Powerpoint Templates and Google slides for Security Operation
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Enabling Automation In Cyber Security Operations Table Of Contents Ppt Slides Infographic Template
Enabling Automation In Cyber Security Operations Table Of Contents Ppt Slides Infographic TemplateDeliver an outstanding presentation on the topic using this Enabling Automation In Cyber Security Operations Table Of Contents Ppt Slides Infographic Template. Dispense information and present a thorough explanation of Protection Platform, Security Automation, Processes using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Enterprise Network It Security Automation Enabling Automation In Cyber Security Operations
Enterprise Network It Security Automation Enabling Automation In Cyber Security OperationsThis slide highlights the network security automation which includes orchestrating network security, optimizing network security infrastructure, security policy automation and integration network with DevOps. Deliver an outstanding presentation on the topic using this Enterprise Network It Security Automation Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Orchestrating Network Security, Troubleshooting, Integrating Network using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security Operations
Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security OperationsThis slide highlights the External Data Representation layer for end security prevention and detection which includes endpoint protection, network protection, user protection and deceptio Increase audience engagement and knowledge by dispensing information using Extended Detection And Response For Endpoint Security Enabling Automation In Cyber Security Operations. This template helps you present information on four stages. You can also present information on Endpoint Protection, Network Protection, User Protection using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Icons Slide For Enabling Automation In Cyber Security Operations Ppt Slides Background Designs
Icons Slide For Enabling Automation In Cyber Security Operations Ppt Slides Background DesignsDeliver an outstanding presentation on the topic using this Icons Slide For Enabling Automation In Cyber Security Operations Ppt Slides Background Designs. Dispense information and present a thorough explanation of Icons using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security Operations
Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security OperationsThis slide highlights the impacts of ineffective information technology security at organization level which includes average cost of security, average time to identify data breach and total legitimate risks. Increase audience engagement and knowledge by dispensing information using Impacts Of Ineffective Information Technology Security Enabling Automation In Cyber Security Operations. This template helps you present information on four stages. You can also present information on Ineffective, Information, Technology using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Managed Detection And Response Layer For Expert Monitoring Enabling Automation In Cyber Security Operations
Managed Detection And Response Layer For Expert Monitoring Enabling Automation In Cyber Security OperationsThis slide highlights the slide Managed Detection and Response security layer which include alter monitoring, attack investigation, threat hunting, and incident response. Introducing Managed Detection And Response Layer For Expert Monitoring Enabling Automation In Cyber Security Operations to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Alert Monitoring, Attack Investigation, Threat Hunting, using this template. Grab it now to reap its full benefits.
-
 Measure Security Automation Metrics For Operations Efficiency Enabling Automation In Cyber Security Operations
Measure Security Automation Metrics For Operations Efficiency Enabling Automation In Cyber Security OperationsThis slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Present the topic in a bit more detail with this Measure Security Automation Metrics For Operations Efficiency Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Automation, Operations, Efficiency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Right Time To Add Automation In Security Enabling Automation In Cyber Security Operations
Right Time To Add Automation In Security Enabling Automation In Cyber Security OperationsThis slide depicts that what is the right time to invest in security automation it showcases failed human insights high time for resolution, high security breaches, no additional budget to hire security team. Present the topic in a bit more detail with this Right Time To Add Automation In Security Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Resolution, Automation, Human Insights. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations
Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security OperationsThis slide highlights the security automation platform which showcases its key features it also showcases the importance and value of security tools, people and system procedures. Present the topic in a bit more detail with this Security Automation Integrates Tools Systems And Processes Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Automation, Integrates, Processes. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Automation Stages With Maturity Level Enabling Automation In Cyber Security Operations
Security Automation Stages With Maturity Level Enabling Automation In Cyber Security OperationsThis slide highlights the security automation stages and maturity level which includes three stages opportunistic stage, systematic stage and institutionalized stage for orchestrate the process. Deliver an outstanding presentation on the topic using this Security Automation Stages With Maturity Level Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Security Automation, Services, Programmatic Workflow using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
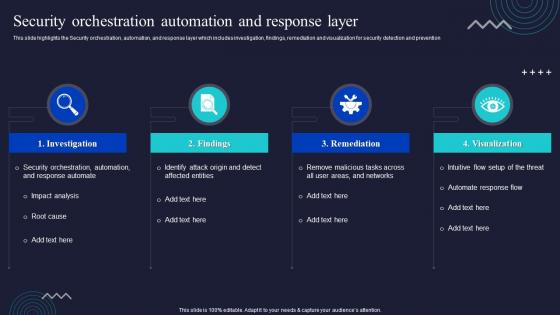 Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security Operations
Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security OperationsThis slide highlights the Security orchestration, automation, and response layer which includes investigation, findings, remediation and visualization for security detection and prevention Deliver an outstanding presentation on the topic using this Security Orchestration Automation And Response Layer Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Investigation, Remediation, Visualization using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Processes That Cant Be Automated Enabling Automation In Cyber Security Operations
Security Processes That Cant Be Automated Enabling Automation In Cyber Security OperationsThe following slide highlights the three processes of the security which cannot be automated which includes threat modeling, penetration testing and bug bounty program. Increase audience engagement and knowledge by dispensing information using Security Processes That Cant Be Automated Enabling Automation In Cyber Security Operations. This template helps you present information on three stages. You can also present information on Threat Modeling, Penetration Testing, Bug Bounty using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Table Of Contents Enabling Automation In Cyber Security Operations Ppt Slides Background Image
Table Of Contents Enabling Automation In Cyber Security Operations Ppt Slides Background ImageIntroducing Table Of Contents Enabling Automation In Cyber Security Operations Ppt Slides Background Image to increase your presentation threshold. Encompassed with eight stages, this template is a great option to educate and entice your audience. Dispence information on Security Automation, Architecture And Importance, Security Automation Dashboards, using this template. Grab it now to reap its full benefits.
-
 Unified Platform Integration For Security Automation Enabling Automation In Cyber Security Operations
Unified Platform Integration For Security Automation Enabling Automation In Cyber Security OperationsThis slide highlights the unifies platform integration for security automation which includes firewalls, intrusion prevention system, security information and event management and privileged access management. Present the topic in a bit more detail with this Unified Platform Integration For Security Automation Enabling Automation In Cyber Security Operations. Use it as a tool for discussion and navigation on Security Automation, Access Management, Platform Integration. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Why To Automate The It Security Process Enabling Automation In Cyber Security Operations
Why To Automate The It Security Process Enabling Automation In Cyber Security OperationsThis slide highlights the benefits or importance of automation security process which includes better threat detection, faster containment, improve productivity, admin role delegation and incident response. Increase audience engagement and knowledge by dispensing information using Why To Automate The It Security Process Enabling Automation In Cyber Security Operations. This template helps you present information on five stages. You can also present information on Better Threat Detection, Faster Containment, Improve Productivity using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Security Automation Architecture With Key Elements Enabling Automation In Cyber Security Operations
Security Automation Architecture With Key Elements Enabling Automation In Cyber Security OperationsThis slide showcases the architecture of security automation which includes security automation logs, security admin, policy server, active directory, reputation feeds and other data sources. Deliver an outstanding presentation on the topic using this Security Automation Architecture With Key Elements Enabling Automation In Cyber Security Operations. Dispense information and present a thorough explanation of Automation, Architecture, Sources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Measure Security Automation Metrics For Operations Security Automation To Investigate And Remediate Cyberthreats
Measure Security Automation Metrics For Operations Security Automation To Investigate And Remediate CyberthreatsThis slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Present the topic in a bit more detail with this Measure Security Automation Metrics For Operations Security Automation To Investigate And Remediate Cyberthreats. Use it as a tool for discussion and navigation on Measure, Automation, Operations Efficiency. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Measure Security Automation Metrics For Operations Efficiency Security Automation In Information Technology
Measure Security Automation Metrics For Operations Efficiency Security Automation In Information TechnologyThis slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Present the topic in a bit more detail with this Measure Security Automation Metrics For Operations Efficiency Security Automation In Information Technology. Use it as a tool for discussion and navigation on Automation, Operations Efficiency, Performance Improvements. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Deploying Internet Logistics Efficient Operations Securing Operations Of Logistics Through Integrated Iot
Deploying Internet Logistics Efficient Operations Securing Operations Of Logistics Through Integrated IotThis slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc. Present the topic in a bit more detail with this Deploying Internet Logistics Efficient Operations Securing Operations Of Logistics Through Integrated Iot. Use it as a tool for discussion and navigation on Operations, Logistics, Potential Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Iot Security Lock For Safe Fleet Management Deploying Internet Logistics Efficient Operations
Iot Security Lock For Safe Fleet Management Deploying Internet Logistics Efficient OperationsThe following slide illustrates internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR code, power saving, alarm notifications, large memory, etc. Introducing Iot Security Lock For Safe Fleet Management Deploying Internet Logistics Efficient Operations to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Four Unlocking Methods, Multiple Positioning Methods, Multiple Alarm Notification, using this template. Grab it now to reap its full benefits.
