Powerpoint Templates and Google slides for Security
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Ethical Hacking And Network Security Purpose Of Ethical Hacking
Ethical Hacking And Network Security Purpose Of Ethical HackingThis slide depicts the purpose of ethical hacking, including the tools and tactics they use and their responsibility to report the discovered vulnerabilities to the authorities. Introducing Ethical Hacking And Network Security Purpose Of Ethical Hacking to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Ethical Hacking, Vulnerabilities To The Authorities, Security Or Protect Systems, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Reasons To Pursue The Certified Ethical Hacker Ceh V11 Program
Ethical Hacking And Network Security Reasons To Pursue The Certified Ethical Hacker Ceh V11 ProgramThis slide depicts the reasons to pursue the certified ethical hacking program, including the number of available jobs, the average salary in US dollars, and so on. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Reasons To Pursue The Certified Ethical Hacker Ceh V11 Program. This template helps you present information on three stages. You can also present information on Ethical Hacking Program, Reasons To Pursue, Certified Ethical Hacker, Baseline Certification using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Roadmap For Ethical Hacking Program
Ethical Hacking And Network Security Roadmap For Ethical Hacking ProgramThis slide describes the roadmap for ethical hacking, including the phases of the ethical hacking training program to become a certified ethical hacking master. Introducing Ethical Hacking And Network Security Roadmap For Ethical Hacking Program to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Roadmap For Ethical Hacking, Ethical Hacking Training Program, Ethical Hacking Master, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Roles And Responsibilities Of Ethical Hacker
Ethical Hacking And Network Security Roles And Responsibilities Of Ethical HackerThis slide depicts the roles and responsibilities of ethical hackers, including preventing future attacks by recognizing open ports, repairing the vulnerabilities of the system, etc. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Roles And Responsibilities Of Ethical Hacker. This template helps you present information on five stages. You can also present information on Roles And Responsibilities, Ethical Hacker, Vulnerabilities Of The System, Preventing Future Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Security Measures To Prevent Phishing Attacks
Ethical Hacking And Network Security Security Measures To Prevent Phishing AttacksThis slide represents the security measures to prevent phishing attacks, such as using the spam filter, updating security software regularly, utilization of multi-factor authentication, and so on. Introducing Ethical Hacking And Network Security Security Measures To Prevent Phishing Attacks to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Prevent Phishing Attacks, Spam Filter, Updating Security Software Regularly, Utilization Of Multi Factor Authentication, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Solarwinds Security Event Manager Ethical Hacking Tool
Ethical Hacking And Network Security Solarwinds Security Event Manager Ethical Hacking ToolThis slide represents the SolarWinds security event manager ethical hacking tool and its features such as integrity monitoring, easy-to-use user interface, built-in compliance reports, etc. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Solarwinds Security Event Manager Ethical Hacking Tool. This template helps you present information on three stages. You can also present information on Solarwinds Security Event, Ethical Hacking Tool, Built In Compliance Reports using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Some Limitations Of Ethical Hacking
Ethical Hacking And Network Security Some Limitations Of Ethical HackingIntroducing Ethical Hacking And Network Security Some Limitations Of Ethical Hacking to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Resource Constraints, Restricted Methods, Ethical Hacking, Computing Power And Funding, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Sql Injection Sqli Technique Of Hacking
Ethical Hacking And Network Security Sql Injection Sqli Technique Of HackingThis slide depicts the SQL injection technique of hacking and how hackers can attack organizations critical information stored in databases through SQL queries. Present the topic in a bit more detail with this Ethical Hacking And Network Security Sql Injection Sqli Technique Of Hacking. Use it as a tool for discussion and navigation on Injection Technique Of Hacking, Attack Organizations, Sql Injection, Credit Card Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ethical Hacking And Network Security Techniques Used In Ethical Hacking
Ethical Hacking And Network Security Techniques Used In Ethical HackingThis slide represents the techniques of ethical hacking such as port scanning, analyzing and sniffing network traffic, detection of SQL injections, an inspection of patch installation. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Techniques Used In Ethical Hacking. This template helps you present information on six stages. You can also present information on Techniques Of Ethical Hacking, Port Scanning, Sniffing Network Traffic, Patch Installation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
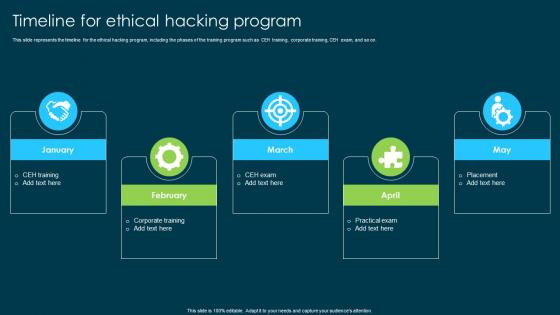 Ethical Hacking And Network Security Timeline For Ethical Hacking Program
