Powerpoint Templates and Google slides for Security Operation
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Operational Outlook Of Security Awareness Training Implementing Security Awareness Training
Operational Outlook Of Security Awareness Training Implementing Security Awareness TrainingThe purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Present the topic in a bit more detail with this Operational Outlook Of Security Awareness Training Implementing Security Awareness Training. Use it as a tool for discussion and navigation on Operational Outlook, Security Awareness, Training Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Operations Dashboard For Detection And Response Effectiveness
Security Operations Dashboard For Detection And Response EffectivenessThis slide exhibits security operations dashboard. It include positive incidents, false positive incidents, false positive risk score, false positive security incident etc. Introducing our Security Operations Dashboard For Detection And Response Effectiveness set of slides. The topics discussed in these slides are Security Operations Dashboard, Detection, Response Effectiveness. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
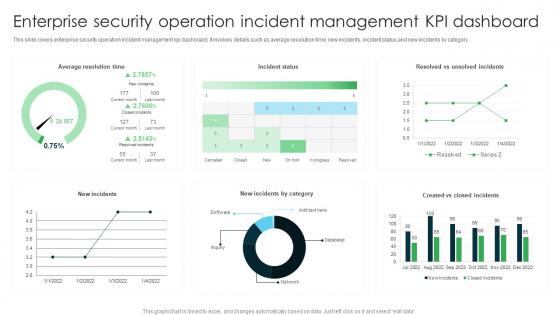 Enterprise Security Operation Incident Management Kpi Dashboard
Enterprise Security Operation Incident Management Kpi DashboardThis slide covers enterprise security operation incident management kpi dashboard. It involves details such as average resolution time, new incidents, incident status and new incidents by category. Presenting our well structured Enterprise Security Operation Incident Management Kpi Dashboard. The topics discussed in this slide are Average Resolution Time, Incident Status, Resolved Vs Unsolved Incidents. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 KPI Dashboard For Enterprise Security Operations
KPI Dashboard For Enterprise Security OperationsThis slide covers kpi dashboard for enterprise security operations. It involves details such as active alerts, active automated investigation, devices with major issues and report of daily devices. Introducing our KPI Dashboard For Enterprise Security Operations set of slides. The topics discussed in these slides are Security Health, Devices With Major Issues, Active Automated Investigations. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber Security
Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber SecurityThe purpose of this slide is to showcase the general outlook of cyber security awareness training software. The slide covers information about opened simulations, links clicked, reported, attachments opened, data entered etc. Present the topic in a bit more detail with this Operational Outlook Of Security Awareness Training Software Preventing Data Breaches Through Cyber Security. Use it as a tool for discussion and navigation on Finished Training, Awareness Factors, Training Software. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
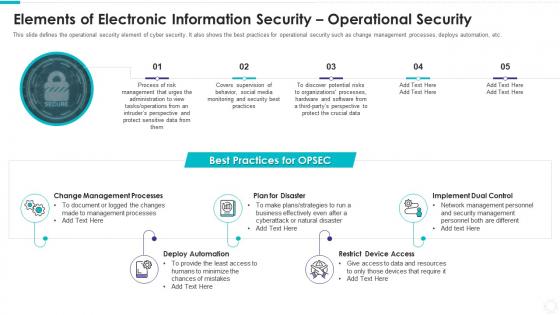 Elements of electronic information security operational security
Elements of electronic information security operational securityThis slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Increase audience engagement and knowledge by dispensing information using Elements Of Electronic Information Security Operational Security. This template helps you present information on five stages. You can also present information on Change Management Processes, Plan Disaster, Deploy Automation, Restrict Device Access, Implement Dual Control using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Electronic information security main steps of operational security
Electronic information security main steps of operational securityThis slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Introducing Electronic Information Security Main Steps Of Operational Security to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Define Sensitive Information, Identify Potential Threats, Analyze Security Holes And Vulnerabilities, Assessment Risks, Implementation Appropriate Countermeasures, using this template. Grab it now to reap its full benefits.
-
 Real time analysis of security alerts benchmarking with security operations maturity model
Real time analysis of security alerts benchmarking with security operations maturity modelThis slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Introducing Real Time Analysis Of Security Alerts Benchmarking With Security Operations Maturity Model to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Centralized Forensic Visibility, Mean Time To Detect, Mean Time To Respond, using this template. Grab it now to reap its full benefits.