-
 Strategy To Provide Layered Security Across Networks Deploying Internet Logistics Efficient Operations
Strategy To Provide Layered Security Across Networks Deploying Internet Logistics Efficient OperationsThis slide showcases strategy to provide layered security across networks. It provides information about user level, device level, network level, risk, malware, vulnerabilities, unusual traffic, access points, user authentication, etc. Deliver an outstanding presentation on the topic using this Strategy To Provide Layered Security Across Networks Deploying Internet Logistics Efficient Operations. Dispense information and present a thorough explanation of Strategy, Information, Authentication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Securing Operations Of Logistics Through Integrated IOT Using IOT Technologies For Better Logistics
Securing Operations Of Logistics Through Integrated IOT Using IOT Technologies For Better LogisticsThis slide showcases securing operations of logistics through integrated internet of things IoT. It provides details such as field network, automation network, process network, operations, operating system, remote access, etc.Deliver an outstanding presentation on the topic using this Securing Operations Of Logistics Through Integrated IOT Using IOT Technologies For Better Logistics. Dispense information and present a thorough explanation of System Integration, Management Capabilities, Quicker Decision using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Strategies To Enhance Retail Store Security Analysis Of Retail Store Operations Efficiency
Strategies To Enhance Retail Store Security Analysis Of Retail Store Operations EfficiencyThis slide provides information regarding the strategies to enhance retail store security such as integrate access control technology, deploy video surveillance, utilizes electronic article surveillance, install monitored alarms. Increase audience engagement and knowledge by dispensing information using Strategies To Enhance Retail Store Security Analysis Of Retail Store Operations Efficiency. This template helps you present information on four stages. You can also present information on Integrate Access Control Technology, Utilizes Electronic Article Surveillance, Install Monitored Alarm using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Multistep Process For Automating Cloud Security Operations
Multistep Process For Automating Cloud Security OperationsThe following slide highlights four step process of cloud security automation. The various steps are container configure management, using infrastructure as code, automating asset tagging and vulnerability scanning where security analysts should implement automation. Introducing our premium set of slides with Multistep Process For Automating Cloud Security Operations. Elucidate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Container Configure Management, Infrastructure As Code, Vulnerability Scanning. So download instantly and tailor it with your information.
-
 Automated Enterprise Security Operation Icon
Automated Enterprise Security Operation IconPresenting our set of slides with Automated Enterprise Security Operation Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Automated Enterprise, Security Operation Icon.
-
 Comparison Assessment Of Enterprise Security Operations Tools
Comparison Assessment Of Enterprise Security Operations ToolsThis slide covers comparison assessment of enterprise security operations tools. It involves features such as vulnerability management, penetration testing and privacy standard compliance. Introducing our Comparison Assessment Of Enterprise Security Operations Tools set of slides. The topics discussed in these slides are Features, Cost Involved, User Rating. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Enterprise Cyber Security Operation Icon
Enterprise Cyber Security Operation IconIntroducing our premium set of slides with Enterprise Cyber Security Operation Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Enterprise Cyber Security, Operation Icon. So download instantly and tailor it with your information.
-
 Enterprise Data Security Operation Center System
Enterprise Data Security Operation Center SystemThis slide covers enterprise data security operation center system to ensure better safety. It involves six stages collection, transmission, storage, processing, exchange and destruction. Presenting our set of slides with Enterprise Data Security Operation Center System. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Collection, Transmission, Processing .
-
 Enterprise Security Operation Center Audit Checklist
Enterprise Security Operation Center Audit ChecklistThis slide covers enterprise security operation center audit checklist. It involves vulnerability scan, employee cyber training, security provisions, asset management policy and network segmentation procedures. Introducing our Enterprise Security Operation Center Audit Checklist set of slides. The topics discussed in these slides are Employee Cyber Training Guide, Vulnerability Scan And Analysis, Incident Response Policy. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Enterprise Security Operation Center Best Practices
Enterprise Security Operation Center Best PracticesThis slide covers enterprise security operation center best practices. It involves practices such as setting up right time, align strategy with business goals, leverage best tools and continuously monitor network. Presenting our well structured Enterprise Security Operation Center Best Practices. The topics discussed in this slide are Leverage Best Tools, Continuously Monitor Network, Business Goals. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Enterprise Security Operation Center Icon
Enterprise Security Operation Center IconIntroducing our premium set of slides with Enterprise Security Operation Center Icon. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Enterprise Security Operation, Center Icon. So download instantly and tailor it with your information.