Ethical Hacking And Network Security Timeline For Ethical Hacking ProgramThis slide represents the timeline for the ethical hacking program, including the phases of the training program such as CEH training, corporate training, CEH exam, and so on. Introducing Ethical Hacking And Network Security Timeline For Ethical Hacking Program to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Ethical Hacking Program, Training Program, Corporate Training, Placement, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Top Ethical Hacking Courses And Certifications
Ethical Hacking And Network Security Top Ethical Hacking Courses And CertificationsThis slide depicts the top ethical hacking courses and certifications such as CEH, SANS GPEN, offensive security certified professional, Found stone ultimate hacking, and CREST. Deliver an outstanding presentation on the topic using this Ethical Hacking And Network Security Top Ethical Hacking Courses And Certifications. Dispense information and present a thorough explanation of Offensive Security Certified Professional, Foundstone Ultimate Hacking, Certified Ethical Hacker using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Ethical Hacking And Network Security Traceroute Ng Ethical Hacking Program
Ethical Hacking And Network Security Traceroute Ng Ethical Hacking ProgramThis slide describes the Traceroute NG ethical hacking program, including its features such as TCP and ICMP network route analysis, txt logfile, IPv4 and IPv6 supported, and so on. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Traceroute Ng Ethical Hacking Program. This template helps you present information on three stages. You can also present information on Network Route Analysis, Enables Precise Evaluation, Analyze Network Paths using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security Types Of Ethical Hacking
Ethical Hacking And Network Security Types Of Ethical HackingThis slide represents the types of ethical hacking such as web application hacking, system hacking, web server hacking, hacking wireless networks, and social engineering. Introducing Ethical Hacking And Network Security Types Of Ethical Hacking to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Hacking Wireless Network, Social Engineering, Web Application Hacking, System Hacking, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Types Of Phishing Attack
Ethical Hacking And Network Security Types Of Phishing AttackThis slide represents the types of phishing attacks such a spear-phishing, clone phishing, whaling, BEC, vishing, and snowshoeing phishing. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Types Of Phishing Attack. This template helps you present information on three stages. You can also present information on Business Email Compromise, Clone Phishing, Snowshoeing, Phishing Attack using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security What Do Ethical Hackers Do
Ethical Hacking And Network Security What Do Ethical Hackers DoThis slide depicts the tasks performed by ethical hackers including scope and goal setting, discovery, exploitation and documentation of the pen-test effort. Present the topic in a bit more detail with this Ethical Hacking And Network Security What Do Ethical Hackers Do. Use it as a tool for discussion and navigation on Ethical Hackers, Scope And Goal Setting, Exploitation And Documentation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Ethical Hacking And Network Security What Is Ethical Hacking
Ethical Hacking And Network Security What Is Ethical HackingThis slide depicts ethical hacking and how ethical hackers could be an asset to a company that can prevent malicious attacks on a computer system or network. Introducing Ethical Hacking And Network Security What Is Ethical Hacking to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Security Professionals, Security Flaws, Ethical Hacking, Computer System, Application, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security What Is Hacking Ppt Icon Format Ideas
Ethical Hacking And Network Security What Is Hacking Ppt Icon Format IdeasThis slide illustrates what hacking is and how businesses are getting affected by it every year, and to prevent this, they hire white hat hackers or ethical hackers. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security What Is Hacking Ppt Icon Format Ideas. This template helps you present information on five stages. You can also present information on Computer System Or Network, Circumvent Security, Personal Or Corporate Data, Password Cracking Technique using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security What Is Phishing Attack
Ethical Hacking And Network Security What Is Phishing AttackThis slide represents what phishing attacks are and how phishers hoax people through emails, SMS, phone calls, and social media platforms. Introducing Ethical Hacking And Network Security What Is Phishing Attack to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Phishing Attacks, Phishers Hoax, Social Media Platforms, System Hacking, Corporate Or Personal Data, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Whats New In Cehv11
Ethical Hacking And Network Security Whats New In Cehv11This slide represents the new concepts added to the Certified Ethical Hacking program, including hacking challenges on a higher level, new attack techniques, enumeration, and others. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Whats New In Cehv11. This template helps you present information on eight stages. You can also present information on Operation Technology, Hacking Web Applications, Inverse Engineering Of Malware, Cloud Computing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ethical Hacking And Network Security White Hat Or Ethical Hackers
