation, etc. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Burp Suite Ethical Hacking Tool. This template helps you present information on three stages. You can also present information on Sophisticated Scanning Logic, Crawl And Scan Automation, Custom Built Software, Comprehensive Scanning Capabilities using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Common Types Of Cyber Crime
Ethical Hacking And Network Security Common Types Of Cyber CrimeThis slide describes the common types of cybercrime such as identity theft, computer fraud, privacy breach, electronic money laundering, electronic funds transfer, and so on. Introducing Ethical Hacking And Network Security Common Types Of Cyber Crime to increase your presentation threshold. Encompassed with ten stages, this template is a great option to educate and entice your audience. Dispence information on Electronic Money Laundering, Electronic Funds Transfer, Denial Of Service Attacks, Sharing Copyrighted Files Or Data, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Cookie Theft Technique Of Hacking
Ethical Hacking And Network Security Cookie Theft Technique Of HackingThis slide depicts the cookie theft technique of hacking and how cookies are used to steal user sessions and use their information to perform malicious activities. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Cookie Theft Technique Of Hacking. This template helps you present information on four stages. You can also present information on Technique Of Hacking, Perform Malicious Activities, Customized Website, Session Hijacking using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.