-
 Enterprise Security Operation Center Process
Enterprise Security Operation Center ProcessThis slide covers enterprise security operation center process. It involves monitoring, basic investigation, mitigation, threat hunting, counter intelligence and advanced investigations. Introducing our Enterprise Security Operation Center Process set of slides. The topics discussed in these slides are Security Intelligence Platform, Help Desks, Monitoring. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Enterprise Security Operation Center System
Enterprise Security Operation Center SystemThis slide covers enterprise security operation center system. It involves business security, data security, infrastructure, office network and application security. Presenting our well structured Enterprise Security Operation Center System. The topics discussed in this slide are Business Security, Data Security, Application Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Enterprise Security Operation Center Team Roles And Responsibilities
Enterprise Security Operation Center Team Roles And ResponsibilitiesThis slide covers enterprise security operation center team roles and responsibilities. It involves key roles such as incident responder, security investigator, advanced security analyst and SOC manager. Introducing our Enterprise Security Operation Center Team Roles And Responsibilities set of slides. The topics discussed in these slides are Security Investigator, Incident Responder, Advanced Security Analyst. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Enterprise Security Operation Center To Enhance Safety
Enterprise Security Operation Center To Enhance SafetyThis slide covers enterprise security operation center to enhance safety. It involves log collection, reporting, research and development, threat intelligence and aggregation. Presenting our set of slides with Enterprise Security Operation Center To Enhance Safety. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Knowledge Base, Ticketing, Log Collection.
-
 Enterprise Security Operation Model To Build Secure Organization
Enterprise Security Operation Model To Build Secure OrganizationThis slide covers enterprise security operation model to build secure organization. It involves regulatory requirements, customer expectations, industry forums and internal business demands. Introducing our premium set of slides with Enterprise Security Operation Model To Build Secure Organization. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Regulatory Requirements, Customer Expectations, Industry Norms. So download instantly and tailor it with your information.
-
 Enterprise Security Operation System Icon
Enterprise Security Operation System IconPresenting our set of slides with Enterprise Security Operation System Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Enterprise Security Operation, System Icon.
-
 Enterprise Security Operations Center Framework
Enterprise Security Operations Center FrameworkThis slide covers enterprise security operations center framework. It involves five stages such as discovery, preliminary investigation, triage, extended investigation and respond. Introducing our premium set of slides with Enterprise Security Operations Center Framework. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Preliminary Investigation, Extended Investigation, Triage. So download instantly and tailor it with your information.
-
 Evolution Of Enterprise Security Operation Center
Evolution Of Enterprise Security Operation CenterThis slide covers evolution of enterprise security operation center. It involves availability monitoring, reactive monitoring, proactive monitoring and monitoring with automation. Introducing our Evolution Of Enterprise Security Operation Center set of slides. The topics discussed in these slides are Reactive Monitoring, Availability Monitoring, Proactive Monitoring. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Inclusion Of Automation In Enterprise Security Operations
Inclusion Of Automation In Enterprise Security OperationsThis slide covers inclusion of automation in enterprise security operations. It involves key roles such as automation, security analysts, incident responder, threat hunter and security operation manager. Presenting our well structured Inclusion Of Automation In Enterprise Security Operations. The topics discussed in this slide are Security Analyst, Incident Responder, Security Operation Manager. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Key Strategies For Enhancing Enterprise Security Operations
Key Strategies For Enhancing Enterprise Security OperationsThis slide covers key strategies for enhancing enterprise security operations. It involves strategies such as detect endpoint threats, leverage advanced analytics and automate incident response. Introducing our premium set of slides with Key Strategies For Enhancing Enterprise Security Operations. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Detect Endpoint Threats, Leverage Advanced Analytics, Automate Incident Response. So download instantly and tailor it with your information.
-
 Role Of Automation In Improving Enterprise Security Operation
Role Of Automation In Improving Enterprise Security OperationThis slide covers role of automation in improving enterprise security operation. It involves AI powered threat detection, integrated threat intelligence and alert validation and noise reduction. Presenting our set of slides with Role Of Automation In Improving Enterprise Security Operation. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on AI Powered Threat Detection, Integrated Threat Intelligence, Alert Validation And Noise Reduction.