Ethical Hacking And Network Security White Hat Or Ethical HackersThis slide represents the white hat or ethical hackers and how they test the information systems of the organizations with the techniques and methods of black hat hackers. Introducing Ethical Hacking And Network Security White Hat Or Ethical Hackers to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on White Hat Or Ethical Hackers, Malware Scans On Networks, Seek To Penetrate Information Systems, Malware Infections, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Why Organizations Recruit Ethical Hackers
Ethical Hacking And Network Security Why Organizations Recruit Ethical HackersThis slide depicts why organizations recruit ethical hackers, including effective security measures, protecting customer information, raising security awareness, and so on. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Why Organizations Recruit Ethical Hackers. This template helps you present information on six stages. You can also present information on Organizations Recruit Ethical Hackers, Company Information Systems, Organization Security Posture, Network Protection Architecture using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Ethical Hacking And Network Security Ppt Icon Slide Portrait
Icons Slide For Ethical Hacking And Network Security Ppt Icon Slide PortraitIntroducing our well researched set of slides titled Icons Slide For Ethical Hacking And Network Security Ppt Icon Slide Portrait. It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Techniques To Establish It Infrastructure And Cyber Security
Techniques To Establish It Infrastructure And Cyber SecurityThis slide depicts the multiple strategies to establish safeguard IT infrastructure and cybersecurity. The purpose of this slide is to help ensure robust safety measures are in place through the use of firewalls, authentication software, etc. Presenting our set of slides with Techniques To Establish It Infrastructure And Cyber Security This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Firewall, Antivirus And Antimalware Systems
-
 Types Of Cyber Security Measures To Safeguard It Infrastructure
Types Of Cyber Security Measures To Safeguard It InfrastructureThis slide depicts the kinds of cyber security approaches to safeguard companys IT infrastructure. The purpose of this slide is to help the business improve its cybersecurity measures in order to prevent online attacks. It includes operational security, network security, etc. Introducing our premium set of slides with Types Of Cyber Security Measures To Safeguard It Infrastructure Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Operational Security, Information Security, Network Security So download instantly and tailor it with your information.
-
 Virtualization Icon For Enhancing Security Isolation
Virtualization Icon For Enhancing Security IsolationPresenting our set of slides with Virtualization Icon For Enhancing Security Isolation This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Virtualization Icon For Enhancing, Security Isolation
-
 Security Of Information In Big Data Big Data Analytics And Management
Security Of Information In Big Data Big Data Analytics And ManagementThis slide represents the securing information in big data challenge of big data and solutions to this challenge, such as encryption data, separation of data, security monitoring in real-time, and so on. Introducing Security Of Information In Big Data Big Data Analytics And Management to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Encrypting Data, Separation Of Data, Endpoint Security, using this template. Grab it now to reap its full benefits.
-
 Assessing Multiple Platforms For Cyber Security Digital Transformation Strategies To Integrate DT SS
Assessing Multiple Platforms For Cyber Security Digital Transformation Strategies To Integrate DT SSThis slide provides glimpse about comparative analysis of cyber security and risk management tools that can help the business in mitigating cyber threats. It includes key features, pricing, deployment, etc. Deliver an outstanding presentation on the topic using this Assessing Multiple Platforms For Cyber Security Digital Transformation Strategies To Integrate DT SS. Dispense information and present a thorough explanation of Management Software, Cybersecurity, Supported Platforms using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Pricing Plans For Selected Cyber Security Digital Transformation Strategies To Integrate DT SS
Pricing Plans For Selected Cyber Security Digital Transformation Strategies To Integrate DT SSPresent the topic in a bit more detail with this Pricing Plans For Selected Cyber Security Digital Transformation Strategies To Integrate DT SS. Use it as a tool for discussion and navigation on Software Features, Real Time, Threat Intelligence. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Classify Incident Report Template For Cyber Security Analysis
Classify Incident Report Template For Cyber Security AnalysisThis slide exhibits cyber report template categorization for ensuring quick and effective understanding of incident nature, impact and implication. It includes elements such as Michigan, sysnets security, techtargets and thycotics template. Presenting our set of slides with Classify Incident Report Template For Cyber Security Analysis. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Michigan Template, Sysnets Security Template, Thycotics Template.
