Powerpoint Templates and Google slides for Security Management
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Network Security Management Market Snapshot
Network Security Management Market SnapshotThis slide showcases the network security management referable for users, investors and business owners for making relevant industry decisions. It include details such as rising cyber threats at network point to improve demand for security solutions, etc. Presenting our well structured Network Security Management Market Snapshot. The topics discussed in this slide are Driving Factors, Juniper Networks, Improve Demand. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Statistics Showcasing Network Security Management Challenges
Statistics Showcasing Network Security Management ChallengesThis slide showcases the statistics showcasing security management challenges which help an organization to find solutions for them and avoid further attacks. It include details such as communicate effectively, negotiate and compromise, etc. Introducing our Statistics Showcasing Network Security Management Challenges set of slides. The topics discussed in these slides are Communicate Effectively, Negotiate And Compromise, Learn Improve. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Smart Water Management Security And Privacy Challenges Associated With Iot Water Management IoT SS
Smart Water Management Security And Privacy Challenges Associated With Iot Water Management IoT SSThe following slide showcases various security challenges which can be faced by companies while deploying Internet of Things IoT water management system. The PPT covers information about data privacy, third-party integrations, physical security, and software update. Introducing Smart Water Management Security And Privacy Challenges Associated With Iot Water Management IoT SS to increase your presentation threshold. Encompassed with Four stages, this template is a great option to educate and entice your audience. Dispence information on Smart Water Management Key Benefits Of Using Iot In Water Management IoT SS using this template. Grab it now to reap its full benefits.
-
 Firewall Network Security Best Practices For Firewall Security Management
Firewall Network Security Best Practices For Firewall Security ManagementThis slide outlines the checklist for managing firewall protection effectively. The purpose of this slide is to showcase the different best practices that businesses should keep in mind while managing a firewall, including automating firewall updates, regular firewall security audits, creating and optimizing network-based firewall policies, etc. Present the topic in a bit more detail with this Firewall Network Security Best Practices For Firewall Security Management Use it as a tool for discussion and navigation on Automate Firewall Updates, Security Audits This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Challenges Associated With IoT Inventory How IoT In Inventory Management Streamlining IoT SS
Security Challenges Associated With IoT Inventory How IoT In Inventory Management Streamlining IoT SSThe following slide outlines various safety and security issues which are associated with Internet of Things IoT inventory management. It covers detailed information about data privacy, third-party integrations, physical security, and software update. Introducing Security Challenges Associated With IoT Inventory How IoT In Inventory Management Streamlining IoT SS to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Data Privacy, Physical Security, Software Update, using this template. Grab it now to reap its full benefits.
-
 Challenges Faced By Network Media Teams In Managing Security Issues
Challenges Faced By Network Media Teams In Managing Security IssuesThis slide depicts challenges faced by network media in solving security issues to safeguard digital assets and ensure the integrity, confidentiality, and availability of media content. Introducing our Challenges Faced By Network Media Teams In Managing Security Issues set of slides. The topics discussed in these slides are Measures, Performance, Functionality. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Triage Cyber Security For Vulnerability Management Dashboard
Triage Cyber Security For Vulnerability Management DashboardThis slide represents triage cyber security for vulnerability management dashboard which assist to identify and prevent system vulnerabilities. It includes key components such as latest scans, tracker, etc Introducing our Triage Cyber Security For Vulnerability Management Dashboard set of slides. The topics discussed in these slides are Most Vulnerable Hosts, Vulnerabilities Status This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
