Powerpoint Templates and Google slides for Security Management
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Strategic Cyber Security Management Objectives
Strategic Cyber Security Management ObjectivesFollowing slide showcases implementation of cyber security management in an organization for employee awareness. It further covers related measures, due date, strategies such as availability, threats, authority management and access control, etc. Introducing our Strategic Cyber Security Management Objectives set of slides. The topics discussed in these slides are Cyber Security Management Objectives, Authority Management, Access Control. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Supply Chain Cyber Security Risk Management Plan
Supply Chain Cyber Security Risk Management PlanThis slide includes cyber security management plan which can be used by supply chain managers to manage security threats. It includes various strategies such as upgrade minimum security baseline, assess process for further risks, and educate employees. Presenting our well structured Supply Chain Cyber Security Risk Management Plan. The topics discussed in this slide are Supervisor, Action Required, Mitigation Strategy. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Tokenization For Improved Data Security Governance And Risk Management In Cloud Based Systems
Tokenization For Improved Data Security Governance And Risk Management In Cloud Based SystemsThis slide discusses the management and risk mitigation in cloud-based systems. The purpose of this slide is to showcase the elements on which tokenization depend, importance of governance and objectives of categorization. Deliver an outstanding presentation on the topic using this Tokenization For Improved Data Security Governance And Risk Management In Cloud Based Systems. Dispense information and present a thorough explanation of Governance And Risk Management, Cloud Based Systems, During Categorization Organization Must using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cloud Based Endpoint Cyber Security Management Services
Cloud Based Endpoint Cyber Security Management ServicesThis slide showcases multiple facets of endpoint cyber security management. The purpose of this slide is to help businesses in implementing cost effective and agile solution to ensure strong network security. It covers services such as analytics, reporting, intrusion prevention, cloud services security, antivirus audit, etc. Presenting our set of slides with Cloud Based Endpoint Cyber Security Management Services This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Discovery, Spyware Blocking, Application Patching
-
 Data Destruction Techniques For Securely Disposing Data Lifecycle Management To Enhance Flow
Data Destruction Techniques For Securely Disposing Data Lifecycle Management To Enhance FlowThis slide presents various data destruction techniques for securely disposing of data. It provides details about techniques such as, overwriting, degussing, physical destruction, cryptographic erasure and secure erase. Present the topic in a bit more detail with this Data Destruction Techniques For Securely Disposing Data Lifecycle Management To Enhance Flow. Use it as a tool for discussion and navigation on Physical Destruction, Cryptographic Erasure, Secure Erase, Data Destruction Technique. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Integrating Algorithms For Encrypting Data Securely Data Lifecycle Management To Enhance Flow
Integrating Algorithms For Encrypting Data Securely Data Lifecycle Management To Enhance FlowThis slide presents algorithms for encrypting data to ensure its protection and security. It includes types such as, AES advanced encryption standard and RSA rivest-shamir-adleman and ECC elliptic curve cryptography. Present the topic in a bit more detail with this Integrating Algorithms For Encrypting Data Securely Data Lifecycle Management To Enhance Flow. Use it as a tool for discussion and navigation on Encryption Algorithm, Key Characteristics, Implementation In Organization. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Overview Of Archival Stage To Ensure Secure Data Lifecycle Management To Enhance Flow
Overview Of Archival Stage To Ensure Secure Data Lifecycle Management To Enhance FlowThis stage presents an overview of the archival data stage to optimizes how necessary resources perform in the active system. It includes information about goals and benefits such as minimizing cost, enhanced backup and restore performance and decrease in data loss. Present the topic in a bit more detail with this Overview Of Archival Stage To Ensure Secure Data Lifecycle Management To Enhance Flow. Use it as a tool for discussion and navigation on Data Archive Storage Devices, Long-Term Retention And Storage Of Data, Cost-Effective Information Storage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Attack Vulnerability Icon For Security Management
Cyber Attack Vulnerability Icon For Security ManagementPresenting our set of slides with Cyber Attack Vulnerability Icon For Security Management This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Cyber Attack Vulnerability, Security Management
-
 Shield Lock Security Icon For Vulnerability Management
Shield Lock Security Icon For Vulnerability ManagementIntroducing our premium set of slides with Shield Lock Security Icon For Vulnerability Management Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Shield Lock Security, Vulnerability Management So download instantly and tailor it with your information.