-
 Implement Authentication Techniques For Wireless Lan Security
Implement Authentication Techniques For Wireless Lan SecurityThis slide highlights wireless security LAN checklist for preventing security threats and compile standard authentication and encryption techniques. It includes elements such as wireless lan security recommendations, applicable, not applicable and notes. Introducing our Implement Authentication Techniques For Wireless Lan Security set of slides. The topics discussed in these slides are Authentication, Techniques, Applicable. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Monitoring And Security Logging With Wireless Lan Standard Modes
Monitoring And Security Logging With Wireless Lan Standard ModesThis slide showcases wireless LANs standards and modes for defining communication protocols, frequency bands and data rates. It includes modes such as IEEE 802.11a, 802.11b, 802.11g, 802.11n and 802.11ac. Introducing our premium set of slides with Monitoring And Security Logging With Wireless Lan Standard Modes. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Monitoring, Security, Standard Modes . So download instantly and tailor it with your information.
-
 Wireless Lan Network Icon For Data Security
Wireless Lan Network Icon For Data SecurityPresenting our well structured Wireless Lan Network Icon For Data Security. The topics discussed in this slide are Wireless, Data Security . This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Data Security Strategies To Protect Retail Customer Comprehensive Retail Transformation DT SS
Data Security Strategies To Protect Retail Customer Comprehensive Retail Transformation DT SSThis slide presents key strategies to ensure data security in retail industry to protect consumer data. It includes PCI DSS compliance, POS security, customer data protection, secure online transactions, inventory management security, and employee training and awareness. Present the topic in a bit more detail with this Data Security Strategies To Protect Retail Customer Comprehensive Retail Transformation DT SS. Use it as a tool for discussion and navigation on Online Transactions, Customer Data Protection, POS Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Strategies For Involving Top Management In Security Comprehensive Retail Transformation DT SS
Strategies For Involving Top Management In Security Comprehensive Retail Transformation DT SSThis slide presents the strategy for involving top management in security initiatives. It includes educate top management, present potential risks, highlight financial and reputational damages, emphasize the need for proactive measures and collaborate with top management. Introducing Strategies For Involving Top Management In Security Comprehensive Retail Transformation DT SS to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Security Investment, Cybersecurity, Business Objectives, using this template. Grab it now to reap its full benefits.
-
 Ethical Hacking And Network Security Is Ethical Hacking Legal
Ethical Hacking And Network Security Is Ethical Hacking LegalThis slide shows the legality of ethical hacking, how ethical hackers work official permission, and companies hire them to protect their networks and computer systems from malicious attacks. Increase audience engagement and knowledge by dispensing information using Ethical Hacking And Network Security Is Ethical Hacking Legal. This template helps you present information on eight stages. You can also present information on Ethical Hacking, Computer Networks, Seek Potential Vulnerabilities, Inflict Unintended Loss using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Saas Software Architectural Framework For Data Security
Saas Software Architectural Framework For Data SecurityThis slide demonstrates SaaS software architectural framework for contributing to design, development and operation of scalable and efficient cloud based applications. It includes basis such as autonomous management, user interface, operational processes, application layer, etc. Introducing our Saas Software Architectural Framework For Data Security set of slides. The topics discussed in these slides are Autonomous Management, Service Provider, Subscriber This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Website Security Management Action Plan Website Launch Announcement
Website Security Management Action Plan Website Launch AnnouncementMentioned slide provides insights into site security management tips which can be implemented by businesses to prevent website hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, SSL certification, etc. Present the topic in a bit more detail with this Website Security Management Action Plan Website Launch Announcement. Use it as a tool for discussion and navigation on Anti Malware Program, High, Medium, Low. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Everything About Mobile Banking Checklist To Ensure Secure Mobile Banking Fin SS V