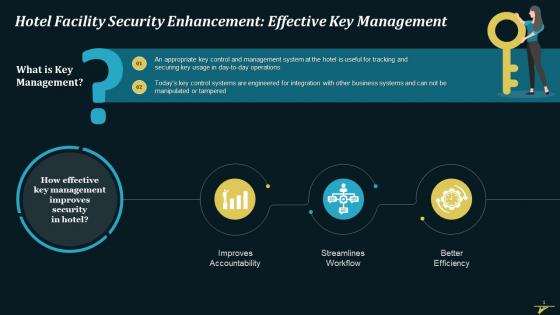 Enhanced Hotel Facility Security With Effective Key Management Training Ppt
Enhanced Hotel Facility Security With Effective Key Management Training PptPresenting Enhanced Hotel Facility Security with Effective Key Management. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizablealter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 KPI Dashboard For Tracking Risk Management In IP Security
KPI Dashboard For Tracking Risk Management In IP SecurityThis slide showcases dashboard for tracking IP security. The main purpose of this template is to showcase risk and analysis of risk. This includes analysis of risk, response of risk, vulnerabilities, entities, etc. Presenting our well structured KPI Dashboard For Tracking Risk Management In IP Security. The topics discussed in this slide are KPI Dashboard, Tracking Risk, Management, IP Security. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 KPI Dashboard For Cyber Security Risk Management Evaluation
KPI Dashboard For Cyber Security Risk Management EvaluationFollowing slide represents cyber security risk management and evaluation KPI dashboard for prevention of cyberattacks. It further covers total risks, severe risks, top risks in industry cyber security, controls assess, average control gap, etc. Presenting our well structured KPI Dashboard For Cyber Security Risk Management Evaluation. The topics discussed in this slide are Identity-Based Cloud Security Threats, Remote Working Risks, Mobile Security Attacks. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Major Cyber Threats Management Strategies Business Recovery Plan To Overcome Cyber Security Threat
Major Cyber Threats Management Strategies Business Recovery Plan To Overcome Cyber Security ThreatMentioned slide provides information about various strategies adopted by company for preventing cyber attacks. It includes key threats such as ransomware, malware, phishing, and denial of service. Deliver an outstanding presentation on the topic using this Major Cyber Threats Management Strategies Business Recovery Plan To Overcome Cyber Security Threat. Dispense information and present a thorough explanation of Management, Strategies, Ransomware using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Budget For Identity And Access Management Training Securing Systems With Identity
Budget For Identity And Access Management Training Securing Systems With IdentityThis slide showcases the breakdown cost for the IAM installation and management training for the customers. The purpose of this slide is to showcase the training cost breakdown for different components such as instructor cost, training cost, etc. Present the topic in a bit more detail with this Budget For Identity And Access Management Training Securing Systems With Identity Use it as a tool for discussion and navigation on Components, Training Cost Distribution This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Identity And Access Management Insights Reporting Dashboard Securing Systems With Identity
Identity And Access Management Insights Reporting Dashboard Securing Systems With IdentityThis slide represents the reporting dashboard of the Identity and Access Management process. The purpose of this slide is to showcase the IAM insights reporting dashboard, and the components include syslog errors, system checks, failed task results, etc. Deliver an outstanding presentation on the topic using this Identity And Access Management Insights Reporting Dashboard Securing Systems With Identity Dispense information and present a thorough explanation of Failed Task Results, Syslog Errors, Certifications Trends using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Us Identity And Access Management Market Size Securing Systems With Identity
Us Identity And Access Management Market Size Securing Systems With IdentityThis slide depicts the US IAM market size in global market. The purpose of this slide is to highlight the US market size of the IAM process in terms of revenue generation and compound annual growth rate. Deliver an outstanding presentation on the topic using this Us Identity And Access Management Market Size Securing Systems With Identity Dispense information and present a thorough explanation of Provisioning Access, Compromising Security using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
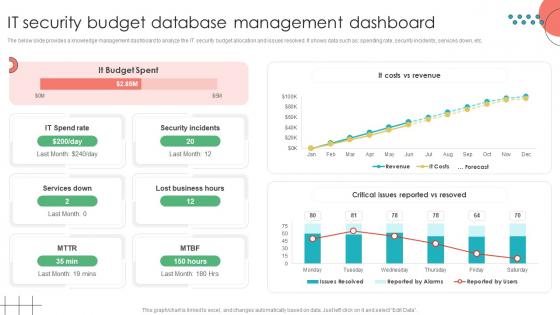 IT Security Budget Database Management Dashboard