-
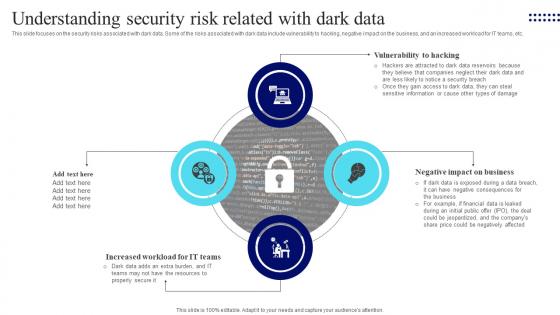 Management Of Redundant Data Understanding Security Risk Related With Dark Data
Management Of Redundant Data Understanding Security Risk Related With Dark DataThis slide focuses on the security risks associated with dark data. Some of the risks associated with dark data include vulnerability to hacking, negative impact on the business, and an increased workload for IT teams, etc. Introducing Management Of Redundant Data Understanding Security Risk Related With Dark Data to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Increased Workload For IT Teams, Negative Impact On Business, Vulnerability To Hacking, using this template. Grab it now to reap its full benefits.
-
 Best Practices For Website Security Management Comprehensive E Commerce Website
Best Practices For Website Security Management Comprehensive E Commerce WebsiteThe following slide showcases best practices that can be used by businesses to protect websites from cyber-attacks and threats. It includes pointers such as incest in SSL certifications, anti-malware programs, regular backups, etc. Increase audience engagement and knowledge by dispensing information using Best Practices For Website Security Management Comprehensive E Commerce Website This template helps you present information on Four stages. You can also present information on Invest In SSL Certificate, Implement Anti Malware Programs using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Website Design Security Management Strategic Plan Comprehensive E Commerce Website
Website Design Security Management Strategic Plan Comprehensive E Commerce WebsiteFollowing slide outlines website security action plan to assure safety from external threats and cybercrimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Deliver an outstanding presentation on the topic using this Website Design Security Management Strategic Plan Comprehensive E Commerce Website Dispense information and present a thorough explanation of Set Strong Passwords, Try New Configurations using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Website Security Management Strategic Plan Comprehensive E Commerce Website
Website Security Management Strategic Plan Comprehensive E Commerce WebsiteFollowing slide outlines website security action plan to assure safety from external threats and cybercrimes. It include steps such as strong passwords, new configurations, mitigate DDOS, safety from SQL, hide website version etc. Increase audience engagement and knowledge by dispensing information using Website Security Management Strategic Plan Comprehensive E Commerce Website This template helps you present information on Five stages. You can also present information on Strategy, Responsible Person, Priority Status using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Assessing Data Storage Options To Ensure Securely Data Lifecycle Management To Enhance Flow
Assessing Data Storage Options To Ensure Securely Data Lifecycle Management To Enhance FlowThis slide presents the types of data storage technologies for data lifecycle management. It provides information about, relational , non-relational, object storage and cloud storage databases. Present the topic in a bit more detail with this Assessing Data Storage Options To Ensure Securely Data Lifecycle Management To Enhance Flow. Use it as a tool for discussion and navigation on Relational Databases, Object Storage, Cloud Data Storage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Physical Security Information Management Across Various Industries
Physical Security Information Management Across Various IndustriesThis slide showcases physical security information management solutions. It includes vendors, system integrations, applications such as retail, BFSI, energy and utility, transportations and hospitality. Presenting our well structured Physical Security Information Management Across Various Industries. The topics discussed in this slide are Vendors, System Integration, Physical Security Information. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
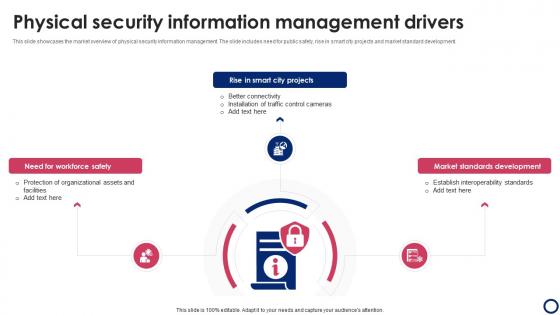 Physical Security Information Management Drivers
Physical Security Information Management DriversThis slide showcases the market overview of physical security information management. The slide includes need for public safety, rise in smart city projects and market standard development. Introducing our premium set of slides with Physical Security Information Management Drivers. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Market Standards Development, Need Workforce Safety, Rise Smart. So download instantly and tailor it with your information.