Everything About Mobile Banking Checklist To Ensure Secure Mobile Banking Fin SS VThis slide shows checklist which can be used to adopt various security measure while using mobile banking. It includes tasks such as change passwords frequently, monitor transactions, avoid using public networks. Present the topic in a bit more detail with this Everything About Mobile Banking Checklist To Ensure Secure Mobile Banking Fin SS V. Use it as a tool for discussion and navigation on Ensure Secure Mobile Banking, Change Passwords Frequently, Monitor Transactions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Everything About Mobile Banking Mobile Banking Application Security Testing Tools Fin SS V
Everything About Mobile Banking Mobile Banking Application Security Testing Tools Fin SS VThis slide shows various tools which can be used to evaluate or analyze the security level of mobile banking apps. It includes features and ratings of applications. It also contains various tools such as ImmuniWeb MobileSuite, CodifiedSecurity, QARK, etc. Deliver an outstanding presentation on the topic using this Everything About Mobile Banking Mobile Banking Application Security Testing Tools Fin SS V. Dispense information and present a thorough explanation of Mobile Banking Application, Security Testing Tools, Mobile Banking Apps, Ratings Of Applications using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Benefits Of Secure Access Service Edge Sase
SD WAN Model Benefits Of Secure Access Service Edge SaseThis slide outlines the key benefits of secure access service edge. The purpose of this slide is to showcase the advantages of the SASE model, such as flexibility, cost savings, reduced complexity, increased performance, threat and data protection and increased network performance. Present the topic in a bit more detail with this SD WAN Model Benefits Of Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Data Protection, Increased Network Performance, Cost Savings, Secure Access Service Edge. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Best Practices To Implement Cloud Access Security Broker
SD WAN Model Best Practices To Implement Cloud Access Security BrokerThis slide represents the best practices for implementing a cloud access security broker within an organization. The purpose of this slide is to demonstrate the best practices and their possible impact on the overall business operations. The best practices include building visibility, forecasting risk and releasing CASB. Deliver an outstanding presentation on the topic using this SD WAN Model Best Practices To Implement Cloud Access Security Broker. Dispense information and present a thorough explanation of Network And Cloud Infrastructure Monitoring, Protection Against Risks, Specific Risk Prototypes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Budget To Implement Secure Access Service Edge
SD WAN Model Budget To Implement Secure Access Service EdgeThis slide depicts the budget calculation for implementing a secure access service edge model in an organization. The purpose of this slide is to showcase the estimated and actual cost and variance for SASE model spending. The key components include SD-WAN, SWG, ZTNA, CASB, and FWaaS. Present the topic in a bit more detail with this SD WAN Model Budget To Implement Secure Access Service Edge. Use it as a tool for discussion and navigation on Secure Web Gateway, Cloud Access Security Broker, Zero Trust Network Access, Firewall As A Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Challenges With Traditional Network Security Approaches
SD WAN Model Challenges With Traditional Network Security ApproachesThis slide describes the challenges with traditional network security approaches. The purpose of this slide is to demonstrate the various challenges caused by conventional network security methods while backhauling traffic to data centers, including disjoint management, workload, slower cloud adoption, and so on. Deliver an outstanding presentation on the topic using this SD WAN Model Challenges With Traditional Network Security Approaches. Dispense information and present a thorough explanation of Challenges With Traditional Network, Security Approaches, Including Disjoint Management, Workload, Slower Cloud Adoption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Checklist To Implement Secure Access Service Edge
SD WAN Model Checklist To Implement Secure Access Service EdgePresent the topic in a bit more detail with this SD WAN Model Checklist To Implement Secure Access Service Edge. Use it as a tool for discussion and navigation on Test And Troubleshoot, Incorporate Zero Trust Solutions, Goals And Requirements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Cloud Access Security Broker Casb Overview
SD WAN Model Cloud Access Security Broker Casb OverviewThis slide outlines the overview and benefits of cloud access security broker. The purpose of this slide is to demonstrate the benefits of CASB, such as risk visibility, threat prevention, granular cloud usage control, shadow IT assessment and management, and data loss prevention. Introducing SD WAN Model Cloud Access Security Broker Casb Overview to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Granular Cloud Usage Control, Data Loss Prevention, Cloud Access Security Broker, Risk Visibility, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Cloud Access Security Broker Implementation Models