-
 Successful siem strategies audit compliance benchmarking security operations maturity
Successful siem strategies audit compliance benchmarking security operations maturityThis slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Increase audience engagement and knowledge by dispensing information using Successful Siem Strategies Audit Compliance Benchmarking Security Operations Maturity. This template helps you present information on three stages. You can also present information on Improve Visibility, Quickly Identify Threats, Decrease Response Time using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Elements Of Information Security Operational Security
Information Security Elements Of Information Security Operational SecurityThis slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Present the topic in a bit more detail with this Information Security Elements Of Information Security Operational Security. Use it as a tool for discussion and navigation on Operational, Security, Elements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Steps Of Operational Security Information Security
Steps Of Operational Security Information SecurityThis slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Increase audience engagement and knowledge by dispensing information using Steps Of Operational Security Information Security. This template helps you present information on five stages. You can also present information on Main Steps Of Operational Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Development operations skills software security skills
Development operations skills software security skillsThis slide provides the glimpse about the software security skills such as security training, code analysis, change management, compliance monitoring, threat investigation, vulnerability management, etc. Introducing Development Operations Skills Software Security Skills to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Security Training, Code Analysis, Change Management, using this template. Grab it now to reap its full benefits.
-
 Benchmarking with security operations maturity model automating threat identification
Benchmarking with security operations maturity model automating threat identificationThis slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Introducing Benchmarking With Security Operations Maturity Model Automating Threat Identification to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Centralized Forensic Visibility, Mean Time To Detect, Mean Time To Respond, using this template. Grab it now to reap its full benefits.
-
 Improve it security with vulnerability benchmarking security operations maturity model
Improve it security with vulnerability benchmarking security operations maturity modelThis slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Introducing Improve It Security With Vulnerability Benchmarking Security Operations Maturity Model to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Improve Visibility, Quickly Identify Threats, Decrease Response Time, using this template. Grab it now to reap its full benefits.
-
 Network Security Main Steps Of Operational Security
Network Security Main Steps Of Operational SecurityThis slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Increase audience engagement and knowledge by dispensing information using Network Security Main Steps Of Operational Security. This template helps you present information on five stages. You can also present information on Sensitive Information, Potential Threats, Vulnerabilities, Implementation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 5 Operational Technology Security Controls To Improve It Security
5 Operational Technology Security Controls To Improve It SecurityFollowing slide depict operational technology OT security controls ways that can be used by an organization. Organization can enhance the security of IT infrastructure by using security controls such as update asset inventory, training, managing portable media, backup and restore and implementing secure configuration. Present the topic in a bit more detail with this 5 Operational Technology Security Controls To Improve IT Security. Use it as a tool for discussion and navigation on Update Asset Inventory, Training Manage, Portable Media, Backup And Restore, Secure Configuration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Checklist For Selecting Operational Technology Security Vendor
Checklist For Selecting Operational Technology Security VendorFollowing slide shows a comprehensive operational technology OT checklist which can be used by an organization for selecting the security vendor. organization can select the best security vendor for improving OT security system after considering points such as vendor understanding regard to OT and IT risk assessment etc. Deliver an outstanding presentation on the topic using this Checklist For Selecting Operational Technology Security Vendor. Dispense information and present a thorough explanation of Checklist, Vendor Understand OT, IT Risk Assessment, Digital Transformation Process using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Comparative Assessment Of Operational Technology Security Vendors
Comparative Assessment Of Operational Technology Security VendorsMentioned slide showcase various vendors who offers operational technology OT security solutions to business organizations. Organization can choose the best among security vendors by making comparison on the basis of features, deployment, operating systems, price and ratings. Present the topic in a bit more detail with this Comparative Assessment Of Operational Technology Security Vendors. Use it as a tool for discussion and navigation on Types Vendors, Key Features, Deployment, Operating Systems, Pricing In USD, Ratings. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Icon For Operational Technology Security
Icon For Operational Technology SecurityIntroducing Icon For Operational Technology Security to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Icon For Operational Technology Security, using this template. Grab it now to reap its full benefits.