IT Security Budget Database Management DashboardThe below slide provides a knowledge management dashboard to analyze the IT security budget allocation and issues resolved. It shows data such as spending rate, security incidents, services down, etc. Presenting our well structured IT Security Budget Database Management Dashboard The topics discussed in this slide are Security Incidents, Lost Business HoursThis is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
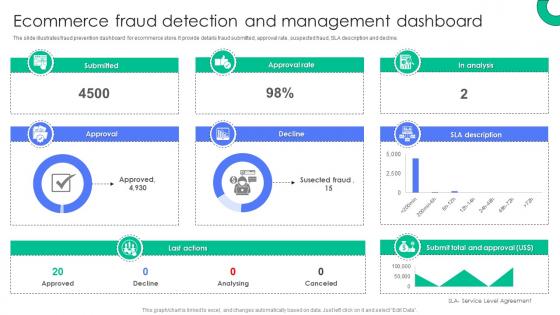 Ecommerce Fraud Detection And Management Dashboard Implementing E Commerce Security Measures
Ecommerce Fraud Detection And Management Dashboard Implementing E Commerce Security MeasuresThe slide illustrates fraud prevention dashboard for ecommerce store. It provide details fraud submitted, approval rate, suspected fraud, SLA description and decline. Present the topic in a bit more detail with this Ecommerce Fraud Detection And Management Dashboard Implementing E Commerce Security Measures. Use it as a tool for discussion and navigation on Submitted, Approval, Approval Rate, Decline, Last Actions. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SS
Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SSThis slide showcases managing endpoint security access management through just in time method. It provides details about access request, permission duration, etc.Present the topic in a bit more detail with this Just In Time For Access Management Building Next Generation Endpoint Security Cybersecurity SS. Use it as a tool for discussion and navigation on Access Request, Our Process, Potential Impact. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Email Security Best Practices Advanced Email Security Management Dashboard
Email Security Best Practices Advanced Email Security Management DashboardThis slide represents the dashboard to track email security incident management process. The purpose of this slide is to provide a graphical representation of email traffic, mitigation summary, unsolicited emails, advanced threat prevention, etc. Present the topic in a bit more detail with this Email Security Best Practices Advanced Email Security Management Dashboard. Use it as a tool for discussion and navigation on Email Traffic, Blocked Summary, Mitigation Summary, Advanced Threat Prevention, Data Loss Prevention, Unsolicited Emails. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 E mail safeguard industry report managed e mail security ppt slides images
E mail safeguard industry report managed e mail security ppt slides imagesThis slide displays the overview and key features of managed E Mail Security. Deliver an outstanding presentation on the topic using this E Mail Safeguard Industry Report Managed E Mail Security Ppt Slides Images. Dispense information and present a thorough explanation of E Mail Delivery, E Mail Security, Provides Organization, Multiple Systems using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Data security it managing data security 60 days plan ppt slides introduction
Data security it managing data security 60 days plan ppt slides introductionThis slide represents the plan for 60 days after implementing the data security model in the organization. Present the topic in a bit more detail with this Data Security IT Managing Data Security 60 Days Plan Ppt Slides Introduction. Use it as a tool for discussion and navigation on Time to Detect Incident, Policy Violations, Data Loss Incidents, Infected Computers. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Data security it managing data security 90 days plan ppt slides icons
Data security it managing data security 90 days plan ppt slides iconsThis slide depicts the 90 days plan of the data security model in an organization and training compliance and methods used for communication. Deliver an outstanding presentation on the topic using this Data Security IT Managing Data Security 90 Days Plan Ppt Slides Icons. Dispense information and present a thorough explanation of Training Completion, Communication Methods, Policy Sign Off using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
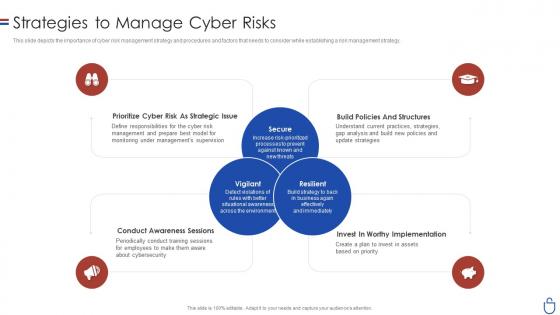 Data security it strategies to manage cyber risks ppt slides clipart images
Data security it strategies to manage cyber risks ppt slides clipart imagesThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Introducing Data Security IT Strategies To Manage Cyber Risks Ppt Slides Clipart Images to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Prioritize Cyber Risk As Strategic Issue, Conduct Awareness Sessions, Invest Worthy Implementation, Build Policies And Structures, using this template. Grab it now to reap its full benefits.