SD WAN Model Cloud Access Security Broker Implementation ModelsThis slide talks about the implementation models of cloud access security broker. The purpose of this slide is to demonstrate the two types of CASB deployment, such as out-of-band and inline. The CASB deployment models include API scanning and forward and reverse proxy. Increase audience engagement and knowledge by dispensing information using SD WAN Model Cloud Access Security Broker Implementation Models. This template helps you present information on three stages. You can also present information on Cloud Access Security Broker, Api Scanning, Forward Proxy, Reverse Proxy using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Cloud Access Security Broker Use Cases
SD WAN Model Cloud Access Security Broker Use CasesThis slide represents the use cases of cloud access security broker. The purpose of this slide is to showcase the multiple use cases of cloud access security broker, covering protection against threats, governing usage, securing data, and enforcing data loss and compliance policies. Present the topic in a bit more detail with this SD WAN Model Cloud Access Security Broker Use Cases. Use it as a tool for discussion and navigation on Cloud Access Security Broker, Covering Protection Against Threats, Governing Usage, Securing Data. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Cloud Access Security Broker Working Process
SD WAN Model Cloud Access Security Broker Working ProcessThis slide outlines the working process of a cloud access security broker. The purpose of this slide is to showcase the overview and working process steps of CASB. The main steps include discovery, classification, and remediation. Introducing SD WAN Model Cloud Access Security Broker Working Process to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Cloud Access Security Broker, Classification And Remediation, Control And Transparency Across Data, Risks In The Cloud, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Comparison Between Secure Access Service Edge And Sd Wan
SD WAN Model Comparison Between Secure Access Service Edge And Sd WanThis slide compares secure access service edge and software-defined wide area network. The purpose of this slide is to demonstrate the difference between SASE and SD-WAN technologies based on deployment and architecture, security, traffic and connectivity, and remote access. Present the topic in a bit more detail with this SD WAN Model Comparison Between Secure Access Service Edge And Sd Wan. Use it as a tool for discussion and navigation on Deployment And Architecture, Traffic And Connectivity, Security, Secure Access Service Edge. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Firewall As A Service Fwaas Working And Security Features
SD WAN Model Firewall As A Service Fwaas Working And Security FeaturesThis slide describes the working and security features of the firewall as a service. The purpose of this slide is to demonstrate the working of the firewall as a service, including its security features such as packet filtering, network monitoring, IPsec, SSL VPN support, DPI, and IP mapping. Introducing SD WAN Model Firewall As A Service Fwaas Working And Security Features to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Packet Filtering, Internet Protocol Mapping, Network Monitoring, Deep Packet Inspection, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Introduction To Secure Access Service Edge Sase
SD WAN Model Introduction To Secure Access Service Edge SaseThis slide represents the introduction of SASE cloud security technology. The purpose of this slide is to demonstrate the core capabilities, benefits and key components of SASE. The key components include SD-WAN, FWaaS, ZTNA, CASB, SWG, and unified management. Present the topic in a bit more detail with this SD WAN Model Introduction To Secure Access Service Edge Sase. Use it as a tool for discussion and navigation on Software Defined Wan, Firewall As A Service, Zero Trust Network Access, Cloud Access Security Broker. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Pillars Of Cloud Access Security Broker Ppt Icon Design Ideas
SD WAN Model Pillars Of Cloud Access Security Broker Ppt Icon Design IdeasThis slide represents the four major pillars of cloud access security broker. The purpose of this slide is to showcase the main pillars of implementing a cloud access security broker. The pillars include compliance, visibility, threat protection, and data security. Increase audience engagement and knowledge by dispensing information using SD WAN Model Pillars Of Cloud Access Security Broker Ppt Icon Design Ideas. This template helps you present information on four stages. You can also present information on Cloud Access Security Broker, Compliance, Visibility, Threat Protection, Data Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Roadmap To Implement Secure Access Service Edge
SD WAN Model Roadmap To Implement Secure Access Service EdgeThis slide depicts the roadmap to implementing secure access service edge in an organization. The purpose of this slide is to demonstrate all the steps to be taken in the SASE implementation process, covering defining SASE objectives and needs, examining the environment and, discovering gaps, etc. Introducing SD WAN Model Roadmap To Implement Secure Access Service Edge to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Implementation Regularly, Transition, Troubleshooting And Assistance, Secure Access Service Edge, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Secure Access Service Edge Architecture Characteristics