-
 Operational Technology Icon For Security Threat Detection
Operational Technology Icon For Security Threat DetectionIntroducing Operational Technology Icon For Security Threat Detection to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Operational Technology Icon For Security Threat Detection, using this template. Grab it now to reap its full benefits.
-
 Operational Technology Security Challenges And Solutions To Overcome
Operational Technology Security Challenges And Solutions To OvercomeMentioned slide illustrates various operational technology OT security challenges. It also cover information about the multiple solutions which will assist organization to overcome challenges and build a strong security IT system. Introducing Operational Technology Security Challenges And Solutions To Overcome to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispence information on Challenges, Solutions, Employees, using this template. Grab it now to reap its full benefits.
-
 Operational Technology Security Services Offered By Vendors
Operational Technology Security Services Offered By VendorsMentioned slide illustrates operational technology OT services offered by vendors to business organizations. Information covered in this slide is related to services such as network operations, fabric connections, multi-cloud security, application security etc. Increase audience engagement and knowledge by dispensing information using Operational Technology Security Services Offered By Vendors. This template helps you present information on eight stages. You can also present information on Network Operations, Multi Cloud Security, Application Security, Fabric Connections, Information Security, Secure Access, Endpoint Protection, Fabric API using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Technology Security Main Steps Of Operational Security
Information Technology Security Main Steps Of Operational SecurityThis slide depicts the main steps of operational security, such as describing sensitive information, identifying potential risks, and so on, by showing how these steps are operating. Present the topic in a bit more detail with this Information Technology Security Main Steps Of Operational Security. Use it as a tool for discussion and navigation on Assessment Of Risks, Define Sensitive Information, Identify Potential Threats This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Security Operational Security
Information Technology Security Operational SecurityThis slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Increase audience engagement and knowledge by dispensing information using Information Technology Security Operational Security. This template helps you present information on five stages. You can also present information on Change Management, Processes, Deploy Automation using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Siem For Security Analysis Benchmarking With Security Operations Maturity Model
Siem For Security Analysis Benchmarking With Security Operations Maturity ModelThis slide focuses on the SOMM which measures the current security posture and understand the progress of operations readiness by visibility improvement, threats identification, etc. Introducing Siem For Security Analysis Benchmarking With Security Operations Maturity Model to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Improve Visibility, Decrease Response Time, Quickly Identify Threats, using this template. Grab it now to reap its full benefits.
-
 Elements Of Network Security Operational Security Ppt Styles Example File
Elements Of Network Security Operational Security Ppt Styles Example FileThis slide defines the operational security element of cyber security. It also shows the best practices for operational security such as change management processes, deploys automation, etc. Introducing Elements Of Network Security Operational Security Ppt Styles Example File to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Management, Sensitive, Administration, Operations, using this template. Grab it now to reap its full benefits.
-
 Company Operations In Us And Canada Home Security Systems Company Profile
Company Operations In Us And Canada Home Security Systems Company ProfileThis slide showcases the security company current operations in USA and Canada through map. It includes the total states covered of USA and Canada along which total served customers. Present the topic in a bit more detail with this Company Operations In Us And Canada Home Security Systems Company Profile . Use it as a tool for discussion and navigation on Company Operations In US And Canada. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Competitive Operations Financials Performance Analysis Home Security Systems Company Profile
Competitive Operations Financials Performance Analysis Home Security Systems Company ProfileThis slide highlights the security company competitive analysis which includes founding year, recurring monthly revenue, CSR initiatives, revenue, net profit and employee count. Deliver an outstanding presentation on the topic using this Competitive Operations Financials Performance Analysis Home Security Systems Company Profile . Dispense information and present a thorough explanation of Competitive, Operations, Performance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Smart Home Operating System Integration Home Security Systems Company Profile
Smart Home Operating System Integration Home Security Systems Company ProfileThis slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation. Deliver an outstanding presentation on the topic using this Smart Home Operating System Integration Home Security Systems Company Profile . Dispense information and present a thorough explanation of Smart Home Operating System Integration using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 F267 Strategies To Enhance Retail Store Security Retail Store Operations Performance Assessment
F267 Strategies To Enhance Retail Store Security Retail Store Operations Performance AssessmentThis slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms. Increase audience engagement and knowledge by dispensing information using F267 Strategies To Enhance Retail Store Security Retail Store Operations Performance Assessment. This template helps you present information on four stages. You can also present information on Technology, Surveillance, Strategies using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Information Security Operations Training Chart
Information Security Operations Training ChartThis slide covers employees training in organizations based on different security operations. It includes training based on security policy, incident management, security audit, cybersecurity, malware analysis, etc. Introducing our Information Security Operations Training Chart set of slides. The topics discussed in these slides are Information Security, Operations Training Chart. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Information Security Operations Training Icon
Information Security Operations Training IconIntroducing our premium set of slides with Information Security Operations Training Icon. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Information Security, Operations Training, Icon. So download instantly and tailor it with your information.