-
 Computer system security managing computer security 90 days plan
Computer system security managing computer security 90 days planThis slide depicts the 90 days plan of the cyber security model in an organization and training compliance and methods used for communication. Deliver an outstanding presentation on the topic using this Computer System Security Managing Computer Security 90 Days Plan. Dispense information and present a thorough explanation of Training Completion, Communication Methods, Policy Sign Off, Measures using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Computer system security managing computer security 60 days plan
Computer system security managing computer security 60 days planThis slide represents the plan for 60 days after implementing the cyber security model in the organization. Present the topic in a bit more detail with this Computer System Security Managing Computer Security 60 Days Plan. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders, Facility Physical Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Computer system security strategies to manage cyber risks
Computer system security strategies to manage cyber risksThis slide depicts the importance of cyber risk management strategy and procedures and factors that needs to consider while establishing a risk management strategy. Introducing Computer System Security Strategies To Manage Cyber Risks to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Secure, Vigilant, Resilient, Implementation, Awareness, using this template. Grab it now to reap its full benefits.
-
 Managing computer security 30 days plan computer system security
Managing computer security 30 days plan computer system securityPresent the topic in a bit more detail with this Managing Computer Security 30 Days Plan Computer System Security. Use it as a tool for discussion and navigation on Phishing Awareness, Phishing Reporting, Phishing Repeat Offenders, Facility Physical Security. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 IoT Security Lock For Supply Chain Management
IoT Security Lock For Supply Chain ManagementThe following slide illustrates the Internet of things IoT security lock for safe fleet management. It provides information about unlocking methods, Bluetooth, QR codes, power saving, alarm notifications, large memory, etc. Introducing our premium set of slides with IoT Security Lock For Supply Chain Management. Ellicudate the Four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Four Unlocking Methods, Multiple Positioning Methods. So download instantly and tailor it with your information.
-
 Risk Management Cyber Security In Powerpoint And Google Slides Cpb
Risk Management Cyber Security In Powerpoint And Google Slides CpbPresenting our Risk Management Cyber Security In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Risk Management Cyber Security This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Enterprise Security Product Management Framework
Enterprise Security Product Management FrameworkThe following slide highlights product management framework for security products. It include various stages that are market segmentation, product capabilities, sales engagement, pricing model and product delivery. Presenting our set of slides with Enterprise Security Product Management Framework. This exhibits information on five stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Segmentation, Capabilities, Engagement.