SD WAN Model Secure Access Service Edge Architecture CharacteristicsThis slide represents the architectural characteristics of a secure access service edge. The purpose of this slide is to showcase the features of SASE architecture that include identity-driven, cloud-native, support for all edges, and global distribution. Introducing SD WAN Model Secure Access Service Edge Architecture Characteristics to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure Access Service Edge, Architecture Characteristics, Cloud Native, Global Distribution, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Secure Access Service Edge Implementation Steps
SD WAN Model Secure Access Service Edge Implementation StepsThis slide outlines the steps to implement a secure service edge in a business. The purpose of this slide is to demonstrate the various guidelines to consider while implementing the SASE model in an organization. The main steps include defining SASE goals and requirements, selecting the SD-WAN backbone, incorporating zero-trust solutions, etc. Increase audience engagement and knowledge by dispensing information using SD WAN Model Secure Access Service Edge Implementation Steps. This template helps you present information on five stages. You can also present information on Incorporate Zero Trust Solutions, Test And Troubleshoot, Secure Access Service Edge, Infrastructure Gaps using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Secure Access Service Edge Importance
SD WAN Model Secure Access Service Edge ImportanceThis slide represents the importance of secure access service edge. This slides purpose is to demonstrate why businesses need the SASE model. The main reasons include scaling with business needs, encouraging work from anywhere environment, standing up for cyber threats, and offering a base for IoT adoption. Introducing SD WAN Model Secure Access Service Edge Importance to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Scales With Business, Encourage Work From Anywhere, Network And Security, Compromising Business Security, using this template. Grab it now to reap its full benefits.
-
 SD WAN Model Secure Access Service Edge Sase Architecture
SD WAN Model Secure Access Service Edge Sase ArchitectureThis slide represents the SASE architecture overview and its goals. The purpose of this slide is to demonstrate the secure access service edge architecture and its goals. The building blocks of SASE architecture include SWG, CASB, ZTNA, FWaaS, SD-WAN, Thin Edge, and so on. Deliver an outstanding presentation on the topic using this SD WAN Model Secure Access Service Edge Sase Architecture. Dispense information and present a thorough explanation of Secure Access Service Edge, Architecture And Its Goals, Geographic Distribution using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SD WAN Model Secure Access Service Edge Training Program
SD WAN Model Secure Access Service Edge Training ProgramThis slide represents the training program for the secure access service edge model. The purpose of this slide is to demonstrate the teams eligible for training, the modules to be covered during the training, the schedule and venue of the training. Present the topic in a bit more detail with this SD WAN Model Secure Access Service Edge Training Program. Use it as a tool for discussion and navigation on Training Program, Secure Access Service Edge, Teams Eligible For Training, Modules To Be Covered. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SD WAN Model Secure Access Service Edge Use Cases
SD WAN Model Secure Access Service Edge Use CasesThis slide represents the use cases of secure access service edge within an organization. The purpose of this slide is to demonstrate the various use cases of the SASE model, including rapid response to network demand, support for IoT and edge computing, VPN replacement, performance assurance and so on. Increase audience engagement and knowledge by dispensing information using SD WAN Model Secure Access Service Edge Use Cases. This template helps you present information on six stages. You can also present information on Performance Assurance, Support For Multiple Operating Systems, Controlled Move To Cloud Services using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SD WAN Model Secure Web Gateway Swg Functional Components
SD WAN Model Secure Web Gateway Swg Functional ComponentsThis slide depicts the functional components of a secure web gateway, including their impact. The purpose of this slide is to demonstrate the required elements of SWG working. The main components include policy enforcement, data loss prevention, web proxy, malware detection, URL filtering, and so on. Deliver an outstanding presentation on the topic using this SD WAN Model Secure Web Gateway Swg Functional Components. Dispense information and present a thorough explanation of Data Loss Prevention, Policy Enforcement, Secure Web Gateway, Functional Components using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