-
 Enterprise Security Lock Operations Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Enterprise Security Lock Operations Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Enterprise security lock operations colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Enterprise Security Lock Operations Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Enterprise Security Lock Operations Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Enterprise security lock operations monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Enterprise Security Operations Monitoring Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Enterprise Security Operations Monitoring Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Enterprise security operations monitoring colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Enterprise Security Operations Monitoring Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Enterprise Security Operations Monitoring Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Enterprise security operations monitoring monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Enterprise Security Operations Processing Colored Icon In Powerpoint Pptx Png And Editable Eps Format
Enterprise Security Operations Processing Colored Icon In Powerpoint Pptx Png And Editable Eps FormatGive your next presentation a sophisticated, yet modern look with this 100 percent editable Enterprise security operations processing colored icon in powerpoint pptx png and editable eps format. Choose from a variety of customizable formats such as PPTx, png, eps. You can use these icons for your presentations, banners, templates, One-pagers that suit your business needs.
-
 Enterprise Security Operations Processing Monotone Icon In Powerpoint Pptx Png And Editable Eps Format
Enterprise Security Operations Processing Monotone Icon In Powerpoint Pptx Png And Editable Eps FormatMake your presentation profoundly eye-catching leveraging our easily customizable Enterprise security operations processing monotone icon in powerpoint pptx png and editable eps format. It is designed to draw the attention of your audience. Available in all editable formats, including PPTx, png, and eps, you can tweak it to deliver your message with ease.
-
 Company Operations In Us And Canada Smart Security Systems Company Profile Ppt Show Format Ideas
Company Operations In Us And Canada Smart Security Systems Company Profile Ppt Show Format IdeasThis slide showcases the security company current operations in USA and Canada through map. It includes the total states covered of USA and Canada along which total served customers. Present the topic in a bit more detail with this Company Operations In Us And Canada Smart Security Systems Company Profile Ppt Show Format Ideas. Use it as a tool for discussion and navigation on Operations, Canadian Provinces, Customers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Competitive Operations And Financials Performance Analysis Smart Security Systems Company Profile
Competitive Operations And Financials Performance Analysis Smart Security Systems Company ProfileThis slide highlights the security company competitive analysis which includes founding year, recurring monthly revenue, CSR initiatives, revenue, net profit and employee count. Deliver an outstanding presentation on the topic using this Competitive Operations And Financials Performance Analysis Smart Security Systems Company Profile. Dispense information and present a thorough explanation of Competitive, Operations, Performance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Smart Home Operating System Integration Smart Security Systems Company Profile
Smart Home Operating System Integration Smart Security Systems Company ProfileThis slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation. Deliver an outstanding presentation on the topic using this Smart Home Operating System Integration Smart Security Systems Company Profile. Dispense information and present a thorough explanation of Integration, Automation, Technology using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Company Operations In Us And Canada Security Alarm And Monitoring Systems Company Profile
Company Operations In Us And Canada Security Alarm And Monitoring Systems Company ProfileThis slide showcases the security company current operations in USA and Canada through map. It includes the total states covered of USA and Canada along which total served customers. Present the topic in a bit more detail with this Company Operations In Us And Canada Security Alarm And Monitoring Systems Company Profile. Use it as a tool for discussion and navigation on Company, Operations, Customers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Competitive Operations And Financials Performance Security Alarm And Monitoring Systems Company Profile
Competitive Operations And Financials Performance Security Alarm And Monitoring Systems Company ProfileThis slide highlights the security company competitive analysis which includes founding year, recurring monthly revenue, CSR initiatives, revenue, net profit and employee count. Deliver an outstanding presentation on the topic using this Competitive Operations And Financials Performance Security Alarm And Monitoring Systems Company Profile. Dispense information and present a thorough explanation of Competitive, Operations, Performance using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Smart Home Operating System Integration Security Alarm And Monitoring Systems Company Profile