-
 Play 11 Administering Security And Privacy Through Reusable Digital Service Management Playbook
Play 11 Administering Security And Privacy Through Reusable Digital Service Management PlaybookThis slide provides information regarding digital services play which helps in managing security and privacy through reusable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc. Present the topic in a bit more detail with this Play 11 Administering Security And Privacy Through Reusable Digital Service Management Playbook. Use it as a tool for discussion and navigation on Procedures, Administering, Service. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Cyber Security Management Quarterly Action Plan
Cyber Security Management Quarterly Action PlanThis slide represents quarterly action plan of cyber security management for protecting customer data. It further includes steps such as evaluate cyber security risks, prioritize cyber risks, etc Presenting our well structured Cyber Security Management Quarterly Action Plan. The topics discussed in this slide are Quarter, Action Taken, Responsible Person, Impact. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Manage Investor Relations With Effective Communication Security Token Offerings BCT SS
Manage Investor Relations With Effective Communication Security Token Offerings BCT SSThe following slide illustrates some ways to maintain effective and healthy relations with investors. It includes elements such as transparent communication, building investor relations team, conducting feedbacks and surveys, ensuring investor integration, etc. Increase audience engagement and knowledge by dispensing information using Manage Investor Relations With Effective Communication Security Token Offerings BCT SS. This template helps you present information on four stages. You can also present information on Transparent Communication, Investor Relations Team, Feedback And Surveys using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Cyber Security Risk Management Company In Powerpoint And Google Slides Cpb
Cyber Security Risk Management Company In Powerpoint And Google Slides CpbPresenting Cyber Security Risk Management Company In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Security Risk Management Company. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Website Security Management Action Plan Virtual Shop Designing For Attracting Customers
Website Security Management Action Plan Virtual Shop Designing For Attracting CustomersMentioned slide provides insights into site security management tips which can be implemented by businesses to prevent website hacking. It includes key components such as select secure domain registrar, use safe plugins, anti malware programs, regular backup, SSL certification, etc. Introducing Website Security Management Action Plan Virtual Shop Designing For Attracting Customers to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Criteria, Description, Priority, using this template. Grab it now to reap its full benefits.
-
 Cyber Security Risk Management Jobs In Powerpoint And Google Slides Cpb
Cyber Security Risk Management Jobs In Powerpoint And Google Slides CpbPresenting our Cyber Security Risk Management Jobs In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cyber Security Risk Management Jobs This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Security Plan To Prevent Cyber Framework For Cybersecurity Risk Management
Security Plan To Prevent Cyber Framework For Cybersecurity Risk ManagementThis slide indicates the framework for cybersecurity risk management. The major sub components of model are data sources, cyber intelligence and monitoring, threat and vulnerabilities, executive board and IT governance. Present the topic in a bit more detail with this Security Plan To Prevent Cyber Framework For Cybersecurity Risk Management. Use it as a tool for discussion and navigation on Cyber Security Communities, Information Sharing, Private Organizations, IT Governance. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Security Awareness And Crisis Management Communication Plan
Security Awareness And Crisis Management Communication PlanThe slide showcases crisis management communication plan used by companies to increase security awareness in their organization. It consists of points such as incident identification, security team, initial assessment and evaluation, incident classification, etc. Presenting our well structured Security Awareness And Crisis Management Communication Plan. The topics discussed in this slide are Identification, Security, Evaluation. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 US Digital Services Management Play 11 Administering Security And Privacy Through ReUSable
US Digital Services Management Play 11 Administering Security And Privacy Through ReUSableThis slide provides information regarding digital services play which helps in managing security and privacy through reUSable processes. During initial phase of new service designing, team leader engage with privacy, security and legal officer to assess type of information to be collected, how to secure it, etc. Deliver an outstanding presentation on the topic USing this US Digital Services Management Play 11 Administering Security And Privacy Through ReUSable Dispense information and present a thorough explanation of Department Or Agency, Secure Controllability USing the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Security Account Manager Salary In Powerpoint And Google Slides Cpb
Security Account Manager Salary In Powerpoint And Google Slides CpbPresenting our Security Account Manager Salary In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases three stages. It is useful to share insightful information on Security Account Manager Salary This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Manage Information Security In Powerpoint And Google Slides Cpb
Manage Information Security In Powerpoint And Google Slides CpbPresenting Manage Information Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase Six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Manage Information Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 3 Pillars Of Successful Project Security Management Plan
3 Pillars Of Successful Project Security Management PlanThis slide highlights the 3 pillars of a successful management plan for ensuring business project security. The purpose of this slide is to help the project manager ensure the optimized running of business processes through the use of an appropriately designed and installed security plan along with its maintenance.Presenting our set of slides with 3 Pillars Of Successful Project Security Management Plan. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Comprehensive Reviewing, Industry Standards, System Schematics.