-
 Mobile Device Management Icon For Security Measures
Mobile Device Management Icon For Security MeasuresIntroducing our premium set of slides with Mobile Device Management Icon For Security Measures. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Management, Security, Measures. So download instantly and tailor it with your information.
-
 Mobile Device Management Practices For Security Enhancement
Mobile Device Management Practices For Security EnhancementThis slide represents mobile device management practices including passcodes, anti-virus software and enforcing updates. Presenting our well structured Mobile Device Management Practices For Security Enhancement. The topics discussed in this slide are Passcodes, Anti Virus Software, Enforcing Updates. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Alternative For Managing Cyber Threats Business Recovery Plan To Overcome Cyber Security Threat
Alternative For Managing Cyber Threats Business Recovery Plan To Overcome Cyber Security ThreatIncrease audience engagement and knowledge by dispensing information using Alternative For Managing Cyber Threats Business Recovery Plan To Overcome Cyber Security Threat. This template helps you present information on five stages. You can also present information on Staff Training, End Point Protection, Wifi Security using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security Threat
Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about system patch management to determine vulnerabilities after cyber attack. It includes key process of automated patch management and best practices such as schedule patching, prioritization, and patch testing. Deliver an outstanding presentation on the topic using this Automated Patch Management Process Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Management, Process, Vulnerability using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Case Study Construction Management Company Business Recovery To Overcome Cyber Security Threat
Case Study Construction Management Company Business Recovery To Overcome Cyber Security ThreatMentioned slide provides information about a case study related to a ransomware attack on the construction company. It includes key elements such as situation detail, adopted strategies, and outcomes. Deliver an outstanding presentation on the topic using this Case Study Construction Management Company Business Recovery To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Construction, Management, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Setting Goals For Cyber Attack Management Business Recovery Plan To Overcome Cyber Security Threat
Setting Goals For Cyber Attack Management Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about time-based goals set for cyber attack management. It includes goals such as mean time to detect incidents, containment time, resolution time, and recovery time. Introducing Setting Goals For Cyber Attack Management Business Recovery Plan To Overcome Cyber Security Threat to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Mean Time To Contain, Mean Time To Resolve, Mean Time To Recover, using this template. Grab it now to reap its full benefits.
-
 Information Security Emergency Management Plan
Information Security Emergency Management PlanThis slide covers the information security management plan control by using firewall, backup drives and encrypted technology. Presenting our well structured Information Security Emergency Management Plan. The topics discussed in this slide are Compensation Control, Duration Required, Impact Level This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Securing Food Safety In Online Restaurant Online Order Management System
Securing Food Safety In Online Restaurant Online Order Management SystemThis slide covers integrating online order management software to track details such as bill number, order ID, customer name, amount paid and status. Present the topic in a bit more detail with this Securing Food Safety In Online Restaurant Online Order Management System. Use it as a tool for discussion and navigation on Duration, Channel, Preparing, Ready For Delivery. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Securing Food Safety In Online Utilizing Food Delivery Management System
Securing Food Safety In Online Utilizing Food Delivery Management SystemThis slide covers utilizing food delivery management software to keep track of deliveries. It involves bill number, channel and estimated duration. Introducing Securing Food Safety In Online Utilizing Food Delivery Management System to increase your presentation threshold. Encompassed with One stages, this template is a great option to educate and entice your audience. Dispence information on Bill Number, Channel, Customer Location, Estimated Duration, using this template. Grab it now to reap its full benefits.
-
 Regtech Icon For Efficient Data Management And Security
Regtech Icon For Efficient Data Management And SecurityIntroducing our premium set of slides with name Regtech Icon For Efficient Data Management And Security. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Regtech Icon, Efficient Data, Management And Security. So download instantly and tailor it with your information.