Smart Home Operating System Integration Security Alarm And Monitoring Systems Company ProfileThis slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation. Deliver an outstanding presentation on the topic using this Smart Home Operating System Integration Security Alarm And Monitoring Systems Company Profile. Dispense information and present a thorough explanation of Integration, Automation, Processing using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Managed Security Service Framework For Operations Management
Managed Security Service Framework For Operations ManagementThe flowing slide highlights managed security service framework. It provides information about components such as clients issues and key operations to be performed by service provider such as antivirus offerings, data loss prevention etc. Presenting our well structured Managed Security Service Framework For Operations Management. The topics discussed in this slide are Major Bottlenecks, Framework Significance, Business Security Users. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Securing Operations Of Logistics Through Integrated Enabling Smart Shipping And Logistics Through Iot
Securing Operations Of Logistics Through Integrated Enabling Smart Shipping And Logistics Through IotThis slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. Deliver an outstanding presentation on the topic using this Securing Operations Of Logistics Through Integrated Enabling Smart Shipping And Logistics Through Iot. Dispense information and present a thorough explanation of Potential Impact, Iot Security System, Securing Operations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
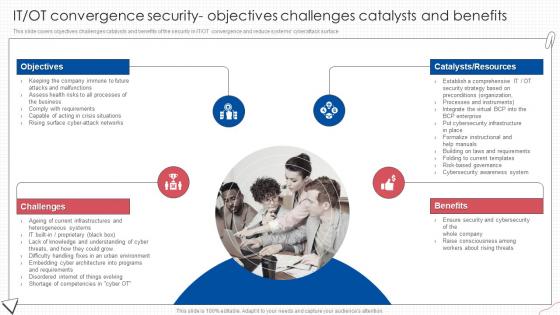 IT OT Convergence Security Objectives Digital Transformation Of Operational Industries
IT OT Convergence Security Objectives Digital Transformation Of Operational IndustriesThis slide covers objectives challenges catalysts and benefits of the security in IT OT convergence and reduce systems cyberattack surface.Introducing IT OT Convergence Security Objectives Digital Transformation Of Operational Industries to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Objectives, Benefits, Consciousness Among, using this template. Grab it now to reap its full benefits.
-
 Key Security Considerations For 5g For Threat Handling 5g Mobile Technology Guidelines Operators
Key Security Considerations For 5g For Threat Handling 5g Mobile Technology Guidelines OperatorsThis slide provides details regarding key security considerations associated to 5G in order to handle threats such as data breach, denial of service, unauthorized activities, etc. Deliver an outstanding presentation on the topic using this Key Security Considerations For 5g For Threat Handling 5g Mobile Technology Guidelines Operators. Dispense information and present a thorough explanation of Unauthorized Activities, Virtualization Threats, Information Interception using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Company Operations In Us And Canada Wireless Home Security Systems Company Profile
Company Operations In Us And Canada Wireless Home Security Systems Company ProfileThis slide showcases the security company current operations in USA and Canada through map. It includes the total states covered of USA and Canada along which total served customers. Increase audience engagement and knowledge by dispensing information using Company Operations In Us And Canada Wireless Home Security Systems Company Profile. This template helps you present information on one stages. You can also present information on Company Operations using this PPT design. This layout is completely editable so personalize it now to meet your audiences expectations
-
 Competitive Operations And Financials Wireless Home Security Systems Company Profile
Competitive Operations And Financials Wireless Home Security Systems Company ProfileThis slide highlights the security company competitive analysis which includes founding year, recurring monthly revenue, CSR initiatives, revenue, net profit and employee count. Deliver an outstanding presentation on the topic using this Competitive Operations And Financials Wireless Home Security Systems Company Profile. Dispense information and present a thorough explanation of Revenue, Recurring Monthly Revenue, Net Profit using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Smart Home Operating System Integration Wireless Home Security Systems Company Profile
Smart Home Operating System Integration Wireless Home Security Systems Company ProfileThis slide highlights the security company smart home operating system integration with all smart devices which includes real time event processing, and AI powered automation. Introducing Smart Home Operating System Integration Wireless Home Security Systems Company Profile to increase your presentation threshold. Encompassed with two stages, this template is a great option to educate and entice your audience. Dispense information on Smart Home Operating, System Integration, using this template. Grab it now to reap its full benefits.