-
 Best Practices For Network Security Management Plan
Best Practices For Network Security Management PlanThos slide showcases the best practices to be followed for establishing a network security management plan. The purpose of this slide is to help the business develop suitable network security in order to avoid breaches and attacks. It includes conducting regular data backups, frequent employee training, etc.Introducing our premium set of slides with Best Practices For Network Security Management Plan. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Implement Formal, Information Security, Governance Framework. So download instantly and tailor it with your information.
-
 Challenges Faced During Cyber Security Management Plan Implementation
Challenges Faced During Cyber Security Management Plan ImplementationThis slide highlights the challenges faced by businesses during the implementation of a cybersecurity management plan. The purpose of this slide is to help the business establish a suitable cyber security management plan through the elimination of structural vulnerabilities such as scarcity of skilled professionals, inability to adapt to evolving cyber attacks, etc.Presenting our well structured Challenges Faced During Cyber Security Management Plan Implementation. The topics discussed in this slide are Complicated Environments, Business Operations, Defending Against. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Critical Elements For Developing Information Security Management Plan
Critical Elements For Developing Information Security Management PlanThis slide shows the key elements for developing a successful information security management plan. This slide aims to help the company establish a robust and suitable security plan for protecting data against cyber threats and attacks. It includes components such as network security, physical measures, employee training, etc.Introducing our premium set of slides with Critical Elements For Developing Information Security Management Plan. Ellicudate the five stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Network Security, Data Backup, Physical Security. So download instantly and tailor it with your information.
-
 High Priority Tasks Under Network Security Management Plan
High Priority Tasks Under Network Security Management PlanThis slide showcases the high sakes tasks to be fulfilled under the network security management plan. The purpose of this slide is to help the business identify important tasks in order to ensure vulnerabilities sin the business network are mitigated. It includes tasks such as infrastructural implementation, monitoring plus analysis, etc.Presenting our set of slides with High Priority Tasks Under Network Security Management Plan. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Infrastructure Implementation, Ongoing Risk Assessment, Control Management.
-
 Icon For Business Security Management Plan
Icon For Business Security Management PlanIntroducing our premium set of slides with Icon For Business Security Management Plan. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon For Business Security, Management Plan. So download instantly and tailor it with your information.
-
 Icon For Information Security Management Plan
Icon For Information Security Management PlanIntroducing our Icon For Information Security Management Plan set of slides. The topics discussed in these slides are Icon Information, Security Management Plan. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Icon For Planning Cyber Security Management
Icon For Planning Cyber Security ManagementPresenting our well structured Icon For Planning Cyber Security Management. The topics discussed in this slide are Icon Planning Cyber, Security Management. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Icon For Security Risk Management Plan
Icon For Security Risk Management PlanIntroducing our Icon For Security Risk Management Plan set of slides. The topics discussed in these slides are Icon Security, Risk Management Plan. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
 Key Components Of A Security Management Plan
Key Components Of A Security Management PlanThis slide showcases the critical components of a business security plan. This slide aims to help the business management develop an effective security plan in case of emergencies or uncertainties to avoid financial losses. It includes elements such as risk assessments, security policy development, training and awareness of employees, etc.Presenting our set of slides with Key Components Of A Security Management Plan. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Develop Suitable, Strategies Procedures, Customized Business.
-
 Key Components Of Data Security Breach Management Plan
Key Components Of Data Security Breach Management PlanThis slide showcases the critical components of a business security breach management plan. This slide aims to help the business effectively manage a data security breach to prevent financial loss, market share loss, or reputational damage.Introducing our premium set of slides with Key Components Of Data Security Breach Management Plan. Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Prevent Identity, Credit Report Monitoring, Review Security Measures. So download instantly and tailor it with your information.