-
 Wealth Management Strategies Secure Retirement Planning With Key Fin SS V
Wealth Management Strategies Secure Retirement Planning With Key Fin SS VThis slide shows information which can be utilized to know basics of retirement planning. It also includes details about key activities included in retirement planning which are lifestyle assessment, income projection, etc. Introducing Wealth Management Strategies Secure Retirement Planning With Key Fin SS V to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Lifestyle Assessment, Retirement Income Projection, Savings Strategies, Pension Optimization, using this template. Grab it now to reap its full benefits.
-
 E Commerce Subscription Data Security Management Techniques
E Commerce Subscription Data Security Management TechniquesThis slide highlights the techniques to secure e-commerce subscription data to ensure data protection and management for trust building. Key strategies are encryption strategy, hand-on monitoring, and contingency planning. Introducing our premium set of slides with E Commerce Subscription Data Security Management Techniques Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Encryption Strategy, Hands-On Monitoring, Contingency Planning So download instantly and tailor it with your information.
-
 Incident Response And Security Management Training Plan
Incident Response And Security Management Training PlanThe purpose of this slide is to ensure quick and effective response to security incidents. It lays out incident response and security management training plan covering elements such as lesson, date, mode of training, duration and trainer. Presenting our well structured Incident Response And Security Management Training Plan The topics discussed in this slide are Mode Of Training, Duration, TrainerThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
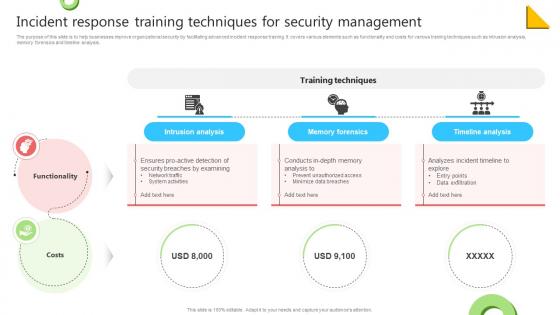 Incident Response Training Techniques For Security Management
Incident Response Training Techniques For Security ManagementThe purpose of this slide is to help businesses improve organizational security by facilitating advanced incident response training. It covers various elements such as functionality and costs for various training techniques such as intrusion analysis, memory forensics and timeline analysis. Introducing our premium set of slides with Incident Response Training Techniques For Security Management Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Intrusion Analysis, Memory Forensics, Timeline Analysis So download instantly and tailor it with your information.
-
 Blockchain Security Trends In Project Management
Blockchain Security Trends In Project ManagementThis slide exhibits the various security trends of blockchain technology in project management that helps to prevent data breaches and optimize the transactional process. The major trends are record management, asset exchange, and performance management. Presenting our set of slides with Blockchain Security Trends In Project Management. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Record Management, Asset Exchange, Performance Optimization.
-
 Secure Retirement Planning With Key Activities Wealth Management Techniques Fin SS V
Secure Retirement Planning With Key Activities Wealth Management Techniques Fin SS VThis slide shows information which can be utilized to know basics of retirement planning. It also includes details about key activities included in retirement planning which are lifestyle assessment, income projection, etc. Introducing Secure Retirement Planning With Key Activities Wealth Management Techniques Fin SS V to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Income Projection, Savings Strategies using this template. Grab it now to reap its full benefits.
-
 Access Management Components Authentication Securing Systems With Identity
Access Management Components Authentication Securing Systems With IdentityThis slide gives an overview of access management of the Identity and Access Management process. The purpose of this slide is to explain access management that primarily focuses on authentication and authorization. Increase audience engagement and knowledge by dispensing information using Access Management Components Authentication Securing Systems With Identity This template helps you present information on Two stages. You can also present information on Authentication, Authorization using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Agenda For Securing Systems With Identity And Access Management
Agenda For Securing Systems With Identity And Access ManagementIntroducing Agenda For Securing Systems With Identity And Access Management to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Agenda using this template. Grab it now to reap its full benefits.