-
 Implementing Iot Architecture In Shipping Business Securing Operations Of Logistics Through Integrated Iot
Implementing Iot Architecture In Shipping Business Securing Operations Of Logistics Through Integrated IotThis slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. Present the topic in a bit more detail with this Implementing Iot Architecture In Shipping Business Securing Operations Of Logistics Through Integrated Iot. Use it as a tool for discussion and navigation on Operations, Integrated, Workstation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Project Estimation Plan To Safeguard Business Operation
Cyber Security Project Estimation Plan To Safeguard Business OperationThis slide signifies the cyber security project evaluation plan for safeguarding organisation operations. It covers information regarding to the stages like initiation, planning, execution, implement and monitor. Introducing our premium set of slides with Cyber Security Project Estimation Plan To Safeguard Business Operation. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Initiation, Planning, Execution. So download instantly and tailor it with your information.
-
 Strategies To Improve Business Security Operations
Strategies To Improve Business Security OperationsThis slide shows various strategies which can be used by organizations to enhance business operations security. These strategies are detect endpoint threats, leverage advanced analytics and automate incident response. Presenting our set of slides with Strategies To Improve Business Security Operations. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Detect Endpoint Threats, Leverage Advanced Analytics, Automate Incident Response.
-
 Cyber Security Elements IT Operational Security Element Of Cyber Security Ppt Introduction
Cyber Security Elements IT Operational Security Element Of Cyber Security Ppt IntroductionThis slide defines the operational security element of cyber security. It also shows the best practices for operational security, such as changing management processes, deploying automation, planning for disasters, restricting device access, and implementing dual control. Increase audience engagement and knowledge by dispensing information using Cyber Security Elements IT Operational Security Element Of Cyber Security Ppt Introduction. This template helps you present information on five stages. You can also present information on Deploy Automation, Restrict Device Access, Change Management Processes using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda Enabling Automation In Cyber Security Operations Ppt Slides Background Images
Agenda Enabling Automation In Cyber Security Operations Ppt Slides Background ImagesIntroducing Agenda Enabling Automation In Cyber Security Operations Ppt Slides Background Images to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Environment, Business, Process, using this template. Grab it now to reap its full benefits.
-
 Criteria To Automate Security Analysis And Response Enabling Automation In Cyber Security Operations
Criteria To Automate Security Analysis And Response Enabling Automation In Cyber Security OperationsThis slide highlight the key criteria to automate the IT security which covers different questions related to tools deployment, set of activities, high time for security threat investigation and pressure from security threats. Present the topic in a bit more detail with this Criteria To Automate Security Analysis And Response Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Intervention, Malware Analysis, Automate. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security Operations
Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security OperationsThis slide highlights the different security automation tools which incudes robotic process automation. Security orchestration, automation and response, extended detection and SIEM. Present the topic in a bit more detail with this Different Security Automation Tools With Pros And Cons Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Information, Management, Automation. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Enabling Automation In Cyber Security Operations Determine Ideal Tasks For Security Automation
Enabling Automation In Cyber Security Operations Determine Ideal Tasks For Security AutomationThis slide highlights which tasks and activities can be automated and which required human insights to detect and prevent security threat. It also covers key takeaways section. Deliver an outstanding presentation on the topic using this Enabling Automation In Cyber Security Operations Determine Ideal Tasks For Security Automation. Dispense information and present a thorough explanation of Automation, Individual, Takeaways Section using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enabling Automation In Cyber Security Operations Domain Security Controls That Can Be Automated
Enabling Automation In Cyber Security Operations Domain Security Controls That Can Be AutomatedThis slide highlights the domain security controls that can be automated which includes security policy, asset management, human resources security, communications and operations management and access control domain. Present the topic in a bit more detail with this Enabling Automation In Cyber Security Operations Domain Security Controls That Can Be Automated. Use it as a tool for discussion and navigation on Communication, Management, Human Resources. This template is free to edit as deemed fit for your organization. Therefore download it now.