-
 Why Enterprise Security Operation Center Is Required
Why Enterprise Security Operation Center Is RequiredThis slide covers need of enterprise security operation center. It involves reasons such as continuous monitoring, centralized visibility, reduced cybersecurity costs and ensures better collaboration. Introducing our premium set of slides with Why Enterprise Security Operation Center Is Required. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Continuous Monitoring, Centralized Visibility, Reduced Cybersecurity Costs. So download instantly and tailor it with your information.
-
 Enterprise Cyber security Operation Monitoring Framework
Enterprise Cyber security Operation Monitoring FrameworkThis slide covers enterprise cyber security operation monitoring framework. It involves five functions such as identify, protect, detect, respond and recover. Presenting our well structured Enterprise Cybersecurity Operation Monitoring Framework. The topics discussed in this slide are Cybersecurity Outcomes, Service Areas, Identify. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Security Orchestration Automation Measure Security Automation Metrics For Operations Efficiency
Security Orchestration Automation Measure Security Automation Metrics For Operations EfficiencyThis slide highlights the security automation metrics for operation efficiency which includes time to remediation, operation performance improvements, sensor value and workflow effectiveness metrics. Present the topic in a bit more detail with this Security Orchestration Automation Measure Security Automation Metrics For Operations Efficiency. Use it as a tool for discussion and navigation on Operational Performance, Deployment Readiness, System Utilization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Information Technology Operations Security Icon
Information Technology Operations Security IconPresenting our set of slides with name Information Technology Operations Security Icon. This exhibits information on three stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Information Technology, Operations Security, Icon.
-
 Cloud Security Maturity Model Assessment To Improve Business Operations
Cloud Security Maturity Model Assessment To Improve Business OperationsThis slide represents cloud security maturity assessment model which helps improve cloud optimization and flexibility. It provides information regarding automation, manual scripts, managed stage and optimization. Introducing our premium set of slides with Cloud Security Maturity Model Assessment To Improve Business Operations. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Automation Optimized, Minimal Automation, Minimal Automation. So download instantly and tailor it with your information.
-
 Operational Technology Cyber Security In Powerpoint And Google Slides Cpb
Operational Technology Cyber Security In Powerpoint And Google Slides CpbPresenting our Operational Technology Cyber Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Operational Technology Cyber Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber Security Risk Governance Operating Model
Cyber Security Risk Governance Operating ModelThe slide showcases an operating model of cyber security risk governance to address business threats. It includes key elements like governance, risk management and compliance. Introducing our Cyber Security Risk Governance Operating Model set of slides. The topics discussed in these slides are Governance, Risk, Compliance. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Security Risk Governance Operating Model
Security Risk Governance Operating ModelThe following slide highlights a risk governance operating model to manage impacts of risk on IT assets. It includes key activities like risks identification, protection, detection, reaction, awareness and compliance and assurance. Presenting our set of slides with Security Risk Governance Operating Model. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information onProtection, Detection, Reaction.
-
 Best Tools For Security Operations Secops Ppt Powerpoint Presentation Diagram Templates
Best Tools For Security Operations Secops Ppt Powerpoint Presentation Diagram TemplatesThis slide represents the best security operations tools for the year 2023. The purpose of this slide is to showcase the various prominent tools for SecOps, including Grafana, StackStorm, GRR Rapid Response, Chef Inspec, and Alerta. Deliver an outstanding presentation on the topic using this Best Tools For Security Operations Secops Ppt Powerpoint Presentation Diagram Templates. Dispense information and present a thorough explanation of Grafana, Stackstorm using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Introduction To Secops Security Operations Ppt Powerpoint Presentation File Pictures
Introduction To Secops Security Operations Ppt Powerpoint Presentation File PicturesThis slide outlines the introduction to security operations. The purpose of this slide is to give an overview of SecOps, including its goals, benefits, and critical functions. The functions include security monitoring, threat intelligence, triage and investigation, incident response, and forensics and root cause analysis. Introducing Introduction To Secops Security Operations Ppt Powerpoint Presentation File Pictures to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Overview, Benefits, Functions, using this template. Grab it now to reap its full benefits.