-
 Architecture Of Identity And Access Management Process Securing Systems With Identity
Architecture Of Identity And Access Management Process Securing Systems With IdentityThis slide discusses the architecture structure of the Identity and Access Management process. The purpose of this slide is to explain the architecture of IAM that is capable of offering multiple data views and enables single sign-on. Present the topic in a bit more detail with this Architecture Of Identity And Access Management Process Securing Systems With Identity Use it as a tool for discussion and navigation on Internet, Corporate Demilitarized Zone, Customers Partners This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Basic Capabilities Of Identity And Access Management System Securing Systems With Identity
Basic Capabilities Of Identity And Access Management System Securing Systems With IdentityThis slide discusses the Identity and Access Management basic capabilities. The purpose of this slide is to explain the various capabilities of IAM these are identity management, user provisioning and de-provisioning, authentication, and so on. Deliver an outstanding presentation on the topic using this Basic Capabilities Of Identity And Access Management System Securing Systems With Identity Dispense information and present a thorough explanation of Identity Management, User Provisioning using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Before Vs After Impact Of Identity And Access Management Securing Systems With Identity
Before Vs After Impact Of Identity And Access Management Securing Systems With IdentityThis slide showcases the comparative analysis of the before versus after IAM implementation. The purpose of this slide is to discuss the different performance aspects and how IAM has proved beneficial for these aspects. Present the topic in a bit more detail with this Before Vs After Impact Of Identity And Access Management Securing Systems With Identity Use it as a tool for discussion and navigation on Aspect, Self Registration, Policy Enforcement This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Benefits Of Identity And Access Management System Securing Systems With Identity
Benefits Of Identity And Access Management System Securing Systems With IdentityThis slide highlights the Identity and Access Management benefits. The purpose of this slide is to discuss the various advantages these include proper access for the right people, unhindered productivity, protection from data breaches, data encryption, etc. Deliver an outstanding presentation on the topic using this Benefits Of Identity And Access Management System Securing Systems With Identity Dispense information and present a thorough explanation of Collaboration And Efficiency, Data Encryption using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Checklist To Implement Identity And Access Management Securing Systems With Identity
Checklist To Implement Identity And Access Management Securing Systems With IdentityThis slide represents the checklist to implement the Identity and Access Management plan in an organization. The purpose of this slide is to provide key functional requirements for implementing and deploying IAM in an enterprise environment. Deliver an outstanding presentation on the topic using this Checklist To Implement Identity And Access Management Securing Systems With Identity Dispense information and present a thorough explanation of Iam Policy And Strategy, User Lifecycle Management using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Components Of Identity And Access Management Process Securing Systems With Identity
Components Of Identity And Access Management Process Securing Systems With IdentityThis slide discusses the Identity and Access Management components. The purpose of this slide is to highlight the various components, including the IAM framework, access and roles, IAM system function, centralized directory services, and so on. Introducing Components Of Identity And Access Management Process Securing Systems With Identity to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Iam Framework Purpose, Access And Roles, Iam System Functions using this template. Grab it now to reap its full benefits.
-
 Concepts Of Identity And Access Management Securing Systems With Identity
Concepts Of Identity And Access Management Securing Systems With IdentityThis slide discusses the terms Identity and Access Management individually. The purpose of this slide is to explain that identity and access are two parts that govern how your users interact with data and applications across your information systems, networks, databases, and software. Increase audience engagement and knowledge by dispensing information using Concepts Of Identity And Access Management Securing Systems With Identity This template helps you present information on Three stages. You can also present information on Identity, Access, Entitlements using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Core Services Of Identity And Access Management Securing Systems With Identity
Core Services Of Identity And Access Management Securing Systems With IdentityThis slide discusses the Identity and Access Management core services. The purpose of this slide is to highlight the core services of IAM these include identifying, authentication, authorizing, auditing, and verifying the accounts. Introducing Core Services Of Identity And Access Management Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Identification, Authentication, Authorization using this template. Grab it now to reap its full benefits.