-
 KPIs For Evaluating Efficiency Of Security Management Plan
KPIs For Evaluating Efficiency Of Security Management PlanThis slide showcases the KPIs for measuring the efficiency of the security management plan. This slide aims to help the business develop a robust security management plan to prevent and mitigate breaches. It includes KPIs such as MTTD, TTT, and MTTA.Presenting our well structured Kpis For Evaluating Efficiency Of Security Management Plan. The topics discussed in this slide are Management Plan, Security Management, Prior Investigating. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Matrix For Cyber Security Risk Management Plan
Matrix For Cyber Security Risk Management PlanThis slide highlights the matrix for prioritizing a cyber security risk management plan. This slide aims to help the IT business firm ensure proper practices are implemented to prevent and mitigate risks through analysis of the risk based on factors such as intensity of impact, probability of occurrence, etc.Introducing our Matrix For Cyber Security Risk Management Plan set of slides. The topics discussed in these slides are Moderate Consequences, Major Consequences, Catastrophic Consequences. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
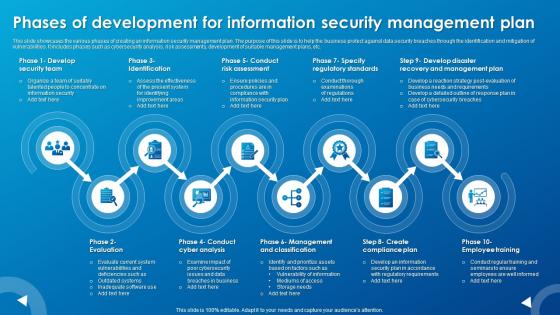 Phases Of Development For Information Security Management Plan
Phases Of Development For Information Security Management PlanThis slide showcases the various phases of creating an information security management plan. The purpose of this slide is to help the business protect against data security breaches through the identification and mitigation of vulnerabilities. It includes phases such as cybersecurity analysis, risk assessments, development of suitable management plans, etc.Presenting our set of slides with Phases Of Development For Information Security Management Plan. This exhibits information on ten stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Evaluate Current System, Outdated Systems, Inadequate Software.
-
 Process For Creating Network Security Management Plan
Process For Creating Network Security Management PlanThis slide showcases the process of network security in business. The main purpose of this slide is to understand and maintain network security in the workplace. This includes understanding business models, identifying threats, developing IT security policies, etc.Introducing our premium set of slides with Process For Creating Network Security Management Plan. Ellicudate the eight stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Understanding Business, Identifying Threat, Maintain Security Future. So download instantly and tailor it with your information.
-
 Roadmap For Establishing Effective Business Security Management Plan
Roadmap For Establishing Effective Business Security Management PlanThis slide showcases the roadmap for executing an effective business security management plan. This slide aims to help the business ensure sufficient security measures are put in place to avoid cyber attacks and data thefts. It includes steps such as risk assessment, framework development, plan reviews, etc.Presenting our set of slides with Roadmap For Establishing Effective Business Security Management Plan. This exhibits information on eight stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Conduct Security Assessment, Conduct Technology Evaluation, Implement Security Plan.
-
 Security Management Plan Ppt Powerpoint Presentation Diagram Graph Charts
Security Management Plan Ppt Powerpoint Presentation Diagram Graph ChartsPresenting our set of slides with Security Management Plan Ppt Powerpoint Presentation Diagram Graph Charts. This exhibits information on one stage of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security Management Plan.
-
 Step Wise Security Risk Management Plan
Step Wise Security Risk Management PlanThis slide depicts the step wise process for a security management plan. The purpose of this slide is to help enterprises successfully identify, assess, and mitigate risk through the use of suitable techniques and strategies. It includes steps such as risk identification, risk assessment, risk analysis, risk mitigation and management, etc.Introducing our premium set of slides with Step Wise Security Risk Management Plan. Ellicudate the six stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Determine Objectives, Risk Identification, Risk Assessment. So download instantly and tailor it with your information.
-
 Types Of Security Management Plans
Types Of Security Management PlansThis slide highlights several types of security management plans. This slide aims to help the business ensure security is introduced and maintained in various spheres such as network security, information security and cyber security.Presenting our set of slides with Types Of Security Management Plans. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Information Security, Management Plan, Network Security.
-
 Party Vendor Management Security Best Practices In Powerpoint And Google Slides Cpb
Party Vendor Management Security Best Practices In Powerpoint And Google Slides CpbPresenting Party Vendor Management Security Best Practices In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase six stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Party Vendor Management Security Best Practices. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.