-
 Roles And Responsibilities Of Security Operations Center Team Ppt Professional
Roles And Responsibilities Of Security Operations Center Team Ppt ProfessionalThis slide outlines the roles and responsibilities of the security operations center team. The purpose of this slide is to showcase the roles as well as duties of the SOC team. The prominent roles include incident responder, security investigator, advanced security analyst, SOC manager, and security engineer. Increase audience engagement and knowledge by dispensing information using Roles And Responsibilities Of Security Operations Center Team Ppt Professional. This template helps you present information on five stages. You can also present information on Incident Responder, Security Investigator using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 SecOps Challenges And Solutions Of Security Operations Centres Ppt Download
SecOps Challenges And Solutions Of Security Operations Centres Ppt DownloadThis slide outlines the key challenges and solutions of security operations centers. The purpose of this slide is to highlight the problems faced by SOC teams and methods to overcome those problems. The main challenges include talent gaps, sophisticated attackers, increased data and network traffic, etc. Deliver an outstanding presentation on the topic using this SecOps Challenges And Solutions Of Security Operations Centres Ppt Download. Dispense information and present a thorough explanation of Talent Gap, Sophisticated Attackers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SecOps Conceptual Architecture Of Security Operations Center Ppt Brochure
SecOps Conceptual Architecture Of Security Operations Center Ppt BrochureThis slide describes the conceptual architecture of the security operations center. The purpose of this slide is to highlight the architecture of SecOps and the elements that formalize the architecture. The main components include network taps, operating systems, apps, security elements, etc. Deliver an outstanding presentation on the topic using this SecOps Conceptual Architecture Of Security Operations Center Ppt Brochure. Dispense information and present a thorough explanation of Network Taps, Operating System using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SecOps Key Outcomes Manage By Security Operations Team Ppt Pictures
SecOps Key Outcomes Manage By Security Operations Team Ppt PicturesThis slide outlines the critical outcomes that are handled by the security operations team. The purpose of this slide is to demonstrate the various key outcomes, their activities, responsible person and remarks. The main outcomes include incident management, incident preparation and threat intelligence. Deliver an outstanding presentation on the topic using this SecOps Key Outcomes Manage By Security Operations Team Ppt Pictures. Dispense information and present a thorough explanation of Incident Management, Incident Preparation using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 SecOps Key Responsibilities Of Command Security Operations Center Ppt Slides
SecOps Key Responsibilities Of Command Security Operations Center Ppt SlidesThis slide depicts the main tasks of the command security operations center. The purpose of this slide is to highlight the main responsibilities, responsible team members, and task status. The main tasks include monitoring and analyzing security events, coordinating incident response, managing security operations, etc. Present the topic in a bit more detail with this SecOps Key Responsibilities Of Command Security Operations Center Ppt Slides. Use it as a tool for discussion and navigation on Coordinating Incident Response, Responsible Team Members. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SecOps Main Responsibilities Of Security Operations Center Soc
SecOps Main Responsibilities Of Security Operations Center SocThis slide describes the different responsibilities of a secure operations center. The purpose of this slide is to showcase the multiple functions SOC teams perform, including communication with DevOps teams, coordinating incident response process, incident investigation, and prioritization of threats. Introducing SecOps Main Responsibilities Of Security Operations Center Soc to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Communication, Incident Investigation, using this template. Grab it now to reap its full benefits.
-
 SecOps Security Operations Center Teams Ppt Powerpoint Presentation Portfolio Aids
SecOps Security Operations Center Teams Ppt Powerpoint Presentation Portfolio AidsThis slide describes the team structure of the security operations center. The purpose of this slide is to showcase the team hierarchy of SOC and it includes teams, their tasks and the name of the team members. The primary units include triage, investigation, and hunters. Present the topic in a bit more detail with this SecOps Security Operations Center Teams Ppt Powerpoint Presentation Portfolio Aids. Use it as a tool for discussion and navigation on Description, Team Members. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 SecOps Security Operations Model And Incidents Management Ppt Diagrams
SecOps Security Operations Model And Incidents Management Ppt DiagramsThis slide represents the security operations model, covering the incidents managed by the security operations center. The model includes three teams such as hunters, investigators, and triage. The incidents include multi stage incidents, known campaign tracking, and high volume incidents. Deliver an outstanding presentation on the topic using this SecOps Security Operations Model And Incidents Management Ppt Diagrams. Dispense information and present a thorough explanation of Threat Intelligence, External Intelligence Sources using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.