-
 Customer Identity And Access Management Vs IAM Securing Systems With Identity
Customer Identity And Access Management Vs IAM Securing Systems With IdentityThis slide showcases the comparison of Customer Identity and Access Management and the Identity and Access Management process. The purpose of this slide is to highlight the purpose and features of the CIAM and IAM process. Deliver an outstanding presentation on the topic using this Customer Identity And Access Management Vs IAM Securing Systems With Identity Dispense information and present a thorough explanation of Ciam Software, Iam Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data Analytics Importance In Identity And Access Management Securing Systems With Identity
Data Analytics Importance In Identity And Access Management Securing Systems With IdentityThis slide showcases the importance of Identity and Access Management based data analytics. The purpose of this slide is to explain the benefits, which are anomaly detection, account monitoring, policy violation detection, and so on. Increase audience engagement and knowledge by dispensing information using Data Analytics Importance In Identity And Access Management Securing Systems With Identity This template helps you present information on Five stages. You can also present information on Anomaly Detection, Identity Certification Campaigns using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Examples Of Identity And Access Management Securing Systems With Identity
Examples Of Identity And Access Management Securing Systems With IdentityThis slide highlights the Identity and Access Management examples. The purpose of this slide is to discuss the examples these include multi-factor authentication tools, access provisioning and de-provisioning, and user monitoring for access control. Introducing Examples Of Identity And Access Management Securing Systems With Identity to increase your presentation threshold. Encompassed with Three stages, this template is a great option to educate and entice your audience. Dispence information on Authentication Tools, Provisioning And Deprovisioning, Monitoring For Access Control using this template. Grab it now to reap its full benefits.
-
 Features Of Identity And Access Management Process Securing Systems With Identity
Features Of Identity And Access Management Process Securing Systems With IdentityThis slide discusses the Identity and Access Management features. The purpose of this slide is to explain the various features, including stored information authentication and authorization, external user registration, and so on. Present the topic in a bit more detail with this Features Of Identity And Access Management Process Securing Systems With Identity Use it as a tool for discussion and navigation on Stored Information, External User Registration This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Framework Of Identity And Access Management Process Securing Systems With Identity
Framework Of Identity And Access Management Process Securing Systems With IdentityThis slide discusses the Identity and Access Management framework. The purpose of this slide is to highlight the procedure that includes outlining how IAM architecture components work together, define user access to resources, and so on. Increase audience engagement and knowledge by dispensing information using Framework Of Identity And Access Management Process Securing Systems With Identity This template helps you present information on Eight stages. You can also present information on Employee Movements, Security Threat Reduction, Standard Framework using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Functions Of Identity And Access Management Process Securing Systems With Identity
Functions Of Identity And Access Management Process Securing Systems With IdentityThis slide discusses the Identity and Access Management process functions. The purpose of this slide is to highlight the various functions, including identification in the system, roles in the design, assigning access levels, protecting sensitive data, and so on. Introducing Functions Of Identity And Access Management Process Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Identification In System, Roles In System using this template. Grab it now to reap its full benefits.
-
 Fundamentals Of Identity And Access Management Securing Systems With Identity
Fundamentals Of Identity And Access Management Securing Systems With IdentityThis slide discusses the fundamentals of the Identity and Access Management process. The purpose of this slide is to highlight the fundamental concepts of IAM, including authentication, authorization, administration, and audit. Increase audience engagement and knowledge by dispensing information using Fundamentals Of Identity And Access Management Securing Systems With Identity This template helps you present information on Five stages. You can also present information on Authentication, Authorization, Administration using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Historical Evolution Of Identity And Access Management Securing Systems With Identity
Historical Evolution Of Identity And Access Management Securing Systems With IdentityThis slide discusses the Identity and Access Management historical evolution. The purpose of this slide is to explain the historical background of IAM, including the historical roots of IAM, early IAM solutions, the role of tools, challenges with the directory, and so on. Introducing Historical Evolution Of Identity And Access Management Securing Systems With Identity to increase your presentation threshold. Encompassed with Six stages, this template is a great option to educate and entice your audience. Dispence information on Historical Roots Of Iam, Early Iam Solutions, Role Of Tools using this template. Grab it now to reap its full benefits.
-
 Icons Slide For Securing Systems With Identity And Access Management
Icons Slide For Securing Systems With Identity And Access ManagementIntroducing our well researched set of slides titled Icons Slide For Securing Systems With Identity And Access Management It displays a hundred percent editable icons. You can use these icons in your presentation to captivate your audiences attention. Download now and use it multiple times.
-
 Identity And Access Management Challenges And Solutions Securing Systems With Identity
Identity And Access Management Challenges And Solutions Securing Systems With IdentityThis slide highlights the challenges associated with IAM. The purpose of this slide is to discuss the solutions provided to different challenges related to IAM. These include distributed workforce, distributed application, productive provisioning, BYOD, etc. Present the topic in a bit more detail with this Identity And Access Management Challenges And Solutions Securing Systems With Identity Use it as a tool for discussion and navigation on Challenges, Description, Solutions This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Introduction And Functions Securing Systems With Identity
Identity And Access Management Introduction And Functions Securing Systems With IdentityThis slide gives an overview of the Identity and Access Management process. The purpose of this slide is to explain the IAM and its functions in ensuring authentication, reporting, authorization, workflow, access management, and so on. Introducing Identity And Access Management Introduction And Functions Securing Systems With Identity to increase your presentation threshold. Encompassed with Five stages, this template is a great option to educate and entice your audience. Dispence information on Company Data And Resources, Streamline Workflows using this template. Grab it now to reap its full benefits.
-
 Identity And Access Management Process In Workplace Securing Systems With Identity
Identity And Access Management Process In Workplace Securing Systems With IdentityThis slide discusses the Identity and Access Management process in the workplace. The purpose of this slide is to highlight the various usages of IAM in the workplace these include increasing the number of applications, managing identity data, and complex access scenarios. Increase audience engagement and knowledge by dispensing information using Identity And Access Management Process In Workplace Securing Systems With Identity This template helps you present information on Three stages. You can also present information on Increasing Number Of Applications, Managing Identity Data using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Identity And Access Management Technologies And Tools Securing Systems With Identity
Identity And Access Management Technologies And Tools Securing Systems With IdentityThis slide discusses the tools and technologies used in the Identity and Access Management process. The purpose of this slide is to highlight the various tools, which are security assertion markup language, open ID connect, and a system for cross-domain identity management. Present the topic in a bit more detail with this Identity And Access Management Technologies And Tools Securing Systems With Identity Use it as a tool for discussion and navigation on Saml, Oidc, Scim This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Training Schedule For Staff Securing Systems With Identity
Identity And Access Management Training Schedule For Staff Securing Systems With IdentityThis slide represents the training schedule for staff in the Identity and Access Management. The purpose of this slide is to manage and monitor IAM training procedures. It includes the time slots for training, the total days of training, and the modules to be covered in the training. Deliver an outstanding presentation on the topic using this Identity And Access Management Training Schedule For Staff Securing Systems With Identity Dispense information and present a thorough explanation of Policies And Procedures, Infrastructure And Software using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Identity And Access Management Working Functions Securing Systems With Identity
Identity And Access Management Working Functions Securing Systems With IdentityThis slide discusses the working process of Identity and Access Management . The purpose of this slide is to explain the workflow of the IAM this includes identity management that validates login attempts and access management that manages the entitys access. Introducing Identity And Access Management Working Functions Securing Systems With Identity to increase your presentation threshold. Encompassed with Two stages, this template is a great option to educate and entice your audience. Dispence information on Identity Management, Access Management using this template. Grab it now to reap its full benefits.
-
 Impact Of Identity And Access Management On Business Securing Systems With Identity
Impact Of Identity And Access Management On Business Securing Systems With IdentityThis slide represents the Identity and Access Management impact on organization. The purpose of this slide is to highlight the impact associated with IAM for business which are enhances security, regularity compliance and so on. Deliver an outstanding presentation on the topic using this Impact Of Identity And Access Management On Business Securing Systems With Identity Dispense information and present a thorough explanation of Enhanced Security, Cost Savings using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Major Focus Areas Of Identity And Access Management Securing Systems With Identity
Major Focus Areas Of Identity And Access Management Securing Systems With IdentityThis slide discusses the Identity and Access Management focus area. The purpose of this slide is to explain the focus area of IAM these include access management, privilege management, and identity governance. Increase audience engagement and knowledge by dispensing information using Major Focus Areas Of Identity And Access Management Securing Systems With Identity This template helps you present information on Three stages. You can also present information on Access Management, Privilege Management, Identity Governance using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Need For The Identity And Access Management Securing Systems With Identity
Need For The Identity And Access Management Securing Systems With IdentityThis slide discusses the requirement for Identity and Access Management process. The purpose of this slide is to highlight the needs these include secure user access, strong authentication, IAM solutions, IAM tasks, an evolving IT environment, etc. Present the topic in a bit more detail with this Need For The Identity And Access Management Securing Systems With Identity Use it as a tool for discussion and navigation on Secure User Access, Strong Authentication This template is free to edit as deemed fit for your organization. Therefore download it now.





